可以为防火墙启用基于威胁情报的筛选,以提醒和拒绝来自/到达已知恶意 IP 地址、FQDN 和 URL 的流量。 IP 地址、域和 URL 来自 Microsoft 威胁情报源,其中包括多个来源,包括 Azure 网络安全团队。
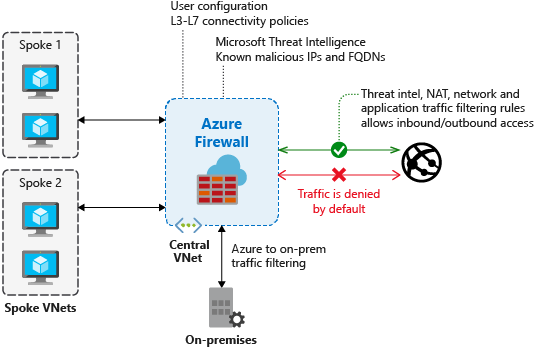
启用基于威胁情报的筛选后,Azure 防火墙会根据威胁情报规则评估流量,然后再应用 NAT、网络或应用程序规则。
管理员可以将防火墙配置为仅警报模式或警报和拒绝模式,当威胁情报规则被触发时采取相应行动。 默认情况下,防火墙以仅限警报模式运行。 此模式可以禁用或更改为警报和拒绝。
可以定义白名单,以排除威胁情报筛选的特定 FQDN、IP 地址、范围或子网。
对于批处理作,管理员可以上传包含 IP 地址、范围和子网的 CSV 文件,以填充允许列表。
日志
以下日志摘录显示了一个触发的规则:
{
"category": "AzureFirewallNetworkRule",
"time": "2018-04-16T23:45:04.8295030Z",
"resourceId": "/SUBSCRIPTIONS/{subscriptionId}/RESOURCEGROUPS/{resourceGroupName}/PROVIDERS/MICROSOFT.NETWORK/AZUREFIREWALLS/{resourceName}",
"operationName": "AzureFirewallThreatIntelLog",
"properties": {
"msg": "HTTP request from 10.0.0.5:54074 to somemaliciousdomain.com:80. Action: Alert. ThreatIntel: Bot Networks"
}
}
测试
出站测试 - 出站流量警报应该比较罕见,因为这意味着环境已遭到入侵。 为了帮助测试出站警报是否正常工作,存在触发警报的测试 FQDN。 将
testmaliciousdomain.chinaeast.cloudapp.chinacloudapi.cn用于出站测试。要准备测试并确保不会出现 DNS 解析失败,请配置以下各项:
- 将虚拟记录添加到测试计算机上的主机文件。 例如,在运行 Windows 的计算机上,可以将
1.2.3.4 testmaliciousdomain.chinaeast.cloudapp.chinacloudapi.cn添加到C:\Windows\System32\drivers\etc\hosts文件。 - 确保使用应用程序规则(而不是网络规则)允许测试的 HTTP/S 请求。
- 将虚拟记录添加到测试计算机上的主机文件。 例如,在运行 Windows 的计算机上,可以将
入站测试 - 如果在防火墙上配置了 DNAT 规则,则预计可以看到传入流量的警报。 即使防火墙仅允许 DNAT 规则上的特定源,并且流量被拒绝,你也会看到警报。 Azure 防火墙不会在所有已知的端口扫描仪上发出警报;仅在也会参与恶意活动的扫描仪上发出警报。