适用于:Azure SQL 数据库
Azure Synapse Analytics(仅限专用 SQL 池)
使用 Azure 专用链接可以通过专用终结点连接到 Azure 中的各种 PaaS 服务。 若要查看支持专用链接功能的 PaaS 服务列表,请转到专用链接文档页。 专用终结点是特定 VNet 和子网中的专用 IP 地址。
重要
本文适用于 Azure SQL 数据库和 Azure Synapse Analytics 中的专用 SQL 池(以前称为 SQL DW)。 这些设置适用于所有与服务器关联的 SQL 数据库和专用 SQL 池(以前的 SQL DW)数据库。 为简单起见,术语“数据库”是指 Azure SQL 数据库中的数据库和 Azure Synapse Analytic 中的数据库。 同样,无论何时提及“服务器”,都是指托管 Azure SQL 数据库和 Azure Synapse Analytics 中专用 SQL 池(以前称为 SQL DW)的逻辑服务器。 本文不适用于 Azure SQL 托管实例或 Azure Synapse Analytics 工作区中的专用 SQL 池。
如何设置专用链接
创建过程
可以使用 Azure 门户、PowerShell 或 Azure CLI 创建专用终结点:
审批过程
网络管理员创建专用终结点 (PE) 后,SQL 管理员可以管理与 SQL 数据库建立的专用终结点连接 (PEC)。
在 Azure 门户中,导航到服务器资源。
导航到专用终结点审批页:
- 在“SQL Server”的“安全性”下,选择“网络”。 选择“专用访问”选项卡。
- 在 Synapse 工作区的资源菜单中的“安全性”下,选择“专用终结点连接”。
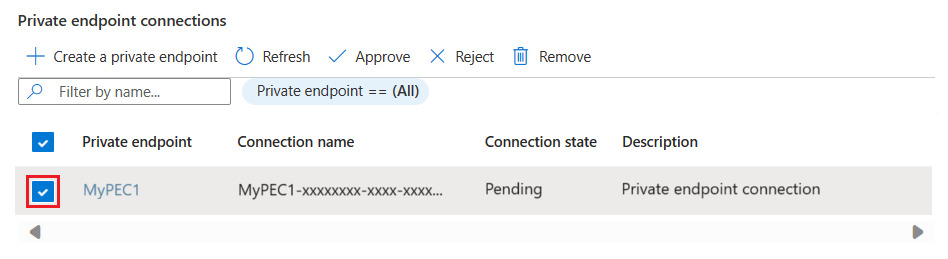
此页面显示以下字段:
- 所有专用终结点连接 (PEC) 的列表
- 已创建专用终结点 (PE)
如果没有专用终结点,请使用“创建专用终结点”按钮创建一个终结点。 否则,请通过选择它在列表中选择单个 PEC。
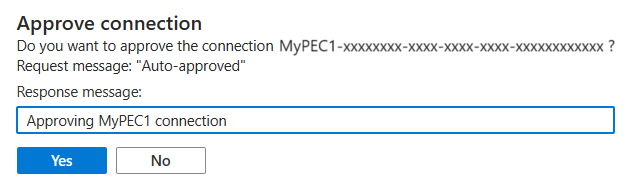
SQL 管理员可以选择批准或拒绝 PEC,并可以选择性地添加简短的文本回复。
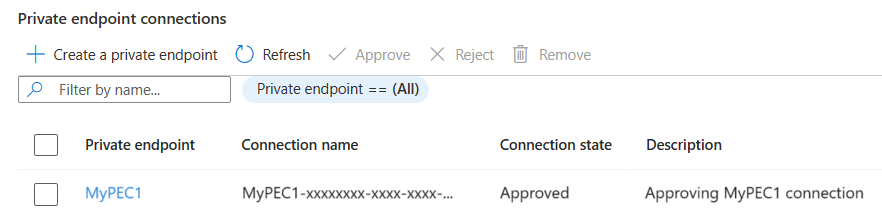
批准或拒绝后,该列表将反映相应的状态以及回复文本。
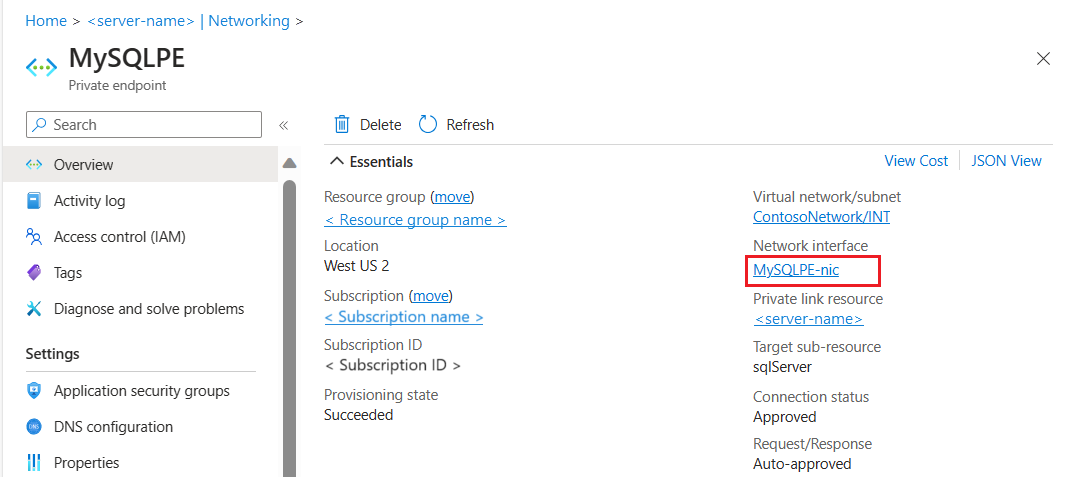
最后,选择专用终结点名称
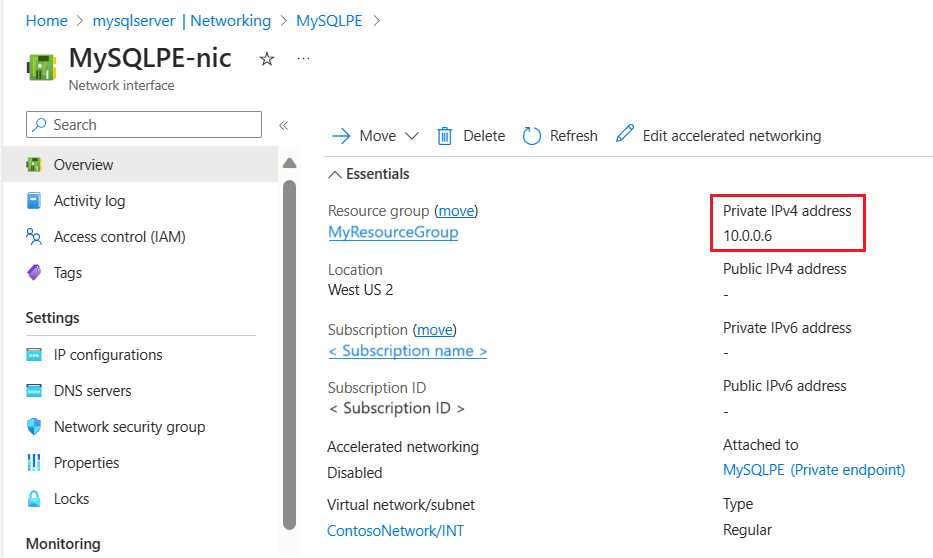
此操作会将你转到“专用终结点概述”页。 选择“网络接口”链接以获取专用终结点连接的网络接口详细信息。
“网络接口”页面显示专用终结点连接的专用 IP 地址。
重要
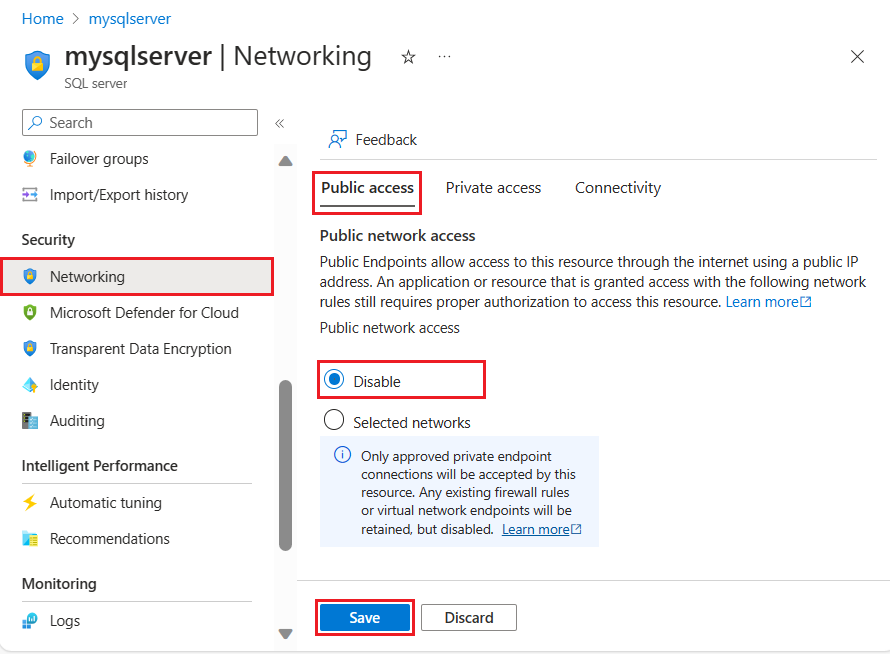
添加专用终结点连接时,默认情况下不会阻止到逻辑服务器的公共路由。 在“防火墙和虚拟网络”窗格中,“拒绝公用网络访问”设置默认处于未选中状态。 若要禁用公用网络访问,请确保选择“拒绝公用网络访问”。
禁用对逻辑服务器的公共访问
在 Azure SQL 数据库逻辑 SQL 服务器中,假设要禁用对逻辑服务器的所有公共访问,并且仅允许来自虚拟网络的连接。
首先,确保已启用并已配置专用终结点连接。 然后,禁用对逻辑服务器的公共访问:
测试从同一虚拟网络中的 Azure VM 到 SQL 数据库的连接
对于此场景,假设你已在与专用终结点相同的虚拟网络中创建了一个运行最新版 Windows 的 Azure虚拟机 (VM)。
然后,可以使用以下工具执行一些基本的连接检查,以确保 VM 通过专用终结点连接到 SQL 数据库:
- Telnet
- PsPing
- Nmap
- SQL Server Management Studio (SSMS)
使用 Telnet 检查连接
Telnet 客户端是可用于测试连接的 Windows 功能。 根据 Windows OS 的版本,可能需要显式启用此功能。
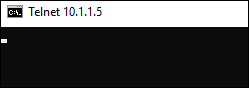
安装 Telnet 后,打开命令提示符窗口。 运行 Telnet 命令并指定 SQL 数据库中的数据库的 IP 地址和专用终结点。
telnet 10.9.0.4 1433
Telnet 连接成功后,命令窗口将输出白屏,如下图所示:
使用 Powershell 命令检查连接性:
Test-NetConnection -computer myserver.database.chinacloudapi.cn -port 1433
使用 Psping 检查连接性
可按如下所示使用 Psping 检查专用终结点是否正在侦听端口 1433 上的连接。
按如下所示通过提供逻辑 SQL 服务器的 FQDN 和端口 1433 来运行 Psping:
PsPing.exe mysqldbsrvr.database.chinacloudapi.cn:1433
以下是预期输出的示例:
TCP connect to 10.9.0.4:1433:
5 iterations (warmup 1) ping test:
Connecting to 10.9.0.4:1433 (warmup): from 10.6.0.4:49953: 2.83ms
Connecting to 10.9.0.4:1433: from 10.6.0.4:49954: 1.26ms
Connecting to 10.9.0.4:1433: from 10.6.0.4:49955: 1.98ms
Connecting to 10.9.0.4:1433: from 10.6.0.4:49956: 1.43ms
Connecting to 10.9.0.4:1433: from 10.6.0.4:49958: 2.28ms
输出显示 Psping 可以对与专用终结点关联的专用 IP 地址执行 Ping 操作。
使用 Nmap 检查连接
Nmap(网络映射器)是一个用于网络发现和安全审核的免费开源工具。 有关详细信息和下载链接,请访问 https://Nmap.org。可以使用此工具来确保专用终结点侦听端口 1433 上的连接。
按如下所示运行 Nmap,并提供托管专用终结点的子网的地址范围。
Nmap -n -sP 10.9.0.0/24
以下是预期输出的示例:
Nmap scan report for 10.9.0.4
Host is up (0.00s latency).
Nmap done: 256 IP addresses (1 host up) scanned in 207.00 seconds
结果显示,一个对应于专用终结点 IP 地址的 IP 地址已启动。
使用 SQL Server Management Studio (SSMS) 检查连接
注意
在客户端的连接字符串中 () 使用服务器的完全限定域名 (FQDN)<server>.database.chinacloudapi.cn。 直接登录 IP 地址的任何尝试或使用专用链接 FQDN (<server>.privatelink.database.chinacloudapi.cn) 都将失败。 此行为是设计使然,因为专用终结点会将流量路由到该区域中的 SQL 网关,并且需要指定正确的 FQDN 才能成功登录。
请按照此处的步骤使用 SSMS 连接到 SQL 数据库。 使用 SSMS 连接到 SQL 数据库后,以下查询应反映与你从中连接的 Azure VM 的专用 IP 地址匹配的 client_net_address:
SELECT client_net_address
FROM sys.dm_exec_connections
WHERE session_id = @@SPID;
将重定向连接策略与专用终结点配合使用
我们建议客户将专用链接与“重定向连接策略”配合使用,以减少延迟并提高吞吐量。 对于使用此模式的连接,客户端需满足以下先决条件:
允许从托管专用终结点的 VNET 到端口范围 1433 到 65535 的入站通信。
允许从托管客户端的 VNET 至端口范围 1433 到 65535 的出站通信。
使用 内置了重定向支持的最新版本的驱动程序。 ODBC、OLE DB、.NET SqlClient 数据提供程序、Core .NET SqlClient 数据提供程序和 JDBC(版本 9.4 或更高版本)驱动程序中包含重定向支持。 源自所有其他驱动程序的连接将使用代理。
满足先决条件后,客户端需要明确选择“重定向”连接策略。 如果在设置专用终结点之前将连接策略设置为 “重定向” ,则设置专用终结点后,可能需要切换连接策略。
如果修改防火墙设置以允许在 1433-65535 端口范围内进行出站访问不可行,则替代解决方法是将连接策略更改为“代理”。
使用“默认”连接策略的现有专用终结点将使用具有端口 1433 的代理连接策略。 这样做的原因是为了避免由于重定向所需的端口范围未开放而导致从客户端访问 SQL 数据库的流量发生任何中断。
注意
对于专用 SQL 池,使用专用终结点时的连接策略始终是“代理”。 使用专用终结点时,更改设置不会影响专用 SQL 池。
通过专用对等互连建立本地连接
当客户从本地计算机连接到公共终结点时,需要使用服务器级防火墙规则将其 IP 地址添加到基于 IP 的防火墙。 尽管此模型非常适合用于允许对开发或测试工作负荷的单个计算机进行访问,但在生产环境中却难以管理。
借助专用链接,客户可以使用 ExpressRoute、专用对等互连或 VPN 隧道实现对专用终结点的跨界访问。 然后,客户可以通过公共终结点禁用所有访问,而无需使用基于 IP 的防火墙来允许任何 IP 地址。
Azure SQL 数据库专用链接的用例
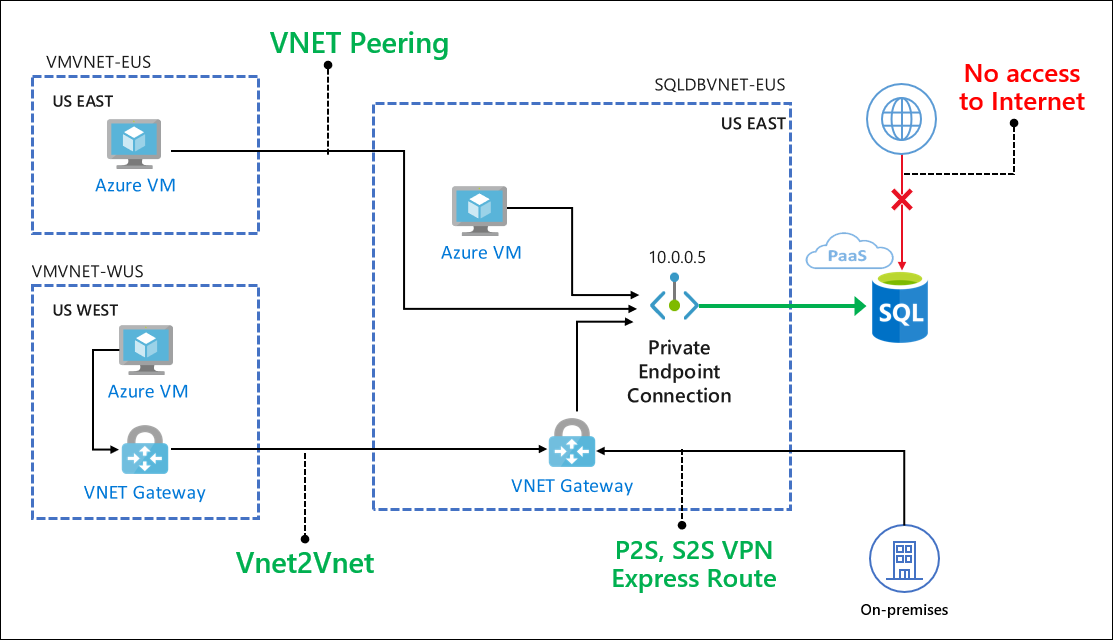
客户端可以从同一虚拟网络、同一区域中的对等互连虚拟网络,或通过跨区域的虚拟网络到虚拟网络连接来连接到专用终结点。 此外,用户可以通过 ExpressRoute、专用对等互连或 VPN 隧道从本地环境进行连接。 以下简化示意图显示了常见用例。
此外,不直接在虚拟网络中运行但与之集成的服务(例如,应用服务 Web 应用或 Functions)也可以实现与数据库的专用连接。 有关此特定用例的详细信息,请参阅与 Azure SQL 数据库建立专用连接的 Web 应用体系结构方案。
从对等互连虚拟网络中的 Azure VM 进行连接
配置虚拟网络对等互联,以便从对等互联虚拟网络中的 Azure VM 建立与 SQL 数据库的连接。
从虚拟网络中的 Azure VM 连接到虚拟网络环境
配置虚拟网络到虚拟网络 VPN 网关连接,以便从另一区域或订阅中的 Azure VM 建立与 SQL 数据库中的数据库的连接。
通过 VPN 从本地环境进行连接
若要建立从本地环境到 SQL 数据库中的数据库的连接,请选择并实施以下选项之一:
还要考虑 DNS 配置方案,因为服务的 FQDN 可以解析为公共 IP 地址。
使用 PolyBase 和 COPY 语句从 Azure Synapse Analytics 连接到 Azure 存储
PolyBase 和 COPY 语句通常用于将数据从 Azure 存储帐户加载到 Azure Synapse Analytics 中。 如果要从中加载数据的 Azure 存储帐户仅允许通过专用终结点、服务终结点或基于 IP 的防火墙访问一组虚拟网络子网,则通过 PolyBase 和 COPY 语句与该帐户建立的连接将会断开。 若要启用 Azure Synapse Analytics 连接到已保护到虚拟网络的 Azure 存储的导入和导出方案,请参阅 将虚拟网络服务终结点与 Azure 存储配合使用的影响。
数据渗透防护
Azure SQL 数据库中的数据渗透是指用户(例如数据库管理员)能够从一个系统提取数据,并将其移到组织外部的其他位置或系统。 例如,该用户将数据移到非 Microsoft 实体拥有的存储帐户。
假设某个用户在连接到 SQL 数据库中的数据库的 Azure 虚拟机中运行 SQL Server Management Studio (SSMS)。 此数据库位于中国东部数据中心。 以下示例演示如何使用网络访问控制来限制通过公共终结点对 SQL 数据库进行访问。
- 通过将“允许 Azure 服务”设置为“关闭”,禁用所有 Azure 服务流量通过公共终结点进入 SQL 数据库。 确保不要在服务器和数据库级防火墙规则中允许任何 IP 地址。 有关详细信息,请参阅 Azure SQL 数据库和 Azure Synapse Analytics 网络访问控制。
- 仅允许使用 VM 的专用 IP 地址向 SQL 数据库中的数据库发送流量。 有关详细信息,请参阅有关服务终结点和虚拟网络防火墙规则的文章。
- 在 Azure 虚拟机上,按如下所示使用网络安全组 (NSG) 和服务标记缩小传出连接的范围。
- 指定 NSG 规则,以允许服务标记 = SQL.ChinaEast 的流量 - 仅允许连接到“中国东部”的 SQL 数据库。
- 指定 NSG 规则(具有较高的优先级),以拒绝服务标记 = SQL 的流量 - 拒绝连接到所有区域中的 SQL 数据库。
完成此设置后,Azure VM 只能连接到“中国东部”区域 SQL 数据库中的一个数据库。 不过,连接并不局限于 SQL 数据库中的单个数据库。 VM 仍可连接到“中国东部”区域中的任意数据库,包括不在订阅中的数据库。 尽管我们在上述场景中已将数据渗透范围缩小到了特定的区域,但我们并未完全消除这种渗透。
借助专用链接,客户现在可以设置 NSG 等网络访问控制来限制对专用终结点的访问。 然后,将单个 Azure PaaS 资源映射到特定的专用终结点。 恶意预览体验成员只能访问映射的 PaaS 资源(例如 SQL 数据库中的数据库),而不能访问其他资源。