重要
从 2026 年 3 月 31 日起,Azure Kubernetes 服务(AKS)不再支持虚拟机(VM)的默认出站访问。 对于使用 AKS 托管虚拟网络选项 的新 AKS 群集,默认情况下会将群集的 子网放入专用子网 (defaultOutboundAccess = false)。 此设置 不会影响 AKS 管理的群集流量,后者使用显式配置的出站路径。 它可能会影响 不支持的方案,例如将其他资源部署到同一子网中。 使用此 BYO VNet 的群集不受 此更改影响。 在受支持的配置中,无需执行任何作。 有关此停用的详细信息,请参阅 Azure 更新停用公告。 若要随时了解公告和更新,请关注AKS 发行说明。
可以自定义 AKS 群集的流出量,以适应特定方案。 默认情况下,AKS 会创建一个标准负载均衡器来设置并用于出口。 但是,如果不允许公共 IP,或者流出量需要其他跃点,则默认设置可能无法满足所有方案的要求。
本文介绍了 AKS 群集中各种类型的出站连接。
注意
现在可以在创建群集后更新 outboundType。
重要
在非专用群集中,API 服务器群集流量是通过群集出站类型路由和处理的。 若要防止 API 服务器流量作为公共流量进行处理,请考虑使用 专用群集。
限制
- 设置
outboundType需要将 AKS 群集的vm-set-type指定为VirtualMachineScaleSets,将load-balancer-sku指定为Standard。
AKS 中的出站类型
可以使用以下出站类型配置 AKS 群集:负载均衡器、NAT 网关或用户定义的路由。 出站类型仅影响群集的出口流量。 有关详细信息,请参阅设置入口控制器。
loadBalancer 出站类型
负载均衡器用于通过 AKS 分配的公共 IP 的流出量。 出站类型 loadBalancer 支持 loadBalancer 类型的 Kubernetes 服务,此类型的服务应收到由 AKS 资源提供程序创建的负载均衡器传出的流量。
如果设置了 loadBalancer,AKS 将自动完成以下配置:
- 针对群集出口创建了公共 IP 地址。
- 将该公共 IP 地址分配给负载均衡器资源。
- 为群集中的代理节点设置负载均衡器的后端池。
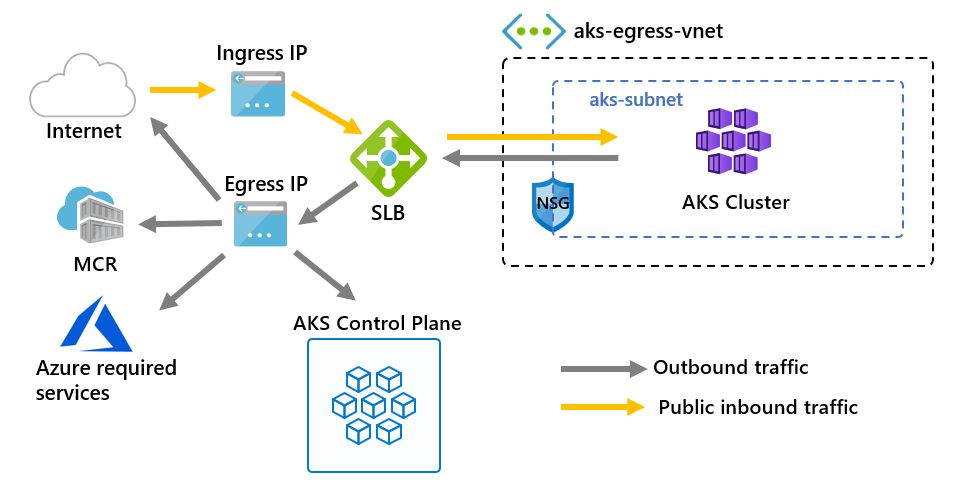
有关详细信息,请参阅在 AKS 中使用标准负载均衡器。
managedNatGateway 或 userAssignedNatGateway 出站类型
如果为 managedNatGateway 选择了 userAssignedNatGateway 或 outboundType,AKS 将依赖 Azure 网络 NAT 网关配置群集出口。
- 使用托管虚拟网络时选择
managedNatGateway。 AKS 将预配 NAT 网关并将其附加到群集子网。 - 使用自带虚拟网络时选择
userAssignedNatGateway。 此选项要求在创建群集之前创建 NAT 网关。
有关详细信息,请参阅将 NAT 网关与 AKS 配合使用。
userDefinedRouting 出站类型
注意
userDefinedRouting 出站类型是一种高级网络方案,需要正确的网络配置。
如果设置了 userDefinedRouting,AKS 不会自动配置出口路径。 出站设置由你完成。
必须将 AKS 群集部署到具有已配置的子网的现有虚拟网络中。 由于未使用标准负载均衡器 (SLB) 体系结构,因此必须建立显式流出量。 此体系结构需要向防火墙、网关、代理等设备显式发送出口流量,或需要允许 NAT 由分配给标准负载均衡器或设备的公共 IP 完成。
有关详细信息,请参阅通过用户定义的路由配置群集流出量。
创建群集后更新 outboundType
若在创建群集后更改出站类型,则会根据需要部署或移除资源,以将群集放入新的出口配置。
下面的表显示了托管虚拟网络和 BYO 虚拟网络的出站类型之间支持的迁移路径。
托管 VNet 支持的迁移路径
每行显示出站类型是否可以迁移到顶部列出的类型。 “支持”意味着迁移是可能的,而“不支持”或“N/A”则表示它不是。
| 从|到 | loadBalancer |
managedNATGateway |
userAssignedNATGateway |
userDefinedRouting |
none |
block |
|---|---|---|---|---|---|---|
loadBalancer |
空值 | 支持 | 不支持 | 不支持 | 支持 | 支持 |
managedNATGateway |
支持 | 空值 | 不支持 | 不支持 | 支持 | 支持 |
userAssignedNATGateway |
不支持 | 不支持 | 空值 | 不支持 | 不支持 | 不支持 |
none |
支持 | 支持 | 不支持 | 不支持 | 空值 | 支持 |
block |
支持 | 支持 | 不支持 | 不支持 | 支持 | 空值 |
BYO VNet 支持的迁移路径
| 从|到 | loadBalancer |
managedNATGateway |
userAssignedNATGateway |
userDefinedRouting |
none |
block |
|---|---|---|---|---|---|---|
loadBalancer |
空值 | 不支持 | 支持 | 支持 | 支持 | 不支持 |
managedNATGateway |
不支持 | 空值 | 不支持 | 不支持 | 不支持 | 不支持 |
userAssignedNATGateway |
支持 | 不支持 | 空值 | 支持 | 支持 | 不支持 |
userDefinedRouting |
支持 | 不支持 | 支持 | 空值 | 支持 | 不支持 |
none |
支持 | 不支持 | 支持 | 支持 | 空值 | 不支持 |
仅支持在 loadBalancer、managedNATGateway(如果使用托管虚拟网络)、userAssignedNATGateway 和 userDefinedRouting(如果使用自定义虚拟网络)之间进行迁移。
警告
将出站类型迁移到用户托管类型(userAssignedNATGateway 或 userDefinedRouting)将会更改群集的出站公共 IP 地址。
如果启用了授权 IP 范围,请确保将新的出站 IP 范围追加到授权 IP 范围。
警告
更改群集上的出站类型会中断网络连接,并将导致群集的出口 IP 地址发生变化。 如果将任何防火墙规则配置为限制来自群集的流量,需要更新这些规则以匹配新的出口 IP 地址。
更新群集以使用新的出站类型
注意
需要使用 >= 2.56 版本的 Azure CLI 迁移出站类型。 使用 az upgrade 更新到最新版本的 Azure CLI。
- 使用
az aks update命令更新群集的出站配置。
将群集从 loadbalancer 更新为 managedNATGateway
az aks update --resource-group <resourceGroup> --name <clusterName> --outbound-type managedNATGateway --nat-gateway-managed-outbound-ip-count <number of managed outbound ip>
将群集从 managedNATGateway 更新为 loadbalancer
az aks update --resource-group <resourceGroup> --name <clusterName> \
--outbound-type loadBalancer \
<--load-balancer-managed-outbound-ip-count <number of managed outbound ip>| --load-balancer-outbound-ips <outbound ip ids> | --load-balancer-outbound-ip-prefixes <outbound ip prefix ids> >
警告
不要重复使用已在先前的出站配置中使用的 IP 地址。
将群集从 managedNATGateway 更新为 userDefinedRouting
- 添加路由到默认路由表
0.0.0.0/0。 请参阅在 Azure Kubernetes 服务 (AKS) 中使用用户定义的路由表自定义群集出口
az aks update --resource-group <resourceGroup> --name <clusterName> --outbound-type userDefinedRouting
在 BYO vnet 方案中将群集从 loadbalancer 更新为 userAssignedNATGateway
- 将 nat 网关与关联工作负载的子网相关联。 请参阅创建托管或用户分配的 NAT 网关
az aks update --resource-group <resourceGroup> --name <clusterName> --outbound-type userAssignedNATGateway