安全管理员需要管理防火墙,并确保跨本地部署和云部署的合规性。 一个关键因素是使应用程序团队能够灵活地实现 CI/CD 管道,从而以自动方式创建防火墙规则。
Azure 防火墙策略可用于定义规则层次结构并强制实施合规性:
- 提供一个层次结构,使中心基本策略覆盖子应用程序团队策略。 基本策略具有更高的优先级,并在子策略之前运行。
- 使用 Azure 自定义角色定义防止意外删除基本策略,并提供对订阅或资源组内规则集合组的选择性访问。
解决方案概述
本示例的概要步骤如下:
- 在安全团队资源组中创建基本防火墙策略。
- 在基本策略中定义特定于 IT 安全性的规则。 这会添加一组通用规则,以允许/拒绝流量。
- 创建继承基本策略的应用程序团队策略。
- 在策略中定义特定于应用程序团队的规则。 还可以从预先存在的防火墙迁移规则。
- 创建 Microsoft Entra 自定义角色以提供对规则集合组的精细访问,并在防火墙策略范围内添加角色。 在以下示例中,销售团队成员可以编辑销售团队防火墙策略的规则集合组。 这同样适用于数据库团队和工程团队。
- 将策略关联到相应的防火墙。 Azure 防火墙只能有一个分配的策略。 这要求每个应用程序团队都有自己的防火墙。
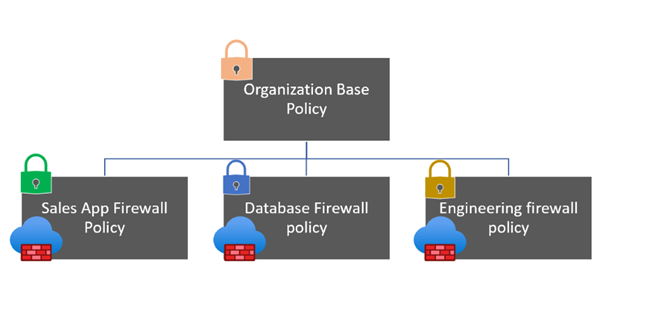
创建防火墙策略
- 基本防火墙策略。
为每个应用程序团队创建策略:
- 销售防火墙策略。 销售防火墙策略继承基本防火墙策略。
- 数据库防火墙策略。 数据库防火墙策略继承基本防火墙策略。
- 工程防火墙策略。 工程防火墙策略也继承基本防火墙策略。
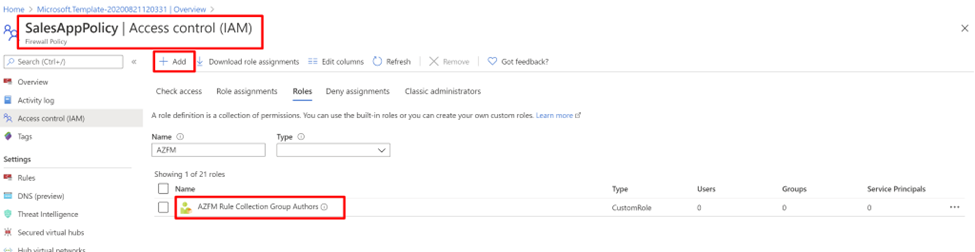
创建自定义角色以访问规则集合组
为每个应用程序团队定义自定义角色。 角色定义操作和范围。 应用程序团队可编辑其各自应用程序的规则集合组。
使用以下概要过程定义自定义角色:
获取订阅。
Select-AzSubscription -SubscriptionId xxxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxxxx运行以下命令。
Get-AzProviderOperation "Microsoft.Support/*" | FT Operation, Description -AutoSize使用 Get-AzRoleDefinition 命令以 JSON 格式输出 Reader 角色。
Get-AzRoleDefinition -Name "Reader" | ConvertTo-Json | Out-File C:\CustomRoles\ReaderSupportRole.json在编辑器中打开 ReaderSupportRole.json 文件。
下面是 JSON 输出。 有关不同属性的信息,请参阅 Azure 自定义角色。
{
"Name": "Reader",
"Id": "acdd72a7-3385-48ef-bd42-f606fba81ae7",
"IsCustom": false,
"Description": "Lets you view everything, but not make any changes.",
"Actions": [
"*/read"
],
"NotActions": [],
"DataActions": [],
"NotDataActions": [],
"AssignableScopes": [
"/"
]
}
编辑 JSON 文件,以将
*/read", "Microsoft.Network/*/read", "Microsoft.Network/firewallPolicies/ruleCollectionGroups/write操作添加到“Actions”属性。 请确保在读取操作后包括一个逗号。 此操作允许用户创建和更新规则集合组。
在“AssignableScopes”中,采用以下格式添加订阅 ID。
/subscriptions/xxxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxxxx必须添加显式订阅 ID。 否则不允许你将角色导入订阅。
删除 Id 属性行,并将 IsCustom 属性更改为 true。
将“Name”和“Description”属性更改为“AZFM 规则集合组作者”和“具有此角色的用户可以编辑防火墙策略规则集合组”
JSON 文件应类似于以下示例:
{
"Name": "AZFM Rule Collection Group Author",
"IsCustom": true,
"Description": "Users in this role can edit Firewall Policy rule collection groups",
"Actions": [
"*/read",
"Microsoft.Network/*/read",
"Microsoft.Network/firewallPolicies/ruleCollectionGroups/write"
],
"NotActions": [
],
"DataActions": [
],
"NotDataActions": [
],
"AssignableScopes": [
"/subscriptions/xxxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxxxx"]
}
若要新建自定义角色,请使用 New-AzRoleDefinition 命令,并指定 JSON 角色定义文件。
New-AzRoleDefinition -InputFile "C:\CustomRoles\RuleCollectionGroupRole.json
列出自定义角色
若要列出所有自定义角色,可以使用 Get-AzRoleDefinition 命令:
Get-AzRoleDefinition | ? {$_.IsCustom -eq $true} | FT Name, IsCustom
还可以在 Azure 门户中查看自定义角色。 转到你的订阅,选择“访问控制(IAM)”、“角色” 。
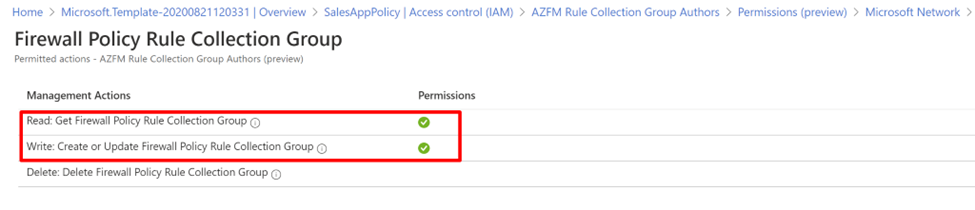
将用户添加到自定义角色
在门户中,可以将用户添加到“AZFM 规则集合组作者”角色,并提供对防火墙策略的访问权限。
- 从门户中选择应用程序团队防火墙策略(例如,SalesAppPolicy)。
- 选择“访问控制”。
- 选择“添加角色分配”。
- 将用户/用户组(例如,销售团队)添加到该角色。
对其他防火墙策略重复此过程。
总结
具有自定义角色的防火墙策略现在提供对防火墙策略规则集合组的选择性访问。
用户无权执行以下操作:
- 删除 Azure 防火墙或防火墙策略。
- 更新防火墙策略层次结构、DNS 设置或威胁情报。
- 如果他们不是“AZFM 规则集合组作者”组的成员,则无权更新防火墙策略。
安全管理员可以使用基本策略强制实施防护措施,并根据企业要求阻止某些类型的流量(例如 ICMP)。