Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Applies to:
Azure SQL Managed Instance
This article describes the connectivity architecture of Azure SQL Managed Instance and how components direct communication traffic for a SQL managed instance.
Overview
In SQL Managed Instance, an instance is placed inside the Azure virtual network and inside the subnet that's dedicated to SQL managed instances. The deployment provides:
- A secure virtual network-local (VNet-local) IP address.
- The ability to connect an on-premises network to SQL Managed Instance.
- The ability to connect SQL Managed Instance to a linked server or to another on-premises data store.
- The ability to connect SQL Managed Instance to Azure resources.
High-level connectivity architecture
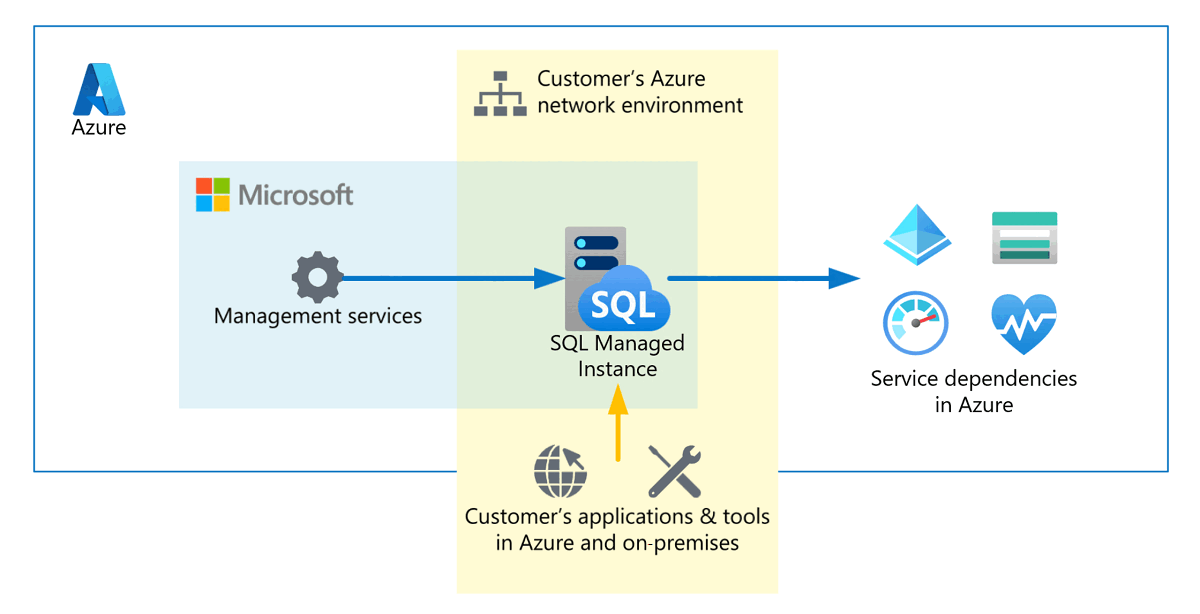
SQL Managed Instance is made up of service components hosted on a dedicated set of isolated virtual machines grouped together by similar configuration attributes and joined to a virtual cluster. Some service components are deployed inside the customer's virtual network subnet, while other services operate within a secure network environment that Azure manages.
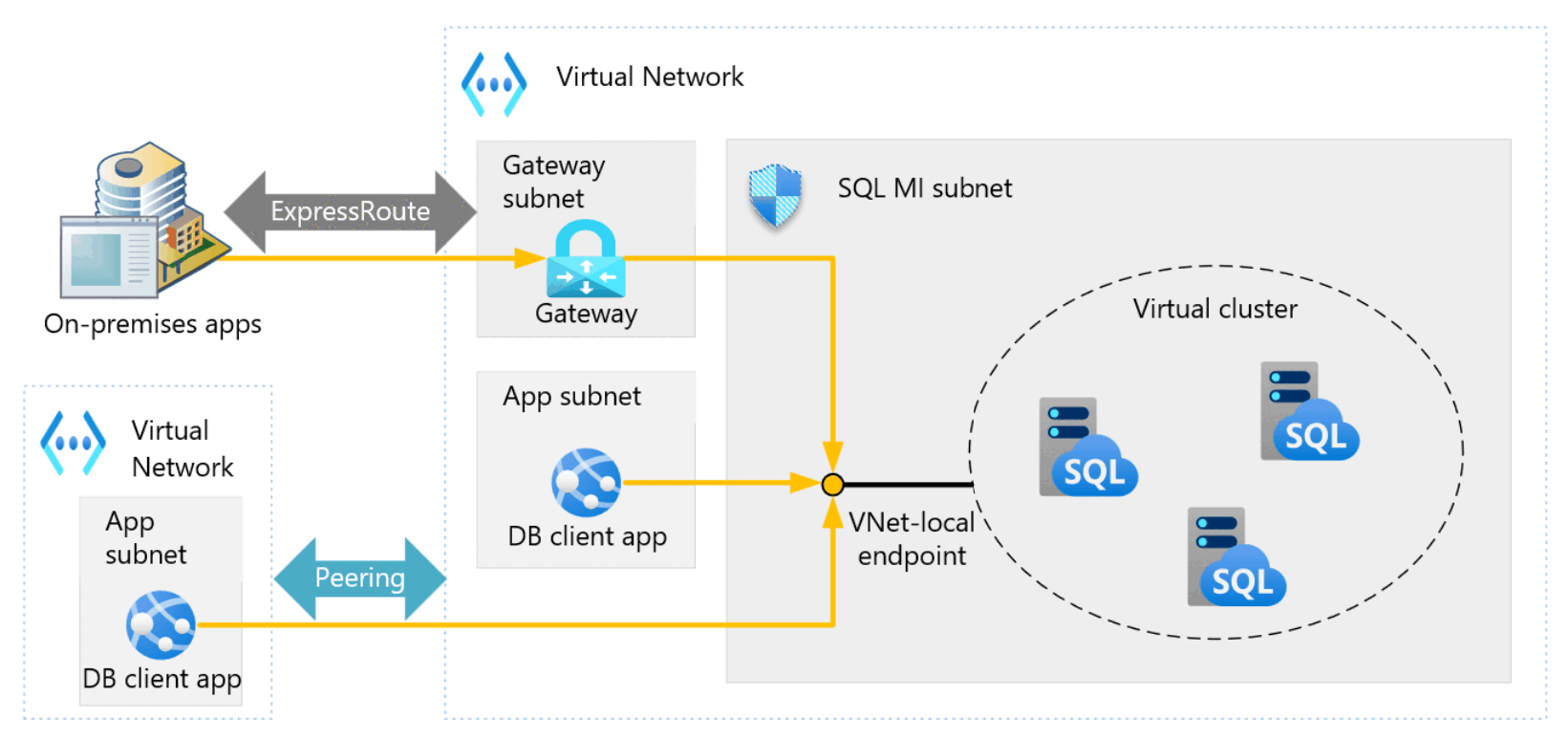
Customer applications can connect to SQL Managed Instance and can query and update databases inside the virtual network, peered virtual network, or network connected by VPN or Azure ExpressRoute.
The following diagram shows entities that connect to SQL Managed Instance. It also shows the resources that need to communicate with a SQL managed instance. The communication process at the bottom of the diagram represents customer applications and tools that connect to SQL Managed Instance as data sources.
SQL Managed Instance is a single-tenant, platform as a service offering that operates in two planes: a data plane and a control plane.
The data plane is deployed inside the customer's subnet for compatibility, connectivity, and network isolation. The data plane depends on Azure services like Azure Storage, Microsoft Entra ID (formerly Azure Active Directory) for authentication, and telemetry collection services. You'll see traffic that originates in subnets that contain SQL Managed Instance going to those services.
The control plane carries the deployment, management, and core service maintenance functions via automated agents. These agents have exclusive access to the compute resources that operate the service. You can't use SSH or Remote Desktop Protocol to access those hosts. All control plane communications are encrypted and signed by using certificates. To check the trustworthiness of communicating parties, SQL Managed Instance constantly verifies these certificates by using certificate revocation lists.
Communication overview
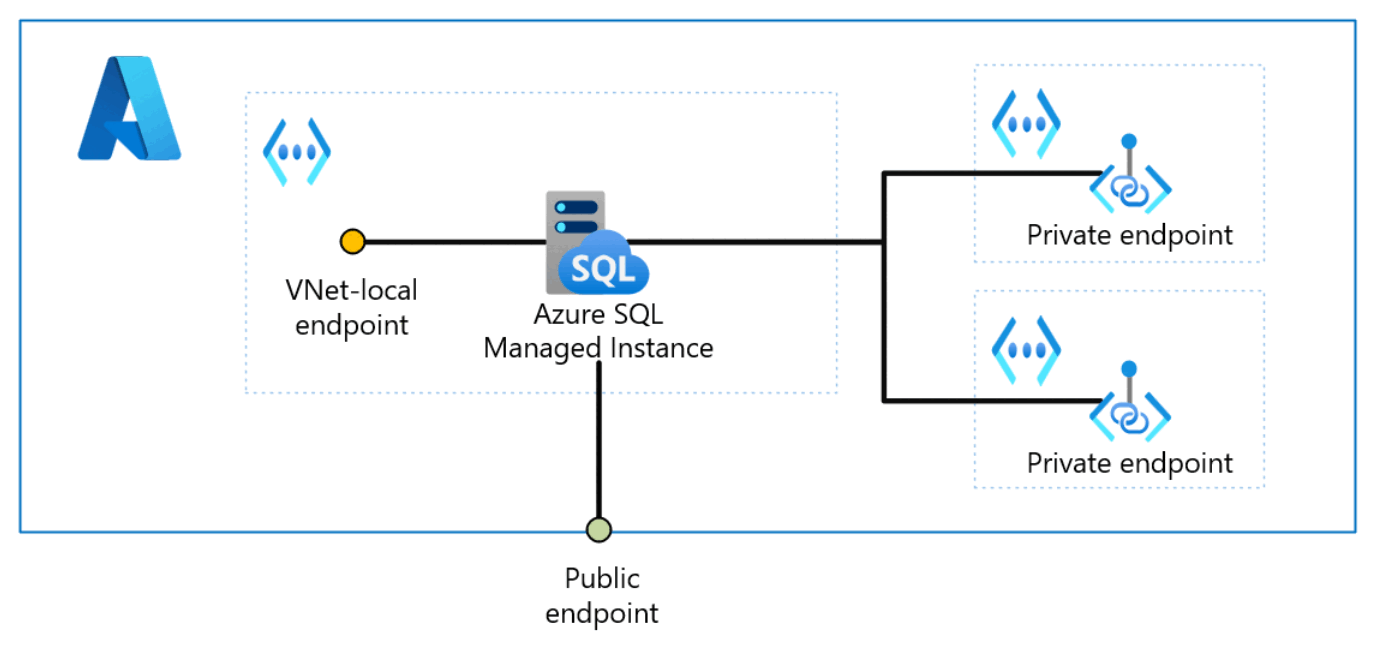
Applications can connect to SQL Managed Instance via three types of endpoints: VNet-local endpoint, public endpoint, and private endpoints. These endpoints exhibit distinct properties and behaviors suitable for different scenarios.
VNet-local endpoint
The VNet-local endpoint is the default means to connect to SQL Managed Instance. The VNet-local endpoint domain name is in the form of <mi_name>.<dns_zone>.database.chinacloudapi.cn. This domain name resolves to an IP address from the subnet's address range. Use the VNet-local endpoint to connect to a SQL Managed Instance in all standard connectivity scenarios. The VNet-local endpoint accepts connections on port 1433.
The VNet-local endpoint supports Proxy and redirect connection types.
When connecting to the VNet-local endpoint, always use its domain name and allow inbound traffic on the required ports across the entire subnet range, as the underlying IP address can occasionally change.
To find the VNet-local endpoint domain name for an instance:
- Azure portal: On the Overview pane, in the Essentials section, the Host value shows the VNet-local endpoint domain name.
- PowerShell:
Get-AzSqlInstance -ResourceGroupName <resource-group> -Name <mi-name>shows the VNet-local endpoint domain name as thefullyQualifiedDomainNameproperty. - Azure CLI:
az sql mi show -g <resource-group> -n <mi-name>shows the VNet-local endpoint domain name as thefullyQualifiedDomainNameproperty.
For improved security, specify an encrypted connection, and don't trust the certificate. For more information, see Security overview.
Public endpoint
The public endpoint is a domain name in the form of <mi_name>.public.<dns_zone>.database.chinacloudapi.cn. This domain name resolves to a public IP address reachable from the internet. The public endpoint is suitable for scenarios when a SQL managed instance needs to be accessible via the public internet. For example, when connecting to it from a different virtual network when peering or private endpoints aren't available. Public endpoints only carry client traffic and can't be used for data replication between two instances, such as failover groups or Managed Instance link. Public endpoint accepts connections on port 3342.
Public endpoint always uses the Proxy connection type regardless of the connection type setting.
An instance's public endpoint domain name is equal to its VNet-local endpoint name with the label public inserted between the hostname and the rest of the domain: <mi-name>.public.<dns-zone>.database.chinacloudapi.cn.
When connecting to the public endpoint, always use its domain name and allow inbound traffic on port 3342 across the entire subnet range, as the underlying IP address can occasionally change.
Learn how to set up a public endpoint in Configure public endpoint for Azure SQL Managed Instance.
Private endpoints
A private endpoint is an optional fixed IP address in another virtual network that conducts traffic to your SQL managed instance. One Azure SQL Managed Instance can have multiple private endpoints in multiple virtual networks. Private endpoints only carry client traffic and can't be used for data replication between two instances, such as failover groups or Managed Instance link. The private endpoint accepts connections on port 1433.
Private endpoints always use the Proxy connection type regardless of the connection type setting.
An instance's private endpoint domain name is equal to its VNet-local domain name unless the endpoint has been configured differently. This is the case when both the private endpoint and VNet-local endpoint are in the same virtual network. For more information, see Set up domain name resolution for private endpoint.
When connecting to a private endpoint, always use the domain name since connecting to Azure SQL Managed Instance via its IP address isn't supported yet. The IP address of a private endpoint, however, doesn't change.
Learn more about private endpoints and how to configure them in Azure Private Link for Azure SQL Managed Instance.
Virtual cluster connectivity architecture
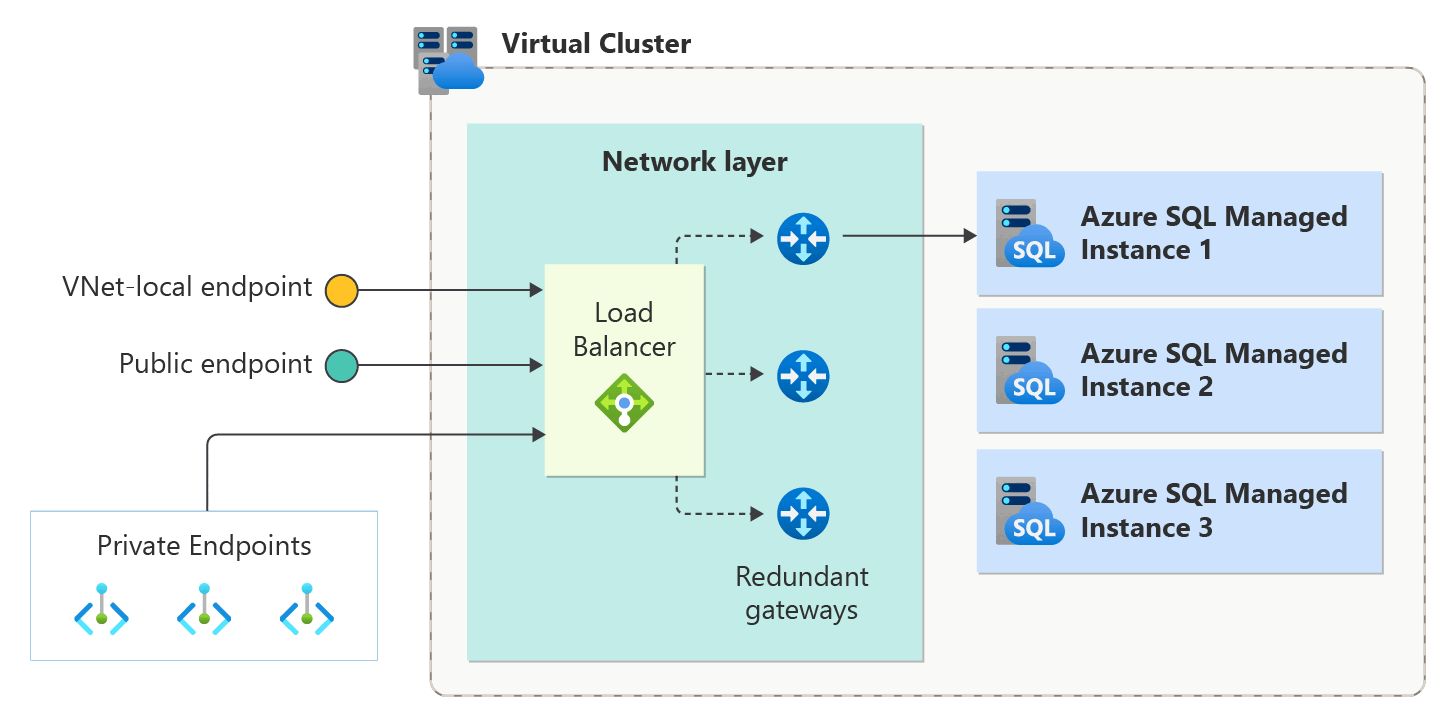
The following diagram shows the conceptual layout of the Virtual cluster architecture:
The domain name of the VNet-local endpoint resolves to the private IP address of an internal load balancer. Although this domain name is registered in a public Domain Name System (DNS) zone and is publicly resolvable, its IP address belongs to the subnet's address range and can only be reached from inside its virtual network by default.
The load balancer directs traffic to a SQL Managed Instance gateway. Because multiple SQL managed instances can run inside the same cluster, the gateway uses the SQL Managed Instance host name as seen in the connection string to redirect traffic to the correct SQL engine service.
The value for dns-zone is automatically generated when you create the cluster. If a newly created cluster hosts a secondary SQL managed instance, it shares its zone ID with the primary cluster.
Network requirements
Azure SQL Managed Instance requires aspects of the delegated subnet to be configured in specific ways, which you can achieve by using the service-aided subnet configuration. Beyond what the service requires, users have full control over their subnet network configuration, such as:
- Allowing or blocking traffic on some or all the ports.
- Adding entries to the route table to route traffic through virtual network appliances or a gateway.
- Configuring custom DNS resolution.
- Setting up peering or a VPN.
To meet the Compliant Network Configuration criteria in the Service Level Agreement for Microsoft Online Services, the virtual network and subnet in which SQL Managed Instance is deployed must meet the following requirements:
- Dedicated subnet: The subnet SQL Managed Instance uses can be delegated only to the SQL Managed Instance service. The subnet can't be a gateway subnet, and you can deploy only SQL Managed Instance resources in the subnet.
- Subnet delegation: The SQL Managed Instance subnet must be delegated to the
Microsoft.Sql/managedInstancesresource provider. - Network security group: A network security group must be associated with the SQL Managed Instance subnet. You can use a network security group to control access to the SQL Managed Instance data endpoint by filtering inbound traffic on port 1433. The service automatically provisions rules and keeps them current as required to allow uninterrupted flow of management traffic.
- Route table: A route table must be associated with the SQL Managed Instance subnet. You can add entries to this route table, for example to route traffic to premises through a virtual network gateway, or to add the default 0.0.0.0/0 route directing all traffic through a virtual network appliance such as a firewall. Azure SQL Managed Instance automatically provisions and manages its required entries in the route table.
- Sufficient IP addresses: The SQL Managed Instance subnet must have at least 32 IP addresses. For more information, see Determine the size of the subnet for SQL Managed Instance. You can deploy SQL managed instances within an existing network after you configure it to satisfy the networking requirements for SQL Managed Instance. Otherwise, create a new network and subnet.
- Allowed by Azure policies: If you use Azure Policy to prevent resource creation or modification in a scope that includes a SQL Managed Instance subnet or virtual network, your policies must not prevent SQL Managed Instance from managing its internal resources. The following resources need to be excluded from policy deny effects for normal operation:
- Resources of type
Microsoft.Network/serviceEndpointPolicies, when resource name begins with\_e41f87a2\_ - All resources of type
Microsoft.Network/networkIntentPolicies - All resources of type
Microsoft.Network/virtualNetworks/subnets/contextualServiceEndpointPolicies
- Resources of type
- Locks on virtual network: Locks on the dedicated subnet's virtual network, its parent resource group, or subscription might occasionally interfere with SQL Managed Instance management and maintenance operations. Take special care when you use resource locks.
- Resolvable public DNS records: If the virtual network is configured to use a custom DNS server, the DNS server must be able to resolve public DNS records. Using features like Microsoft Entra authentication might require resolving more fully qualified domain names (FQDNs). For more information, see Resolving private DNS names in Azure SQL Managed Instance.
- Required DNS records: SQL managed instances depend on having certain domain names resolve correctly. Those domain names must not be overridden in their virtual networks, either via Azure DNS private zones or by a custom DNS server. Otherwise, SQL managed instances will fail to deploy or might become unavailable. The following domains must not be overridden:
chinacloudapi.cn,database.chinacloudapi.cn,core.chinacloudapi.cn,blob.core.chinacloudapi.cn,table.core.chinacloudapi.cn,management.core.chinacloudapi.cn,monitoring.core.chinacloudapi.cn,queue.core.chinacloudapi.cn,graph.chinacloudapi.cn,login.partner.microsoftonline.cn,login.chinacloudapi.cn,servicebus.chinacloudapi.cn, andvault.azure.cn. You can still create private endpoints inside a SQL managed instance's virtual network, even to resources in the aforementioned domains. Private endpoints use a DNS mechanism that doesn't require that a local DNS server become authoritative for an entire zone. - AzurePlatformDNS tag: Using the AzurePlatformDNS service tag to block platform DNS resolution might render SQL Managed Instance unavailable. Although SQL Managed Instance supports customer-defined DNS for DNS resolution inside the engine, there's a dependency on Azure DNS for platform operations.
Service-aided subnet configuration
To improve service security, manageability, and availability, SQL Managed Instance uses service-aided subnet configuration and network intent policy on the Azure virtual network infrastructure to configure the network, associated components, and route table to ensure that minimum requirements for SQL Managed Instance are met.
Automatically configured network security and route table rules are visible to the customer and annotated with one of these prefixes:
Microsoft.Sql-managedInstances_UseOnly_mi-for mandatory rules and routesMicrosoft.Sql-managedInstances_UseOnly_mi-optional-for optional rules and routes
For additional details, review Service-aided subnet configuration.
For more information about the connectivity architecture and management traffic, see High-level connectivity architecture.
Networking constraints
The following constraints on virtual network features and traffic are in effect:
- Private subnets: Deploying SQL managed instances in private subnets (where default outbound access is disabled) is currently not supported.
- VNet encryption: Deploying and operating SQL managed instances in virtual networks where Azure Virtual Network encryption is enabled is currently not supported.
- Database mail to external SMTP relays on port 25: Sending database mail via port 25 to external email services is only available to certain subscription types in Microsoft Azure. Instances on other subscription types should use a different port (for example, 587) to contact external SMTP relays. Otherwise, instances might fail to deliver database mail. For more information, see Troubleshoot outbound SMTP connectivity problems in Azure.
- Microsoft peering: Enabling Microsoft peering on ExpressRoute circuits that are peered directly or transitively with a virtual network in which SQL Managed Instance resides affects traffic flow between SQL Managed Instance components inside the virtual network and services it depends on. Availability issues result. SQL Managed Instance deployments to a virtual network that already has Microsoft peering enabled are expected to fail.
- Global virtual network peering: Virtual network peering connectivity across Azure regions doesn't work for SQL managed instances that are placed in subnets that were created before September 9, 2020.
- Virtual network peering - configuration: When establishing virtual network peering between virtual networks that contain subnets with SQL managed instances, such subnets must use different route tables and network security groups (NSG). Reusing the route table and NSG in two or more subnets participating in virtual network peering will cause connectivity issues in all subnets using those route tables or NSG, and cause SQL Managed Instance's management operations to fail.
- NAT gateway: Using Azure Virtual Network NAT to control outbound connectivity with a specific public IP address is currently not supported.
- IPv6 for Azure Virtual Network: Deploying SQL Managed Instance to dual stack IPv4/IPv6 virtual networks is expected to fail. Associating a network security group or a route table with user-defined routes (UDRs) that contains IPv6 address prefixes to a SQL Managed Instance subnet renders SQL Managed Instance unavailable. Also, adding IPv6 address prefixes to a network security group or UDR that's already associated with a SQL managed instance subnet renders SQL Managed Instance unavailable. SQL Managed Instance deployments to a subnet with a network security group and UDR that already have IPv6 prefixes are expected to fail.
- TLS 1.2 is enforced on outbound connections: Beginning in January 2020, Microsoft enforces TLS 1.2 for intra-service traffic in all Azure services. For SQL Managed Instance, this resulted in TLS 1.2 being enforced on outbound connections that are used for replication and on linked server connections to SQL Server. If you use a version of SQL Server that's earlier than 2016 with SQL Managed Instance, make sure that you apply TLS 1.2-specific updates.
- Internal fallback to Azure DNS: SQL managed instances depend on functioning DNS resolution in their virtual networks. If a SQL managed instance's virtual network is configured to use custom DNS servers and a DNS request issued to custom DNS servers fails to complete within a certain interval (1-2 seconds), SQL managed instance will repeat the request against Azure DNS in that virtual network.
Related content
- For an overview, see What is Azure SQL Managed Instance?.
- To learn more, see:
- Virtual cluster architecture.
- Service-aided subnet configuration.
- Set up a new Azure virtual network or an existing Azure virtual network where you can deploy SQL Managed Instance.
- Calculate the size of the subnet where you want to deploy SQL Managed Instance.
- Learn how to create a SQL managed instance:
- From the Azure portal.
- By using PowerShell.
- By using an Azure Resource Manager template.
- By using an Azure Resource Manager template with a jumpbox and SQL Server Management Studio.