适用于:Azure SQL 数据库
Azure Synapse Analytics
虚拟网络规则是一项防火墙安全功能,用于控制 Azure SQL 数据库中数据库和弹性池的服务器或 Azure Synapse Analytics 中专用 SQL 池(之前称为 SQL DW)数据库的服务器是否接受从虚拟网络中的特定子网发出的通信。 本文说明了为何有时候最好选择虚拟网络规则来安全地启用与 Azure SQL 数据库和 Azure Synapse Analytics 中数据库的通信。
注意
本文同时适用于 Azure SQL 数据库和 Azure Synapse Analytics。 为简单起见,术语“数据库”是指 Azure SQL 数据库中的数据库和 Azure Synapse Analytic 中的数据库。 同样,对服务器的任何引用都是指托管 SQL 数据库和 Azure Synapse Analytics 的逻辑服务器。
若要创建虚拟网络规则,首先必须具有可供规则引用的虚拟网络服务终结点。
注意
Microsoft Entra ID 以前称为 Azure Active Directory (Azure AD)。
创建虚拟网络规则
如果只想创建虚拟网络规则,则可跳到本文后面的步骤和说明。
虚拟网络规则详细信息
此部分介绍虚拟网络规则的多项详细信息。
只有一个地理区域
一个虚拟网络服务终结点只适用于一个 Azure 区域。 终结点不允许其他区域接受来自子网的通信。
任何虚拟网络规则都只能应用于基础终结点应用到的区域。
服务器级而非数据库级
每个虚拟网络规则都适用于整个服务器,而不仅仅是该服务器上某个特定的数据库。 换句话说,虚拟网络规则在服务器级而非数据库级应用。
与之不同的是,IP 规则适用于这其中的任一级别。
安全管理角色
在管理虚拟网络服务终结点时,安全角色是分开的。 下述每个角色都需要采取行动:
- 网络管理员(网络参与者角色):启用终结点。
- 数据库管理员(SQL Server 参与者角色):更新访问控制列表 (ACL),将给定的子网添加到服务器。
Azure RBAC 替代方案
网络管理员和数据库管理员角色的权限超出虚拟网络规则的管理需要, 只有部分权限是必需的。
可以选择在 Azure 中使用基于角色的访问控制 (RBAC),创建一个只有部分必需权限的自定义角色。 在涉及到网络管理员或数据库管理员时,可以使用自定义角色来代替。与向两个主要的管理员角色添加用户相比,向自定义角色添加用户的安全风险较低。
注意
在某些情况下,Azure SQL 数据库中的数据库和虚拟网络子网位于不同的订阅中。 在这些情况下,必须确保以下配置:
- 用户具有启动多项操作(例如启用服务终结点和向给定服务器添加虚拟网络子网)所需的权限。
- 两个订阅都必须注册 Microsoft.Sql 提供程序。
限制
对于 SQL 数据库,虚拟网络规则功能具有以下限制:
- 在 Azure SQL 数据库中数据库的防火墙中,每个虚拟网络规则都引用一个子网。 引用的所有这些子网都必须托管在同一个托管数据库的地理区域内。
- 对于任何虚拟网络,每个服务器最多可以有 128 个 ACL 条目。
- 虚拟网络规则仅适用于 Azure 资源管理器虚拟网络,不适用于经典部署模型网络。
- 在防火墙上,IP 地址范围适用于以下网络项,但虚拟网络规则并不适用:
- 站点到站点虚拟专用网络(S2S VPN)
- 在本地通过 Azure ExpressRoute 进行部署
- 两个订阅必须位于同一个 Microsoft Entra 租户中。
使用服务终结点时的注意事项
在使用 Azure SQL 数据库的服务终结点时,请查看以下注意事项:
- 需要到 Azure SQL 数据库公共 IP 的出站连接。 必须为 Azure SQL 数据库 IP 启用网络安全组 (NSG) 才能进行连接。 为此,可以将 NSG 服务标记用于 SQL 数据库。
ExpressRoute
如果您在本地使用 ExpressRoute 进行公共对等互连或 Microsoft 对等互连,则需要标识所用的 NAT IP 地址。 进行公共对等互连时,每条 ExpressRoute 线路默认情况下会使用两个 NAT IP 地址。当流量进入 Azure 网络主干时,会向 Azure 服务流量应用这些地址。 在进行 Microsoft 对等互连时,所用 NAT IP 地址由客户或服务提供商提供。 若要允许访问服务资源,必须在资源 IP 防火墙设置中允许这些公共 IP 地址。 若要查找公共对等互连 ExpressRoute 线路 IP 地址,请通过 Azure 门户开具 ExpressRoute 支持票证。 若要详细了解适用于 ExpressRoute 公共对等互连和 Microsoft 对等互连的 NAT,请参阅 Azure 公共对等互连的 NAT 要求。
若要允许从线路到 Azure SQL 数据库的通信,必须为 NAT 的公共 IP 地址创建 IP 网络规则。
将虚拟网络服务终结点与 Azure 存储配合使用的影响
Azure 存储已实现相同的功能,允许限制到 Azure 存储帐户的连接。 如果选择将此功能与某个 Azure 存储帐户配合使用,而该帐户正由 Azure SQL 数据库使用,则可能会出现问题。 接下来会列出受此影响的 Azure SQL 数据库和 Azure Synapse Analytics 功能并对其进行讨论。
Azure Synapse Analytics PolyBase 和 COPY 语句
PolyBase 和 COPY 语句通常用于将数据从 Azure 存储帐户加载到 Azure Synapse Analytics 中,以实现高吞吐量数据引入。 如果你要从中加载数据的 Azure 存储帐户将访问权限限定于一组虚拟网络子网,则使用 PolyBase 和 COPY 语句时,与存储帐户的连接会断开。 对于与 Azure 存储(已通过安全方式连接到虚拟网络)连接的 Azure Synapse Analytics,若要通过 COPY 和 PolyBase 来启用导入和导出方案,请执行本部分的步骤。
先决条件
- 安装 Azure PowerShell。 有关详细信息,请查看安装 Azure Az PowerShell 模块。
- 如果你有常规用途 v1 或 Azure Blob 存储帐户,则必须先按照升级到常规用途 v2 存储帐户中的步骤升级到常规用途 v2。
- 必须在 Azure 存储帐户的“防火墙和虚拟网络”设置菜单下 启用“允许受信任的 Microsoft 服务访问此存储帐户”。 启用此配置将允许 PolyBase 和 COPY 语句使用强身份验证连接到存储帐户,而网络流量仍保留在 Azure 主干上。 有关详细信息,请参阅此指南。
重要
PowerShell Azure 资源管理器(AzureRM)模块已于 2024 年 2 月 29 日弃用。 所有未来的开发都应使用 Az.Sql 模块。 建议用户从 AzureRM 迁移到 Az PowerShell 模块,以确保持续支持和更新。 不再维护或支持 AzureRM 模块。 Az PowerShell 模块和 AzureRM 模块中命令的参数基本相同。 有关兼容性的详细信息,请参阅 介绍新的 Az PowerShell 模块。
步骤
如果你有独立的专用 SQL 池(以前称为 SQL DW),请使用 PowerShell 向 Microsoft Entra ID 注册 SQL Server:
Connect-AzAccount -Environment AzureChinaCloud Select-AzSubscription -SubscriptionId <subscriptionId> Set-AzSqlServer -ResourceGroupName your-database-server-resourceGroup -ServerName your-SQL-servername -AssignIdentityAzure Synapse Analytics 工作区中的专用 SQL 池不需要此步骤。 工作区的系统分配托管标识 (SA-MI) 是 Synapse 管理员角色的成员,因此对工作区的专用 SQL 池拥有更高的权限。
遵循创建存储帐户中的步骤创建一个常规用途 v2 存储帐户。
- 如果你有常规用途 v1 或 Blob 存储帐户,则必须按照升级到常规用途 v2 存储帐户中的步骤先升级到 v2。
- 有关 Azure Data Lake Storage Gen2 的已知问题,请参阅 Azure Data Lake Storage Gen2 的已知问题。
在存储帐户页,选择“访问控制(IAM)”。
选择添加,然后选择添加角色分配以打开添加角色分配页面。
分配以下角色。 有关详细步骤,请参阅使用 Azure 门户分配 Azure 角色。
设置 价值 角色 存储 Blob 数据参与者 将访问权限分配到 用户、组或服务主体 成员 托管已注册到 Microsoft Entra ID 的专用 SQL 池的服务器或工作区 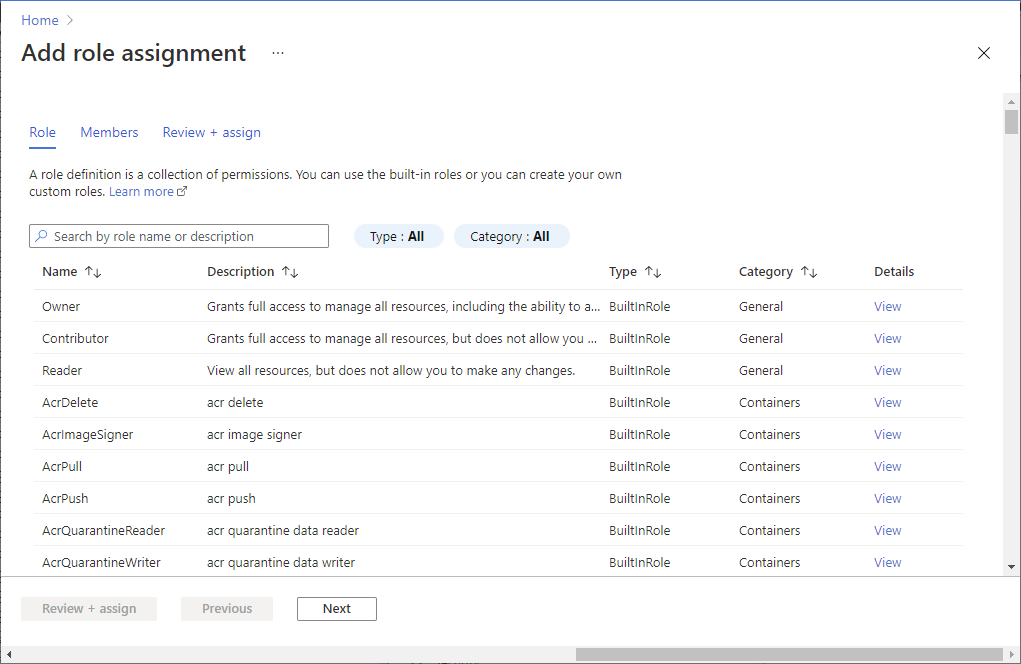
备注
只有对存储帐户具有“所有者”权限的成员才能执行此步骤。 有关各种 Azure 内置角色,请参阅 Azure 内置角色。
若要启用到 Azure 存储帐户的 PolyBase 连接,请执行以下操作:
创建数据库主密钥(如果此前尚未创建)。
CREATE MASTER KEY [ENCRYPTION BY PASSWORD = 'somepassword'];使用 IDENTITY = '托管服务标识' 创建以数据库为作用域的凭据。
CREATE DATABASE SCOPED CREDENTIAL msi_cred WITH IDENTITY = 'Managed Service Identity';使用 Azure 存储访问密钥时,不需指定 SECRET,因为此机制在后台使用托管标识。 Azure Synapse Analytics 工作区中的专用 SQL 池不需要此步骤。 工作区的系统分配托管标识 (SA-MI) 是 Synapse 管理员角色的成员,因此对工作区的专用 SQL 池拥有更高的权限。
使用 Azure 存储帐户连接到安全的虚拟网络时,IDENTITY 名称必须为“Managed Service Identity”,才能使 PolyBase 连接正常工作。
使用
abfss://方案创建一个外部数据源,以便通过 PolyBase 连接到常规用途 v2 存储帐户。CREATE EXTERNAL DATA SOURCE ext_datasource_with_abfss WITH (TYPE = hadoop, LOCATION = 'abfss://myfile@mystorageaccount.dfs.core.chinacloudapi.cn', CREDENTIAL = msi_cred);- 如果已经有外部表与常规用途 v1 或 Blob 存储帐户关联,则应先删除这些外部表。 然后删除相应的外部数据源。 接下来,使用
abfss://方案创建一个外部数据源,以便连接到常规用途 v2 存储帐户,如前所示。 然后,使用这个新的外部数据源重新创建所有外部表。 可以通过生成和发布脚本向导为所有外部表生成 create-script,以方便使用。 - 有关
abfss://方案的详细信息,请参阅使用 Azure Data Lake Storage Gen2 URI。 - 有关 T-SQL 命令的详细信息,请参阅 CREATE EXTERNAL DATA SOURCE。
- 如果已经有外部表与常规用途 v1 或 Blob 存储帐户关联,则应先删除这些外部表。 然后删除相应的外部数据源。 接下来,使用
使用外部表进行正常查询。
Azure SQL 数据库 Blob 审核
Azure SQL 审核可将 SQL 审核日志写入你自己的存储帐户。 如果此存储帐户使用虚拟网络服务终结点功能,请参阅如何将审计日志写入受 VNet 和防火墙保护的存储帐户。
向服务器添加虚拟网络防火墙规则
很久以前,此功能尚未得到增强,系统会要求你先启用虚拟网络服务终结点,然后才能在防火墙中实施实时虚拟网络规则。 这些终结点将指定的虚拟网络子网关联到 SQL 数据库中的一个数据库。 从 2018 年 1 月起,可以通过设置 IgnoreMissingVNetServiceEndpoint 标志来规避此要求。 现在,你可以向服务器添加虚拟网络防火墙规则,而无需启用虚拟网络服务终结点。
仅设置防火墙规则无助于保护服务器。 你还必须启用虚拟网络服务终结点才能使安全措施生效。 启用服务终结点时,你的虚拟网络子网会经历停机,直到完成从关闭到开启的转换。 在使用大型虚拟网络的情况下,这一停机时间尤其明显。 可以使用 IgnoreMissingVNetServiceEndpoint 标志,减少或消除转换期间的停机时间。
可以使用 PowerShell 设置 IgnoreMissingVNetServiceEndpoint 标志。 有关详细信息,请参阅使用 PowerShell 创建 Azure SQL 数据库的虚拟网络服务终结点和规则。
注意
有关 Azure Synapse Analytics 中的类似说明,请参阅 Azure Synapse Analytics IP 防火墙规则
使用 Azure 门户创建虚拟网络规则
本部分介绍了如何使用 Azure 门户在 Azure SQL 数据库中的数据库中创建虚拟网络规则。 此规则要求数据库接受来自已被标记为“虚拟网络服务终结点”的特定子网的通信。
注意
若要向服务器的虚拟网络防火墙规则添加服务终结点,请确保为子网启用服务终结点。
如果子网上未开启服务终结点,门户会要求你启用它们。 在你添加规则的窗格中选择“启用”按钮。
先决条件
必须已经有一个子网使用特定的虚拟网络服务终结点类型名称进行标记,且该名称必须与 Azure SQL 数据库相关。
- 相关的终结点类型名称为 Microsoft.Sql。
- 如果您的子网可能未使用类型名称标记,请参阅验证子网是否是端点。
Azure 门户操作步骤
登录到 Azure 门户。
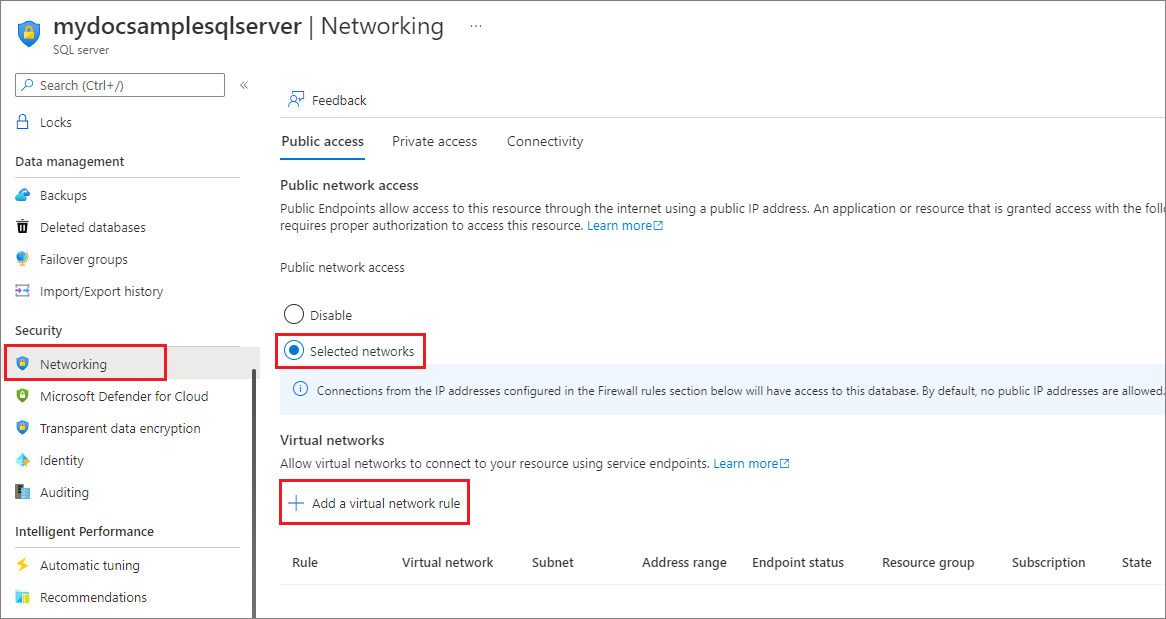
搜索并选择“SQL Server”,然后选择你的服务器。 在“安全性”下,选择“网络”。
在“公共访问”选项卡下,确保“公用网络访问”设置为“选择网络”,否则将隐藏“虚拟网络”设置。 在“虚拟网络”部分选择“+ 添加现有虚拟网络”。
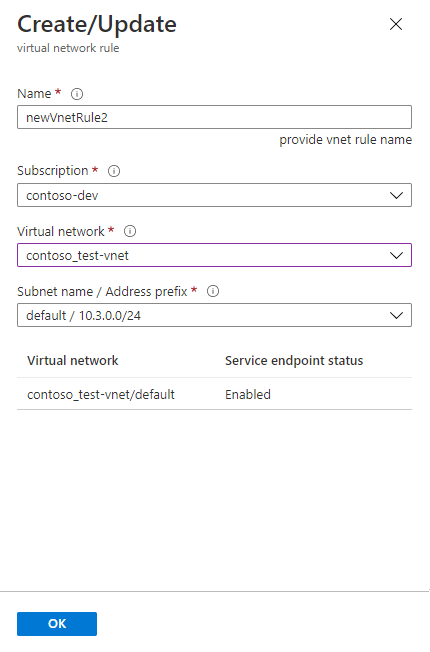
在新的“创建/更新”窗格中,使用你的 Azure 资源的名称填写各个框。
提示
必须包括子网的正确地址前缀。 可以在门户中找到“地址前缀”值。 转到“所有资源”“所有类型”>“虚拟网络”。 筛选器会显示虚拟网络。 选择你的虚拟网络,然后选择“子网”。 “地址范围”列包含你需要的地址前缀。
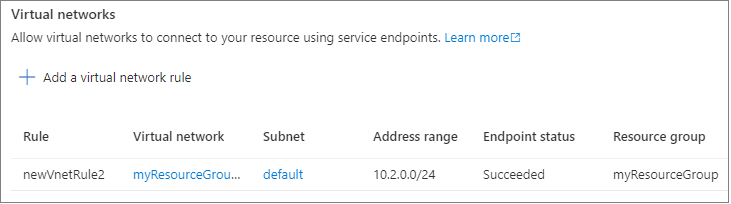
查看“防火墙”窗格中生成的虚拟网络规则。
将“允许 Azure 服务和资源访问此服务器”设置为“否”。
重要
如果将“允许 Azure 服务和资源访问此服务器”保持在选中状态,则服务器将接受来自 Azure 边界内任何子网的通信。 该通信源自系统认定的 IP 地址之一,系统认定这些地址在为 Azure 数据中心定义的范围内。 从安全角度来看,将此控件设置为“开启”可能会导致过度访问。 结合使用 Azure 虚拟网络服务终结点功能与 SQL 数据库的虚拟网络规则功能,可以共同减少您的安全攻击面。
选择窗格底部的“确定”按钮。
注意
以下状态适用于这些规则:
- 就绪:表示你启动的操作已成功。
- 失败:表示你启动的操作已失败。
- 已删除:仅适用于
Delete操作,表示规则已被删除,不再应用。 - InProgress:表示操作正在进行。 操作处于这种状态时,会应用旧规则。
使用 PowerShell 创建虚拟网络规则
脚本还可以使用 PowerShell cmdlet New-AzSqlServerVirtualNetworkRule 或 az network vnet create 创建虚拟网络规则。 有关详细信息,请参阅使用 PowerShell 创建 Azure SQL 数据库的虚拟网络服务终结点和规则。
使用 REST API 创建虚拟网络规则
在内部,用于 SQL 虚拟网络操作的 PowerShell cmdlet 会调用 REST API。 可以直接调用 REST API。 有关详细信息,请参阅虚拟网络规则:操作。
排查错误 40914 和 40615
连接错误 40914 与虚拟网络规则(如 Azure 门户中的“防火墙”窗格所指定的那样)相关。
错误 40615 基本相似,不同之处在于它与防火墙上的 IP 地址规则相关。
错误 40914
消息文本:“无法打开登录时请求的服务器 ‘[server-name]’。 不允许客户端访问服务器。”
错误说明:客户端位于包含虚拟网络服务器终结点的子网中。 不过,服务器没有授权子网与数据库进行通信的虚拟网络规则。
错误解决方法:在 Azure 门户的“防火墙”窗格中,使用虚拟网络规则控件为子网添加虚拟网络规则。
错误 40615
消息文本:“无法打开登录时请求的服务器 ‘’。 不允许 IP 地址为 ‘{1}’ 的客户端访问此服务器。”
错误说明:客户端尝试从无权连接到服务器的 IP 地址进行连接。 服务器防火墙没有 IP 地址规则允许客户端从给定 IP 地址与数据库进行通信。
错误解决方法:输入客户端 IP 地址作为 IP 规则。 使用 Azure 门户中的“防火墙”窗格执行此步骤。