可以将 Azure 防火墙与公共或内部 Azure 标准负载均衡器集成到虚拟网络中。
首选设计是将内部负载均衡器与 Azure 防火墙配合使用,因为它简化了设置。 如果已部署公共负载均衡器并希望继续使用它,请注意可能会中断功能的潜在非对称路由问题。
有关 Azure 负载均衡器的详细信息,请参阅什么是 Azure 负载均衡器?
公共负载均衡器
使用公共负载均衡器时,部署的负载均衡器使用公共前端 IP 地址。
非对称路由
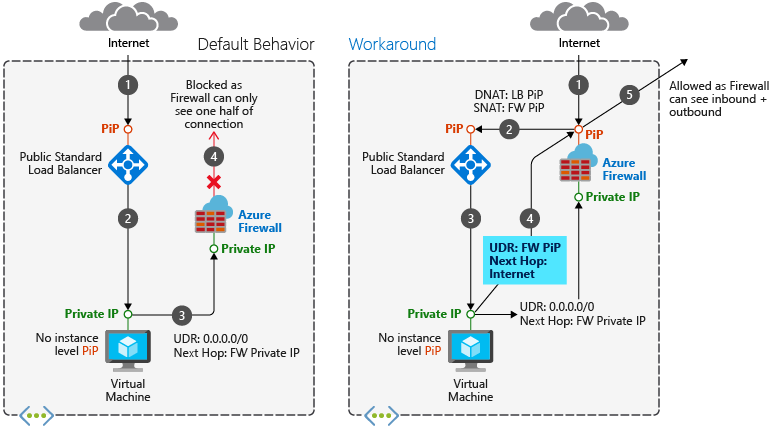
非对称路由是指数据包采用一条路径发往目标,并采用另一条路径返回到源。 当子网的默认路由指向防火墙的专用 IP 地址,并且您使用的是公共负载均衡器时,会出现此问题。 在这种情况下,传入的负载均衡器流量通过其公共 IP 地址接收,但返回路径则通过防火墙的私有 IP 地址。 由于防火墙是有状态的,并且无法识别此类已建立的会话,因此会丢弃返回的数据包。
解决路由问题
方案 1:不使用 NAT 网关的 Azure 防火墙
将 Azure 防火墙部署到子网时,需要为子网创建默认路由。 此路由通过位于 AzureFirewallSubnet 的防火墙专用 IP 地址将数据包引导。 有关详细步骤,请参阅 使用 Azure 门户部署和配置 Azure 防火墙。 将防火墙集成到负载均衡器方案中时,请确保 Internet 流量通过防火墙的公共 IP 地址进入。 防火墙应用其规则并对数据包进行 NAT,然后将其发送到负载均衡器的公共 IP 地址。 当数据包到达防火墙的公共 IP 地址,但通过专用 IP 地址(使用默认路由)返回时,会出现此问题。
若要防止非对称路由,请为防火墙的公共 IP 地址添加特定路由。 针对防火墙的公共 IP 地址的数据包通过 Internet 定向,绕过到防火墙的专用 IP 地址的默认路由。
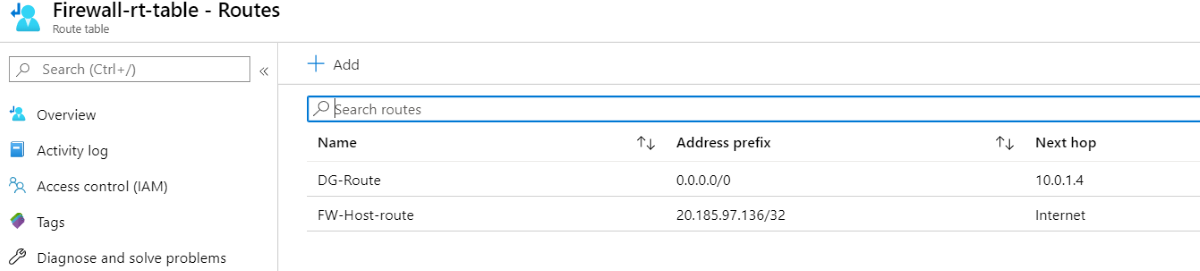
路由表示例
例如,以下路由表显示公共 IP 地址为 203.0.113.136 的防火墙的路由,专用 IP 地址为 10.0.1.4。
方案 2:使用 NAT 网关的 Azure 防火墙
在某些情况下,可以在 Azure 防火墙子网上配置 NAT 网关,以克服出站连接的 SNAT(源网络地址转换)端口限制。 在这些情况下,方案 1 中的路由配置不起作用,因为 NAT 网关的公共 IP 地址优先于 Azure 防火墙的公共 IP 地址。
有关详细信息,请参阅 NAT 网关与 Azure 防火墙的集成。
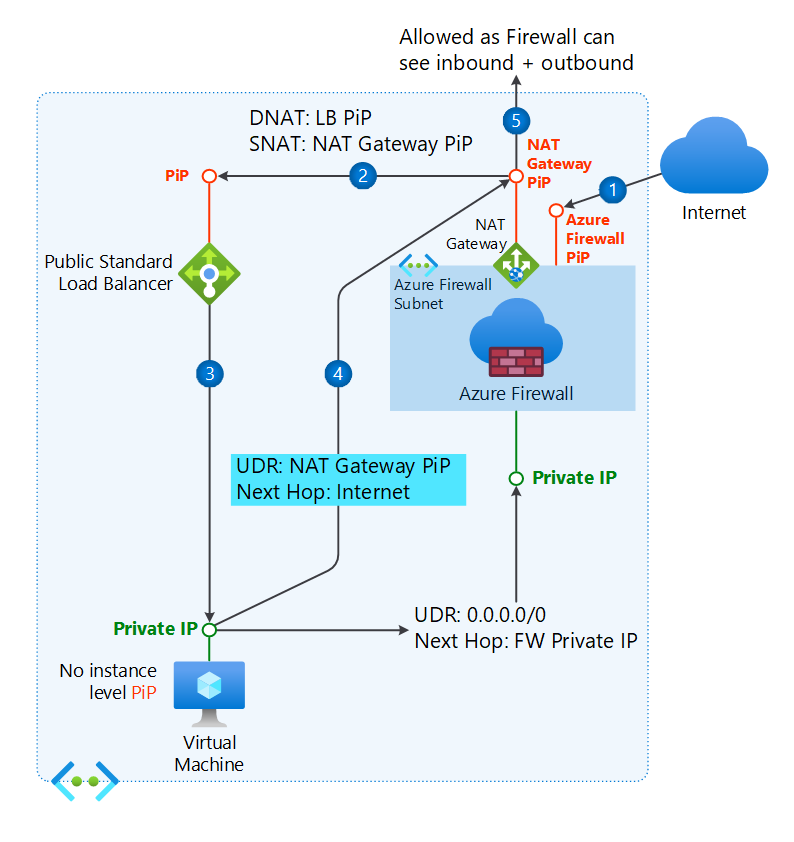
当 NAT 网关与 Azure 防火墙子网关联时,来自 Internet 的入站流量将登陆 Azure 防火墙的公共 IP 地址。 然后,Azure 防火墙将源 IP 更改为 NAT 网关的公共 IP 地址,然后将流量转发到负载均衡器的公共 IP 地址。
如果没有 NAT 网关,Azure 防火墙会将源 IP 地址更改为自己的公共 IP 地址,然后再将流量转发到负载均衡器的公共 IP 地址。
重要
请在与资源(AKS/VM)子网关联的网络安全组(NSG)规则中允许使用公共 IP 地址或公共前缀的 NAT 网关。
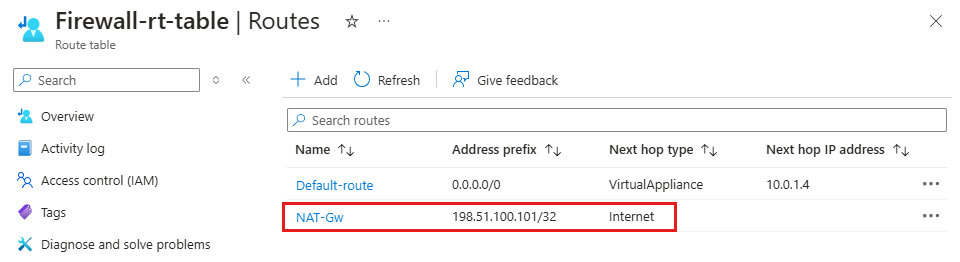
使用 NAT 网关的路由表示例
必须为返回路径添加路由,以使用 NAT 网关公共 IP 地址,而不是 Azure 防火墙公共 IP 地址,并将 Internet 作为下一跃点。
例如,以下路由表显示了具有公共 IP 地址为 198.51.100.101 的 NAT 网关的路由,以及具有专用 IP 地址为 10.0.1.4 的防火墙。
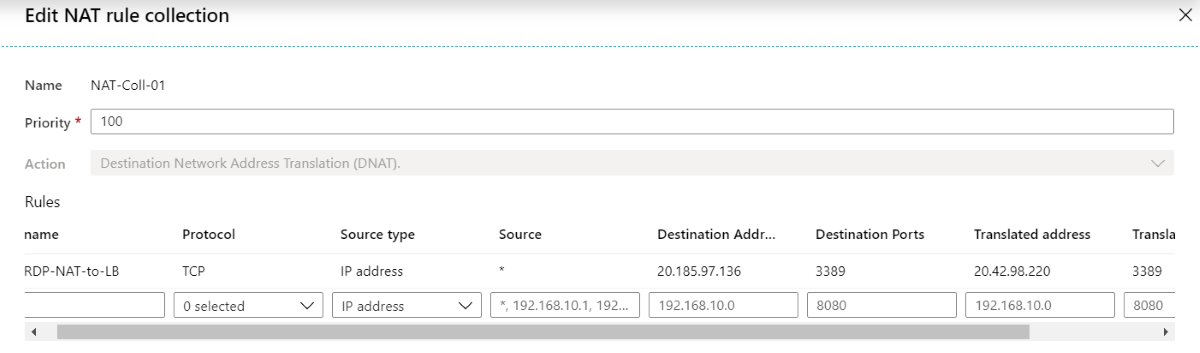
NAT 规则示例
在这两种情况下,NAT 规则会将来自防火墙的公共 IP 地址(203.0.113.136)的 RDP(远程桌面协议)流量转换为负载均衡器的公共 IP 地址(203.0.113.220):
运行状况探测
请记住,如果你对端口 80 使用 TCP(传输控制协议)运行状况探测,或者使用 HTTP/HTTPS 探测,则需要在负载均衡器池中的主机上运行 Web 服务。
内部负载均衡器
使用专用前端 IP 地址部署内部负载均衡器。
此方案没有非对称路由问题。 传入数据包到达防火墙的公共 IP 地址,将转换为负载均衡器的专用 IP 地址,并使用同一路径返回到防火墙的专用 IP 地址。
部署此方案类似于公共负载均衡器方案,但不需要防火墙公共 IP 地址主机路由。
后端池中的虚拟机可以通过 Azure 防火墙建立出站 Internet 连接。 在虚拟机子网上配置用户定义的路由,并将防火墙配置为下一跃点。
额外的安全性
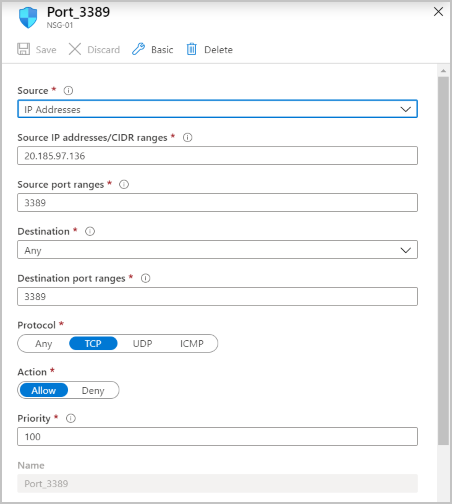
若要进一步增强负载均衡方案的安全性,请使用网络安全组(NSG)。
例如,在负载均衡虚拟机所在的后端子网上创建 NSG。 允许来自防火墙的公共 IP 地址和端口的传入流量。 如果 NAT 网关与 Azure 防火墙子网相关联,则允许来自 NAT 网关的公共 IP 地址和端口的传入流量。
有关 NSG 的详细信息,请参阅安全组。
后续步骤
- 了解如何部署和配置 Azure 防火墙。