本文介绍如何在 Azure 虚拟网络内的多个不同应用程序方案中将应用程序连接到 Azure SQL 托管实例。
在确定如何以及在何处托管应用程序时,目前有多个选项可供选择。 可以选择使用 Azure 应用服务或某些 Azure 虚拟网络集成选项在云中托管应用程序。 例如,Azure 应用服务环境、Azure 虚拟机和虚拟机规模集。 还可以采用混合云方法,将应用程序保留在本地。 无论做出何种选择,应用程序都可以在 Azure 虚拟网络内或之间在许多不同的应用程序方案中连接到 Azure SQL 托管实例。
还可以从虚拟网络外部启用对 SQL 托管实例的数据访问 -例如,从 Power BI 和 Azure 应用服务等多租户 Azure 服务,或者从未通过 VPN 连接到虚拟网络的本地网络进行访问。 若要完成这些和类似的方案,请参阅在 Azure SQL 托管实例中配置公共终结点。
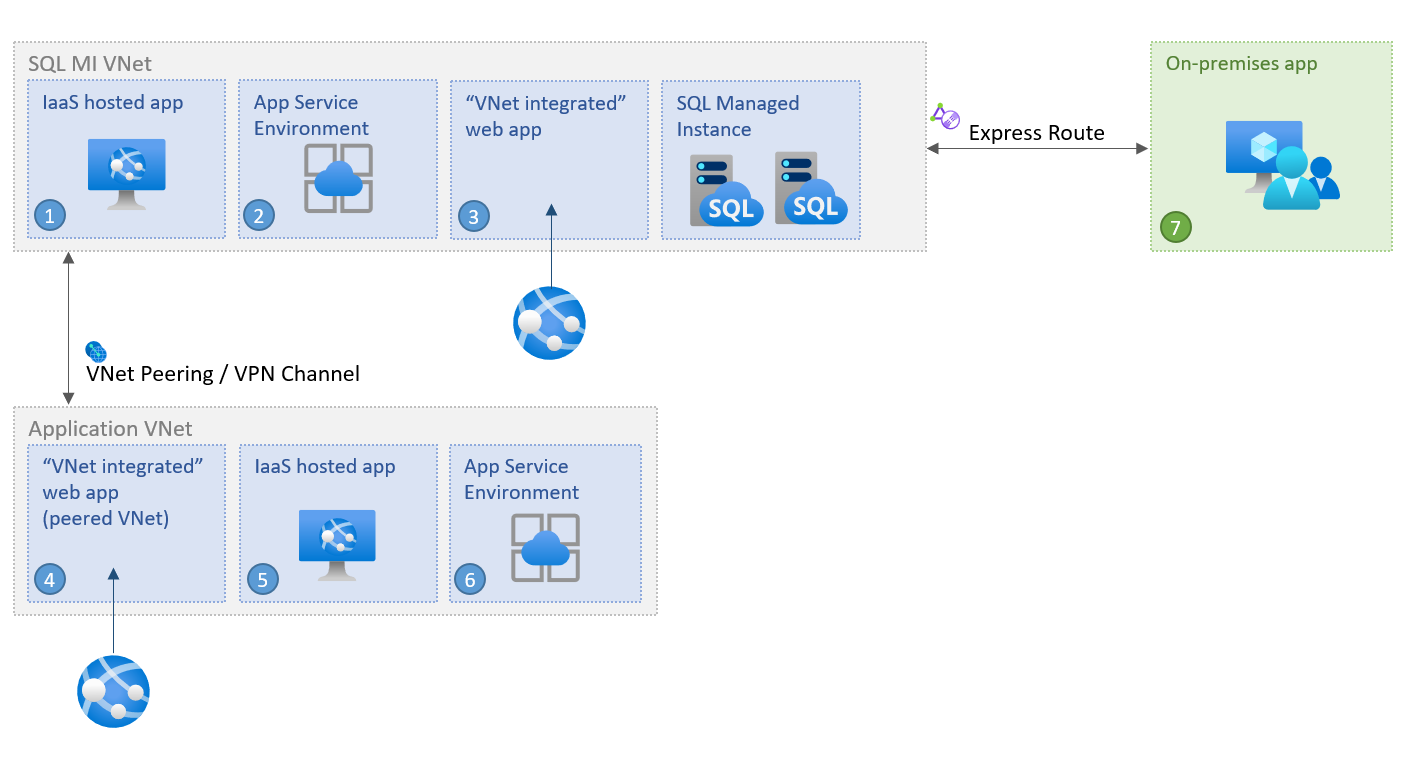
从同一虚拟网络内部进行连接
最简单的方案是将应用程序连接到 Azure SQL 托管实例所在的虚拟网络中。 虚拟网络中的虚拟机即使位于不同子网,也能直接相互连接。 这表示只需配置指向 VNet 本地终结点的连接字符串,就能连接应用服务环境内的应用程序或者与 SQL 托管实例部署在同一虚拟网络中的虚拟机。
从其他虚拟网络内部进行连接
如果应用程序驻留在与 SQL 托管实例不同的虚拟网络中,则连接该应用程序需要首先获得对部署 SQL 托管实例的虚拟网络的访问权限,或者对 SQL 托管实例自身的访问权限。 两个虚拟网络不需要位于同一订阅中。
可通过三个选项连接到不同虚拟网络中的 SQL 托管实例:
- 专用终结点
- Azure 虚拟网络对等互连
- VNet 到 VNet VPN 网关(Azure 门户、PowerShell、Azure CLI)
在这三个选项中,专用终结点是最安全、最节省资源的选项,因为它们:
- 仅从其虚拟网络公开 SQL 托管实例。
- 仅允许单向连接。
- 只需在应用程序的虚拟网络中提供一个 IP 地址。
如果专用终结点无法完全满足方案的要求,请考虑改为虚拟网络对等互连。 对等互连使用主干 Azure 网络,因此跨虚拟网络边界的通信不会受到明显的延迟损失。 在所有区域(全局虚拟网络对等互连)的网络之间支持虚拟网络对等互连。 但是, 托管在 2020 年 9 月 22 日之前创建的子网中的实例 仅支持其区域内的对等互连。
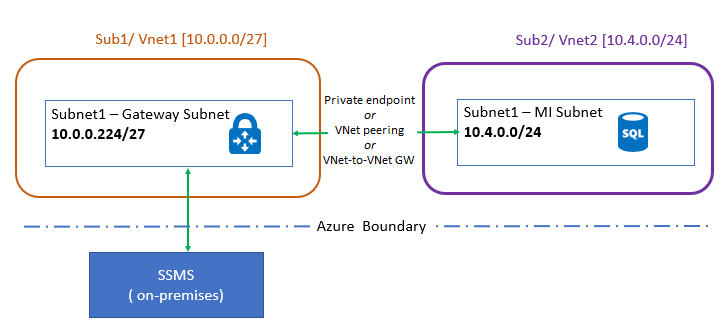
从本地连接
可以将本地应用程序连接到 SQL 托管实例的 VNet 本地终结点。 若要从本地访问它,需在应用程序与 SQL 托管实例虚拟网络之间建立站点到站点连接。 如果仅数据访问 SQL 托管实例已足够,则可以通过公共终结点从虚拟网络外部连接到该实例 - 查看 在 Azure SQL 托管实例中配置公共终结点 以了解详细信息。
可使用两个选项将本地应用程序连接到 Azure 虚拟网络:
- 站点到站点 VPN 连接(Azure 门户、PowerShell、Azure CLI)
- Azure ExpressRoute 连接
如果可以建立从本地到 Azure 的连接,但无法与 SQL 托管实例建立连接,请检查从客户端到 SQL 托管实例的网络路径是否符合所选 连接类型的连接要求。
连接开发人员工具箱
还可将开发人员工具箱连接到 SQL 托管实例。 若要通过虚拟网络从开发人员工具箱访问该实例,首先需要在开发人员工具箱与 SQL 托管实例虚拟网络之间建立连接。 为此,请使用本机 Azure 证书身份验证配置与虚拟网络的点到站点连接。 有关详细信息,请参阅配置点到站点连接,以便从本地计算机连接到 Azure SQL 托管实例。
有关从虚拟网络外部访问 SQL 托管实例的数据,请参阅 在 Azure SQL 托管实例中配置公共终结点。
连接到辐射型网络
另一种常见情况是,VPN 网关安装在单独的虚拟网络(也许订阅)( 辐射网络 )中,该网关安装在托管 SQL 托管实例(中心网络)的虚拟网络中。 从辐射网络连接到 SQL 托管实例是通过 连接从其他虚拟网络内部列出的选项之一配置的:专用终结点、Azure 虚拟网络对等互连或 VNet 到 VNet 网关。
以下示例体系结构图显示了虚拟网络对等互连:
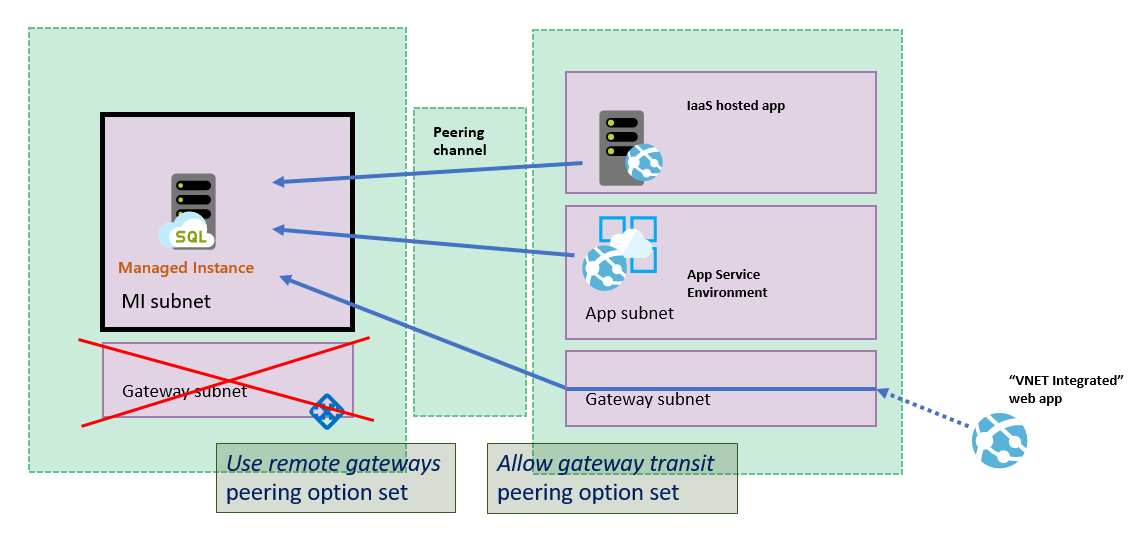
如果要对等互连中心网络和分支网络,请确保 VPN 网关能够从中心网络看到 IP 地址。 为此,请在“对等互连设置”下进行以下更改:
- 在托管 VPN 网关的虚拟网络(分支网络)中,转到“对等互连”,然后转到 SQL 托管实例的对等虚拟网络连接,再选择“允许网关传输”。
- 在托管 SQL 托管实例的虚拟网络(中心网络)中,转到“对等互连”,然后转到 VPN 网关的对等虚拟网络连接,再选择“使用远程网关”。
连接 Azure 应用服务
当应用程序与虚拟网络集成时,还可以连接由 Azure 应用服务托管的应用程序。 为此,请 从其他虚拟网络内选择 Connect 中列出的机制之一。 有关从虚拟网络外部访问 SQL 托管实例的数据,请参阅 在 Azure SQL 托管实例中配置公共终结点。
在将 Azure 应用服务连接到 SQL 托管实例时,有一种特殊情况是将 Azure 应用服务集成到已与 SQL 托管实例虚拟网络建立对等互连的网络。 对于这种情况,需要设置以下配置:
- SQL 托管实例 虚拟网络不得具有 网关
- SQL 托管实例虚拟网络必须设置
Use remote gateways选项 - 对等的虚拟网络必须设置
Allow gateway transit选项
下图演示了此方案:
注意
虚拟网络集成功能不会将应用与具有 ExpressRoute 网关的虚拟网络集成。 即使 ExpressRoute 网关在共存模式下配置,虚拟网络集成也不起作用。 如果需要通过 ExpressRoute 连接访问资源,可使用虚拟网络中运行的应用服务环境。
要对通过虚拟网络的 Azure 应用服务访问进行故障排除,请参阅对虚拟网络和应用程序进行故障排除。
解决连接问题
若要排查连接问题,请查看以下设置:
如果无法从同一虚拟网络中的 Azure 虚拟机连接到 SQL 托管实例,但子网不同,请检查是否在可能阻止访问的 VM 子网上设置了网络安全组(NSG)。 此外,允许 SQL 端口 1433 上的出站流量,因为需要在 Azure 边界内通过重定向进行连接。 有关详细信息,请查看 Azure SQL 托管实例连接类型中的要求。
对于与虚拟网络关联的路由表,请确保将“网关路由传播”设置为“禁用”。
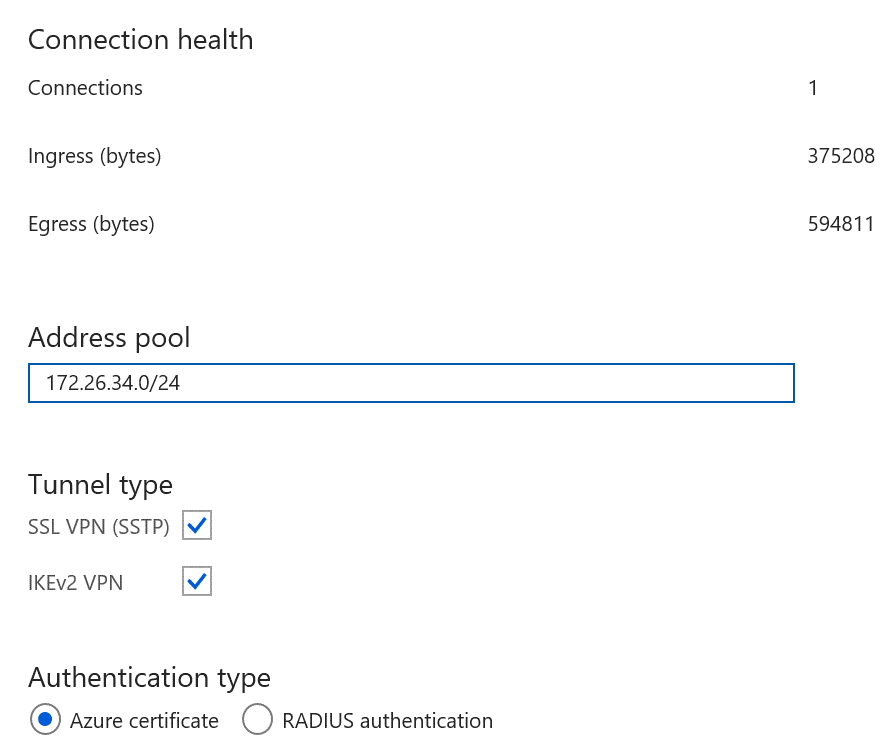
如果使用点到站点 VPN,请在 Azure 门户中检查配置,确定能否看到“入口/出口”编号。 如果编号不为零,则表示 Azure 在本地进行流量的出入路由。
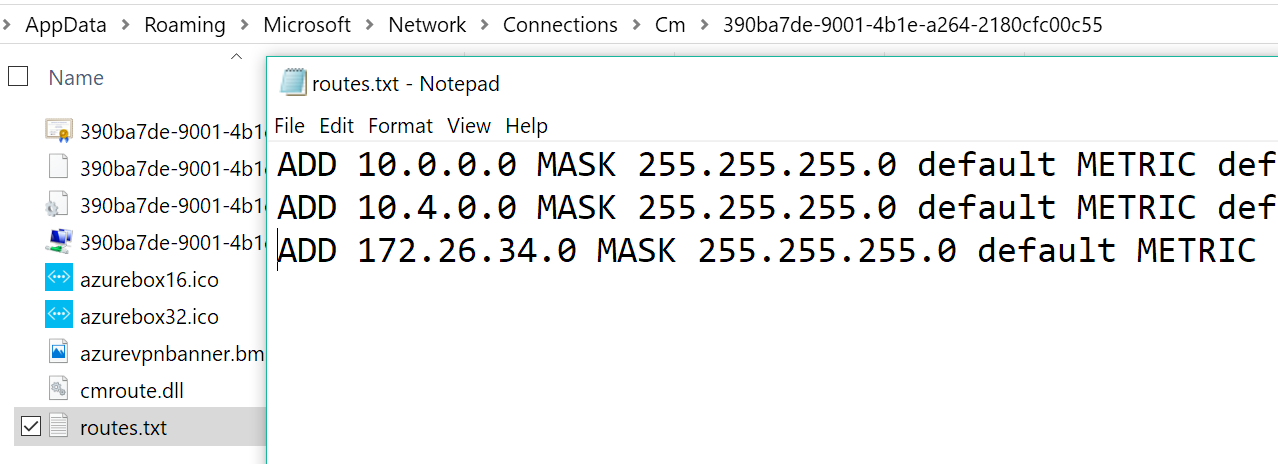
查看客户端计算机(运行 VPN 客户端的计算机)是否针对你需要访问的所有虚拟网络设置了路由条目。 路由存储在
%AppData%\Roaming\Microsoft\Network\Connections\Cm\<GUID>\routes.txt中。如此图所示,有两个条目用于所涉及的每个虚拟网络,还有第三个条目与门户中配置的 VPN 终结点相对应。
检查路由的另一种方式是执行以下命令。 输出显示到各种子网的路由:
C:\ >route print -4 =========================================================================== Interface List 14...54 ee 75 67 6b 39 ......Intel(R) Ethernet Connection (3) I218-LM 57...........................rndatavnet 18...94 65 9c 7d e5 ce ......Intel(R) Dual Band Wireless-AC 7265 1...........................Software Loopback Interface 1 Adapter=========================================================================== IPv4 Route Table =========================================================================== Active Routes: Network Destination Netmask Gateway Interface Metric 0.0.0.0 0.0.0.0 10.83.72.1 10.83.74.112 35 10.0.0.0 255.255.255.0 On-link 172.26.34.2 43 10.4.0.0 255.255.255.0 On-link 172.26.34.2 43 =========================================================================== Persistent Routes: None如果使用虚拟网络对等互连,请确保按照设置 “允许网关传输和使用远程网关”的说明进行作。
如果使用虚拟网络对等互连连接 Azure 应用服务托管应用程序,而且 SQL 托管实例虚拟网络具有公共 IP 地址范围,请确保你的托管应用程序设置允许出站流量路由到公共 IP 网络。 按照区域虚拟网络集成中的说明进行操作。
建议的驱动程序和工具版本
尽管较旧版本可能可用,但下表列出了连接到 SQL 托管实例的建议的最低版本的工具和驱动程序:
| 驱动程序/工具 | 版本 |
|---|---|
| .NET Framework | 4.6.1(或 .NET Core) |
| ODBC 驱动程序 | v17 |
| PHP 驱动程序 | 5.2.0 |
| JDBC 驱动程序 | 6.4.0 |
| Node.js 驱动程序 | 2.1.1 |
| OLEDB 驱动程序 | 18.0.2.0 |
| SSMS | 18.0 或更高版本 |
| SMO | 150 或更高版本 |
注意
早期版本的 JDBC 4.0 和 4.1 驱动程序(分别随 Java SE 6 和 Java SE 7 一起提供)可以显示为支持 TDS 7.4 的服务器,即使它们未完全实现 TDS 7.4。 这些驱动程序无法连接到 SQL 托管实例,其 连接类型 设置为重定向。 将驱动程序升级到 JDBC 4.2 或更高版本,或将实例的连接类型切换到代理。