备注
你是否正在寻找 Microsoft 信息保护? Azure 信息保护统一标记客户端当前处于维护模式。 建议为 Office 365 应用程序启用 Microsoft 信息保护的内置标记功能。 了解详细信息。
本文介绍如何使用 Microsoft Purview 中的审核解决方案来查看 Azure 信息保护统一标记客户端生成的审核事件。 可在活动资源管理器中查看发送到 Microsoft 365 统一审核日志以用于中央报告的审核事件,这有助于跟踪用于对组织数据进行分类和保护的标签的采用情况。
通过审核,可以执行以下步骤:
- 从 Azure 信息保护客户端、Azure 信息保护扫描程序和 Microsoft Defender for Cloud 应用聚合数据。
- 在组织的 Microsoft 365 统一审核日志和 Office 365 活动日志中查看审核事件。
- 使用合规门户中的图形界面在活动资源管理器中查询、查看和检测审核事件。
Microsoft 365 统一审核日志中的审核事件
AIP 统一标记客户端包括 Office 加载项、扫描程序、Windows 查看器、客户端 PowerShell 和适用于 Windows 的分类保护 shell 扩展。 所有这些组件都会生成显示在 Office 365 活动日志中的审核事件,并可以使用 Office 365 管理活动 API 进行查询。
审核事件使管理员能够:
- 监视整个组织中带标签和受保护的文档和电子邮件。
- 监控用户对带标签文档和电子邮件的访问,并跟踪文档分类更改。
Microsoft 365 统一审核日志事件架构
下面列出了特定于 AIP 的五个事件(也称为“AuditLogRecordType”),有关每个事件的更多详细信息,请参阅 API 参考。
| 值 | 成员名称 | 说明 |
|---|---|---|
| 93 | AipDiscover | Azure 信息保护 (AIP) 扫描程序事件。 |
| 94 | AipSensitivityLabelAction | AIP 敏感度标签事件。 |
| 95 | AipProtectionAction | AIP 保护事件。 |
| 96 | AipFileDeleted | AIP 文件删除事件。 |
| 97 | AipHeartBeat | AIP 检测信号事件。 |
此信息可在组织的 Microsoft 365 统一审核日志中访问,并可在活动资源管理器中查看。
在活动资源管理器中查询审核事件
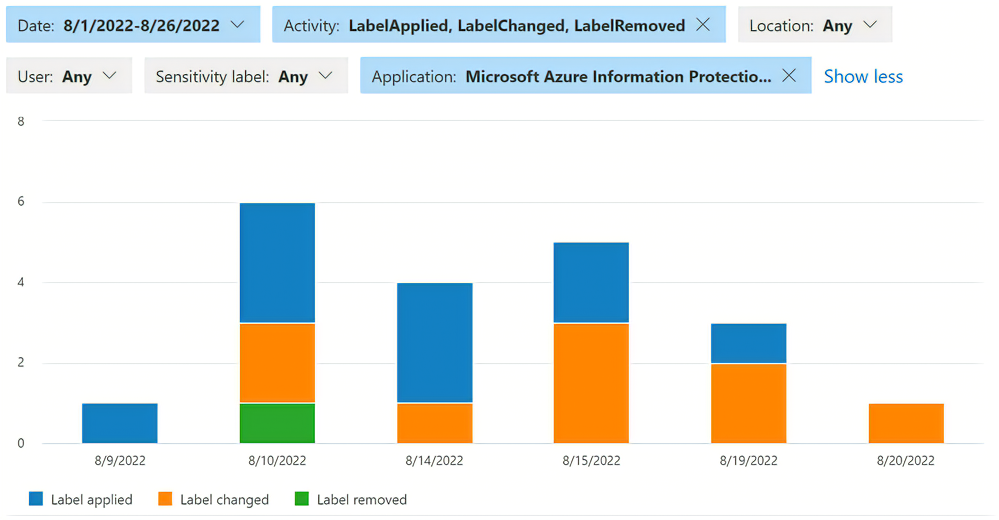
Microsoft Purview 合规门户中的活动资源管理器是一个图形界面,用于查看发送到 Microsoft 365 统一审核日志的审核事件。 租户的管理员可以使用内置查询来确定组织实现的策略和控制是否有效。 借助长达 30 天时间的可用数据,管理员可以设置筛选器,并清楚地了解在组织内处理敏感数据的时间和方式。
要查看特定于 AIP 的活动,管理员可以从以下筛选器开始:
- 活动类型:
- Label applied
- 更改的标签
- 已删除标签
- 标签文件读取
- 一个应用程序:
- Azure 信息保护 Word 加载项
- Azure 信息保护 Excel 加载项
- Azure 信息保护 PowerPoint 加载项
- Azure 信息保护 Outlook 加载项
管理员可能看不到筛选器中的所有选项,也可能会看到更多选项;筛选器值取决于为租户捕获的活动。 有关活动资源管理器的详细信息,请参阅:
从 AIP 统一标记客户端收集并发送到 Microsoft Purview 的信息
为了生成这些报告,终结点将以下信息类型发送给 Microsoft 365 统一审核日志:
标签操作。 例如,设置标签、更改标签、添加或删除保护、自动和建议的标签。
标签操作之前和之后的标签名称。
组织的租户 ID。
用户 ID(电子邮件地址或 UPN)。
用户设备的名称。
用户设备的 IP 地址。
相关进程名称,如 outlook 或 msip.app 。
执行标记的应用程序的名称,如 Outlook 或文件资源管理器
对于文档:被标记的文档的文件路径和文件名。
对于电子邮件:带标签的电子邮件的电子邮件主题和电子邮件发件人。
在内容中已检测到的敏感信息类型(预定义和自定义)。
Azure 信息保护客户端版本。
客户端操作系统版本。
阻止 AIP 客户端发送审核数据
若要阻止 Azure 信息保护统一标记客户端发送审核数据,请配置标签策略高级设置。
更深入分析的内容匹配项
Azure 信息保护使你可以收集和存储标识为敏感信息类型(预定义或自定义)的实际数据。 例如,这可以包括查找到的信用卡号码,以及社会安全号码、护照号码和银行帐户号码。 从“活动日志”中选择条目并查看“活动详细信息”时,会显示内容匹配项 。
默认情况下,Azure 信息保护客户端不发送内容匹配项。 若要更改此行为以发送内容匹配项,请在标签策略中配置一个高级设置。
先决条件
默认情况下会为组织启用审核事件。 要查看 Microsoft Purview 中的审核事件,请查看基本和审核(高级版)解决方案的许可要求。
后续步骤
查看报表中的信息后,你可能想详细了解如何为组织配置 Microsoft Purview 的审核解决方案。
- 了解如何使用 GitHub 上的 AIP 审核导出将审核事件从 Microsoft 365 统一审核日志导出到 Azure 日志分析工作区。
- 请阅读管理员指南:API 统一标记客户端的审核和报告,深入了解 Microsoft Purview 的审核解决方案。
- 查看保护使用情况日志文档,了解 Rights Management Service 生成的文件访问和拒绝事件。 这些事件是与 Azure 信息保护统一标记客户端生成的事件分开处理的。
- 请参考 Microsoft 365 文档中关于敏感度标签的内容,了解如何在合规门户中更改标记策略。