本文介绍:
- 可以为此服务收集的监视数据的类型。
- 如何分析这些数据。
如果具有依赖于 Azure 资源的关键应用程序和业务流程,则需要监视并获取系统的警报。 Azure Monitor 服务会从系统的每个组件收集并聚合指标和日志。 Azure Monitor 提供可用性、性能和复原能力视图,并在出现问题时向你发送通知。 可以使用 Azure 门户、PowerShell、Azure CLI、REST API 或客户端库来设置和查看监视数据。
- 有关 Azure Monitor 的详细信息,请参阅 Azure Monitor 概述。
- 有关监视 Azure 资源的常规方法的详细信息,请参阅使用 Azure Monitor 监视 Azure 资源。
可以使用 Azure 防火墙日志和指标来监视防火墙内的流量和操作。 这些日志和指标有几个基本用途,包括:
流量分析:使用日志检查和分析通过防火墙传递的流量。 此分析包括检查允许和拒绝的流量、检查源和目标 IP 地址、URL、端口号、协议等。 这些见解对于了解流量模式、识别潜在安全威胁和解决连接问题至关重要。
性能和运行状况指标:Azure 防火墙指标提供性能和运行状况指标,例如已处理的数据、吞吐量、规则命中计数和延迟。 监控这些指标以评估防火墙的整体健康状况、识别性能瓶颈并检测任何异常情况。
审核跟踪:活动日志允许对与防火墙资源相关的操作进行审核,捕获诸如创建、更新或删除防火墙规则和策略的操作。 查看活动日志有助于维护配置更改的历史记录,并确保符合安全和审核要求。
资源类型
Azure 使用资源类型和 ID 的概念来标识订阅中的所有内容。 同样的,Azure Monitor 根据资源类型(也称为“命名空间”)将核心监视数据组织为指标和日志。 不同的指标和日志可用于不同的资源类型。 服务可能与多种资源类型关联。
资源类型也是 Azure 中运行的每个资源的资源 ID 的一部分。 例如,虚拟机的一种资源类型是 Microsoft.Compute/virtualMachines。 有关服务及其关联资源类型的列表,请参阅资源提供程序。
有关 Azure 防火墙的资源类型的详细信息,请参阅 Azure 防火墙监视数据参考。
数据存储
对于 Azure Monitor:
- 指标数据存储在 Azure Monitor 指标数据库中。
- 日志数据存储在 Azure Monitor 日志存储中。 Log Analytics 是 Azure 门户中可以查询此存储的工具。
- Azure 活动日志是一个单独的存储区,在 Azure 门户中有自己的接口。
- 可选择将指标和活动日志数据路由到 Azure Monitor 日志数据库存储,以便可使用 Log Analytics 查询数据并将其与其他日志数据关联。
有关 Azure Monitor 如何存储数据的详细信息,请参阅 Azure Monitor 数据平台。
Azure Monitor 平台指标
Azure Monitor 为大多数服务提供平台指标。 这些指标是:
- 针对每个命名空间单独定义。
- 存储在 Azure Monitor 时序指标数据库中。
- 轻量级且具备支持准实时警报的能力。
- 用于跟踪资源随时间推移的性能变化。
集合:Azure Monitor 会自动收集平台指标。 不需要任何配置。
路由:通常还可将平台指标路由到 Azure Monitor 日志/Log Analytics,从而可以使用其他日志数据对其进行查询。 有关详细信息,请参阅指标诊断设置。 有关如何为服务配置诊断设置,请参阅在 Azure Monitor 中创建诊断设置。
有关可以为 Azure Monitor 中的所有资源收集的所有指标的列表,请参阅 Azure Monitor 中支持的指标。
有关 Azure 防火墙可用指标的列表,请参阅 Azure 防火墙监视数据参考。
Azure Monitor 资源日志
借助资源日志,可以深入了解 Azure 资源已执行的操作。 日志是自动生成的,但必须将日志路由到 Azure Monitor 日志以保存或查询它们。 日志按类别组织。 给定的命名空间可能具有多个资源日志类别。
收集:在创建诊断设置并将日志路由到一个或多个位置之前,不会收集和存储资源日志。 创建诊断设置时,指定要收集的日志类别。 可以通过多种方式创建和维护诊断设置,包括 Azure 门户、编程方式以及通过 Azure Policy。
路由:建议的默认设置是将资源日志路由到 Azure Monitor 日志,以便可以使用其他日志数据查询它们。 其他位置(例如 Azure 存储、Azure 事件中心和某些 Azure 监视合作伙伴)也可用。 有关详细信息,请参阅 Azure 资源日志和资源日志目标。
有关收集、存储和路由资源日志的详细信息,请参阅 Azure Monitor 中的诊断设置。
有关 Azure Monitor 中所有可用资源日志类别的列表,请参阅 Azure Monitor 中支持的资源日志。
Azure Monitor 中的所有资源日志都具有相同的标头字段,后跟特定于服务的字段。 Azure Monitor 资源日志架构中概述了通用架构。
有关可用的资源日志类别、其关联的 Log Analytics 表和 Azure 防火墙的日志架构,请参阅 Azure 防火墙监视数据参考。
Azure 防火墙工作簿 为 Azure 防火墙数据分析提供了灵活的画布。 该画布可用于在 Azure 门户中创建丰富的视觉对象报表。 你可以利用跨 Azure 部署的多个防火墙,并将其组合成统一的交互式体验。
还可以连接到存储帐户并检索访问和性能日志的 JSON 日志条目。 下载 JSON 文件后,可以将其转换为 CSV 并在 Excel、Power BI 或任何其他数据可视化工具中查看。
小窍门
如果你熟悉 Visual Studio 以及 C# 中常量和变量更改值的基本概念,则可以使用 GitHub 中提供的 日志转换器工具 。
Azure 活动日志
活动日志包含订阅级事件,这些事件跟踪从资源外部看到的每个 Azure 资源的操作;例如,创建新资源或启动虚拟机。
收集:活动日志事件会自动生成并收集在单独的存储中,以便在 Azure 门户中查看。
路由:可将活动日志数据发送到 Azure Monitor 日志,以便可以将它们与其他日志数据一起进行分析。 其他位置(例如 Azure 存储、Azure 事件中心和某些 Azure 监视合作伙伴)也可用。 有关如何路由活动日志的详细信息,请参阅 Azure 活动日志概述。
结构化的 Azure 防火墙日志
结构化日志是一种以特定格式组织的日志数据。 它们使用预定义的架构来构建日志数据,使其易于搜索、筛选和分析。 与由自由格式文本组成的非结构化日志不同,结构化日志具有计算机可以解析和分析的一致格式。
Azure 防火墙的结构化日志提供了防火墙事件的更详细的视图。 其中包括源和目标 IP 地址、协议、端口号以及防火墙执行的操作等信息。 它们还包括更多元数据,例如事件时间和 Azure 防火墙实例的名称。
目前,以下诊断日志类别适用于 Azure 防火墙:
- 应用程序规则日志
- 网络规则日志
- DNS 代理日志
这些日志类别使用 Azure 诊断模式。 在此模式下, AzureDiagnostics 表中收集来自任何诊断设置的所有数据。
使用结构化日志,可以选择使用 特定于资源的表 ,而不是现有的 AzureDiagnostics 表。 如果需要这两组日志,则每个防火墙至少需要创建两个诊断设置。
“特定于资源”模式
在“特定于资源”模式下,将会根据在诊断设置中选择的每个类别,在所选工作区中创建各个表。 建议使用此方法,因为它:
- 将总体日志记录成本降低高达 80%。
- 大大简化日志查询中的数据处理程序。
- 简化发现架构及其结构的过程。
- 提升引入延迟和查询时间方面的性能。
- 允许对特定表授予 Azure RBAC 权限。
现在,“诊断设置”中提供了新的特定于资源的表,可以让你利用以下类别:
- 网络规则日志 - 包含所有网络规则日志数据。 数据平面和网络规则之间的每个匹配项都会创建一个日志条目,其中包含数据平面数据包和所匹配规则的属性。
- NAT 规则日志 - 包含所有 DNAT(目标网络地址转换)事件日志数据。 数据平面和 DNAT 规则之间的每个匹配项都会创建一个日志条目,其中包含数据平面数据包和所匹配规则的属性。 请注意,AZFWNATRule 表仅在发生 DNAT 规则匹配时记录。 如果没有匹配项,则不会生成日志。
- 应用程序规则日志 - 包含所有应用程序规则日志数据。 数据平面和应用程序规则之间的每个匹配项都会创建一个日志条目,其中包含数据平面数据包和所匹配规则的属性。
- 威胁智能日志 - 包含所有威胁情报事件。
- IDPS 日志 - 包含与一个或多个 IDPS 签名匹配的所有数据平面数据包。
- DNS 代理日志 - 包含所有 DNS 代理事件日志数据。
- 内部 FQDN 解决失败日志 - 包含导致失败的所有内部防火墙 FQDN 解析请求。
- 应用程序规则聚合日志 - 包含策略分析的聚合应用程序规则日志数据。
- 网络规则聚合日志 - 包含策略分析的聚合网络规则日志数据。
- NAT 规则聚合日志 - 包含策略分析的聚合 NAT 规则日志数据。
- 顶级流日志 - 顶级流 (Fat Flow) 日志显示通过防火墙导致最高吞吐量的顶级连接。 有关详细信息,请参阅顶级流日志。
- 流跟踪 - 包含流信息、标志和记录流的时间段。 你能够看到完整的流信息,例如 SYN、SYN-ACK、FIN、FIN-ACK、RST、INVALID(流)。
启用结构化日志
若要启用 Azure 防火墙结构化日志,必须先在 Azure 订阅中配置 Log Analytics 工作区。 此工作区用于存储 Azure 防火墙生成的结构化日志。
配置 Log Analytics 工作区后,可以通过导航到 Azure 门户中防火墙的 “诊断设置 ”页,在 Azure 防火墙中启用结构化日志。 在此处,必须选择 特定于资源 的目标表,然后选择要记录的事件类型。
注释
- 若要启用 Azure 防火墙 Fat Flow 日志(顶级流日志),需要通过 Azure PowerShell 对其进行配置。 有关详细信息,请参阅顶级流日志。
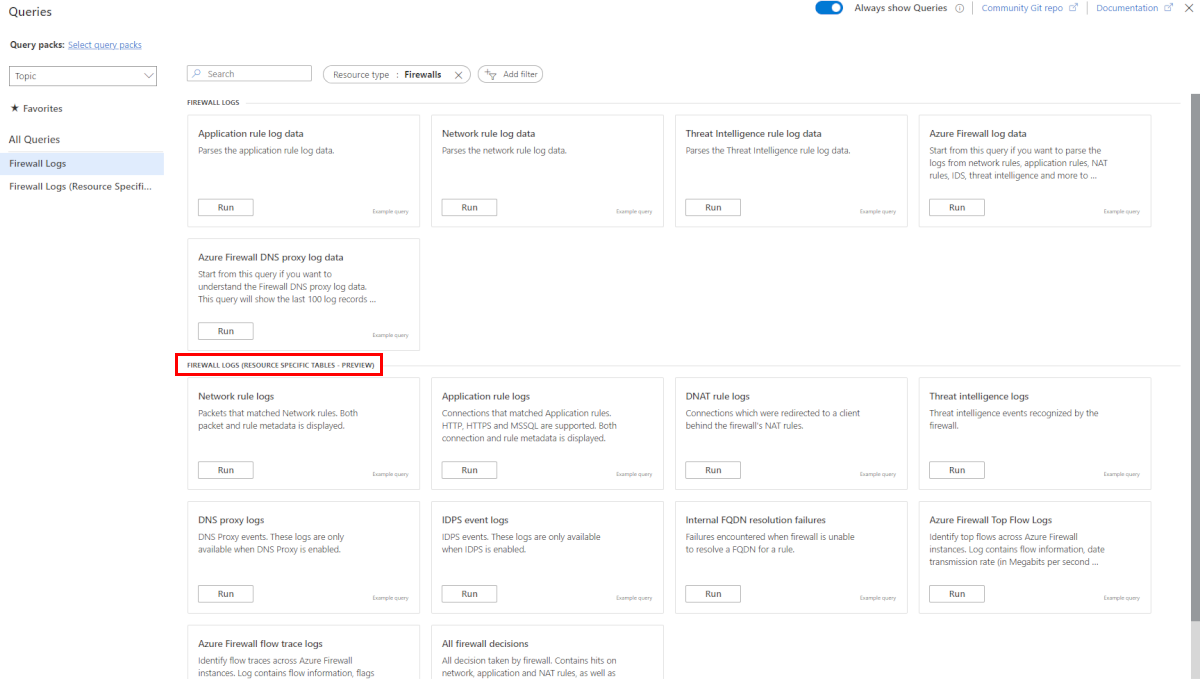
结构化日志查询
Azure 门户中提供了预定义查询的列表。 此列表具有针对每个类别的预定义 KQL(Kusto 查询语言)日志查询,以及在单个视图中显示整个 Azure 防火墙日志记录事件的联接查询。
Azure 防火墙工作簿
Azure 防火墙工作簿 为 Azure 防火墙数据分析提供了灵活的画布。 该画布可用于在 Azure 门户中创建丰富的视觉对象报表。 你可以利用跨 Azure 部署的多个防火墙,并将它们组合成统一的交互式体验。
若要部署使用 Azure 防火墙结构化日志的新工作簿,请参阅 适用于 Azure 防火墙的 Azure Monitor 工作簿。
旧版 Azure 诊断日志
旧版 Azure 诊断日志是原始 Azure 防火墙日志查询,以非结构化或自由格式文本格式输出日志数据。 Azure 防火墙旧日志类别使用 Azure 诊断模式,在 AzureDiagnostics 表中收集整个数据。 如果同时需要结构化日志和诊断日志,则每个防火墙至少需要创建两个诊断设置。
诊断日志支持以下日志类别:
- Azure 防火墙应用程序规则
- Azure 防火墙网络规则
- Azure 防火墙 DNS 代理
若要了解如何使用 Azure 门户启用诊断日志记录,请参阅 “启用结构化日志”。
应用程序规则日志
仅当为每个 Azure 防火墙启用了应用程序规则日志时,才会将此日志保存到存储帐户、流式传输到事件中心和/或发送到 Azure Monitor 日志。 每当建立与某个配置的应用程序规则匹配的新连接,就会为接受/拒绝的连接生成一条日志。 如以下示例中所示,数据以 JSON 格式记录:
Category: application rule logs.
Time: log timestamp.
Properties: currently contains the full message.
note: this field will be parsed to specific fields in the future, while maintaining backward compatibility with the existing properties field.
{
"category": "AzureFirewallApplicationRule",
"time": "2018-04-16T23:45:04.8295030Z",
"resourceId": "/SUBSCRIPTIONS/{subscriptionId}/RESOURCEGROUPS/{resourceGroupName}/PROVIDERS/MICROSOFT.NETWORK/AZUREFIREWALLS/{resourceName}",
"operationName": "AzureFirewallApplicationRuleLog",
"properties": {
"msg": "HTTPS request from 10.1.0.5:55640 to mydestination.com:443. Action: Allow. Rule Collection: collection1000. Rule: rule1002"
}
}
{
"category": "AzureFirewallApplicationRule",
"time": "2018-04-16T23:45:04.8295030Z",
"resourceId": "/SUBSCRIPTIONS/{subscriptionId}/RESOURCEGROUPS/{resourceGroupName}/PROVIDERS/MICROSOFT.NETWORK/AZUREFIREWALLS/{resourceName}",
"operationName": "AzureFirewallApplicationRuleLog",
"properties": {
"msg": "HTTPS request from 10.11.2.4:53344 to www.bing.com:443. Action: Allow. Rule Collection: ExampleRuleCollection. Rule: ExampleRule. Web Category: SearchEnginesAndPortals"
}
}
网络规则日志
仅当为每个 Azure 防火墙启用了网络规则日志时,才会将此日志保存到存储帐户、流式传输到事件中心和/或发送到 Azure Monitor 日志。 每当建立与某个配置的网络规则匹配的新连接,就会为接受/拒绝的连接生成一条日志。 如以下示例中所示,数据以 JSON 格式记录:
Category: network rule logs.
Time: log timestamp.
Properties: currently contains the full message.
note: this field will be parsed to specific fields in the future, while maintaining backward compatibility with the existing properties field.
{
"category": "AzureFirewallNetworkRule",
"time": "2018-06-14T23:44:11.0590400Z",
"resourceId": "/SUBSCRIPTIONS/{subscriptionId}/RESOURCEGROUPS/{resourceGroupName}/PROVIDERS/MICROSOFT.NETWORK/AZUREFIREWALLS/{resourceName}",
"operationName": "AzureFirewallNetworkRuleLog",
"properties": {
"msg": "TCP request from 111.35.136.173:12518 to 13.78.143.217:2323. Action: Deny"
}
}
DNS 代理日志
仅当为每个 Azure 防火墙启用了 DNS 代理日志后,才会将此日志保存到存储帐户,流式传输到事件中心和/或发送到 Azure Monitor 日志。 此日志跟踪发送到使用 DNS 代理配置的 DNS 服务器的 DNS 消息。 如以下示例中所示,数据以 JSON 格式记录:
Category: DNS proxy logs.
Time: log timestamp.
Properties: currently contains the full message.
note: this field will be parsed to specific fields in the future, while maintaining backward compatibility with the existing properties field.
成功:
{
"category": "AzureFirewallDnsProxy",
"time": "2020-09-02T19:12:33.751Z",
"resourceId": "/SUBSCRIPTIONS/{subscriptionId}/RESOURCEGROUPS/{resourceGroupName}/PROVIDERS/MICROSOFT.NETWORK/AZUREFIREWALLS/{resourceName}",
"operationName": "AzureFirewallDnsProxyLog",
"properties": {
"msg": "DNS Request: 11.5.0.7:48197 - 15676 AAA IN md-l1l1pg5lcmkq.blob.core.chinacloudapi.cn. udp 55 false 512 NOERROR - 0 2.000301956s"
}
}
失败:
{
"category": "AzureFirewallDnsProxy",
"time": "2020-09-02T19:12:33.751Z",
"resourceId": "/SUBSCRIPTIONS/{subscriptionId}/RESOURCEGROUPS/{resourceGroupName}/PROVIDERS/MICROSOFT.NETWORK/AZUREFIREWALLS/{resourceName}",
"operationName": "AzureFirewallDnsProxyLog",
"properties": {
"msg": " Error: 2 time.windows.com.reddog.microsoft.com. A: read udp 10.0.1.5:49126->168.63.129.160:53: i/o timeout"
}
}
消息格式:
[client's IP address]:[client's port] - [query ID] [type of the request] [class of the request] [name of the request] [protocol used] [request size in bytes] [EDNS0 DO (DNSSEC OK) bit set in the query] [EDNS0 buffer size advertised in the query] [response CODE] [response flags] [response size] [response duration]
分析监视数据
有许多工具可用于分析监视数据。
Azure Monitor 工具
Azure Monitor 支持以下基本工具:
指标资源管理器,它是 Azure 门户中的工具,可用于查看和分析 Azure 资源的指标。 有关详细信息,请参阅使用 Azure Monitor 指标资源管理器分析指标。
Log Analytics 是 Azure 门户中的一种工具,可用于使用 Kusto 查询语言(KQL)查询和分析日志数据。 有关详细信息,请参阅 Azure Monitor 日志查询入门。
活动日志,该日志在 Azure 门户中具有用于查看和基本搜索的用户界面。 要进行更深入的分析,必须将数据路由到 Azure Monitor 日志,并在 Log Analytics 中运行更复杂的查询。
支持更复杂可视化效果的工具包括:
- 仪表板,它支持将不同类型的数据合并到 Azure 门户的单个窗格中。
- 工作簿、可在 Azure 门户中创建的可自定义报表。 工作簿可以包括文本、指标和日志查询。
- Power BI 是一项业务分析服务,可跨各种数据源提供交互式可视化效果。 可将 Power BI 配置为自动从 Azure Monitor 导入日志数据,以利用这些可视化效果。
Azure Monitor 导出工具
可以使用以下方法将数据从 Azure Monitor 中提取到其他工具中:
指标:使用适用于指标的 REST API 从 Azure Monitor 指标数据库提取指标数据。 API 支持使用筛选表达式优化检索到的数据。 有关详细信息,请参阅 Azure Monitor REST API 参考。
日志: 使用 REST API 或 相关的客户端库。
要开始使用适用于 Azure Monitor 的 REST API,请参阅 Azure 监视 REST API 演练。
Kusto 查询
可使用 Kusto 查询语言 (KQL) 来分析 Azure Monitor 日志/Log Analytics 存储中的监视数据。
重要
在门户的服务菜单中选择“日志”时,会打开 Log Analytics,并且其查询范围设置为当前服务。 此范围意味着日志查询将仅包含来自该资源类型的数据。 如果希望运行的查询包含来自其他 Azure 服务的数据,请从“Azure Monitor”菜单中选择“日志”。 有关详细信息,请参阅 Azure Monitor Log Analytics 中的日志查询范围和时间范围。
有关任何服务的常见查询列表,请参阅 Log Analytics 查询接口。
警报
在监视数据中发现特定情况时,Azure Monitor 警报会主动向你发出通知。 有了警报,你就可以在客户注意到你的系统中的问题之前找出和解决问题。 有关详细信息,请参阅 Azure Monitor 警报。
Azure 资源的常见警报具有许多来源。 有关 Azure 资源常见警报的示例,请参阅示例日志警报查询。 Azure Monitor 基线警报 (AMBA) 站点提供了 Azure 登陆区域 (ALZ) 场景的关键警报指标、仪表板和指南。
通用警报模式对 Azure Monitor 警报通知的使用体验进行了标准化。 有关详细信息,请参阅 常见警报架构。
警报类型
可以在 Azure Monitor 数据平台中针对任何指标或日志数据源发出警报。 警报具有许多不同类型,具体取决于要监视的服务以及要收集的监视数据。 不同类型的警报各有优缺点。 有关详细信息,请参阅选择正确的监视警报类型。
以下列表介绍了可以创建的 Azure Monitor 警报类型:
- 指标警报会定期评估资源指标。 指标可以是平台指标、自定义指标、Azure Monitor 中的日志转换为的指标或 Application Insights 指标。 指标警报还可以应用多个条件和动态阈值。
- 日志警报支持用户使用 Log Analytics 查询按照预定义的频率评估资源日志。
- 当发生匹配所定义条件的新活动日志事件时,会触发活动日志警报。 资源运行状况警报和服务运行状况警报是报告服务和资源运行状况的活动日志警报。
还可以为某些 Azure 服务创建以下类型的警报:
- Application Insights 资源上的智能检测警报会就 Web 应用程序中的潜在性能问题和故障异常自动向你发出警报。 可以在 Application Insights 资源上迁移智能检测,以便为不同的智能检测模块创建警报规则。
- Prometheus 警报:针对 Prometheus 指标的警报,这些指标存储在适用于 Prometheus 的 Azure Monitor 托管服务中。 该警报规则基于 PromQL,它是一种开源查询语言。 你的服务可能不支持此类型警报。 目前,Prometheus 用于具有来宾操作系统的有限服务集,例如 Azure 虚拟机和 Azure 容器实例。
- 对于某些 Azure 资源(包括虚拟机、Azure Kubernetes 服务 [AKS] 资源和 Log Analytics 工作区),提供了现成可用的建议警报规则。
监视多个资源
通过将相同的指标警报规则应用于同一 Azure 区域中的多个相同类型资源,可以进行大规模的监视。 将为每个受监视的资源发送单独通知。 有关支持的 Azure 服务和云,请参阅使用一个警报规则监视多个资源。
有关 Azure 防火墙指标的警报
指标提供用于跟踪资源运行状况的关键信号。 因此,请务必监视资源的指标并注意任何异常。 但是,如果 Azure 防火墙指标停止流动,该怎么办? 这可能表示潜在的配置问题或更不祥的情况,例如中断。 由于发布阻止 Azure 防火墙上传指标的默认路由或正常实例数下降到零,因此可能会发生缺失的指标。 在本节中,你将了解如何为 Log Analytics 工作区配置指标以及如何对缺失的指标发出警报。
将指标配置为 Log Analytics 工作区
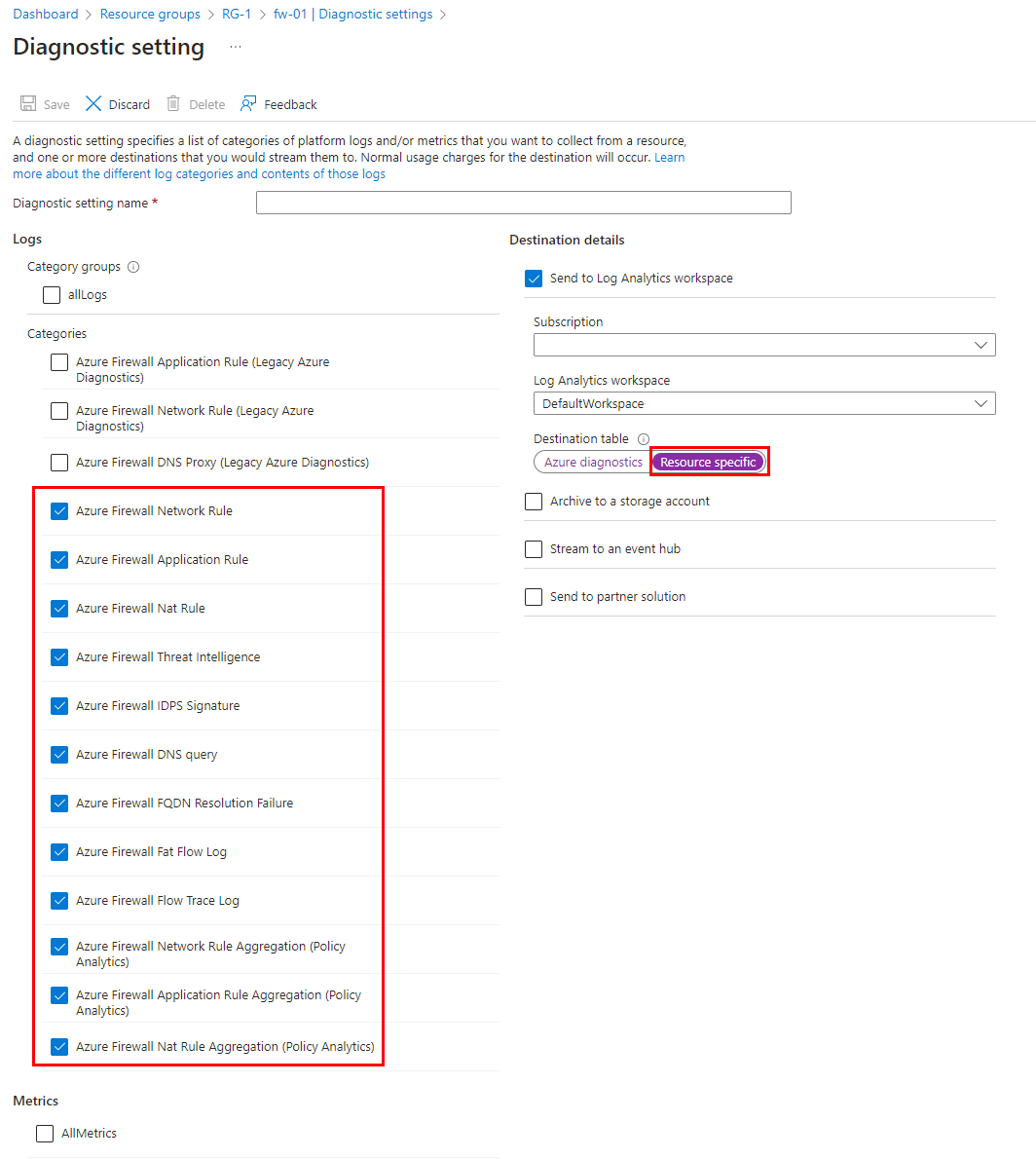
第一步是使用防火墙中的诊断设置配置 Log Analytics 工作区的指标可用性。
若要配置诊断设置,请浏览到 Azure 防火墙资源页,如以下屏幕截图所示。 这会将防火墙指标推送到配置的工作区。
注释
指标的诊断设置必须是与日志不同的配置。 防火墙日志可配置为使用 Azure 诊断或特定于资源。 但是,防火墙指标必须始终使用 Azure 诊断。
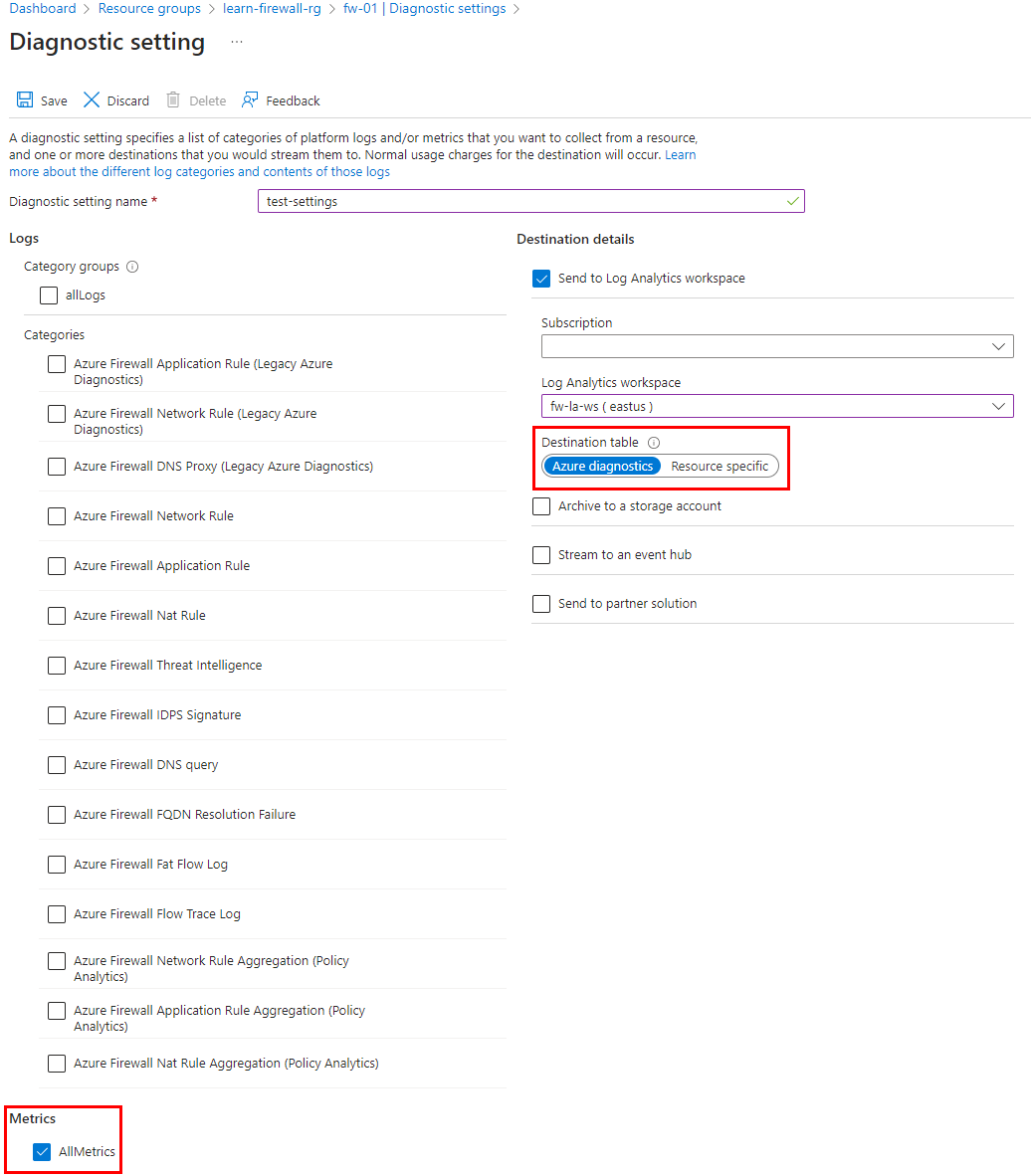
创建警报以跟踪接收防火墙指标而不发生任何故障
浏览到指标诊断设置中配置的工作区。 使用以下查询检查指标是否可用:
AzureMetrics
| where MetricName contains "FirewallHealth"
| where ResourceId contains "/SUBSCRIPTIONS/XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX/RESOURCEGROUPS/PARALLELIPGROUPRG/PROVIDERS/MICROSOFT.NETWORK/AZUREFIREWALLS/HUBVNET-FIREWALL"
| where TimeGenerated > ago(30m)
接下来,为 60 分钟内缺少的指标创建警报。 若要针对缺少的指标设置新警报,请浏览到 Log Analytics 工作区的警报页。
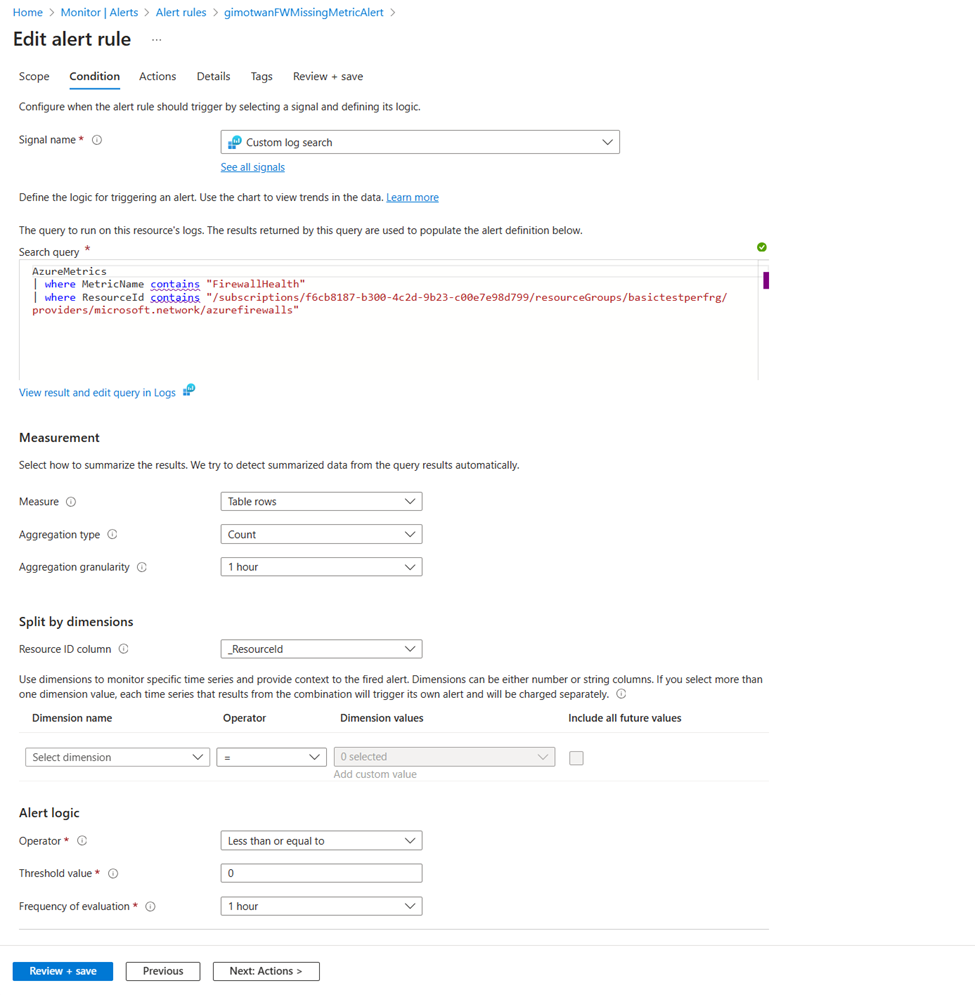
Azure 防火墙警报规则
可以为 Azure 防火墙监视数据参考中列出的任何指标、日志条目或活动日志条目设置警报。
顾问建议
如果在资源操作期间出现严重情况或即将发生变化,则门户中的“概述”页面上会显示一个警报。
可以在监控下的顾问建议中找到警报的详细信息和建议的修复措施。 在正常操作期间,不会显示任何顾问建议。
有关 Azure 顾问的详细信息,请参阅 Azure 顾问概述。
相关内容
- 有关为 Azure 防火墙创建的指标、日志和其他重要值的参考,请参阅 Azure 防火墙监视数据参考 。
- 有关监视 Azure 资源的一般详细信息,请参阅使用 Azure Monitor 监视 Azure 资源。