适用于:✔️ Linux VM ✔️ Windows VM ✔️
Azure 磁盘存储使你能在对托管磁盘使用服务器端加密 (SSE) 时管理自己的密钥(如果你选择)。 有关使用客户管理的密钥的 SSE 以及其他托管磁盘加密类型的概念信息,请参阅客户管理的密钥这一磁盘加密文章的“客户管理的密钥”部分
先决条件
限制
目前,客户托管密钥具有以下限制:
如果为具有增量快照的磁盘启用了此功能,则不能在该磁盘或其快照上禁用此功能。 要解决此问题,请将所有数据复制到完全不同的、不使用客户管理的密钥的托管磁盘。 可以使用 Azure CLI 或 Azure PowerShell 模块执行此操作。
磁盘及其关联的所有增量快照都必须具有相同的磁盘加密集。
仅支持大小为 2048 位、3,072 位和 4,096 位的软件密钥,不支持其他密钥或其他大小。
仅适用于超级磁盘和高级 SSD v2 磁盘:
- 基于使用服务器端加密和客户管理的密钥加密的快照创建的磁盘必须使用同一磁盘加密集进行加密。
- 使用客户管理的密钥加密的超级磁盘和高级 SSD v2 磁盘不支持用户分配的托管标识。
- 目前不支持使用在其他 Microsoft Entra ID 租户中存储的 Azure 密钥保管库,通过客户管理的密钥加密超级磁盘和高级 SSD v2 磁盘。
与客户管理的密钥相关的大部分资源(磁盘加密集、VM、磁盘和快照)都必须位于同一订阅和区域中。
Azure 密钥保管库可以在不同的订阅中使用,但必须与磁盘加密集位于同一区域中。
使用客户管理的密钥加密的磁盘只能移动到另一个资源组(如果附加到的 VM 已解除分配)。
无法在不同订阅间移动使用客户管理的密钥加密的磁盘、快照和映像。
当前或以前使用 Azure 磁盘加密加密的托管磁盘不能使用客户管理的密钥进行加密。
每个区域、每个订阅最多只能创建 5000 个磁盘加密集。
有关将客户托管密钥与共享映像库结合使用的信息,请参阅预览版:使用客户托管密钥加密映像。
以下部分介绍如何为托管磁盘启用客户管理的密钥以及如何使用这种密钥:
如果你是第一次执行此操作,则为磁盘设置客户管理的密钥时会要求你按特定顺序创建资源。 首先,需要创建并设置 Azure Key Vault。
设置 Azure 密钥保管库
登录到 Azure 门户。
搜索并选择“Key Vault”。
重要
磁盘加密集、VM、磁盘和快照必须都位于同一区域和订阅中才能成功部署。 Azure Key Vault 可以在不同的订阅中使用,但必须与磁盘加密集位于同一区域和租户中。
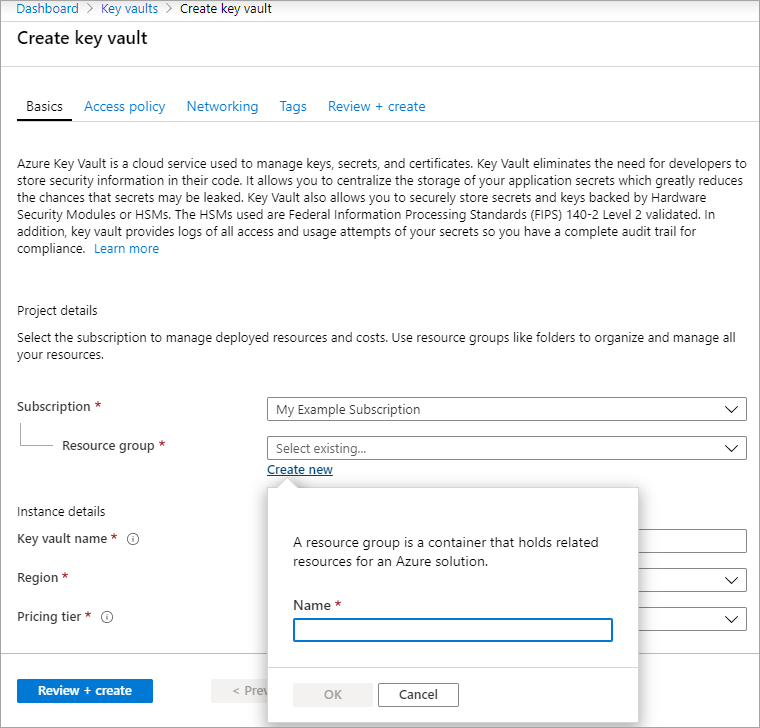
选择“+创建”以创建新的 Key Vault。
创建新的资源组。
输入 Key Vault 名称,选择区域,然后选择定价层。
注意
创建 Key Vault 实例时,必须启用软删除和清除保护。 软删除可确保 Key Vault 在给定的保留期(默认为 90 天)内保留已删除的密钥。 清除保护可确保在保留期结束之前,无法永久删除已删除的密钥。 这些设置可防止由于意外删除而丢失数据。 使用 Key Vault 加密托管磁盘时,这些设置是必需的。
选择“审阅 + 创建”,验证选择,然后选择“创建” 。
Key Vault 部署完成后,请选择它。
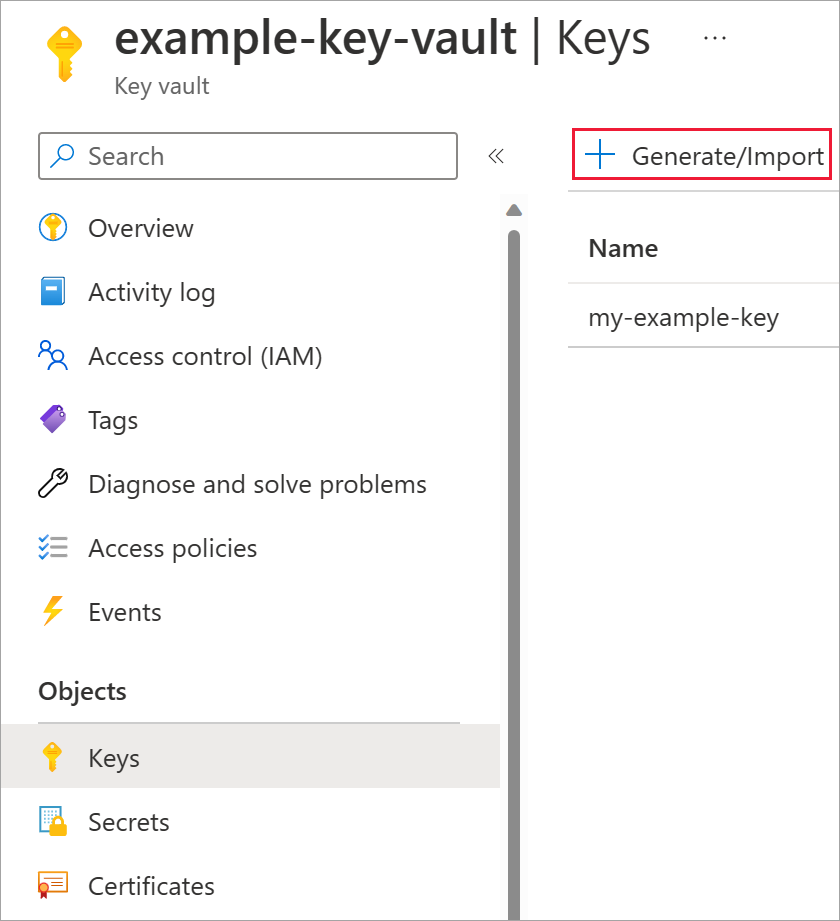
选择“对象”下的“密钥”。
选择“生成/导入”。
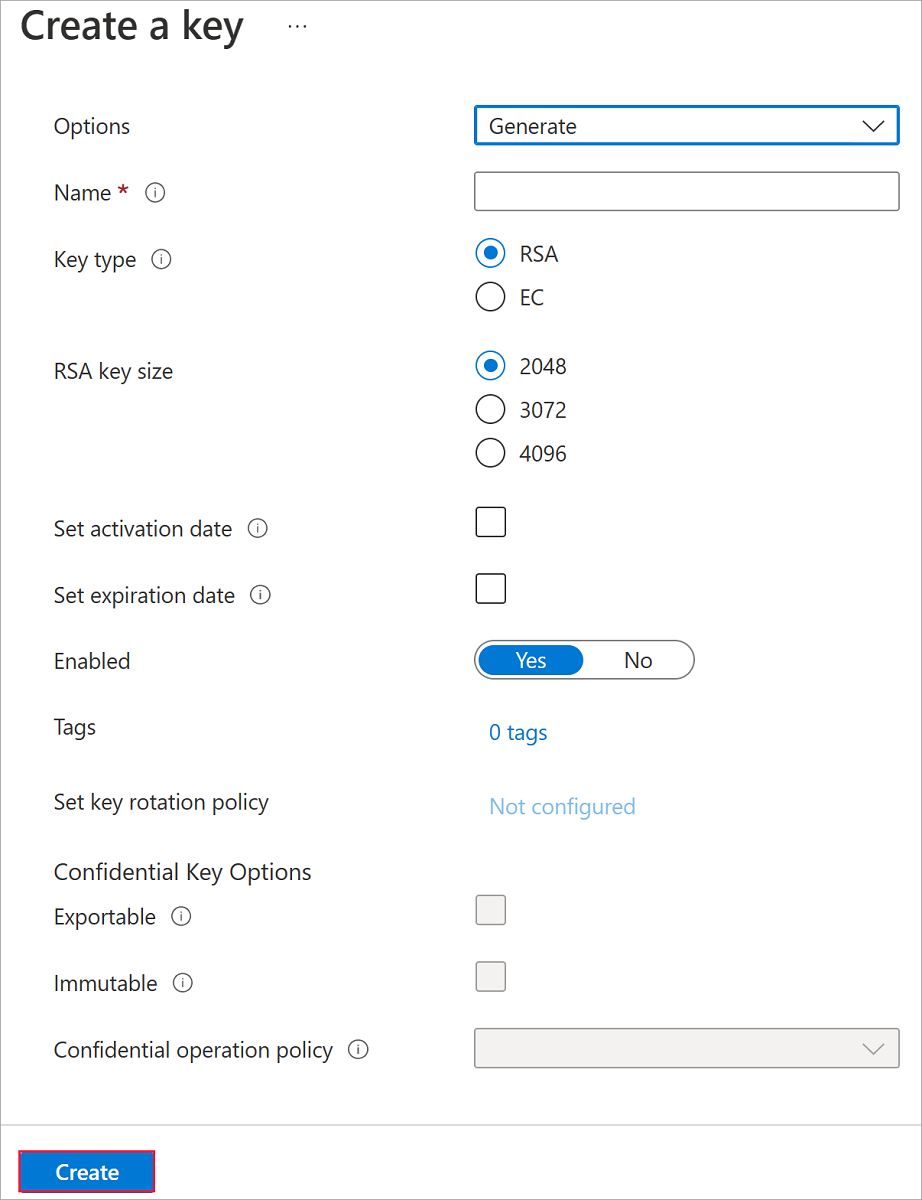
将“密钥类型”设置为“RSA”,将“RSA 密钥大小”设置为“2048” 。
根据需要填写其余选项,然后选择“创建”。
添加 Azure RBAC 角色
你已创建 Azure 密钥保管库和密钥,现在必须添加 Azure RBAC 角色,以便可以将 Azure 密钥保管库用于磁盘加密集。
- 选择“访问控制(IAM)”并添加角色。
- 添加“Key Vault 管理员”、“所有者”或“参与者”角色。
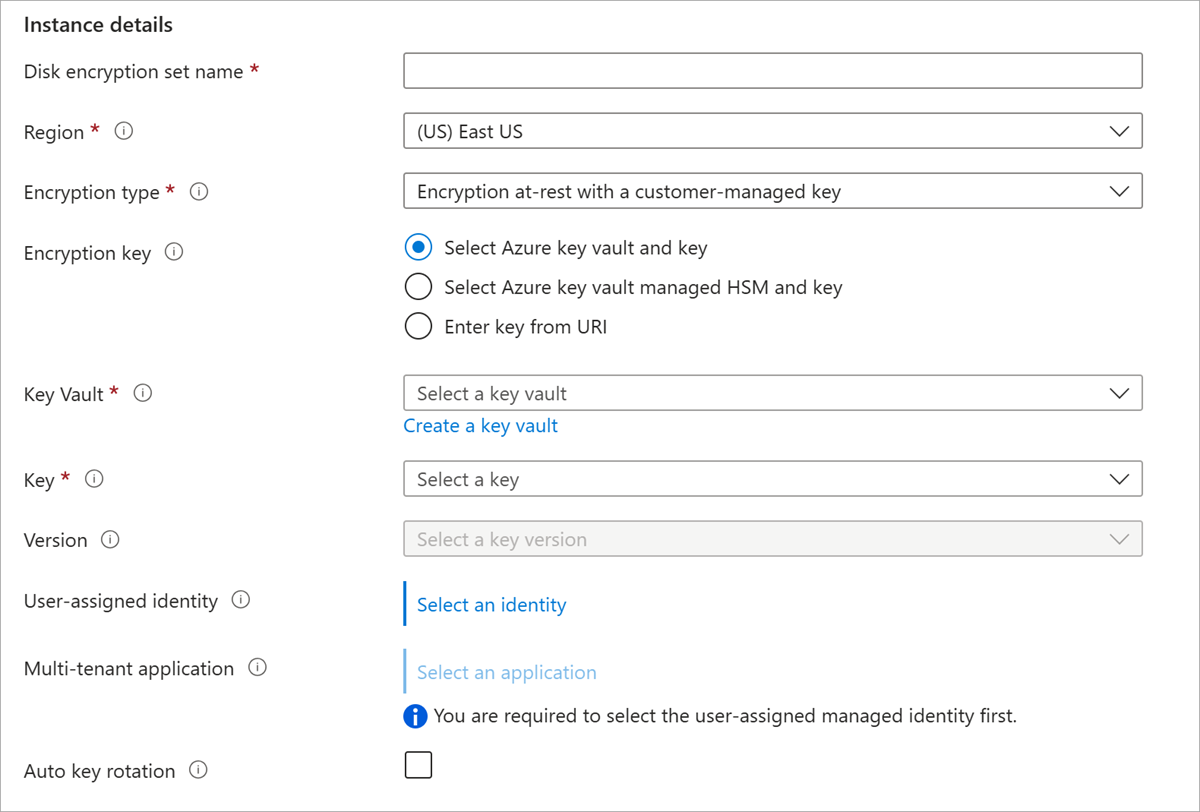
设置磁盘加密集
搜索“磁盘加密集”并选择它。
在“磁盘加密集”窗格中,选择“+ 创建”。
选择资源组,命名加密集,然后选择与 Key Vault 相同的区域。
对于“加密类型”,请选择“使用客户管理的密钥进行静态加密”。
注意
一旦创建了具有特定加密类型的磁盘加密集,就无法对其进行更改。 如果要使用其他加密类型,则必须创建新的磁盘加密集。
确保选择了“选择 Azure 密钥保管库和密钥”。
选择先前创建的密钥保管库和密钥,以及版本。
如果要启用客户管理的密钥的自动轮换,请选择“自动密钥轮换”。
选择“审阅 + 创建”,然后选择“创建” 。
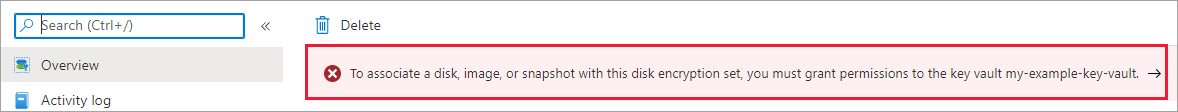
部署磁盘加密集后,导航到该加密集,然后选择显示的警报。
这会向磁盘加密集授予密钥保管库权限。
部署 VM
创建并设置好 Key Vault 和磁盘加密集之后,接下来即可使用加密来部署 VM。 VM 部署过程与标准部署过程类似,唯一的差别在于,你需要将 VM 部署到与其他资源相同的区域中,并选择使用客户托管密钥。
在现有磁盘上启用
注意
在附加到 VM 的任何磁盘上启用磁盘加密都需要你停止 VM。
导航到与磁盘加密集位于同一区域中的 VM。
打开 VM 并选择“停止”。
- VM 停止后,选择“磁盘”,然后选择要加密的磁盘。
依次选择“加密”、“使用客户托管密钥进行静态加密”,然后在下拉列表中选择“磁盘加密集” 。
选择“保存” 。
对于附加到你想要加密的 VM 的任何其他磁盘,请重复此过程。
当磁盘切换到客户管理的密钥后,如果没有其他需要进行加密的附加磁盘,请启动 VM。
重要
客户管理的密钥依赖于 Azure 资源的托管标识,后者是 Microsoft Entra ID 的一项功能。 配置客户托管密钥时,实际上会自动将托管标识分配给你的资源。 如果随后在两个 Microsoft Entra 目录之间移动订阅、资源组或托管磁盘,则与托管磁盘关联的托管标识不会转移到新租户,因此客户管理的密钥可能不再有效。 有关详细信息,请参阅在 Microsoft Entra 目录之间转移订阅。
在现有磁盘加密集上启用自动密钥轮换
导航到要在其上启用自动密钥轮换的磁盘加密集。
在“设置”下,选择“密钥” 。
选择“自动密钥轮换”,然后选择“保存” 。