概述
Azure 应用程序网关支持对流量进行端到端加密。 该应用程序网关将 TLS/SSL 连接的一端连接到应用程序网关。 网关随后将路由规则应用于流量、重新加密数据包,并根据定义的路由规则将数据包转发到相应的后端服务器。 来自 Web 服务器的任何响应都会经历相同的过程返回最终用户。
应用程序网关支持定义自定义 TLS 选项。 除了支持定义要使用的密码套件和优先级顺序外,它还支持禁用以下协议版本:TLSv1.0、TLSv1.1 和 TLSv1.2。 若要详细了解可配置的 TLS 选项,请参阅 TLS 策略概述。
注意
SSL 2.0 和 SSL 3.0 默认处于禁用状态且无法启用。 这些版本被视为不安全的版本,不能用于应用程序网关。
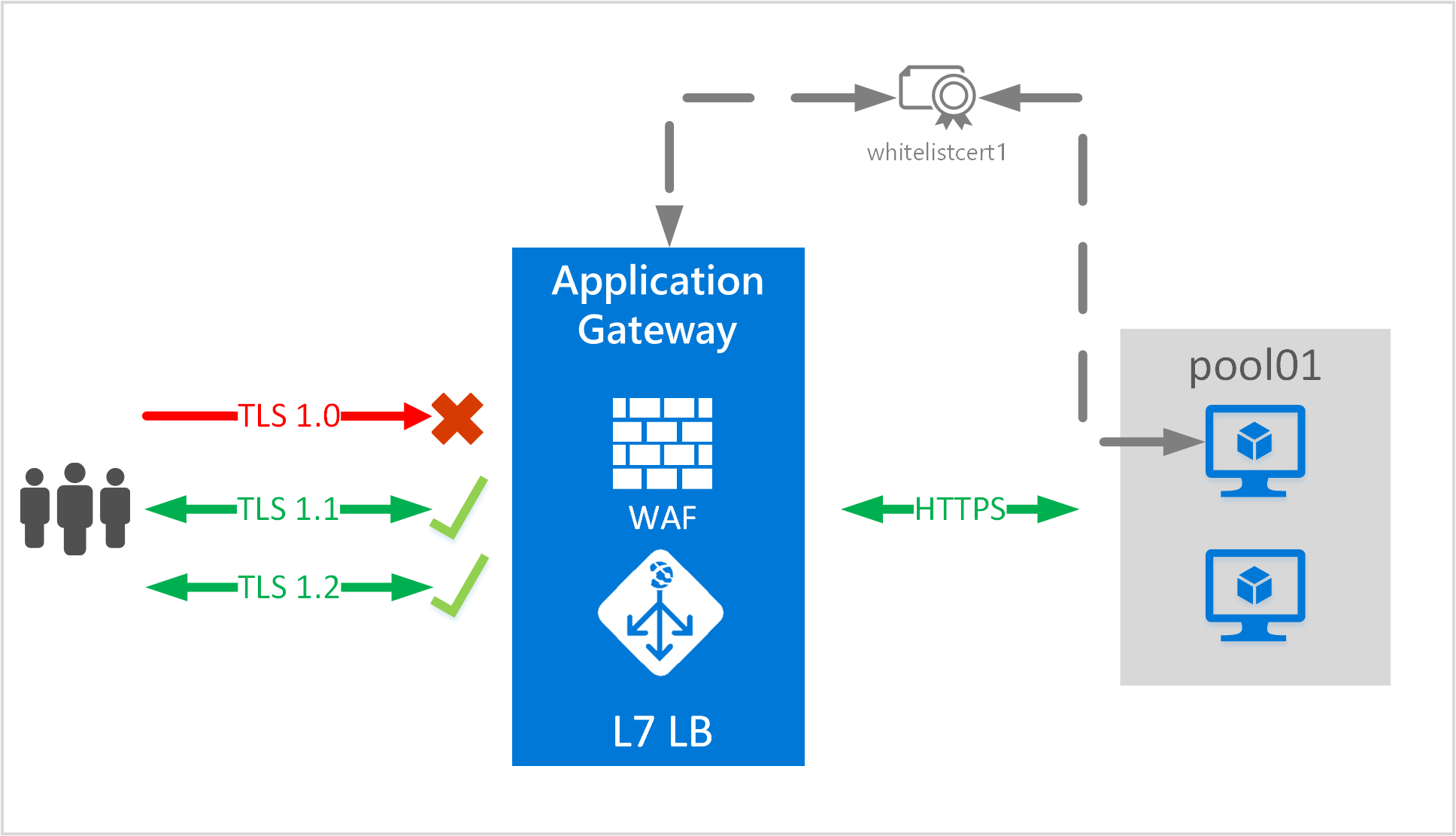
方案
在此方案中,你将了解如何通过 PowerShell 使用端到端 TLS 创建应用程序网关。
此方案将:
- 创建名为 appgw-rg 的资源组。
- 创建名为 appgwvnet,地址空间为 10.0.0.0/16 的虚拟网络 。
- 创建名为“appgwsubnet”和“appsubnet”的两个子网 。
- 创建支持端到端 TLS 加密且限制 TLS 协议版本和密码套件的小型应用程序网关。
准备阶段
注意
建议使用 Azure Az PowerShell 模块与 Azure 交互。 若要开始,请参阅安装 Azure PowerShell。 若要了解如何迁移到 Az PowerShell 模块,请参阅 将 Azure PowerShell 从 AzureRM 迁移到 Az。
若要为应用程序网关配置端到端 TLS,需要网关证书和后端服务器证书。 网关证书用来根据 TLS 协议规范派生对称密钥。 然后,对称密钥用来加密和解密发送到网关的流量。 网关证书需要采用个人信息交换 (PFX) 格式。 此文件格式适用于导出私钥,后者是应用程序网关对流量进行加解密所必需的。
对于端到端 TLS 加密,应用程序网关必须显式允许后端。 将后端服务器的公用证书上传到应用程序网关。 添加证书后,可确保应用程序网关仅与已知后端实例通信。 从而进一步保护端到端通信。
配置过程在以下部分中介绍。
创建资源组
本部分指导创建资源组,其中包含应用程序网关。
登录 Azure 帐户。
Connect-AzAccount -Environment AzureChinaCloud选择要用于此方案的订阅。
Select-Azsubscription -SubscriptionName "<Subscription name>"创建资源组。 (若要使用现有资源组,请跳过此步骤。)
New-AzResourceGroup -Name appgw-rg -Location "China North 2"
为应用程序网关创建虚拟网络和子网
以下示例创建一个虚拟网络和两个子网。 一个子网用于托管应用程序网关。 另一个子网用于可托管 Web 应用程序的后端。
分配要用于应用程序网关的子网地址范围。
$gwSubnet = New-AzVirtualNetworkSubnetConfig -Name 'appgwsubnet' -AddressPrefix 10.0.0.0/24注意
应适当调整为应用程序网关配置的子网的大小。 最多可以为 10 个实例配置应用程序网关。 每个实例从子网获取 1 个 IP 地址。 子网太小可能会对应用程序网关的向外缩放造成负面影响。
分配要用于后端地址池的地址范围。
$nicSubnet = New-AzVirtualNetworkSubnetConfig -Name 'appsubnet' -AddressPrefix 10.0.2.0/24创建具有上述步骤中定义的子网的虚拟网络。
$vnet = New-AzvirtualNetwork -Name 'appgwvnet' -ResourceGroupName appgw-rg -Location "China North 2" -AddressPrefix 10.0.0.0/16 -Subnet $gwSubnet, $nicSubnet检索要用于后续步骤的虚拟网络资源和子网资源。
$vnet = Get-AzvirtualNetwork -Name 'appgwvnet' -ResourceGroupName appgw-rg $gwSubnet = Get-AzVirtualNetworkSubnetConfig -Name 'appgwsubnet' -VirtualNetwork $vnet $nicSubnet = Get-AzVirtualNetworkSubnetConfig -Name 'appsubnet' -VirtualNetwork $vnet
创建前端配置的公共 IP 地址
创建要用于应用程序网关的公共 IP 资源。 此公共 IP 地址会用于后续步骤之一。
$publicip = New-AzPublicIpAddress -ResourceGroupName appgw-rg -Name 'publicIP01' -Location "China North 2" -AllocationMethod Dynamic
重要
应用程序网关不支持使用通过定义的域标签创建的公共 IP 地址。 仅支持具有动态创建的域标签的公共 IP 地址。 如果需要应用程序网关具有友好 DNS 名称,建议使用 CNAME 记录作为别名。
创建应用程序网关配置对象
在创建应用程序网关之前设置所有配置项。 以下步骤会创建应用程序网关资源所需的配置项目。
创建应用程序网关 IP 配置。 此设置配置应用程序网关要使用的子网。 当应用程序网关启动时,它会先从配置的子网获取 IP 地址,再将网络流量路由到后端 IP 池中的 IP 地址。 请记住,每个实例需要一个 IP 地址。
$gipconfig = New-AzApplicationGatewayIPConfiguration -Name 'gwconfig' -Subnet $gwSubnet创建前端 IP 配置。 此设置将专用或公共 IP 地址映射到应用程序网关的前端。 以下步骤将上一步骤中的公共 IP 地址与前端 IP 配置关联。
$fipconfig = New-AzApplicationGatewayFrontendIPConfig -Name 'fip01' -PublicIPAddress $publicip使用后端 Web 服务器的 IP 地址配置后端 IP 地址池。 这些 IP 地址将接收来自前端 IP 终结点的网络流量。 使用自己的应用程序 IP 地址端点替换样本中的 IP 地址。
$pool = New-AzApplicationGatewayBackendAddressPool -Name 'pool01' -BackendIPAddresses 203.0.113.1, 203.0.113.2, 203.0.113.3注意
完全限定的域名 (FQDN) 也是可用于替换后端服务器 IP 地址的有效值。 可通过 -BackendFqdns 开关启用它。
配置公共 IP 终结点的前端 IP 端口。 此端口是最终用户连接到的端口。
$fp = New-AzApplicationGatewayFrontendPort -Name 'port01' -Port 443配置应用程序网关的证书。 此证书用于加密和解密应用程序网关上的流量。
$passwd = ConvertTo-SecureString <certificate file password> -AsPlainText -Force $cert = New-AzApplicationGatewaySSLCertificate -Name cert01 -CertificateFile <full path to .pfx file> -Password $passwd注意
此示例配置用于 TLS 连接的证书。 该证书需要采用 .pfx 格式。
创建应用程序网关的 HTTP 侦听器。 分配要使用的前端 IP 配置、端口和 TLS/SSL 证书。
$listener = New-AzApplicationGatewayHttpListener -Name listener01 -Protocol Https -FrontendIPConfiguration $fipconfig -FrontendPort $fp -SSLCertificate $cert上传要在已启用 TLS 的后端池资源上使用的证书。
注意
默认探测从后端的 IP 地址上的默认 TLS 绑定获取公钥,并将其收到的公钥值与你在此处提供的公钥值进行比较。
如果你是在后端使用主机头和服务器名称指示 (SNI),则检索到的公钥可能不是流量预期流向的站点。 如有疑问,请访问后端服务器上的 https://127.0.0.1/,确认用于默认 TLS 绑定的证书。 本部分使用该请求中的公钥。 如果对 HTTPS 绑定使用主机头和 SNI,但未从发往后端服务器上的 https://127.0.0.1/ 的手动浏览器请求收到响应和证书,则必须在该服务器上设置默认 TLS 绑定。 如果不这样做,探测会失败,后端不会被系统允许。
有关应用程序网关中 SNI 的详细信息,请参阅应用程序网关的 TLS 终止和端到端 TLS 概述。
$authcert = New-AzApplicationGatewayAuthenticationCertificate -Name 'allowlistcert1' -CertificateFile C:\cert.cer注意
上一步骤中提供的证书应该是后端中存在的 .pfx 证书的公钥。 以声明、证据和推理 (CER) 格式导出后端服务器上安装的证书(不是根证书),将其用在此步骤中。 此步骤会使用应用程序网关来允许后端。
如果使用的是应用程序网关 v2 SKU,则创建受信任的根证书而不是身份验证证书。 有关详细信息,请参阅应用程序网关的端到端 TLS 概述:
$trustedRootCert01 = New-AzApplicationGatewayTrustedRootCertificate -Name "test1" -CertificateFile <path to root cert file>配置应用程序网关后端 HTTP 设置。 将上述步骤中上传的证书分配给 HTTP 设置。
$poolSetting = New-AzApplicationGatewayBackendHttpSettings -Name 'setting01' -Port 443 -Protocol Https -CookieBasedAffinity Enabled -AuthenticationCertificates $authcert对于应用程序网关 v2 SKU,请使用以下命令:
$poolSetting01 = New-AzApplicationGatewayBackendHttpSettings -Name “setting01” -Port 443 -Protocol Https -CookieBasedAffinity Disabled -TrustedRootCertificate $trustedRootCert01 -HostName "test1"创建配置负载均衡器行为的负载均衡器路由规则。 在此示例中,创建基本轮循机制规则。
$rule = New-AzApplicationGatewayRequestRoutingRule -Name 'rule01' -RuleType basic -BackendHttpSettings $poolSetting -HttpListener $listener -BackendAddressPool $pool配置应用程序网关的实例大小。 可以在 Standard_Small、Standard_Medium 和 Standard_Large 之间选择大小。 对于容量,可用值为 1 到 10 。
$sku = New-AzApplicationGatewaySku -Name Standard_Small -Tier Standard -Capacity 2注意
进行测试时,可以选择 1 作为实例计数。 必须知道的是,2 以下的实例计数不受 SLA 支持,因此不建议使用。 小型网关用于开发/测试,不用于生产。
配置要在应用程序网关上使用的 TLS 策略。 应用程序网关支持设置 TLS 协议最低版本的功能。
以下值是可以定义的协议版本的列表:
- TLSV1_0
- TLSV1_1
- TLSV1_2
下面的示例将最低协议版本设置为 TLSv1_2 并仅启用 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256、TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 和 TLS_RSA_WITH_AES_128_GCM_SHA256。
$SSLPolicy = New-AzApplicationGatewaySSLPolicy -MinProtocolVersion TLSv1_2 -CipherSuite "TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256", "TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384", "TLS_RSA_WITH_AES_128_GCM_SHA256" -PolicyType Custom
创建应用程序网关
使用上述所有步骤创建应用程序网关。 网关创建过程需要花费较长时间。
对于 V1 SKU,请使用以下命令
$appgw = New-AzApplicationGateway -Name appgateway -SSLCertificates $cert -ResourceGroupName "appgw-rg" -Location "China North 2" -BackendAddressPools $pool -BackendHttpSettingsCollection $poolSetting -FrontendIpConfigurations $fipconfig -GatewayIpConfigurations $gipconfig -FrontendPorts $fp -HttpListeners $listener -RequestRoutingRules $rule -Sku $sku -SSLPolicy $SSLPolicy -AuthenticationCertificates $authcert -Verbose
对于 V2 SKU,请使用以下命令
$appgw = New-AzApplicationGateway -Name appgateway -SSLCertificates $cert -ResourceGroupName "appgw-rg" -Location "China North 2" -BackendAddressPools $pool -BackendHttpSettingsCollection $poolSetting01 -FrontendIpConfigurations $fipconfig -GatewayIpConfigurations $gipconfig -FrontendPorts $fp -HttpListeners $listener -RequestRoutingRules $rule -Sku $sku -SSLPolicy $SSLPolicy -TrustedRootCertificate $trustedRootCert01 -Verbose
如果后端证书已过期,请应用新证书
如果后端证书已过期,请使用此过程来应用新证书。
检索要更新的应用程序网关。
$gw = Get-AzApplicationGateway -Name AdatumAppGateway -ResourceGroupName AdatumAppGatewayRG从 .cer 文件中添加新的证书资源,该文件包含证书的公钥,也可以是添加到侦听器中用于在应用程序网关上终止 TLS 的同一证书。
Add-AzApplicationGatewayAuthenticationCertificate -ApplicationGateway $gw -Name 'NewCert' -CertificateFile "appgw_NewCert.cer"将新的身份验证证书对象导入变量 (TypeName:Microsoft.Azure.Commands.Network.Models.PSApplicationGatewayAuthenticationCertificate)。
$AuthCert = Get-AzApplicationGatewayAuthenticationCertificate -ApplicationGateway $gw -Name NewCert将新证书分配到 BackendHttp 设置中,并使用 $AuthCert 变量引用它。 (指定要更改的 HTTP 设置名称。)
$out= Set-AzApplicationGatewayBackendHttpSetting -ApplicationGateway $gw -Name "HTTP1" -Port 443 -Protocol "Https" -CookieBasedAffinity Disabled -AuthenticationCertificates $Authcert
- 将更改提交到应用程序网关,并将包含的新配置传递到 $out 变量中。
Set-AzApplicationGateway -ApplicationGateway $gw
从 HTTP 设置中删除未使用的过期证书
使用此过程从 HTTP 设置中删除未使用的过期证书。
检索要更新的应用程序网关。
$gw = Get-AzApplicationGateway -Name AdatumAppGateway -ResourceGroupName AdatumAppGatewayRG列出要删除的身份验证证书的名称。
Get-AzApplicationGatewayAuthenticationCertificate -ApplicationGateway $gw | select name从应用程序网关中删除身份验证证书。
$gw=Remove-AzApplicationGatewayAuthenticationCertificate -ApplicationGateway $gw -Name ExpiredCert提交更改。
Set-AzApplicationGateway -ApplicationGateway $gw
限制现有应用程序网关上的 TLS 协议版本
上述步骤指导你创建具有端到端 TLS 并禁用特定 TLS 协议版本的应用程序。 以下示例禁用现有应用程序网关上的特定 TLS 策略。
检索要更新的应用程序网关。
$gw = Get-AzApplicationGateway -Name AdatumAppGateway -ResourceGroupName AdatumAppGatewayRG定义 TLS 策略。 在以下示例中,TLSv1.0 和 TLSv1.1 处于禁用状态,并且仅允许使用密码套件 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256、TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 和 TLS_RSA_WITH_AES_128_GCM_SHA256。
Set-AzApplicationGatewaySSLPolicy -MinProtocolVersion TLSv1_2 -PolicyType Custom -CipherSuite "TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256", "TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384", "TLS_RSA_WITH_AES_128_GCM_SHA256" -ApplicationGateway $gw最后,更新网关。 最后一步是耗时较长的任务。 完成时,应用程序网关上便配置了端到端 TLS。
$gw | Set-AzApplicationGateway
获取应用程序网关 DNS 名称
创建网关后,下一步是配置前端以进行通信。 使用公共 IP 时,应用程序网关需要动态分配的 DNS 名称,这会造成不便。 若要确保最终用户能够访问应用程序网关,可以使用 CNAME 记录指向应用程序网关的公共终结点。 有关详细信息,请参阅在 Azure 中配置自定义域名。
若要配置别名,可使用附加到应用程序网关的 PublicIPAddress 元素检索应用程序网关及其关联的 IP/DNS 名称的详细信息。 使用应用程序网关的 DNS 名称来创建 CNAME 记录,使两个 Web 应用程序都指向此 DNS 名称。 不建议使用 A 记录,因为重新启动应用程序网关后 VIP 可能会变化。
Get-AzPublicIpAddress -ResourceGroupName appgw-RG -Name publicIP01
Name : publicIP01
ResourceGroupName : appgw-RG
Location : chinanorth2
Id : /subscriptions/<subscription_id>/resourceGroups/appgw-RG/providers/Microsoft.Network/publicIPAddresses/publicIP01
Etag : W/"00000d5b-54ed-4907-bae8-99bd5766d0e5"
ResourceGuid : 00000000-0000-0000-0000-000000000000
ProvisioningState : Succeeded
Tags :
PublicIpAllocationMethod : Dynamic
IpAddress : xx.xx.xxx.xx
PublicIpAddressVersion : IPv4
IdleTimeoutInMinutes : 4
IpConfiguration : {
"Id": "/subscriptions/<subscription_id>/resourceGroups/appgw-RG/providers/Microsoft.Network/applicationGateways/appgwtest/frontendIP
Configurations/frontend1"
}
DnsSettings : {
"Fqdn": "00000000-0000-xxxx-xxxx-xxxxxxxxxxxx.chinacloudapp.cn"
}
后续步骤
请参阅 Web 应用程序防火墙概述,详细了解如何通过应用程序网关的 Web 应用程序防火墙强化 Web 应用程序的安全性。