角色定义是可以执行的权限集合,例如读取、写入和删除。 它通常只是被称为“角色”。 Azure 基于角色的访问控制(Azure RBAC) 具有超过 120 个 内置角色 ,也可以创建自己的自定义角色。 本文介绍如何列出可用于授予对 Azure 资源的访问权限的内置角色和自定义角色。
若要查看Microsoft Entra ID 的管理员角色列表,请参阅 Microsoft Entra ID 中的管理员角色权限。
Azure 门户
列出所有角色
按照以下步骤列出 Azure 门户中的所有角色。
在 Azure 门户中,单击“ 所有服务 ”,然后选择任何范围。 例如,可以选择“管理组”、“订阅”、“资源组”或某个资源 。
单击特定的资源。
单击“访问控制(IAM)”。
单击“角色”选项卡以查看包含所有内置角色和自定义角色的列表。
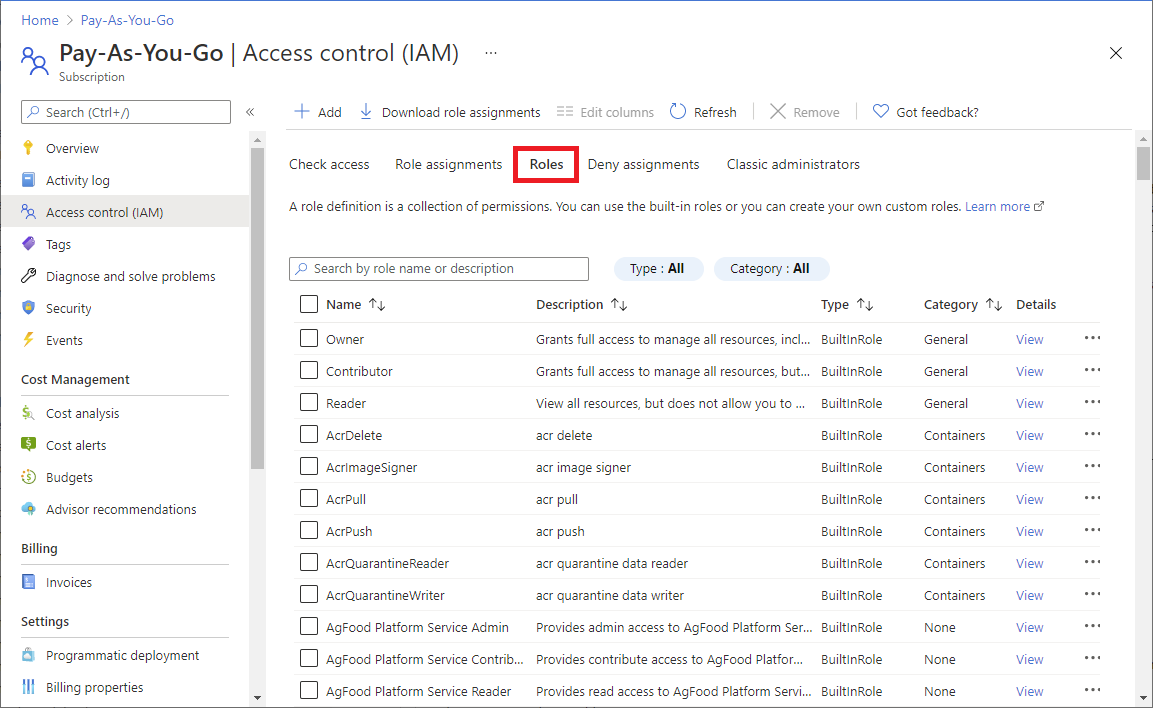
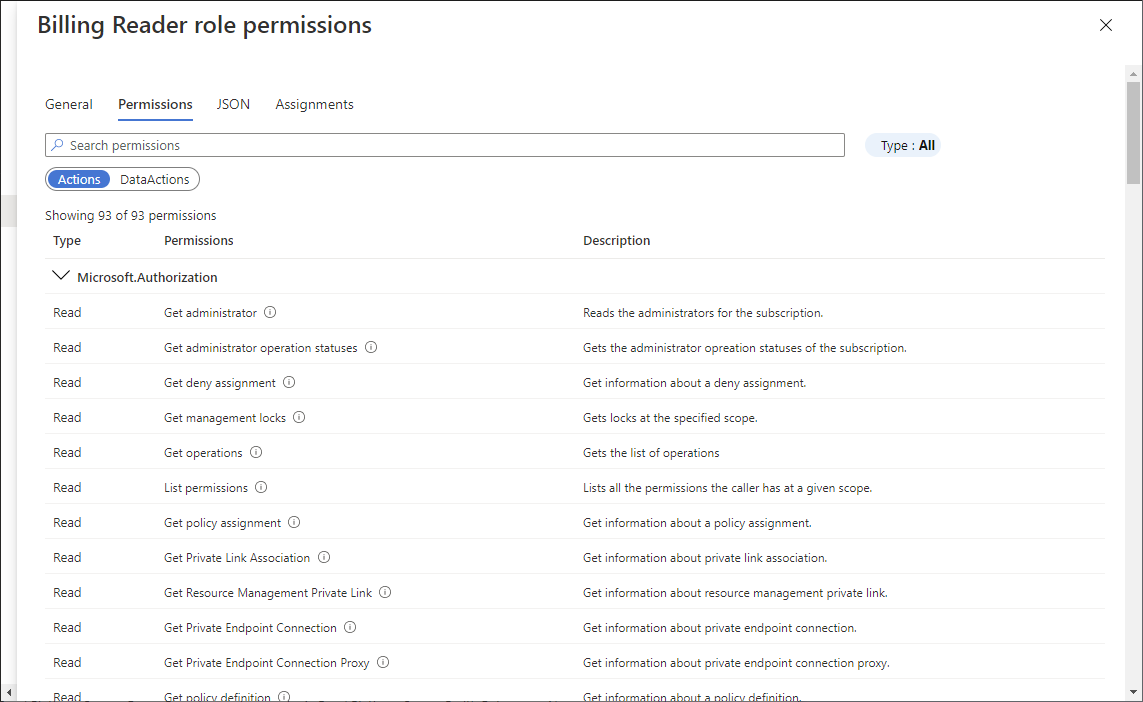
若要查看特定角色的权限,请在“ 详细信息 ”列中单击“ 查看” 链接。
此时会显示权限窗格。
单击“ 权限 ”选项卡可查看和搜索所选角色的权限。
Azure PowerShell
列出所有角色
若要列出 Azure PowerShell 中的所有角色,请使用 Get-AzRoleDefinition。
Get-AzRoleDefinition | FT Name, Description
AcrImageSigner acr image signer
AcrQuarantineReader acr quarantine data reader
AcrQuarantineWriter acr quarantine data writer
API Management Service Contributor Can manage service and the APIs
API Management Service Operator Role Can manage service but not the APIs
API Management Service Reader Role Read-only access to service and APIs
Application Insights Component Contributor Can manage Application Insights components
Application Insights Snapshot Debugger Gives user permission to use Application Insights Snapshot Debugge...
Automation Job Operator Create and Manage Jobs using Automation Runbooks.
Automation Operator Automation Operators are able to start, stop, suspend, and resume ...
...
列出角色定义
若要列出特定角色的详细信息,请使用 Get-AzRoleDefinition。
Get-AzRoleDefinition <role_name>
PS C:\> Get-AzRoleDefinition "Contributor"
Name : Contributor
Id : b24988ac-6180-42a0-ab88-20f7382dd24c
IsCustom : False
Description : Lets you manage everything except access to resources.
Actions : {*}
NotActions : {Microsoft.Authorization/*/Delete, Microsoft.Authorization/*/Write,
Microsoft.Authorization/elevateAccess/Action}
DataActions : {}
NotDataActions : {}
AssignableScopes : {/}
以 JSON 格式列出角色定义
若要以 JSON 格式列出角色,请使用 Get-AzRoleDefinition。
Get-AzRoleDefinition <role_name> | ConvertTo-Json
PS C:\> Get-AzRoleDefinition "Contributor" | ConvertTo-Json
{
"Name": "Contributor",
"Id": "b24988ac-6180-42a0-ab88-20f7382dd24c",
"IsCustom": false,
"Description": "Lets you manage everything except access to resources.",
"Actions": [
"*"
],
"NotActions": [
"Microsoft.Authorization/*/Delete",
"Microsoft.Authorization/*/Write",
"Microsoft.Authorization/elevateAccess/Action",
"Microsoft.Blueprint/blueprintAssignments/write",
"Microsoft.Blueprint/blueprintAssignments/delete"
],
"DataActions": [],
"NotDataActions": [],
"AssignableScopes": [
"/"
]
}
列出角色定义的权限
若要列出特定角色的权限,请使用 Get-AzRoleDefinition。
Get-AzRoleDefinition <role_name> | FL Actions, NotActions
PS C:\> Get-AzRoleDefinition "Contributor" | FL Actions, NotActions
Actions : {*}
NotActions : {Microsoft.Authorization/*/Delete, Microsoft.Authorization/*/Write,
Microsoft.Authorization/elevateAccess/Action,
Microsoft.Blueprint/blueprintAssignments/write...}
(Get-AzRoleDefinition <role_name>).Actions
PS C:\> (Get-AzRoleDefinition "Virtual Machine Contributor").Actions
Microsoft.Authorization/*/read
Microsoft.Compute/availabilitySets/*
Microsoft.Compute/locations/*
Microsoft.Compute/virtualMachines/*
Microsoft.Compute/virtualMachineScaleSets/*
Microsoft.Insights/alertRules/*
Microsoft.Network/applicationGateways/backendAddressPools/join/action
Microsoft.Network/loadBalancers/backendAddressPools/join/action
...
Azure CLI
列出所有角色
若要列出 Azure CLI 中的所有角色,请使用 az role definition list。
az role definition list
以下示例列出了所有可用角色定义的名称和说明:
az role definition list --output json --query '[].{roleName:roleName, description:description}'
[
{
"description": "Can manage service and the APIs",
"roleName": "API Management Service Contributor"
},
{
"description": "Can manage service but not the APIs",
"roleName": "API Management Service Operator Role"
},
{
"description": "Read-only access to service and APIs",
"roleName": "API Management Service Reader Role"
},
...
]
以下示例列出了所有内置角色。
az role definition list --custom-role-only false --output json --query '[].{roleName:roleName, description:description, roleType:roleType}'
[
{
"description": "Can manage service and the APIs",
"roleName": "API Management Service Contributor",
"roleType": "BuiltInRole"
},
{
"description": "Can manage service but not the APIs",
"roleName": "API Management Service Operator Role",
"roleType": "BuiltInRole"
},
{
"description": "Read-only access to service and APIs",
"roleName": "API Management Service Reader Role",
"roleType": "BuiltInRole"
},
...
]
列出角色定义
若要列出角色的详细信息,请使用 az role definition list。
az role definition list --name {roleName}
以下示例列出了 参与者 角色定义:
az role definition list --name "Contributor"
[
{
"assignableScopes": [
"/"
],
"description": "Lets you manage everything except access to resources.",
"id": "/subscriptions/{subscriptionId}/providers/Microsoft.Authorization/roleDefinitions/b24988ac-6180-42a0-ab88-20f7382dd24c",
"name": "b24988ac-6180-42a0-ab88-20f7382dd24c",
"permissions": [
{
"actions": [
"*"
],
"dataActions": [],
"notActions": [
"Microsoft.Authorization/*/Delete",
"Microsoft.Authorization/*/Write",
"Microsoft.Authorization/elevateAccess/Action",
"Microsoft.Blueprint/blueprintAssignments/write",
"Microsoft.Blueprint/blueprintAssignments/delete"
],
"notDataActions": []
}
],
"roleName": "Contributor",
"roleType": "BuiltInRole",
"type": "Microsoft.Authorization/roleDefinitions"
}
]
列出角色定义的权限
以下示例仅列出Contributor角色的操作和notActions。
az role definition list --name "Contributor" --output json --query '[].{actions:permissions[0].actions, notActions:permissions[0].notActions}'
[
{
"actions": [
"*"
],
"notActions": [
"Microsoft.Authorization/*/Delete",
"Microsoft.Authorization/*/Write",
"Microsoft.Authorization/elevateAccess/Action",
"Microsoft.Blueprint/blueprintAssignments/write",
"Microsoft.Blueprint/blueprintAssignments/delete"
]
}
]
以下示例仅列出 虚拟机参与者 角色的操作。
az role definition list --name "Virtual Machine Contributor" --output json --query '[].permissions[0].actions'
[
[
"Microsoft.Authorization/*/read",
"Microsoft.Compute/availabilitySets/*",
"Microsoft.Compute/locations/*",
"Microsoft.Compute/virtualMachines/*",
"Microsoft.Compute/virtualMachineScaleSets/*",
"Microsoft.Compute/disks/write",
"Microsoft.Compute/disks/read",
"Microsoft.Compute/disks/delete",
"Microsoft.Insights/alertRules/*",
"Microsoft.Network/applicationGateways/backendAddressPools/join/action",
"Microsoft.Network/loadBalancers/backendAddressPools/join/action",
...
"Microsoft.Storage/storageAccounts/listKeys/action",
"Microsoft.Storage/storageAccounts/read"
]
]
REST API
先决条件
必须使用以下版本:
-
2015-07-01或更高版本
有关详细信息,请参阅 Azure RBAC REST API 的 API 版本。
列出所有角色定义
若要列出租户中的角色定义,请使用 角色定义 - 列出 REST API。
以下示例列出租户中的所有角色定义:
请求
GET https://management.chinacloudapi.cn/providers/Microsoft.Authorization/roleDefinitions?api-version=2022-04-01响应
{ "value": [ { "properties": { "roleName": "Billing Reader Plus", "type": "CustomRole", "description": "Read billing data and download invoices", "assignableScopes": [ "/subscriptions/eeee4e4e-ff5f-aa6a-bb7b-cccccc8c8c8c" ], "permissions": [ { "actions": [ "Microsoft.Authorization/*/read", "Microsoft.Billing/*/read", "Microsoft.Consumption/*/read", "Microsoft.Management/managementGroups/read", "Microsoft.Billing/invoices/download/action" ], "notActions": [ ], "dataActions": [], "notDataActions": [] } ], "createdOn": "2021-05-22T21:57:23.5764138Z", "updatedOn": "2021-05-22T21:57:23.5764138Z", "createdBy": "68f66d4c-c0eb-4009-819b-e5315d677d70", "updatedBy": "68f66d4c-c0eb-4009-819b-e5315d677d70" }, "id": "/providers/Microsoft.Authorization/roleDefinitions/17adabda-4bf1-4f4e-8c97-1f0cab6dea1c", "type": "Microsoft.Authorization/roleDefinitions", "name": "17adabda-4bf1-4f4e-8c97-1f0cab6dea1c" }, { "properties": { "roleName": "AcrPush", "type": "BuiltInRole", "description": "acr push", "assignableScopes": [ "/" ], "permissions": [ { "actions": [ "Microsoft.ContainerRegistry/registries/pull/read", "Microsoft.ContainerRegistry/registries/push/write" ], "notActions": [], "dataActions": [], "notDataActions": [] } ], "createdOn": "2018-10-29T17:52:32.5201177Z", "updatedOn": "2021-11-11T20:13:07.4993029Z", "createdBy": null, "updatedBy": null }, "id": "/providers/Microsoft.Authorization/roleDefinitions/8311e382-0749-4cb8-b61a-304f252e45ec", "type": "Microsoft.Authorization/roleDefinitions", "name": "8311e382-0749-4cb8-b61a-304f252e45ec" } ] }
列出角色定义
若要列出角色定义,请使用 角色定义 - 列出 REST API。 若要优化结果,请指定范围和可选筛选器。
从以下请求开始:
GET https://management.chinacloudapi.cn/{scope}/providers/Microsoft.Authorization/roleDefinitions?$filter={$filter}&api-version=2022-04-01对于租户级别的范围,可以使用此请求:
GET https://management.chinacloudapi.cn/providers/Microsoft.Authorization/roleDefinitions?filter={$filter}&api-version=2022-04-01在 URI 中,将 {scope} 替换为要列出角色定义的范围。
Scope 类型 providers/Microsoft.Management/managementGroups/{groupId1}管理组 subscriptions/{subscriptionId1}Subscription subscriptions/{subscriptionId1}/resourceGroups/myresourcegroup1资源组 subscriptions/{subscriptionId1}/resourceGroups/myresourcegroup1/providers/Microsoft.Web/sites/mysite1Resource 在前面的示例中,microsoft.web 是引用应用服务实例的资源提供程序。 同样,您可以使用任何其他资源供应商并指定其作用范围。 有关详细信息,请参阅 Azure 资源提供程序和类型 和支持的 Azure 资源提供程序操作。
将 {filter} 替换为要应用于筛选角色定义列表的条件。
过滤器 Description $filter=type+eq+'{type}'列出指定类型的角色定义。 角色的类型可以是 CustomRole或BuiltInRole。$filter=roleName+eq+'{roleName}'列出角色定义,其角色名称为“虚拟机贡献者”。 以下示例列出租户中的所有自定义角色:
请求
GET https://management.chinacloudapi.cn/providers/Microsoft.Authorization/roleDefinitions?$filter=type+eq+'CustomRole'&api-version=2022-04-01响应
{ "value": [ { "properties": { "roleName": "Billing Reader Plus", "type": "CustomRole", "description": "Read billing data and download invoices", "assignableScopes": [ "/subscriptions/eeee4e4e-ff5f-aa6a-bb7b-cccccc8c8c8c" ], "permissions": [ { "actions": [ "Microsoft.Authorization/*/read", "Microsoft.Billing/*/read", "Microsoft.Consumption/*/read", "Microsoft.Management/managementGroups/read", "Microsoft.Billing/invoices/download/action" ], "notActions": [ ], "dataActions": [], "notDataActions": [] } ], "createdOn": "2021-05-22T21:57:23.5764138Z", "updatedOn": "2021-05-22T21:57:23.5764138Z", "createdBy": "68f66d4c-c0eb-4009-819b-e5315d677d70", "updatedBy": "68f66d4c-c0eb-4009-819b-e5315d677d70" }, "id": "/providers/Microsoft.Authorization/roleDefinitions/17adabda-4bf1-4f4e-8c97-1f0cab6dea1c", "type": "Microsoft.Authorization/roleDefinitions", "name": "17adabda-4bf1-4f4e-8c97-1f0cab6dea1c" } ] }
列出角色定义
若要列出特定角色的详细信息,请使用 角色定义 - 获取 或 角色定义 - 按 ID REST API 获取。
从以下请求开始:
GET https://management.chinacloudapi.cn/{scope}/providers/Microsoft.Authorization/roleDefinitions/{roleDefinitionId}?api-version=2022-04-01对于租户级角色定义,可以使用以下请求:
GET https://management.chinacloudapi.cn/providers/Microsoft.Authorization/roleDefinitions/{roleDefinitionId}?api-version=2022-04-01在 URI 中,将 {scope} 替换为要列出角色定义的作用域。
Scope 类型 providers/Microsoft.Management/managementGroups/{groupId1}管理组 subscriptions/{subscriptionId1}Subscription subscriptions/{subscriptionId1}/resourceGroups/myresourcegroup1资源组 subscriptions/{subscriptionId1}/resourceGroups/myresourcegroup1/providers/Microsoft.Web/sites/mysite1Resource 将 {roleDefinitionId} 替换为角色定义标识符。
以下示例列出了 “读取者” 角色定义:
请求
GET https://management.chinacloudapi.cn/providers/Microsoft.Authorization/roleDefinitions/acdd72a7-3385-48ef-bd42-f606fba81ae7?api-version=2022-04-01
响应
{
"properties": {
"roleName": "Reader",
"type": "BuiltInRole",
"description": "View all resources, but does not allow you to make any changes.",
"assignableScopes": [
"/"
],
"permissions": [
{
"actions": [
"*/read"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
],
"createdOn": "2015-02-02T21:55:09.8806423Z",
"updatedOn": "2021-11-11T20:13:47.8628684Z",
"createdBy": null,
"updatedBy": null
},
"id": "/providers/Microsoft.Authorization/roleDefinitions/acdd72a7-3385-48ef-bd42-f606fba81ae7",
"type": "Microsoft.Authorization/roleDefinitions",
"name": "acdd72a7-3385-48ef-bd42-f606fba81ae7"
}