如果 Azure 内置角色不满足组织的特定需求,你可以创建自己的自定义角色。 与内置角色一样,可将自定义角色分配到管理组、订阅和资源组范围内的用户、组与服务主体。
自定义角色可在信任同一 Microsoft Entra 租户的订阅之间共享。 每个租户都有 5,000 个自定义角色的限制。 (由世纪互联运营的 Microsoft Azure 的限制为 2000 个自定义角色。)可以使用 Azure 门户、Azure PowerShell、Azure CLI 或 REST API 创建自定义角色。
创建自定义角色的步骤
下面是创建自定义角色的基本步骤。
确定所需的权限。
创建自定义角色时,需要清楚可以执行的操作以定义权限。 通常,我们会从一个现有的内置角色着手,并根据需要对其进行修改。 将操作添加到
Actions或NotActions属性中的角色定义中。 如果有数据操作,请将这些操作添加到DataActions或NotDataActions属性。有关详细信息,请参阅下一部分:如何确定所需的权限。
确定如何创建自定义角色。
可以使用 Azure 门户、Azure PowerShell、Azure CLI 或 REST API 创建自定义角色。
创建自定义角色。
最简单的方法是使用 Azure 门户。 要查看使用 Azure 门户创建自定义角色的步骤,请参阅使用 Azure 门户创建或更新 Azure 自定义角色。
测试自定义角色。
创建自定义角色后,必须对其进行测试,以验证它是否按预期工作。 如果以后需要进行调整,可以更新自定义角色。
如何确定所需的权限
Azure 具有数千个权限,你可将这些权限包含在自定义角色中。 可通过一些方法来确定要添加到自定义角色的权限:
查看现有的内置角色。
你可能需要修改现有角色或组合多个角色中使用的权限。
列出要授予对其的访问权限的 Azure 服务。
-
Azure 服务通过资源提供程序公开其功能和权限。 例如,Microsoft.Compute 资源提供程序提供虚拟机资源,而 Microsoft.Billing 资源提供程序提供订阅和计费资源。 了解资源提供程序可以帮助你缩小和确定自定义角色所需的权限。
使用 Azure 门户创建自定义角色时,还可以通过搜索关键字来确定资源提供程序。 使用 Azure 门户创建或更新 Azure 自定义角色中介绍了此搜索功能。
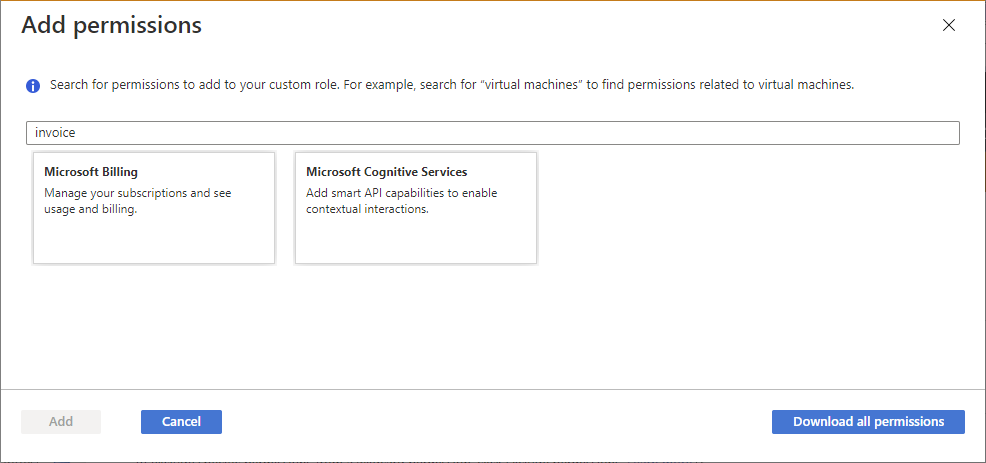
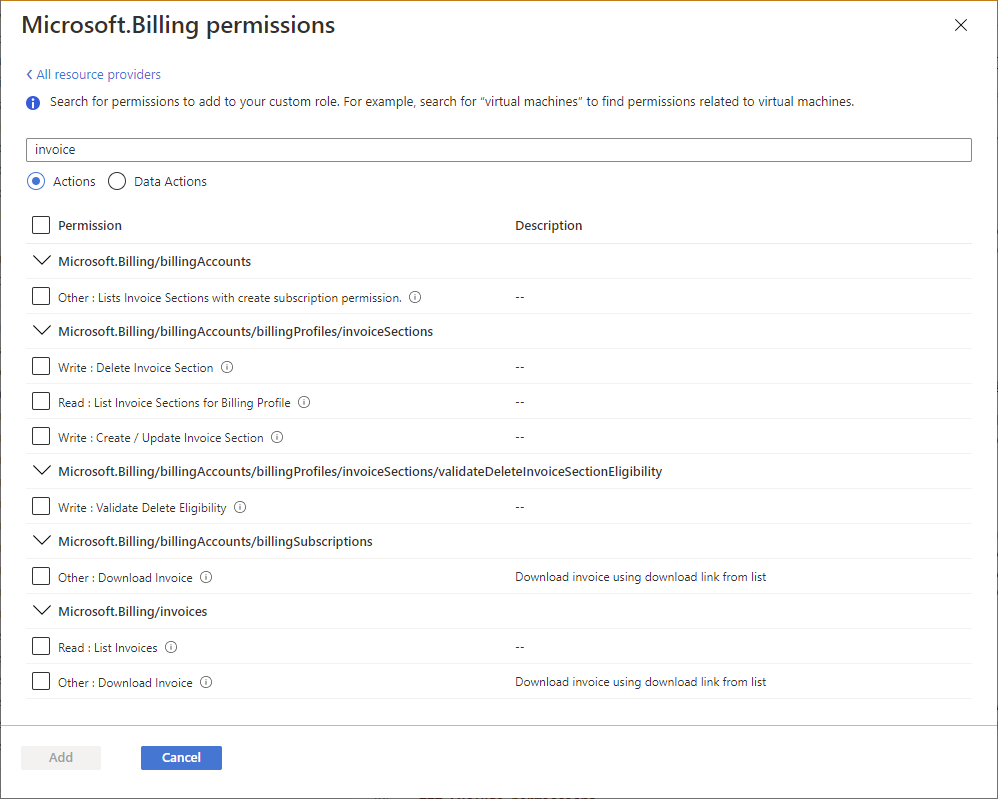
搜索可用权限,找到要包括的权限。
使用 Azure 门户创建自定义角色时,可以按关键字搜索权限。 例如,您可以搜索“虚拟机”或“计费”权限。 你还可以将所有权限下载为 CSV 文件,然后搜索此文件。 使用 Azure 门户创建或更新 Azure 自定义角色中介绍了此搜索功能。
自定义角色示例
下面展示了使用 Azure PowerShell 以 JSON 格式显示的自定义角色。 自定义角色可以用于监视和重新启动虚拟机。
{
"Name": "Virtual Machine Operator",
"Id": "88888888-8888-8888-8888-888888888888",
"IsCustom": true,
"Description": "Can monitor and restart virtual machines.",
"Actions": [
"Microsoft.Storage/*/read",
"Microsoft.Network/*/read",
"Microsoft.Compute/*/read",
"Microsoft.Compute/virtualMachines/start/action",
"Microsoft.Compute/virtualMachines/restart/action",
"Microsoft.Authorization/*/read",
"Microsoft.ResourceHealth/availabilityStatuses/read",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Insights/alertRules/*",
"Microsoft.Insights/diagnosticSettings/*"
],
"NotActions": [],
"DataActions": [],
"NotDataActions": [],
"AssignableScopes": [
"/subscriptions/{subscriptionId1}",
"/subscriptions/{subscriptionId2}",
"/providers/Microsoft.Management/managementGroups/{groupId1}"
]
}
下面展示了使用 Azure CLI 显示的相同自定义角色。
[
{
"assignableScopes": [
"/subscriptions/{subscriptionId1}",
"/subscriptions/{subscriptionId2}",
"/providers/Microsoft.Management/managementGroups/{groupId1}"
],
"description": "Can monitor and restart virtual machines.",
"id": "/subscriptions/{subscriptionId1}/providers/Microsoft.Authorization/roleDefinitions/88888888-8888-8888-8888-888888888888",
"name": "88888888-8888-8888-8888-888888888888",
"permissions": [
{
"actions": [
"Microsoft.Storage/*/read",
"Microsoft.Network/*/read",
"Microsoft.Compute/*/read",
"Microsoft.Compute/virtualMachines/start/action",
"Microsoft.Compute/virtualMachines/restart/action",
"Microsoft.Authorization/*/read",
"Microsoft.ResourceHealth/availabilityStatuses/read",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Insights/alertRules/*",
"Microsoft.Insights/diagnosticSettings/*"
],
"dataActions": [],
"notActions": [],
"notDataActions": []
}
],
"roleName": "Virtual Machine Operator",
"roleType": "CustomRole",
"type": "Microsoft.Authorization/roleDefinitions"
}
]
自定义角色属性
下表说明了自定义角色属性的含义。
| 属性 | 必须 | 类型 | 说明 |
|---|---|---|---|
NameroleName |
是 | 字符串 | 自定义角色的显示名称。 虽然角色定义是管理组或订阅级资源,但角色定义可以在共享同一 Microsoft Entra 租户的多个订阅中使用。 此显示名称在 Microsoft Entra 租户范围内必须是唯一的。 可以包含字母、数字、空格和特殊字符。 建议的最大值:256 个字符。 |
Idname |
是 | 字符串 | 自定义角色的唯一 ID。 如果使用 Azure PowerShell 和 Azure CLI,在创建新角色时会自动生成此 ID。 |
IsCustomroleType |
是 | 字符串 | 指示此角色是否为自定义角色。 对于自定义角色,设置为 true 或 CustomRole。 对于内置角色,设置为 false 或 BuiltInRole。 |
Descriptiondescription |
是 | 字符串 | 自定义角色的说明。 可以包含字母、数字、空格和特殊字符。 建议的最大值:512 个字符。 |
Actionsactions |
是 | String[] | 一个字符串数组,指定该角色允许执行的控制平面操作。 有关详细信息,请参阅 Actions。 |
NotActionsnotActions |
否 | String[] | 一个字符串数组,指定从允许的 Actions 中排除的控制平面操作。 有关详细信息,请参阅 NotActions。 |
DataActionsdataActions |
否 | String[] | 一个字符串数组,指定该角色允许对该对象中的数据进行的“数据平面”操作。 如果使用 DataActions 创建自定义角色,则无法在管理组范围内分配该角色。 有关详细信息,请参阅 DataActions。 |
NotDataActionsnotDataActions |
否 | String[] | 一个字符串数组,指定已从允许的 DataActions 中排除的数据平面操作。 有关详细信息,请参阅 NotDataActions。 |
AssignableScopesassignableScopes |
是 | String[] | 一个字符串数组,指定自定义角色的可分配范围。 最大 AssignableScopes 数为 2,000 个。 有关详细信息,请参阅 AssignableScopes。 |
权限字符串不区分大小写。 创建自定义角色时,约定是匹配可以在其中找到 Azure 资源提供程序操作中所述权限的大小写。
通配符权限
Actions、NotActions、DataActions 和 NotDataActions 支持使用通配符 (*) 来定义权限。 通配符 (*) 将权限扩展到与所提供的操作字符串匹配的所有内容。 例如,假设你想要添加与Microsoft成本管理和导出相关的所有权限。 可以添加所有这些操作字符串:
Microsoft.CostManagement/exports/action
Microsoft.CostManagement/exports/read
Microsoft.CostManagement/exports/write
Microsoft.CostManagement/exports/delete
Microsoft.CostManagement/exports/run/action
也可以不添加所有这些字符串,而只需添加一个通配符字符串。 例如,以下通配符字符串等效于上面的五个字符串。 此处还包括任何将来可能会添加的导出权限。
Microsoft.CostManagement/exports/*
注意
建议显式指定 Actions 和 DataActions,而不要使用通配符 (*) 字符。 通过将来的 Actions 或 DataActions 授予的额外访问权限,可能是使用通配符时不希望出现的行为。
谁可以创建、删除、更新或查看自定义角色
与在内置角色中一样,AssignableScopes 属性指定角色的可配置范围。 自定义角色的 AssignableScopes 属性还控制谁可以创建、删除、更新或查看自定义角色。
| 任务 | 动作 | 说明 |
|---|---|---|
| 创建/删除自定义角色 | Microsoft.Authorization/ roleDefinitions/write |
在自定义角色的所有 AssignableScopes 上被允许此操作的用户可以创建(或删除)用于这些范围的自定义角色。 例如,管理组、订阅和资源组的所有者和用户访问管理员。 |
| 更新自定义角色 | Microsoft.Authorization/ roleDefinitions/write |
被授权在自定义角色的所有 AssignableScopes 上执行此操作的用户可以更新这些范围中的自定义角色。 例如,管理组、订阅和资源组的所有者和用户访问管理员。 |
| 查看自定义角色 | Microsoft.Authorization/ roleDefinitions/read |
在某个范围内被允许此操作的用户可以查看可在该范围内分配的自定义角色。 所有内置角色都允许自定义角色可用于分配。 |
注意
即使重命名了角色,角色 ID 也不会更改。 如果使用脚本或自动化来创建角色分配,最佳做法是使用唯一的角色 ID 而非角色名称。 因此,如果角色被重命名,脚本更有可能正常工作。
查找角色分配以删除自定义角色
在删除自定义角色之前,必须删除使用自定义角色的任何角色分配。 如果尝试删除具有角色分配的自定义角色,将收到消息:There are existing role assignments referencing role (code: RoleDefinitionHasAssignments)。
下面是在删除自定义角色之前帮助查找角色分配的步骤:
- 列出自定义角色定义。
- 在 AssignableScopes 部分,获取管理组、订阅和资源组。
- 遍历
AssignableScopes并将列出角色分配。 - 删除使用自定义角色的角色分配。
- 如果是使用 Microsoft Entra Privileged Identity Management,请删除符合条件的自定义角色分配。
- 删除自定义角色。
有关如何查找未使用的自定义角色的信息,请参阅症状 - 无法创建更多角色定义。
自定义角色限制
以下列表描述了对自定义角色的限制。
- 每个租户最多可以有 5000 个自定义角色。
- 由世纪互联运营的 Microsoft Azure 的每个租户最多可以有 2000 个自定义角色。
- 不能将
AssignableScopes设置为根范围 ("/")。 - 不能在
*中使用通配符 (AssignableScopes)。 此通配符限制有助于确保用户不可能通过更新角色定义来获取对某个范围的访问权限。 - 操作字符串中只能有一个通配符。
- 只能在自定义角色的
AssignableScopes中定义一个管理组。 - Azure 资源管理器不验证管理组是否存在于角色定义的
AssignableScopes中。 - 无法在管理组范围内分配具有
DataActions的自定义角色。 - 可以在
DataActions中使用AssignableScopes和一个管理组创建自定义角色。 无法在管理组范围本身分配自定义角色;但是,可以在管理组内的订阅范围内分配自定义角色。 如果需要创建需要在多个订阅中分配DataActions的单个自定义角色,而不是为每个订阅创建单独的自定义角色,这非常有用。
有关自定义角色和管理组的详细信息,请参阅 什么是 Azure 管理组?
输入和输出格式
要使用命令行创建自定义角色,通常使用 JSON 来指定自定义角色的属性。 根据所使用的工具,输入和输出格式看起来会稍有不同。 本部分列出了不同工具的输入和输出格式。
Azure PowerShell
要使用 Azure PowerShell 创建自定义角色,必须提供以下输入。
{
"Name": "",
"Description": "",
"Actions": [],
"NotActions": [],
"DataActions": [],
"NotDataActions": [],
"AssignableScopes": []
}
要使用 Azure PowerShell 更新自定义角色,必须提供以下输入。 请注意,已添加 Id 属性。
{
"Name": "",
"Id": "",
"Description": "",
"Actions": [],
"NotActions": [],
"DataActions": [],
"NotDataActions": [],
"AssignableScopes": []
}
下面显示了使用 Azure PowerShell 和 ConvertTo-Json 命令列出自定义角色时的输出示例。
{
"Name": "",
"Id": "",
"IsCustom": true,
"Description": "",
"Actions": [],
"NotActions": [],
"DataActions": [],
"NotDataActions": [],
"AssignableScopes": []
}
Azure CLI
要使用 Azure CLI 创建或更新自定义角色,必须提供以下输入。 此格式与使用 Azure PowerShell 创建自定义角色时生成的格式相同。
{
"Name": "",
"Description": "",
"Actions": [],
"NotActions": [],
"DataActions": [],
"NotDataActions": [],
"AssignableScopes": []
}
下面显示了使用 Azure CLI 列出自定义角色时的输出示例。
[
{
"assignableScopes": [],
"description": "",
"id": "",
"name": "",
"permissions": [
{
"actions": [],
"dataActions": [],
"notActions": [],
"notDataActions": []
}
],
"roleName": "",
"roleType": "CustomRole",
"type": "Microsoft.Authorization/roleDefinitions"
}
]
REST API
要使用 REST API 创建或更新自定义角色,必须提供以下输入。 此格式与使用 Azure 门户创建自定义角色时生成的格式相同。
{
"properties": {
"roleName": "",
"description": "",
"assignableScopes": [],
"permissions": [
{
"actions": [],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}
下面显示了使用 REST API 列出自定义角色时的输出示例。
{
"properties": {
"roleName": "",
"type": "CustomRole",
"description": "",
"assignableScopes": [],
"permissions": [
{
"actions": [],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
],
"createdOn": "",
"updatedOn": "",
"createdBy": "",
"updatedBy": ""
},
"id": "",
"type": "Microsoft.Authorization/roleDefinitions",
"name": ""
}