通过 Azure 防火墙管理器中的安全合作伙伴提供程序,你可以使用熟悉的同类最佳第三方安全即服务 (SECaaS) 产品/服务来保护用户的 Internet 访问。
要详细了解支持的场景和最佳做法指南,请参阅什么是安全合作伙伴提供程序?
集成的第三方安全即服务 (SECaaS) 合作伙伴现已可用:
- Zscaler
在新中心部署第三方安全提供程序
如果要将第三方提供程序部署到现有中心,请跳过此部分。
- 登录 Azure 门户。
- 在“搜索”中键入“防火墙管理器”,然后在“服务”下选择“防火墙管理器” 。
- 导航到“概述”。 选择“查看安全虚拟中心”。
- 选择“新建安全虚拟中心”。
- 输入你的订阅和资源组,选择受支持的区域,并添加中心和虚拟 WAN 信息。
- 选择“包含 VPN 网关以启用安全合作伙伴提供程序”。
- 根据要求选择适当的“网关缩放单元”。
- 在完成时选择“下一步:Azure 防火墙”
注意
安全合作伙伴提供程序使用 VPN 网关隧道连接到你的中心。 如果删除 VPN 网关,与安全合作伙伴提供程序的连接将会丢失。
- 如果要部署 Azure 防火墙来筛选专用流量,并部署第三方服务提供程序来筛选 Internet 流量,请选择 Azure 防火墙的策略。 请参阅支持的场景。
- 如果只想在中心部署第三方安全提供程序,请选择“Azure 防火墙:启用/禁用”,并将其设置为“禁用”。
- 选择“下一步: 安全合作伙伴提供程序”。
- 将“安全合作伙伴提供程序”设置为“启用” 。
- 选择一个合作伙伴。
- 在完成时选择“下一步:查看 + 创建”。
- 查看内容,然后选择“创建”。
部署 VPN 网关可能需要超过 30 分钟的时间。
要验证是否已创建中心,请导航到“Azure 防火墙管理器”-“>概述”-“>查看安全虚拟中心”。 可以看到安全合作伙伴提供程序名称和安全合作伙伴状态为安全连接挂起。
创建中心并设置安全合作伙伴后,请继续将安全提供程序连接到中心。
在现有中心部署第三方安全提供程序
还可以选择虚拟 WAN 中的现有中心,并将其转换为安全虚拟中心。
- 在“入门”的“概述”中,选择“查看安全虚拟中心”。
- 选择“转换现有中心”。
- 选择订阅和现有中心。 按照剩余步骤在新中心部署第三方安全提供程序。
请记住,必须部署 VPN 网关才能使用第三方提供程序将现有中心转换为安全中心。
配置第三方安全提供程序以连接到安全中心
若要建立到虚拟中心的 VPN 网关的隧道,第三方提供程序需要有该中心的访问权限。 为此,请将服务主体与订阅或资源组关联,并授予访问权限。 然后,必须通过其门户将这些凭据分配给第三方。
注意
第三方安全提供程序代表你创建 VPN 站点。 此 VPN 站点不会显示在 Azure 门户中。
创建服务主体并为其授权
创建 Microsoft Entra 服务主体:可以跳过重定向 URL。
为服务主体添加访问权限和作用域。 如何:使用门户创建可访问资源的 Microsoft Entra 应用程序和服务主体
注意
可以将访问权限限制为仅针对你的资源组,以便进行更精细的控制。
访问合作伙伴门户
按照合作伙伴提供的说明完成设置。 这包括提交 Microsoft Entra 信息以检测并连接到中心、更新出口策略,以及检查连接状态和日志。
可以在 Azure 的 Azure 虚拟 WAN 门户中查看隧道创建状态。 Azure 门户和合作伙伴门户中的隧道状态均显示“已连接”后,请继续执行后续步骤,以设置路由,并选择哪些分支和 Vnet 应将 Internet 流量发送到合作伙伴。
使用防火墙管理器配置安全性
浏览到“Azure 防火墙管理器”->“安全中心”。
选择一个中心。 现在,中心状态应显示“已预配”,而不是“安全连接挂起”。
请确保第三方提供程序可以连接到中心。 VPN 网关上的隧道应处于“已连接”状态。 与之前的状态相比,此状态更能反映中心与第三方合作伙伴之间的连接运行状况。
选择中心,并导航到“安全配置”。
向中心部署第三方提供程序时,该第三方提供程序会将该中心转换为安全虚拟中心。 这可确保第三方提供程序向中心播发 0.0.0.0/0(默认)路由。 但是,除非你选择了哪些连接应获得此默认路由,否则连接到中心的虚拟网络连接和站点不会获得此路由。
注意
对于分支播发,不要手动创建使用 BGP 的 0.0.0.0/0(默认)路由。 对于使用第三方安全提供程序进行的安全虚拟中心部署,这会自动创建。 这样做可能会中断部署过程。
通过 Azure 防火墙设置“Internet 流量”,并通过信任的安全合作伙伴设置“专用流量”来配置虚拟 WAN 安全性。 这会自动保护虚拟 WAN 中单个连接的安全。
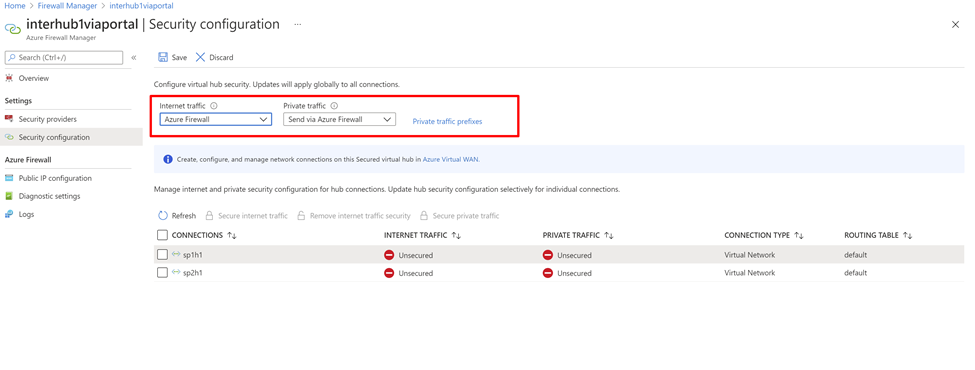
此外,如果你的组织使用虚拟网络和分支机构中的公共 IP 范围,则需要使用“专用流量前缀”显式指定这些 IP 前缀。 可单独指定公共 IP 前缀,也可以聚合形式指定。
如果将非 RFC1918 地址用于专用流量前缀,可能需要为防火墙配置 SNAT 策略,以对非 RFC1918 专用流量禁用 SNAT。 默认情况下,Azure 防火墙 SNAT 应用于所有非 RFC1918 流量。
通过第三方服务的分支或虚拟网络 Internet 流量
接下来,可以检查虚拟网络虚拟机或分支站点是否可访问 Internet,并验证流量是否流向第三方服务。
完成路由设置步骤后,系统会向虚拟网络虚拟机和分支站点发送 0/0 到第三方服务的路由。 无法通过 RDP 或 SSH 登录这些虚拟机。 若要登录,可在对等互连的虚拟网络中部署 Azure Bastion 服务。
规则配置
使用合作伙伴门户配置防火墙规则。 Azure 防火墙会让流量通过。
例如,你可能会观察到允许通过 Azure 防火墙的流量,即使没有明确的规则允许该流量。 这是因为 Azure 防火墙会将流量传递给下一个跃点安全合作伙伴提供者 (ZScalar)。 Azure 防火墙仍有允许出站流量的规则,但规则名称不会被记录。
有关详细信息,请参阅合作伙伴文档。