重要
网络安全组(NSG)流日志将于 2027 年 9 月 30 日停用。 2025 年 6 月 30 日之后,将无法再创建新的 NSG 流日志。 建议迁移到虚拟网络流日志,这些日志解决了 NSG 流日志的限制。 退休日期后,将不再支持 NSG 流日志中启用的流量分析功能,订阅中的现有 NSG 流日志资源也将被删除。 但是,不会从 Azure 存储中删除现有的 NSG 流日志记录,并且将继续遵循其配置的保留策略。 有关详细信息,请查看官方公告。
网络安全组流日志记录是 Azure 网络观察程序的一项功能,可用于记录流经网络安全组的 IP 流量的相关信息。 有关网络安全组流日志记录的详细信息,请参阅 NSG 流日志概述。
本文介绍如何使用 Azure 门户、PowerShell 和 Azure CLI 创建、更改、启用、禁用或删除网络安全组流日志。
先决条件
注册洞察服务商
必须注册 Microsoft.Insights 提供程序才能成功记录流经虚拟网络的流量。 如果不确定是否已注册 Microsoft.Insights 提供程序,请按照以下步骤在 Azure 门户中检查其状态:
在门户顶部的搜索框中,输入“订阅”。 从搜索结果中选择“订阅”。
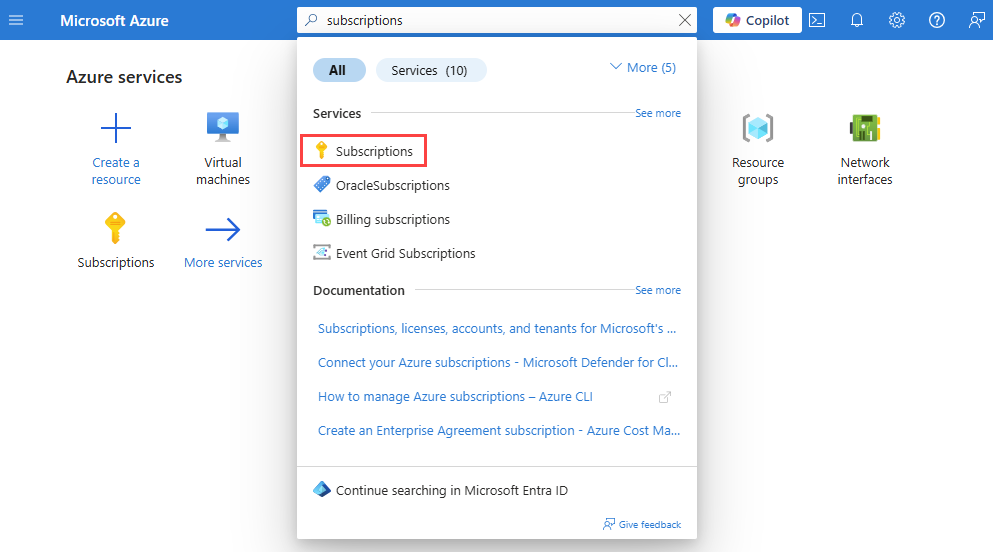
在“订阅”中,选择要为其启用提供程序的 Azure 订阅。
在“设置”下,选择“资源提供程序”。
在筛选器框中输入见解。
确认显示的提供程序状态为“已注册”。 如果状态为“NotRegistered”,请选择“Microsoft.Insights”提供程序,然后选择“注册”。

必须注册 Microsoft.Insights 提供程序才能成功记录虚拟网络中的流量。 如果不确定 Microsoft.Insights 提供者是否已注册,请使用 Register-AzResourceProvider 来注册它:
# Register Microsoft.Insights provider.
Register-AzResourceProvider -ProviderNamespace 'Microsoft.Insights'
必须注册 Microsoft.Insights 提供程序才能成功记录虚拟网络中的流量。 如果您不确定 Microsoft.Insights 提供程序是否已注册,请使用 az provider register 进行注册:
# Register Microsoft.Insights provider.
az provider register --namespace 'Microsoft.Insights'
创建流日志
为网络安全组创建流日志。 流日志保存在 Azure 存储帐户中。
在门户顶部的搜索框中,输入网络监视工具。 在搜索结果中,选择“网络监视器”。
在“日志”下,选择“流日志”。
在“网络观察程序 | 流日志”,选择“+ 创建”或“创建流日志”蓝色按钮。
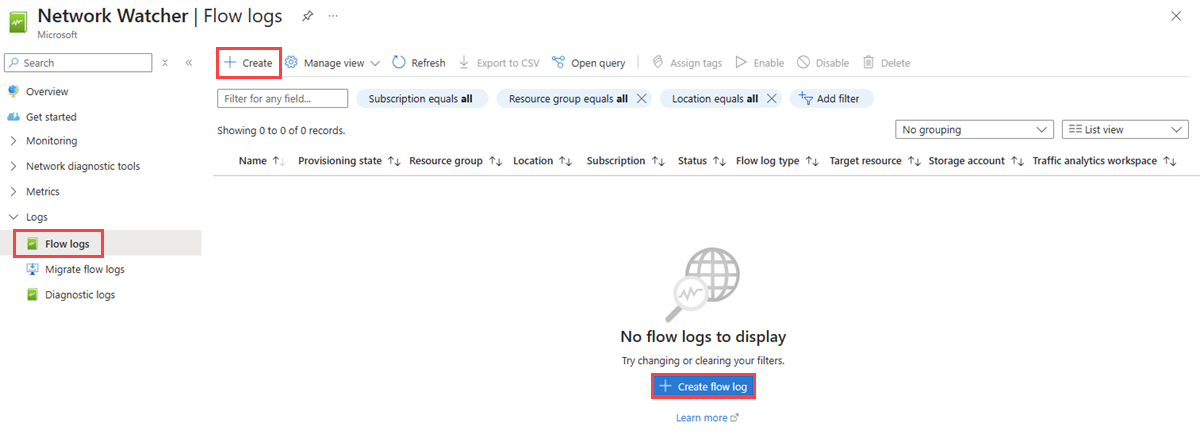
在“创建流日志”的“基本信息”选项卡上,输入或选择以下值:
| 设置 |
价值 |
|
项目详细信息 |
|
| 订阅 |
选择要记录的网络安全组的 Azure 订阅。 |
| 流日志类型 |
选择“网络安全组”,然后选择“+ 选择目标资源”。
选择要启用流日志的网络安全组,然后选择“确认选择”。 |
| 流日志名称 |
输入流日志的名称或保留默认名称。 Azure 门户使用 {ResourceName}-{ResourceGroupName}-flowlog 作为流日志的默认名称。
myNSG-myResourceGroup-flowlog 是本文中使用的默认名称。 |
|
实例详细信息 |
|
| 订阅 |
选择存储帐户的 Azure 订阅。 |
| 存储帐户 |
选择要在其中保存流日志的存储帐户。 如果要创建新的存储帐户,可选择“新建存储帐户”。 |
| 保留期(天数) |
输入日志的保留时间(此选项仅适用于标准常规用途 v2 存储帐户)。 如果要永久保留存储帐户中的流日志数据(直到手动将其从存储帐户中删除),请输入 0。 有关定价的详细信息,请参阅 Azure 存储定价。 |
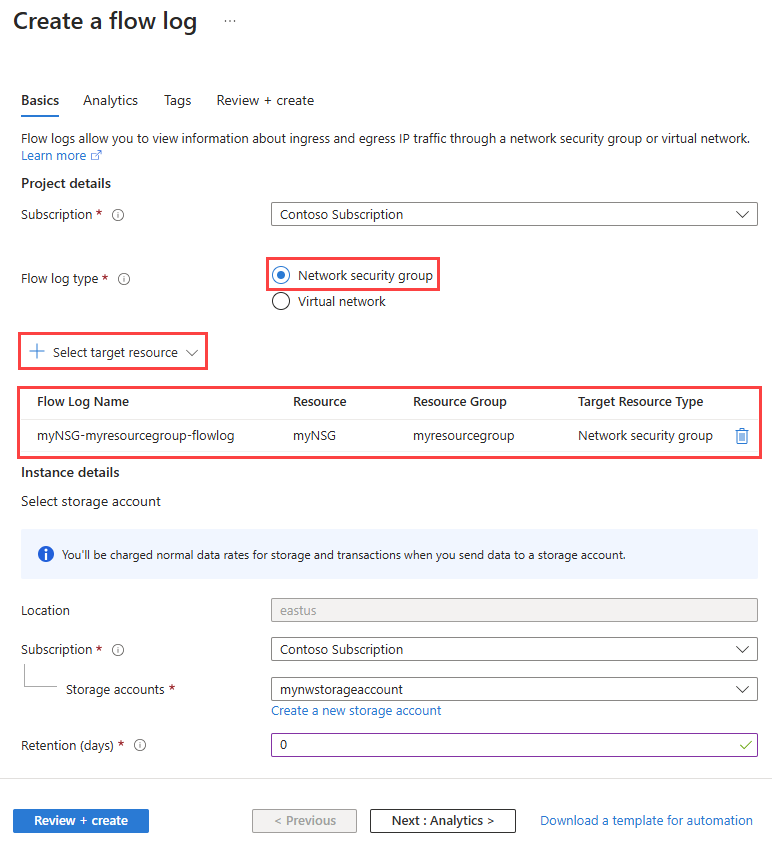
若要启用流量分析,请选择“下一步: 分析”按钮,或选择“分析”选项卡。输入或选择下列值:
| 设置 |
价值 |
| 流日志版本 |
选择网络安全组流日志的版本,可用选项包括:版本 1 和 版本 2。 默认版本为版本 2。 有关详细信息,请参阅网络安全组的流日志记录。 |
| 启用流量分析 |
选中复选框,以启用流日志的流量监测。 |
| 流量分析处理间隔 |
选择所需的处理间隔,可用选项包括:每小时和每 10 分钟。 默认处理间隔为每小时。 有关详细信息,请参阅流量分析。 |
| 订阅 |
选择您的 Log Analytics 工作区对应的 Azure 订阅。 |
| Log Analytics 工作区 |
选择 Log Analytics 工作区。 默认情况下,Azure 门户会在 defaultresourcegroup-{Region} 资源组中创建 DefaultWorkspace-{SubscriptionID}-{Region} Log Analytics 工作区。 |

选择“查看 + 创建”。
检查设置,然后选择创建。
使用 New-AzNetworkWatcherFlowLog cmdlet 创建流日志。 流日志是在网络观察程序默认资源组 NetworkWatcherRG 中创建的。
在没有流量分析的情况下启用 NSG 流日志:
# Place the network security group properties into a variable.
$nsg = Get-AzNetworkSecurityGroup -Name 'myNSG' -ResourceGroupName 'myResourceGroup'
# Place the storage account configuration into a variable.
$sa = Get-AzStorageAccount -Name 'myStorageAccount' -ResourceGroupName 'myResourceGroup'
# Create a version 1 NSG flow log.
New-AzNetworkWatcherFlowLog -Name 'myFlowLog' -Location 'chinaeast' -TargetResourceId $nsg.Id -StorageId $sa.Id -Enabled $true
启用 NSG 流日志和流量分析功能:
# Place the network security group properties into a variable.
$nsg = Get-AzNetworkSecurityGroup -Name 'myNSG' -ResourceGroupName 'myResourceGroup'
# Place the storage account configuration into a variable.
$sa = Get-AzStorageAccount -Name 'myStorageAccount' -ResourceGroupName 'myResourceGroup'
# Create a traffic analytics workspace and place its configuration into a variable.
$workspace = New-AzOperationalInsightsWorkspace -Name 'myWorkspace' -ResourceGroupName 'myResourceGroup' -Location 'chinaeast'
# Create a version 1 NSG flow log.
New-AzNetworkWatcherFlowLog -Name 'myFlowLog' -Location 'chinaeast' -TargetResourceId $nsg.Id -StorageId $sa.Id -Enabled $true -EnableTrafficAnalytics -TrafficAnalyticsWorkspaceId $workspace.ResourceId
使用 az network watcher flow-log create 命令创建虚拟网络流日志。 流日志是在网络观察程序默认资源组 NetworkWatcherRG 中创建的。
在没有流量分析的情况下启用 NSG 流日志:
# Create a version 1 NSG flow log.
az network watcher flow-log create --name 'myFlowLog' --nsg 'myNSG' --resource-group 'myResourceGroup' --storage-account 'myStorageAccount' --location 'chinaeast'
如果存储帐户位于与网络安全组不同的资源组中,请使用存储帐户的资源 ID,而不是其名称:
# Create a version 1 NSG flow log (the storage account is in a different resource group from the network security group).
az network watcher flow-log create --name 'myFlowLog' --nsg 'myNSG' --resource-group 'myResourceGroup' --storage-account '/subscriptions/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/resourceGroups/StorageRG/providers/Microsoft.Storage/storageAccounts/myStorageAccount' --location 'chinaeast'
启用 NSG 流日志和流量分析功能:
# Create a traffic analytics workspace.
az monitor log-analytics workspace create --name 'myWorkspace' --resource-group 'myResourceGroup' --location 'chinaeast'
# Create a version 1 NSG flow log and enable traffic analytics for it.
az network watcher flow-log create --name 'myFlowLog' --nsg 'myNSG' --resource-group 'myResourceGroup' --storage-account 'myStorageAccount' --traffic-analytics true --workspace 'myWorkspace' --location 'chinaeast'
如果存储帐户位于与网络安全组不同的资源组中,请使用存储帐户的资源 ID 而不是其名称。
注释
如果存储帐户位于不同的订阅中,则网络安全组和存储帐户必须与同一 Microsoft Entra 租户相关联。 用于每个订阅的帐户必须有必要的权限。
重要
存储帐户不得具有限制仅对 Azure 服务或特定虚拟网络的网络访问的网络规则。
启用或禁用流量分析
为流日志启用流量分析以分析流日志数据。 流量分析提供对虚拟网络流量模式的见解。 可以随时为流日志启用或禁用流量分析。
注释
除了启用或禁用流量分析之外,还可以更改其他流日志设置。
若要为流日志启用流量分析,请执行以下步骤:
在门户顶部的搜索框中,输入网络监视工具。 在搜索结果中,选择“网络监视器”。
在“日志”下,选择“流日志”。
在“网络观察程序 | 流日志”中,选择要启用流量分析的流日志。
在“流日志设置”的“流量分析”下,选中“启用流量分析”复选框。
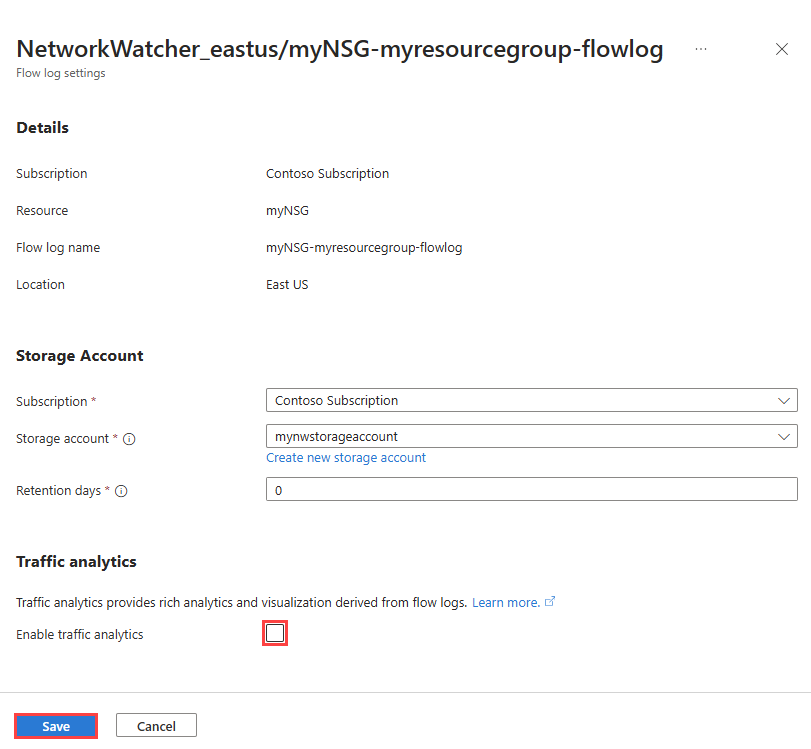
输入或选择下列值:
| 设置 |
价值 |
| 订阅 |
选择您的 Log Analytics 工作区对应的 Azure 订阅。 |
| Log Analytics 工作区 |
选择 Log Analytics 工作区。 默认情况下,Azure 门户会在 defaultresourcegroup-{Region} 资源组中创建 DefaultWorkspace-{SubscriptionID}-{Region} Log Analytics 工作区。 |
| 流量日志记录间隔 |
选择所需的处理间隔,可用选项包括:每小时和每 10 分钟。 默认处理间隔为每小时。 有关详细信息,请参阅流量分析。 |
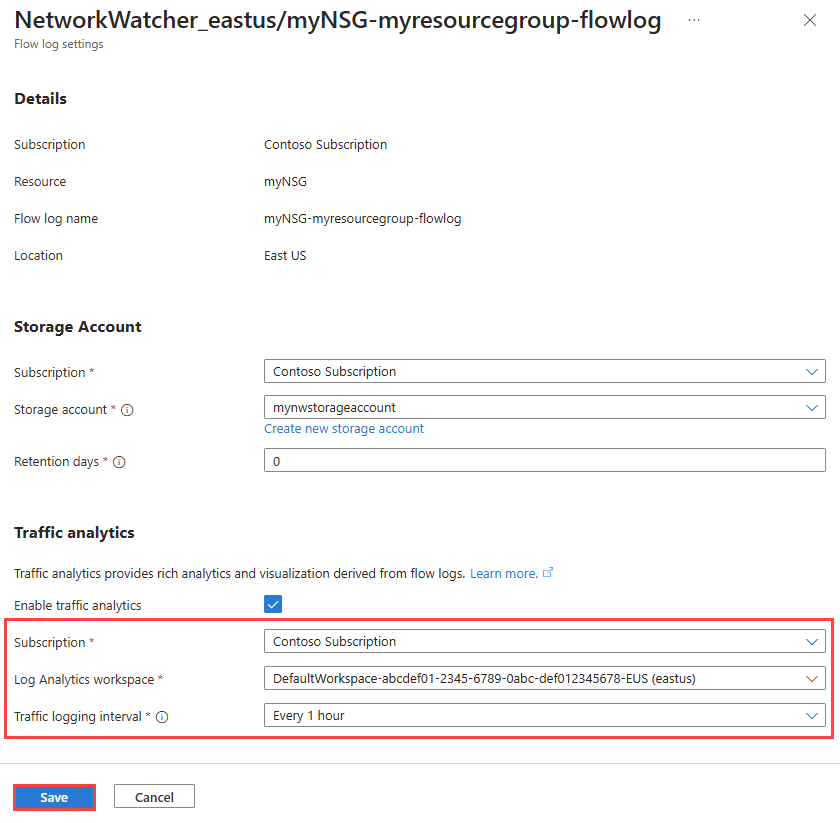
选择保存以应用更改。
若要为流日志禁用流量分析,请执行前面的步骤 1-3,然后取消选中“启用流量分析”复选框,并选择“保存”。

若要在流日志资源上启用流量分析,请使用 Set-AzNetworkWatcherFlowLog cmdlet:
# Place the network security group properties into a variable.
$nsg = Get-AzNetworkSecurityGroup -Name 'myNSG' -ResourceGroupName 'myResourceGroup'
# Place the storage account properties into a variable.
$sa = Get-AzStorageAccount -Name 'myStorageAccount' -ResourceGroupName 'myResourceGroup'
# Place the workspace configuration into a variable.
$workspace = Get-AzOperationalInsightsWorkspace -Name 'myWorkspace' -ResourceGroupName 'myResourceGroup'
# Update the NSG flow log.
Set-AzNetworkWatcherFlowLog -Enabled $true -Name 'myFlowLog' -Location 'chinaeast' -TargetResourceId $nsg.Id -StorageId $sa.Id -EnableTrafficAnalytics -TrafficAnalyticsWorkspaceId $workspace.ResourceId -FormatVersion 2
若要在流日志资源上禁用流量分析并继续生成流日志并将其保存到存储帐户,请使用 Set-AzNetworkWatcherFlowLog cmdlet:
# Place the network security group properties into a variable.
$nsg = Get-AzNetworkSecurityGroup -Name 'myNSG' -ResourceGroupName 'myResourceGroup'
# Place the storage account configuration into a variable.
$sa = Get-AzStorageAccount -Name 'myStorageAccount' -ResourceGroupName 'myResourceGroup'
# Update the NSG flow log.
Set-AzNetworkWatcherFlowLog -Enabled $true -Name 'myFlowLog' -Location 'chinaeast' -TargetResourceId $nsg.Id -StorageId $sa.Id -FormatVersion 2
若要在流日志资源上启用流量分析,请使用 az network watcher flow-log update 命令:
# Update the NSG flow log.
az network watcher flow-log update --name 'myFlowLog' --nsg 'myNSG' --resource-group 'myResourceGroup' --storage-account 'myStorageAccount' --traffic-analytics true --workspace 'myWorkspace' --log-version '2'
若要在流日志资源上禁用流量分析,并继续生成流日志并将其保存到存储帐户,请使用 az network watcher flow-log update 命令:
# Update the NSG flow log.
az network watcher flow-log update --name 'myFlowLog' --nsg 'myNSG' --resource-group 'myResourceGroup' --storage-account 'myStorageAccount' --traffic-analytics false --log-version '2'
列出所有流日志
可以列出一个订阅或一组订阅中的所有流日志(Azure 门户)。 还可以列出某个区域中的所有流日志。
在门户顶部的搜索框中,输入网络监视工具。 在搜索结果中,选择“网络监视器”。
在“日志”下,选择“流日志”。
选择“订阅等于”筛选器,以选择一个或多个订阅。 可以应用其他筛选器,例如 Location 等于 列出区域中的所有流日志。
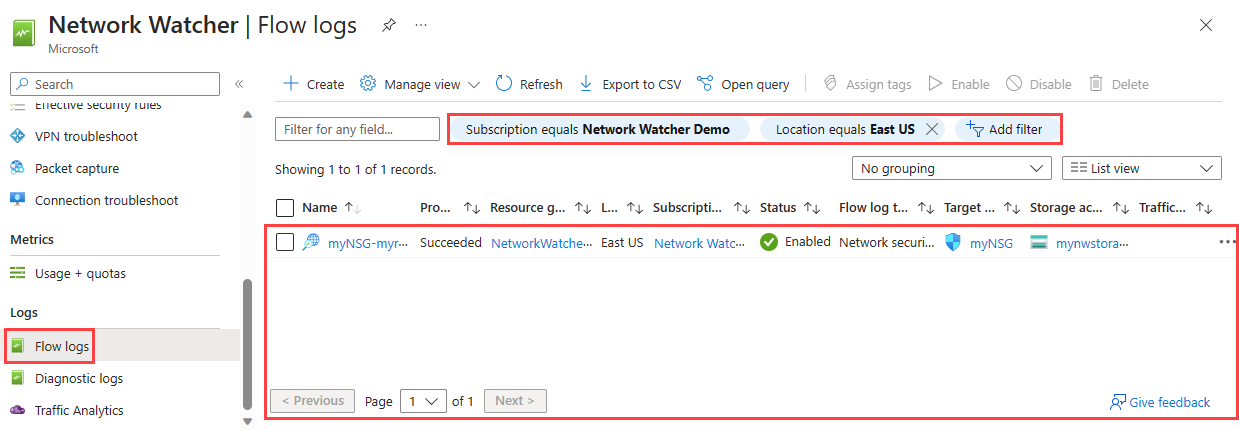
使用 Get-AzNetworkWatcherFlowLog cmdlet 列出订阅中特定区域中的所有流日志资源:
# Get all flow logs in China East region.
Get-AzNetworkWatcherFlowLog -Location 'chinaeast' | format-table Name
注释
若要将 -Location 参数与 Get-AzNetworkWatcherFlowLog cmdlet 结合使用,需要在 NetworkWatcherRG 资源组中拥有额外的“读取者”权限。
使用 az network watcher flow-log list 命令列出订阅中特定区域中的所有流日志资源:
# Get all flow logs in China East region.
az network watcher flow-log list --location 'chinaeast' --out table
查看流日志资源的详细信息
可以查看流日志的详细信息。
在门户顶部的搜索框中,输入网络监视工具。 在搜索结果中,选择“网络监视器”。
在“日志”下,选择“流日志”。
在“网络观察程序|流日志”中选择要查看的流日志。
在“流日志设置”中,可以查看流日志资源的设置。
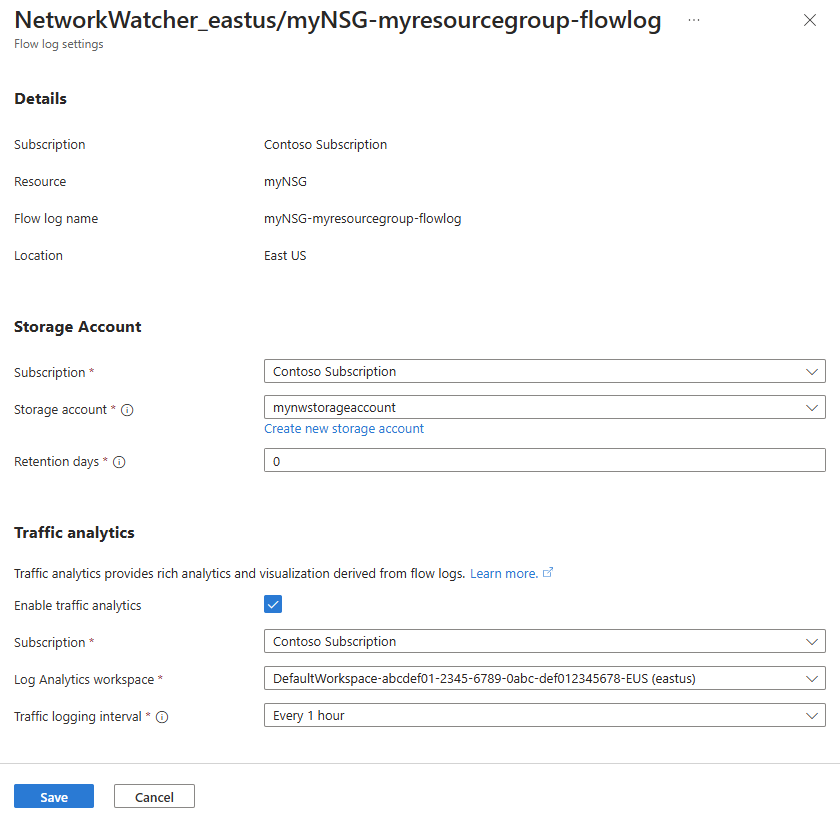
选择“取消”关闭设置页,无需进行更改。
使用 Get-AzNetworkWatcherFlowLog cmdlet 查看流日志资源的详细信息:
# Get the details of a flow log.
Get-AzNetworkWatcherFlowLog -Name 'myFlowLog' -Location 'chinaeast'
注释
若要将 -Location 参数与 Get-AzNetworkWatcherFlowLog cmdlet 结合使用,需要在 NetworkWatcherRG 资源组中拥有额外的“读取者”权限。
使用 az network watcher flow-log show 命令查看流日志资源的详细信息:
# Get the details of a flow log.
az network watcher flow-log show --name 'myFlowLog' --resource-group 'NetworkWatcherRG' --location 'chinaeast'
下载流日志
可以从将流日志保存到的存储帐户下载流日志数据。
在门户顶部的搜索框中,输入“存储帐户”。 从搜索结果中选择“存储帐户”Storage accounts。
选择用于存储日志的存储帐户。
在“数据存储”下,选择“容器”。
选择 insights-logs-networksecuritygroupflowevent 容器。
在 insights-logs-networksecuritygroupflowevent 中,依次浏览文件夹层次结构,直到找到你想下载的 PT1H.json 文件。 NSG 流日志文件遵循以下路径:
https://{storageAccountName}.blob.core.chinacloudapi.cn/insights-logs-networksecuritygroupflowevent/resourceId=/SUBSCRIPTIONS/{subscriptionID}/RESOURCEGROUPS/{resourceGroupName}/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/{NetworkSecurityGroupName}/y={year}/m={month}/d={day}/h={hour}/m=00/macAddress={macAddress}/PT1H.json
选择 文件右侧的省略号“...”,然后选择“下载”PT1H.json。
若要从存储帐户下载虚拟网络流日志,请使用 Get-AzStorageBlobContent cmdlet。 有关详细信息,请参阅下载 blob。
NSG 流日志文件保存到存储账户的路径为:
https://{storageAccountName}.blob.core.chinacloudapi.cn/insights-logs-networksecuritygroupflowevent/resourceId=/SUBSCRIPTIONS/{subscriptionID}/RESOURCEGROUPS/{resourceGroupName}/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/{NetworkSecurityGroupName}/y={year}/m={month}/d={day}/h={hour}/m=00/macAddress={macAddress}/PT1H.json
若要从存储帐户下载虚拟网络流日志,请使用 az storage blob download 命令。 有关详细信息,请参阅下载 blob。
NSG 流日志文件保存到存储账户的路径为:
https://{storageAccountName}.blob.core.chinacloudapi.cn/insights-logs-networksecuritygroupflowevent/resourceId=/SUBSCRIPTIONS/{subscriptionID}/RESOURCEGROUPS/{resourceGroupName}/PROVIDERS/MICROSOFT.NETWORK/NETWORKSECURITYGROUPS/{NetworkSecurityGroupName}/y={year}/m={month}/d={day}/h={hour}/m=00/macAddress={macAddress}/PT1H.json
有关流日志结构的信息,请参阅 NSG 流日志的日志格式。
禁用流日志
可以暂时禁用流日志,而无需删除流日志。 禁用流日志会停止关联网络安全组的流日志记录。 但是,流日志资源会保留其所有设置和关联。 可以随时重新启用它,以恢复对配置的网络安全组进行流日志记录。
在门户顶部的搜索框中,输入“网络观察程序”。 在搜索结果中,选择“网络监视器”。
在“日志”下,选择“流日志”。
在“网络观察程序|流日志”中,选择要禁用的流日志的复选框。
选择禁用。

使用 Set-AzNetworkWatcherFlowLog cmdlet 禁用流日志:
# Place the network security group properties into a variable.
$nsg = Get-AzNetworkSecurityGroup -Name 'myNSG' -ResourceGroupName 'myResourceGroup'
# Place the storage account properties into a variable.
$sa = Get-AzStorageAccount -Name 'myStorageAccount' -ResourceGroupName 'myResourceGroup'
# Update the NSG flow log.
Set-AzNetworkWatcherFlowLog -Enabled $false -Name 'myFlowLog' -Location 'chinaeast' -TargetResourceId $nsg.Id -StorageId $sa.Id
使用 az network watcher flow-log update 命令禁用流日志:
# Disable the flow log.
az network watcher flow-log update --name 'myFlowLog' --nsg 'myNSG' --resource-group 'myResourceGroup' --storage-account 'myStorageAccount' --enabled false
注释
如果为流日志启用了流量分析,则必须先禁用流量分析,然后才能禁用流日志。 若要禁用流量分析,请参阅启用或禁用流量分析。
删除流日志
可以永久删除虚拟网络流日志。 删除流日志会删除其所有设置和关联。 要为同一资源重新开始流日志记录,必须为其创建新的流日志。
在门户顶部的搜索框中,输入“网络观察程序”。 在搜索结果中,选择“网络监视器”。
在“日志”下,选择“流日志”。
在“网络观察程序|流日志”中,选择要删除的流日志的复选框。
选择 删除。
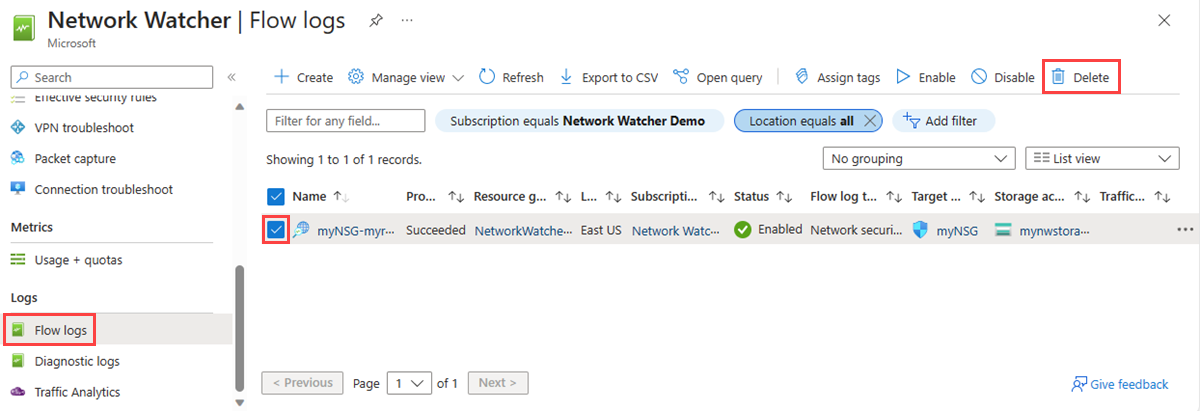
注释
删除流日志不会从存储帐户中删除流日志数据。 存储在存储帐户中的流日志数据遵循配置的保留策略或保留在存储帐户中,直到手动删除。
相关内容











