重要
网络安全组(NSG)流日志将于 2027 年 9 月 30 日停用。 2025 年 6 月 30 日之后,将无法再创建新的 NSG 流日志。 建议迁移到虚拟网络流日志,这些日志解决了 NSG 流日志的限制。 退休日期后,将不再支持 NSG 流日志中启用的流量分析功能,订阅中的现有 NSG 流日志资源也将被删除。 但是,不会从 Azure 存储中删除现有的 NSG 流日志记录,并且将继续遵循其配置的保留策略。 有关详细信息,请查看官方公告。
Azure Policy 可帮助你执行组织标准并大规模评估合规性。 Azure Policy 的常见用例包括实施监管来满足资源一致性、法规遵从性、安全性、成本和管理方面的要求。 若要详细了解 Azure Policy,请参阅什么是 Azure Policy?和快速入门:创建策略分配以识别不合规资源。
本文介绍如何使用两个内置策略来管理网络安全组 (NSG) 流日志的设置。 第一个策略标记任何未启用流日志的网络安全组。 第二个策略自动部署未启用流日志的 NSG 流日志。
使用内置策略审核网络安全组
“应为每个网络安全组配置流日志”策略通过检查类型为 的所有 Azure 资源管理器对象来审核范围内的所有现有网络安全组。Microsoft.Network/networkSecurityGroups 然后,此策略通过网络安全组的流日志属性检查链接的流日志,并标记任何未启用流日志的网络安全组。
若要使用内置策略审核流日志,请执行以下步骤:
登录到 Azure 门户。
在门户顶部的搜索框中,输入“policy”。 从搜索结果中选择策略。
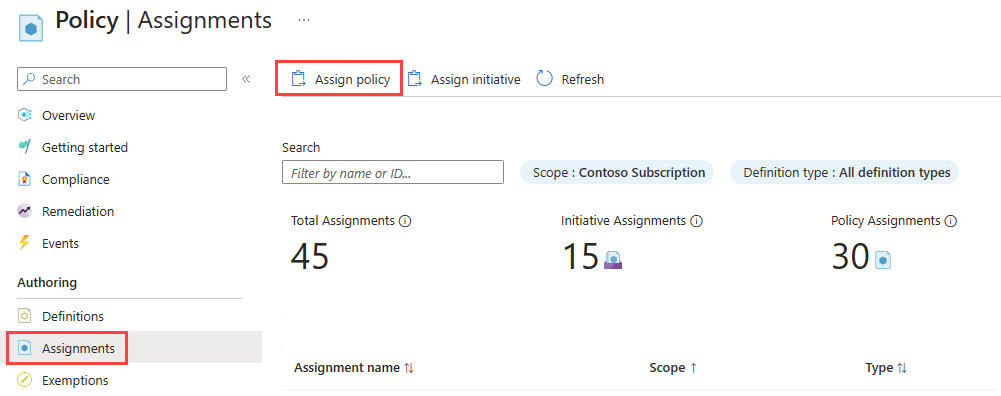
选择“任务”,然后选择“分配策略”。
选择“范围”旁边的省略号 (...),以选择具有你要使用策略审核的网络安全组的 Azure 订阅。 还可以选择具有网络安全组的资源组。 做出选择后,选择“选择”按钮。
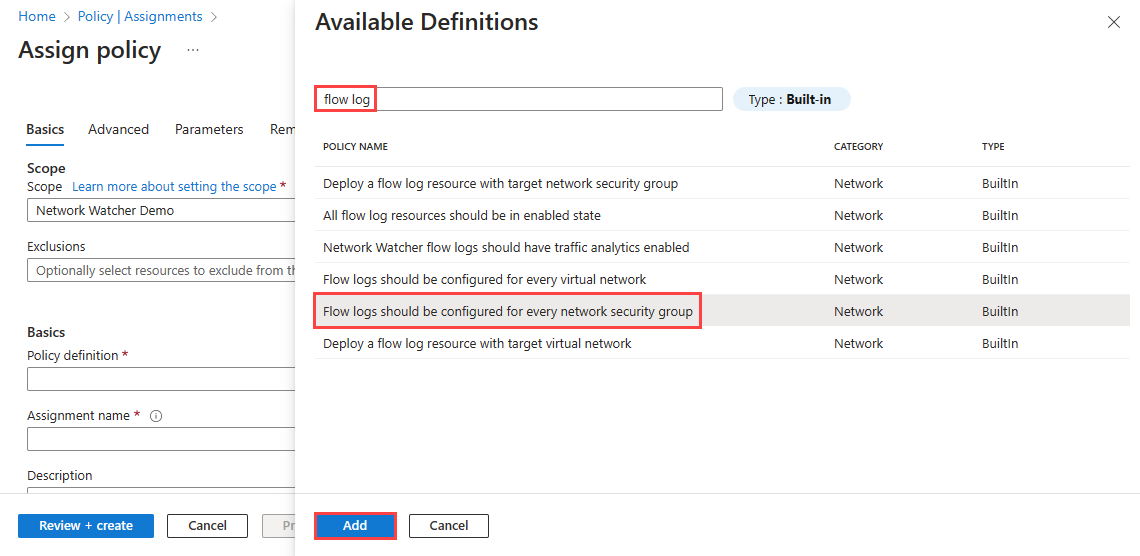
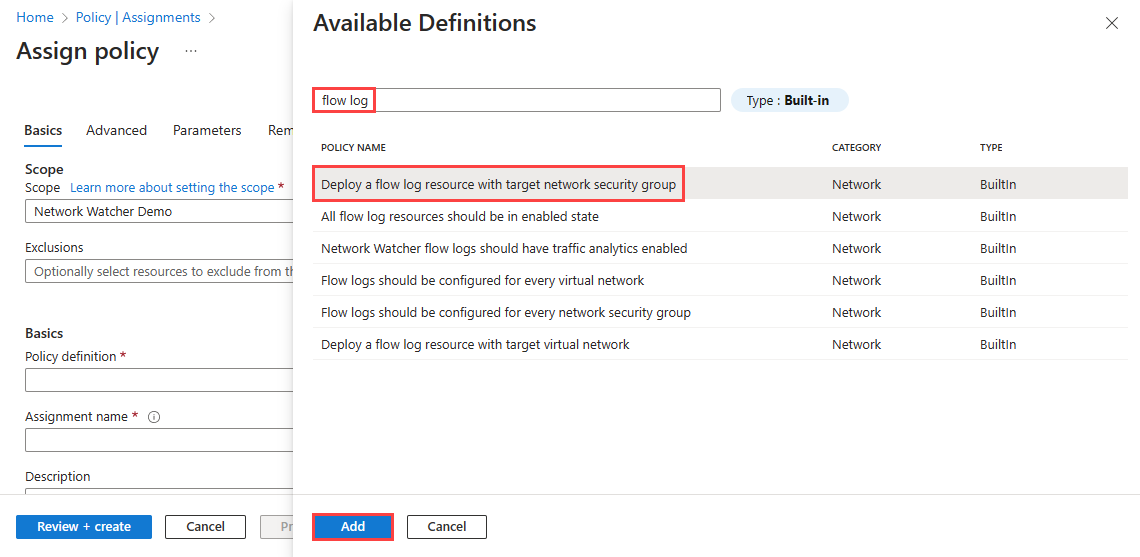
选择“策略定义”旁边的省略号 (...),然后选择要分配的内置策略。 在搜索框中输入“流日志”,然后选择“内置”筛选器。 在搜索结果中,选择“应为每个网络安全组配置流日志”,然后选择“添加”。
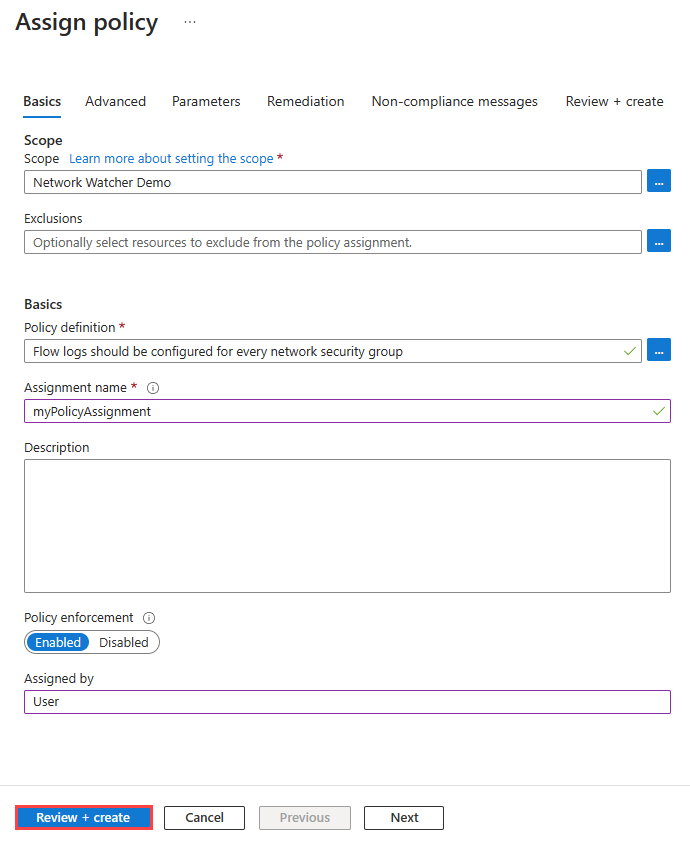
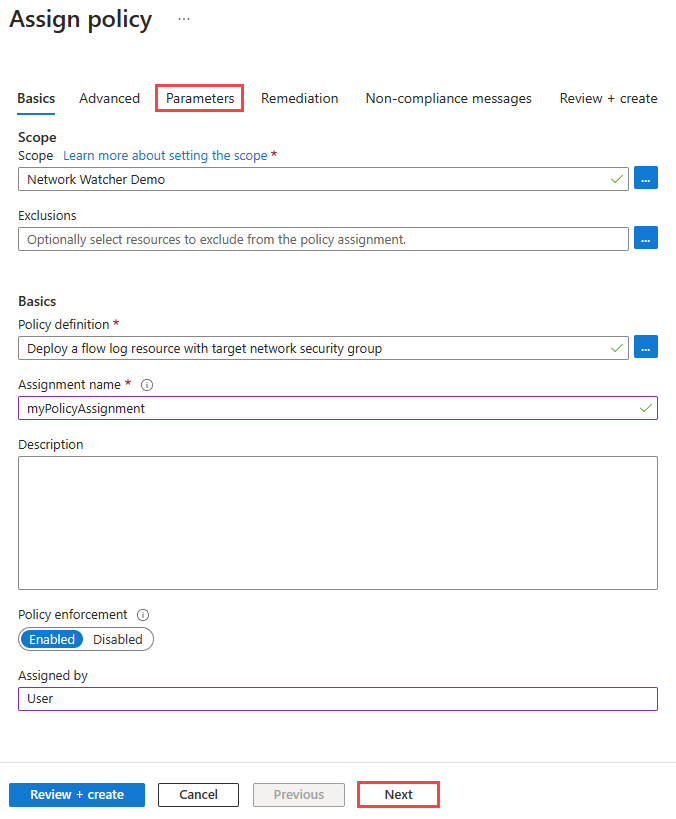
在“分配名称”中输入名称,在“分配者”中输入你的名字。
此策略不需要任何参数。 它也不包含任何角色定义,因此无需在“修正”选项卡中为托管标识创建角色分配。
选择“查看 + 创建”,然后选择“创建”。
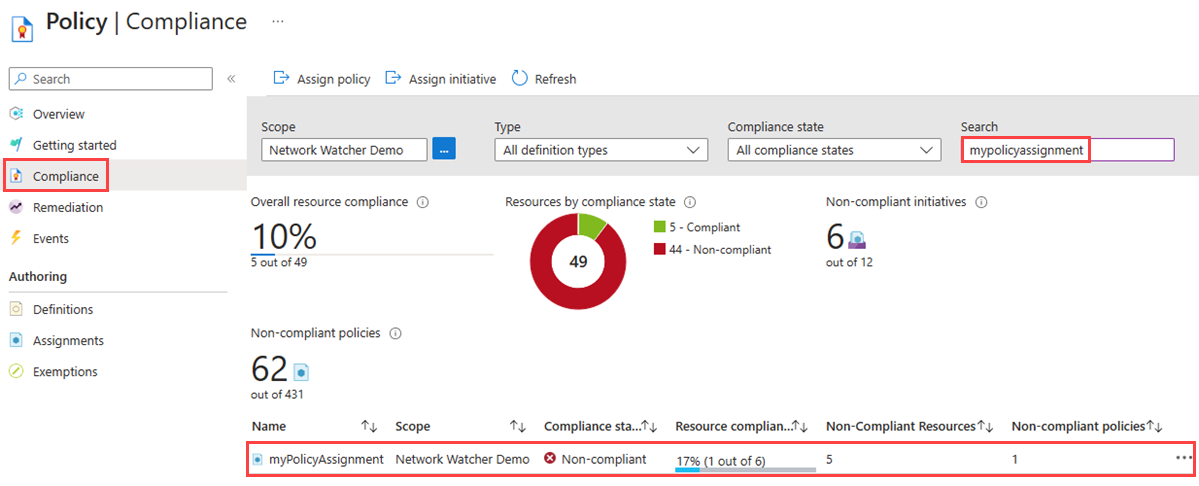
选择“合规性”。 搜索你的任务名称,然后选择它。
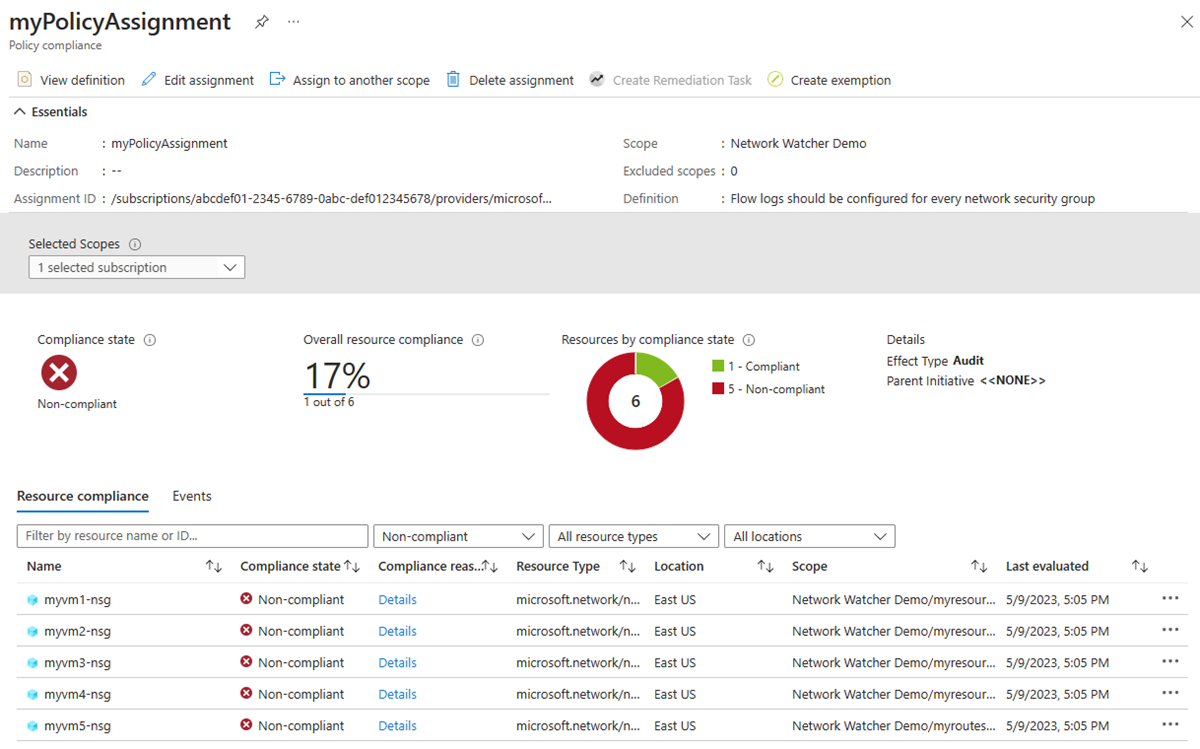
选择“资源合规性”以获取所有不合规网络安全组的列表。
使用内置策略部署和配置 NSG 流日志
“使用目标网络安全组来部署流日志资源”策略通过检查类型为 Microsoft.Network/networkSecurityGroups 的所有 Azure 资源管理器对象来检查范围内的所有现有网络安全组。 然后,它通过网络安全组的流日志属性检查链接的流日志。 如果该属性不存在,则策略将部署流日志。
若要分配 deployIfNotExists 策略,请执行以下操作:
登录到 Azure 门户。
在门户顶部的搜索框中,输入“policy”。 从搜索结果中选择策略。
选择“任务”,然后选择“分配策略”。
选择“范围”旁边的省略号 (...),以选择具有你要使用策略审核的网络安全组的 Azure 订阅。 还可以选择具有网络安全组的资源组。 做出选择后,选择“选择”按钮。
选择“策略定义”旁边的省略号 (...),然后选择要分配的内置策略。 在搜索框中输入“流日志”,然后选择“内置”筛选器。 在搜索结果中,选择“使用目标网络安全组部署流日志资源”,然后选择“添加”。
在“分配名称”中输入名称,在“分配者”中输入你的名字。
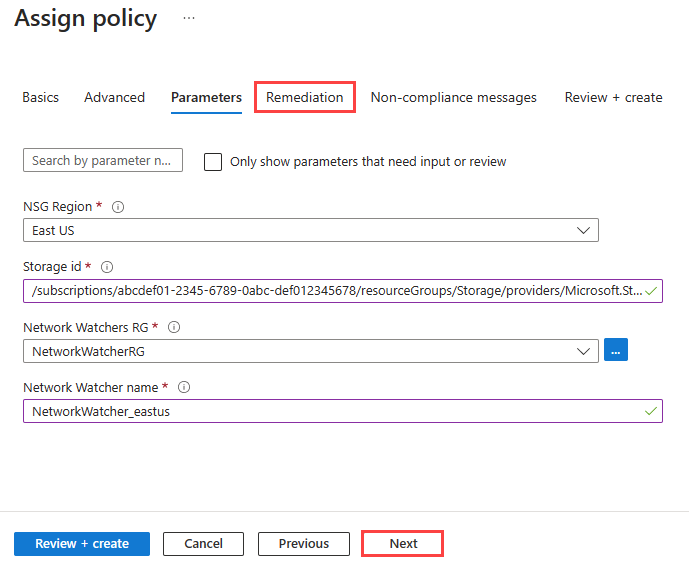
选择“下一步”按钮两次,或者选择“参数”选项卡。然后输入或选择以下值:
设置 值 NSG 区域 选择要将策略应用到的网络安全组的区域。 存储 ID 输入存储帐户的完整资源 ID。 存储帐户必须与网络安全组位于同一区域中。 存储资源 ID 的格式为 /subscriptions/<SubscriptionID>/resourceGroups/<ResourceGroupName>/providers/Microsoft.Storage/storageAccounts/<StorageAccountName>。网络观察程序 RG 选择 Azure 网络观察程序实例的资源组。 网络观察程序名称 输入网络观察程序实例的名称。 选择“下一步”或“修正”选项卡。输入或选择以下值:
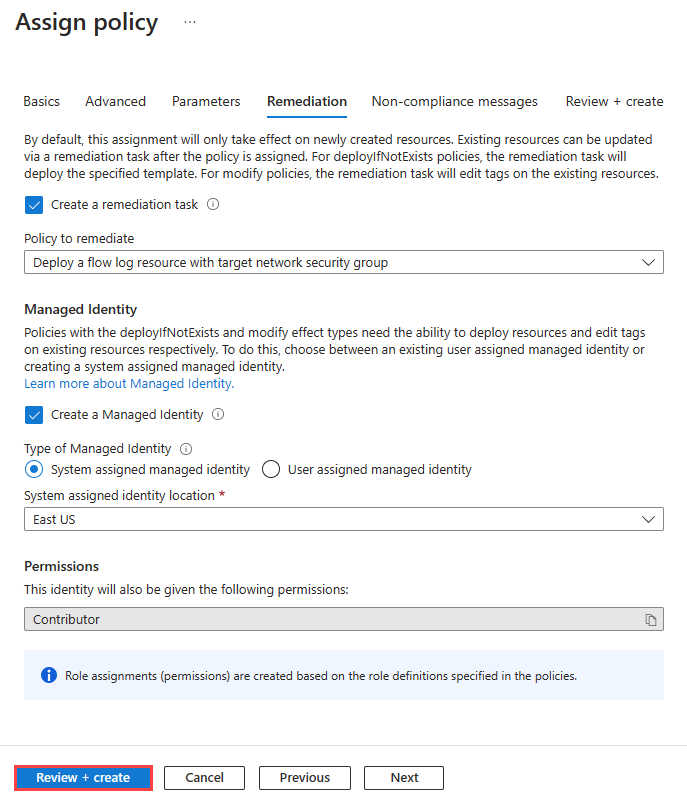
设置 值 创建修正任务 如果你希望策略影响现有资源,请选中该复选框。 创建托管标识 选中复选框。 托管标识类型 选择要使用的托管标识的类型。 系统分配的标识位置 选择系统分配标识的区域。 范围 选择用户分配标识的范围。 现有的用户分配标识 选择用户分配的标识。 注意
你需要“参与者”或“所有者”权限才能使用此策略。
选择“查看 + 创建”,然后选择“创建”。
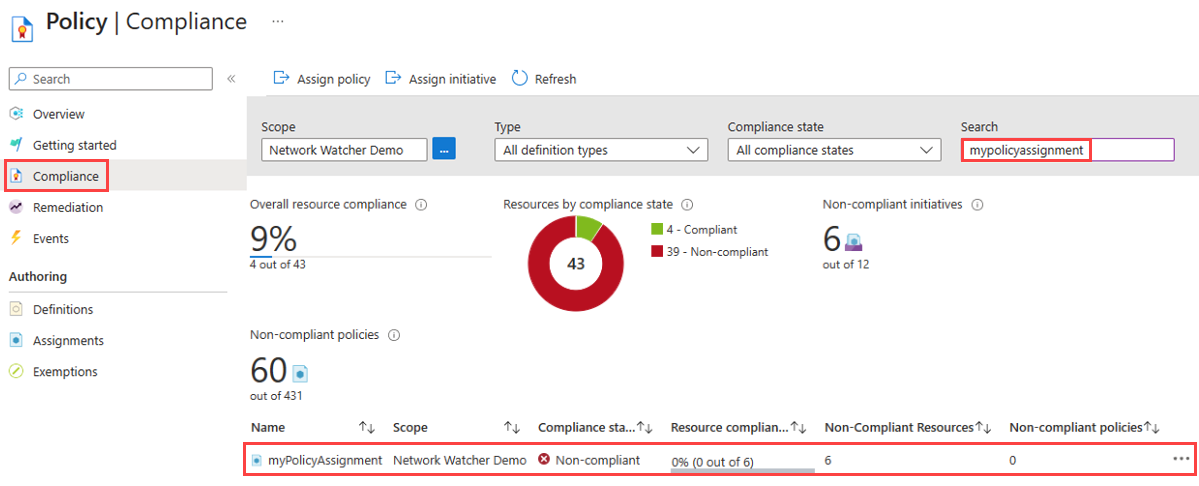
选择“合规性”。 搜索你的任务名称,然后选择它。
选择“资源合规性”以获取所有不合规网络安全组的列表。
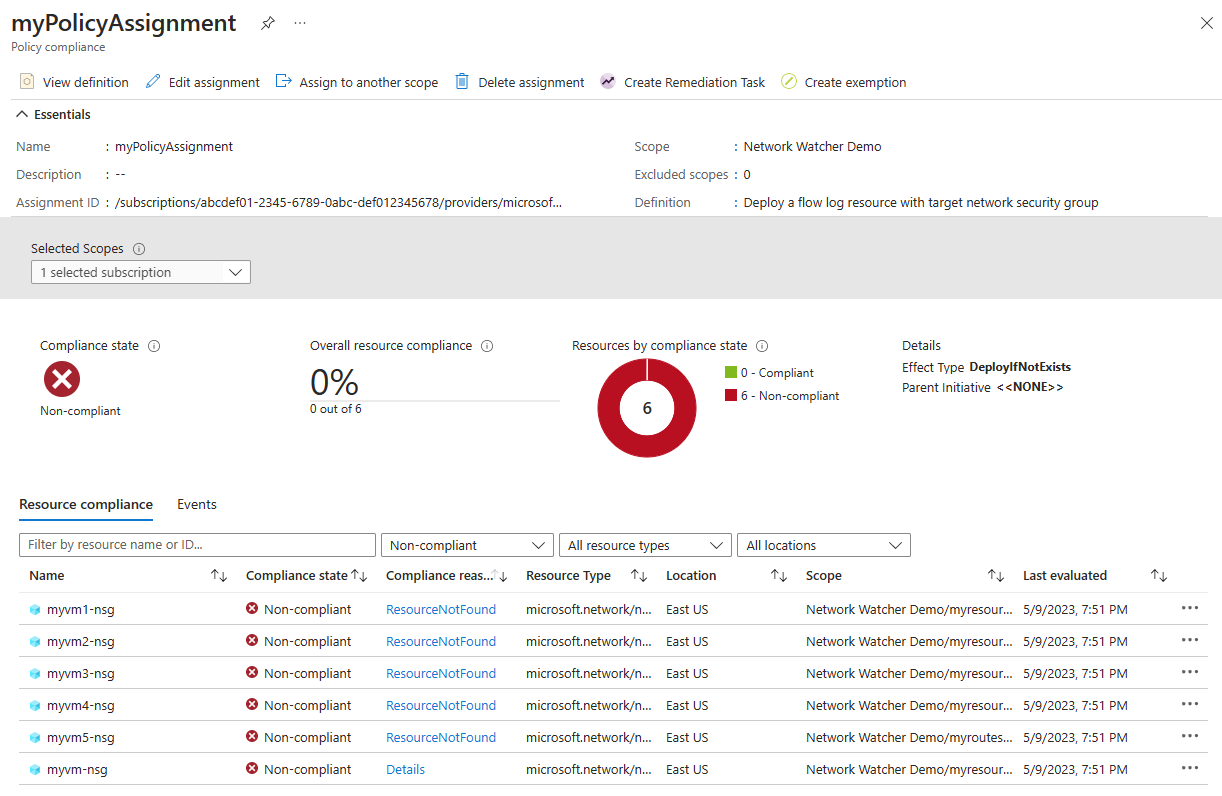
让策略保持运行,以评估并部署所有不合规网络安全组的流日志。 然后再次选择“资源合规性”以检查网络安全组的状态(如果策略已完成修正,将不会显示不合规的网络安全组)。
相关内容
- 若要详细了解网络安全组流日志记录,请参阅网络安全组流日志。
- 若要了解如何将内置策略与流量分析配合使用,请参阅使用 Azure Policy 管理流量分析。
- 要了解如何使用 Azure 资源管理器模板(ARM 模板)部署流日志和流量分析,请参阅使用 Azure 资源管理器模板配置 NSG 流日志。