Azure 基于角色的访问控制 (Azure RBAC) 可用于对 Azure 资源进行访问管理。 使用 Azure RBAC,可以在团队中对职责进行分配,仅向用户、组和应用程序授予执行作业所需的访问权限。 可以使用 Azure 门户、Azure 命令行工具或 Azure 管理 API 将基于角色的访问权限授予用户。
自动化帐户中的角色
在 Azure 自动化中,访问权限是通过将相应的 Azure 角色分配给自动化帐户作用域的用户、组和应用程序来授予的。 以下是自动化帐户所支持的内置角色:
| 角色 | 说明 |
|---|---|
| 所有者 | “所有者”角色允许访问自动化帐户中的所有资源和操作,包括访问其他用户、组和应用程序以管理自动化帐户。 |
| 贡献者 | “参与者”角色允许管理所有事项,修改其他用户对自动化帐户的访问权限除外。 |
| 读取者 | “读取者”角色允许查看自动化帐户中的所有资源,但不能进行任何更改。 |
| 自动化参与者 | 拥有“自动化参与者”角色后,你可管理自动化帐户中的所有资源,但无法修改其他用户对自动化帐户的访问权限。 |
| 自动化操作员 | 自动化操作员角色允许针对某个自动化帐户中的所有 Runbook 查看 Runbook 名称和属性,以及为其创建和管理作业。 如果想要防止他人查看或修改自动化帐户资源(例如凭据资产和 Runbook),但仍允许所在组织的成员执行这些 Runbook,则可使用此角色。 |
| 自动化作业操作员 | 自动化作业操作员角色允许针对某个自动化帐户中的所有 Runbook 创建和管理作业。 |
| 自动化 Runbook 操作员 | 自动化 Runbook 操作员角色允许查看某个 Runbook 的名称和属性。 |
| Log Analytics 参与者 | Log Analytics 参与者可以读取所有监视数据并编辑监视设置。 编辑监视设置包括向 VM 添加 VM 扩展、读取存储帐户密钥以便能够从 Azure 存储配置日志收集、创建和配置自动化帐户、添加 Azure 自动化功能以及配置对所有 Azure 资源的 Azure 诊断。 |
| Log Analytics 读者 | Log Analytics 读取者可以读取所有监视数据并编辑监视设置。 这包括查看 Azure 诊断在所有 Azure 资源上的配置。 |
| 监视参与者 | 监视参与者可以读取所有监视数据并更新监视设置。 |
| 监视读取者 | 监视读取者角色,可以读取所有监视数据。 |
| 用户访问管理员 | “用户访问管理员”角色允许管理用户对 Azure 自动化帐户的访问。 |
角色权限
下表描述授予每个角色的特定权限。 这可能包括授予权限的“操作”和限制权限的“不操作”。
所有者
所有者可管理所有内容,包括访问权限。 下表显示了授予角色的权限:
| 行动 | DESCRIPTION |
|---|---|
| Microsoft.Automation/automationAccounts/* | 创建和管理所有类型的资源。 |
贡献者
参与者可管理访问权限以外的所有内容 下表显示了授予和拒绝角色的权限:
| 行动 | 说明 |
|---|---|
| Microsoft.Automation/automationAccounts/* | 创建和管理所有类型的资源 |
| 无操作 | |
| 微软.授权/*/删除 | 删除角色和角色分配。 |
| Microsoft.Authorization/*/Write | 创建角色和角色分配。 |
| Microsoft.Authorization/elevateAccess/Action | 拒绝创建用户访问管理员。 |
读取者
注释
最近,我们更改了自动化帐户的内置读取者角色权限。 了解详细信息
读取者可以查看自动化帐户中的所有资源,但不能进行任何更改。
| 行动 | 说明 |
|---|---|
| Microsoft.Automation/automationAccounts/read | 查看自动化帐户中的所有资源。 |
自动化参与者
自动化参与者可管理自动化帐户中除访问权限之外的所有资源。 下表显示了授予角色的权限:
| 行动 | 说明 |
|---|---|
| Microsoft.Automation/automationAccounts/* | 创建和管理所有类型的资源。 |
| Microsoft.Authorization/*/read | 读取角色和角色分配。 |
| Microsoft.Resources/deployments/* | 创建和管理资源组部署。 |
| Microsoft.Resources/subscriptions/resourceGroups/read | 读取资源组部署。 |
| Microsoft.Support/* | 创建和管理支持票证。 |
| Microsoft.Insights/ActionGroups/* | 读取/写入/删除操作组。 |
| Microsoft.Insights/ActivityLogAlerts/* | 读取/写入/删除活动日志警报。 |
| Microsoft.Insights/diagnosticSettings/* | 读取/写入/删除诊断设置。 |
| Microsoft.Insights/MetricAlerts/* | 读取/写入/删除准实时指标警报。 |
| Microsoft.Insights/ScheduledQueryRules/* | 在 Azure Monitor 中读取/写入/删除日志警报。 |
| Microsoft.OperationalInsights/workspaces/sharedKeys/action | 列出 Log Analytics 工作区的密钥 |
注释
如果针对目标资源设置了适当权限,则可使用“自动化参与者”角色通过托管标识访问任何资源,或者通过运行方式帐户访问。 默认情况下,自动化运行方式帐户配置有订阅的参与者权限。 遵循最小权限原则,仔细分配仅执行 runbook 所需的权限。 例如,如果自动化帐户仅用于启动或停止 Azure 虚拟机,则分配给 Run As 帐户或托管标识的权限只需要用于启动或停止该虚拟机。 同样,如果 runbook 要从 Blob 存储读取,则分配只读权限。
分配权限时,建议使用分配给托管标识的 Azure 基于角色的访问控制 (RBAC)。 查看最佳方法建议,了解如何使用系统或用户分配的托管标识(包括生存期内的管理和治理)。
自动化操作员
自动化操作员能够针对某个自动化帐户中的所有 Runbook 创建和管理作业,以及读取 Runbook 名称和属性。
注释
如果希望控制操作员对各个 runbook 的访问,请勿设置此角色。 请改为结合使用“自动化作业操作员”和“自动化 Runbook 操作员”角色 。
下表显示了授予角色的权限:
| 行动 | 说明 |
|---|---|
| Microsoft.Authorization/*/read | 读取授权。 |
| 微软自动化/自动化帐户/混合运行簿工作组/读取 | 读取混合 Runbook 辅助角色资源。 |
| Microsoft.Automation/Automation账户/作业/读取 | 列出 runbook 的作业。 |
| Microsoft.Automation/automationAccounts/jobs/resume/action | 恢复已暂停的作业。 |
| Microsoft.Automation/automationAccounts/jobs/stop/action | 取消正在进行的作业。 |
| Microsoft.Automation/automationAccounts/jobs/streams/read | 读取作业流和输出。 |
| Microsoft.Automation/automationAccounts/jobs/output/read | 获取作业的输出。 |
| Microsoft.Automation/automationAccounts/jobs/suspend/action (挂起操作) | 暂停正在进行的作业。 |
| Microsoft.Automation/automationAccounts/jobs/write | 创建作业。 |
| Microsoft.Automation/automationAccounts/jobSchedules/read | 获取 Azure 自动化作业计划。 |
| Microsoft.Automation/automationAccounts/jobSchedules/write | 创建 Azure 自动化作业计划。 |
| Microsoft.Automation/automationAccounts/linkedWorkspace/read | 获取链接到自动化帐户的工作区。 |
| Microsoft.Automation/automationAccounts/read | 获取 Azure 自动化帐户。 |
| Microsoft.Automation/automationAccounts/runbooks/read | 获取 Azure 自动化 Runbook。 |
| Microsoft.自动化/自动化帐户/计划/读取 | 获取 Azure 自动化计划资产。 |
| Microsoft.Automation/automationAccounts/schedules/写 | 创建或更新 Azure 自动化计划资产。 |
| Microsoft.Resources/subscriptions/resourceGroups/read | 读取角色和角色分配。 |
| Microsoft.Resources/deployments/* | 创建和管理资源组部署。 |
| Microsoft.Insights/alertRules/* | 创建和管理警报规则。 |
| Microsoft.Support/* | 创建和管理支持票证。 |
| Microsoft.ResourceHealth/可用性状态/读取 | 获取指定范围内所有资源的可用性状态。 |
自动化作业操作员
自动化作业操作员角色是在自动化帐户范围内授予的。 这将向操作员授予权限来为帐户中的所有 Runbook 创建和管理作业。 如果为作业操作员角色授予了对包含自动化帐户的资源组的读取权限,则该角色的成员能够启动 runbook。 但他们不能创建、编辑或删除 Runbook。
下表显示了授予角色的权限:
| 行动 | 说明 |
|---|---|
| Microsoft.Authorization/*/read | 读取授权。 |
| Microsoft.Automation/Automation账户/作业/读取 | 列出 runbook 的作业。 |
| Microsoft.Automation/automationAccounts/jobs/resume/action | 恢复已暂停的作业。 |
| Microsoft.Automation/automationAccounts/jobs/stop/action | 取消正在进行的作业。 |
| Microsoft.Automation/automationAccounts/jobs/streams/read | 读取作业流和输出。 |
| Microsoft.Automation/automationAccounts/jobs/suspend/action (挂起操作) | 暂停正在进行的作业。 |
| Microsoft.Automation/automationAccounts/jobs/write | 创建作业。 |
| Microsoft.Resources/subscriptions/resourceGroups/read | 读取角色和角色分配。 |
| Microsoft.Resources/deployments/* | 创建和管理资源组部署。 |
| Microsoft.Insights/alertRules/* | 创建和管理警报规则。 |
| Microsoft.Support/* | 创建和管理支持票证。 |
| 微软自动化/自动化帐户/混合运行簿工作组/读取 | 读取混合 Runbook 辅助角色组。 |
| Microsoft.Automation/automationAccounts/jobs/output/read | 获取作业的输出。 |
自动化 Runbook 操作员
自动化 Runbook 操作员角色在 Runbook 范围授予。 自动化 Runbook 操作员可以查看 Runbook 的名称和属性。 将此角色与“自动化作业操作员”角色组合使用时,也会使操作员能够为 Runbook 创建和管理作业。 下表显示了授予角色的权限:
| 行动 | 说明 |
|---|---|
| Microsoft.Automation/automationAccounts/runbooks/read | 列出 runbook。 |
| Microsoft.Authorization/*/read | 读取授权。 |
| Microsoft.Resources/subscriptions/resourceGroups/read | 读取角色和角色分配。 |
| Microsoft.Resources/deployments/* | 创建和管理资源组部署。 |
| Microsoft.Insights/alertRules/* | 创建和管理警报规则。 |
| Microsoft.Support/* | 创建和管理支持票证。 |
Log Analytics 参与者
Log Analytics 参与者可以读取所有监视数据并编辑监视设置。 编辑监视设置包括向 VM 添加 VM 扩展、读取存储帐户密钥以便能够从 Azure 存储配置日志收集、创建和配置自动化帐户、添加功能以及配置对所有 Azure 资源的 Azure 诊断。 下表显示了授予角色的权限:
| 行动 | 说明 |
|---|---|
| */读取 | 读取除密码外的所有类型的资源。 |
| Microsoft.ClassicCompute/virtualMachines/extensions/* | 创建和管理虚拟机扩展。 |
| Microsoft.ClassicStorage/storageAccounts/列出密钥/操作 | 列出经典存储帐户密钥。 |
| Microsoft.Compute/virtualMachines/extensions/* | 创建和管理经典虚拟机扩展。 |
| Microsoft.Insights/alertRules/* | 读取/写入/删除警报规则。 |
| Microsoft.Insights/diagnosticSettings/* | 读取/写入/删除诊断设置。 |
| Microsoft.OperationalInsights/* | 管理 Azure Monitor 日志。 |
| Microsoft.OperationsManagement/* | 管理工作区中的 Azure 自动化功能。 |
| Microsoft.Resources/deployments/* | 创建和管理资源组部署。 |
| Microsoft.Resources/subscriptions/resourcegroups/deployments/* | 创建和管理资源组部署。 |
| Microsoft.Storage/storageAccounts/listKeys/action | 列出存储帐户密钥。 |
| Microsoft.Support/* | 创建和管理支持票证。 |
| Microsoft.HybridCompute/machines/extensions/write | 安装或更新 Azure Arc 扩展。 |
Log Analytics 读者
Log Analytics 读者可以查看和搜索所有监视数据并查看监视设置,其中包括查看所有 Azure 资源上的 Azure 诊断的配置。 下表显示了授予或拒绝角色的权限:
| 行动 | 说明 |
|---|---|
| */读取 | 读取除密码外的所有类型的资源。 |
| Microsoft.OperationalInsights/workspaces/analytics/query/action | 管理 Azure Monitor 日志中的查询。 |
| Microsoft.OperationalInsights/workspaces/search/action (用于搜索工作区的操作点) | 搜索 Azure Monitor 日志数据。 |
| Microsoft.Support/* | 创建和管理支持票证。 |
| 无操作 | |
| Microsoft.OperationalInsights/workspaces/sharedKeys/read | 无法读取共享访问密钥。 |
监视参与者
监视参与者可以读取所有监视数据并更新监视设置。 下表显示了授予角色的权限:
| 行动 | 说明 |
|---|---|
| */读取 | 读取除密码外的所有类型的资源。 |
| Microsoft.AlertsManagement/alerts/* | 管理警报。 |
| Microsoft.AlertsManagement/alertsSummary/* | 管理警报仪表板。 |
| Microsoft.Insights/AlertRules/* | 管理警报规则。 |
| Microsoft.Insights/components/* | 管理 Application Insights 组件。 |
| Microsoft.Insights/DiagnosticSettings/* | 管理诊断设置。 |
| Microsoft.Insights/eventtypes/* | 列出订阅中的活动日志事件(管理事件)。 此权限适用于对活动日志的编程和门户访问。 |
| Microsoft.Insights/LogDefinitions/* | 需要通过门户访问活动日志的用户需要此权限。 列出活动日志中的日志类别。 |
| Microsoft.Insights/MetricDefinitions/* | 读取指标定义(资源可用的指标类型列表)。 |
| Microsoft.Insights/Metrics/* | 读取资源的指标。 |
| Microsoft.Insights/Register/Action | 注册 Microsoft.Insights 提供程序。 |
| Microsoft.Insights/webtests/* | 管理 Application Insights Web 测试。 |
| Microsoft.OperationalInsights/workspaces/intelligencepacks/* | 管理 Azure Monitor 日志解决方案包。 |
| Microsoft.OperationalInsights/workspaces/savedSearches/* | 管理 Azure Monitor 日志保存的搜索。 |
| Microsoft.OperationalInsights/workspaces/search/action (用于搜索工作区的操作点) | 搜索 Log Analytics 工作区。 |
| Microsoft.OperationalInsights/workspaces/sharedKeys/action | 列出 Log Analytics 工作区的键。 |
| Microsoft.OperationalInsights/workspaces/storageinsightconfigs/* | 管理 Azure Monitor 日志存储见解配置。 |
| Microsoft.Support/* | 创建和管理支持票证。 |
| Microsoft.WorkloadMonitor/workloads/* | 管理工作负荷。 |
监视读取者
监视读取者可以读取所有监视数据。 下表显示了授予角色的权限:
| 行动 | 说明 |
|---|---|
| */读取 | 读取除密码外的所有类型的资源。 |
| Microsoft.OperationalInsights/workspaces/search/action (用于搜索工作区的操作点) | 搜索 Log Analytics 工作区。 |
| Microsoft.Support/* | 创建和管理支持票证 |
用户访问管理员
用户访问管理员可管理 Azure 资源的用户访问权限。 下表显示了授予角色的权限:
| 行动 | 说明 |
|---|---|
| */读取 | 读取所有资源。 |
| Microsoft.Authorization/* | 管理授权 |
| Microsoft.Support/* | 创建和管理支持票证 |
读取者角色访问权限
重要
为了加强整体 Azure 自动化安全状况,内置 RBAC 读取者将无法通过 API 调用 GET /AUTOMATIONACCOUNTS/AGENTREGISTRATIONINFORMATION 来访问自动化帐户密钥。
自动化帐户的内置读取者角色不能使用 API – GET /AUTOMATIONACCOUNTS/AGENTREGISTRATIONINFORMATION 来提取自动化帐户密钥。 这是一项会提供敏感信息的高权限操作,可能造成安全风险,因为拥有较低权限的可恨恶意参与者可以访问自动化帐户密钥,并使用提升的权限级别执行操作。
若要访问 API – GET /AUTOMATIONACCOUNTS/AGENTREGISTRATIONINFORMATION,建议切换到内置角色(如所有者、参与者或自动化参与者)来访问自动化帐户密钥。 默认情况下,这些角色将具有 listKeys 权限。 我们建议你创建具有有限权限的自定义角色来访问自动化帐户密钥,这是最佳做法。 对于自定义角色,需要向角色定义添加 Microsoft.Automation/automationAccounts/listKeys/action 权限。
详细了解如何通过 Azure 门户创建自定义角色。
功能设置权限
以下部分介绍启用更新管理功能所需的最低权限。
从虚拟机启用更新管理的权限
| 行动 | 许可 | 最小范围 |
|---|---|---|
| 写入新部署 | Microsoft.Resources/deployments/* | 订阅 |
| 写入新资源组 | Microsoft.Resources/subscriptions/resourceGroups/write | 订阅 |
| 创建新的默认工作区 | Microsoft.OperationalInsights/workspaces/write | 资源组 |
| 创建新帐户 | Microsoft.Automation/automationAccounts/write | 资源组 |
| 链接工作区和帐户 | Microsoft.OperationalInsights/workspaces/write Microsoft.Automation/automationAccounts/read |
工作区 自动化帐户 |
| 创建 MMA 扩展 | Microsoft.Compute/virtualMachines/write(写入虚拟机) | 虚拟机 |
| 创建保存的搜索 | Microsoft.OperationalInsights/workspaces/write | 工作空间 |
| 创建范围配置 | Microsoft.OperationalInsights/workspaces/write | 工作空间 |
| 加入状态检查 - 读取工作区 | Microsoft.OperationalInsights/workspaces/read | 工作空间 |
| 加入状态检查 - 读取帐户的链接工作区属性 | Microsoft.Automation/automationAccounts/read | 自动化帐户 |
| 加入状态检查 - 读取解决方案 | Microsoft.OperationalInsights/workspaces/intelligencepacks/read (This is not translated as it is a technical string) | 解决方案 |
| 加入状态检查 - 读取 VM | Microsoft.Compute/virtualMachines/read | 虚拟机 |
| 加入状态检查 - 读取帐户 | Microsoft.Automation/automationAccounts/read | 自动化帐户 |
| VM 的加入工作区检查1 | Microsoft.OperationalInsights/workspaces/read | 订阅 |
| 注册 Log Analytics 提供程序 | Microsoft.Insights/register/action | 订阅 |
1 通过 VM 门户体验启用功能需要此权限。
从自动化帐户启用更新管理的权限
| 行动 | 许可 | 最小范围 |
|---|---|---|
| 新建部署 | Microsoft.Resources/deployments/* | 订阅 |
| 新建资源组 | Microsoft.Resources/subscriptions/resourceGroups/write | 订阅 |
| AutomationOnboarding 边栏选项卡 - 创建新工作区 | Microsoft.OperationalInsights/workspaces/write | 资源组 |
| AutomationOnboarding 边栏选项卡 - 读取链接的工作区 | Microsoft.Automation/automationAccounts/read | 自动化帐户 |
| AutomationOnboarding 边栏选项卡 - 读取解决方案 | Microsoft.OperationalInsights/workspaces/intelligencepacks/read (This is not translated as it is a technical string) | 解决方案 |
| AutomationOnboarding 边栏选项卡 - 读取工作区 | Microsoft.OperationalInsights/workspaces/intelligencepacks/read (This is not translated as it is a technical string) | 工作空间 |
| 创建工作区和帐户的链接 | Microsoft.OperationalInsights/workspaces/write | 工作空间 |
| 写入 shoebox 帐户 | Microsoft.Automation/automationAccounts/write | 帐户 |
| 创建/编辑保存的搜索 | Microsoft.OperationalInsights/workspaces/write | 工作空间 |
| 创建/编辑范围配置 | Microsoft.OperationalInsights/workspaces/write | 工作空间 |
| 注册 Log Analytics 提供程序 | Microsoft.Insights/register/action | 订阅 |
| 步骤 2 - 启用多个 VM | ||
| VMOnboarding 边栏选项卡 - 创建 MMA 扩展 | Microsoft.Compute/virtualMachines/write(写入虚拟机) | 虚拟机 |
| 创建/编辑保存的搜索 | Microsoft.OperationalInsights/workspaces/write | 工作空间 |
| 创建/编辑范围配置 | Microsoft.OperationalInsights/workspaces/write | 工作空间 |
管理混合工作组和混合工作者的角色权限
你可以在自动化中创建 Azure 自定义角色,并向混合辅助角色组和混合辅助角色授予以下权限:
为自动化帐户配置 Azure RBAC
以下部分演示如何通过 Azure 门户和 PowerShell 在自动化帐户上配置 Azure RBAC。
使用 Azure 门户配置 Azure RBAC
登录到 Azure 门户,然后从“自动化帐户”页打开自动化帐户。
选择“访问控制(IAM)”并从可用角色列表中选择角色。 可以选择自动化帐户所支持的任何可用的内置角色,或者可能已定义的任何自定义角色。 将角色分配给要向其授予权限的用户。
有关详细步骤,请参阅使用 Azure 门户分配 Azure 角色。
注释
只能在自动化帐户范围内设置基于角色的访问控制,不能在自动化帐户下的任何资源上设置。
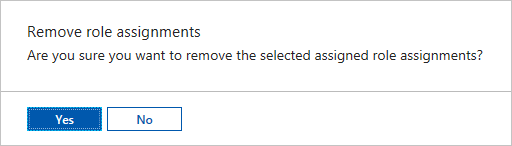
删除用户的角色分配
可以删除不管理自动化帐户或不再为组织工作的用户的访问权限。 以下步骤演示如何删除用户的角色分配。 有关详细步骤,请参阅删除 Azure 角色分配:
在要删除访问权限的范围(例如管理组、订阅、资源组或资源)内打开“访问控制(IAM)”。
选择“角色分配”选项卡以查看在此范围内的所有角色分配。
在角色分配列表中,在具有要删除的角色分配的用户旁边添加一个复选标记。
选择 删除。
使用 PowerShell 配置 Azure RBAC
还可以使用以下 Azure PowerShell cmdlet 为自动化帐户配置基于角色的访问权限:
Get-AzRoleDefinition 列出了 Microsoft Entra ID 中提供的所有 Azure 角色。 可以将此 cmdlet 与 Name 参数一起使用来列出特定角色可以执行的所有操作。
Get-AzRoleDefinition -Name 'Automation Operator'
下面是示例输出:
Name : Automation Operator
Id : d3881f73-407a-4167-8283-e981cbba0404
IsCustom : False
Description : Automation Operators are able to start, stop, suspend, and resume jobs
Actions : {Microsoft.Authorization/*/read, Microsoft.Automation/automationAccounts/jobs/read, Microsoft.Automation/automationAccounts/jobs/resume/action,
Microsoft.Automation/automationAccounts/jobs/stop/action...}
NotActions : {}
AssignableScopes : {/}
Get-AzRoleAssignment 列出了指定范围内的 Azure 角色分配。 在没有任何参数的情况下,此 cmdlet 返回在订阅下进行的所有角色分配。 使用 ExpandPrincipalGroups 参数可列出针对指定用户和该用户所在组的访问权限分配。
示例: 使用以下 cmdlet 列出自动化帐户中的所有用户及其角色。
Get-AzRoleAssignment -Scope '/subscriptions/<SubscriptionID>/resourcegroups/<Resource Group Name>/Providers/Microsoft.Automation/automationAccounts/<Automation account name>'
下面是示例输出:
RoleAssignmentId : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Automation/automationAccounts/myAutomationAccount/provid
ers/Microsoft.Authorization/roleAssignments/00000000-0000-0000-0000-000000000000
Scope : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/myResourceGroup/providers/Microsoft.Automation/automationAccounts/myAutomationAccount
DisplayName : admin@contoso.com
SignInName : admin@contoso.com
RoleDefinitionName : Automation Operator
RoleDefinitionId : d3881f73-407a-4167-8283-e981cbba0404
ObjectId : aaaaaaaa-0000-1111-2222-bbbbbbbbbbbb
ObjectType : User
使用 New-AzRoleAssignment 为特定范围内的用户、组和应用程序分配访问权限。
示例: 使用以下命令为“自动化帐户”范围中的用户分配“自动化操作员”角色。
New-AzRoleAssignment -SignInName <sign-in Id of a user you wish to grant access> -RoleDefinitionName 'Automation operator' -Scope '/subscriptions/<SubscriptionID>/resourcegroups/<Resource Group Name>/Providers/Microsoft.Automation/automationAccounts/<Automation account name>'
下面是示例输出:
RoleAssignmentId : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourcegroups/myResourceGroup/Providers/Microsoft.Automation/automationAccounts/myAutomationAccount/provid
ers/Microsoft.Authorization/roleAssignments/00000000-0000-0000-0000-000000000000
Scope : /subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourcegroups/myResourceGroup/Providers/Microsoft.Automation/automationAccounts/myAutomationAccount
DisplayName : admin@contoso.com
SignInName : admin@contoso.com
RoleDefinitionName : Automation Operator
RoleDefinitionId : d3881f73-407a-4167-8283-e981cbba0404
ObjectId : bbbbbbbb-1111-2222-3333-cccccccccccc
ObjectType : User
使用 Remove-AzRoleAssignment 从特定范围中删除指定用户、组或应用程序的访问权限。
示例: 使用以下命令从自动化帐户范围的自动化操作员角色中删除用户。
Remove-AzRoleAssignment -SignInName <sign-in Id of a user you wish to remove> -RoleDefinitionName 'Automation Operator' -Scope '/subscriptions/<SubscriptionID>/resourcegroups/<Resource Group Name>/Providers/Microsoft.Automation/automationAccounts/<Automation account name>'
在前面的示例中,将 sign-in ID of a user you wish to remove、SubscriptionID、Resource Group Name 和 Automation account name 替换为帐户详细信息。 出现提示时选择“是”以在继续删除用户角色分配前确认。
自动化操作员角色的用户体验 - 自动化帐户
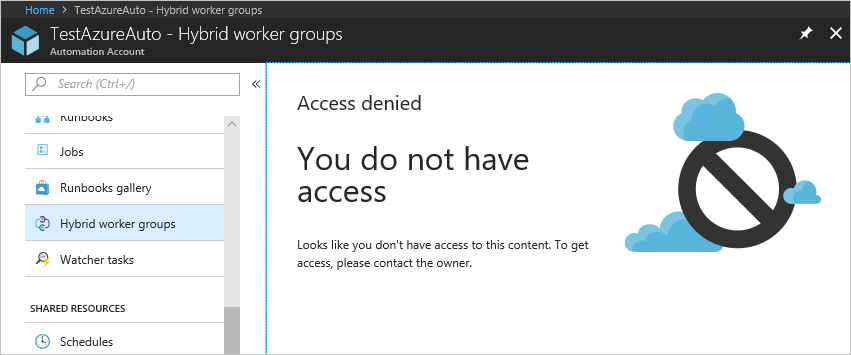
在自动化帐户范围内分配了自动化操作员角色的用户,在查看分配到的自动化帐户时,只能查看在自动化帐户中创建的 Runbook、Runbook 作业和计划的列表。 此用户无法查看这些项的定义。 该用户可以启动、停止、暂停、恢复或计划 Runbook 作业。 但是,此用户无法访问其他自动化资源,例如配置、混合 Runbook 辅助角色组或 DSC 节点。
为 runbook 配置 Azure RBAC
通过 Azure 自动化,可以将 Azure 角色分配给特定的 runbook。 若要执行此操作,运行以下脚本将用户添加到特定 Runbook。 自动化帐户管理员或租户管理员可以运行此脚本。
$rgName = "<Resource Group Name>" # Resource Group name for the Automation account
$automationAccountName ="<Automation account name>" # Name of the Automation account
$rbName = "<Name of Runbook>" # Name of the runbook
$userId = "<User ObjectId>" # Azure Active Directory (AAD) user's ObjectId from the directory
# Gets the Automation account resource
$aa = Get-AzResource -ResourceGroupName $rgName -ResourceType "Microsoft.Automation/automationAccounts" -ResourceName $automationAccountName
# Get the Runbook resource
$rb = Get-AzResource -ResourceGroupName $rgName -ResourceType "Microsoft.Automation/automationAccounts/runbooks" -ResourceName "$rbName"
# The Automation Job Operator role only needs to be run once per user.
New-AzRoleAssignment -ObjectId $userId -RoleDefinitionName "Automation Job Operator" -Scope $aa.ResourceId
# Adds the user to the Automation Runbook Operator role to the Runbook scope
New-AzRoleAssignment -ObjectId $userId -RoleDefinitionName "Automation Runbook Operator" -Scope $rb.ResourceId
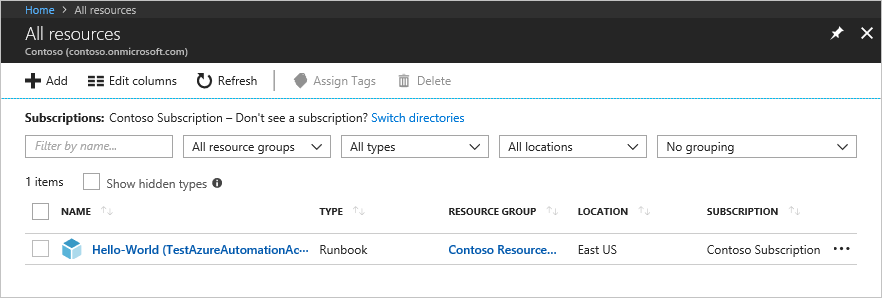
运行脚本后,让用户登录到 Azure 门户并选择“所有资源”。 在列表中,用户可以看到以自动化 Runbook 操作员身份添加的 Runbook。
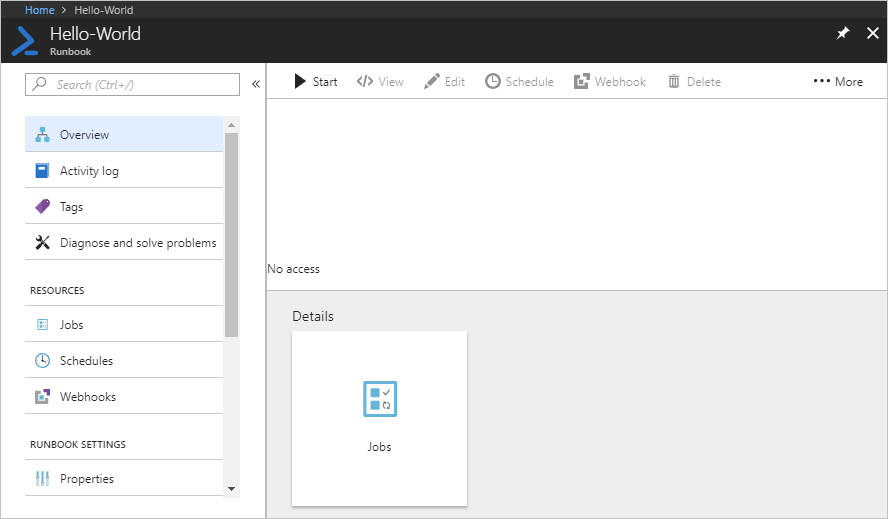
自动化操作员角色的用户体验 - Runbook
在 Runbook 范围内分配了自动化操作员角色的用户,在查看分配到的 Runbook 时,只能启动 Runbook 和查看 Runbook 作业。
后续步骤
- 若要了解安全准则,请参阅 Azure 自动化中的安全最佳做法。
- 若要详细了解使用 PowerShell 的 Azure RBAC,请参阅使用 Azure PowerShell 添加或删除 Azure 角色分配。
- 有关 Runbook 类型的详细信息,请参阅 Azure 自动化 Runbook 类型。
- 若要启动 Runbook,请参阅在 Azure 自动化中启动 Runbook。