Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Attention: All Microsoft Sentinel features will be officially retired in Azure in China regions on August 18, 2026 per the announcement posted by 21Vianet.
This article shows you how to use the Syslog via AMA and Common Event Format (CEF) via AMA connectors to filter and ingest syslog and CEF messages from Linux machines, network devices, and security appliances. To learn more about these data connectors, see Syslog and Common Event Format (CEF) via AMA connectors for Microsoft Sentinel.
Prerequisites
Before you begin, you must have the resources configured and the appropriate permissions assigned, as described in this section.
Microsoft Sentinel prerequisites
Install the appropriate Microsoft Sentinel solution and make sure you have the permissions to complete the steps in this article.
Install the appropriate solution from the Content hub in Microsoft Sentinel. For more information, see Discover and manage Microsoft Sentinel out-of-the-box content.
Identify which data connector the Microsoft Sentinel solution requires Syslog via AMA or Common Event Format (CEF) via AMA and whether you need to install the Syslog or Common Event Format solution. To fulfill this prerequisite,
In the Content hub, select Manage on the installed solution and review the data connector listed.
If either Syslog via AMA or Common Event Format (CEF) via AMA isn't installed with the solution, identify whether you need to install the Syslog or Common Event Format solution:
Then install either the Syslog or Common Event Format solution from the content hub to get the related AMA data connector.
Have an Azure account with the following Azure role-based access control (Azure RBAC) roles:
Built-in role Scope Reason - Virtual Machine Contributor
- Azure Connected Machine
Resource Administrator- Virtual machines (VM)
- Virtual Machine Scale Sets
- Azure Arc-enabled servers
To deploy the agent Any role that includes the action
Microsoft.Resources/deployments/*- Subscription
- Resource group
- Existing data collection rule
To deploy Azure Resource Manager templates Monitoring Contributor - Subscription
- Resource group
- Existing data collection rule
To create or edit data collection rules
Log forwarder prerequisites
If you're collecting messages from a log forwarder, the following prerequisites apply:
You must have a designated Linux VM as a log forwarder to collect logs.
If your log forwarder isn't an Azure virtual machine, it must have the Azure Arc Connected Machine agent installed on it.
The Linux log forwarder VM must have Python 2.7 or 3 installed. Use the
python --versionorpython3 --versioncommand to check. If you're using Python 3, make sure it's set as the default command on the machine, or run scripts with the 'python3' command instead of 'python'.The log forwarder must have either the
syslog-ngorrsyslogdaemon enabled.Your log sources, security devices, and appliances, must be configured to send their log messages to the log forwarder's syslog daemon instead of to their local syslog daemon.
Note
When deploying the AMA to a Virtual Machine Scale Set (VMSS), you're strongly encouraged to use a load balancer that supports the round-robin method to ensure load distribution across all deployed instances.
Machine security prerequisites
Configure the machine's security according to your organization's security policy. For example, configure your network to align with your corporate network security policy and change the ports and protocols in the daemon to align with your requirements. To improve your machine security configuration, secure your VM in Azure, or review these best practices for network security.
If your devices are sending syslog and CEF logs over TLS because, for example, your log forwarder is in the cloud, you need to configure the syslog daemon (rsyslog or syslog-ng) to communicate in TLS. For more information, see:
Configure the data connector
The setup process for the Syslog via AMA or Common Event Format (CEF) via AMA data connectors includes the following steps:
- Install the Azure Monitor Agent and create a Data Collection Rule (DCR) by using either of the following methods:
- If you're collecting logs from other machines using a log forwarder, run the "installation" script on the log forwarder to configure the syslog daemon to listen for messages from other machines, and to open the necessary local ports.
Select the appropriate tab for instructions.
Create data collection rule (DCR)
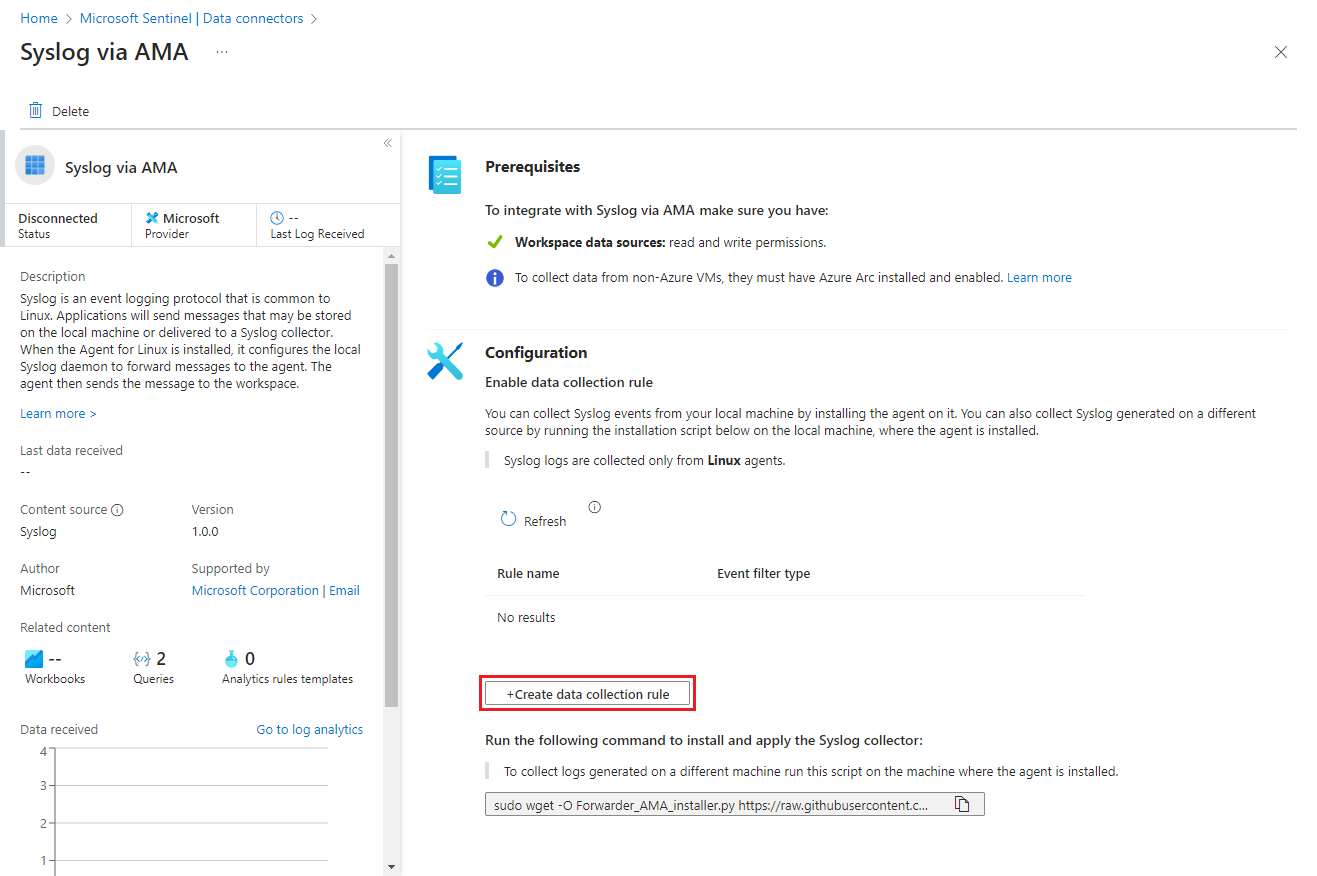
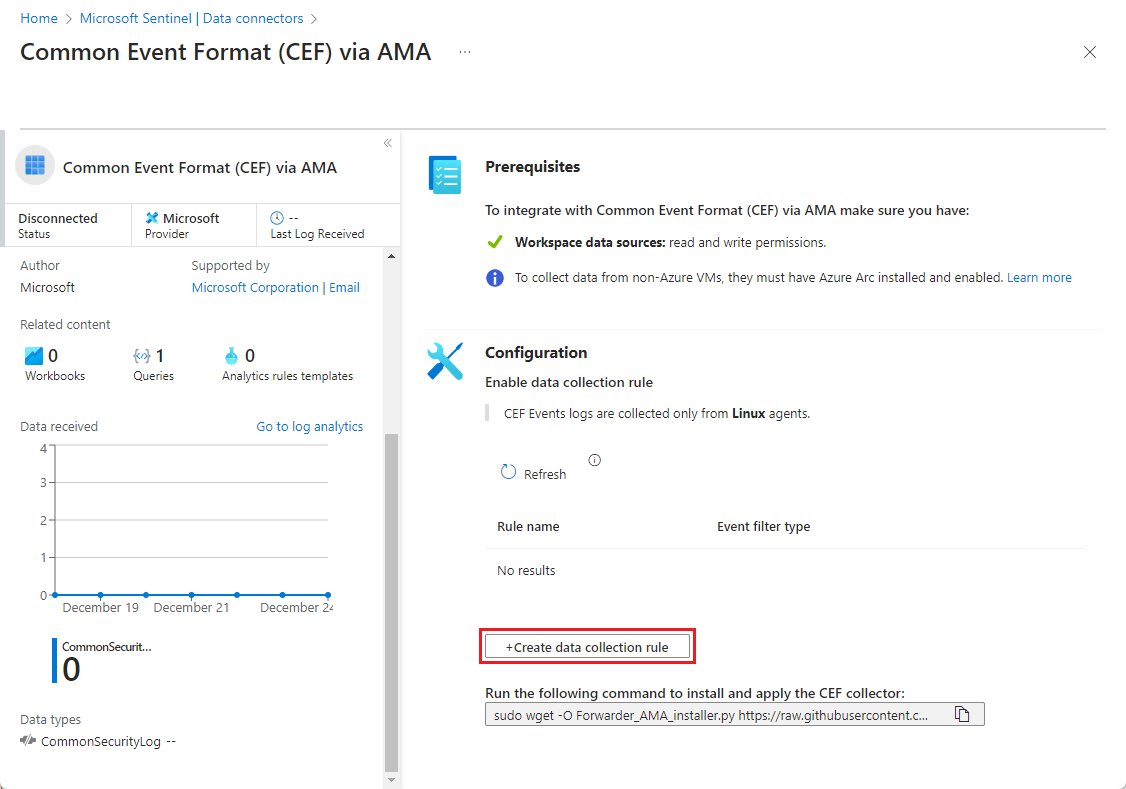
To get started, open either the Syslog via AMA or Common Event Format (CEF) via AMA data connector in Microsoft Sentinel and create a data collection rule (DCR).
In the Azure portal, under Configuration, select Data connectors.
For syslog, type Syslog in the Search box. From the results, select the Syslog via AMA connector.
For CEF, type CEF in the Search box. From the results, select the Common Event Format (CEF) via AMA connector.Select Open connector page on the details pane.
In the Configuration area, select +Create data collection rule.
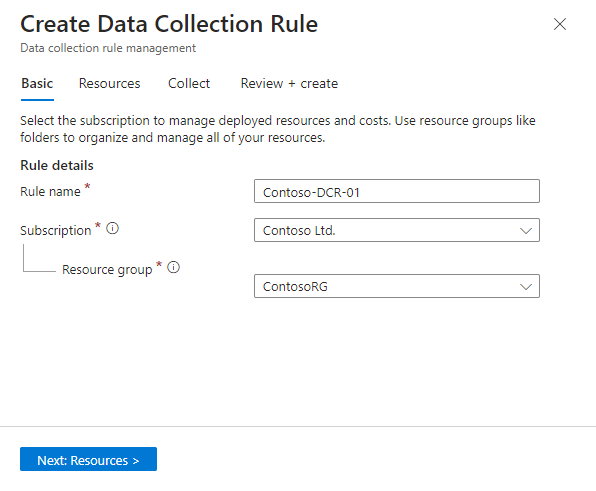
In the Basic tab:
- Type a DCR name.
- Select your subscription.
- Select the resource group where you want to locate your DCR.
Select Next: Resources >.
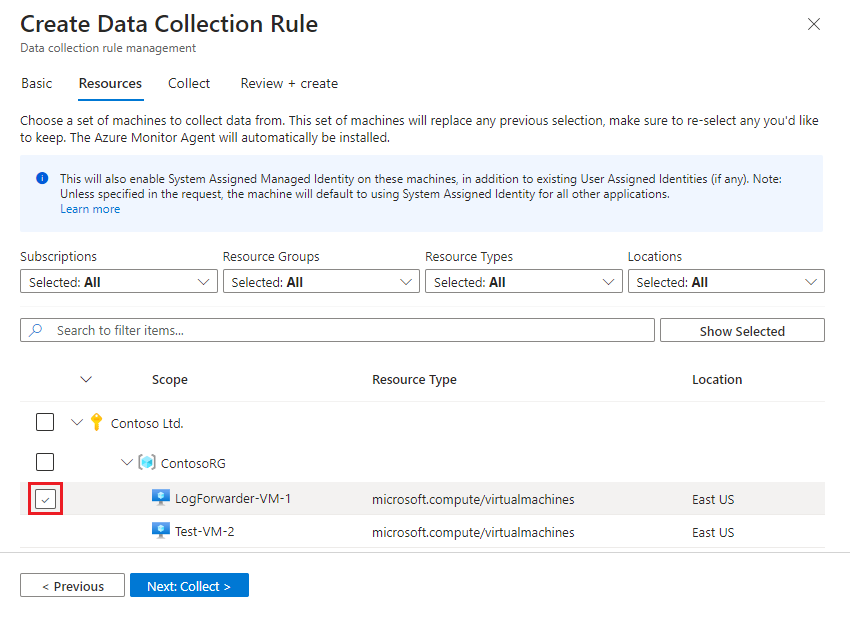
Define VM resources
In the Resources tab, select the machines on which you want to install the AMA—in this case, your log forwarder machine. If your log forwarder doesn't appear in the list, it might not have the Azure Connected Machine agent installed.
Use the available filters or search box to find your log forwarder VM. Expand a subscription in the list to see its resource groups, and a resource group to see its VMs.
Select the log forwarder VM that you want to install the AMA on. The check box appears next to the VM name when you hover over it.
Review your changes and select Next: Collect >.
Select facilities and severities
Be aware that using the same facility for both syslog and CEF messages might result in data ingestion duplication. For more information, see Data ingestion duplication avoidance.
In the Collect tab, select the minimum log level for each facility. When you select a log level, Microsoft Sentinel collects logs for the selected level and other levels with higher severity. For example, if you select LOG_ERR, Microsoft Sentinel collects logs for the LOG_ERR, LOG_CRIT, LOG_ALERT, and LOG_EMERG levels.
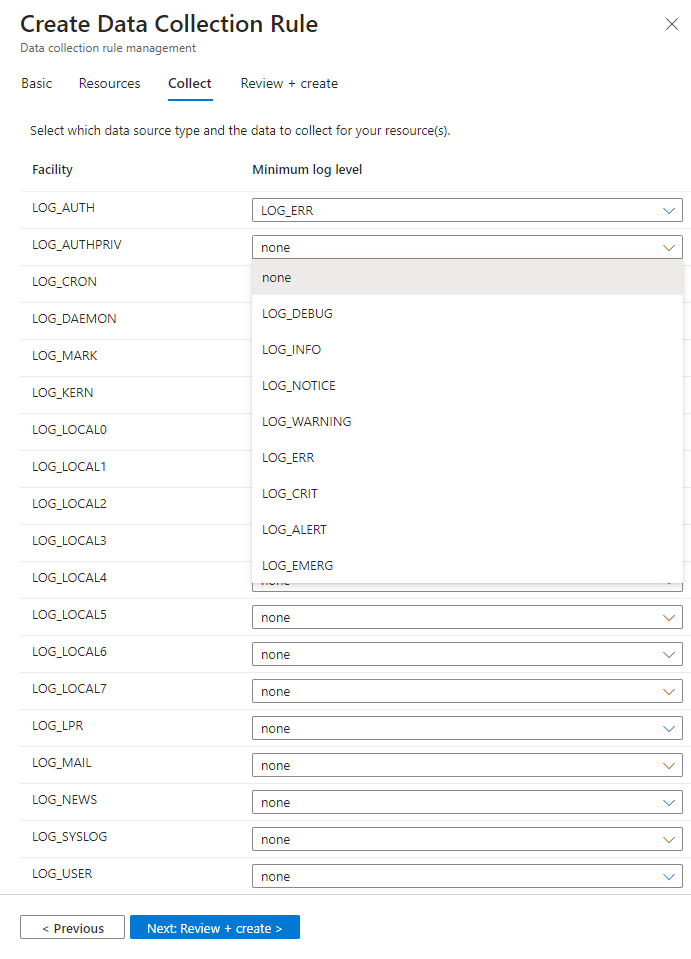
Review your selections and select Next: Review + create.
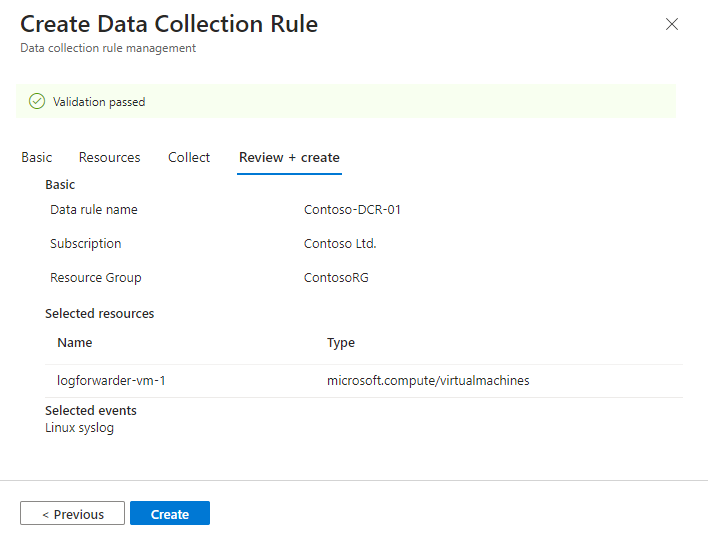
Review and create the rule
After you complete all the tabs, review what you entered and create the data collection rule.
In the Review and create tab, select Create.
The connector installs the Azure Monitor Agent on the machines you selected when creating your DCR.
Check the notifications in the Azure portal to see when the DCR is created and the agent is installed.
Select Refresh on the connector page to see the DCR displayed in the list.
Run the "installation" script
If you're using a log forwarder, configure the syslog daemon to listen for messages from other machines, and open the necessary local ports.
From the connector page, copy the command line that appears under Run the following command to install and apply the CEF collector:
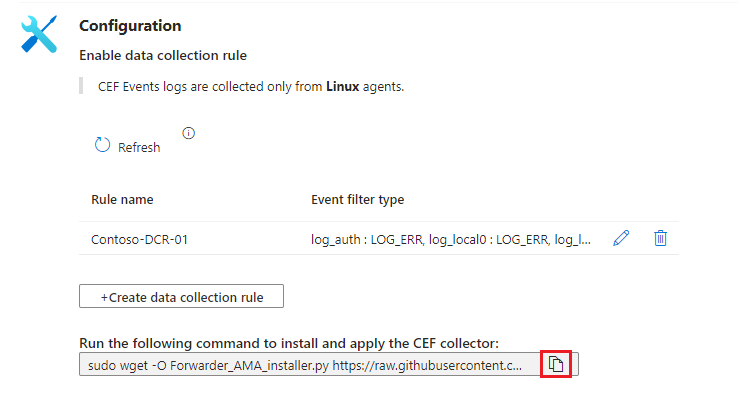
Or copy it from here:
sudo wget -O Forwarder_AMA_installer.py https://raw.githubusercontent.com/Azure/Azure-Sentinel/master/DataConnectors/Syslog/Forwarder_AMA_installer.py&&sudo python Forwarder_AMA_installer.pySign in to the log forwarder machine where you just installed the AMA.
Paste the command you copied in the last step to launch the installation script.
The script configures thersyslogorsyslog-ngdaemon to use the required protocol and restarts the daemon. The script opens port 514 to listen to incoming messages in both UDP and TCP protocols. To change this setting, refer to the syslog daemon configuration file according to the daemon type running on the machine:- Rsyslog:
/etc/rsyslog.conf - Syslog-ng:
/etc/syslog-ng/syslog-ng.conf
If you're using Python 3, and it's not set as the default command on the machine, substitute
python3forpythonin the pasted command. See Log forwarder prerequisites.Note
To avoid Full Disk scenarios where the agent can't function, we recommend that you set the
syslog-ngorrsyslogconfiguration not to store unneeded logs. A Full Disk scenario disrupts the function of the installed AMA. For more information, see RSyslog or Syslog-ng.- Rsyslog:
Test the connector
Verify that log messages from your linux machine or security devices and appliances are ingested into Microsoft Sentinel.
To validate that the syslog daemon is running on the UDP port and that the AMA is listening, run this command:
netstat -lnptvYou should see the
rsyslogorsyslog-ngdaemon listening on port 514.To capture messages sent from a logger or a connected device, run this command in the background:
sudo tcpdump -i any port 514 or 28330 -A -vv &After you complete the validation, stop
tcpdump. Typefg, and then select Ctrl+C.
Send test messages
To send demo messages, complete one of the following steps:
Use the
ncnetcat utility. In this example, the utility reads data posted through theechocommand with the newline switch turned off. The utility then writes the data to UDP port514on the localhost with no timeout. To execute the netcat utility, you might need to install another package.echo -n "<164>CEF:0|Mock-test|MOCK|common=event-format-test|end|TRAFFIC|1|rt=$common=event-formatted-receive_time" | nc -u -w0 localhost 514Use the
loggercommand. This example writes the message to thelocal 4facility, at severity levelWarning, to port514, on the local host, in the CEF RFC format. The-tand--rfc3164flags are used to comply with the expected RFC format.logger -p local4.warn -P 514 -n 127.0.0.1 --rfc3164 -t CEF "0|Mock-test|MOCK|common=event-format-test|end|TRAFFIC|rt=$common=event-formatted-receive_time"Test Cisco ASA ingestion using the following command:
echo -n "<164>%ASA-7-106010: Deny inbound TCP src inet:1.1.1.1 dst inet:2.2.2.2" | nc -u -w0 localhost 514After you run these commands, messages arrive on port 514 and forward to port 28330.
After sending test messages, query your Log Analytics workspace. Logs can take up to 20 minutes to appear in your workspace.
For CEF logs:
CommonSecurityLog
| where TimeGenerated > ago(1d)
| where DeviceProduct == "MOCK"
For Cisco ASA logs:
CommonSecurityLog
| where TimeGenerated > ago(1d)
| where DeviceVendor == "Cisco"
| where DeviceProduct == "ASA"
Additional troubleshooting
If you don't see traffic on port 514 or your test messages aren't ingested, see Troubleshoot Syslog and CEF via AMA connectors for Microsoft Sentinel to troubleshoot.