Azure Service Fabric 是一款分布式系统平台,可方便用户轻松打包、部署和管理可缩放的可靠微服务和容器。 Service Fabric 群集是一组联网的虚拟机,可在其中部署和管理微服务。 本文介绍如何使用 Bicep 在 Azure 中部署 Service Fabric 测试群集。
Bicep 是一种特定于域的语言 (DSL),使用声明性语法来部署 Azure 资源。 它提供简明的语法、可靠的类型安全性以及对代码重用的支持。 Bicep 会针对你的 Azure 基础结构即代码解决方案提供最佳创作体验。
此五节点 Windows 群集由一个自签名证书提供保护,因此仅适用于教学(不能用于生产工作负载)。 我们将使用 Azure PowerShell 来部署 Bicep 文件。
先决条件
如果没有 Azure 订阅,请在开始之前创建一个免费帐户。
安装 Service Fabric SDK 和 PowerShell 模块
若要完成本快速入门,需要安装 Service Fabric SDK 和 PowerShell 模块。
下载示例 Bicep 文件和证书帮助程序脚本
克隆或下载 Azure 资源管理器快速入门模板存储库。 或者,在本地从 service-fabric-secure-cluster-5-node-1-nodetype 文件夹复制要使用的以下文件:
登录 Azure
登录到 Azure,指定要用于创建 Service Fabric 群集的订阅。
# Sign in to your Azure account
Connect-AzAccount -Environment AzureChinaCloud -SubscriptionId "<subscription ID>"
创建一个存储在 Key Vault 中的自签名证书
Service Fabric 使用 X.509 证书来保护群集并提供应用程序安全功能,它使用 Key Vault 来管理那些证书。 若要成功创建群集,需要使用群集证书来实现节点到节点通信。 为了创建此快速入门测试群集,我们将创建一个用于群集身份验证的自签名证书。 生产工作负载需要多个使用正确配置的 Windows Server 证书服务创建的证书,或由已批准的证书颁发机构 (CA) 提供的证书。
# Designate unique (within cloudapp.chinacloudapi.cn) names for your resources
$resourceGroupName = "SFQuickstartRG"
$keyVaultName = "SFQuickstartKV"
# Create a new resource group for your Key Vault and Service Fabric cluster
New-AzResourceGroup -Name $resourceGroupName -Location Southchinanorth
# Create a Key Vault enabled for deployment
New-AzKeyVault -VaultName $keyVaultName -ResourceGroupName $resourceGroupName -Location Southchinanorth -EnabledForDeployment
# Generate a certificate and upload it to Key Vault
.\scripts\New-ServiceFabricClusterCertificate.ps1
此脚本会提示你输入以下内容(请务必修改下面的示例值中的 CertDNSName 和 KeyVaultName):
- 密码: Password!1
- CertDNSName:sfquickstart.chinanorth.cloudapp.chinacloudapi.cn
- KeyVaultName:SFQuickstartKV
- KeyVaultSecretName: clustercert
完成后,该脚本会提供部署所需的参数值。 请确保将它们存储在以下变量中,因为部署需要它们:
$sourceVaultId = "<Source Vault Resource Id>"
$certUrlValue = "<Certificate URL>"
$certThumbprint = "<Certificate Thumbprint>"
查阅 Bicep 文件
本快速入门中使用的 Bicep 文件来自 Azure 快速入门模板。
@description('Location of the Cluster')
param location string = resourceGroup().location
@description('Name of your cluster - Between 3 and 23 characters. Letters and numbers only')
param clusterName string
@description('Remote desktop user Id')
param adminUsername string
@description('Remote desktop user password. Must be a strong password')
@secure()
param adminPassword string
@description('VM image Publisher')
param vmImagePublisher string = 'MicrosoftWindowsServer'
@description('VM image offer')
param vmImageOffer string = 'WindowsServer'
@description('VM image SKU')
param vmImageSku string = '2019-Datacenter'
@description('VM image version')
param vmImageVersion string = 'latest'
@description('Input endpoint1 for the application to use. Replace it with what your application uses')
param loadBalancedAppPort1 int = 80
@description('Input endpoint2 for the application to use. Replace it with what your application uses')
param loadBalancedAppPort2 int = 8081
@description('The store name where the cert will be deployed in the virtual machine')
@allowed([
'My'
])
param certificateStoreValue string = 'My'
@description('Certificate Thumbprint')
param certificateThumbprint string
@description('Resource Id of the key vault, is should be in the format of /subscriptions/<Sub ID>/resourceGroups/<Resource group name>/providers/Microsoft.KeyVault/vaults/<vault name>')
param sourceVaultResourceId string
@description('Refers to the location URL in your key vault where the certificate was uploaded')
param certificateUrlValue string
@description('Protection level.Three values are allowed - EncryptAndSign, Sign, None. It is best to keep the default of EncryptAndSign, unless you have a need not to')
@allowed([
'None'
'Sign'
'EncryptAndSign'
])
param clusterProtectionLevel string = 'EncryptAndSign'
@description('Instance count for node type')
param nt0InstanceCount int = 5
@description('The drive to use to store data on a cluster node.')
@allowed([
'OS'
'Temp'
])
param nodeDataDrive string = 'Temp'
@description('The VM size to use for cluster nodes.')
param nodeTypeSize string = 'Standard_D2_v3'
param tenantId string
param clusterApplication string
param clientapplication string
var dnsName = clusterName
var vmName = 'vm'
var virtualNetworkName = 'VNet'
var addressPrefix = '10.0.0.0/16'
var nicName = 'NIC'
var lbIPName = 'PublicIP-LB-FE'
var overProvision = false
var nt0applicationStartPort = 20000
var nt0applicationEndPort = 30000
var nt0ephemeralStartPort = 49152
var nt0ephemeralEndPort = 65534
var nt0fabricTcpGatewayPort = 19000
var nt0fabricHttpGatewayPort = 19080
var subnet0Name = 'Subnet-0'
var subnet0Prefix = '10.0.0.0/24'
var subnet0Ref = resourceId('Microsoft.Network/virtualNetworks/subnets/', virtualNetworkName, subnet0Name)
var supportLogStorageAccountName = '${uniqueString(resourceGroup().id)}2'
var applicationDiagnosticsStorageAccountName = '${uniqueString(resourceGroup().id)}3'
var lbName = 'LB-${clusterName}-${vmNodeType0Name}'
var lbIPConfig0 = resourceId('Microsoft.Network/loadBalancers/frontendIPConfigurations/', lbName, 'LoadBalancerIPConfig')
var lbPoolID0 = resourceId('Microsoft.Network/loadBalancers/backendAddressPools', lbName, 'LoadBalancerBEAddressPool')
var lbProbeID0 = resourceId('Microsoft.Network/loadBalancers/probes', lbName, 'FabricGatewayProbe')
var lbHttpProbeID0 = resourceId('Microsoft.Network/loadBalancers/probes', lbName, 'FabricHttpGatewayProbe')
var lbNatPoolID0 = resourceId('Microsoft.Network/loadBalancers/inboundNatPools', lbName, 'LoadBalancerBEAddressNatPool')
var vmNodeType0Name = toLower('NT1${vmName}')
var vmNodeType0Size = nodeTypeSize
resource supportLogStorageAccount 'Microsoft.Storage/storageAccounts@2023-01-01' = {
name: supportLogStorageAccountName
location: location
sku: {
name: 'Standard_LRS'
}
kind: 'Storage'
tags: {
resourceType: 'Service Fabric'
clusterName: clusterName
}
properties: {}
}
resource applicationDiagnosticsStorageAccount 'Microsoft.Storage/storageAccounts@2023-01-01' = {
name: applicationDiagnosticsStorageAccountName
location: location
sku: {
name: 'Standard_LRS'
}
kind: 'Storage'
tags: {
resourceType: 'Service Fabric'
clusterName: clusterName
}
properties: {}
}
resource virtualNetwork 'Microsoft.Network/virtualNetworks@2023-09-01' = {
name: virtualNetworkName
location: location
tags: {
resourceType: 'Service Fabric'
clusterName: clusterName
}
properties: {
addressSpace: {
addressPrefixes: [
addressPrefix
]
}
subnets: [
{
name: subnet0Name
properties: {
addressPrefix: subnet0Prefix
}
}
]
}
}
resource lbIP 'Microsoft.Network/publicIPAddresses@2023-09-01' = {
name: lbIPName
location: location
tags: {
resourceType: 'Service Fabric'
clusterName: clusterName
}
properties: {
dnsSettings: {
domainNameLabel: dnsName
}
publicIPAllocationMethod: 'Dynamic'
}
}
resource lb 'Microsoft.Network/loadBalancers@2023-09-01' = {
name: lbName
location: location
tags: {
resourceType: 'Service Fabric'
clusterName: clusterName
}
properties: {
frontendIPConfigurations: [
{
name: 'LoadBalancerIPConfig'
properties: {
publicIPAddress: {
id: lbIP.id
}
}
}
]
backendAddressPools: [
{
name: 'LoadBalancerBEAddressPool'
properties: {}
}
]
loadBalancingRules: [
{
name: 'LBRule'
properties: {
backendAddressPool: {
id: lbPoolID0
}
backendPort: nt0fabricTcpGatewayPort
enableFloatingIP: false
frontendIPConfiguration: {
id: lbIPConfig0
}
frontendPort: nt0fabricTcpGatewayPort
idleTimeoutInMinutes: 5
probe: {
id: lbProbeID0
}
protocol: 'Tcp'
}
}
{
name: 'LBHttpRule'
properties: {
backendAddressPool: {
id: lbPoolID0
}
backendPort: nt0fabricHttpGatewayPort
enableFloatingIP: false
frontendIPConfiguration: {
id: lbIPConfig0
}
frontendPort: nt0fabricHttpGatewayPort
idleTimeoutInMinutes: 5
probe: {
id: lbHttpProbeID0
}
protocol: 'Tcp'
}
}
{
name: 'AppPortLBRule1'
properties: {
backendAddressPool: {
id: lbPoolID0
}
backendPort: loadBalancedAppPort1
enableFloatingIP: false
frontendIPConfiguration: {
id: lbIPConfig0
}
frontendPort: loadBalancedAppPort1
idleTimeoutInMinutes: 5
probe: {
id: resourceId('Microsoft.Network/loadBalancers/probes', lbName, 'AppPortProbe1')
}
protocol: 'Tcp'
}
}
{
name: 'AppPortLBRule2'
properties: {
backendAddressPool: {
id: lbPoolID0
}
backendPort: loadBalancedAppPort2
enableFloatingIP: false
frontendIPConfiguration: {
id: lbIPConfig0
}
frontendPort: loadBalancedAppPort2
idleTimeoutInMinutes: 5
probe: {
id: resourceId('Microsoft.Network/loadBalancers/probes', lbName, 'AppPortProbe2')
}
protocol: 'Tcp'
}
}
]
probes: [
{
name: 'FabricGatewayProbe'
properties: {
intervalInSeconds: 5
numberOfProbes: 2
port: nt0fabricTcpGatewayPort
protocol: 'Tcp'
}
}
{
name: 'FabricHttpGatewayProbe'
properties: {
intervalInSeconds: 5
numberOfProbes: 2
port: nt0fabricHttpGatewayPort
protocol: 'Tcp'
}
}
{
name: 'AppPortProbe1'
properties: {
intervalInSeconds: 5
numberOfProbes: 2
port: loadBalancedAppPort1
protocol: 'Tcp'
}
}
{
name: 'AppPortProbe2'
properties: {
intervalInSeconds: 5
numberOfProbes: 2
port: loadBalancedAppPort2
protocol: 'Tcp'
}
}
]
inboundNatPools: [
{
name: 'LoadBalancerBEAddressNatPool'
properties: {
backendPort: 3389
frontendIPConfiguration: {
id: lbIPConfig0
}
frontendPortRangeEnd: 4500
frontendPortRangeStart: 3389
protocol: 'Tcp'
}
}
]
}
}
resource vmNodeType0 'Microsoft.Compute/virtualMachineScaleSets@2023-09-01' = {
name: vmNodeType0Name
location: location
sku: {
name: vmNodeType0Size
capacity: nt0InstanceCount
tier: 'Standard'
}
tags: {
resourceType: 'Service Fabric'
clusterName: clusterName
}
properties: {
overprovision: overProvision
upgradePolicy: {
mode: 'Automatic'
}
virtualMachineProfile: {
extensionProfile: {
extensions: [
{
name: 'ServiceFabricNodeVmExt_vmNodeType0Name'
properties: {
type: 'ServiceFabricNode'
autoUpgradeMinorVersion: true
protectedSettings: {
StorageAccountKey1: supportLogStorageAccount.listKeys().keys[0].value
StorageAccountKey2: supportLogStorageAccount.listkeys().keys[1].value
}
publisher: 'Microsoft.Azure.ServiceFabric'
settings: {
clusterEndpoint: cluster.properties.clusterEndpoint
nodeTypeRef: vmNodeType0Name
dataPath: '${((nodeDataDrive == 'OS') ? 'C' : 'D')}:\\\\SvcFab'
durabilityLevel: 'Silver'
nicPrefixOverride: subnet0Prefix
certificate: {
thumbprint: certificateThumbprint
x509StoreName: certificateStoreValue
}
}
typeHandlerVersion: '1.0'
}
}
{
name: 'VMDiagnosticsVmExt_vmNodeType0Name'
properties: {
type: 'IaaSDiagnostics'
autoUpgradeMinorVersion: true
protectedSettings: {
storageAccountName: applicationDiagnosticsStorageAccountName
storageAccountKey: listKeys(applicationDiagnosticsStorageAccount.id, '2021-01-01').keys[0].value
storageAccountEndPoint: 'https://${environment().suffixes.storage}'
}
publisher: 'Microsoft.Azure.Diagnostics'
settings: {
WadCfg: {
DiagnosticMonitorConfiguration: {
overallQuotaInMB: '50000'
EtwProviders: {
EtwEventSourceProviderConfiguration: [
{
provider: 'Microsoft-ServiceFabric-Actors'
scheduledTransferKeywordFilter: '1'
scheduledTransferPeriod: 'PT5M'
DefaultEvents: {
eventDestination: 'ServiceFabricReliableActorEventTable'
}
}
{
provider: 'Microsoft-ServiceFabric-Services'
scheduledTransferPeriod: 'PT5M'
DefaultEvents: {
eventDestination: 'ServiceFabricReliableServiceEventTable'
}
}
]
EtwManifestProviderConfiguration: [
{
provider: 'cbd93bc2-71e5-4566-b3a7-595d8eeca6e8'
scheduledTransferLogLevelFilter: 'Information'
scheduledTransferKeywordFilter: '4611686018427387904'
scheduledTransferPeriod: 'PT5M'
DefaultEvents: {
eventDestination: 'ServiceFabricSystemEventTable'
}
}
]
}
}
}
StorageAccount: applicationDiagnosticsStorageAccountName
}
typeHandlerVersion: '1.5'
}
}
]
}
networkProfile: {
networkInterfaceConfigurations: [
{
name: '${nicName}-0'
properties: {
ipConfigurations: [
{
name: '${nicName}-0'
properties: {
loadBalancerBackendAddressPools: [
{
id: lbPoolID0
}
]
loadBalancerInboundNatPools: [
{
id: lbNatPoolID0
}
]
subnet: {
id: subnet0Ref
}
}
}
]
primary: true
}
}
]
}
osProfile: {
adminPassword: adminPassword
adminUsername: adminUsername
computerNamePrefix: vmNodeType0Name
secrets: [
{
sourceVault: {
id: sourceVaultResourceId
}
vaultCertificates: [
{
certificateStore: certificateStoreValue
certificateUrl: certificateUrlValue
}
]
}
]
}
storageProfile: {
imageReference: {
publisher: vmImagePublisher
offer: vmImageOffer
sku: vmImageSku
version: vmImageVersion
}
osDisk: {
managedDisk: {
storageAccountType: 'StandardSSD_LRS'
}
caching: 'ReadOnly'
createOption: 'FromImage'
}
}
}
}
dependsOn: [
virtualNetwork
lb
]
}
resource cluster 'Microsoft.ServiceFabric/clusters@2023-11-01-preview' = {
name: clusterName
location: location
tags: {
resourceType: 'Service Fabric'
clusterName: clusterName
}
properties: {
azureActiveDirectory: {
clientApplication: clientapplication
clusterApplication: clusterApplication
tenantId: tenantId
}
certificate: {
thumbprint: certificateThumbprint
x509StoreName: certificateStoreValue
}
diagnosticsStorageAccountConfig: {
blobEndpoint: reference(supportLogStorageAccount.id, '2021-01-01').primaryEndpoints.blob
protectedAccountKeyName: 'StorageAccountKey1'
queueEndpoint: reference(supportLogStorageAccount.id, '2021-01-01').primaryEndpoints.queue
storageAccountName: supportLogStorageAccountName
tableEndpoint: reference(supportLogStorageAccount.id, '2021-01-01').primaryEndpoints.table
}
fabricSettings: [
{
parameters: [
{
name: 'ClusterProtectionLevel'
value: clusterProtectionLevel
}
]
name: 'Security'
}
]
managementEndpoint: 'https://${lbIP.properties.dnsSettings.fqdn}:${nt0fabricHttpGatewayPort}'
nodeTypes: [
{
name: vmNodeType0Name
applicationPorts: {
endPort: nt0applicationEndPort
startPort: nt0applicationStartPort
}
clientConnectionEndpointPort: nt0fabricTcpGatewayPort
durabilityLevel: 'Silver'
ephemeralPorts: {
endPort: nt0ephemeralEndPort
startPort: nt0ephemeralStartPort
}
httpGatewayEndpointPort: nt0fabricHttpGatewayPort
isPrimary: true
vmInstanceCount: nt0InstanceCount
}
]
reliabilityLevel: 'Silver'
upgradeMode: 'Automatic'
vmImage: 'Windows'
}
}
output location string = location
output name string = cluster.name
output resourceGroupName string = resourceGroup().name
output resourceId string = cluster.id
output clusterProperties object = cluster.properties
该 Bicep 文件中定义了多个 Azure 资源:
- Microsoft.Storage/storageAccounts
- Microsoft.Network/virtualNetworks
- Microsoft.Network/publicIPAddresses
- Microsoft.Network/loadBalancers
- Microsoft.Compute/virtualMachineScaleSets
- Microsoft.ServiceFabric/clusters
自定义参数文件
打开 azuredeploy.parameters.json 并编辑参数值,以实现以下目的:
- clusterName 与你在创建群集证书时为 CertDNSName 提供的值匹配
- adminUserName 是不同于默认的 GEN-UNIQUE 令牌的某个值
- adminPassword 是不同于默认的 GEN-PASSWORD 令牌的某个值
- certificateThumbprint、sourceVaultResourceId 和 certificateUrlValue 都是空字符串 ()
例如:
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentParameters.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"clusterName": {
"value": "sfquickstart"
},
"adminUsername": {
"value": "testadm"
},
"adminPassword": {
"value": "Password#1234"
},
"certificateThumbprint": {
"value": ""
},
"sourceVaultResourceId": {
"value": ""
},
"certificateUrlValue": {
"value": ""
}
}
}
部署 Bicep 文件
在变量中存储 Bicep 文件和参数文件的路径,然后部署 Bicep 文件。
$templateFilePath = "<full path to main.bicep>"
$parameterFilePath = "<full path to azuredeploy.parameters.json>"
New-AzResourceGroupDeployment `
-ResourceGroupName $resourceGroupName `
-TemplateFile $templateFilePath `
-TemplateParameterFile $parameterFilePath `
-CertificateThumbprint $certThumbprint `
-CertificateUrlValue $certUrlValue `
-SourceVaultResourceId $sourceVaultId `
-Verbose
查看已部署的资源
部署完成后,在输出中找到 managementEndpoint 值,然后在 Web 浏览器中打开该地址,以便在 Service Fabric Explorer 中查看群集。
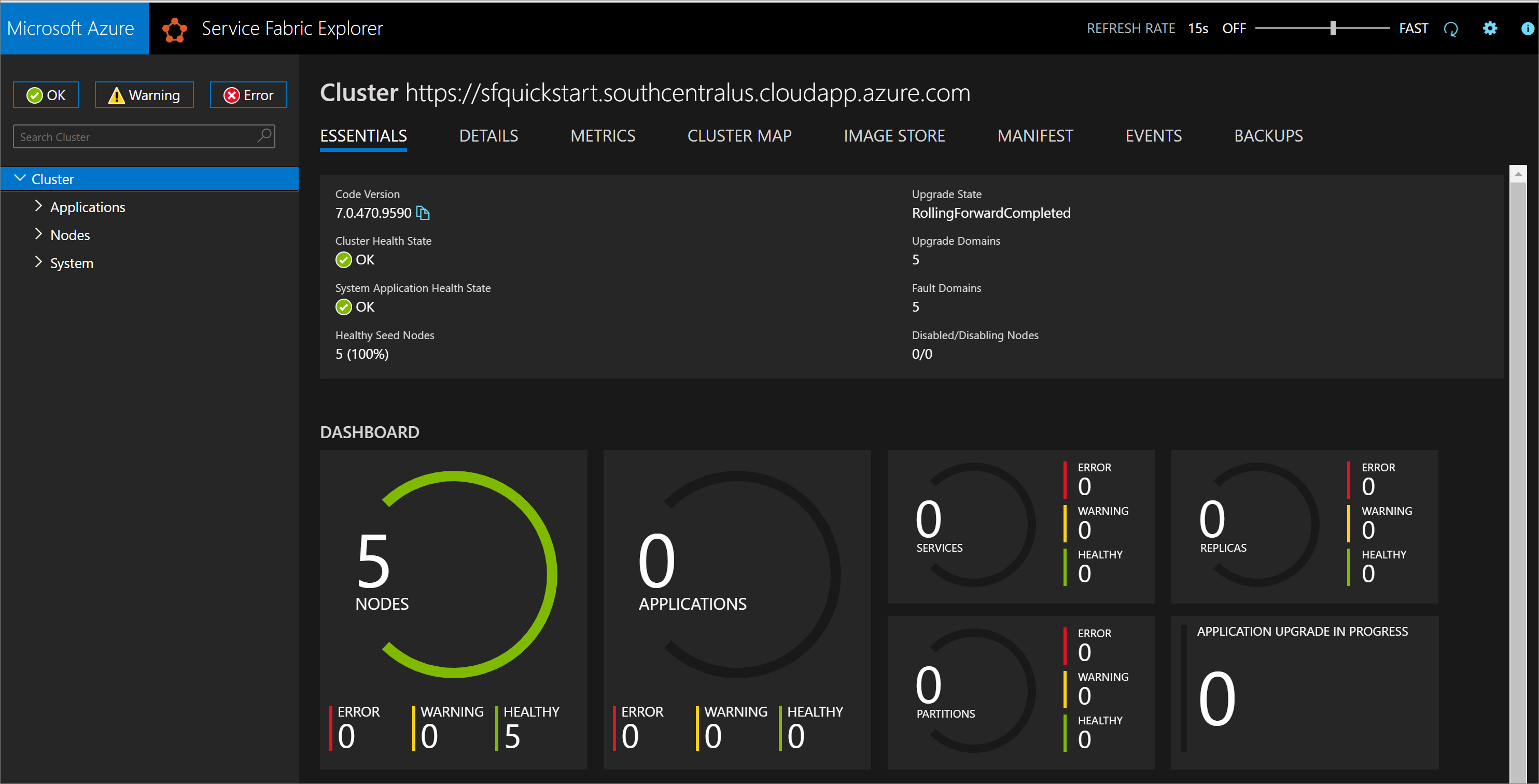
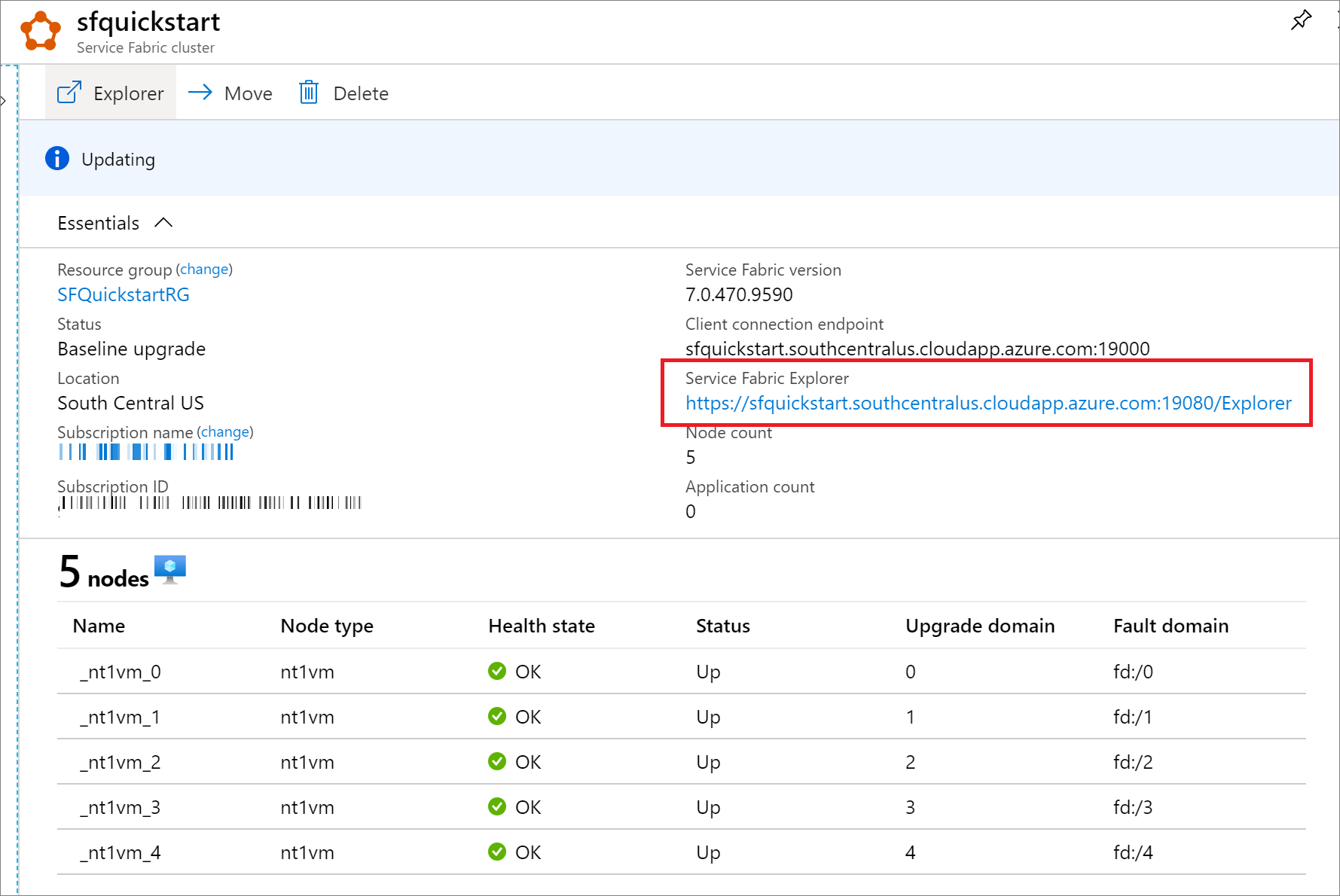
在 Azure 门户中,还可以通过 Service Fabric 资源边栏选项卡找到 Service Fabric Explorer 终结点。
清理资源
如果不再需要资源组及其资源,请使用 Azure 门户、Azure CLI 或 Azure PowerShell 将其删除。
az group delete --name exampleRG
接下来,从本地存储中删除群集证书。 列出已安装的证书以查找群集的指纹:
Get-ChildItem Cert:\CurrentUser\My\
然后删除证书:
Get-ChildItem Cert:\CurrentUser\My\{THUMBPRINT} | Remove-Item
后续步骤
若要了解如何通过 Visual Studio Code 创建 Bicep 文件,请参阅: