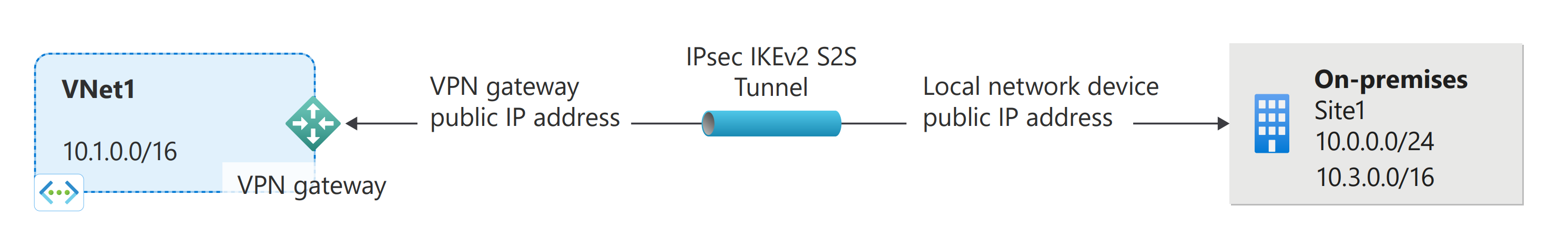
本文介绍如何使用 PowerShell 创建从本地网络到虚拟网络 (VNet) 的站点到站点 VPN 网关连接。
使用站点到站点 VPN 网关连接,通过 IPsec/IKE(IKEv1 或 IKEv2)VPN 隧道将本地网络连接到 Azure 虚拟网络。 此类型的连接要求在本地网络中的 VPN 设备被分配一个面向外部的公共 IP 地址。 本文中的步骤使用共享密钥在 VPN 网关和本地 VPN 设备之间创建连接。 有关 VPN 网关的详细信息,请参阅关于 VPN 网关。
开始之前
在开始配置之前,请验证环境是否符合以下条件:
验证是否具有基于路由的正常运行的 VPN 网关。 要创建 VPN 网关,请参阅创建 VPN 网关。
如果不熟悉本地网络配置中的 IP 地址范围,则需咨询能够提供此类详细信息的人员。 创建此配置时,必须指定 IP 地址范围前缀,Azure 会将该前缀路由到本地位置。 本地网络的任何子网都不得与要连接到的虚拟网络子网重叠。
VPN 设备:
- 确保有一台兼容的 VPN 设备,并且有人能够对其进行配置。 有关兼容的 VPN 设备和设备配置的详细信息,请参阅关于 VPN 设备。
- 确定您的 VPN 设备是否支持双活模式网关。 本文将创建一个主动-主动模式的 VPN 网关,建议将该网关用于高可用性连接。 主动-主动模式指定两个网关 VM 实例都处于活动状态。 此模式需要两个公共 IP 地址,每个网关 VM 实例使用一个。 需要将 VPN 设备配置为连接到每个网关 VM 实例的 IP 地址。
如果 VPN 设备不支持此模式,请不要为网关启用此模式。 有关详细信息,请参阅为跨界连接和 VNet 到 VNet 连接设计高可用性连接和关于主动-主动模式 VPN 网关。
如果虚拟网络网关和本地网关驻留在不同的订阅和不同的租户中,则需要使用略有不同的步骤。 请参阅与不同租户和不同订阅的连接。
Azure PowerShell
可以在计算机本地安装并运行 Azure PowerShell cmdlet。 PowerShell 命令(cmdlet)经常更新。 如果尚未安装最新版本,说明中指定的值可能会失败。 若要查找计算机上安装的 Azure PowerShell 版本,请使用 Get-Module -ListAvailable Az cmdlet。 若要进行安装或更新,请参阅安装 Azure PowerShell 模块。
创建本地网络网关
本地网关 (LNG) 通常是指本地位置。 它与虚拟网络网关不同。 可以为站点提供一个名称供 Azure 引用,并指定本地 VPN 设备的 IP 地址,以便创建一个连接来连接到该设备。 此外还可指定 IP 地址前缀,以便通过 VPN 网关将其路由到 VPN 设备。 指定的地址前缀是位于本地网络的前缀。 如果本地网络出现变化,可以轻松更新这些前缀。
请选择以下示例之一。 示例中使用的值包括:
- GatewayIPAddress 是本地 VPN 设备的 IP 地址,而不是 Azure VPN 网关。
- AddressPrefix 是本地地址空间。
单地址前缀示例
New-AzLocalNetworkGateway -Name Site1 -ResourceGroupName TestRG1 `
-Location 'China North' -GatewayIpAddress '[IP address of your on-premises VPN device]' -AddressPrefix '10.0.0.0/24'
多地址前缀示例
New-AzLocalNetworkGateway -Name Site1 -ResourceGroupName TestRG1 `
-Location 'China North' -GatewayIpAddress '[IP address of your on-premises VPN device]' -AddressPrefix @('10.3.0.0/16','10.0.0.0/24')
配置 VPN 设备
通过站点到站点连接连接到本地网络需要 VPN 设备。 在此步骤中,请配置 VPN 设备。 配置 VPN 设备时,需要以下项:
共享密钥:此共享密钥与创建站点到站点 VPN 连接时指定的密钥相同。 示例将使用简单的共享密钥。 建议生成更复杂的可用密钥。
虚拟网络网关实例的公共 IP 地址:获取每个 VM 实例的 IP 地址。 如果网关处于主动-主动模式,则每个网关 VM 实例都有一个 IP 地址。 请务必为设备配置这两个 IP 地址,每个主动网关 VM 一个。 主动-备用模式网关只有一个 IP 地址。 在该示例中,VNet1GWpip1 是公共 IP 地址资源的名称。
Get-AzPublicIpAddress -Name VNet1GWpip1 -ResourceGroupName TestRG1
根据所用的 VPN 设备,有时可以下载 VPN 设备配置脚本。 有关详细信息,请参阅下载 VPN 设备配置脚本。
以下链接提供了更多配置信息:
有关兼容 VPN 设备的信息,请参阅关于 VPN 设备。
有关设备配置设置的链接,请参阅已验证的 VPN 设备。 我们会尽量提供设备配置链接,但你最好是咨询设备制造商以获取最新的配置信息。
该列表显示了我们已测试过的版本。 即使列表中未显示你的 VPN 设备的 OS 版本,该版本也仍然可能是兼容的。 请咨询设备制造商。
有关 VPN 设备配置的基本信息,请参阅合作伙伴 VPN 设备配置概述。
若要了解如何编辑设备配置示例,请参阅编辑示例。
有关加密要求的信息,请参阅关于加密要求和 Azure VPN 网关。
有关完成配置所需的参数的信息,请参阅默认 IPsec/IKE 参数。 这些信息包括 IKE 版本、Diffie-Hellman (DH) 组、身份验证方法、加密和散列算法、安全关联 (SA) 生存期、完美前向保密 (PFS) 和死对等体检测 (DPD)。
有关 IPsec/IKE 策略配置步骤,请参阅为 S2S VPN 和 VNet 到 VNet 配置自定义 IPsec/IKE 连接策略。
若要连接多个基于策略的 VPN 设备,请参阅将 VPN 网关连接到多个基于策略的本地 VPN 设备。
创建 VPN 连接
在虚拟网关和本地 VPN 设备之间创建站点到站点 VPN 连接。 如果使用主动-主动模式网关(推荐),则每个网关 VM 实例都会拥有单独的 IP 地址。 要正确配置高可用性连接,必须在每个 VM 实例和 VPN 设备之间建立隧道。 这两条隧道都是同一连接的一部分。 如果本地网络网关和虚拟网络网关驻留在不同的订阅和不同的租户中,请参阅 “具有不同租户和不同订阅的连接 ”部分。
共享密钥必须与用于 VPN 设备配置的值匹配。 请注意,站点到站点的“-ConnectionType”为 IPsec。
设置变量。
$gateway1 = Get-AzVirtualNetworkGateway -Name VNet1GW -ResourceGroupName TestRG1 $local = Get-AzLocalNetworkGateway -Name Site1 -ResourceGroupName TestRG1创建连接。
New-AzVirtualNetworkGatewayConnection -Name VNet1toSite1 -ResourceGroupName TestRG1 ` -Location 'China North' -VirtualNetworkGateway1 $gateway1 -LocalNetworkGateway2 $local ` -ConnectionType IPsec -SharedKey 'abc123'
连接不同租户和不同订阅
当虚拟网络网关和本地网络网关驻留在不同的订阅和不同租户中时,需要以不同于上一部分的方式指定连接命令。
对于驻留在租户 2(订阅 2)中的 LocalNetworkGateway,请使用以下命令。 调整任何变量以匹配环境。
Connect-AzAccount -TenantID $Tenant2 -Environment AzureChinaCloud
Select-AzSubscription -SubscriptionId $subscription2
$local = Get-AzLocalNetworkGateway -Name Site1 -ResourceGroupName TestRG1
对于驻留在租户 1(订阅 1)中的 VirtualNetworkGateway,请使用以下命令。 调整任何变量以匹配环境。
Connect-AzAccount -TenantID $Tenant1 -Environment AzureChinaCloud
Select-AzSubscription -SubscriptionId $subscription1
$gateway1 = Get-AzVirtualNetworkGateway -Name VNet1GW -ResourceGroupName TestRG1
New-AzVirtualNetworkGatewayConnection -Name VNet1toSite1 -ResourceGroupName TestRG1 -Location 'China East 2' -VirtualNetworkGateway1 $gateway1 -LocalNetworkGateway2 $local -ConnectionType IPsec -SharedKey 'abc123'
验证 VPN 连接
VPN 连接有几种不同的验证方式。
可以验证连接是否成功,方法是使用“Get-AzVirtualNetworkGatewayConnection”cmdlet,带或不带“-Debug”。
使用以下 cmdlet 示例,配置符合自己需要的值。 如果出现提示,选择“A”以运行“所有”。 在此示例中,“ -Name”是指要测试的连接的名称。
Get-AzVirtualNetworkGatewayConnection -Name VNet1toSite1 -ResourceGroupName TestRG1cmdlet 运行完毕后,查看该值。 在以下示例中,连接状态显示为“已连接”,且可以看到入口和出口字节数。
"connectionStatus": "Connected", "ingressBytesTransferred": 33509044, "egressBytesTransferred": 4142431
修改本地网关的 IP 地址前缀
如果需要路由到本地位置的 IP 地址前缀发生更改,则可修改本地网关。 使用这些示例时,修改这些值以匹配你的环境。
若要添加更多地址前缀,请执行以下操作:
设置 LocalNetworkGateway 的变量。
$local = Get-AzLocalNetworkGateway -Name Site1 -ResourceGroupName TestRG1修改前缀。 指定的值将覆盖之前的值。
Set-AzLocalNetworkGateway -LocalNetworkGateway $local ` -AddressPrefix @('10.101.0.0/24','10.101.1.0/24','10.101.2.0/24')
移除地址前缀:
省去你不再需要的前缀。 在此示例中,我们不再需要前缀 10.101.2.0/24(来自前面的示例),因此我们会更新本地网关并排除该前缀。
设置 LocalNetworkGateway 的变量。
$local = Get-AzLocalNetworkGateway -Name Site1 -ResourceGroupName TestRG1使用更新的前缀来配置网关。
Set-AzLocalNetworkGateway -LocalNetworkGateway $local ` -AddressPrefix @('10.101.0.0/24','10.101.1.0/24')
修改本地网关的网关 IP 地址
如果更改 VPN 设备的公共 IP 地址,那么需要使用更新的 IP 地址来修改本地网关。 修改此值时,还可同时修改地址前缀。 修改时,请务必使用本地网关的现有名称。 如果使用其他名称,请创建一个新的本地网关,而不是覆盖现有网关信息。
New-AzLocalNetworkGateway -Name Site1 `
-Location "China North" -AddressPrefix @('10.101.0.0/24','10.101.1.0/24') `
-GatewayIpAddress "5.4.3.2" -ResourceGroupName TestRG1
删除网关连接
如果不知道连接的名称,可以使用“Get-AzVirtualNetworkGatewayConnection”cmdlet 找到它。
Remove-AzVirtualNetworkGatewayConnection -Name VNet1toSite1 `
-ResourceGroupName TestRG1
后续步骤
- 连接完成后,即可将虚拟机添加到虚拟网络。 有关详细信息,请参阅虚拟机。
- 有关 BGP 的信息,请参阅 BGP 概述和如何配置 BGP。
- 有关使用 Azure 资源管理器模板创建站点到站点 VPN 连接的信息,请参阅创建站点到站点 VPN 连接。
- 有关使用 Azure 资源管理器模板创建 vnet 到 vnet VPN 连接的信息,请参阅部署 HBase 异地复制。