适用范围:Azure 逻辑应用(消耗型 + 标准型)
本指南介绍如何使用 Azure Blob 存储连接器从 Azure 逻辑应用中的工作流访问 Azure Blob 存储帐户和容器。 此连接器提供工作流可用于 blob 操作的触发器和操作。 然后,你可以创建自动工作流,该工作流在存储容器或其他系统中的事件触发时运行,并运行操作来处理存储容器中的数据。 例如,可以在 Azure 存储帐户中访问和管理作为 blob 存储的文件。
可以从多租户消耗逻辑应用或单租户标准逻辑应用中的工作流连接到 Azure Blob 存储。 虽然消耗工作流仅提供托管连接器版本,但标准工作流同时提供内置连接器和托管连接器版本。
连接器技术参考
Azure Blob 存储连接器具有不同的版本,具体取决于逻辑应用类型和主机环境。
| 逻辑应用 | 环境 | 连接器版本 |
|---|---|---|
| 消耗 | 多租户 Azure 逻辑应用 | 托管连接器,该连接器显示在 “共享”下的连接器库中。 有关详细信息,请查看以下文档: - Azure Blob 存储托管连接器参考 - Azure 逻辑应用中的托管连接器 |
| 标准 | 单租户 Azure 逻辑应用和应用服务环境 v3(仅限 Windows 计划) | 托管连接器(Azure 托管),该连接器显示在 “共享”下的连接器库中,内置连接器( 基于服务提供商)显示在 “内置”下的连接器库中。 内置版本在以下方面有所不同: - 内置版本仅需连接字符串便可直接连接到 Azure 存储帐户。 - 内置版本可以直接访问 Azure 虚拟网络。 有关详细信息,请查看以下文档: - Azure Blob 存储托管连接器参考 - Azure Blob 内置连接器参考 - Azure 逻辑应用中的内置连接器 |
限制
Azure Blob 存储托管连接器操作可以读取或写入 50 MB 或更小的文件。 若要处理大于 50 MB 但最大为 1,024 MB 的文件,Azure Blob 存储作支持 消息分块。 名为“获取 Blob 内容”的 Blob 存储操作将隐式使用分块。
虽然 Azure Blob 存储托管触发器和内置触发器不支持分块,但内置触发器可以处理 50 MB 或更大的文件。 但是,当托管触发器请求文件内容时,该触发器只会选择 50 MB 或更小的文件。 若要获取大于 50 MB 的文件,请遵循以下模式:
使用返回文件属性的 Blob 触发器,比如当添加或者修改 Blob 时(仅属性)。
接下来,通过名为获取 blob 内容的 Azure Blob 存储托管连接器操作,读取完整的文件并隐式地使用区块。
Azure Blob 存储触发器限制
- 在轮询虚拟文件夹中,托管连接器触发器限制为 30,000 个 blob。
- 在整个轮询容器中,内置连接器触发器限制为 10,000 个 blob。
如果超出该限制,则新 blob 可能无法触发工作流,因此会跳过该触发器。
先决条件
Azure 帐户和订阅。 如果没有 Azure 订阅,请注册试用版 Azure 订阅。
要从中访问 Azure 存储帐户的逻辑应用工作流。
若要使用 Azure Blob 存储触发器启动工作流,需要有一个空白工作流。 若要使用 Azure Blob 存储操作,需要已经有一个触发器的工作流。
如果没有逻辑应用资源和工作流,请立即按照所需的逻辑应用的步骤创建它们:
添加 Blob 触发器
在消费工作流中,只有 Azure Blob 存储管理连接器可用。 在标准工作流中,可以使用 Azure Blob 存储托管连接器和内置连接器。 尽管每个连接器版本仅提供一个 Azure Blob 存储触发器,但触发器名称因是否有消耗工作流或标准工作流而异:
| 逻辑应用 | 连接器版本 | 触发器名称 | 说明 |
|---|---|---|---|
| 消耗 | 仅托管连接器 | “添加或修改 Blob 时(仅属性)” | 在存储容器的根文件夹中添加或更新 Blob 的属性时,会触发触发器。 设置托管触发器时,托管版本会忽略存储容器中的现有 blob。 |
| 标准 | 内置连接器 托管连接器 |
内置:添加或更新 Blob 时 托管:添加或修改 Blob 时(仅属性) |
内置:在存储容器中添加或更新 Blob 时会触发触发器,触发器也会针对存储容器中的任何嵌套文件夹(而不仅仅是根文件夹)触发。 设置内置触发器时,内置版本将处理存储容器中的所有现有 blob。 托管:在存储容器的根文件夹中添加或更新 Blob 的属性时,会触发触发器。 设置托管触发器时,托管版本会忽略存储容器中的现有 blob。 |
以下步骤使用 Azure 门户,但利用适当的 Azure 逻辑应用扩展,也可以使用以下工具来创建逻辑应用工作流:
- 消耗逻辑应用工作流:Visual Studio Code
- 标准逻辑应用工作流:Visual Studio Code
在 Azure 门户中,打开你的消耗逻辑应用资源。
在“资源边栏”菜单的 “开发工具”下,选择设计器以打开空白工作流。
按照将触发器添加到工作流的常规步骤,为你的方案添加 Azure Blob 存储托管触发器。
此示例继续使用名为“添加或修改 Blob 时”的 Azure Blob 存储触发器(仅属性)。
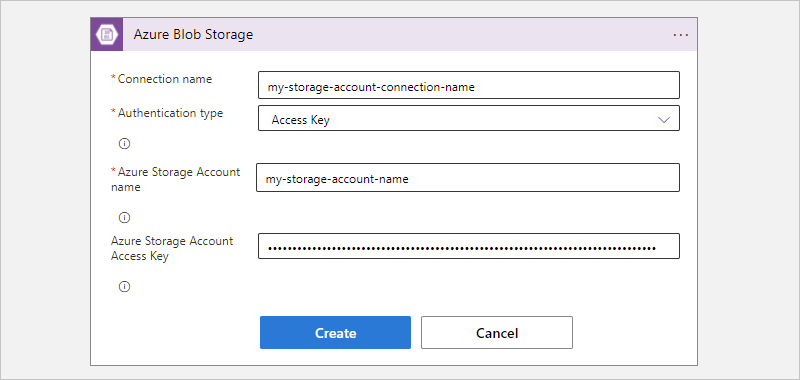
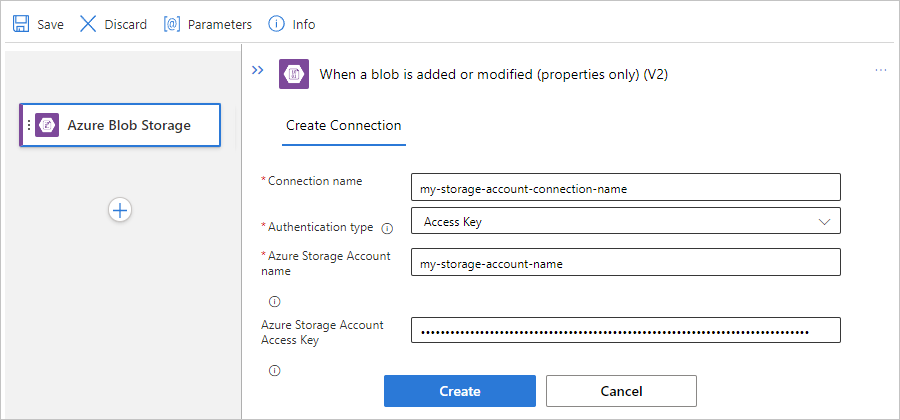
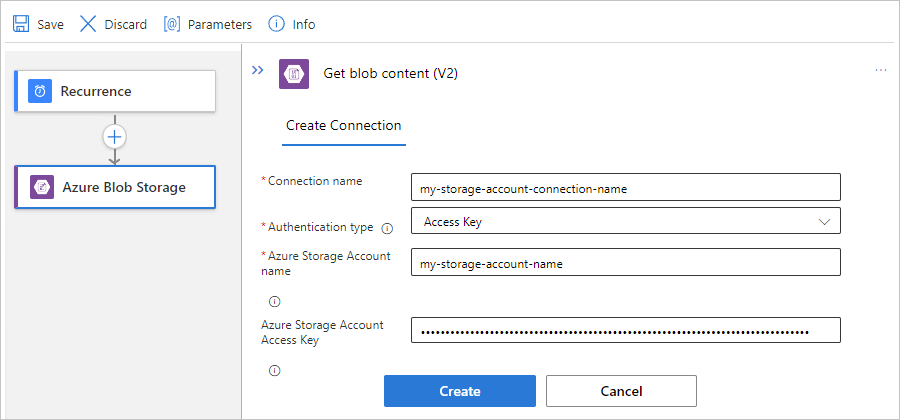
如果出现提示,请为与存储帐户的连接提供以下信息。 完成操作后,选择“创建”。
属性 必选 说明 连接名称 是 连接的名称。 身份验证类型 是 存储帐户的身份验证类型。 有关详细信息,请查看 支持身份验证的触发器和操作的身份验证类型。 例如,此连接使用 访问密钥 身份验证,并提供存储帐户的访问密钥值以及以下属性值:
属性 必选 值 说明 Azure 存储帐户名称或 Blob 终结点 是,但仅用于访问密钥身份验证 <存储帐户名称 Blob 容器所在的 Azure 存储帐户的名称。
注意:若要查找存储帐户名称,请在 Azure 门户中打开存储帐户资源。 在资源菜单中的“安全性 + 网络”下,选择“访问密钥”。 在“存储帐户名称”下,复制并保存名称。Azure 存储帐户访问密钥 是,但仅用于访问密钥身份验证 < > Azure 存储帐户的访问密钥。
注意:若要查找访问密钥,请在 Azure 门户中打开存储帐户资源。 在资源菜单中的“安全性 + 网络”下,选择“访问密钥”“密钥1”“显示”。 复制并保存主键值。在触发器信息框显示后,提供必要的信息。
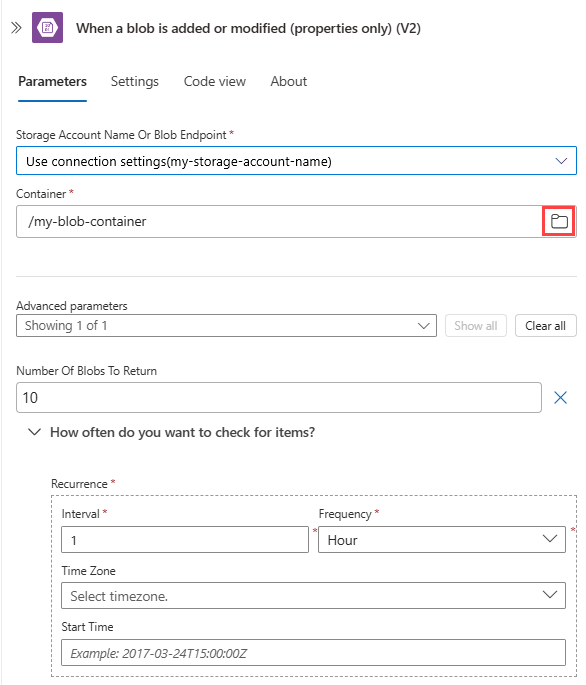
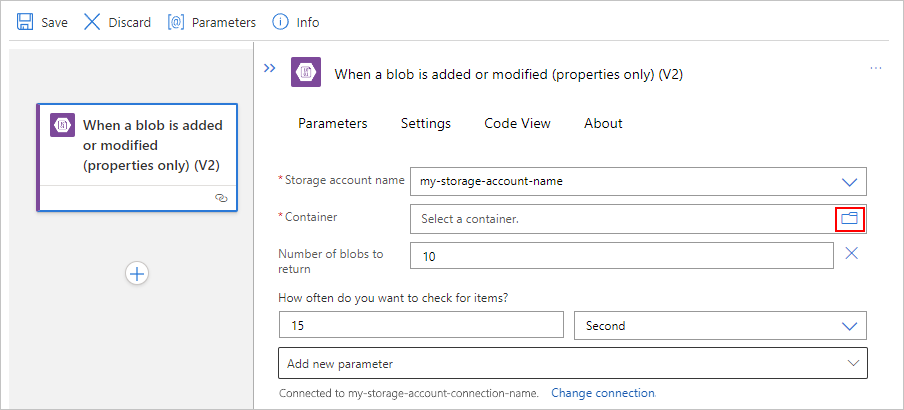
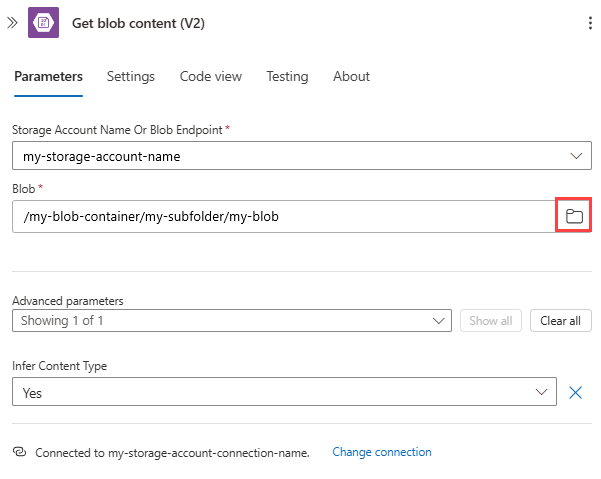
对于“容器”属性值,选择文件夹图标以浏览 blob 容器。 或者,使用语法 /<container-name>手动输入路径,例如:
如果触发器存在任何其他参数,请打开 “高级参数 ”列表,然后选择所需的参数。
有关详细信息,请查看 Azure Blob 存储托管连接器触发器属性。
添加工作流所需的任何其他操作。
完成后,保存工作流。 在设计器工具栏上选择“保存”。
添加 Blob 操作
在消费工作流中,只有 Azure Blob 存储管理连接器可用。 在标准工作流中,可以使用 Azure Blob 存储托管连接器和内置连接器。 每个版本都根据您使用的是消费型工作流还是标准型工作流,提供多种不同命名的操作。 例如,托管连接器和内置连接器版本都有各自的操作来获取文件元数据和文件内容。
在消费或标准工作流中提供了托管连接器操作。
内置连接器操作仅在标准工作流中可用。
以下步骤使用 Azure 门户,但利用适当的 Azure 逻辑应用扩展,也可使用以下工具来生成逻辑应用工作流:
- 消耗工作流:Visual Studio Code
- 标准工作流:Visual Studio Code
在 Azure 门户中,打开你的消耗逻辑应用资源。
在“资源边栏”菜单的 “开发工具”下,选择设计器以打开工作流。
这些步骤假定工作流已有触发器。
此示例使用定期触发器。
按照将操作添加到工作流的常规步骤,为你的方案添加 Azure Blob 存储托管操作。
此示例继续执行名为“获取 blob 内容”的操作。
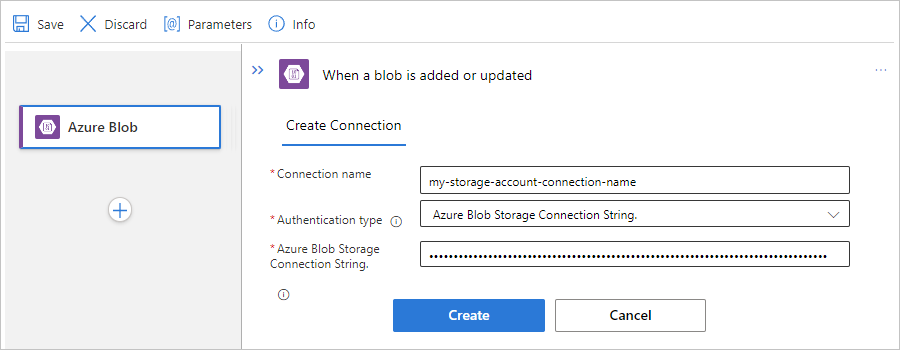
根据提示为连接提供以下信息。 完成操作后,选择“创建”。
属性 必选 说明 连接名称 是 连接的名称 身份验证类型 是 存储帐户的身份验证类型。 有关详细信息,请查看 支持身份验证的触发器和操作的身份验证类型。 例如,此连接使用 访问密钥 身份验证,并提供存储帐户的访问密钥值以及以下属性值:
属性 必选 值 说明 Azure 存储帐户名称或 Blob 终结点 是,但仅用于访问密钥身份验证 <存储帐户名称 Blob 容器所在的 Azure 存储帐户的名称。
注意:若要查找存储帐户名称,请在 Azure 门户中打开存储帐户资源。 在资源菜单中的“安全性 + 网络”下,选择“访问密钥”。 在“存储帐户名称”下,复制并保存名称。Azure 存储帐户访问密钥 是,但仅用于访问密钥身份验证 < > Azure 存储帐户的访问密钥。
注意:若要查找访问密钥,请在 Azure 门户中打开存储帐户资源。 在资源菜单中的“安全性 + 网络”下,选择“访问密钥”“密钥1”“显示”。 复制并保存主键值。在操作信息框中,提供必需的信息。
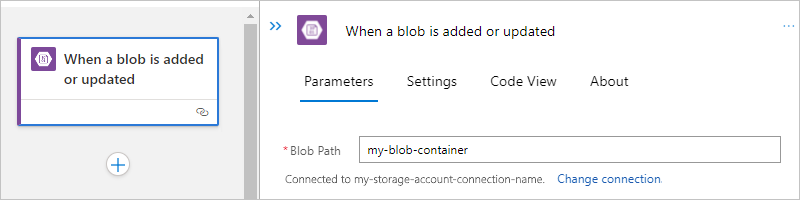
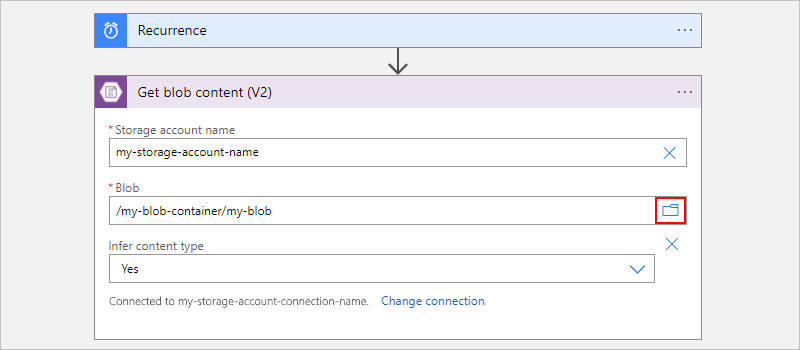
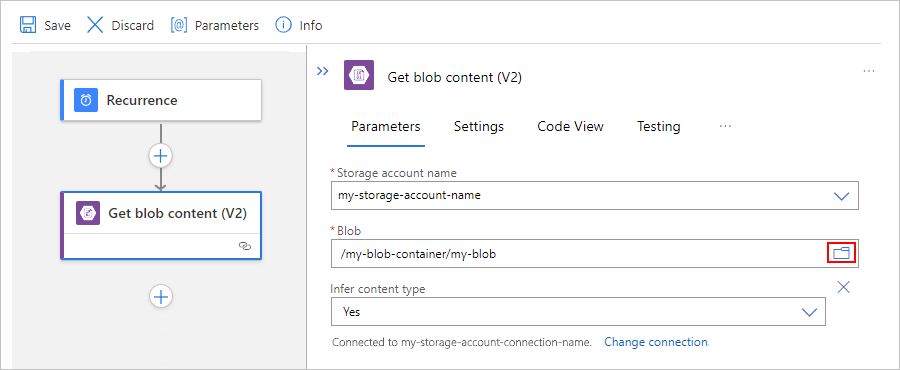
例如,在“获取 blob 内容”操作中提供存储帐户名称。 对于“Blob”属性值,选择文件夹图标以浏览存储容器或文件夹。 或者,手动输入路径。
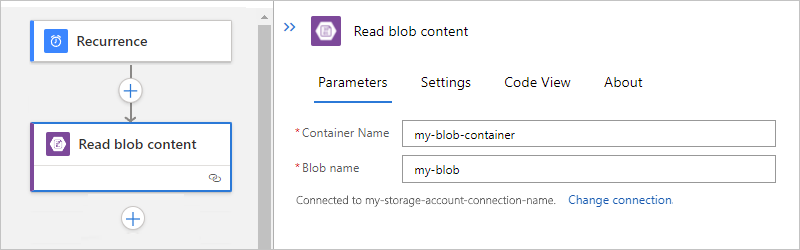
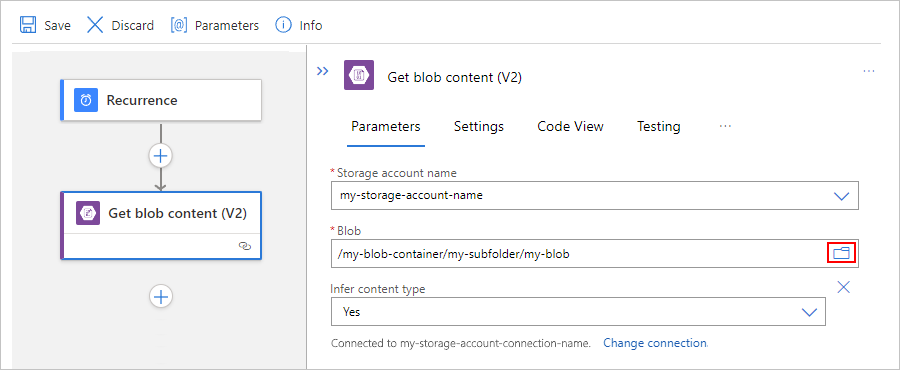
任务 Blob 路径语法 获取根文件夹中有关特定 Blob 的内容。 /<container-name>/<blob-name> 获取子文件夹中有关特定 Blob 的内容。 /<container-name>/<subfolder>/<blob-name> 以下示例展示了从根文件夹中的 Blob 获取内容的操作设置:
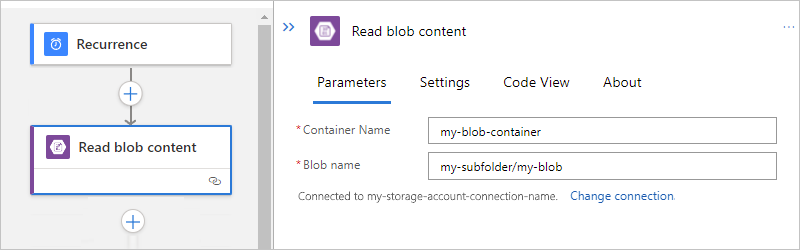
以下示例展示了从子文件夹中的 Blob 获取内容的操作设置:
添加工作流所需的任何其他操作。
完成后,保存工作流。 在设计器工具栏上选择“保存”。
访问防火墙后的存储帐户
通过使用防火墙和防火墙规则限制访问,可以提高 Azure 存储帐户的网络安全性。 但是,此设置会给需要访问存储帐户的 Azure 和其他 Azure 服务带来挑战。 数据中心的本地通信抽象化了内部 IP 地址,因此仅允许通过 IP 地址的流量可能无法成功支持跨防火墙进行通信。 根据所使用的 Azure Blob 存储连接器,可以使用以下选项:
若要在消耗逻辑应用中使用 Azure Blob 存储托管连接器访问防火墙后面的存储帐户,请参阅以下部分:
若要在标准逻辑应用中访问防火墙后面的存储帐户,请查看以下文档:
Azure Blob 存储内置连接器:通过虚拟网络集成访问存储帐户
Azure Blob 存储托管连接器:访问其他区域中的存储帐户
访问其他区域中的存储帐户
如果不使用托管标识身份验证,当逻辑应用资源和存储帐户位于同一区域时,逻辑应用工作流无法直接访问防火墙后面的存储帐户。 一种解决方案是,将逻辑应用资源放置在与存储帐户不同的区域。 然后,允许访问区域中托管连接器的出站 IP 地址。
注意
此解决方案不适用于 Azure 表存储连接器和 Azure 队列存储连接器。 若要访问表存储或队列存储,请使用内置的 HTTP 触发器和操作。
若要将出站 IP 地址添加到存储帐户防火墙,请执行以下步骤:
记下逻辑应用资源所在区域的托管连接器出站 IP 地址。
在 Azure 门户中,找到并打开你的存储帐户资源。
在“资源边栏”菜单的 “安全性 + 网络”下,选择“ 网络”。
通过受信任的虚拟网络访问存储帐户
如果逻辑应用和存储帐户位于 同一 区域:
可以通过创建专用终结点,将存储帐户放入 Azure 虚拟网络,然后将该虚拟网络添加到受信任的虚拟网络列表中。 为了让逻辑应用通过受信任的虚拟网络访问存储帐户,需要创建可连接到虚拟网络中的资源的标准逻辑应用。
如果逻辑应用和存储帐户位于 不同的 区域中:
在存储帐户上创建专用终结点以进行访问。
通过虚拟网络集成访问存储帐户
如果逻辑应用和存储帐户位于 同一 区域:
可以通过创建专用终结点,将存储帐户放入 Azure 虚拟网络,然后将该虚拟网络添加到受信任的虚拟网络列表中。 若要给予逻辑应用对存储帐户的访问权限,必须使用虚拟网络集成设置出站流量,以便能够连接到虚拟网络中的资源。 然后,可以将虚拟网络添加到存储帐户的受信任虚拟网络列表中。
如果逻辑应用和存储帐户位于 不同的 区域中:
在存储帐户上创建专用终结点以进行访问。
使用系统管理的标识访问同一区域中的 Blob 存储
若要连接到任何区域中的 Azure Blob 存储,可以使用托管标识进行身份验证。 你可以创建一个异常,让 Azure 受信任的服务(如托管标识)可以穿过防火墙访问存储帐户。
注意
此解决方案不适用于标准逻辑应用。 即使对标准逻辑应用使用系统分配的托管标识,Azure Blob 存储托管连接器也无法连接到同一区域中的存储帐户。
若要在逻辑应用中使用托管标识访问 Blob 存储,请执行以下步骤:
注意
此解决方案具有以下限制:
若要对存储帐户连接进行身份验证,必须设置系统分配的托管标识。 用户分配的托管标识将不起作用。
配置存储帐户访问权限
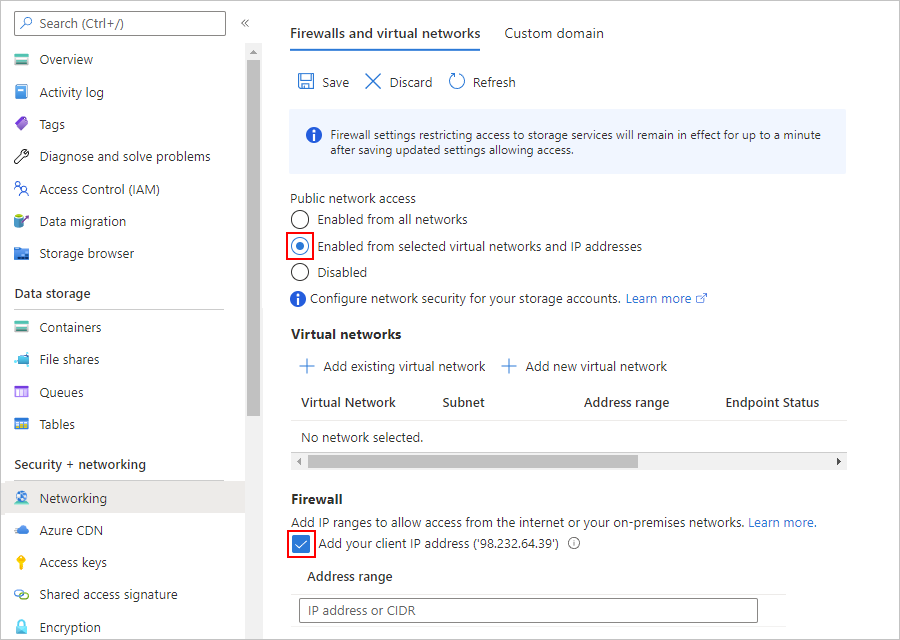
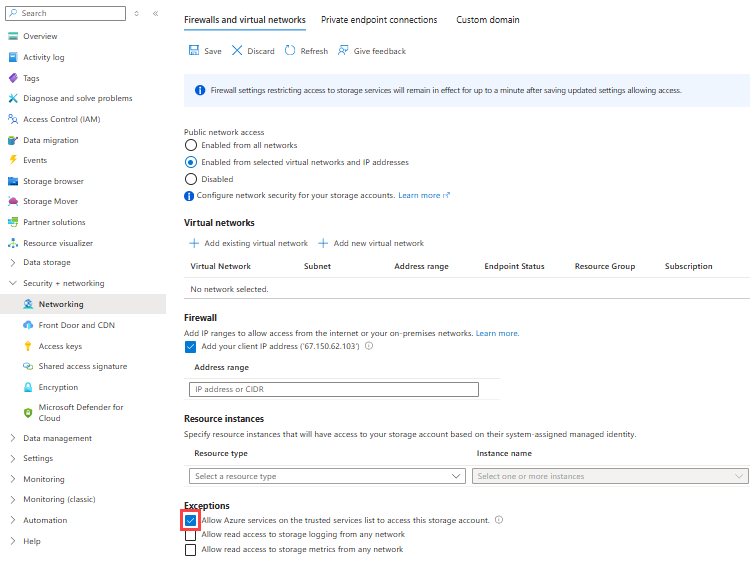
若要设置异常和托管标识支持,请先为存储帐户配置适当访问权限:
在 Azure 门户中,找到并打开你的存储帐户资源。
在存储帐户导航菜单的“安全性 + 网络”下,选择“网络” 。
注意
如果尝试从工作流连接到存储帐户时收到“403 禁止”错误,则可能有多种原因。 在继续执行其他步骤之前,请尝试以下解决方法。 首先,禁用 “允许受信任的服务”列表中的 Azure 服务访问此存储帐户 并保存更改的设置。 然后重新启用此设置,并再次保存更改。
为逻辑应用创建角色分配
接下来,在逻辑应用资源上启用托管标识支持。
对于多租户环境中的消耗型逻辑应用和单租户环境中的标准逻辑应用,以下步骤是相同的。
在 Azure 门户中,打开你的逻辑应用资源。
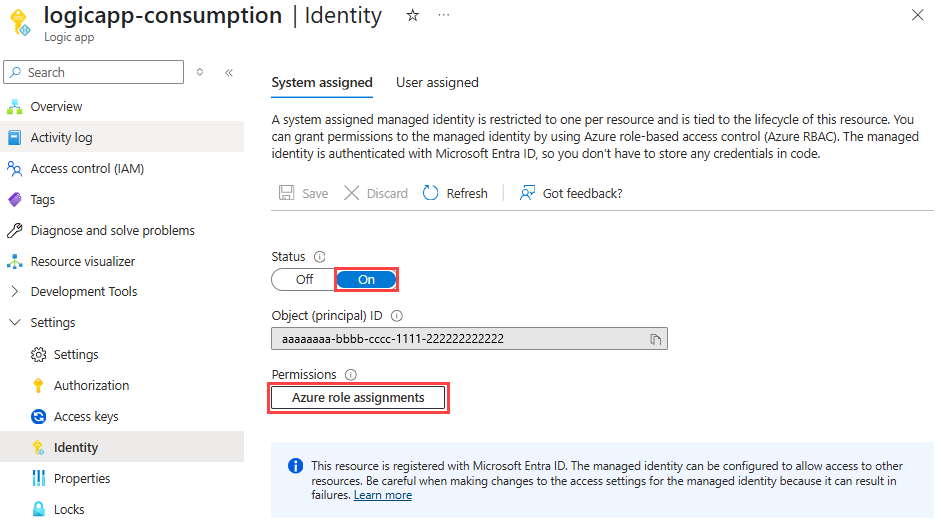
在逻辑应用资源导航菜单的“设置”下,选择“标识” 。
在“系统分配”窗格上,将“状态”设置为“开”,如果尚未启用,请选择“保存”,然后确认你的更改。 在“权限”下,选择“Azure 角色分配” 。
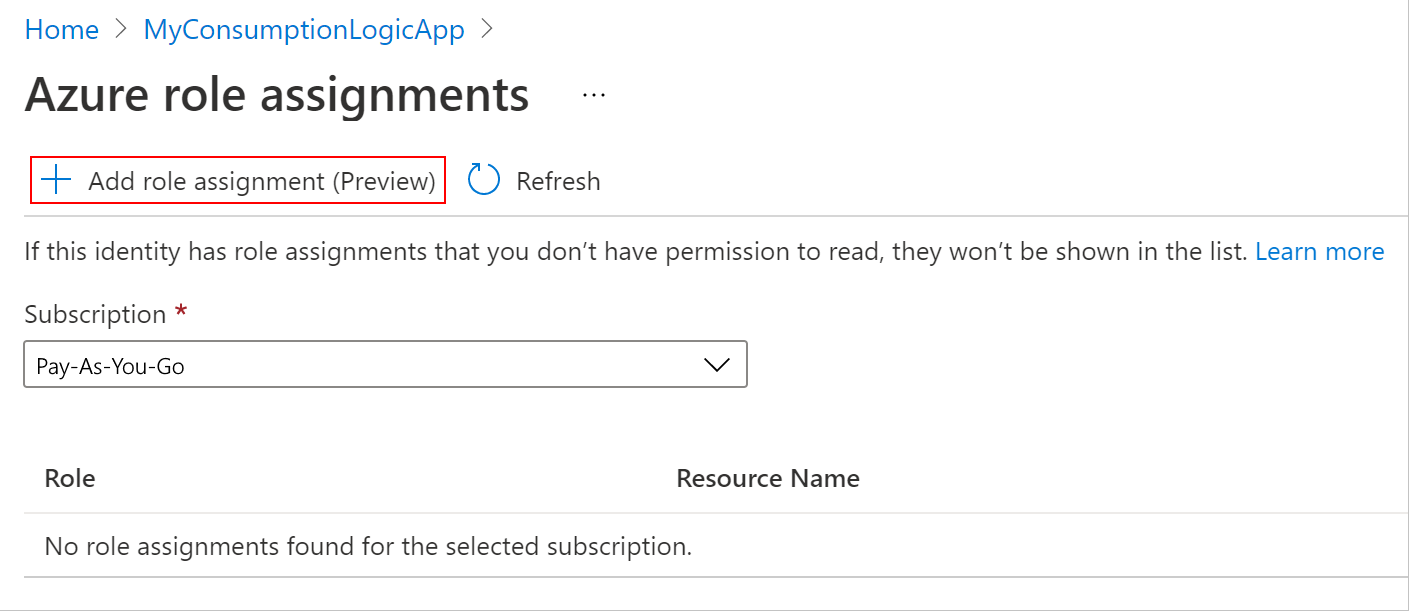
在“Azure 角色分配”窗格中,选择“添加角色分配” 。
在“添加角色分配”窗格上,使用以下值设置新的角色分配:
属性 值 说明 范围 <资源范围 要应用角色分配的资源集。 对于本示例,请选择“存储”。 订阅 <Azure 订阅 你的存储帐户的 Azure 订阅。 资源 <存储帐户名称 要从逻辑应用工作流访问的存储帐户的名称。 角色 <要分配的角色 要让工作流处理资源,方案所需要的角色。 此示例需要“存储 Blob 数据参与者”,该角色允许对 Blob 容器和日期的读取、写入和删除的权限。 将鼠标悬停在下拉菜单中某个角色旁边的信息图标上,即可获取详细的权限信息。 完成后,选择“保存”以完成角色分配的创建。
在逻辑应用上启用托管标识支持
然后,完成以下步骤:
如果具有空白工作流,请添加 Azure Blob 存储连接器触发器。 否则,添加 Azure Blob 存储连接器操作。 请确保为触发器或操作创建新的连接,而不是使用现有连接。
请确保将身份验证类型设置为使用托管标识。
配置触发器或操作后,可以保存工作流并测试触发器或操作。
排查访问存储帐户时遇到的问题
错误: 此请求无权执行此操作。
以下错误是逻辑应用和存储帐户位于同一区域时发生的常见问题。 但是,可以根据访问受防火墙保护的存储帐户部分所述,使用一些方法来解决此限制。
{ "status": 403, "message": "This request is not authorized to perform this operation.\\r\\nclientRequestId: a3da2269-7120-44b4-9fe5-ede7a9b0fbb8", "error": { "message": "This request is not authorized to perform this operation." }, "source": "azureblob-ase.azconn-ase.p.chinacloudsites.cn" }
Application Insights 错误
404 和 409 错误:
如果标准工作流使用将 blob 添加到存储容器的 Azure Blob 内置操作,则可能会在 Application Insights 中收到表示请求失败的 404 和 409 错误。 由于连接器在添加 blob 之前检查 blob 文件是否存在,因此这些错误在意料之中。 文件不存在时的错误结果。 尽管出现这些错误,但内置操作已成功添加 blob。