Applies to:  Azure SQL Database
Azure SQL Database
Note
- Database Level TDE CMK is available for Azure SQL Database (all SQL Database editions). It isn't available for Azure SQL Managed Instance, SQL Server on-premises, Azure VMs, and Azure Synapse Analytics (dedicated SQL pools (formerly SQL DW)).
- The same guide can be applied to configure database level customer-managed keys in the same tenant by excluding the federated client ID parameter. For more information on database level customer-managed keys, see Transparent data encryption (TDE) with customer-managed keys at the database level.
In this guide, we go through the steps to create, update, and retrieve an Azure SQL Database with transparent data encryption (TDE) and customer-managed keys (CMK) at the database level, utilizing a user-assigned managed identity to access Azure Key Vault. The Azure Key Vault is in a different Microsoft Entra tenant than the Azure SQL Database. For more information, see Cross-tenant customer-managed keys with transparent data encryption.
Prerequisites
- This guide assumes that you have two Microsoft Entra tenants.
- The first consists of the Azure SQL Database resource, a multitenant Microsoft Entra application, and a user-assigned managed identity.
- The second tenant houses the Azure Key Vault.
- For comprehensive instructions on setting up cross-tenant CMK and the RBAC permissions necessary for configuring Microsoft Entra applications and Azure Key Vault, refer to one of the following guides:
- The Azure CLI version 2.52.0 or higher.
- Az PowerShell module version 10.3.0 or higher.
- The RBAC permissions necessary for database level CMK are the same permissions that are required for server level CMK. Specifically, the same RBAC permissions that are applicable when using Azure Key Vault, Managed identities, and Cross-tenant CMK for TDE at the server level are applicable at the database level. For more information on key management and access policy, see Key management.
Required resources on the first tenant
For the purpose of this tutorial, we'll assume the first tenant belongs to an independent software vendor (ISV), and the second tenant is from their client. For more information on this scenario, see Cross-tenant customer-managed keys with transparent data encryption.
Before we can configure TDE for Azure SQL Database with a cross-tenant CMK, we need to have a multitenant Microsoft Entra application that is configured with a user-assigned managed identity assigned as a federated identity credential for the application. Follow one of the guides in the Prerequisites.
On the first tenant where you want to create the Azure SQL Database, create and configure a multitenant Microsoft Entra application.
Create a user-assigned managed identity.
Configure the user-assigned managed identity as a federated identity credential for the multi-tenant application.
Record the application name and application ID. This can be found in the Azure portal > Microsoft Entra ID > Enterprise applications and search for the created application.
Required resources on the second tenant
Note
Azure AD and MSOnline PowerShell modules are deprecated as of March 30, 2024. To learn more, read the deprecation update. After this date, support for these modules are limited to migration assistance to Microsoft Graph PowerShell SDK and security fixes. The deprecated modules will continue to function through March, 30 2025.
We recommend migrating to Microsoft Graph PowerShell to interact with Microsoft Entra ID (formerly Azure AD). For common migration questions, refer to the Migration FAQ. Note: Versions 1.0.x of MSOnline may experience disruption after June 30, 2024.
On the second tenant where the Azure Key Vault resides, create a service principal (application) using the application ID from the registered application from the first tenant. Here's some examples of how to register the multi-tenant application. Replace <TenantID> and <ApplicationID> with the client Tenant ID from Microsoft Entra ID and Application ID from the multitenant application, respectively:
Go to the Azure portal > Microsoft Entra ID > Enterprise applications and search for the application that was created.
Create an Azure Key Vault if you don't have one, and create a key
Create or set the access policy.
- Select the Get, Wrap Key, Unwrap Key permissions under Key permissions when creating the access policy.
- Select the multitenant application created in the first step in the Principal option when creating the access policy.
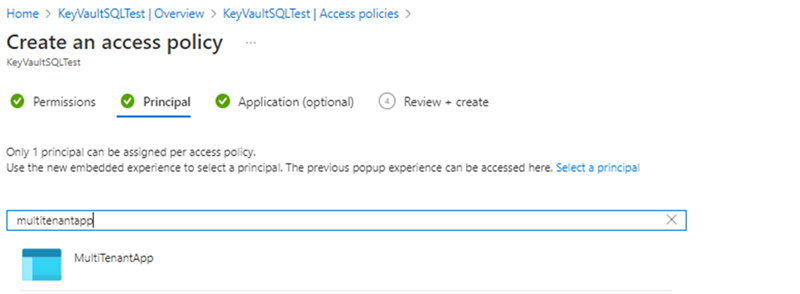
Once the access policy and key has been created, Retrieve the key from Azure Key Vault and record the Key Identifier.
Create a new Azure SQL Database with database level customer-managed keys
The following are examples for creating a database on Azure SQL Database with a user-assigned managed identity, and how to set a cross-tenant customer managed key at the database level. The user-assigned managed identity is required for setting up a customer-managed key for transparent data encryption during the database creation phase.
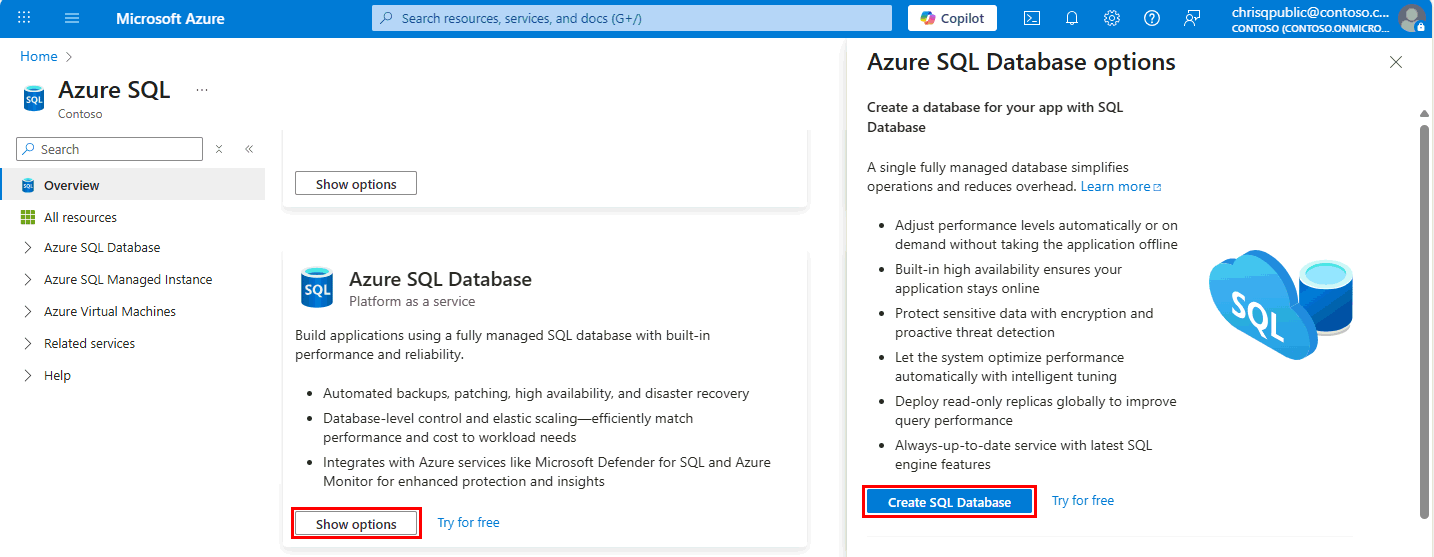
Go to Azure SQL hub.
In the pane for Azure SQL Database, select Show options.
In the Azure SQL Database options window, select Create SQL Database.
On the Basics tab of the Create SQL Database form, under Project details, select the desired Azure Subscription, Resource group, and Server for your database. Then, use a unique name for your Database name. If you haven't created a logical server for Azure SQL Database, see Create server configured with TDE with cross-tenant customer-managed key (CMK) for reference.
When you get to the Security tab, select Configure transparent data encryption for the Database level key.
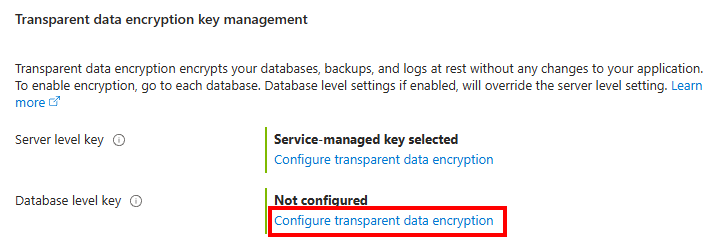
On the Transparent data encryption menu, select Database level customer managed key (CMK).
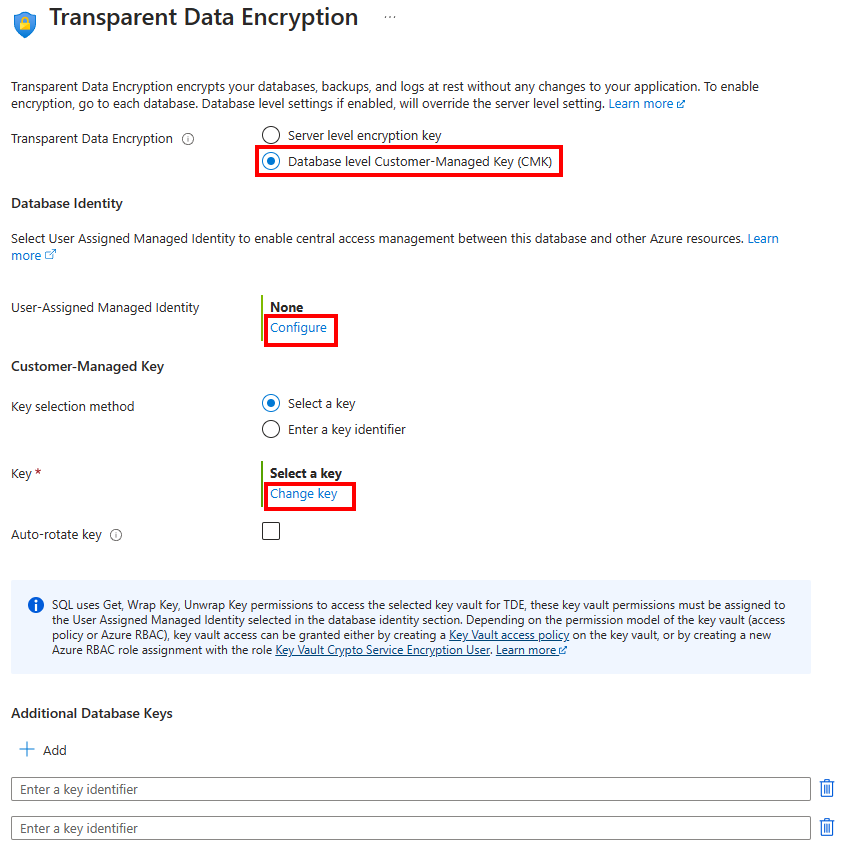
For User-Assigned Managed Identity, select Configure to enable a Database identity and Add a user assigned managed identity to the resource if a desired identity isn't list in the Identity menu. Then select Apply.
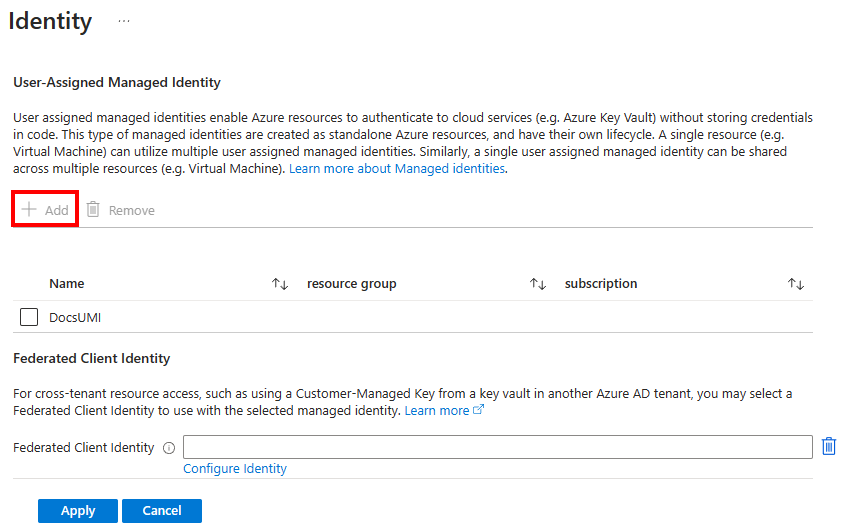
On the Transparent data encryption menu, select Change key. Select the desired Subscription, Key vault, Key, and Version for the customer-managed key to be used for TDE. Select the Select button. After you have selected a key, you can also add additional database keys as needed using the Azure Key vault URI (object identifier) in the Transparent data encryption menu.
Automatic key rotation can also be enabled on the database level by using the Auto-rotate key checkbox in the Transparent data encryption menu.
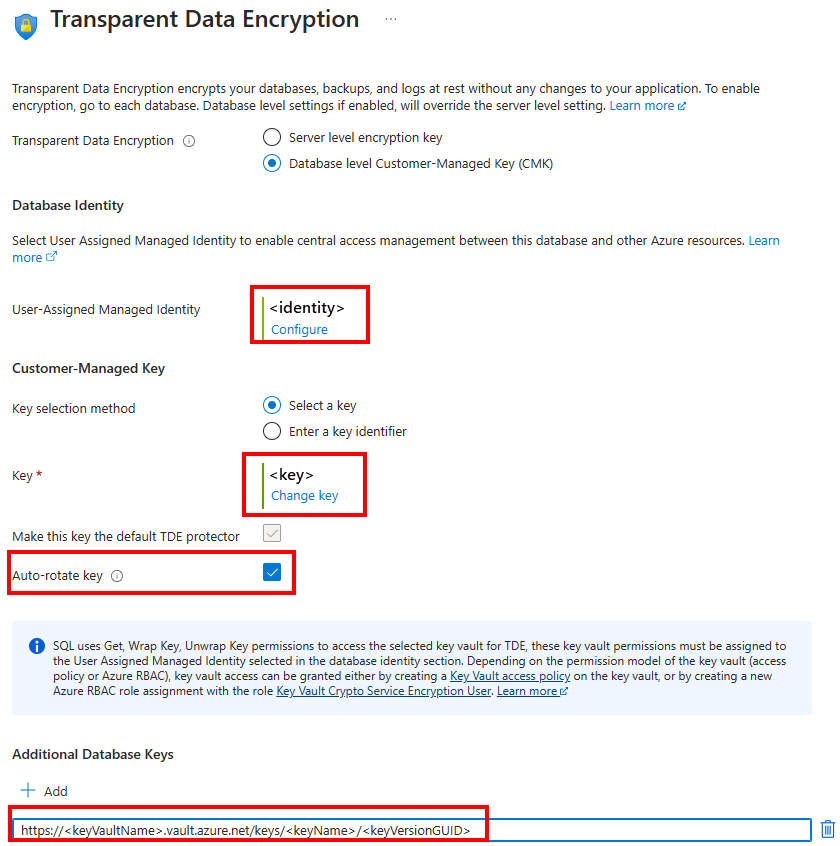
Select Apply to continue creating the database.
Select Next: Additional settings.
Select Next: Tags.
Consider using Azure tags. For example, the "Owner" or "CreatedBy" tag to identify who created the resource, and the Environment tag to identify whether this resource is in Production, Development, etc.
Select Review + create.
On the Review + create page, after reviewing, select Create.
For information on installing the current release of Azure CLI, see Install the Azure CLI article.
Create a database configured with user-assigned managed identity and cross-tenant customer-managed TDE using the az sql db create command. The Key Identifier from the second tenant can be used in the encryption-protector field. The Application ID of the multi-tenant application can be used in the federated-client-id field. The --encryption-protector-auto-rotation parameter can be used to enable automatic key rotation on the database level.
To get your user-assigned managed identity Resource ID, search for Managed Identities in the Azure portal. Find your managed identity, and go to Properties. An example of your UMI Resource ID looks like /subscriptions/<subscriptionId>/resourceGroups/<ResourceGroupName>/providers/Microsoft.ManagedIdentity/userAssignedIdentities/<managedIdentity>
az sql db create --resource-group $resourceGroupName --server $serverName --name mySampleDatabase --sample-name AdventureWorksLT --edition GeneralPurpose --compute-model Serverless --family Gen5 --capacity 2 --assign-identity --user-assigned-identity-id $identityid --encryption-protector $keyid --federated-client-id $federatedclientid --encryption-protector-auto-rotation True
Create a database configured with user-assigned managed identity and cross-tenant customer-managed TDE at the database level using PowerShell.
For Az PowerShell module installation instructions, see Install Azure PowerShell.
Use the New-AzSqlDatabase cmdlet.
Replace the following values in the example:
<ResourceGroupName>: Name of the resource group for your Azure SQL logical server<DatabaseName>: Use a unique Azure SQL database name<ServerName>: Use a unique Azure SQL logical server name<UserAssignedIdentityId>: The list of user-assigned managed identities to be assigned to the server (can be one or multiple)<CustomerManagedKeyId>: The Key Identifier from the second tenant Azure Key Vault<FederatedClientId>: The Application ID of the multitenant application-EncryptionProtectorAutoRotation: Can be used to enable automatic key rotation on the database level
To get your user-assigned managed identity Resource ID, search for Managed Identities in the Azure portal. Find your managed identity, and go to Properties. An example of your UMI Resource ID looks like /subscriptions/<subscriptionId>/resourceGroups/<ResourceGroupName>/providers/Microsoft.ManagedIdentity/userAssignedIdentities/<managedIdentity>
# create a server with user-assigned managed identity and cross-tenant customer-managed TDE with automatic key rotation enabled
$params = @{
ResourceGroupName = '<ResourceGroupName>'
ServerName = '<ServerName>'
DatabaseName = '<DatabaseName>'
AssignIdentity = $true
UserAssignedIdentityId = '<UserAssignedIdentityId>'
EncryptionProtector = '<CustomerManagedKeyId>'
FederatedClientId = '<FederatedClientId>'
EncryptionProtectorAutoRotation = $true
}
New-AzSqlDatabase @params
Here's an example of an ARM template that creates an Azure SQL Database with a user-assigned managed identity and customer-managed TDE at the database level. For a cross-tenant CMK, use the Key Identifier from the second tenant Azure Key Vault, and the Application ID from the multitenant application.
For more information and ARM templates, see Azure Resource Manager templates for Azure SQL Database.
Use a Custom deployment in the Azure portal, and Build your own template in the editor. Next, Save the configuration once you pasted in the example.
To get your user-assigned managed identity Resource ID, search for Managed Identities in the Azure portal. Find your managed identity, and go to Properties. An example of your UMI Resource ID looks like /subscriptions/<subscriptionId>/resourceGroups/<ResourceGroupName>/providers/Microsoft.ManagedIdentity/userAssignedIdentities/<managedIdentity>.
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"server_name": {
"type": "String"
},
"database_name": {
"type": "String"
},
"user_assigned_identity": {
"type": "String"
},
"encryption_protector": {
"type": "String"
},
"federated_client_id": {
"type": "String"
},
"location": {
"type": "String"
},
"encryption_protector_auto_rotation": {
"type": "bool"
}
},
"variables": {},
"resources": [
{
"type": "Microsoft.Sql/servers/databases",
"apiVersion": "2023-02-01-preview",
"name": "[concat(parameters('server_name'), concat('/',parameters('database_name')))]",
"location": "[parameters('location')]",
"sku": {
"name": "Basic",
"tier": "Basic",
"capacity": 5
},
"identity": {
"type": "UserAssigned",
"userAssignedIdentities": {
"[parameters('user_assigned_identity')]": {}
}
},
"properties": {
"collation": "SQL_Latin1_General_CP1_CI_AS",
"maxSizeBytes": 104857600,
"catalogCollation": "SQL_Latin1_General_CP1_CI_AS",
"zoneRedundant": false,
"readScale": "Disabled",
"requestedBackupStorageRedundancy": "Geo",
"maintenanceConfigurationId": "/subscriptions/00000000-0000-0000-0000-000000000000/providers/Microsoft.Maintenance/publicMaintenanceConfigurations/SQL_Default",
"isLedgerOn": false,
"encryptionProtector": "[parameters('encryption_protector')]",
"federatedClientId": "[parameters('federated_client_id')]",
"encryptionProtectorAutoRotation": "[parameters('encryption_protector_auto_rotation')]"
}
}
]
}
Update an existing Azure SQL Database with database level customer-managed keys
This following are examples of updating an existing database on Azure SQL Database with a user-assigned managed identity, and how to set a cross-tenant customer managed key at the database level. The user-assigned managed identity is required for setting up a customer-managed key for transparent data encryption during the database creation phase.
In the Azure portal, navigate to the SQL database resource that you want to update with a database level customer-managed key.
Under Security, select Identity. Add a User assigned managed identity for this database, and then select Save
Now go to the Data Encryption menu under Security for your database. Select Database level customer managed key (CMK). The Database Identity for the database should already be Enabled as you have configured the identity in the last step.
Select Change key. Select the desired Subscription, Key vault, Key, and Version for the customer-managed key to be used for TDE. Select the Select button. After you have selected a key, you can also add additional database keys as needed using the Azure Key vault URI (object identifier) in the Data Encryption menu.
Select the Auto-rotate key checkbox if you want to enable automatic key rotation on the database level.
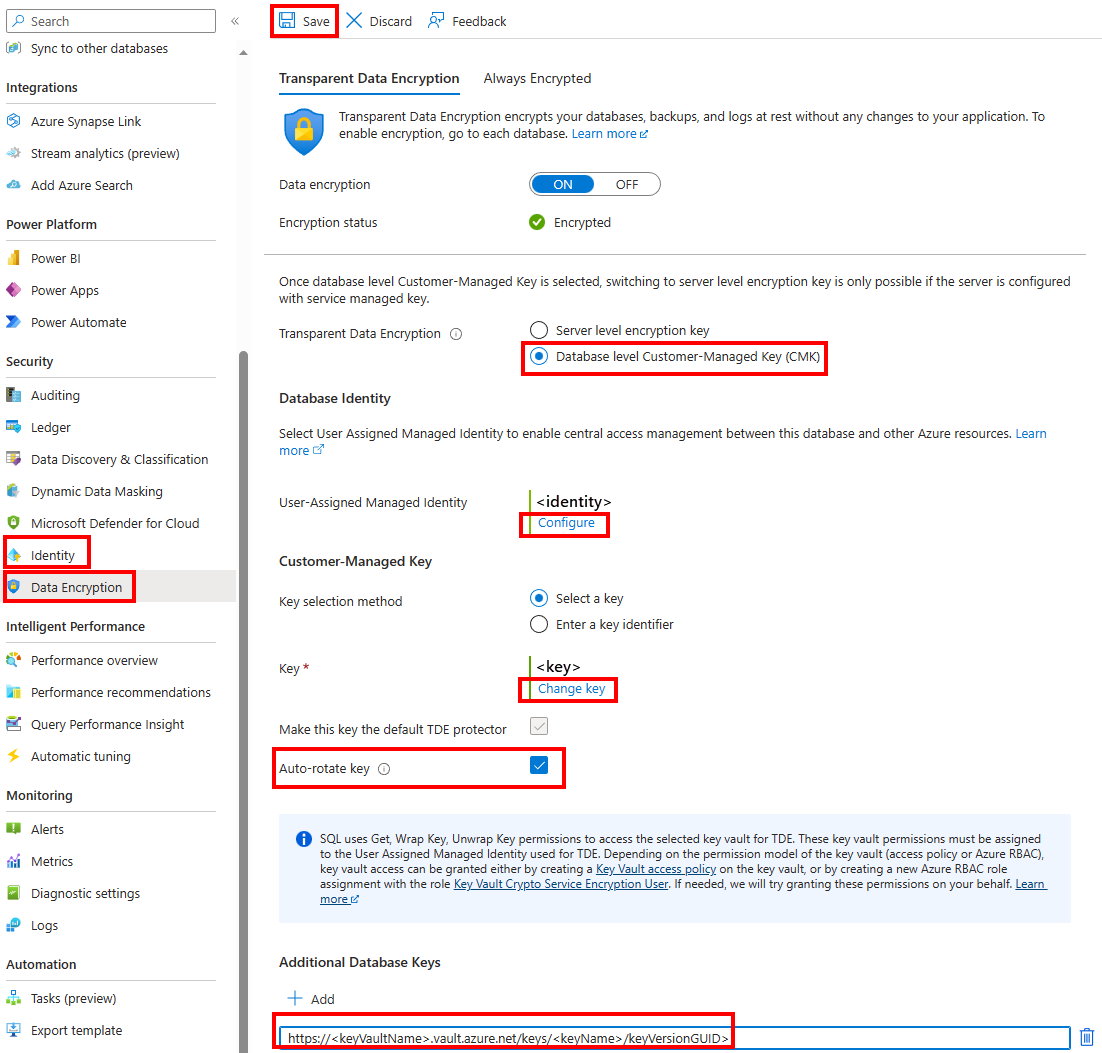
Select Save.
For information on installing the current release of Azure CLI, see Install the Azure CLI article.
Update a database configured with user-assigned managed identity and cross-tenant customer-managed TDE using the az sql db create command. The Key Identifier from the second tenant can be used in the encryption-protector field. The Application ID of the multi-tenant application can be used in the federated-client-id field.
To get your user-assigned managed identity Resource ID, search for Managed Identities in the Azure portal. Find your managed identity, and go to Properties. An example of your UMI Resource ID looks like /subscriptions/<subscriptionId>/resourceGroups/<ResourceGroupName>/providers/Microsoft.ManagedIdentity/userAssignedIdentities/<managedIdentity>. The --encryption-protector-auto-rotation parameter can be used to enable automatic key rotation on the database level.
az sql db update --resource-group $resourceGroupName --server $serverName --name mySampleDatabase --sample-name AdventureWorksLT --edition GeneralPurpose --compute-model Serverless --family Gen5 --capacity 2 --assign-identity --user-assigned-identity-id $identityid --encryption-protector $keyid --federated-client-id $federatedclientid --keys $keys --keys-to-remove $keysToRemove --encryption-protector-auto-rotation True
The list $keys are a space separated list of keys that are to be added on the database and $keysToRemove is a space separated list of keys that have to be removed from the database
$keys = '"https://yourvault.vault.azure.cn/keys/yourkey1/6638b3667e384aefa31364f94d230000" "https://yourvault.vault.azure.cn/keys/yourkey2/ fd021f84a0d94d43b8ef33154bca0000"'
$keysToRemove = '"https://yourvault.vault.azure.cn/keys/yourkey3/6638b3667e384aefa31364f94d230000" "https://yourvault.vault.azure.cn/keys/yourkey4/fd021f84a0d94d43b8ef33154bca0000"'
Update a database configured with user-assigned managed identity and cross-tenant customer-managed TDE at the database level using PowerShell.
For Az PowerShell module installation instructions, see Install Azure PowerShell.
Use the Set-AzSqlDatabase cmdlet.
Replace the following values in the example:
<ResourceGroupName>: Name of the resource group for your Azure SQL logical server<DatabaseName>: Use a unique Azure SQL database name<ServerName>: Use a unique Azure SQL logical server name<UserAssignedIdentityId>: The list of user-assigned managed identities to be assigned to the server (can be one or multiple)<CustomerManagedKeyId>: The Key Identifier from the second tenant Azure Key Vault<FederatedClientId>: The Application ID of the multitenant application<ListOfKeys>: The comma separated list of database level customer-managed keys to be added to the database<ListOfKeysToRemove>: The comma separated list of database level customer-managed keys to be removed from the database-EncryptionProtectorAutoRotation: Can be used to enable automatic key rotation on the database level
To get your user-assigned managed identity Resource ID, search for Managed Identities in the Azure portal. Find your managed identity, and go to Properties. An example of your UMI Resource ID looks like /subscriptions/<subscriptionId>/resourceGroups/<ResourceGroupName>/providers/Microsoft.ManagedIdentity/userAssignedIdentities/<managedIdentity>.
$params = @{
ResourceGroupName = "<ResourceGroupName>"
ServerName = "<ServerName>"
DatabaseName = "<DatabaseName>"
AssignIdentity = $true
UserAssignedIdentityId = "<UserAssignedIdentityId>"
EncryptionProtector = "<CustomerManagedKeyId>"
FederatedClientId = "<FederatedClientId>"
KeyList = "<ListOfKeys>"
KeysToRemove = "<ListOfKeysToRemove>"
EncryptionProtectorAutoRotation = $true
}
Set-AzSqlDatabase @params
An example of -KeyList and -KeysToRemove is:
$keysToAdd = "https://yourvault.vault.azure.cn/keys/yourkey1/fd021f84a0d94d43b8ef33154bca0000","https://yourvault.vault.azure.cn/keys/yourkey2/fd021f84a0d94d43b8ef33154bca0000"
$keysToRemove = "https://yourvault.vault.azure.cn/keys/yourkey3/fd021f84a0d94d43b8ef33154bca0000"
Here's an example of an ARM template that updates an Azure SQL Database with a user-assigned managed identity and customer-managed TDE at the database level. For a cross-tenant CMK, use the Key Identifier from the second tenant Azure Key Vault, and the Application ID from the multitenant application.
For more information and ARM templates, see Azure Resource Manager templates for Azure SQL Database.
Use a Custom deployment in the Azure portal, and Build your own template in the editor. Next, Save the configuration once you pasted in the example.
To get your user-assigned managed identity Resource ID, search for Managed Identities in the Azure portal. Find your managed identity, and go to Properties. An example of your UMI Resource ID looks like /subscriptions/<subscriptionId>/resourceGroups/<ResourceGroupName>/providers/Microsoft.ManagedIdentity/userAssignedIdentities/<managedIdentity>.
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"server_name": {
"type": "String"
},
"database_name": {
"type": "String"
},
"user_assigned_identity": {
"type": "String"
},
"encryption_protector": {
"type": "String"
},
"location": {
"type": "String"
},
"federated_client_id": {
"type": "String"
},
"keys_to_add": {
"type": "Object"
},
"encryption_protector_auto_rotation": {
"type": "bool"
}
},
"variables": {},
"resources": [
{
"type": "Microsoft.Sql/servers/databases",
"apiVersion": "2023-02-01-preview",
"name": "[concat(parameters('server_name'), concat('/',parameters('database_name')))]",
"location": "[parameters('location')]",
"sku": {
"name": "Basic",
"tier": "Basic",
"capacity": 5
},
"identity": {
"type": "UserAssigned",
"userAssignedIdentities": {
"[parameters('user_assigned_identity')]": {}
}
},
"properties": {
"collation": "SQL_Latin1_General_CP1_CI_AS",
"maxSizeBytes": 104857600,
"catalogCollation": "SQL_Latin1_General_CP1_CI_AS",
"zoneRedundant": false,
"readScale": "Disabled",
"requestedBackupStorageRedundancy": "Geo",
"maintenanceConfigurationId": "/subscriptions/e1775f9f-a286-474d-b6f0-29c42ac74554/providers/Microsoft.Maintenance/publicMaintenanceConfigurations/SQL_Default",
"isLedgerOn": false,
"encryptionProtector": "[parameters('encryption_protector')]",
"keys": "[parameters('keys_to_add')]",
"federatedClientId": "[parameters('federated_client_id')]",
"encryptionProtectorAutoRotation": "[parameters('encryption_protector_auto_rotation')]"
}
}
]
}
An example of the encryption_protector and keys_to_add parameter is:
"keys_to_add": {
"value": {
"https://yourvault.vault.azure.cn/keys/yourkey1/fd021f84a0d94d43b8ef33154bca0000": {},
"https://yourvault.vault.azure.cn/keys/yourkey2/fd021f84a0d94d43b8ef33154bca0000": {}
}
},
"encryption_protector": {
"value": "https://yourvault.vault.azure.cn/keys/yourkey2/fd021f84a0d94d43b8ef33154bca0000"
}
Important
To remove a key from the database, the keys dictionary value of a particular key must be passed as null. For example, "https://yourvault.vault.azure.cn/keys/yourkey1/fd021f84a0d94d43b8ef33154bca0000": null.
View the database level customer-managed key settings on an Azure SQL Database
The following are examples of retrieving the database level customer-managed keys for a database. The ARM resource Microsoft.Sql/servers/databases by default only shows the TDE protector and managed identity configured on the database. To expand the full list of keys use the parameter, -ExpandKeyList. Additionally, filters such as -KeysFilter "current" and a point in time value (for example, 2023-01-01) can be used to retrieve the current keys used and keys used in the past at a specific point in time. These filters are only supported for individual database queries and not for server level queries.
To view the database level customer-managed keys in the Azure portal, go to the Data Encryption menu of the SQL database resource.
For information on installing the current release of Azure CLI, see Install the Azure CLI article.
# Retrieve the basic database level customer-managed key settings from a database
az sql db show --resource-group $resourceGroupName --server $serverName --name mySampleDatabase
# Retrieve the basic database level customer-managed key settings from a database and all the keys ever added
az sql db show --resource-group $resourceGroupName --server $serverName --name mySampleDatabase --expand-keys
# Retrieve the basic database level customer-managed key settings from a database and the current keys in use
az sql db show --resource-group $resourceGroupName --server $serverName --name mySampleDatabase --expand-keys --keys-filter current
# Retrieve the basic database level customer-managed key settings from a database and the keys in use at a particular point in time
az sql db show --resource-group $resourceGroupName --server $serverName --name mySampleDatabase --expand-keys --keys-filter 01-01-2015
# Retrieve all the databases in a server to check which ones are configured with database level customer-managed keys
az sql db list --resource-group $resourceGroupName --server $serverName
For Az PowerShell module installation instructions, see Install Azure PowerShell.
Use the Get-AzSqlDatabase cmdlet.
# Retrieve the basic database level customer-managed key settings from a database
Get-AzSqlDatabase -ResourceGroupName <ResourceGroupName> -ServerName <ServerName> -DatabaseName <DatabaseName>
# Retrieve the basic database level customer-managed key settings from a database and all the keys ever added
Get-AzSqlDatabase -ResourceGroupName <ResourceGroupName> -ServerName <ServerName> -DatabaseName <DatabaseName> -ExpandKeyList
# Retrieve the basic database level customer-managed key settings from a database and the current keys in use
Get-AzSqlDatabase -ResourceGroupName <ResourceGroupName> -ServerName <ServerName> -DatabaseName <DatabaseName> -ExpandKeyList -KeysFilter "current"
# Retrieve the basic database level customer-managed key settings from a database and the keys in use at a particular point in time
Get-AzSqlDatabase -ResourceGroupName <ResourceGroupName> -ServerName <ServerName> -DatabaseName <DatabaseName> -ExpandKeyList -KeysFilter '2023-02-03 00:00:00'
# Retrieve all the databases in a server to check which ones are configured with database level customer-managed keys
Get-AzSqlDatabase -resourceGroupName <ResourceGroupName> -ServerName <ServerName> | Select DatabaseName, EncryptionProtector
Use the 2022-08-01-preview REST API for Azure SQL Database.
Retrieve the basic database level customer-managed key settings from a database.
GET https://management.chinacloudapi.cn/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/Microsoft.Sql/servers/{serverName}/databases/{databaseName}?api-version=2022-08-01-preview
Retrieve the basic database level customer-managed key settings from a database and all the keys ever added
GET https://management.chinacloudapi.cn/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/Microsoft.Sql/servers/{serverName}/databases/{databaseName}?api-version=2022-08-01-preview&$expand=keys
Retrieve the basic database level customer-managed key settings from a database and the current keys in use
GET https://management.chinacloudapi.cn/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/Microsoft.Sql/servers/{serverName}/databases/{databaseName}?api-version=2022-08-01-preview&$expand=keys($filter=pointInTime('current'))
Retrieve the basic database level customer-managed key settings from a database and the keys in use at a particular point in time
GET https://management.chinacloudapi.cn/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/Microsoft.Sql/servers/{serverName}/databases/{databaseName}?api-version=2022-08-01-preview&$expand=keys($filter=pointInTime('2023-02-04T01:57:42.49Z'))
List all keys in a logical server
To fetch the list of all the keys (and not just the primary protector) used by each database under the server, it must be individually queried with the key filters. The following is an example of a PowerShell query to list each key under the logical server.
Use the Get-AzSqlDatabase cmdlet.
$dbs = Get-AzSqlDatabase -resourceGroupName <ResourceGroupName> -ServerName <ServerName>
foreach ($db in $dbs)
{
Get-AzSqlDatabase -DatabaseName $db.DatabaseName -ServerName $db.ServerName -ResourceGroupName $db.ResourceGroupName -ExpandKeyList
}
Revalidate the database level customer-managed key on an Azure SQL Database
In case of an inaccessible TDE protector as described in Azure SQL transparent data encryption with customer-managed key, once the key access has been corrected, a revalidate key operation can be used to make the database accessible. See the following instructions or commands for examples.
Using the Azure portal, find your SQL database resource. Once you have selected your SQL database resource, go to the Transparent Data Encryption tab of the Data Encryption menu under the Security settings. If the database has lost access to the Azure Key Vault, a Revalidate key button will appear, and you'll have the option to revalidate the existing key by selecting Retry existing key, or another key by selecting Select backup key.
For information on installing the current release of Azure CLI, see Install the Azure CLI article.
az sql db tde key revalidate --resource-group $resourceGroupName --server $serverName --database mySampleDatabase
Use the 2022-08-01-preview REST API for Azure SQL Database.
POST https://management.chinacloudapi.cn/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/Microsoft.Sql/servers/{serverName}/databases/{databaseName}/encryptionProtector/current/revalidate?api-version=2022-08-01-preview
Revert the database level customer-managed key on an Azure SQL Database
A database configured with database level CMK can be reverted to server level encryption if the server is configured with a service-managed key using the following commands.
To revert the database level customer-managed key setting to server level encryption key in the Azure portal, go to the Transparent Data Encryption tab of the Data Encryption menu of the SQL database resource. Select Server level encryption key and select Save to save the settings.
Note
In order to use the Server level encryption key setting for individual databases, the logical server for the Azure SQL Database must be configured to use Service-managed key for TDE.
For information on installing the current release of Azure CLI, see Install the Azure CLI article.
az sql db tde key revert --resource-group $resourceGroupName --server $serverName --name mySampleDatabase
Use the 2022-08-01-preview REST API for Azure SQL Database.
POST https://management.chinacloudapi.cn/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/Microsoft.Sql/servers/{serverName}/databases/{databaseName}/encryptionProtector/current/revert?api-version=2022-08-01-preview
Related content
Azure SQL Database






