Azure 逻辑应用依赖于 Azure 存储 来存储和自动 加密静态数据。 此加密可保护数据,并帮助满足组织安全性和合规性承诺。 默认情况下,Azure 存储使用Microsoft管理的密钥来加密数据。 有关详细信息,请查看 Azure 存储静态数据的加密。
若要进一步控制 Azure 逻辑应用中的访问和保护敏感数据,可以在以下方面设置更多安全性:
- 对逻辑应用操作的访问
- 访问运行历史记录输入和输出
- 访问参数输入
- 支持身份验证的触发器和操作的身份验证类型
- 对基于请求的触发器的入站调用的访问
- 对其他服务和系统的出站调用的访问
- 阻止为特定连接器创建连接
- Azure 逻辑应用的 Azure 安全基线
有关 Azure 中安全性的详细信息,请查看以下主题:
访问逻辑应用操作
仅对于消耗逻辑应用,在创建或管理逻辑应用及其连接之前,需要使用 Azure 基于角色的访问控制(Azure RBAC)通过角色提供的特定权限。 还可以设置权限,以便只有特定用户或组才能运行特定任务,例如管理、编辑和查看逻辑应用。 若要控制其权限,可以将内置角色或自定义角色分配给有权访问 Azure 订阅的成员。 Azure 逻辑应用根据您拥有的是“消费型”还是“标准”逻辑应用工作流,具有以下特定角色:
消耗型工作流
| 角色 | Description |
|---|---|
| 逻辑应用参与者 | 可以管理逻辑应用工作流,但不能更改对其的访问权限。 |
| 逻辑应用操作员 | 可以读取、启用和禁用逻辑应用工作流,但无法编辑或更新它们。 |
| 贡献 | 可以完全访问管理所有资源,但不能在 Azure RBAC 中分配角色、管理 Azure 蓝图中的分配或共享映像库。 |
例如,假设您需要处理一个不是您创建的逻辑应用工作流,并且需要验证该逻辑应用工作流所使用的连接。 您的 Azure 订阅需要对包含该逻辑应用资源的资源组拥有 贡献者 权限。 如果创建逻辑应用资源,则会自动拥有参与者访问权限。
若要防止其他人更改或删除逻辑应用工作流,可以使用 Azure 资源锁。 此功能可防止其他人更改或删除生产资源。 有关连接安全性的详细信息,请查看 Azure 逻辑应用中的连接配置 以及 连接安全性和加密。
标准工作流
注释
此功能为预览版,受 Azure 预览版补充使用条款约束。
| 角色 | Description |
|---|---|
| 逻辑应用标准读取器(预览版) | 对标准型逻辑应用和工作流中的所有资源(包括工作流运行及其历史记录)具有只读访问权限。 |
| 逻辑应用标准运算符(预览版) | 有权启用、重新提交和禁用工作流,并为标准逻辑应用创建与服务、系统和网络的连接。 操作员角色可以在 Azure 逻辑应用平台上执行管理和支持任务,但无权编辑工作流或设置。 |
| 逻辑应用标准开发者(预览版) | 有权为标准逻辑应用创建和编辑工作流、连接和设置。 开发人员角色无权在工作流范围之外进行更改,例如,应用程序范围的更改,例如配置虚拟网络集成。 不支持应用服务计划。 |
| 逻辑应用标准贡献者(预览版) | 有权管理标准逻辑应用的各个方面,但不能更改访问权限或所有权。 |
访问运行历史记录数据
在逻辑应用运行期间,所有数据在传输期间通过使用传输层安全性 (TLS) 加密,并在静态时加密。 逻辑应用运行完成后,您可以查看此运行的历史记录,包括所执行步骤的状态、持续时间、输入和输出。 详细信息从中提供关于逻辑应用运行过程的见解,以及潜在问题的排查起始点。
查看逻辑应用的运行历史记录时,Azure 逻辑应用会验证访问权限,然后提供指向每个运行的请求和响应的输入和输出的链接。 但是,对于处理任何密码、机密、密钥或其他敏感信息的作,你想要阻止其他人查看和访问该数据。 例如,如果逻辑应用从 Azure Key Vault 获取机密,以便在对 HTTP作进行身份验证时使用,则希望从视图中隐藏该机密。
若要控制对逻辑应用的运行历史记录中的输入和输出的访问,可以使用以下选项:
-
此选项可帮助你根据来自特定 IP 地址范围的请求保护对运行历史记录的访问。
-
在许多逻辑应用的触发器和操作中,您可以在运行历史记录中保护输入、输出或两者。
按 IP 地址范围限制访问
可以限制对逻辑应用工作流的运行历史记录中的输入和输出的访问,以便只有来自特定 IP 地址范围的请求才能查看该数据。
例如,若要阻止任何人访问输入和输出,请指定 IP 地址范围,例如 0.0.0.0-0.0.0.0。 只有具有管理员权限的人员才能删除此限制,这样就有可能“实时”访问逻辑应用工作流中的数据。 有效的 IP 范围使用以下格式: x.x.x.x/x 或 x.x.x.x-x.x.x.
若要指定允许的 IP 范围,请在 Azure 门户或 Azure 资源管理器模板中为消耗或标准逻辑应用执行以下步骤:
消耗型工作流
在 Azure 门户中,在设计器中打开消耗逻辑应用工作流。
在逻辑应用菜单上的 “设置”下,选择 “工作流设置”。
在“ 访问控制配置 ”部分的 “允许入站 IP 地址”下,从 “触发器访问”选项 列表中选择 “特定 IP 范围”。
在 内容的 IP 范围 框中,指定可从输入和输出访问内容的 IP 地址范围。
标准工作流
在 Azure 门户中,打开你的标准逻辑应用资源。
在逻辑应用菜单上的 “设置”下,选择“ 网络”。
在 “入站流量配置” 部分的 “公用网络访问”旁边,选择“ 已启用”,且没有访问限制。
在 “访问限制 ”页上,在 “应用访问”下, 从选择虚拟网络和 IP 地址中选择“已启用”。
在“主站点”选项卡上的“站点访问和规则”下,将一个或多个规则添加到来自特定 IP 范围的“允许”或“拒绝”请求。 还可以使用 HTTP 标头筛选器设置和转发设置。 有效的 IP 范围使用以下格式: x.x.x.x/x 或 x.x.x.x-x.x.x.
有关详细信息,请参阅在 Azure Logic Apps(标准)中阻止入站 IP 地址。
使用模糊处理保护运行历史记录中的数据
许多触发器和操作都有设置来安全保护逻辑应用程序的运行历史中的输入、输出或两者。 所有 托管连接器 和 自定义连接器 都支持这些选项。 但是,以下 内置作不支持以下选项:
| 安全输入 - 不支持 | 安全输出 - 不支持 |
|---|---|
| 追加到数组变量 追加到字符串变量 递减变量 对于每个 如果 递增变量 初始化变量 复发 范围 设置变量 交换机 终止 截止 |
追加到数组变量 追加到字符串变量 撰写 递减变量 对于每个 如果 递增变量 初始化变量 解析 JSON 复发 响应 范围 设置变量 交换机 终止 直到 Wait |
保护输入和输出的注意事项
在使用这些设置来帮助保护此数据之前,请查看以下注意事项:
当您在触发器或操作上隐藏输入或输出时,Azure 逻辑应用不会将受保护的数据发送到 Azure Log Analytics。 此外,您无法在触发器或操作中添加跟踪的属性进行监视。
用于处理工作流历史记录的 Azure 逻辑应用 API 不会返回受保护的输出。
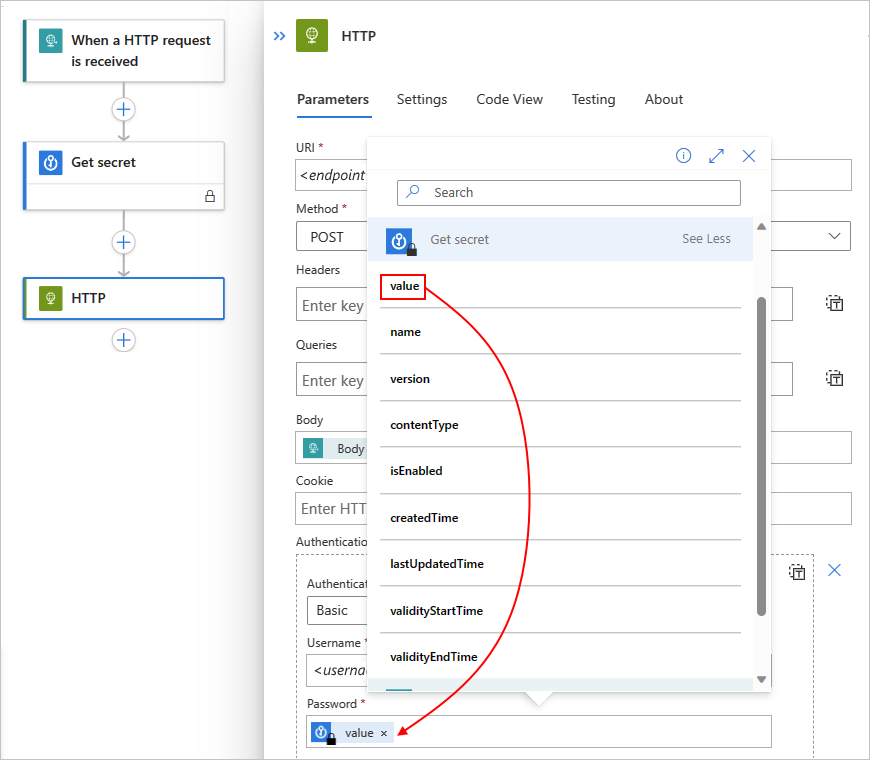
若要保护从一个操作中隐藏输入或显式隐藏输出的结果,请在该操作中手动打开安全输出。
请确保在下游作中启用 “安全输入 ”或“ 安全输出 ”,预期运行历史记录会掩盖该数据。
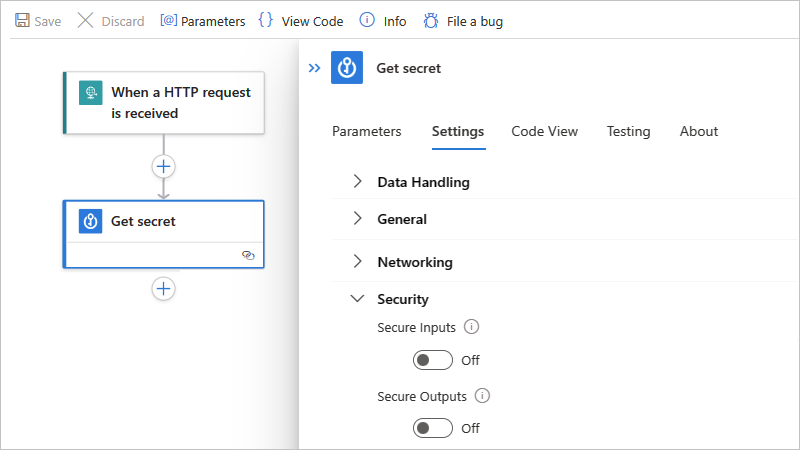
安全输出设置
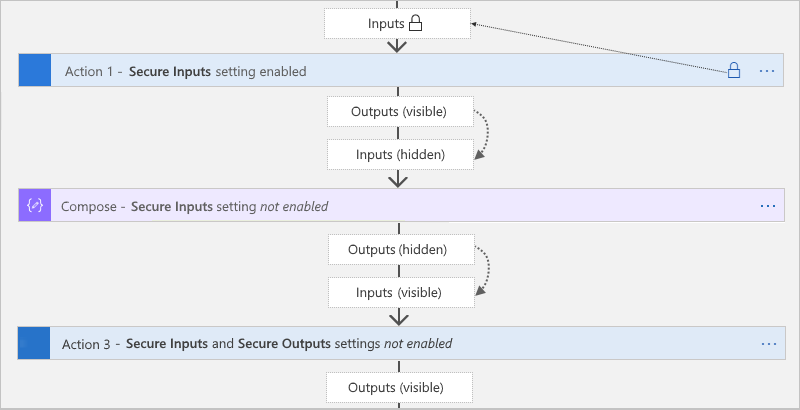
在触发器或作中手动打开 安全输出 时,Azure 逻辑应用在运行历史记录中隐藏这些输出。 如果下游动作显式使用这些安全输出作为输入,Azure 逻辑应用将在运行历史记录中隐藏此动作的输入,但不会启用该动作的安全输入设置。
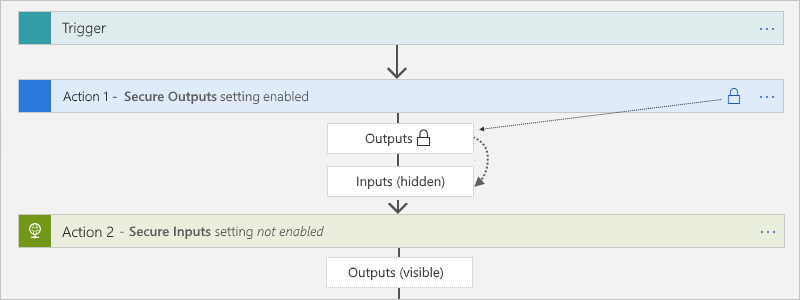
Compose、Parse JSON 和 Response 操作仅具有 安全输入 设置。 打开后,该设置还会隐藏这些操作的输出。 如果这些操作显式使用上游安全输出作为输入,Azure 逻辑应用会隐藏这些操作的输入和输出,但不启用这些操作的安全输入设置。 如果下游作显式使用 Compose、Parse JSON 或响应作的隐藏输出作为输入,Azure 逻辑应用 不会隐藏此下游作的输入或输出。
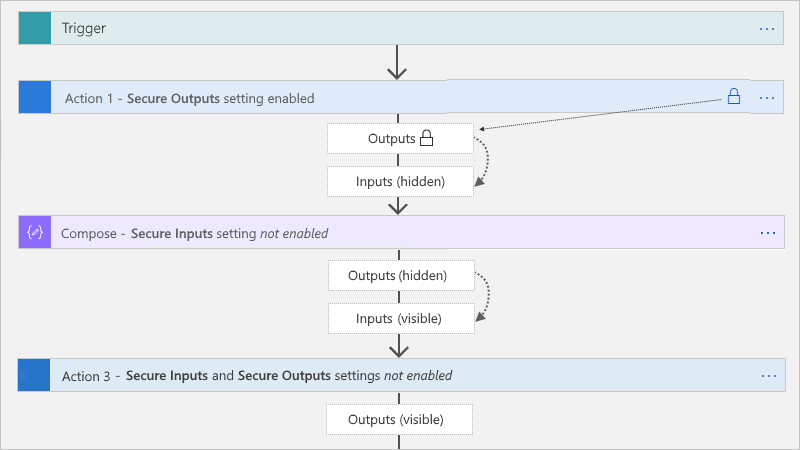
安全输入设置
在触发器或作中手动打开 安全输入 时,Azure 逻辑应用在运行历史记录中隐藏这些输入。 如果下游作显式使用该触发器或作的可见输出作为输入,Azure 逻辑应用会将此下游作的输入隐藏在运行历史记录中,但不在此作中 启用安全输入 ,并且不隐藏此作的输出。
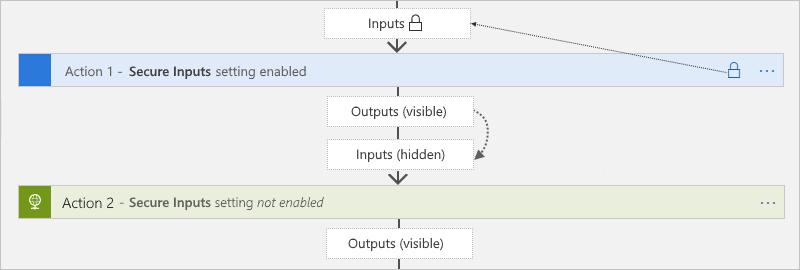
如果 Compose、Parse JSON 和 Response 操作显式使用触发器或者具有安全输入的操作的可见输出,则 Azure 逻辑应用会隐藏这些操作的输入和输出,但 未启用 这些操作的 安全输入 设置。 如果下游作显式使用 Compose、Parse JSON 或响应作的隐藏输出作为输入,Azure 逻辑应用 不会隐藏此下游作的输入或输出。
保护设计器中的输入和输出
在 Azure 门户中,打开设计器的逻辑应用工作流。
在设计器中,选择要保护敏感数据的触发器或操作。
在打开的信息窗格中,选择“ 设置”,然后展开“ 安全性”。
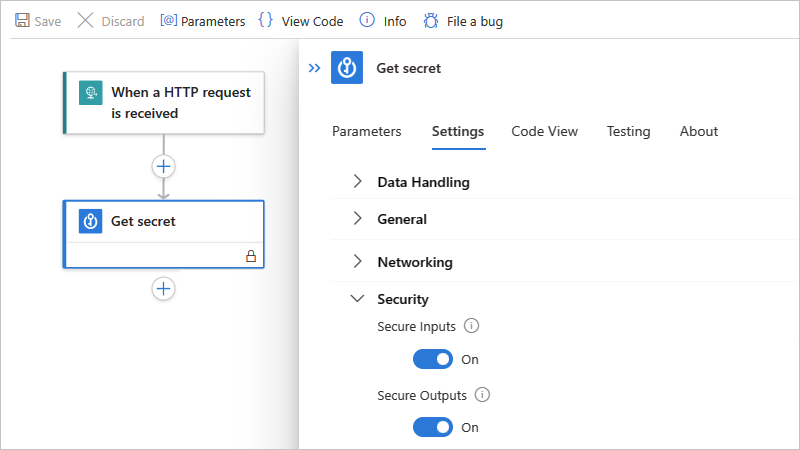
打开 安全输入、 安全输出或两者兼有。
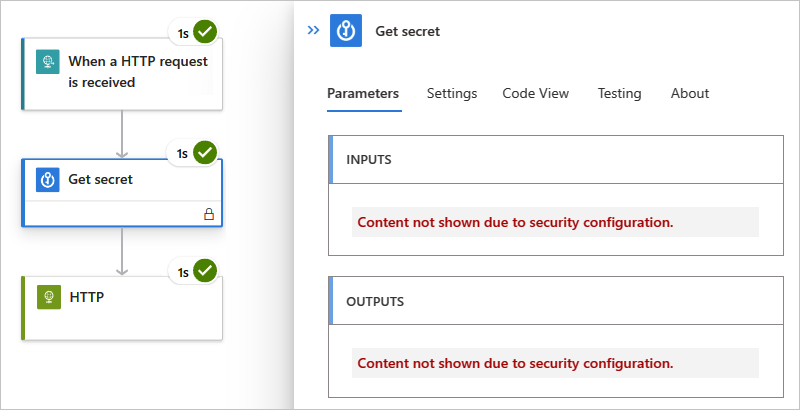
触发器或动作现在会在标题栏中显示锁图标。 任何代表先前操作中安全输出的令牌也显示锁定图标。 例如,在后续作中,在从动态内容列表中选择安全输出的令牌后,该令牌会显示锁定图标。
工作流运行后,可以查看该运行的历史记录。
在代码视图中保护输入和输出
在基础触发器或作定义中,使用以下值之一或两者添加或更新 runtimeConfiguration.secureData.properties 数组:
-
"inputs":保护运行历史记录中的输入。 -
"outputs":保护运行历史记录中的输出。
"<trigger-or-action-name>": {
"type": "<trigger-or-action-type>",
"inputs": {
<trigger-or-action-inputs>
},
"runtimeConfiguration": {
"secureData": {
"properties": [
"inputs",
"outputs"
]
}
},
<other-attributes>
}
访问参数输入
如果跨不同的环境进行部署,请考虑参数化工作流定义中因这些环境而异的值。 这样,可以通过使用 Azure 资源管理器模板部署逻辑应用、通过定义安全参数来保护敏感数据,以及通过使用参数文件将这些数据作为单独的输入传递,从而避免硬编码的数据。
例如,如果使用 Microsoft Entra ID 通过 OAuth 对 HTTP作进行身份验证,则可以定义并掩盖接受用于身份验证的客户端 ID 和客户端密码的参数。 若要在逻辑应用工作流中定义这些参数,请使用 parameters 逻辑应用的工作流定义和资源管理器模板中的部分进行部署。 为了帮助保护编辑逻辑应用或查看运行历史记录时不希望显示的参数值,请使用 securestring 或 secureobject 类型定义参数,并根据需要使用编码。 具有此类型的参数不会随资源定义一起返回,在部署后查看资源时无法访问。 若要在运行时访问这些参数值,请使用 @parameters('<parameter-name>') 工作流定义中的表达式。 此表达式仅在运行时计算,并由 工作流定义语言描述。
注释
如果在请求标头或正文中使用参数,则查看工作流的运行历史记录和传出 HTTP 请求时,该参数可能可见。 请确保还相应地设置内容访问策略。 还可以使用 模糊处理 来隐藏运行历史记录中的输入和输出。
默认情况下, Authorization 标头不通过输入或输出可见。
因此,如果在那里使用了机密,则无法检索该机密。
有关详细信息,请查看本主题中的以下部分:
如果使用资源管理器模板自动部署逻辑应用,则可以使用和securestring类型定义在部署时评估的安全secureobject。 若要定义模板参数,请使用模板的顶级 parameters 部分,该部分与工作流定义的 parameters 部分不同。 若要提供模板参数的值,请使用单独的 参数文件。
例如,如果使用机密,则可以定义和使用在部署时从 Azure Key Vault 检索这些机密的安全模板参数。 然后,可以在参数文件中引用密钥保管库和机密。 有关详细信息,请查看以下主题:
保护工作流定义中的参数 (消耗工作流)
若要保护逻辑应用的工作流定义中的敏感信息,请使用受保护的参数,以便在保存逻辑应用工作流后此信息不可见。 例如,假设你有一个 HTTP作需要基本身份验证,该身份验证使用用户名和密码。 在工作流定义中,该parameters节使用basicAuthPasswordParam类型定义basicAuthUsernameParam和securestring参数。 然后,操作定义在 authentication 节中引用这些参数。
重要
为了获得最佳安全性,Microsoft建议尽可能将 Microsoft Entra ID 与 托管标识 配合使用进行身份验证。 此选项提供卓越的安全性,而无需提供凭据。 Azure 负责管理此标识并帮助保护身份验证信息的安全,这样你就无需管理这种敏感信息了。 若要为 Azure 逻辑应用设置托管标识,请参阅在 Azure 逻辑应用中使用托管标识对 Azure 资源的访问和连接进行身份验证。
"definition": {
"$schema": "https://schema.management.azure.com/providers/Microsoft.Logic/schemas/2016-06-01/workflowdefinition.json#",
"actions": {
"HTTP": {
"type": "Http",
"inputs": {
"method": "GET",
"uri": "https://www.microsoft.com",
"authentication": {
"type": "Basic",
"username": "@parameters('basicAuthUsernameParam')",
"password": "@parameters('basicAuthPasswordParam')"
}
},
"runAfter": {}
}
},
"parameters": {
"basicAuthPasswordParam": {
"type": "securestring"
},
"basicAuthUsernameParam": {
"type": "securestring"
}
},
"triggers": {
"manual": {
"type": "Request",
"kind": "Http",
"inputs": {
"schema": {}
}
}
},
"contentVersion": "1.0.0.0",
"outputs": {}
}
保护 Azure 资源管理器模板中的参数(消耗工作流)
逻辑应用资源和工作流的 资源管理器模板 具有多个 parameters 部分。 若要保护密码、密钥、机密和其他敏感信息,请使用 securestring 或 secureobject 类型在模板级别和工作流定义级别定义安全参数。 然后,可以将这些值存储在 Azure Key Vault 中,并使用 参数文件 引用密钥保管库和机密。 然后,模板会在部署时检索该信息。 有关详细信息,请参阅 使用 Azure Key Vault 在部署时传递敏感值。
重要
为了获得最佳安全性,Microsoft建议尽可能将 Microsoft Entra ID 与 托管标识 配合使用进行身份验证。 此选项提供卓越的安全性,而无需提供凭据。 Azure 负责管理此标识并帮助保护身份验证信息的安全,这样你就无需管理这种敏感信息了。 若要为 Azure 逻辑应用设置托管标识,请参阅在 Azure 逻辑应用中使用托管标识对 Azure 资源的访问和连接进行身份验证。
此列表包含有关以下 parameters 部分的详细信息:
在模板的顶层,
parameters节定义了模板在 部署时使用的值参数。 例如,这些值可以包括特定部署环境的连接字符串。 然后,可以将这些值存储在单独的 参数文件中,这使得更改这些值更容易。在逻辑应用的资源定义中,但位于工作流定义外,
parameters节指明工作流定义参数的值。 在本部分中,可以使用引用模板参数的模板表达式来分配这些值。 这些表达式在部署时计算。在工作流定义中,一个
parameters部分定义逻辑应用工作流在运行时使用的参数。 然后,可以使用在运行时计算的工作流定义表达式,在逻辑应用的工作流中引用这些参数。
此示例模板,其中包含使用该 securestring 类型的多个安全参数定义:
| 参数名称 | Description |
|---|---|
TemplatePasswordParam |
一个模板参数,它接受随后传递给工作流定义 basicAuthPasswordParam 参数的密码 |
TemplateUsernameParam |
接受用户名并将其传递给工作流定义的basicAuthUserNameParam参数的模板参数 |
basicAuthPasswordParam |
一个接受在 HTTP 操作中用于基本身份验证的密码的工作流定义参数。 |
basicAuthUserNameParam |
工作流定义参数,用于接受 HTTP 操作中进行基本身份验证的用户名 |
{
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"LogicAppName": {
"type": "string",
"minLength": 1,
"maxLength": 80,
"metadata": {
"description": "Name of the Logic App."
}
},
"TemplatePasswordParam": {
"type": "securestring"
},
"TemplateUsernameParam": {
"type": "securestring"
},
"LogicAppLocation": {
"type": "string",
"defaultValue": "[resourceGroup().location]",
"allowedValues": [
"[resourceGroup().location]",
"chinaeast",
"chinanorth",
"chinaeast2",
"chinanorth2",
"chinanorth3"
],
"metadata": {
"description": "Location of the Logic App."
}
}
},
"variables": {},
"resources": [
{
"name": "[parameters('LogicAppName')]",
"type": "Microsoft.Logic/workflows",
"location": "[parameters('LogicAppLocation')]",
"tags": {
"displayName": "LogicApp"
},
"apiVersion": "2016-06-01",
"properties": {
"definition": {
"$schema": "https://schema.management.azure.com/providers/Microsoft.Logic/schemas/2016-06-01/workflowdefinition.json#",
"actions": {
"HTTP": {
"type": "Http",
"inputs": {
"method": "GET",
"uri": "https://www.microsoft.com",
"authentication": {
"type": "Basic",
"username": "@parameters('basicAuthUsernameParam')",
"password": "@parameters('basicAuthPasswordParam')"
}
},
"runAfter": {}
}
},
"parameters": {
"basicAuthPasswordParam": {
"type": "securestring"
},
"basicAuthUsernameParam": {
"type": "securestring"
}
},
"triggers": {
"manual": {
"type": "Request",
"kind": "Http",
"inputs": {
"schema": {}
}
}
},
"contentVersion": "1.0.0.0",
"outputs": {}
},
"parameters": {
"basicAuthPasswordParam": {
"value": "[parameters('TemplatePasswordParam')]"
},
"basicAuthUsernameParam": {
"value": "[parameters('TemplateUsernameParam')]"
}
}
}
}
],
"outputs": {}
}
支持身份验证的连接器的身份验证类型
下表标识连接器作上可用的身份验证类型,可在其中选择身份验证类型:
| 身份验证类型 | 逻辑应用程序及其支持的连接器 |
|---|---|
| 基本 | Azure API 管理、Azure 应用服务、HTTP、HTTP + Swagger、HTTP Webhook |
| 客户端证书 | Azure API 管理、Azure 应用服务、HTTP、HTTP + Swagger、HTTP Webhook |
| Active Directory OAuth (具有 Microsoft Entra ID 的 OAuth 2.0) |
-
消耗:Azure API 管理、Azure 应用服务、Azure Functions、HTTP、HTTP + Swagger、HTTP Webhook - 标准:Azure 自动化、Azure Blob 存储、Azure 事件中心、Azure 队列、Azure 服务总线、Azure 表、HTTP、HTTP Webhook、SQL Server |
| 原始 | Azure API 管理、Azure 应用服务、Azure Functions、HTTP、HTTP + Swagger、HTTP Webhook |
| 托管标识 |
内置连接器: - 消耗:Azure API 管理、Azure 应用服务、Azure Functions、HTTP、HTTP Webhook - 标准:Azure 自动化、Azure Blob 存储、Azure 事件中心、Azure 队列、Azure 服务总线、Azure 表、HTTP、HTTP Webhook、SQL Server 注意:目前,大多数基于 服务提供商的内置连接器 不支持选择用户分配的托管标识进行身份验证。 托管连接器:Azure 应用服务、Azure 自动化、Azure Blob 存储、Azure 容器实例、Azure Cosmos DB、Azure 数据资源管理器、Azure 数据工厂、Azure 数据湖、Azure 事件网格、Azure 事件中心、Azure IoT Central V2、Azure IoT Central V3、Azure Key Vault、Azure Log Analytics、Azure 队列、Azure 资源管理器、Azure 服务总线、Azure Sentinel、Azure 表存储、Azure 虚拟机、使用 Microsoft Entra ID 的 HTTP、SQL Server |
重要
为了获得最佳安全性,Microsoft建议尽可能将 Microsoft Entra ID 与 托管标识 配合使用进行身份验证。 此选项提供卓越的安全性,而无需提供凭据。 Azure 负责管理此标识并帮助保护身份验证信息的安全,这样你就无需管理这种敏感信息了。 若要为 Azure 逻辑应用设置托管标识,请参阅在 Azure 逻辑应用中使用托管标识对 Azure 资源的访问和连接进行身份验证。
对请求触发器的入站呼叫访问权限
逻辑应用通过基于请求的触发器(例如 请求 触发器 或 HTTP Webhook 触发器)接收的入站调用支持加密,并且 至少受传输层安全性 (TLS) 1.2 保护,以前称为安全套接字层 (SSL)。 Azure 逻辑应用在收到对 请求 触发器的入站调用或对 HTTP Webhook 触发器或操作的回调时,会强制执行此版本。
对于入站调用,请使用以下密码套件:
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
重要
为了向后兼容,Azure 逻辑应用目前支持一些较旧的密码套件。 但是,开发新应用时 不要使用 较旧的密码套件,因为将来 可能不支持 此类套件。
例如,如果检查 Azure 逻辑应用中的 TLS 握手消息,或者通过在逻辑应用的 URL 上使用安全工具来检查 TLS 握手消息,则可能会找到以下密码套件。 同样, 不要使用这些 较旧的套件:
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
- TLS_RSA_WITH_AES_256_GCM_SHA384
- TLS_RSA_WITH_AES_128_GCM_SHA256
- TLS_RSA_WITH_AES_256_CBC_SHA256
- TLS_RSA_WITH_AES_128_CBC_SHA256
- TLS_RSA_WITH_AES_256_CBC_SHA
- TLS_RSA_WITH_AES_128_CBC_SHA
- TLS_RSA_WITH_3DES_EDE_CBC_SHA
以下列表包括限制对接收逻辑应用工作流入站调用的触发器的访问方式,以便只有经过授权的客户端才能调用工作流:
- 使用 Microsoft Entra ID 启用 OAuth
- 生成共享访问签名(SAS)密钥或令牌
- 禁用共享访问签名 (SAS) 身份验证
- 限制入站 IP 地址
- 使用 Azure API 管理公开逻辑应用
使用 Microsoft Entra ID 启用 OAuth 2.0
在以基于请求的触发器开头的消耗工作流中,可以通过启用 具有 Microsoft Entra ID 的 OAuth 2.0,对发送到该触发器创建的终结点的入站调用进行身份验证和授权。 若要设置此身份验证,请在 逻辑应用资源级别定义或添加授权策略。 这样,入站调用将使用 OAuth 访问令牌 进行授权。
当逻辑应用工作流收到包含 OAuth 访问令牌的入站请求时,Azure 逻辑应用会将令牌的声明与每个授权策略指定的声明进行比较。 如果令牌的声明与至少一个策略中的所有声明之间存在匹配项,则入站请求的授权会成功。 令牌的声明数可能多于授权策略指定的数目。
在以 请求 触发器(但不是 Webhook 触发器)开头的标准工作流中,可以使用 Azure Functions 预配通过托管标识对发送到 请求 触发器创建的终结点的入站调用进行身份验证。 此预配也称为“简易身份验证”。 有关详细信息,请参阅 使用 Easy Auth 的标准逻辑应用中触发工作流。
使用 Microsoft Entra ID 启用 OAuth 2.0 之前的注意事项
为了获得最佳安全性,Microsoft建议尽可能将 Microsoft Entra ID 与 托管标识 配合使用进行身份验证。 此选项提供卓越的安全性,而无需提供凭据。 Azure 负责管理此标识并帮助保护身份验证信息的安全,这样你就无需管理这种敏感信息了。 若要为 Azure 逻辑应用设置托管标识,请参阅在 Azure 逻辑应用中使用托管标识对 Azure 资源的访问和连接进行身份验证。
在消耗工作流中,对基于请求的触发器的终结点 URL 的入站调用只能使用一种授权方案,即要么使用 Microsoft Entra ID 的 OAuth 2.0,或者共享访问签名(SAS)。 尽管使用一个方案不会禁用另一个方案,但如果同时使用这两种方案,Azure 逻辑应用会生成错误,因为服务不知道要选择哪个方案。 如果你的 Consumption 工作流以 请求 触发器开头,则可以 禁用 SAS 身份验证,并 限制授权仅限使用 Microsoft Entra ID 的 OAuth 2.0。 对于标准工作流,无需禁用 SAS 即可使用其他身份验证类型。
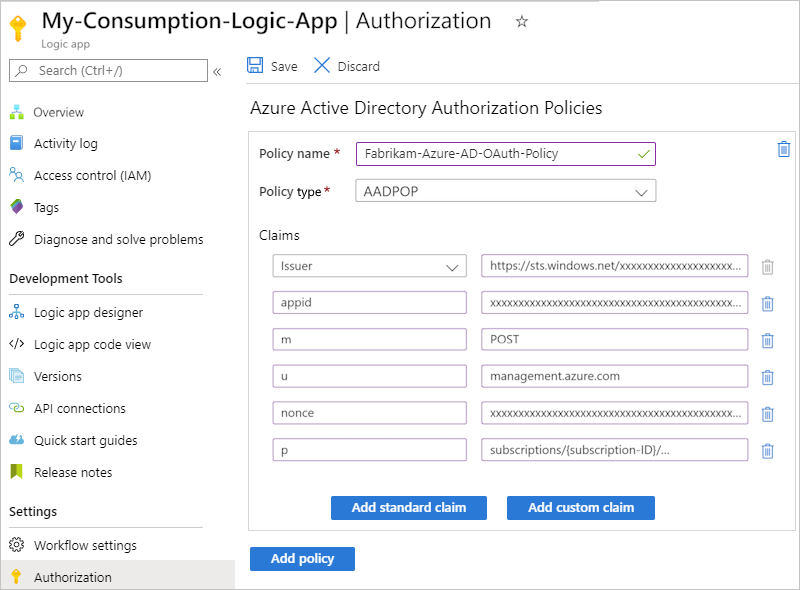
Azure 逻辑应用支持Microsoft Entra ID OAuth 访问令牌的 持有者类型 或 所有权证明类型(仅限消耗逻辑应用) 授权方案。 但是,
Authorization访问令牌的标头必须指定Bearer类型或PoP类型。 有关如何获取和使用 PoP 令牌的详细信息,请参阅 获取所有权证明(PoP)令牌。您的 Consumption 逻辑应用资源的授权策略数量受到限制,达到最大值。 每个授权策略也具有最大 数量的声明。 有关详细信息,请参阅 Azure 逻辑应用的限制和配置。
授权策略必须至少包含 颁发者 声明,该声明的值应以
https://sts.chinacloudapi.cn/或https://login.chinacloudapi.cn/(OAuth V2)开头,这是 Microsoft Entra ID 的颁发者。例如,假设逻辑应用资源具有一个授权策略,该策略需要两种声明类型: 受众 和 颁发者。 解码访问令牌的这个示例有效负载部分包括两种声明类型:
aud受众值和iss颁发者值。{ "aud": "https://management.core.chinacloudapi.cn/", "iss": "https://sts.chinacloudapi.cn/<Azure-AD-issuer-ID>/", "iat": 1582056988, "nbf": 1582056988, "exp": 1582060888, "_claim_names": { "groups": "src1" }, "_claim_sources": { "src1": { "endpoint": "https://graph.chinacloudapi.cn/7200000-86f1-41af-91ab-2d7cd011db47/users/00000-f433-403e-b3aa-7d8406464625d7/getMemberObjects" } }, "acr": "1", "aio": "AVQAq/8OAAAA7k1O1C2fRfeG604U9e6EzYcy52wb65Cx2OkaHIqDOkuyyr0IBa/YuaImaydaf/twVaeW/etbzzlKFNI4Q=", "amr": [ "rsa", "mfa" ], "appid": "c44b4083-3bb0-00001-b47d-97400853cbdf3c", "appidacr": "2", "deviceid": "bfk817a1-3d981-4dddf82-8ade-2bddd2f5f8172ab", "family_name": "Sophia Owen", "given_name": "Sophia Owen (Fabrikam)", "ipaddr": "167.220.2.46", "name": "sophiaowen", "oid": "3d5053d9-f433-00000e-b3aa-7d84041625d7", "onprem_sid": "S-1-5-21-2497521184-1604012920-1887927527-21913475", "puid": "1003000000098FE48CE", "scp": "user_impersonation", "sub": "KGlhIodTx3XCVIWjJarRfJbsLX9JcdYYWDPkufGVij7_7k", "tid": "aaaabbbb-0000-cccc-1111-dddd2222eeee", "unique_name": "SophiaOwen@fabrikam.com", "upn": "SophiaOwen@fabrikam.com", "uti": "TPJ7nNNMMZkOSx6_uVczUAA", "ver": "1.0" }
使用 Microsoft Entra ID 启用 OAuth 2.0 作为调用请求终结点的唯一选项(仅限消费计划)
对于基于请求的终结点,可以将授权限制为仅将 OAuth 2.0 与 Microsoft Entra ID 一起使用。 即使还 禁用共享访问签名(SAS)身份验证,此选项也能正常工作。
对于消耗工作流,请按照步骤将 请求 触发器或 HTTP Webhook 触发器设置为具有检查 OAuth 访问令牌的功能, 以便在请求或 HTTP Webhook 触发器输出中包含“授权”标头。
注释
此步骤使
Authorization标头在工作流的运行历史记录和触发器的输出中可见。在 Azure 门户中,打开设计器中的消耗工作流。
在设计器上,选择触发器。 在打开的信息窗格中,选择 “设置”。
在 “常规>触发器”条件下,选择“ 添加”。 在触发器条件框中,根据要使用的令牌类型输入以下任一表达式:
@startsWith(triggerOutputs()?['headers']?['Authorization'], 'Bearer')-或-
@startsWith(triggerOutputs()?['headers']?['Authorization'], 'PoP')
如果在没有正确授权的情况下调用触发器终结点,则运行历史记录只会象征性地显示触发器 Skipped,而没有任何消息表明触发条件已失败。
获取所有权证明(PoP)令牌
Microsoft身份验证库(MSAL)库提供 PoP 令牌供你使用。 如果要调用的消耗逻辑应用工作流需要 PoP 令牌,则可以使用 MSAL 库获取此令牌。 以下示例演示如何获取 PoP 令牌:
若要将 PoP 令牌用于您的消耗逻辑应用工作流,请按照以下步骤,使用 Microsoft Entra ID 设置 OAuth。
为您的消费逻辑应用资源启用 Microsoft Entra ID 的 OAuth
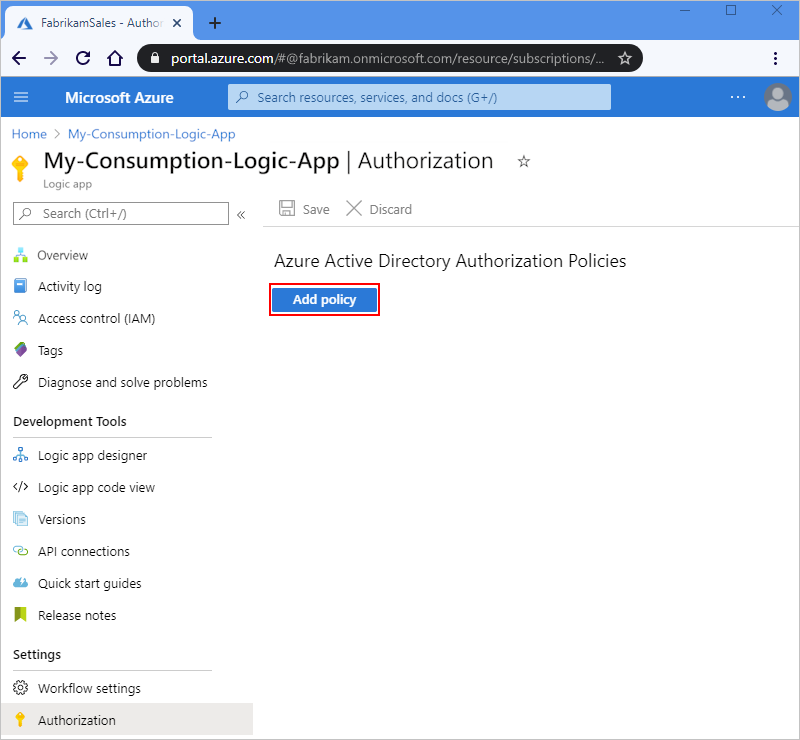
若要将授权策略添加到消耗逻辑应用,请遵循 Azure 门户或 Azure 资源管理器模板的步骤:
在 Azure 门户中,在设计器中打开您的消费型逻辑应用和工作流。
在逻辑应用菜单上的 “设置”下,选择“ 授权”。
在 “授权 ”页上,选择“ 添加策略”。
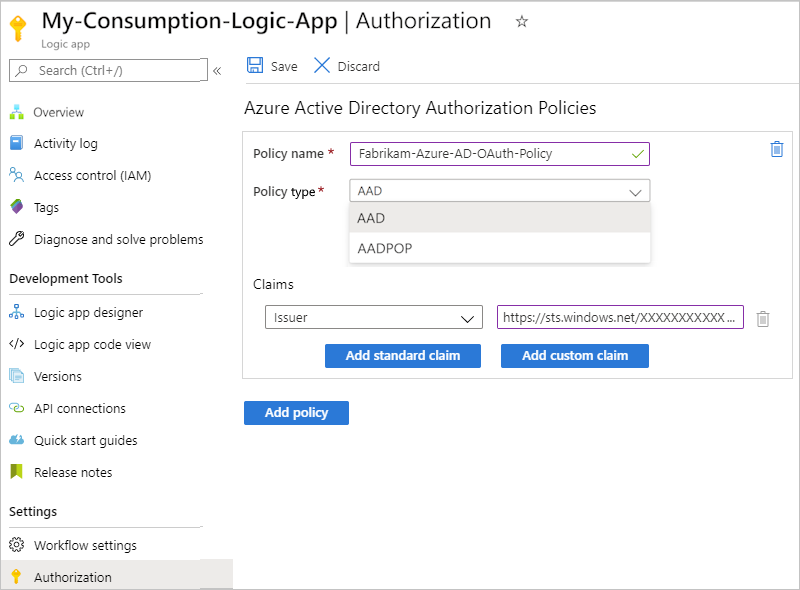
通过指定逻辑应用在对请求触发器的每个入站调用提供的访问令牌中预期的声明类型和值来提供有关授权策略的信息:
资产 必选 类型 Description 策略名称 是的 String 要用于授权策略的名称 策略类型 是的 String 持有者类型令牌的 AAD 或所有权证明类型令牌的 AADPOP 。 Claims 是的 String 一个键值对,指定工作流的请求触发器在对触发器的每个入站调用提供的访问令牌中预期的声明类型和值。 可以通过选择“ 添加标准声明”来添加所需的任何标准声明。 若要添加特定于 PoP 令牌的声明,请选择 “添加自定义声明”。
可用的标准声明类型:
- 发行人
- 观众
- 主题
- JWT ID (JSON Web 令牌标识符)
要求:
- 至少,声明列表必须包含颁发者声明,该声明的值必须以https://sts.chinacloudapi.cn/或https://login.chinacloudapi.cn/作为开头,这是 Microsoft Entra 颁发者 ID。
- 每个声明必须是单个字符串值,而不是值数组。 例如,您可以拥有一个声明,其类型为Role,值为Developer。 不能有一个声明,其类型为 角色,且值设置为 开发人员 和 项目经理。
- 声明值限制为 最大字符数。
有关这些声明类型的详细信息,请查看 Microsoft Entra 安全令牌中的声明。 还可以指定自己的声明类型和值。以下示例显示了 PoP 令牌的信息:
若要添加另一个声明,请从以下选项中进行选择:
若要添加其他声明类型,请选择 “添加标准声明”,选择声明类型,并指定声明值。
若要添加自己的声明,请选择 “添加自定义声明”。 有关详细信息,请查看 如何向应用提供可选声明。 然后,自定义声明作为 JWT ID 的一部分存储;例如,
"tid": "aaaabbbb-0000-cccc-1111-dddd2222eeee".
若要添加另一个授权策略,请选择 “添加策略”。 重复前面的步骤以设置策略。
完成后,选择“保存”。
若要在请求触发器输出中包含来自访问令牌的标头,请查看在请求和 HTTP Webhook 触发器输出中包含“Authorization”标头。
工作流属性(如策略)不会显示在 Azure 门户中工作流的代码视图中。 若要以编程方式访问策略,请通过 Azure 资源管理器调用以下 API: https://management.chinacloudapi.cn/subscriptions/{Azure-subscription-ID}/resourceGroups/{Azure-resource-group-name}/providers/Microsoft.Logic/workflows/{your-workflow-name}?api-version=2016-10-01&_=1612212851820 请确保替换 Azure 订阅 ID、资源组名称和工作流名称的占位符值。
在请求或 HTTP Webhook 触发器输出中包含“Authorization”标头
对于 使用 Microsoft Entra ID 启用 OAuth 的逻辑应用,为了授权入站调用获取基于请求的触发器,可以启用 请求 触发器或 HTTP Webhook 触发器的输出,以包括从 OAuth 访问令牌中获取的 Authorization 标头。 在触发器的基础 JSON 定义中,添加属性并将其设置为 operationOptionsIncludeAuthorizationHeadersInOutputs。 下面是 请求 触发器的示例:
"triggers": {
"manual": {
"inputs": {
"schema": {}
},
"kind": "Http",
"type": "Request",
"operationOptions": "IncludeAuthorizationHeadersInOutputs"
}
}
有关详细信息,请查看以下主题:
生成共享访问签名(SAS)密钥或令牌
当工作流以基于请求的触发器开头,并且首次保存该工作流时,Azure 逻辑应用在该触发器上创建可调用的终结点。 此终结点具有可以接收入站调用或启动工作流的请求的 URL。 URL 包括 共享访问签名(SAS),这是授予存储服务权限的密钥或令牌。 此终结点 URL 使用以下格式:
https://<request-endpoint-URI>sp=<permissions>sv=<SAS-version>sig=<signature>
例如,若要在 请求 触发器中查看此 URL,请查找触发器的 HTTP URL 属性:
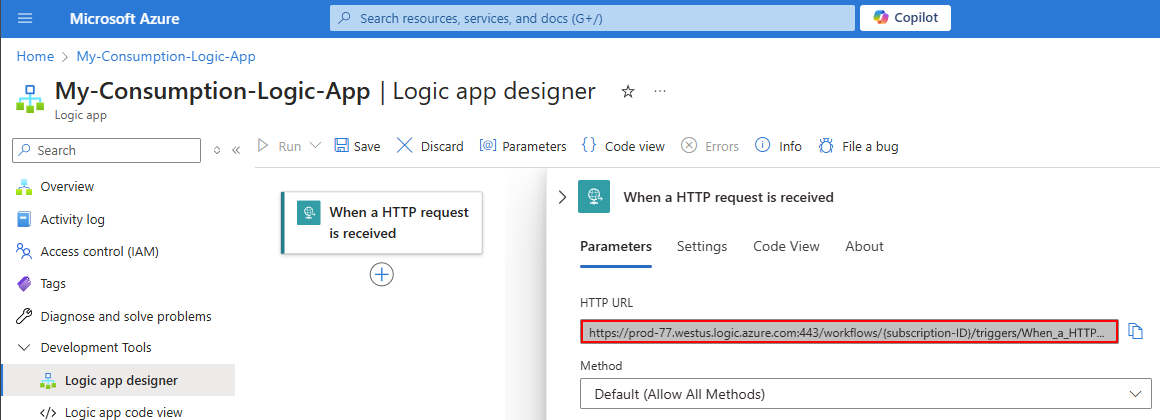
完整的 URL 如以下示例所示:
https://{domain}:443/workflows/XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX/triggers/When_a_HTTP_request_is_received/paths/invoke?api-version=2016-10-01&sp=%2Ftriggers%2FWhen_a_HTTP_request_is_received%2Frun&sv=1.0&sig=ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ
URL 中的 SAS 具有查询参数,下表描述了这些参数:
| 查询参数 | Description |
|---|---|
sp |
指定允许使用的 HTTP 方法的权限。 |
sv |
指定要用于生成签名的 SAS 版本。 |
sig |
指定要用于对触发器的访问进行身份验证的签名。 此签名是使用 SHA256 算法在所有 URL 路径和属性上使用机密访问密钥生成的。 此密钥保持机密和加密,与逻辑应用一起存储,永远不会公开或发布。 逻辑应用仅授权包含使用密钥创建的有效签名的触发器。 |
重要
请确保保护 SAS 密钥,就像保护帐户密钥免受未经授权的使用一样。 设置或具有撤消已泄露访问密钥的计划。 在分发使用访问密钥的 URI 时,使用自由裁量权,并且仅通过安全连接(如 HTTPS)分发此类 URI。 请确保仅在 HTTPS 连接上执行使用访问密钥的操作。 具有有效密钥的 URI 的任何人都可以访问关联的资源。 若要维护安全性和保护对逻辑应用工作流的访问,请定期 重新生成访问密钥 ,因为它们可能需要遵守安全策略或遭到入侵。 这样,就可以确保只有授权的请求才能触发工作流,从而防止数据和进程受到未经授权的访问。
如果使用 SAS 密钥访问存储服务,Microsoft建议 创建用户委派 SAS,该 SAS 使用 Microsoft Entra ID 进行保护,而不是帐户密钥。
为了获得最佳安全性,Microsoft建议尽可能将 Microsoft Entra ID 与 托管标识 一起使用进行身份验证。 此选项提供卓越的安全性,而无需提供凭据。 Azure 负责管理此标识并帮助保护身份验证信息的安全,这样你就无需管理这种敏感信息了。 若要为 Azure 逻辑应用设置托管标识,请参阅在 Azure 逻辑应用中使用托管标识对 Azure 资源的访问和连接进行身份验证。
对基于请求的触发器上的终结点的入站调用只能使用一个授权方案,即 SAS 或 具有 Microsoft Entra ID 的 OAuth 2.0。 尽管使用一个方案不会禁用另一种方案,但如果同时使用这两种方案,Azure 逻辑应用会生成错误,因为该服务不知道要选择哪个方案。
如果有一个以 请求 触发器开头的消耗工作流,则可以 禁用 SAS 身份验证。 即使您已将授权限制为仅使用具有 Microsoft Entra ID 的 OAuth 2.0,该选项也能正常工作。 对于标准工作流,无需禁用 SAS 即可使用其他身份验证类型。
有关使用 SAS 密钥时的安全性的详细信息,请参阅本指南中的以下部分:
禁用共享访问签名 (SAS) 身份验证(仅限消耗型)
默认情况下,基于请求的触发器已启用 SAS 身份验证。 触发器的终结点 URL 包括一个 SAS,从查询参数开始, sp-<permissions>sv-<SAS-version>sig=<signature>例如:
https://{domain}:443/workflows/XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX/triggers/When_a_HTTP_request_is_received/paths/invoke?api-version=2016-10-01&sp=%2Ftriggers%2FWhen_a_HTTP_request_is_received%2Frun&sv=1.0&sig=ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ
如果您的消费工作流以 请求 触发器开头,并且您想要将 OAuth 与 Microsoft Entra ID 一起使用,那么可以禁用 SAS 身份验证,以避免在运行工作流时出现错误和问题。 还可以通过删除对机密的依赖项来添加安全层,从而降低记录或泄露机密的风险。
即使还 启用具有 Microsoft Entra ID 的 OAuth 2.0 作为调用基于请求的终结点的唯一选项,此选项也能正常工作。 对于标准工作流,无需禁用 SAS 即可使用其他身份验证类型。
注释
此作将禁用传入请求的 SAS 身份验证,并阻止现有 SAS 密钥或签名正常工作。 但是,如果再次启用 SAS 身份验证,SAS 密钥或签名仍然有效,仍然有效。 若要通过创建新版本禁用 SAS 密钥和签名,请参阅 “重新生成访问密钥”。
禁用 SAS 身份验证后, 请求 触发器的终结点 URL 不再包含 SAS 密钥,例如:
https://{domain}:443/workflows/XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX/triggers/When_a_HTTP_request_is_received/paths/invoke?api-version=2016-10-01
先决条件
对于此任务,需要一个发送 REST API 调用的工具,例如:
注意
对于具有敏感数据(例如凭据、机密、访问令牌、API 密钥和其他类似信息)的方案,请确保使用一个工具,以必要的安全功能保护数据、脱机或本地工作,不会将数据同步到云,并且不需要登录到联机帐户。 这样,就可以降低向公众公开敏感数据的风险。
检查已启用或禁用 SAS 的触发器
禁用 SAS 身份验证后,触发器的终结点 URL 不再包含 SAS 密钥。 此外,消耗工作流定义包括 sasAuthenticationPolicy JSON 对象。 此对象具有一个state属性,该属性设置为Disabled,例如:
"properties": {
"accessControl": {
"triggers": {
"sasAuthenticationPolicy": {
"state": "Disabled"
}
}
}
}
若要查找已启用或禁用 SAS 的消耗工作流,请检查工作流定义是否包含状态属性设置为 Disabled 的 sasAuthenticationPolicy 对象。
借助发送 REST API 调用的工具,通过运行 Workflows - Get 操作,使用以下 GET 请求来获取有关您工作流的信息,例如:
GET https://management.chinacloudapi.cn/subscriptions/{subscription-ID}/resourceGroups/{resource-group-name}/providers/Microsoft.Logic/workflows/{workflow-name}?api-version=2016-06-01获取 工作流 - 获取 操作的输出,并检查是否存在 sasAuthenticationPolicy 对象,其中 状态 属性设置为 Disabled。
将 sasAuthenticationPolicy 属性添加到工作流定义
对于想要禁用 SAS 身份验证的消耗工作流,请执行以下步骤:
如果尚未这样做,请通过运行Workflows - Get 操作获取有关工作流的信息,方法是使用以下 GET 请求,例如:
GET https://management.chinacloudapi.cn/subscriptions/{subscription-ID}/resourceGroups/{resource-group-name}/providers/Microsoft.Logic/workflows/{workflow-name}?api-version=2016-06-01获取 工作流 - 获取 操作的输出,并手动添加以下元素:
如果不存在
triggers对象,在properties对象中添加一个包含triggers对象的accessControl对象。在
triggers对象中,添加一个包含state属性设置为Disabled的sasAuthenticationPolicy对象。
完成后,编辑后的部分如以下示例所示:
"properties": { "accessControl": { "triggers": { "sasAuthenticationPolicy": { "state": "Disabled" } } } }通过运行工作流 - 更新操作,使用如下 PUT 请求,发送另一个请求以更新您的工作流,其中使用编辑的输出作为请求正文中的输入,例如:
PUT https://management.chinacloudapi.cn/subscriptions/{subscription-ID}/resourceGroups/{resource-group-name}/providers/Microsoft.Logic/workflows/{workflow-name}?api-version=2016-06-01在 Azure 门户中,转到设计器中的“消费工作流”,并确认 请求触发器的 URL 不再包含 SAS。
若要在逻辑应用资源级别启用具有 Microsoft Entra ID 的 OAuth 2.0, 请为具有 Microsoft Entra ID 的 OAuth 添加授权策略。
有关详细信息,请参阅 使用 Microsoft Entra ID 启用 OAuth 2.0。
重新生成访问密钥
若要维护安全性和保护对逻辑应用工作流的访问,请定期重新生成访问密钥,因为它们可能需要遵守安全策略或遭到入侵。 这样,就可以确保只有授权的请求才能触发工作流,从而防止数据和进程受到未经授权的访问。
若要随时生成新的访问密钥,请使用 Azure REST API 或 Azure 门户。 以前生成的所有使用旧密钥的 URI 或 URL 都失效,并且不再具有触发逻辑应用工作流的授权。 重新生成后检索的 URI 使用新的访问密钥进行签名。
在 Azure 门户中,打开使用要重新生成的密钥的逻辑应用资源。
在逻辑应用资源菜单上的 “设置”下,选择“ 访问密钥”。
选择要重新生成并完成过程的密钥。
重要
确保保护访问密钥,就像保护帐户密钥免受未经授权的使用一样。 设置或具有撤消已泄露访问密钥的计划。 在分发使用访问密钥的 URI 时,使用自由裁量权,并且仅通过安全连接(如 HTTPS)分发此类 URI。 请确保仅在 HTTPS 连接上执行使用访问密钥的操作。 具有有效密钥的 URI 的任何人都可以访问关联的资源。
如果使用 SAS 密钥访问存储服务,Microsoft建议 创建用户委派 SAS,该 SAS 使用 Microsoft Entra ID 进行保护,而不是帐户密钥。
为了获得最佳安全性,Microsoft建议尽可能将 Microsoft Entra ID 与 托管标识 配合使用进行身份验证。 此选项提供卓越的安全性,而无需提供凭据。 Azure 负责管理此标识并帮助保护身份验证信息的安全,这样你就无需管理这种敏感信息了。 若要为 Azure 逻辑应用设置托管标识,请参阅在 Azure 逻辑应用中使用托管标识对 Azure 资源的访问和连接进行身份验证。
创建即将过期的回调 URL
如果您将请求触发器的终结点 URL 与其他方共享,您可以生成使用特定密钥并具有到期日期的回调 URL。 这样,就可以无缝轮换密钥,或限制访问以根据特定时间段触发逻辑应用。 若要指定 URL 的到期日期,请使用 Azure 逻辑应用 REST API,例如:
POST /subscriptions/{subscription-ID}/resourceGroups/{resource-group-name}/providers/Microsoft.Logic/workflows/{workflow-name}/triggers/{trigger-name}/listCallbackUrl?api-version=2016-06-01
在正文中,使用 JSON 日期字符串包含 NotAfter 属性。 此属性返回的回调 URL 仅在指定的NotAfter日期和时间之前有效。
使用主密钥或辅助密钥创建 URL
为基于请求的触发器生成或列出回调 URL 时,可以指定用于对 URL 进行签名的密钥。 若要生成由特定密钥签名的 URL,请使用 Azure 逻辑应用 REST API,例如:
POST /subscriptions/{subscription-ID}/resourceGroups/{resource-group-name}/providers/Microsoft.Logic/workflows/{workflow-name}/triggers/{trigger-name}/listCallbackUrl?api-version=2016-06-01
在正文中,将 KeyType 属性作为 Primary 或 Secondary。 此属性返回由指定安全密钥签名的 URL。
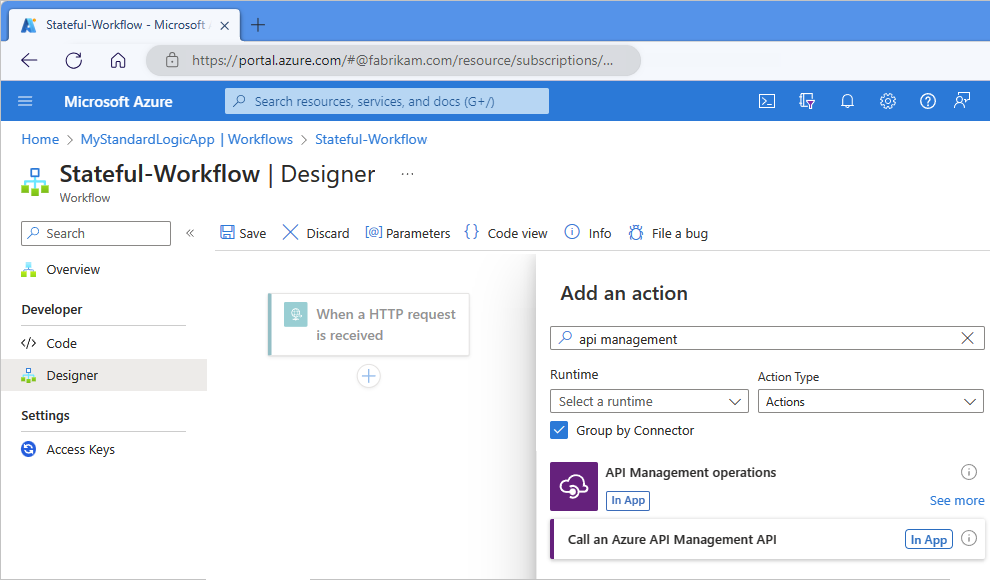
使用 Azure API 管理公开逻辑应用工作流
有关更多身份验证协议和选项,请考虑使用 Azure API 管理将逻辑应用工作流公开为 API。 此服务为任何终结点提供丰富的监视、安全、策略和文档功能。 API 管理可以为逻辑应用公开公共或专用终结点。 若要授权访问此终结点,可以将 OAuth 与 Microsoft Entra ID、客户端证书或其他安全标准一起使用。 当 API 管理收到请求时,服务会将请求发送到逻辑应用,并在此过程中进行任何必要的转换或限制。 若要仅允许 API 管理调用逻辑应用工作流,可以 限制逻辑应用的入站 IP 地址。
有关详细信息,请参阅以下文档:
- 关于 API 管理
- 使用具有 Microsoft Entra ID 的 OAuth 2.0 授权保护 Azure API 管理中的 Web API 后端
- 在 API 管理中使用客户端证书身份验证保护 API
- API 管理身份验证策略
限制入站 IP 地址
除了共享访问签名(SAS),你可能希望专门限制可以调用逻辑应用工作流的客户端。 例如,如果使用 Azure API 管理管理请求终结点,则可以限制逻辑应用工作流以仅接受来自 所创建的 API 管理服务实例的 IP 地址的请求。
无论您指定了哪些 IP 地址,您仍然可以运行具有请求触发器的逻辑应用工作流,方法是使用
若要限制逻辑应用工作流的入站 IP 地址,请遵循 Azure 门户或 Azure 资源管理器模板的相应步骤。 有效的 IP 范围使用以下格式: x.x.x.x/x 或 x.x.x.x-x.x.x.
在 Azure 门户中,IP 地址限制会影响触发器 和 作,这与门户中“ 允许的入站 IP 地址”下的说明相反。 若要为触发器和操作单独设置此筛选器,请在 Azure 资源管理器模板中将
消耗型工作流
在 Azure 门户中,在工作流设计器中打开消耗逻辑应用。
在逻辑应用菜单上的 “设置”下,选择 “工作流设置”。
在“ 访问控制配置 ”部分中,在 “允许的入站 IP 地址”下,选择方案的路径:
若要使用 Azure 逻辑应用 内置操作使工作流可调用,但仅作为嵌套工作流,请选择 “仅其他 Logic Apps”。 仅当使用 Azure 逻辑应用作调用嵌套工作流时,此选项才有效。
此选项将空数组写入您的逻辑应用资源,并要求只有使用内置 Azure 逻辑应用操作的父工作流的调用才能触发嵌套工作流。
若要使用 HTTP作使工作流可调用,但仅作为嵌套工作流,请选择 “特定 IP 范围”。 当触发器框的 IP 范围 出现时,输入父工作流的 出站 IP 地址。 有效的 IP 范围使用以下格式: x.x.x.x/x 或 x.x.x.x-x.x.x.
注释
如果您使用 “仅其他逻辑应用” 选项和 HTTP 操作来调用嵌套工作流,该调用将被阻止,您会收到“401 未授权”错误。
对于想要限制来自其他 IP 的入站调用的情况,当 触发器的 IP 范围 出现时,请指定触发器接受的 IP 地址范围。 有效的 IP 范围使用以下格式: x.x.x.x/x 或 x.x.x.x-x.x.x.
(可选)在“限制调用以通过提供的 IP 地址获取运行历史记录中的输入和输出消息”选项下,您可以指定入站调用的 IP 地址范围,以允许其访问运行历史记录中的输入和输出消息。
标准工作流
在 Azure 门户中,打开你的标准逻辑应用资源。
在逻辑应用菜单上的 “设置”下,选择“ 网络”。
在 “入站流量配置” 部分的 “公用网络访问”旁边,选择“ 已启用”,且没有访问限制。
在 “访问限制 ”页上,在 “应用访问”下, 从选择虚拟网络和 IP 地址中选择“已启用”。
在“主站点”选项卡上的“站点访问和规则”下,将一个或多个规则添加到来自特定 IP 范围的“允许”或“拒绝”请求。 有效的 IP 范围使用以下格式: x.x.x.x/x 或 x.x.x.x-x.x.x.
有关详细信息,请参阅在 Azure Logic Apps(标准)中阻止入站 IP 地址。
对其他服务和系统的出站调用的访问
根据目标终结点的功能,HTTP 触发器或 HTTP 操作发送的出站调用支持加密,并且使用传输层安全性(TLS)1.0、1.1 或 1.2(以前称为安全套接字层(SSL))进行保护。 Azure 逻辑应用与目标终结点谈判使用所支持的最高版本。 例如,如果目标终结点支持 1.2,则 HTTP 触发器或作首先使用 1.2。 否则,连接器将使用下一个支持最高的版本。
此列表包含有关 TLS/SSL 自签名证书的信息:
对于多租户 Azure 逻辑应用环境中的消费逻辑应用工作流,HTTP 操作不允许自签名 TLS/SSL 证书。 如果逻辑应用对服务器进行 HTTP 调用并显示 TLS/SSL 自签名证书,则 HTTP 调用将失败并
TrustFailure显示错误。对于单租户 Azure 逻辑应用环境中的标准逻辑应用工作流,HTTP 操作支持自签名 TLS/SSL 证书。 但是,必须完成此身份验证类型的几个额外步骤。 否则,调用会失败。 有关详细信息,请查看 单租户 Azure 逻辑应用的 TLS/SSL 证书身份验证。
如果要改用具有“证书”凭据类型的Microsoft Entra ID 的客户端证书或 OAuth,仍必须完成此身份验证类型的几个额外步骤。 否则,调用会失败。 有关详细信息,请查看 具有 Microsoft Entra ID 的客户端证书或 OAuth,其中包含单租户 Azure 逻辑应用的“证书”凭据类型。
下面是更多方法,可以帮助保护处理从逻辑应用工作流发送调用的端点:
-
使用 HTTP 触发器或作发送出站调用时,可以将身份验证添加到逻辑应用发送的请求。 例如,可以选择以下身份验证类型:
限制从逻辑应用工作流 IP 地址进行访问。
从逻辑应用工作流对终结点的所有调用都源自基于逻辑应用区域的特定指定 IP 地址。 可以添加仅接受来自这些 IP 地址的请求的筛选。 若要获取这些 IP 地址,请查看 Azure 逻辑应用的限制和配置。
提高连接到本地系统的安全性。
Azure 逻辑应用提供与这些服务的集成,以帮助提供更安全、更可靠的本地通信。
本地数据网关
Azure 逻辑应用中的许多托管连接器有助于与本地系统(例如文件系统、SQL、SharePoint 和 DB2)建立安全连接。 网关通过加密通道将本地部署的来源的数据发送到 Azure 服务总线。 所有流量最初都是网关代理的安全出站流量。 了解 本地数据网关的工作原理。
通过 Azure API 管理进行连接
Azure API 管理 提供本地连接选项,例如站点到站点虚拟专用网络和 ExpressRoute 集成,用于安全代理和与本地系统的通信。 如果 API 提供对本地系统的访问权限,并且通过创建 API 管理服务实例公开该 API,则可以通过在工作流设计器中选择相应的 API 管理 作从逻辑应用的工作流调用该 API。
注释
连接器仅显示有权查看和连接的 API 管理服务,但不显示基于消耗的 API 管理服务。
根据逻辑应用资源类型,执行相应的步骤:
消耗工作流
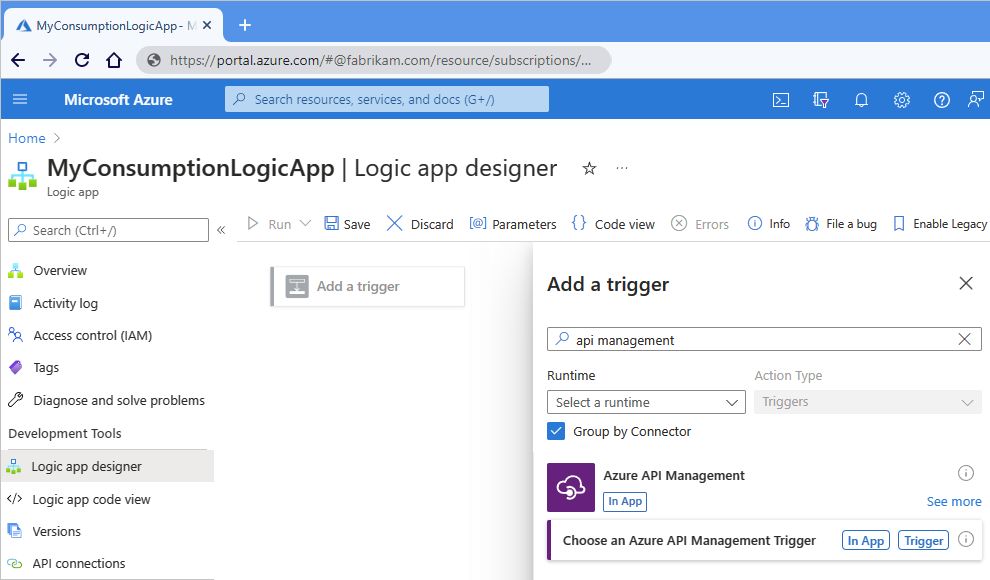
根据您是要添加 API 管理触发器还是操作,请执行以下步骤:
触发:
在工作流设计器上,选择 “添加触发器”。
“ 添加触发器 ”窗格打开后,在搜索框中输入 API 管理。
在触发器结果列表中, 选择“选择 Azure API 管理触发器”。
操作:
在工作流设计器上,选择加号(+),以添加动作。
“添加操作”窗格打开后,在搜索框中输入API 管理。
从操作结果列表中选择 “选择一个 Azure API 管理操作”。
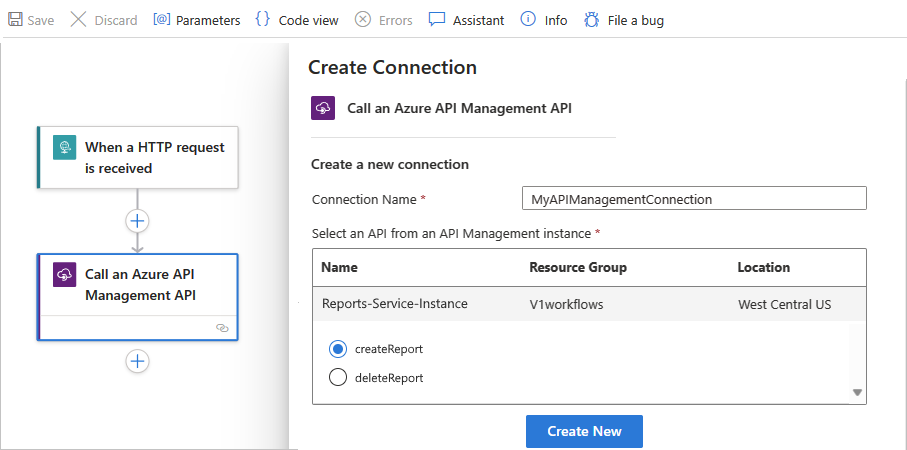
以下示例演示如何查找 Azure API 管理触发器:
从 API 管理服务实例列表中,选择之前创建的 API 管理服务实例。
从 API操作列表中选择要调用的 API操作,然后选择“添加操作”。
标准工作流
对于标准工作流,只能添加 API 管理 作,而不能添加触发器。
将身份验证添加到出站调用
HTTP 和 HTTPS 终结点支持各种身份验证。 在用于发送出站调用或请求到这些终结点的某些触发器和操作中,您可以指定身份验证类型。 在工作流设计器中,支持选择身份验证类型的触发器和作具有 身份验证 属性。 但是,此属性可能不会始终默认显示。 在这些情况下,在触发器或作上,打开 “高级参数 ”列表,然后选择“ 身份验证”。
重要
若要保护逻辑应用工作流处理的敏感信息,请使用受保护的参数并根据需要对数据进行编码。 有关使用和保护参数的详细信息,请查看 对参数输入的访问。
为了获得最佳安全性,Microsoft建议尽可能将 Microsoft Entra ID 与 托管标识 配合使用进行身份验证。 此选项提供卓越的安全性,而无需提供凭据。 Azure 负责管理此标识并帮助保护身份验证信息的安全,这样你就无需管理这种敏感信息了。 若要为 Azure 逻辑应用设置托管标识,请参阅在 Azure 逻辑应用中使用托管标识对 Azure 资源的访问和连接进行身份验证。
基本身份验证
对于 HTTP 调用,基本身份验证使用 base64 编码的字符串,其中包含用户名和密码发出请求。 除非将此选项用于 HTTPS/SSL 协议,否则此方法传输不加密的凭据,并带来更高的安全风险。
重要
为了获得最佳安全性,Microsoft建议尽可能将 Microsoft Entra ID 与 托管标识 配合使用进行身份验证。 此选项提供卓越的安全性,而无需提供凭据。 Azure 负责管理此标识并帮助保护身份验证信息的安全,这样你就无需管理这种敏感信息了。 若要为 Azure 逻辑应用设置托管标识,请参阅在 Azure 逻辑应用中使用托管标识对 Azure 资源的访问和连接进行身份验证。
如果“ 基本 ”选项可用且处于选中状态,请指定以下属性值:
| 属性(设计器) | 属性 (JSON) | 必选 | 价值 | Description |
|---|---|---|---|---|
| 身份验证 | type |
是的 | 基本 | 要使用的身份验证类型 |
| 用户名 | username |
是的 | < user-name> | 用于对目标服务终结点的访问进行身份验证的用户名 |
| 密码 | password |
是的 | < 密码> | 用于验证访问目标服务终结点的密码 |
使用 安全参数 来处理和保护敏感信息(例如,在 用于自动部署的 Azure 资源管理器模板中)时,可以使用表达式在运行时访问这些参数值。 此示例 HTTP 操作定义指定身份验证为 type,以及 Basic 并使用 parameters() 函数 获取参数值:
"HTTP": {
"type": "Http",
"inputs": {
"method": "GET",
"uri": "@parameters('endpointUrlParam')",
"authentication": {
"type": "Basic",
"username": "@parameters('userNameParam')",
"password": "@parameters('passwordParam')"
}
},
"runAfter": {}
}
客户端证书身份验证
客户端证书身份验证 允许或要求用户使用 X.509 证书直接对其 Microsoft Entra ID 进行身份验证,以用于应用程序和浏览器登录。 此功能可帮助你采用防钓鱼身份验证,并使用针对公钥基础结构 (PKI) 的 X.509 证书进行身份验证。
重要
为了获得最佳安全性,Microsoft建议尽可能将 Microsoft Entra ID 与 托管标识 配合使用进行身份验证。 此选项提供卓越的安全性,而无需提供凭据。 Azure 负责管理此标识并帮助保护身份验证信息的安全,这样你就无需管理这种敏感信息了。 若要为 Azure 逻辑应用设置托管标识,请参阅在 Azure 逻辑应用中使用托管标识对 Azure 资源的访问和连接进行身份验证。
如果 “客户端证书 ”选项可用且处于选中状态,请指定以下属性值:
| 属性(设计器) | 属性 (JSON) | 必选 | 价值 | Description |
|---|---|---|---|---|
| 身份验证 | type |
是的 |
客户端证书 或 ClientCertificate |
要使用的认证类型。 可以使用 Azure API 管理来管理证书。 注意:自定义连接器不支持入站和出站调用的基于证书的身份验证。 |
| Pfx | pfx |
是的 | < encoded-pfx-file-content> | 个人信息交换 (PFX) 文件中的 base64 编码内容 若要将 PFX 文件转换为 base64 编码格式,可以按照以下步骤使用 PowerShell 7: 1.将证书内容保存到变量中: $pfx_cert = [System.IO.File]::ReadAllBytes('c:\certificate.pfx') 2.使用 ToBase64String() 函数转换证书内容,并将该内容保存到文本文件: [System.Convert]::ToBase64String($pfx_cert) | Out-File 'pfx-encoded-bytes.txt' 疑难解答:如果使用 cert mmc/PowerShell 命令,可能会收到此错误: Could not load the certificate private key. Please check the authentication certificate password is correct and try again. 若要解决此错误,请尝试使用 openssl 以下命令将 PFX 文件转换为 PEM 文件并再次返回: openssl pkcs12 -in certificate.pfx -out certificate.pem openssl pkcs12 -in certificate.pem -export -out certificate2.pfx 之后,当您获取证书新转换的 PFX 文件的 base64 编码字符串时,该字符串现在可以在 Azure Logic Apps 中正常使用。 |
| 密码 | password |
否 | < password-for-pfx-file> | 用于访问 PFX 文件的密码 |
注释
如果尝试使用 OpenSSL 通过客户端证书进行身份验证,可能会收到以下错误:
BadRequest: Could not load private key
为了解决此错误,请执行以下步骤:
- 卸载所有 OpenSSL 实例。
- 安装 OpenSSL 版本 1.1.1t。
- 使用新更新重新签名证书。
- 使用客户端证书身份验证时,将新证书添加到 HTTP 操作中。
使用 安全参数 来处理和保护敏感信息(例如,在 用于自动部署的 Azure 资源管理器模板中)时,可以使用表达式在运行时访问这些参数值。 此示例 HTTP 操作定义指定身份验证 type 为 ClientCertificate,并使用 parameters() 函数 获取参数值。
"HTTP": {
"type": "Http",
"inputs": {
"method": "GET",
"uri": "@parameters('endpointUrlParam')",
"authentication": {
"type": "ClientCertificate",
"pfx": "@parameters('pfxParam')",
"password": "@parameters('passwordParam')"
}
},
"runAfter": {}
}
重要
如果在单租户 Azure 逻辑应用中有标准逻辑应用资源,并且想要将 HTTP 操作与 TLS/SSL 证书、客户端证书或 Microsoft Entra ID OAuth(Microsoft Entra ID 开放身份验证)与 Certificate 凭据类型配合使用,请确保完成该身份验证类型的额外设置步骤。 否则,调用会失败。 有关详细信息,请查看 单租户环境中的身份验证。
有关使用客户端证书身份验证保护服务的详细信息,请查看以下主题:
- 在 Azure API 管理中使用客户端证书身份验证提高 API 的安全性
- 在 Azure API 管理中使用客户端证书身份验证提高后端服务的安全性
- 用于应用程序身份验证的证书凭据
- 在 Azure 应用服务中通过代码使用 TLS/SSL 证书
Microsoft Entra 平台
在请求触发器上,可以在为逻辑应用设置Microsoft Entra 授权策略后,使用 Microsoft Entra 平台对传入调用进行身份验证。
重要
为了获得最佳安全性,Microsoft建议尽可能将 Microsoft Entra ID 与 托管标识 配合使用进行身份验证。 此选项提供卓越的安全性,而无需提供凭据。 Azure 负责管理此标识并帮助保护身份验证信息的安全,这样你就无需管理这种敏感信息了。 若要为 Azure 逻辑应用设置托管标识,请参阅在 Azure 逻辑应用中使用托管标识对 Azure 资源的访问和连接进行身份验证。
在支持 Active Directory OAuth(OAuth 2.0 with Microsoft Entra ID)身份验证类型的所有其他触发器和操作上,指定以下属性值:
| 属性(设计器) | 属性 (JSON) | 必选 | 价值 | Description |
|---|---|---|---|---|
| 身份验证 | type |
是的 |
Active Directory OAuth (具有 Microsoft Entra ID 的 OAuth 2.0) 或 ActiveDirectoryOAuth |
要使用的认证类型。 Azure 逻辑应用当前遵循 OAuth 2.0 协议。 |
| 权限 | authority |
否 | < 用于权限令牌发行者的URL> | 提供访问令牌的颁发机构的 URL,例如 Azure 全球服务区的 https://login.chinacloudapi.cn/。 对于其他国家云,请查看 Microsoft Entra 身份验证终结点 - 选择您的身份认证权威。 |
| 租户 | tenant |
是的 | < tenant-ID> | Microsoft Entra 租户的租户 ID |
| 观众 | audience |
是的 | < 需要授权的资源> | 要用于授权的资源,例如 https://management.core.chinacloudapi.cn/ |
| 客户端 ID | clientId |
是的 | < client-ID> | 请求授权的应用的客户端 ID |
| 凭据类型 | credentialType |
是的 | 证书 或 机密 |
客户端用于请求授权的凭据类型。 此属性和值虽然不会显示在逻辑应用的基础定义中,但它们决定了所选凭据类型将显示哪些属性。 |
| 机密 | secret |
是,但仅适用于“机密”凭据类型 | < client-secret> | 请求授权的客户端密码 |
| Pfx | pfx |
是,但仅适用于“证书”凭据类型 | < encoded-pfx-file-content> | 个人信息交换 (PFX) 文件中的 base64 编码内容 |
| 密码 | password |
是,但仅适用于“证书”凭据类型 | < password-for-pfx-file> | 用于访问 PFX 文件的密码 |
使用 安全参数 来处理和保护敏感信息(例如,在 用于自动部署的 Azure 资源管理器模板中)时,可以使用表达式在运行时访问这些参数值。 此示例 HTTP作定义将身份验证 type 指定为 ActiveDirectoryOAuth凭据类型 Secret,并使用 parameters() 函数 获取参数值:
"HTTP": {
"type": "Http",
"inputs": {
"method": "GET",
"uri": "@parameters('endpointUrlParam')",
"authentication": {
"type": "ActiveDirectoryOAuth",
"tenant": "@parameters('tenantIdParam')",
"audience": "https://management.core.chinacloudapi.cn/",
"clientId": "@parameters('clientIdParam')",
"credentialType": "Secret",
"secret": "@parameters('secretParam')"
}
},
"runAfter": {}
}
重要
如果您在单租户 Azure 逻辑应用中有标准逻辑应用资源,并且想要将 HTTP 操作与 TLS/SSL 证书、客户端证书或 Microsoft Entra ID OAuth 凭据类型Certificate配合使用,请确保完成此身份验证类型的额外设置步骤。 否则,调用会失败。 有关详细信息,请参阅 单租户环境中的身份验证。
原始身份验证
如果原始选项可用,则必须使用不遵循 OAuth 2.0 协议的身份验证方案时,可以使用此身份验证类型。 使用此类型,可以手动创建使用传出请求发送的授权标头值,并在触发器或作中指定该标头值。
重要
为了获得最佳安全性,Microsoft建议尽可能将 Microsoft Entra ID 与 托管标识 配合使用进行身份验证。 此选项提供卓越的安全性,而无需提供凭据。 Azure 负责管理此标识并帮助保护身份验证信息的安全,这样你就无需管理这种敏感信息了。 若要为 Azure 逻辑应用设置托管标识,请参阅在 Azure 逻辑应用中使用托管标识对 Azure 资源的访问和连接进行身份验证。
以下示例显示了 遵循 OAuth 1.0 协议的 HTTPS 请求的示例标头:
Authorization: OAuth realm="Photos",
oauth_consumer_key="dpf43f3p2l4k3l03",
oauth_signature_method="HMAC-SHA1",
oauth_timestamp="137131200",
oauth_nonce="wIjqoS",
oauth_callback="http%3A%2F%2Fprinter.example.com%2Fready",
oauth_signature="74KNZJeDHnMBp0EMJ9ZHt%2FXKycU%3D"
在支持原始身份验证的触发器或作中,指定以下属性值:
| 属性(设计器) | 属性 (JSON) | 必选 | 价值 | Description |
|---|---|---|---|---|
| 身份验证 | type |
是的 | 原始 | 要使用的身份验证类型 |
| 价值 | value |
是的 | < authorization-header-value> | 要用于身份验证的授权标头值 |
使用 安全参数 来处理和保护敏感信息(例如,在 用于自动部署的 Azure 资源管理器模板中)时,可以使用表达式在运行时访问这些参数值。 此示例 HTTP作定义将身份验证 type 指定为 Raw,并使用 parameters() 函数 获取参数值:
"HTTP": {
"type": "Http",
"inputs": {
"method": "GET",
"uri": "@parameters('endpointUrlParam')",
"authentication": {
"type": "Raw",
"value": "@parameters('authHeaderParam')"
}
},
"runAfter": {}
}
托管标识身份验证
当 托管标识 选项在 支持托管标识身份验证的触发器或作上可用时,逻辑应用可以使用此标识对受 Microsoft Entra ID 保护的 Azure 资源(而不是凭据、机密或Microsoft Entra 令牌)的访问进行身份验证。 Azure 会为你管理此标识并帮助保护凭据,因为无需管理机密或直接使用 Microsoft Entra 令牌。 详细了解 支持用于Microsoft Entra 身份验证的托管标识的 Azure 服务。
消耗逻辑应用资源可以使用系统分配的标识或 单个 手动创建的用户分配标识。
标准逻辑应用资源支持同时启用 系统分配的托管标识 和 多个用户分配的托管标识 ,不过你仍只能选择一个标识随时使用。
注释
在默认情况下,已启用系统分配的标识,以便在运行时对连接进行身份验证。 该标识与你在创建连接时使用的身份验证凭据或连接字符串不同。 如果禁用该标识,则运行时连接无效。 若要查看此设置,请在逻辑应用菜单上的 “设置”下选择“ 标识”。
在逻辑应用可以使用托管标识之前,请按照 在 Azure 逻辑应用中使用托管标识对 Azure 资源进行访问身份验证中的步骤操作。 这些步骤在逻辑应用上启用托管标识,并设置该标识对目标 Azure 资源的访问权限。
在 Azure 函数可以使用托管标识之前,请先 为 Azure Functions 启用身份验证。
在支持使用托管标识的触发器或操作中,提供以下信息:
内置触发器和操作
属性(设计器) 属性 (JSON) 必选 价值 Description 身份验证 type是的 托管标识
或ManagedServiceIdentity要使用的身份验证类型 托管标识 identity否 < user-assigned-identity-ID> 由用户分配的要使用的托管标识。 注意:使用系统分配的托管标识时,请勿包含此属性。 观众 audience是的 < target-resource-ID> 要访问的目标资源的资源 ID。
例如,https://storage.azure.com/使 访问令牌 对所有存储帐户都有效。 但是,还可以指定根服务 URL,例如https://fabrikamstorageaccount.blob.core.chinacloudapi.cn针对特定存储帐户。
注意:某些触发器或作中可能会隐藏 Audience 属性。 若要使此属性可见,请在触发器或作中打开 “高级参数 ”列表,然后选择“ 受众”。
重要:确保该目标资源 ID 完全匹配 Microsoft Entra ID 所需的值,包括任何必需的末尾斜杠。 因此,所有 Azure Blob 存储帐户的https://storage.azure.com/资源 ID 都需要斜杠结尾。 但是,特定存储帐户的资源 ID 不需要尾部反斜杠。 若要查找这些资源 ID,请查看 支持 Microsoft Entra ID 的 Azure 服务。使用 安全参数 来处理和保护敏感信息(例如,在 用于自动部署的 Azure 资源管理器模板中)时,可以使用表达式在运行时访问这些参数值。 例如,此 HTTP 动作定义将身份验证指定为
typeManagedServiceIdentity,并使用 parameters() 函数 获取参数值。"HTTP": { "type": "Http", "inputs": { "method": "GET", "uri": "@parameters('endpointUrlParam')", "authentication": { "type": "ManagedServiceIdentity", "audience": "https://management.chinacloudapi.cn/" }, }, "runAfter": {} }托管的连接器触发器和操作
属性(设计器) 必选 价值 Description 连接名称 是的 < 连接名称> 托管标识 是的 系统分配的托管标识
或
< 用户分配的托管身份名称>要使用的身份验证类型
阻止创建连接
如果组织不允许使用 Azure 逻辑应用中的连接器连接到特定资源,则可以阻止使用 Azure Policy 在逻辑应用工作流中为特定连接器创建这些连接的功能。 有关详细信息,请查看 在 Azure 逻辑应用中由特定连接器创建的连接块。