适用于:Azure SQL 数据库
Azure Synapse Analytics(仅限专用 SQL 池)
从快速入门:创建单一数据库 - Azure SQL 数据库和 Azure Synapse Analytics中创建逻辑服务器时,结果是采用特定格式的公共终结点:yourservername.database.chinacloudapi.cn。
默认情况下,逻辑服务器拒绝所有连接以确保安全性。 可以使用以下一个或多个网络访问控制来选择性地允许通过公共终结点访问数据库
IP 防火墙规则:使用此功能可以显式允许从特定的 IP 地址建立连接。 例如,可以通过从本地计算机或指定起始和结束 IP 地址来定义 IP 地址范围。
允许 Azure 服务和资源访问此服务器:启用此选项后,Azure 边界范围内的其他资源可以访问 SQL 数据库。 例如,Azure 虚拟机可以访问SQL 数据库资源。
虚拟网络防火墙规则:使用此功能可以允许来自 Azure 边界内特定虚拟网络的流量。
专用链接:使用此功能可为特定虚拟网络内的 Azure 中的逻辑服务器创建专用终结点。
重要
本文不适用于“SQL 托管实例”。 有关网络配置的详细信息,请参阅连接到 Azure SQL 托管实例。
IP 防火墙规则
基于 IP 的防火墙规则是 Azure 中逻辑服务器的一项功能,可在显式添加客户端计算机的 IP 地址 之前阻止对服务器的所有访问。
有两种类型的防火墙规则:
- 服务器级防火墙规则适用于服务器上的所有数据库。 可以通过 Azure 门户、PowerShell 或 T-SQL 命令(如 sp_set_firewall_rule)配置它们。
- 数据库级防火墙规则:这些规则适用于单个数据库,只能使用 T-SQL 命令(如 sp_set_database_firewall_rule)进行配置
以下是命名防火墙规则的约束:
- 防火墙规则名称不能为空。
- 它不能包含下列字符:
<, >, *, %, &, :, \\, /, ?. - 它不能以句点 (.) 结尾。
- 防火墙规则名称不能超过 128 个字符。
创建不符合这些约束的防火墙规则的任何尝试都失败,并显示错误消息。 对现有基于 IP 的防火墙规则所做的任何修改最多可能需要 5 分钟才能生效。
允许 Azure 服务
默认情况下,在从 Azure 门户创建新的逻辑服务器期间,“允许 Azure 服务和资源访问此服务器”未选中且未启用。 允许使用公共终结点建立连接时,将显示此设置。
创建逻辑服务器后,也可以按如下所示通过“网络”设置更改此设置:
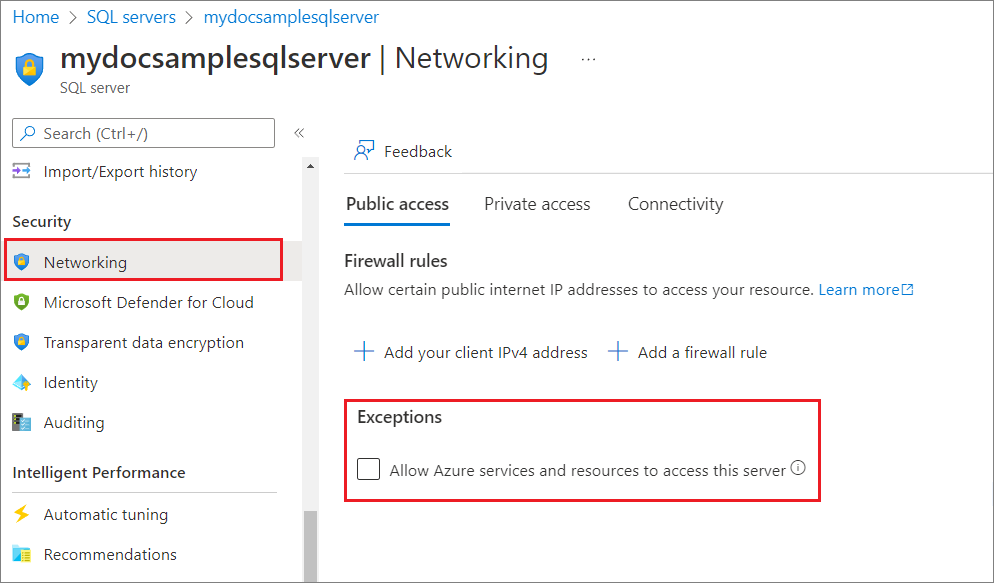
启用“允许 Azure 服务和资源访问此服务器”时,服务器会允许来自 Azure 边界内所有资源的通信,而无论这是否是订阅的一部分。 在后台,添加了一个特殊的服务器级防火墙规则,该规则以 IP 地址 0.0.0.0 开头和结尾。
在许多情况下,启用该设置的访问权限宽松度会超过大多数客户的需要。 可能需要取消选中此设置,并将其替换为限制性严格的 IP 防火墙规则,或者使用一种专用访问选项。
重要
如果选中“允许 Azure 服务和资源访问此服务器”,则会添加一个基于 IP 的防火墙规则,其起始和结束 IP 地址为 0.0.0.0
但是,这样做会影响在 Azure 中的虚拟机上运行的以下功能,这些虚拟机未包含在你的虚拟网络中,因此会通过 Azure IP 地址连接到数据库:
导入/导出服务
未启用“允许 Azure 服务和资源访问此服务器”时,导入导出服务不起作用。 不过,可通过以下方式解决此问题:在 Azure VM 中手动运行 SqlPackage,或者直接在代码中使用 DACFx API 执行导出。
数据同步
若要在未启用“允许 Azure 服务和资源访问此服务器”的情况下使用数据同步功能,需要创建单个防火墙规则条目,以便为托管中心数据库的区域,从 SQL 服务标记添加 IP 地址。 将这些服务器级防火墙规则添加到托管“中心”和“成员”数据库的服务器(可能位于不同的区域)。
使用以下 PowerShell 脚本生成与中国东部 2 区域的 SQL 服务标记对应的 IP 地址。
PS C:\> $serviceTags = Get-AzNetworkServiceTag -Location chinaeast2
PS C:\> $sql = $serviceTags.Values | Where-Object { $_.Name -eq "Sql.ChinaEast2" }
PS C:\> $sql.Properties.AddressPrefixes.Count
3
PS C:\> $sql.Properties.AddressPrefixes
40.73.82.0/23
40.73.169.0/26
40.73.170.0/26
提示
即使指定 Location 参数,Get-AzNetworkServiceTag 也会返回 SQL 服务标记的全局范围。 请务必将范围筛选为托管同步组所用中心数据库的区域
PowerShell 脚本的输出采用无类域间路由 (CIDR) 表示法。 需要使用 Get-IPrangeStartEnd.ps1 将其转换为开始和结束IP地址的格式,如下所示:
PS C:\> Get-IPrangeStartEnd -ip 52.229.17.93 -cidr 26
start end
----- ---
52.229.17.64 52.229.17.127
可以使用以下 PowerShell 脚本将所有 IP 地址从 CIDR 转换为开始和结束 IP 地址格式。
PS C:\>foreach( $i in $sql.Properties.AddressPrefixes) {$ip,$cidr= $i.split('/') ; Get-IPrangeStartEnd -ip $ip -cidr $cidr;}
start end
----- ---
13.86.216.0 13.86.216.127
13.86.216.128 13.86.216.191
13.86.216.192 13.86.216.223
现在可以将这些规则添加为不同的防火墙规则,然后禁用“允许 Azure 服务和资源访问此服务器”设置。
SQL 服务标记
可以在安全规则以及从客户端到SQL 数据库的路由使用服务标记。 只需在安全规则的源或目的地字段中指定服务标记,即可在网络安全组、Azure 防火墙和用户定义的路由中使用它们。 Sql 服务标记由 SQL 数据库使用的所有 IP 地址组成。 该标记按区域进一步分段。 例如,Sql.ChinaEast 列出了中国东部 SQL 数据库使用的所有 IP 地址。
Sql 服务标记由与 SQL 数据库建立连接所需的 IP 地址组成,详见网关 IP 地址。 此外,服务标记还将与以下功能中使用的任何 SQL 数据库出站流量相关联:
- Azure SQL 数据库和 Azure Synapse Analytics 的审核
- 漏洞评估
- 导入或导出 Azure SQL 数据库,而无需允许 Azure 服务访问服务器
- OPENROWSET
- 批量插入
- sp_invoke_external_rest_endpoint
- Ledger
- PowerShell 和 Azure CLI:使用 Azure 密钥保管库中客户管理的密钥实现透明数据加密
SqlManagement 服务标记
SqlManagement 服务标记用于针对 SQL 数据库的控制平面操作。
虚拟网络防火墙规则
使用 Azure SQL 数据库中服务器的虚拟网络服务终结点和规则 可以更轻松地从包含 VM 的特定子网建立和管理访问权限。
专用链接
专用链接允许您通过“专用终结点”连接到服务器。 专用终结点是特定虚拟网络和子网中的专用 IP 地址。