Azure 文件存储提供两种主要类型的终结点用于访问 Azure 文件共享:
- 公共终结点:使用公共 IP 地址,可从全球任意位置访问。
- 专用终结点存在于某个虚拟网络中,拥有该虚拟网络地址空间内的一个专用 IP 地址。
公共和专用终结点位于 Azure 存储帐户中。 存储帐户是代表共享存储池的管理结构,你可以在其中部署多个文件共享以及其他存储资源(例如,Blob 容器或队列)。
本文重点介绍如何配置存储帐户的终结点,以便直接访问 Azure 文件共享。 本文的大部分内容也适用于 Azure 文件同步如何与存储帐户的公共和专用终结点互操作。 若要详细了解 Azure 文件同步的网络注意事项,请参阅配置 Azure 文件同步代理和防火墙设置。
在阅读本指南之前,建议先阅读 Azure 文件存储的网络注意事项。
先决条件
- 本文假设你已经创建了一个 Azure 订阅。 如果还没有订阅,请在开始前创建一个试用帐户。
- 本文假设你已经在要从本地连接到的存储帐户中创建了一个 Azure 文件共享。 若要了解如何创建 Azure 文件共享,请参阅创建 Azure 文件共享。
- 如果你打算使用 Azure PowerShell,请安装最新版本。
- 如果你打算使用 Azure CLI,请安装最新版本。
终结点配置
可以配置终结点,以限制对存储帐户的网络访问。 可通过两种方法来仅限虚拟网络访问存储帐户:
创建专用终结点
为存储帐户创建专用终结点时,会部署以下 Azure 资源:
-
一个专用终结点:表示存储帐户专用终结点的 Azure 资源。 可将此资源视为连接存储帐户和网络接口的资源。
-
一个网络接口 (NIC) :在指定的虚拟网络/子网中保留专用 IP 地址的网络接口。 这是完全相同的资源,在部署虚拟机 (VM) 时会使用相同的资源。但是,该资源不是分配给 VM 的,而是由专用终结点拥有。
-
专用域名系统 DNS 区域:如果你以前没有为此虚拟网络部署过专用终结点,系统将为虚拟网络部署新的专用 DNS 区域。 此外,将为此 DNS 区域中的存储帐户创建 DNS A 记录。 如果已在此虚拟网络中部署了专用终结点,则会将存储帐户的新 A 记录添加到现有 DNS 区域。 部署 DNS 区域是可选操作。 不过,强烈建议执行此操作;如果使用 AD 服务主体或 FileREST API 装载 Azure 文件共享,则必须执行此操作。
请导航到要为其创建私有终结点的存储帐户。 在服务菜单的“安全性 + 网络”下,依次选择“网络”、“专用终结点连接”,然后选择“+ 专用终结点”创建新的专用终结点。
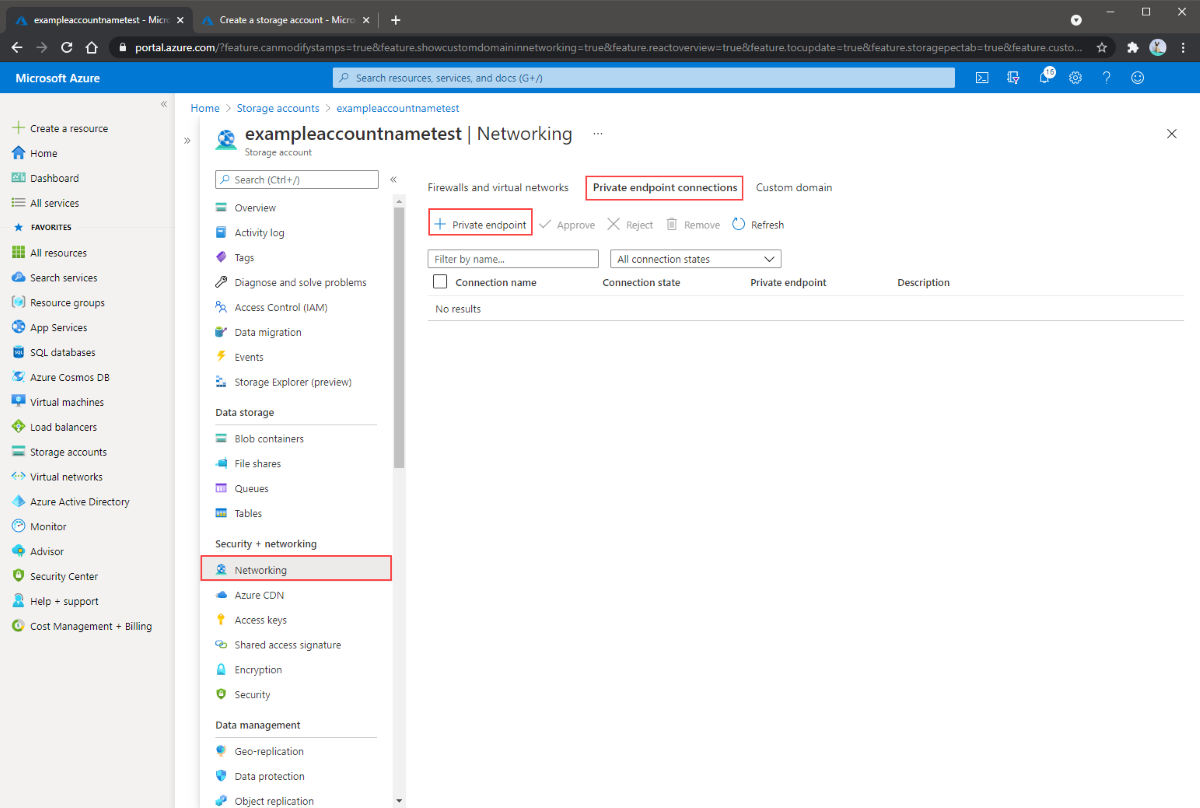
生成的向导包含多个需要完成的页。
在“基本信息”面板中,为专用终端选择所需的订阅、资源组、名称和区域。 资源组、名称和区域可以随意配置,不需要与存储帐户匹配,但必须在与您希望创建专用终结点的虚拟网络相同的区域中创建该专用终结点。 然后选择“下一步: 资源”。
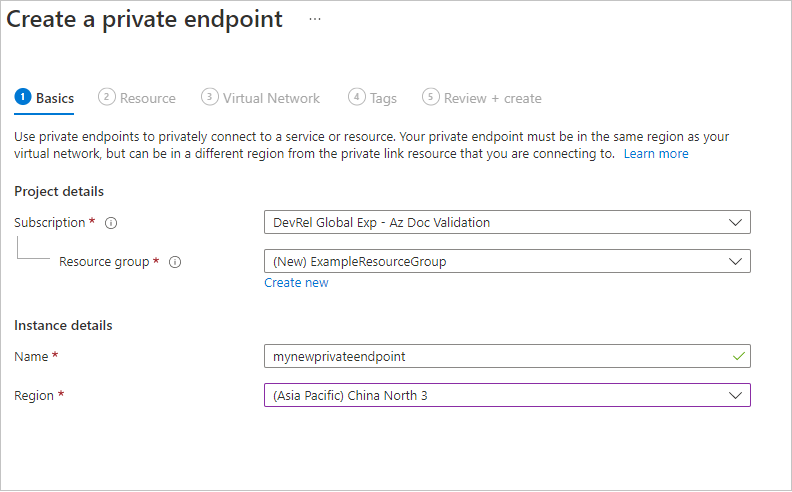
在“资源”边栏中,为目标子资源选择“文件”。 然后选择“下一步: 虚拟网络”。
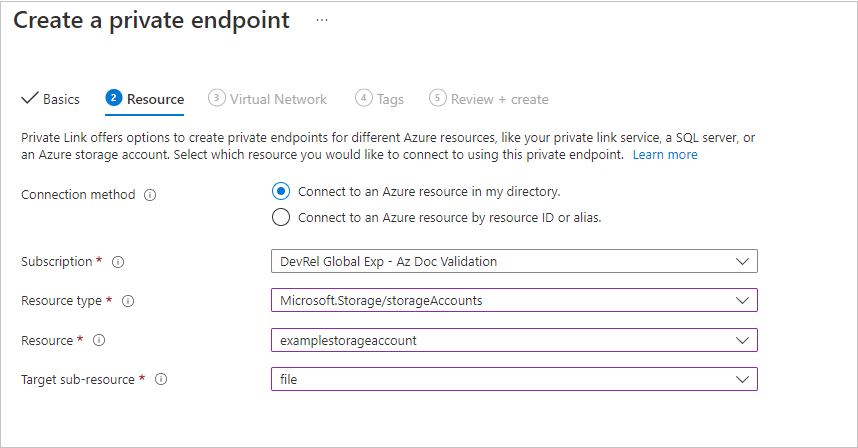
在“虚拟网络”边栏中,可以选择要向其添加专用终结点的特定虚拟网络和子网。 为新的专用终结点选择动态或静态 IP 地址分配。 如果选择静态,则还需要提供名称和专用 IP 地址。 DNS 部分包含用于将专用终结点与专用 DNS 区域集成的信息。 确保订阅和资源组正确,然后选择“下一步: 标记”。
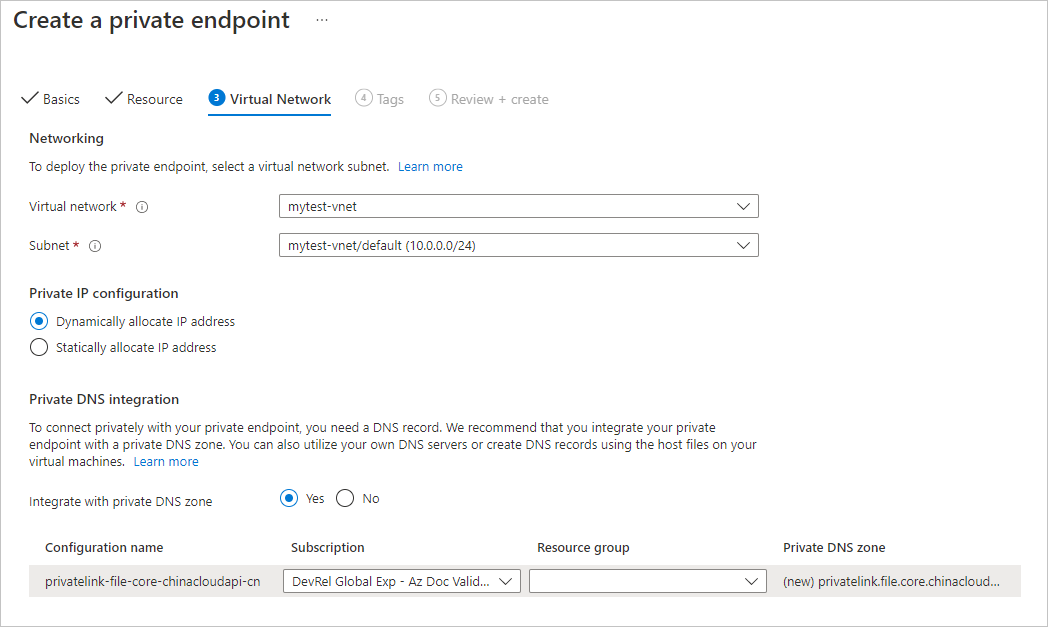
可以选择性地应用标记来对资源进行分类,如将名称“环境”和值“测试”应用于所有测试资源。 输入名称/值对(如果需要),然后选择“下一步: 查看 + 创建”。
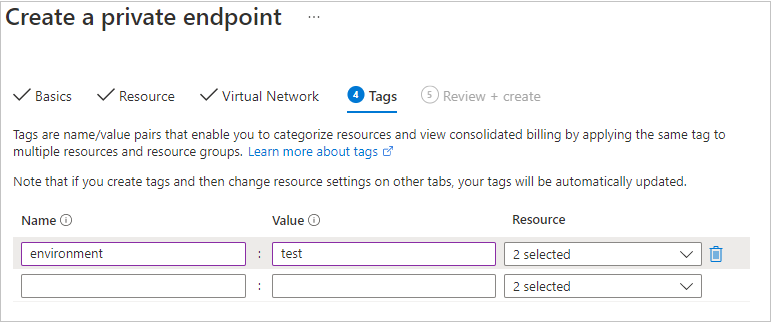
选择“查看 + 创建”以创建专用终结点。
若要为存储帐户创建专用终结点,首先需要获取对存储帐户的引用,以及要将专用终结点添加到的虚拟网络子网的引用。 请替换下面的 <storage-account-resource-group-name>、<storage-account-name>、<vnet-resource-group-name>、<vnet-name> 和 <vnet-subnet-name>:
$storageAccountResourceGroupName = "<storage-account-resource-group-name>"
$storageAccountName = "<storage-account-name>"
$virtualNetworkResourceGroupName = "<vnet-resource-group-name>"
$virtualNetworkName = "<vnet-name>"
$subnetName = "<vnet-subnet-name>"
# Get storage account reference, and throw error if it doesn't exist
$storageAccount = Get-AzStorageAccount `
-ResourceGroupName $storageAccountResourceGroupName `
-Name $storageAccountName `
-ErrorAction SilentlyContinue
if ($null -eq $storageAccount) {
$errorMessage = "Storage account $storageAccountName not found "
$errorMessage += "in resource group $storageAccountResourceGroupName."
Write-Error -Message $errorMessage -ErrorAction Stop
}
# Get virtual network reference, and throw error if it doesn't exist
$virtualNetwork = Get-AzVirtualNetwork `
-ResourceGroupName $virtualNetworkResourceGroupName `
-Name $virtualNetworkName `
-ErrorAction SilentlyContinue
if ($null -eq $virtualNetwork) {
$errorMessage = "Virtual network $virtualNetworkName not found "
$errorMessage += "in resource group $virtualNetworkResourceGroupName."
Write-Error -Message $errorMessage -ErrorAction Stop
}
# Get reference to virtual network subnet, and throw error if it doesn't exist
$subnet = $virtualNetwork | `
Select-Object -ExpandProperty Subnets | `
Where-Object { $_.Name -eq $subnetName }
if ($null -eq $subnet) {
Write-Error `
-Message "Subnet $subnetName not found in virtual network $virtualNetworkName." `
-ErrorAction Stop
}
若要创建专用终结点,必须与存储帐户建立专用链接服务连接。 专用链接服务连接是创建专用终结点时使用的输入。
# Disable private endpoint network policies
$subnet.PrivateEndpointNetworkPolicies = "Disabled"
$virtualNetwork = $virtualNetwork | `
Set-AzVirtualNetwork -ErrorAction Stop
# Create a private link service connection to the storage account.
$privateEndpointConnection = New-AzPrivateLinkServiceConnection `
-Name "$storageAccountName-Connection" `
-PrivateLinkServiceId $storageAccount.Id `
-GroupId "file" `
-ErrorAction Stop
# Create a new private endpoint.
$privateEndpoint = New-AzPrivateEndpoint `
-ResourceGroupName $storageAccountResourceGroupName `
-Name "$storageAccountName-PrivateEndpoint" `
-Location $virtualNetwork.Location `
-Subnet $subnet `
-PrivateLinkServiceConnection $privateEndpointConnection `
-ErrorAction Stop
创建 Azure 专用 DNS 区域可将存储帐户的原始名称(例如 storageaccount.file.core.chinacloudapi.cn)解析为虚拟网络内部的专用 IP。 尽管从创建专用终结点的角度来看,此操作是可选的,但如果直接使用 AD 用户主体装载或通过 REST API 访问 Azure 文件共享,则此操作肯定是必需的。
# Get the desired storage account suffix (core.chinacloudapi.cn for Azure China cloud).
# This is done like this so this script will seamlessly work for non-public Azure.
$storageAccountSuffix = Get-AzContext | `
Select-Object -ExpandProperty Environment | `
Select-Object -ExpandProperty StorageEndpointSuffix
# For Azure China cloud, this will generate the following DNS suffix:
# privatelink.file.core.chinacloudapi.cn.
$dnsZoneName = "privatelink.file.$storageAccountSuffix"
# Find a DNS zone matching desired name attached to this virtual network.
$dnsZone = Get-AzPrivateDnsZone | `
Where-Object { $_.Name -eq $dnsZoneName } | `
Where-Object {
$privateDnsLink = Get-AzPrivateDnsVirtualNetworkLink `
-ResourceGroupName $_.ResourceGroupName `
-ZoneName $_.Name `
-ErrorAction SilentlyContinue
$privateDnsLink.VirtualNetworkId -eq $virtualNetwork.Id
}
if ($null -eq $dnsZone) {
# No matching DNS zone attached to virtual network, so create new one.
$dnsZone = New-AzPrivateDnsZone `
-ResourceGroupName $virtualNetworkResourceGroupName `
-Name $dnsZoneName `
-ErrorAction Stop
$privateDnsLink = New-AzPrivateDnsVirtualNetworkLink `
-ResourceGroupName $virtualNetworkResourceGroupName `
-ZoneName $dnsZoneName `
-Name "$virtualNetworkName-DnsLink" `
-VirtualNetworkId $virtualNetwork.Id `
-ErrorAction Stop
}
获取对专用 DNS 区域的引用后,接下来必须创建存储帐户的 A 记录。
$privateEndpointIP = $privateEndpoint | `
Select-Object -ExpandProperty NetworkInterfaces | `
Select-Object @{
Name = "NetworkInterfaces";
Expression = { Get-AzNetworkInterface -ResourceId $_.Id }
} | `
Select-Object -ExpandProperty NetworkInterfaces | `
Select-Object -ExpandProperty IpConfigurations | `
Select-Object -ExpandProperty PrivateIpAddress
$privateDnsRecordConfig = New-AzPrivateDnsRecordConfig `
-IPv4Address $privateEndpointIP
New-AzPrivateDnsRecordSet `
-ResourceGroupName $virtualNetworkResourceGroupName `
-Name $storageAccountName `
-RecordType A `
-ZoneName $dnsZoneName `
-Ttl 600 `
-PrivateDnsRecords $privateDnsRecordConfig `
-ErrorAction Stop | `
Out-Null
若要为存储帐户创建专用终结点,首先需要获取对存储帐户的引用,以及要将专用终结点添加到的虚拟网络子网的引用。 请替换下面的 <storage-account-resource-group-name>、<storage-account-name>、<vnet-resource-group-name>、<vnet-name> 和 <vnet-subnet-name>:
storageAccountResourceGroupName="<storage-account-resource-group-name>"
storageAccountName="<storage-account-name>"
virtualNetworkResourceGroupName="<vnet-resource-group-name>"
virtualNetworkName="<vnet-name>"
subnetName="<vnet-subnet-name>"
# Get storage account ID
storageAccount=$(az storage account show \
--resource-group $storageAccountResourceGroupName \
--name $storageAccountName \
--query "id" | \
tr -d '"')
# Get virtual network ID
virtualNetwork=$(az network vnet show \
--resource-group $virtualNetworkResourceGroupName \
--name $virtualNetworkName \
--query "id" | \
tr -d '"')
# Get subnet ID
subnet=$(az network vnet subnet show \
--resource-group $virtualNetworkResourceGroupName \
--vnet-name $virtualNetworkName \
--name $subnetName \
--query "id" | \
tr -d '"')
若要创建专用终结点,首先必须确保子网的专用终结点网络策略设置为“已禁用”。 然后,可以使用 az network private-endpoint create 命令创建专用终结点。
# Disable private endpoint network policies
az network vnet subnet update \
--ids $subnet \
--disable-private-endpoint-network-policies \
--output none
# Get virtual network location
region=$(az network vnet show \
--ids $virtualNetwork \
--query "location" | \
tr -d '"')
# Create a private endpoint
privateEndpoint=$(az network private-endpoint create \
--resource-group $storageAccountResourceGroupName \
--name "$storageAccountName-PrivateEndpoint" \
--location $region \
--subnet $subnet \
--private-connection-resource-id $storageAccount \
--group-id "file" \
--connection-name "$storageAccountName-Connection" \
--query "id" | \
tr -d '"')
创建 Azure 专用 DNS 区域可将存储帐户的原始名称(例如 storageaccount.file.core.chinacloudapi.cn)解析为虚拟网络内部的专用 IP。 尽管从创建专用终结点的角度来看,此操作是可选的,但如果使用 AD 用户主体装载或通过 REST API 访问 Azure 文件共享,则此操作肯定是必需的。
# Get the desired storage account suffix (core.chinacloudapi.cn for Azure China cloud).
# This is done like this so this script will seamlessly work for non-public Azure.
storageAccountSuffix=$(az cloud show \
--query "suffixes.storageEndpoint" | \
tr -d '"')
# For Azure China cloud, this will generate the following DNS suffix:
# privatelink.file.core.chinacloudapi.cn.
dnsZoneName="privatelink.file.$storageAccountSuffix"
# Find a DNS zone matching desired name attached to this virtual network.
possibleDnsZones=""
possibleDnsZones=$(az network private-dns zone list \
--query "[?name == '$dnsZoneName'].id" \
--output tsv)
dnsZone=""
possibleDnsZone=""
for possibleDnsZone in $possibleDnsZones
do
possibleResourceGroupName=$(az resource show \
--ids $possibleDnsZone \
--query "resourceGroup" | \
tr -d '"')
link=$(az network private-dns link vnet list \
--resource-group $possibleResourceGroupName \
--zone-name $dnsZoneName \
--query "[?virtualNetwork.id == '$virtualNetwork'].id" \
--output tsv)
if [ -z $link ]
then
echo "1" > /dev/null
else
dnsZoneResourceGroup=$possibleResourceGroupName
dnsZone=$possibleDnsZone
break
fi
done
if [ -z $dnsZone ]
then
# No matching DNS zone attached to virtual network, so create a new one
dnsZone=$(az network private-dns zone create \
--resource-group $virtualNetworkResourceGroupName \
--name $dnsZoneName \
--query "id" | \
tr -d '"')
az network private-dns link vnet create \
--resource-group $virtualNetworkResourceGroupName \
--zone-name $dnsZoneName \
--name "$virtualNetworkName-DnsLink" \
--virtual-network $virtualNetwork \
--registration-enabled false \
--output none
dnsZoneResourceGroup=$virtualNetworkResourceGroupName
fi
获取对专用 DNS 区域的引用后,接下来必须创建存储帐户的 A 记录。
privateEndpointNIC=$(az network private-endpoint show \
--ids $privateEndpoint \
--query "networkInterfaces[0].id" | \
tr -d '"')
privateEndpointIP=$(az network nic show \
--ids $privateEndpointNIC \
--query "ipConfigurations[0].privateIPAddress" | \
tr -d '"')
az network private-dns record-set a create \
--resource-group $dnsZoneResourceGroup \
--zone-name $dnsZoneName \
--name $storageAccountName \
--output none
az network private-dns record-set a add-record \
--resource-group $dnsZoneResourceGroup \
--zone-name $dnsZoneName \
--record-set-name $storageAccountName \
--ipv4-address $privateEndpointIP \
--output none
验证连接性
如果您在虚拟网络中有一台 VM,或者按配置 Azure 文件存储的 DNS 转发中所述配置了 DNS 转发,那么您可以测试私有终结点是否设置正确。 从 PowerShell、命令行或终端运行以下命令(适用于 Windows、Linux 或 macOS)。 必须将 <storage-account-name> 替换为相应的存储帐户名称:
nslookup <storage-account-name>.file.core.chinacloudapi.cn
如果成功,应会看到以下输出,其中 192.168.0.5 是虚拟网络中专用终结点的专用 IP 地址(Windows 中显示的输出):
Server: UnKnown
Address: 10.2.4.4
Non-authoritative answer:
Name: storageaccount.privatelink.file.core.chinacloudapi.cn
Address: 192.168.0.5
Aliases: storageaccount.file.core.chinacloudapi.cn
如果你的虚拟网络中拥有一个 VM,或者已按配置 Azure 文件存储的 DNS 转发所述配置了 DNS 转发,你可以通过运行以下命令来测试专用终结点是否已正确设置:
$storageAccountHostName = [System.Uri]::new($storageAccount.PrimaryEndpoints.file) | `
Select-Object -ExpandProperty Host
Resolve-DnsName -Name $storageAccountHostName
如果成功,应会看到以下输出,其中 192.168.0.5 是虚拟网络中专用终结点的专用 IP 地址:
Name Type TTL Section NameHost
---- ---- --- ------- --------
storageaccount.file.core.chinacloudapi.cn CNAME 60 Answer storageaccount.privatelink.file.core.chinacloudapi.cn
Name : storageaccount.privatelink.file.core.chinacloudapi.cn
QueryType : A
TTL : 600
Section : Answer
IP4Address : 192.168.0.5
如果你在虚拟网络中有一个 VM,或者已按配置 Azure 文件存储的 DNS 转发所述配置了 DNS 转发,你可通过运行以下命令来测试是否已正确设置专用终结点:
httpEndpoint=$(az storage account show \
--resource-group $storageAccountResourceGroupName \
--name $storageAccountName \
--query "primaryEndpoints.file" | \
tr -d '"')
hostName=$(echo $httpEndpoint | cut -c7-$(expr length $httpEndpoint) | tr -d "/")
nslookup $hostName
如果一切成功进行,应会看到以下输出,其中 192.168.0.5 是虚拟网络中专用终结点的专用 IP 地址。 仍应使用 storageaccount.file.core.chinacloudapi.cn 来装载文件共享,而不是 privatelink 路径。
Server: 127.0.0.53
Address: 127.0.0.53#53
Non-authoritative answer:
storageaccount.file.core.chinacloudapi.cn canonical name = storageaccount.privatelink.file.core.chinacloudapi.cn.
Name: storageaccount.privatelink.file.core.chinacloudapi.cn
Address: 192.168.0.5
限制公共终结点访问
若要限制公共终结点访问,首先需要禁用对公共终结点的一般访问。 禁用对公共终结点的访问不会影响专用终结点。 禁用公共终结点后,可选择可继续访问它的特定网络或 IP 地址。 通常,大多数针对存储帐户的防火墙策略仅限一个或多个虚拟网络进行网络访问。
禁止对公共终结点的访问
禁止对公共终结点的访问时,仍可通过存储帐户的专用终结点来访问该存储帐户。 否则,对存储帐户的公共终结点发出的有效请求将被拒绝,除非这些请求来自特别指定的源。
导航到您要限制所有对公共终结点访问的存储帐户。 在该存储帐户的目录中,选择“网络”。
在页面顶部,选择“从选定的虚拟网络和 IP 地址启用”单选按钮。 这将取消隐藏一些用于控制公共端点限制的设置。 选择“允许受信任服务列表上的 Azure 服务访问此存储帐户”,以允许受信任的第一方 Microsoft 服务(例如 Azure 文件同步)访问存储帐户。
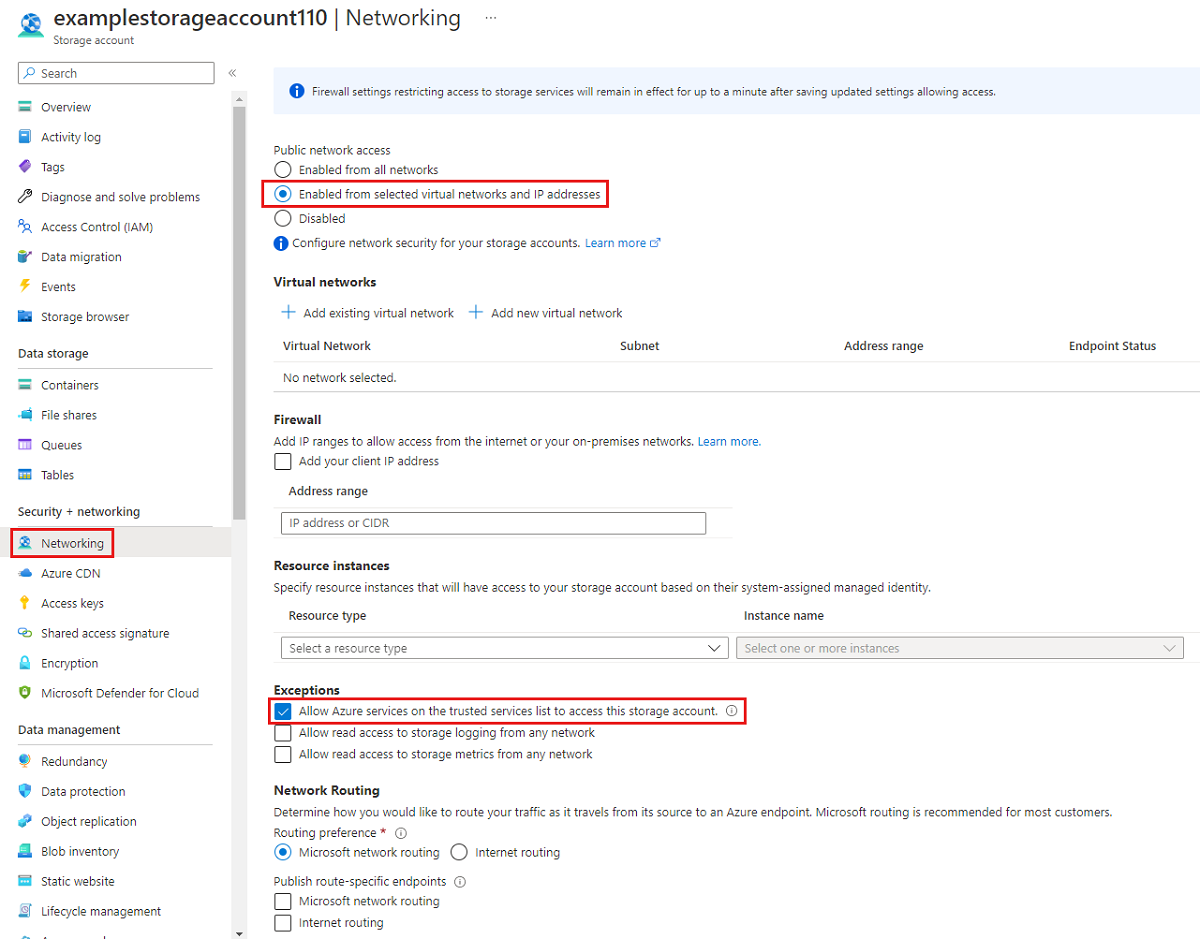
以下 PowerShell 命令将拒绝发往存储帐户公共终结点的所有流量。 请注意,此命令的 -Bypass 参数设置为 AzureServices。 这会允许受信任的第一方服务(例如 Azure 文件同步)通过公共终结点访问存储帐户。
# This assumes $storageAccount is still defined from the beginning of this of this guide.
$storageAccount | Update-AzStorageAccountNetworkRuleSet `
-DefaultAction Deny `
-Bypass AzureServices `
-WarningAction SilentlyContinue `
-ErrorAction Stop | `
Out-Null
以下 CLI 命令将拒绝发往存储帐户公共终结点的所有流量。 请注意,此命令的 -bypass 参数设置为 AzureServices。 这会允许受信任的第一方服务(例如 Azure 文件同步)通过公共终结点访问存储帐户。
# This assumes $storageAccountResourceGroupName and $storageAccountName
# are still defined from the beginning of this guide.
az storage account update \
--resource-group $storageAccountResourceGroupName \
--name $storageAccountName \
--bypass "AzureServices" \
--default-action "Deny" \
--output none
将公共终结点的访问限制为仅特定虚拟网络可以访问
如果仅限从特定的虚拟网络访问存储帐户,则会允许从指定的虚拟网络内部对公共终结点发出请求。 为此,可以使用称作“服务终结点”的虚拟网络功能。 在具有或没有专用终结点的情况下都可以使用此功能。
导航到想要将公共终结点访问限制为特定虚拟网络的存储帐户。 在该存储帐户的目录中,选择“网络”。
在页面顶部,选择“从选定的虚拟网络和 IP 地址启用”单选按钮。 随后会显示一些用于控制公共终结点限制的设置。 选择“+添加现有虚拟网络”,以选择应允许其通过公共终结点访问存储帐户的特定虚拟网络。 选择虚拟网络并为该虚拟网络选择子网,然后选择“启用”。
选择“允许受信任服务列表上的 Azure 服务访问此存储帐户”,以允许受信任的第一方 Microsoft 服务(例如 Azure 文件同步)访问存储帐户。
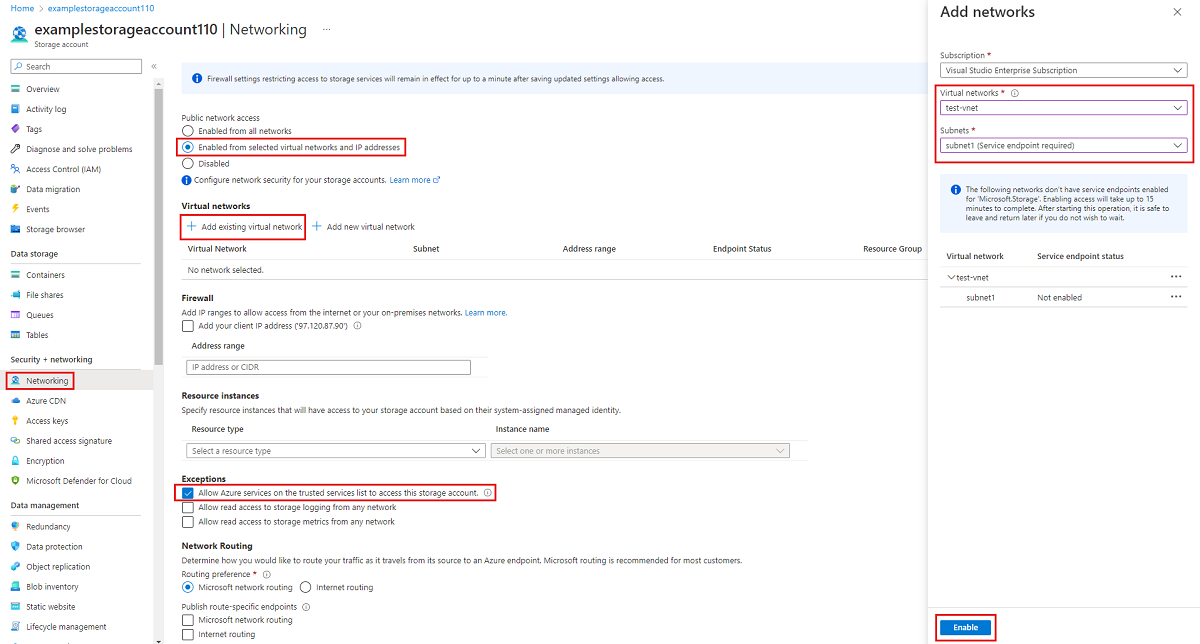
若要仅限特定的虚拟网络使用服务终结点访问存储帐户的公共终结点,首先需要收集有关该存储帐户和虚拟网络的信息。 填写 <storage-account-resource-group>、<storage-account-name>、<vnet-resource-group-name>、<vnet-name> 和 <subnet-name> 以收集此信息。
$storageAccountResourceGroupName = "<storage-account-resource-group>"
$storageAccountName = "<storage-account-name>"
$restrictToVirtualNetworkResourceGroupName = "<vnet-resource-group-name>"
$restrictToVirtualNetworkName = "<vnet-name>"
$subnetName = "<subnet-name>"
$storageAccount = Get-AzStorageAccount `
-ResourceGroupName $storageAccountResourceGroupName `
-Name $storageAccountName `
-ErrorAction Stop
$virtualNetwork = Get-AzVirtualNetwork `
-ResourceGroupName $restrictToVirtualNetworkResourceGroupName `
-Name $restrictToVirtualNetworkName `
-ErrorAction Stop
$subnet = $virtualNetwork | `
Select-Object -ExpandProperty Subnets | `
Where-Object { $_.Name -eq $subnetName }
if ($null -eq $subnet) {
Write-Error `
-Message "Subnet $subnetName not found in virtual network $restrictToVirtualNetworkName." `
-ErrorAction Stop
}
要使 Azure 网络结构允许来自该虚拟网络的流量进入存储帐户公共终结点,该虚拟网络的子网必须公开 Microsoft.Storage 服务终结点。 以下 PowerShell 命令将 Microsoft.Storage 服务终结点添加到子网(如果其中不存在该服务终结点)。
$serviceEndpoints = $subnet | `
Select-Object -ExpandProperty ServiceEndpoints | `
Select-Object -ExpandProperty Service
if ($serviceEndpoints -notcontains "Microsoft.Storage") {
if ($null -eq $serviceEndpoints) {
$serviceEndpoints = @("Microsoft.Storage")
} elseif ($serviceEndpoints -is [string]) {
$serviceEndpoints = @($serviceEndpoints, "Microsoft.Storage")
} else {
$serviceEndpoints += "Microsoft.Storage"
}
$virtualNetwork = $virtualNetwork | Set-AzVirtualNetworkSubnetConfig `
-Name $subnetName `
-AddressPrefix $subnet.AddressPrefix `
-ServiceEndpoint $serviceEndpoints `
-WarningAction SilentlyContinue `
-ErrorAction Stop | `
Set-AzVirtualNetwork `
-ErrorAction Stop
}
限制发往存储帐户的流量的最后一步是创建网络规则并将其添加到存储帐户的网络规则集。
$networkRule = $storageAccount | Add-AzStorageAccountNetworkRule `
-VirtualNetworkResourceId $subnet.Id `
-ErrorAction Stop
$storageAccount | Update-AzStorageAccountNetworkRuleSet `
-DefaultAction Deny `
-Bypass AzureServices `
-VirtualNetworkRule $networkRule `
-WarningAction SilentlyContinue `
-ErrorAction Stop | `
Out-Null
若要仅限特定的虚拟网络使用服务终结点访问存储帐户的公共终结点,首先需要收集有关该存储帐户和虚拟网络的信息。 填写 <storage-account-resource-group>、<storage-account-name>、<vnet-resource-group-name>、<vnet-name> 和 <subnet-name> 以收集此信息。
storageAccountResourceGroupName="<storage-account-resource-group>"
storageAccountName="<storage-account-name>"
restrictToVirtualNetworkResourceGroupName="<vnet-resource-group-name>"
restrictToVirtualNetworkName="<vnet-name>"
subnetName="<subnet-name>"
storageAccount=$(az storage account show \
--resource-group $storageAccountResourceGroupName \
--name $storageAccountName \
--query "id" | \
tr -d '"')
virtualNetwork=$(az network vnet show \
--resource-group $restrictToVirtualNetworkResourceGroupName \
--name $restrictToVirtualNetworkName \
--query "id" | \
tr -d '"')
subnet=$(az network vnet subnet show \
--resource-group $restrictToVirtualNetworkResourceGroupName \
--vnet-name $restrictToVirtualNetworkName \
--name $subnetName \
--query "id" | \
tr -d '"')
要使 Azure 网络结构允许来自该虚拟网络的流量进入存储帐户公共终结点,该虚拟网络的子网必须公开 Microsoft.Storage 服务终结点。 以下 CLI 命令将 Microsoft.Storage 服务终结点添加到子网(如果其中不存在该服务终结点)。
serviceEndpoints=$(az network vnet subnet show \
--resource-group $restrictToVirtualNetworkResourceGroupName \
--vnet-name $restrictToVirtualNetworkName \
--name $subnetName \
--query "serviceEndpoints[].service" \
--output tsv)
foundStorageServiceEndpoint=false
for serviceEndpoint in $serviceEndpoints
do
if [ $serviceEndpoint = "Microsoft.Storage" ]
then
foundStorageServiceEndpoint=true
fi
done
if [ $foundStorageServiceEndpoint = false ]
then
serviceEndpointList=""
for serviceEndpoint in $serviceEndpoints
do
serviceEndpointList+=$serviceEndpoint
serviceEndpointList+=" "
done
serviceEndpointList+="Microsoft.Storage"
az network vnet subnet update \
--ids $subnet \
--service-endpoints $serviceEndpointList \
--output none
fi
限制发往存储帐户的流量的最后一步是创建网络规则并将其添加到存储帐户的网络规则集。
az storage account network-rule add \
--resource-group $storageAccountResourceGroupName \
--account-name $storageAccountName \
--subnet $subnet \
--output none
az storage account update \
--resource-group $storageAccountResourceGroupName \
--name $storageAccountName \
--bypass "AzureServices" \
--default-action "Deny" \
--output none
另请参阅






