作为 Microsoft Entra ID 中的全局管理员,你可能无权访问租户中的所有订阅和管理组。 本文介绍如何自我提升对所有订阅和管理组的访问权限。
为何需要提升访问权限?
全局管理员有时可能需要执行以下操作:
- 在用户失去访问权限时重新获取对 Azure 订阅或管理组的访问权限
- 授予其他用户或自己对 Azure 订阅或管理组的访问权限
- 查看组织中的所有 Azure 订阅或管理组
- 允许自动化应用(例如发票或审计应用)访问所有 Azure 订阅或管理组
提升访问权限的工作原理是什么?
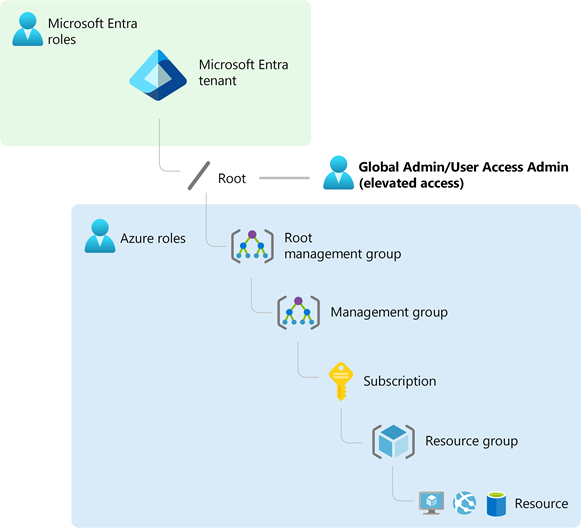
Microsoft Entra ID 和 Azure 资源彼此独立保护。 也就是说,Microsoft Entra 角色分配不授予对 Azure 资源的访问权限,Azure 角色分配也不授予对 Microsoft Entra ID 的访问权限。 但是,如果你是 Microsoft Entra ID 中的全局管理员,则你可为自己分配对租户中所有 Azure 订阅和管理组的访问权限。 如果你无权访问 Azure 订阅资源(如虚拟机或存储帐户),并且想使用全局管理员特权来获取这些资源的访问权限,则请使用此功能。
当你提升访问权限时,你将在 Azure 的根范围 (/) 内被分配为 用户访问管理员 角色。 此功能允许您查看所有资源,并在租户中的任何订阅或管理组中分配访问权限。 可以使用 Azure PowerShell、Azure CLI 或 REST API 删除“用户访问管理员”角色分配。
完成需在根范围执行的更改后,应删除此提升的访问权限。
步骤 1:提升全局管理员的访问权限
请按照这些步骤,使用 Azure 门户为全局管理员提升访问权限。
以全局管理员的身份登录到 Azure 门户。
如果使用 Microsoft Entra Privileged Identity Management,请激活全局管理员角色分配。
浏览到Microsoft Entra ID>管理>属性。
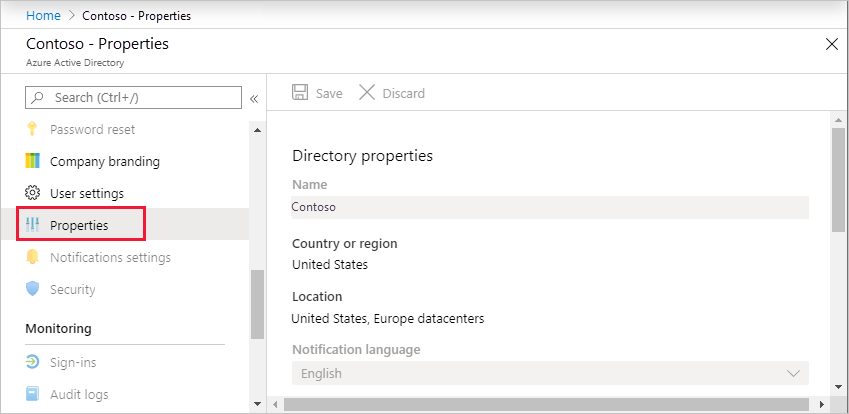
在“Azure 资源的访问管理”下,将开关设置为“是”。
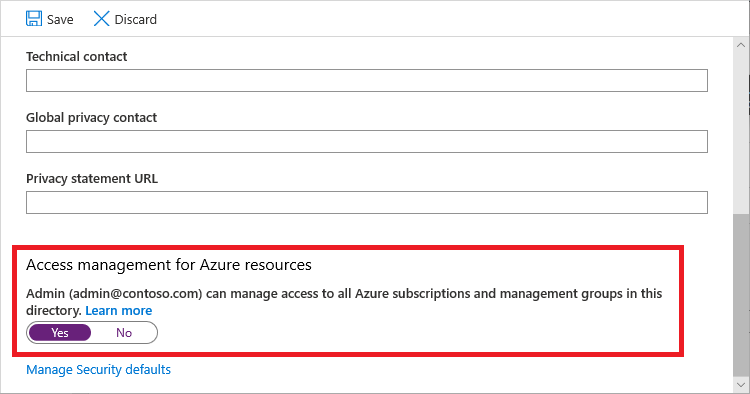
当您将切换开关设为“是”时,您将被授予在 Azure RBAC 中根范围 (/) 的“用户访问管理员”角色。 这将授予你在与此 Microsoft Entra 租户关联的所有 Azure 订阅和管理组中分配角色的权限。 此开关仅适用于分配到 Microsoft Entra ID 中全局管理员角色的用户。
将开关设为“否”时,会从用户帐户中删除 Azure RBAC 中的用户访问管理员角色。 你将无法再分配在与此 Microsoft Entra 租户关联的所有 Azure 订阅和管理组中的角色。 只能查看和管理已获取访问权限的 Azure 订阅和管理组。
选择“保存”以保存设置。
此设置不是全局属性,仅适用于当前已登录的用户。 无法提升所有全局管理员角色成员的访问权限。
请注销并重新登录以刷新访问权限。
现在,你应该有权访问租户中的所有订阅和管理组。 在查看“访问控制(IAM)”页时,你会注意到,系统为你分配了根范围的“用户访问管理员”角色。
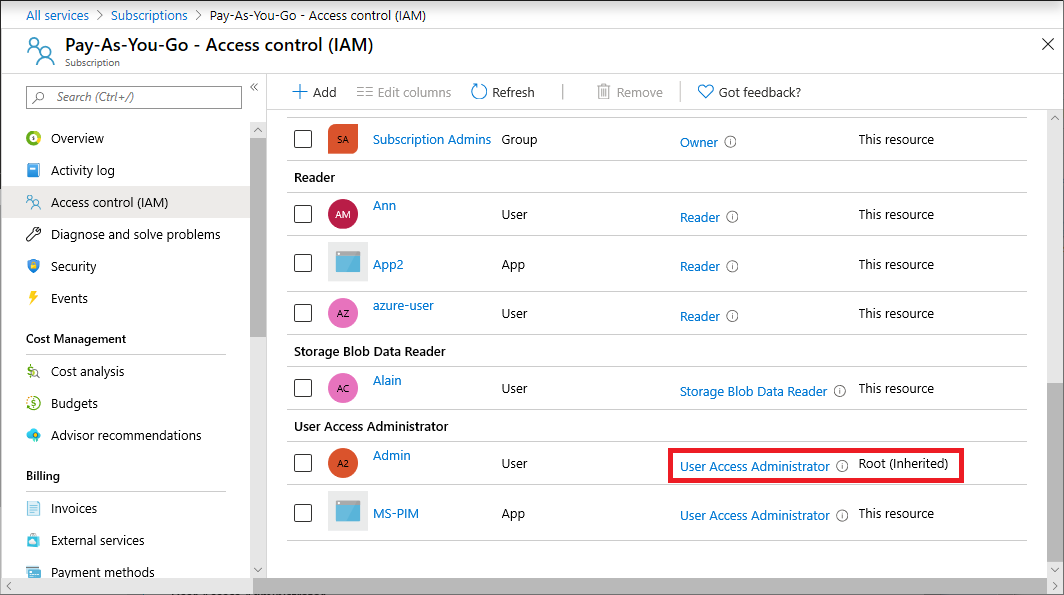
在提升的访问权限下做出必要的更改。
有关分配角色的信息,请参阅使用 Azure 门户分配 Azure 角色。 如果使用 Privileged Identity Management,请参阅发现要管理的 Azure 资源或分配 Azure 资源角色。
执行以下部分中的步骤以删除提升的访问权限。
步骤 2:移除已提升的访问权限
若要删除根范围 (/) 的“用户访问管理员”角色分配,请遵循以下步骤。
以提升访问权限时使用的用户身份登录。
浏览到Microsoft Entra ID>管理>属性。
将Azure 资源的访问管理切换回否。 由于此设置特定于用户,因此,必须以提升访问权限时所用的同一用户登录。
如果尝试移除“访问控制(IAM)”页上的“用户访问管理员”角色分配,你将看到以下消息。 若要删除角色分配,必须切换回“否”,或者使用 Azure PowerShell、Azure CLI 或 REST API。
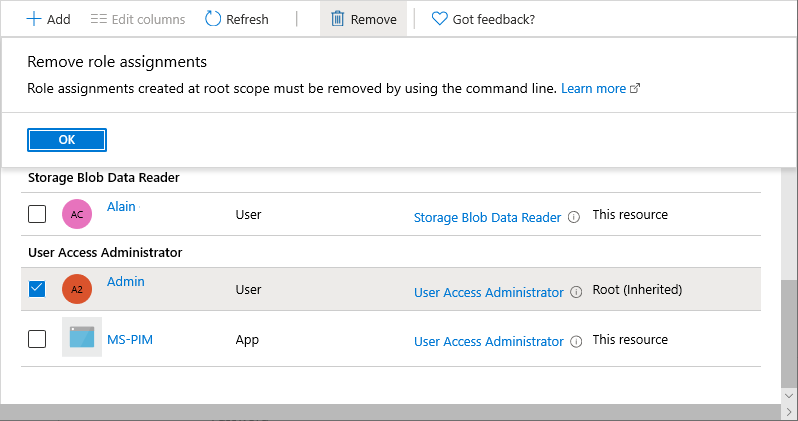
以全局管理员身份注销。
如果使用 Privileged Identity Management,请停用全局管理员角色分配。
步骤 1:提升全局管理员的访问权限
使用 Azure 门户或 REST API 提升全局管理员的访问权限。
步骤 2:列出根范围的角色分配 (/)
提升访问权限后,如果要列出用户在根范围 (/) 内的用户访问管理员角色分配,请使用 Get-AzRoleAssignment 命令。
Get-AzRoleAssignment | where {$_.RoleDefinitionName -eq "User Access Administrator" `
-and $_.SignInName -eq "<username@example.com>" -and $_.Scope -eq "/"}
RoleAssignmentId : /providers/Microsoft.Authorization/roleAssignments/11111111-1111-1111-1111-111111111111
Scope : /
DisplayName : username
SignInName : username@example.com
RoleDefinitionName : User Access Administrator
RoleDefinitionId : 18d7d88d-d35e-4fb5-a5c3-7773c20a72d9
ObjectId : 22222222-2222-2222-2222-222222222222
ObjectType : User
CanDelegate : False
步骤 3:移除已提升的访问权限
若要删除自己或其他用户在根范围 (/) 的“用户访问管理员”角色分配,请遵循以下步骤。
以能够删除提升访问权限的用户身份登录。 此用户可以是提升访问权限时所用的同一用户,也可以是在根范围拥有提升访问权限的另一个“全局管理员”。
使用 Remove-AzRoleAssignment 命令删除用户访问管理员角色分配。
Remove-AzRoleAssignment -SignInName <username@example.com> `
-RoleDefinitionName "User Access Administrator" -Scope "/"
步骤 1:提升全局管理员的访问权限
使用以下基本步骤,通过 Azure CLI 为全局管理员提升访问权限。
使用 az rest 命令调用 elevateAccess 终结点,这将授予你根范围 (/) 内的“用户访问管理员”角色。
az rest --method post --url "/providers/Microsoft.Authorization/elevateAccess?api-version=2016-07-01"
以提升的访问权限做出所需的更改。
有关分配角色的信息,请参阅使用 Azure CLI 分配 Azure 角色。
执行后续部分中的步骤以删除提升的访问权限。
步骤 2:列出根目录范围的角色分配情况 (/)
提升访问权限后,要列出用户在根范围 (/) 内的“用户访问管理员”角色分配,请使用 az role assignment list 命令。
az role assignment list --role "User Access Administrator" --scope "/"
[
{
"canDelegate": null,
"id": "/providers/Microsoft.Authorization/roleAssignments/11111111-1111-1111-1111-111111111111",
"name": "11111111-1111-1111-1111-111111111111",
"principalId": "22222222-2222-2222-2222-222222222222",
"principalName": "username@example.com",
"principalType": "User",
"roleDefinitionId": "/providers/Microsoft.Authorization/roleDefinitions/18d7d88d-d35e-4fb5-a5c3-7773c20a72d9",
"roleDefinitionName": "User Access Administrator",
"scope": "/",
"type": "Microsoft.Authorization/roleAssignments"
}
]
步骤 3:移除已提升的访问权限
若要删除自己或其他用户在根范围 (/) 的“用户访问管理员”角色分配,请遵循以下步骤。
以能够删除提升访问权限的用户身份登录。 此用户可以是提升访问权限时所用的同一用户,也可以是在根范围拥有提升访问权限的另一个“全局管理员”。
使用 az role assignment delete 命令删除“用户访问管理员”角色分配。
az role assignment delete --assignee username@example.com --role "User Access Administrator" --scope "/"
先决条件
必须使用以下版本:
-
2015-07-01 或更高版本,用于列出和删除角色分配
-
2016-07-01 或更高版本,用于提升访问权限
-
2018-07-01-preview 或更高版本,用于列出拒绝指派
有关详细信息,请参阅 Azure RBAC REST API 的 API 版本。
步骤 1:提升全局管理员的访问权限
使用以下基本步骤,通过 REST API 为全局管理员提升访问权限。
使用 REST 调用 elevateAccess,这将授予你根范围 (/) 内的“用户访问管理员”角色。
POST https://management.chinacloudapi.cn/providers/Microsoft.Authorization/elevateAccess?api-version=2016-07-01
在提升的访问权限下进行必要的更改。
有关分配角色的信息,请参阅使用 REST API 分配 Azure 角色。
执行后续部分中的步骤以删除提升的访问权限。
步骤 2:列出根范围 (/) 上的角色分配
一旦提升访问权限后,就可以查看用户在根范围 (/) 的所有角色分配。
调用角色分配 - 按范围列出,其中 {objectIdOfUser} 是您要检索角色分配的用户的对象 ID。
GET https://management.chinacloudapi.cn/providers/Microsoft.Authorization/roleAssignments?api-version=2022-04-01&$filter=principalId+eq+'{objectIdOfUser}'
步骤 3:在根范围 (/) 列出拒绝分配项
提升访问权限后,可以在根范围 (/) 列出用户的所有拒绝分配。
调用 拒绝分配 - 列出范围,其中 {objectIdOfUser} 是您要检索其拒绝分配的用户的对象 ID。
GET https://management.chinacloudapi.cn/providers/Microsoft.Authorization/denyAssignments?api-version=2022-04-01&$filter=gdprExportPrincipalId+eq+'{objectIdOfUser}'
步骤 4:移除已提升的访问权限
调用 elevateAccess 即为自己创建角色分配,因此若要撤销这些特权,需要删除自己在根范围 (/) 内的“用户访问管理员”角色分配。
调用角色分配 - 获取,其中 roleName = 用户访问管理员,由此确定用户访问管理员角色的名称 ID。
GET https://management.chinacloudapi.cn/providers/Microsoft.Authorization/roleDefinitions?api-version=2022-04-01&$filter=roleName+eq+'User Access Administrator'
{
"value": [
{
"properties": {
"roleName": "User Access Administrator",
"type": "BuiltInRole",
"description": "Lets you manage user access to Azure resources.",
"assignableScopes": [
"/"
],
"permissions": [
{
"actions": [
"*/read",
"Microsoft.Authorization/*"
],
"notActions": []
}
],
"createdOn": "0001-01-01T08:00:00.0000000Z",
"updatedOn": "2016-05-31T23:14:04.6964687Z",
"createdBy": null,
"updatedBy": null
},
"id": "/providers/Microsoft.Authorization/roleDefinitions/18d7d88d-d35e-4fb5-a5c3-7773c20a72d9",
"type": "Microsoft.Authorization/roleDefinitions",
"name": "18d7d88d-d35e-4fb5-a5c3-7773c20a72d9"
}
],
"nextLink": null
}
保存 name 参数中的 ID,在本例中为 18d7d88d-d35e-4fb5-a5c3-7773c20a72d9。
你还需要列出租户管理员在租户范围内的角色分配。 对于发起提升访问权限调用的租户管理员,请列出其在租户范围内的所有任务principalId。 这将列出租户中与 objectid 相关的所有分配任务。
GET https://management.chinacloudapi.cn/providers/Microsoft.Authorization/roleAssignments?api-version=2022-04-01&$filter=principalId+eq+'{objectid}'
注意
租户管理员不应有太多分配。 如果前面的查询返回的分配过多,则还可以在租户范围内查询所有分配,然后筛选结果:GET https://management.chinacloudapi.cn/providers/Microsoft.Authorization/roleAssignments?api-version=2022-04-01&$filter=atScope()
上述调用将返回角色分配列表。 在范围为 "/" 时,查找角色分配,其中 roleDefinitionId 以您在第 1 步中找到的角色名称 ID 结尾,并且 principalId 匹配租户管理员的 objectId。
示例角色分配:
{
"value": [
{
"properties": {
"roleDefinitionId": "/providers/Microsoft.Authorization/roleDefinitions/18d7d88d-d35e-4fb5-a5c3-7773c20a72d9",
"principalId": "{objectID}",
"scope": "/",
"createdOn": "2016-08-17T19:21:16.3422480Z",
"updatedOn": "2016-08-17T19:21:16.3422480Z",
"createdBy": "22222222-2222-2222-2222-222222222222",
"updatedBy": "22222222-2222-2222-2222-222222222222"
},
"id": "/providers/Microsoft.Authorization/roleAssignments/11111111-1111-1111-1111-111111111111",
"type": "Microsoft.Authorization/roleAssignments",
"name": "11111111-1111-1111-1111-111111111111"
}
],
"nextLink": null
}
同样,请保存 name 参数中的 ID,在本例中为 11111111-1111-1111-1111-111111111111。
最后,使用角色分配 ID 删除由 elevateAccess 添加的分配:
DELETE https://management.chinacloudapi.cn/providers/Microsoft.Authorization/roleAssignments/11111111-1111-1111-1111-111111111111?api-version=2022-04-01
查看具有提升访问权限的用户
如果你有具有提升访问权限的用户并且具有适当的权限,横幅会显示在 Azure 门户的几个位置。 全局管理员有权从根范围及更下级范围读取租户中所有 Azure 管理组和订阅的 Azure 角色分配。 本部分介绍如何确定你的租户中是否有具有提升访问权限的用户。
选项 1
在 Azure 门户中,以全局管理员身份登录。
浏览到Microsoft Entra ID>管理>属性。
在“Azure 资源的访问管理”下,查找以下横幅。
You have X users with elevated access. Microsoft Security recommends deleting access for users who have unnecessary elevated access. Manage elevated access users
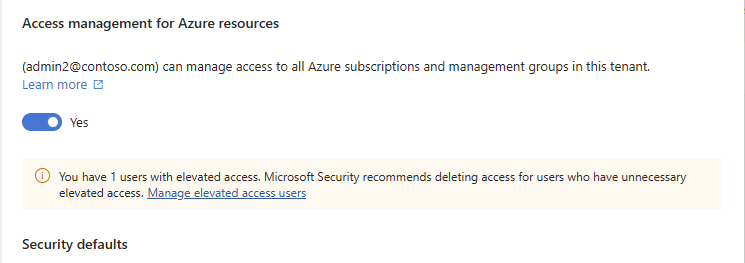
选择“管理提升访问权限用户”链接以查看具有提升访问权限的用户列表。
方法 2
在 Azure 门户中,使用提升的访问权限以全局管理员身份登录。
浏览到订阅。
选择“访问控制(IAM)”。
在页面顶部,查找以下横幅。
Action required: X users have elevated access in your tenant. You should take immediate action and remove all role assignments with elevated access. View role assignments
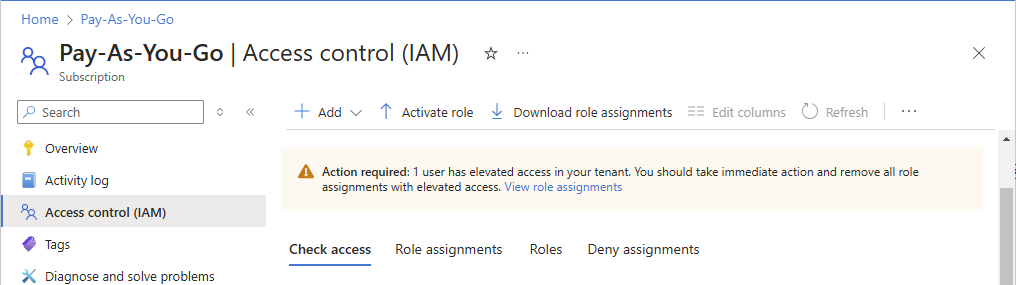
选择“查看角色分配”链接以查看具有提升访问权限的用户列表。
移除用户的提升访问权限
如果你有具有提升访问权限的用户,则应立即采取措施并移除该访问权限。 若要移除这些角色分配,你还必须具有提升的访问权限。 本部分介绍如何使用 Azure 门户移除租户中用户的提升访问权限。 此功能正在分阶段部署,因此它可能尚未在你的租户中提供。
以全局管理员的身份登录到 Azure 门户。
浏览到Microsoft Entra ID>管理>属性。
在“Azure 资源的访问管理”下,将切换开关设置为“是”,如之前在“步骤 1:提升全局管理员的访问权限”中所述。
选择“管理提升访问权限用户”链接。
“ 具有提升访问权限 的用户”窗格会显示租户中具有提升访问权限的用户列表。
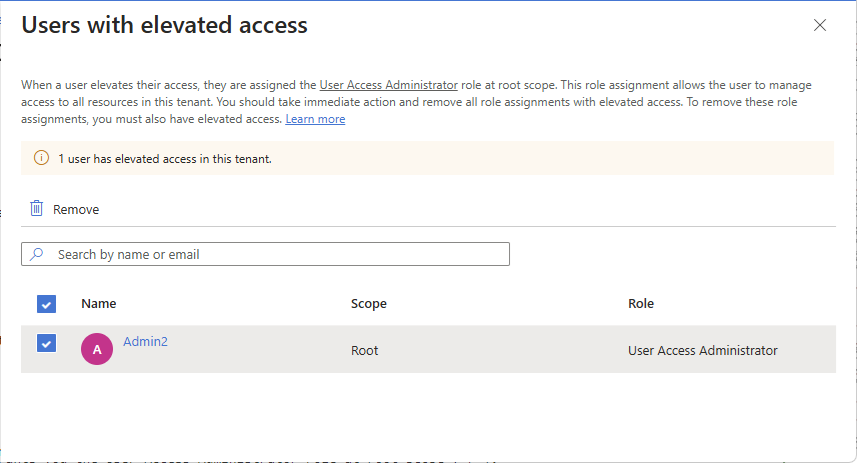
若要移除用户的提升访问权限,请在用户旁边添加复选标记,然后选择“移除”。
查看提升访问日志条目
当访问权限提升或移除时,会将一个条目添加到日志中。 作为 Microsoft Entra ID 中的管理员,你可能想要检查访问权限何时已提升,以及由谁提升。
提升访问权限日志条目显示在 Microsoft Entra 目录审核日志和 Azure 活动日志中。 目录审核日志和活动日志的高级访问日志条目包含类似的信息。 但是,目录审核日志更易于筛选和导出。 此外,使用导出功能可以流式传输访问事件,这些事件可用于警报和检测解决方案,例如 Microsoft Sentinel 或其他系统。 有关如何将日志发送到不同目标的信息,请参阅为活动日志配置 Microsoft Entra 诊断设置。
本部分介绍查看提升访问权限日志条目的不同方式。
重要
Microsoft Entra 目录审核日志中的提升访问日志条目当前以预览版推出。
此预览版在提供时没有附带服务级别协议,不建议将其用于生产工作负荷。 某些功能可能不受支持或者受限。
有关详细信息,请参阅适用于 Azure 预览版的补充使用条款。
以全局管理员的身份登录到 Azure 门户。
浏览到“Microsoft Entra ID”“监视”>“审核日志”>。
在“服务”筛选器中,选择“Azure RBAC (提升的访问权限)”,然后选择“应用”。
系统将显示提升访问权限日志。
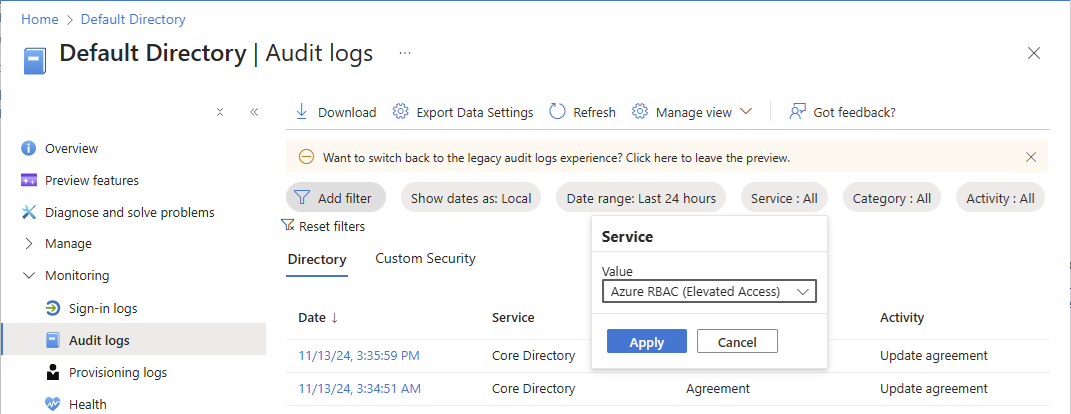
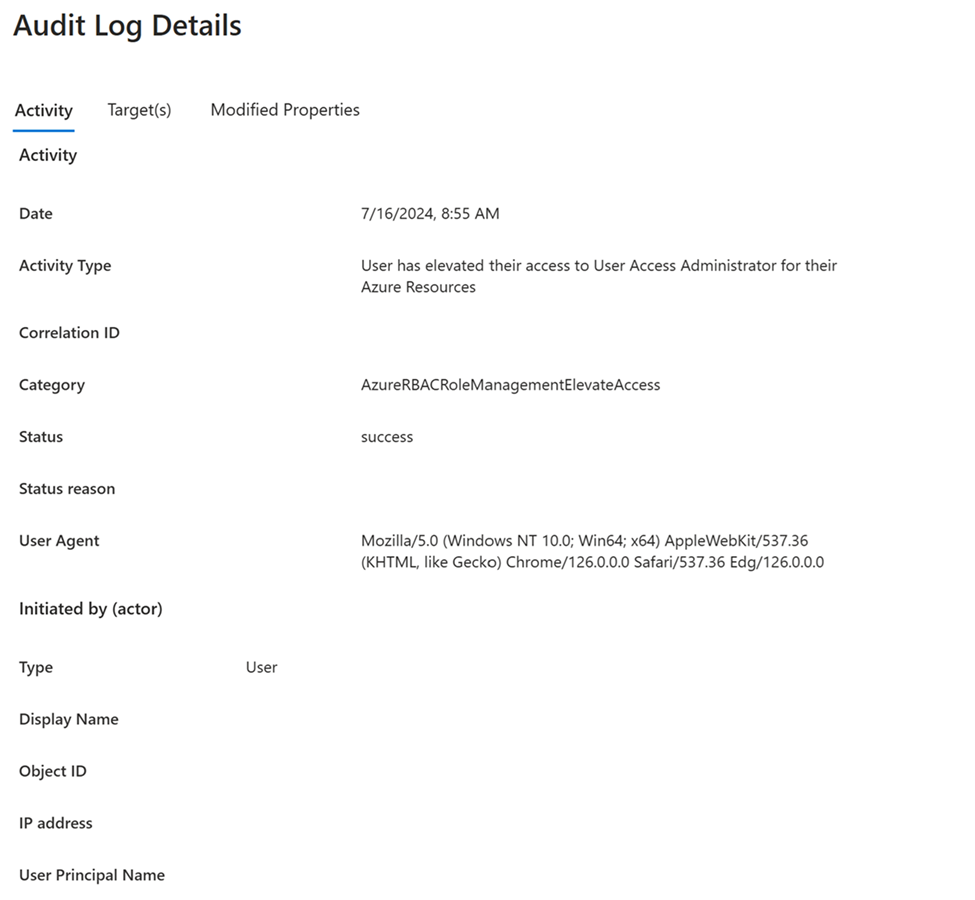
若要查看访问权限提升或移除时的详细信息,请选择这些审核日志条目。
User has elevated their access to User Access Administrator for their Azure Resources
The role assignment of User Access Administrator has been removed from the user
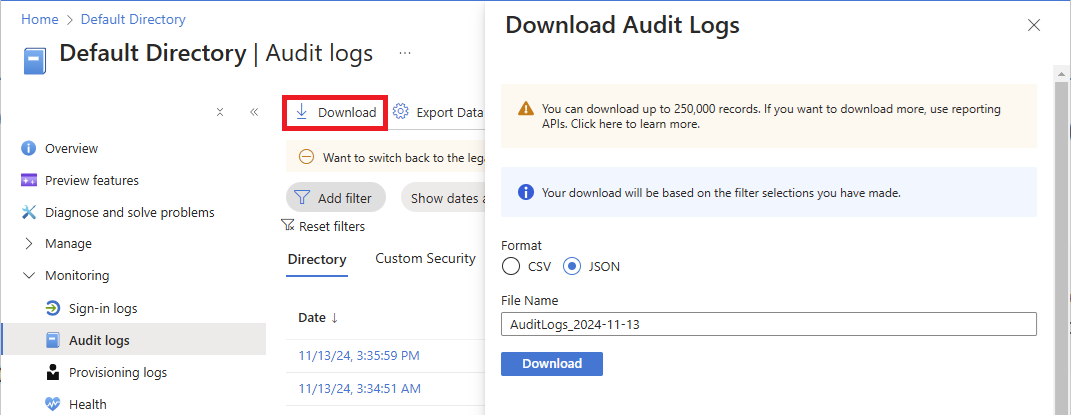
若要下载并查看 JSON 格式的日志条目的有效负载,请选择“下载”和“JSON”。
使用 Azure 门户查看提升访问权限日志条目
以全局管理员的身份登录到 Azure 门户。
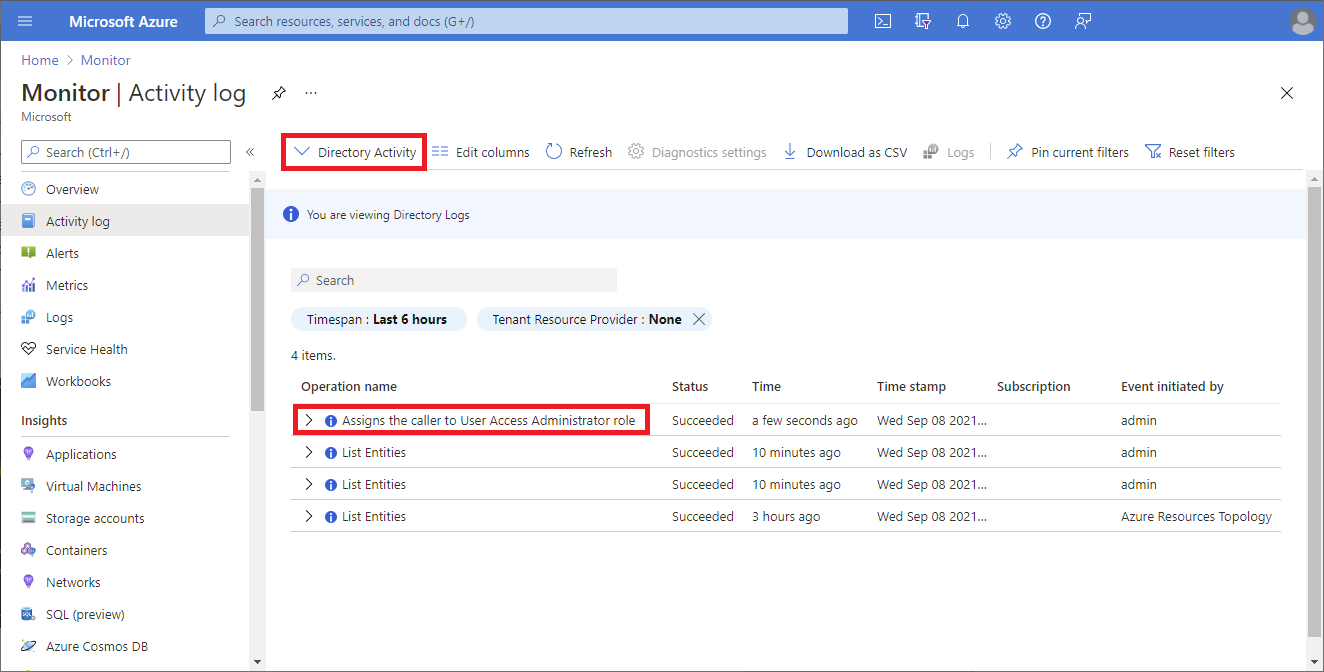
浏览到监控活动日志。>
将“活动”列表更改为“目录活动”。
搜索以下操作,它表示提升访问权限的动作。
Assigns the caller to User Access Administrator role
使用 Azure CLI 查看提升访问权限日志条目
使用 az login 命令以全局管理员身份登录。
使用 az rest 命令进行以下调用,你将必须按示例时间戳所示的日期进行筛选,并指定用于存储日志的文件名。
url 调用 API 来检索 Microsoft.Insights 中的日志。 输出将保存到你指定的文件中。
az rest --url "https://management.chinacloudapi.cn/providers/Microsoft.Insights/eventtypes/management/values?api-version=2015-04-01&$filter=eventTimestamp ge '2021-09-10T20:00:00Z'" > output.txt
在输出文件中,搜索 elevateAccess。
日志将类似于以下内容,可以在其中查看操作发生时间的时间戳和调用者。
"submissionTimestamp": "2021-08-27T15:42:00.1527942Z",
"subscriptionId": "",
"tenantId": "33333333-3333-3333-3333-333333333333"
},
{
"authorization": {
"action": "Microsoft.Authorization/elevateAccess/action",
"scope": "/providers/Microsoft.Authorization"
},
"caller": "user@example.com",
"category": {
"localizedValue": "Administrative",
"value": "Administrative"
},
使用 Azure CLI 为组授予查看提升访问日志条目的权限
如果你希望能够定期获取提升访问权限日志条目,可以向组委托访问权限,然后使用 Azure CLI。
浏览到:Microsoft Entra ID>中的组。
创建新的安全组,并记下组对象 ID。
使用 az login 命令以全局管理员身份登录。
使用 az role assignment create 命令将读取者角色分配给只能在租户级别读取日志的组,这些日志位于 Microsoft/Insights。
az role assignment create --assignee "{groupId}" --role "Reader" --scope "/providers/Microsoft.Insights"
将读取日志的用户添加到之前创建的组中。
该组中的用户现在可以定期运行 az rest 命令来查看提升访问权限日志条目。
az rest --url "https://management.chinacloudapi.cn/providers/Microsoft.Insights/eventtypes/management/values?api-version=2015-04-01&$filter=eventTimestamp ge '2021-09-10T20:00:00Z'" > output.txt
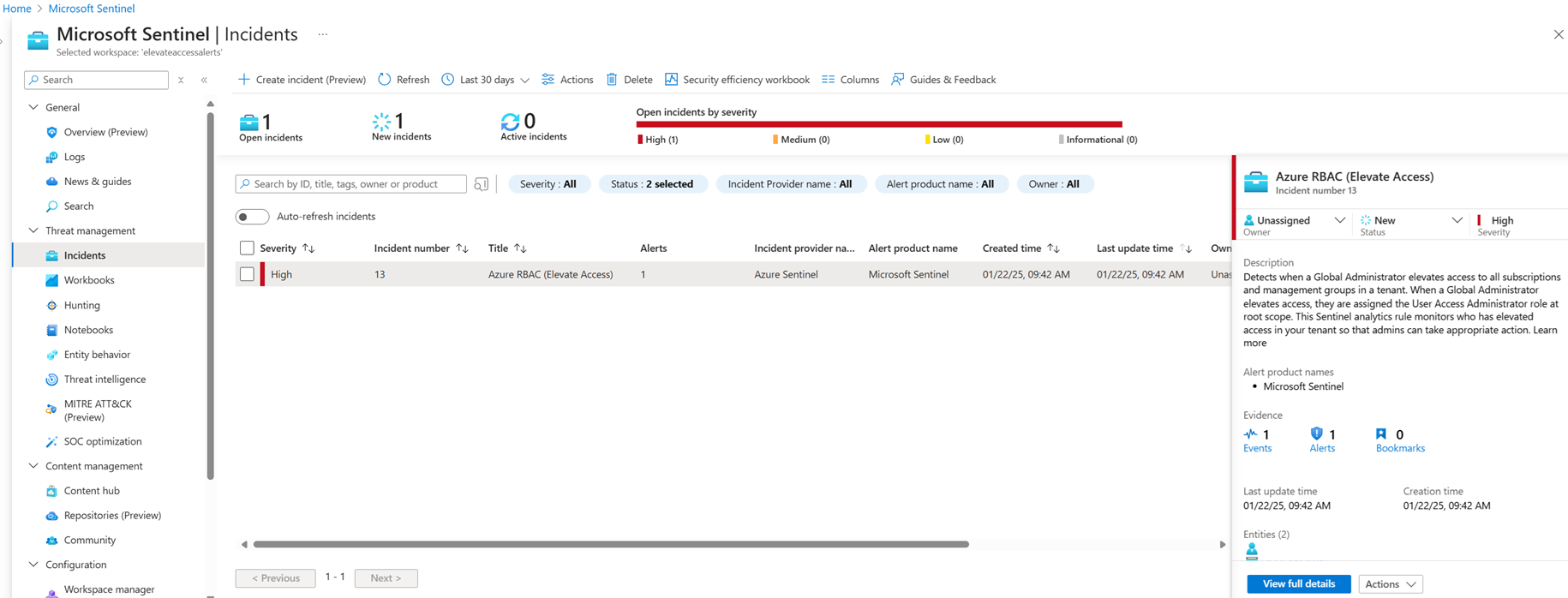
使用 Microsoft Sentinel 检测提升访问权限事件
你可以使用 Microsoft Sentinel 检测提升访问权限的事件并深入了解潜在的欺诈活动。
Microsoft Sentinel 是一个安全信息和事件管理 (SIEM) 平台,提供安全分析和威胁响应能力。 本部分介绍如何将 Microsoft Entra 审核日志连接到 Microsoft Sentinel,以便检测组织中提升访问权限的事件。
步骤 1:设置 Microsoft Sentinel
遵循以下步骤入门 Microsoft Sentinel:
查找现有的 Log Analytics 工作区或 创建新工作区。
将 Microsoft Sentinel 添加到工作区。
第 2 步:将 Microsoft Entra 数据连接到 Microsoft Sentinel
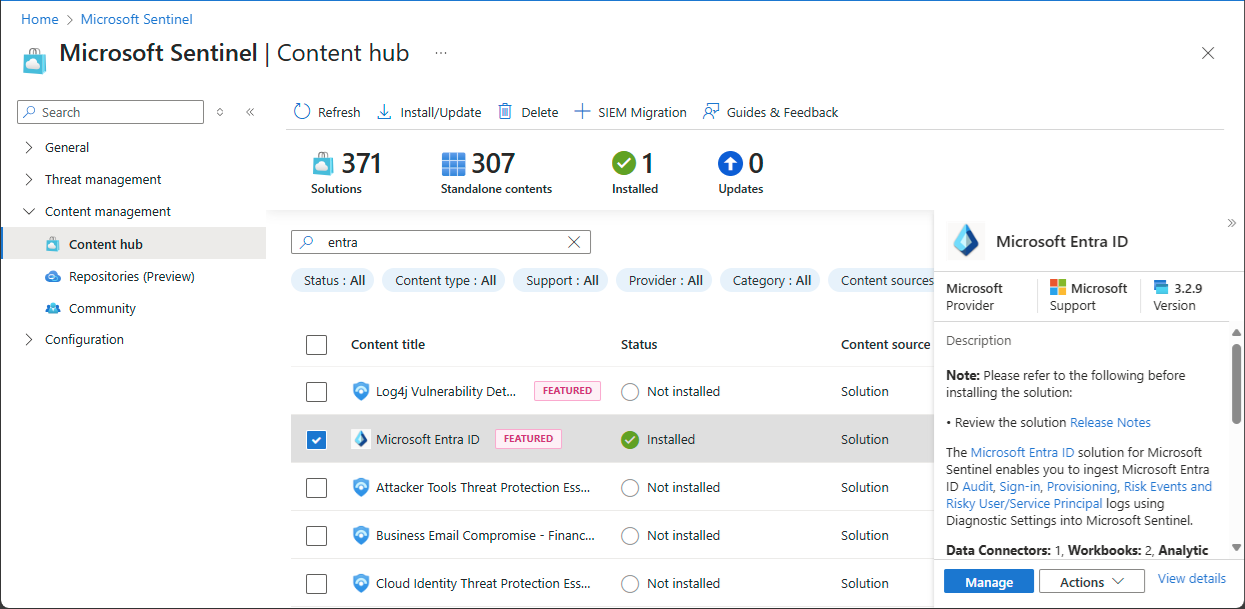
在此步骤中,安装 Microsoft Entra ID 解决方案,并使用 Microsoft Entra ID 连接器 来收集 Microsoft Entra ID 的数据。
你的组织可能已经配置了诊断设置以便集成 Microsoft Entra 审核日志。 请按照如何访问诊断设置中的指示查看诊断设置,以进行确认。
按照探索和管理 Microsoft Sentinel 现成内容中的步骤安装 Microsoft Entra ID 解决方案。
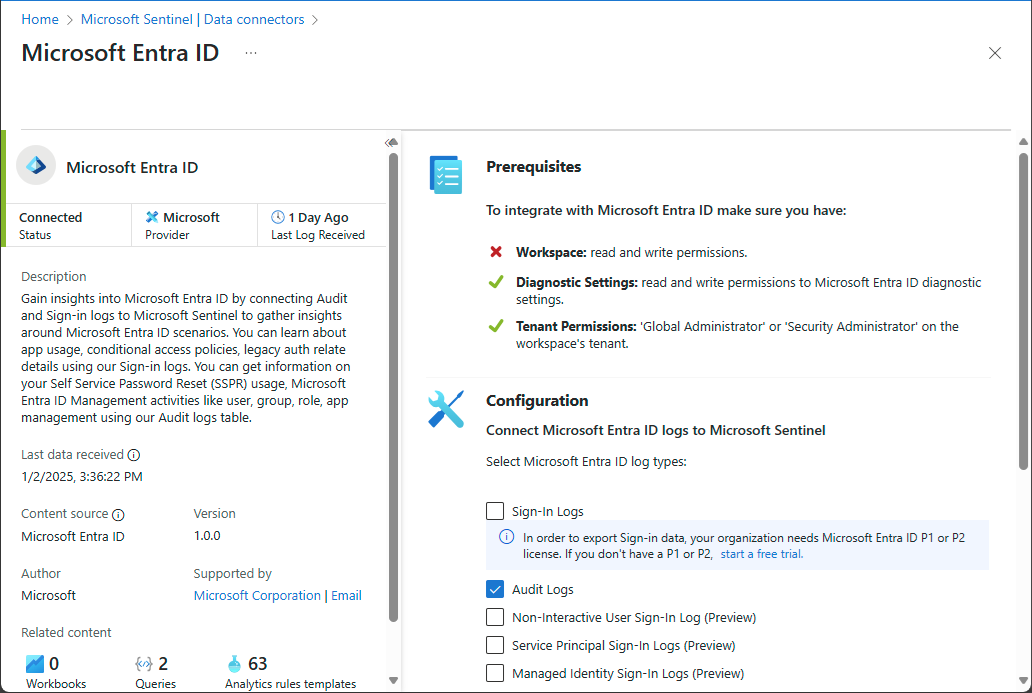
按照将 Microsoft Entra 数据连接至 Microsoft Sentinel 中的步骤,使用 Microsoft Entra ID 连接器来收集 Microsoft Entra ID 的数据。
在“数据连接器”页面上,勾选“审核日志”。
第 3 步:创建提升访问权限的规则
在此步骤中,在模板的基础上创建计划分析规则,以检查 Microsoft Entra 审核日志中提升访问权限的事件。
按照从模板创建规则中的步骤创建提升访问权限的分析规则。
选择“Azure RBAC(提升访问权限)”模板,然后在详细信息窗格中选择“创建规则”按钮。
如果未看到详细信息窗格,请在右边缘选择展开图标。

在“分析规则向导”中,使用默认设置创建新的计划规则。
第 4 步:查看提升访问权限的事件
在此步骤中,你可以查看和调查提升访问权限的事件。
后续步骤