适用范围: Azure CLI ml 扩展 v2(最新版)
Azure CLI ml 扩展 v2(最新版) Python SDK azure-ai-ml v2(最新版)
Python SDK azure-ai-ml v2(最新版)
了解如何从 Azure CLI 或 Azure 机器学习 SDK v2 设置对 Azure 机器学习工作区的身份验证。 在大多数情况下,Azure 机器学习工作区的身份验证基于 Microsoft Entra ID。 通常,在连接到工作区时可使用 4 种身份验证工作流:
交互:你可以使用 Microsoft Entra ID 中的帐户直接进行身份验证,或者使用它来获取用于身份验证的令牌。 在试验和迭代开发期间,使用交互式身份验证。 借助交互式身份验证,可基于每位用户控制对资源(例如 Web 服务)的访问。
服务主体:在 Microsoft Entra ID 中创建一个服务主体帐户,并使用它来进行身份验证或获取令牌。 使用服务主体向服务自动进行身份验证,无需用户交互。 例如连续集成和部署脚本,它可以在训练代码每次发生更改时对模型进行训练和测试。
Azure CLI 会话:使用活动 Azure CLI 会话进行身份验证。 适用于机器学习的 Azure CLI 扩展(
ml扩展或 CLI v2)是用于使用 Azure 机器学习的命令行工具。 你可以通过本地工作站上的 Azure CLI 登录到 Azure,而无需在 Python 代码中存储凭据,也无需提示用户进行身份验证。 同样,你可以在持续集成和部署管道中重复使用相同的脚本,同时使用服务主体标识对 Azure CLI 进行身份验证。托管标识:在计算实例上或在 Azure 虚拟机上使用 Azure 机器学习 SDK v2 时,可使用 Azure 的托管标识。 此工作流允许 VM 使用托管标识连接到工作区,无需在 Python 代码中存储凭据或提示用户进行身份验证。 训练模型时,还可配置 Azure 机器学习计算群集来使用托管标识访问工作区。
无论使用何种身份验证工作流,都可使用 Azure 基于角色的访问控制 (Azure RBAC) 来限定允许拥有的资源访问权限(授权)级别。 例如,管理员或自动化过程可能具有创建计算实例的权限,但不使用此权限。 而数据科学家可能会使用它,但不能删除或创建此权限。 有关详细信息,请参阅管理对 Azure 机器学习工作区的访问权限。
Microsoft Entra 条件访问可用于进一步控制或限制对每个身份验证工作流的工作区的访问。 例如,管理员可以仅允许从托管设备访问工作区。
先决条件
Python 3.10 或更高版本。
创建 Azure 机器学习工作区。
安装 Azure CLI。
Microsoft Entra ID
工作区的所有身份验证工作流都依赖于 Microsoft Entra ID。 如果希望用户使用个人帐户进行身份验证,这些用户必须在 Microsoft Entra ID 中有帐户。 如果希望使用服务主体,这些主体必须位于 Microsoft Entra ID 中。 托管标识也是 Microsoft Entra ID 的一项功能。
有关 Microsoft Entra ID 的详细信息,请参阅什么是 Microsoft Entra 身份验证。
创建 Microsoft Entra 帐户后,请参阅管理对 Azure 机器学习工作区的访问权限,了解如何在 Azure 机器学习中授予帐户对工作区和其他操作的访问权限。
使用交互式身份验证
适用范围: Python SDK azure-ai-ml v2(最新版)
Python SDK azure-ai-ml v2(最新版)
交互式身份验证使用适用于 Python 的 Azure 标识包。 可通过多种方式以交互方式进行身份验证,但大多数示例都使用 DefaultAzureCredential,因为它可以处理大多数身份验证场景。
DefaultAzureCredential 类依次使用多种方法(EnvironmentCredential、ManagedIdentityCredential、SharedTokenCacheCredential、VisualStudioCodeCredential、AzureCliCredential 和 AzurePowerShellCredential),当其中一种方法提供令牌时停止。 有关详细信息,请参阅 DefaultAzureCredential 类引用。
以下代码是使用 DefaultAzureCredential 进行身份验证的示例。 如果使用 DefaultAzureCredential 进行身份验证失败,则会改用通过 Web 浏览器进行身份验证的后备方案。
from azure.identity import DefaultAzureCredential, InteractiveBrowserCredential
try:
credential = DefaultAzureCredential()
# Check if given credential can get token successfully.
credential.get_token("https://management.chinacloudapi.cn/.default")
except Exception as ex:
# Fall back to InteractiveBrowserCredential in case DefaultAzureCredential not work
# This will open a browser page for
credential = InteractiveBrowserCredential()
创建凭据对象后,使用 MLClient 类连接到工作区。 例如,以下代码使用 from_config() 方法加载连接信息:
from azure.ai.ml import MLClient
try:
ml_client = MLClient.from_config(credential=credential)
except Exception as ex:
# NOTE: Update following workspace information to contain
# your subscription ID, resource group name, and workspace name
client_config = {
"subscription_id": "<SUBSCRIPTION_ID>",
"resource_group": "<RESOURCE_GROUP>",
"workspace_name": "<AZUREML_WORKSPACE_NAME>",
}
# write and reload from config file
import json, os
config_path = "../.azureml/config.json"
os.makedirs(os.path.dirname(config_path), exist_ok=True)
with open(config_path, "w") as fo:
fo.write(json.dumps(client_config))
ml_client = MLClient.from_config(credential=credential, path=config_path)
print(ml_client)
配置服务主体
若要使用服务主体 (SP),必须首先创建 SP。 然后授予它访问工作区的权限。 如前文所述,将使用 Azure 基于角色的访问控制 (Azure RBAC) 来控制访问,因此你还必须确定要授予 SP 的访问权限。
重要
使用服务主体时,请向它授予它所用于的任务所需的最低访问权限。 例如,如果服务主体仅用于读取 Web 部署的访问令牌,则不要向服务主体授予所有者或参与者访问权限。
授予最低访问权限的原因是服务主体使用密码进行身份验证,并且该密码可以存储为自动化脚本的一部分。 如果密码泄露,则特定任务所需的最低访问权限可最大程度地减少 SP 的恶意使用。
创建 SP 并向其授予对工作区的访问权限的最简单方法是使用 Azure CLI。 若要创建服务主体并向其授予对工作区的访问权限,请执行以下步骤:
注意
你必须是订阅的管理员才能执行所有这些步骤。
对 Azure 订阅进行身份验证:
az login如果 CLI 可以打开默认的浏览器,则会打开该浏览器并加载登录页面。 否则,需要打开浏览器并按照命令行中的说明操作。 按说明操作时,需要浏览到 https://aka.ms/deviceloginchina 并输入授权代码。
如果你拥有多个 Azure 订阅,可使用
az account set -s <subscription name or ID>命令设置订阅。 有关详细信息,请参阅使用多个 Azure 订阅。有关其他身份验证方法,请参阅使用 Azure CLI 登录。
创建服务主体。 在以下示例中,将创建一个名为 ml-auth 的 SP:
az ad sp create-for-rbac --json-auth --name ml-auth --role Contributor --scopes /subscriptions/<subscription id>参数
--json-auth在 Azure CLI 版本 >= 2.51.0 中可用。 在此以前的版本使用--sdk-auth。输出是类似于以下内容的 JSON 文档。 记下
clientId、clientSecret和tenantId字段,因为在本文的其他步骤中需要用到这些信息。{ "clientId": "your-client-id", "clientSecret": "your-client-secret", "subscriptionId": "your-sub-id", "tenantId": "your-tenant-id", "activeDirectoryEndpointUrl": "https://login.partner.microsoftonline.cn", "resourceManagerEndpointUrl": "https://management.chinacloudapi.cn", "activeDirectoryGraphResourceId": "https://graph.chinacloudapi.cn", "sqlManagementEndpointUrl": "https://management.core.chinacloudapi.cn:5555", "galleryEndpointUrl": "https://gallery.chinacloudapi.cn/", "managementEndpointUrl": "https://management.core.chinacloudapi.cn" }使用上一步返回的
clientId值检索服务主体的详细信息:az ad sp show --id your-client-id下面的 JSON 是命令的输出的简化示例。 记下
objectId字段,因为在接下来的步骤中需要用到它的值。{ "accountEnabled": "True", "addIns": [], "appDisplayName": "ml-auth", ... ... ... "objectId": "your-sp-object-id", "objectType": "ServicePrincipal" }若要授予对 Azure 机器学习使用的工作区和其他资源的访问权限,请按以下文章中的要求操作:
重要
所有者访问权限允许服务主体在工作区中执行几乎所有操作。 本文档中使用它来演示如何授予访问权限;在生产环境中,Azure 建议仅向服务主体授予行使目标角色职能所需的最低访问权限。 若要了解如何创建具有方案所需的访问权限的自定义角色,请参阅管理对 Azure 机器学习工作区的访问权限。
配置托管标识
重要
仅当从 Azure 虚拟机、Azure 机器学习计算群集或计算实例使用 Azure 机器学习 SDK 时,才支持托管标识。
VM 的托管标识
在 Azure 门户中,选择工作区,然后选择“访问控制(IAM)”。
依次选择“添加”、“添加角色分配”,以打开“添加角色分配”页 。
选择要分配托管标识的角色。 例如,读取者。 有关详细步骤,请参阅使用 Azure 门户分配 Azure 角色。
计算群集的托管标识
有关详细信息,请参阅为计算群集设置托管标识。
计算实例的托管标识
有关详细信息,请参阅为计算实例设置托管标识。
使用服务主体身份验证
适用范围: Python SDK azure-ai-ml v2(最新版)
Python SDK azure-ai-ml v2(最新版)
通过服务主体进行身份验证使用适用于 Python 的 Azure 标识包。
DefaultAzureCredential 类查找以下环境变量,并在作为服务主体进行身份验证时使用这些值:
-
AZURE_CLIENT_ID- 创建服务主体时返回的客户端 ID。 -
AZURE_TENANT_ID- 创建服务主体时返回的租户 ID。 -
AZURE_CLIENT_SECRET- 为服务主体生成的密码/凭据。
提示
在开发过程中,请考虑使用 python-dotenv 包来设置这些环境变量。 python-dotenv 从 .env 文件加载环境变量。 Python 的标准 .gitignore 文件会自动排除 .env 文件,因此在开发期间不应将它们签入任何 GitHub 存储库。
以下示例演示了使用 python-dotenv 从 .env 文件加载环境变量,然后使用 DefaultAzureCredential 创建凭据对象:
from dotenv import load_dotenv
if ( os.environ['ENVIRONMENT'] == 'development'):
print("Loading environment variables from .env file")
load_dotenv(".env")
from azure.identity import DefaultAzureCredential
credential = DefaultAzureCredential()
# Check if given credential can get token successfully.
credential.get_token("https://management.chinacloudapi.cn/.default")
创建凭据对象后,使用 MLClient 类连接到工作区。 例如,以下代码使用 from_config() 方法加载连接信息:
try:
ml_client = MLClient.from_config(credential=credential)
except Exception as ex:
# NOTE: Update following workspace information to contain
# your subscription ID, resource group name, and workspace name
client_config = {
"subscription_id": "<SUBSCRIPTION_ID>",
"resource_group": "<RESOURCE_GROUP>",
"workspace_name": "<AZUREML_WORKSPACE_NAME>",
}
# write and reload from config file
import json, os
config_path = "../.azureml/config.json"
os.makedirs(os.path.dirname(config_path), exist_ok=True)
with open(config_path, "w") as fo:
fo.write(json.dumps(client_config))
ml_client = MLClient.from_config(credential=credential, path=config_path)
print(ml_client)
还可以使用服务主体向 Azure 机器学习 REST API 进行身份验证。 如果使用 Microsoft Entra ID 客户端凭据授予流,则可在自动化工作流中进行无外设身份验证的服务到服务调用。
重要
如果你当前正在使用 Azure Active Directory 身份验证库 (ADAL) 获取凭据,我们建议迁移到 Azure 身份验证库 (MSAL)。 ADAL 支持已于 2023 年 6 月 30 日结束。
有关使用 MSAL 进行身份验证的信息和示例,请参阅以下文章:
- JavaScript - 如何将 JavaScript 应用从 ADAL.js 迁移到 MSAL.js。
- Node.js - 如何将 Node.js 应用从 Azure 身份验证库迁移到 MSAL。
- Python - Microsoft 身份验证库到 Python 的 MSAL 迁移指南。
使用托管标识身份验证
适用范围: Python SDK azure-ai-ml v2(最新版)
Python SDK azure-ai-ml v2(最新版)
通过托管标识进行身份验证使用适用于 Python 的 Azure 标识包。 若要从配置有托管标识的 VM 或计算群集对工作区进行身份验证,请使用 DefaultAzureCredential 类。 此类自动检测是否正在使用托管标识,并使用托管标识对 Azure 服务进行身份验证。
以下示例演示了使用 DefaultAzureCredential 类创建凭据对象,然后使用 MLClient 类连接到工作区:
from azure.identity import DefaultAzureCredential
credential = DefaultAzureCredential()
# Check if given credential can get token successfully.
credential.get_token("https://management.chinacloudapi.cn/.default")
try:
ml_client = MLClient.from_config(credential=credential)
except Exception as ex:
# NOTE: Update following workspace information to contain
# your subscription ID, resource group name, and workspace name
client_config = {
"subscription_id": "<SUBSCRIPTION_ID>",
"resource_group": "<RESOURCE_GROUP>",
"workspace_name": "<AZUREML_WORKSPACE_NAME>",
}
# write and reload from config file
import json, os
config_path = "../.azureml/config.json"
os.makedirs(os.path.dirname(config_path), exist_ok=True)
with open(config_path, "w") as fo:
fo.write(json.dumps(client_config))
ml_client = MLClient.from_config(credential=credential, path=config_path)
print(ml_client)
使用条件访问
作为管理员,你可以为登录到工作区的用户强制实施 Microsoft Entra 条件访问策略。 例如,你可以要求双因素身份验证,或者仅允许从托管设备登录。 以下是用于条件访问的应用 ID:
| 应用程序 ID | 名称 | 注意 |
|---|---|---|
| d7304df8-741f-47d3-9bc2-df0e24e2071f | Azure Machine Learning Workbench Web 应用 | Azure 机器学习工作室 |
| cb2ff863-7f30-4ced-ab89-a00194bcf6d9 | Azure AI Foundry 应用 | Azure AI Foundry |
检查是否存在服务主体
在添加条件访问策略之前,请验证 Azure 门户的“企业应用程序”部分中是否列出了应用程序 ID:
重要
要执行本部分中的步骤,必须具有“Microsoft Entra ID P2”。 有关详细信息,请参阅 Microsoft Entra 授权。
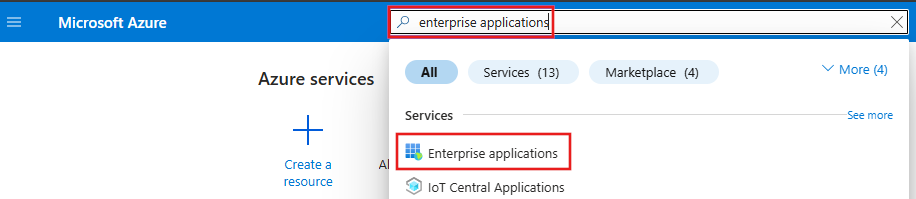
在门户顶部的搜索字段中搜索“企业应用程序”,然后选择企业应用程序条目。
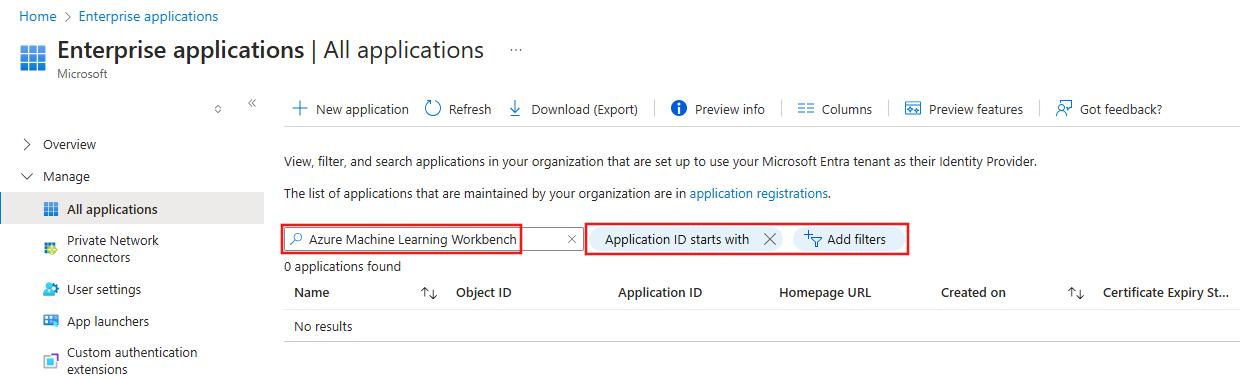
在“企业应用程序”中,使用“按应用程序名称或对象 ID 搜索”字段来搜索要用于条件访问的条目。 如果显示一个条目,则表明应用程序 ID 已存在服务主体。 跳过本部分中的其余步骤,然后转到“添加条件访问”部分。
重要
唯一的筛选器应是“应用程序 ID 开头为”。 删除可能存在的任何其他筛选器。
如果未显示任何条目,则使用以下 Azure PowerShell cmdlet 为应用程序 ID 创建服务主体:
New-AzAdServicePrincipal -ApplicationId "application-ID"例如
New-AzADServicePrincipal -ApplicationId "d7304df8-741f-47d3-9bc2-df0e24e2071f"。创建服务主体后,返回到“企业应用程序”,并验证现在能否找到应用程序 ID。 可以在使用条件访问部分中找到 ID 列表。
添加条件访问
要使用条件访问,请为应用程序 ID 分配条件访问策略。 如果应用程序未显示在条件访问中,请使用检查是否存在服务主体部分中的步骤。