本文介绍用于控制与 Azure SQL 数据库的服务器的连接的设置。
- 有关定向网络流量和连接策略的各种组件的详细信息,请参阅连接体系结构。
- 本文不适用于 Azure SQL 托管实例,请参阅将应用程序连接到 Azure SQL 托管实例。
- 本文不适用于 Azure Synapse Analytics。
- 有关控制与 Azure Synapse Analytics 中专用 SQL 池的连接的设置,请参阅 Azure Synapse Analytics 连接设置。
- 有关 Azure Synapse Analytics 池的连接字符串,请参阅连接到 Synapse SQL。
- 有关如何使用工作区为 Azure Synapse Analytics 配置 IP 防火墙规则的指南,请参阅 Azure Synapse Analytics IP 防火墙规则。
网络和连接
可以在逻辑服务器中更改这些设置。
更改公共网络访问
可以通过 Azure 门户、Azure PowerShell 和 Azure CLI 更改 Azure SQL 数据库的公用网络访问。
注意
这些设置在应用后会立即生效。 如果客户不满足每个设置的要求,则可能会遇到连接丢失的情况。
若要为托管数据库的逻辑服务器启用公用网络访问,请执行以下操作:
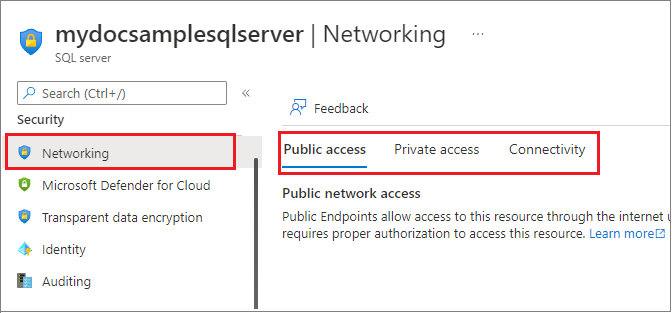
- 转到 Azure 门户,并转到 Azure 中的逻辑服务器。
- 在“安全性”部分下,选择“网络”页。
- 选择“公用访问”选项卡,然后将“公用网络访问”设置为“选择网络”。
在此页中,可以添加虚拟网络规则,并为公共终结点配置防火墙规则。
选择“专用访问”选项卡以配置专用终结点。
拒绝公用网络访问
“公用网络访问”默认设置为“禁用”。 客户可以选择使用公共终结点(使用基于 IP 的服务器级防火墙规则或虚拟网络防火墙规则)或专用终结点(使用 Azure 专用链接)连接到数据库,如网络访问概述中所述。
当将“公用网络访问”设置为“禁用”时,将只允许从专用终结点进行连接。 将拒绝从公共终结点进行的所有连接,并显示如下错误消息:
Error 47073
An instance-specific error occurred while establishing a connection to SQL Server.
The public network interface on this server is not accessible.
To connect to this server, use the Private Endpoint from inside your virtual network.
当将“公用网络访问”设置为“禁用”时,将拒绝添加、删除或编辑任何防火墙规则的所有尝试,并显示如下错误消息:
Error 42101
Unable to create or modify firewall rules when public network interface for the server is disabled.
To manage server or database level firewall rules, please enable the public network interface.
确保将 公用网络访问 设置为 所选网络,以便能够添加、删除或编辑 Azure SQL 数据库的任何防火墙规则。
最低 TLS 版本
借助最低传输层安全性 (TLS) 版本设置,客户可以选择其 SQL 数据库使用哪个 TLS 版本。 TLS 是用于通过网络保护客户端服务器通信的加密协议。 这可确保敏感信息(如身份验证凭据和数据库查询)可以安全地拦截和篡改。 可以使用 Azure 门户、Azure PowerShell 和 Azure CLI 更改最低 TLS 版本。
设置最低 TLS 版本可确保基线级别的符合性,并保证对较新的 TLS 协议的支持。 例如,选择 TLS 1.2 意味着仅接受 TLS 1.2 或 TLS 1.3 的连接,同时拒绝使用 TLS 1.1 或更低版本的连接。
目前,Azure SQL 数据库支持的最低 TLS 版本是 TLS 1.2。 此版本解决了早期版本中发现的漏洞。 建议在测试后将最低 TLS 版本设置为 TLS 1.2,以确认应用程序兼容。
注意
TLS 1.0 和 1.1 已停用 ,不再可用。
配置最低 TLS 版本
可使用 Azure 门户、Azure PowerShell 或 Azure CLI 配置客户端连接的最低 TLS 版本。
注意
- 最低 TLS 版本的默认值是允许所有版本的 TLS 1.2 及更高版本。 确定使用某个版本的 TLS 后,就不能恢复为默认值。
- 强制实施最低 TLS 1.3 可能会导致来自不支持 TLS 1.3 的客户端的连接出现问题,因为并非所有驱动程序和操作系统都支持 TLS 1.3。
如果客户使用的应用程序依赖于更低的 TLS 版本,我们建议根据应用程序的要求设置最低 TLS 版本。 如果应用程序要求未知或工作负载依赖于不再维护的旧驱动程序,建议不要设置任何最低 TLS 版本。
有关详细信息,请参阅 SQL 数据库连接的 TLS 注意事项。
设置最低 TLS 版本后,如果客户所使用的 TLS 版本低于服务器的最低 TLS 版本,则将无法进行身份认证,并显示以下错误:
Error 47072
Login failed with invalid TLS version
注意
在应用层强制实施最低 TLS 版本。 当直接针对 SQL 数据库终结点运行时,尝试在协议层确定 TLS 支持的工具可能会返回 TLS 版本以及所需的最低版本。
- 转到 Azure 门户,并转到 Azure 中的逻辑服务器。
- 在“安全性”部分下,选择“网络”页。
- 选择“连接”选项卡。选择与服务器关联的所有数据库所需的“最低 TLS 版本”,然后选择“保存”。
识别客户端连接
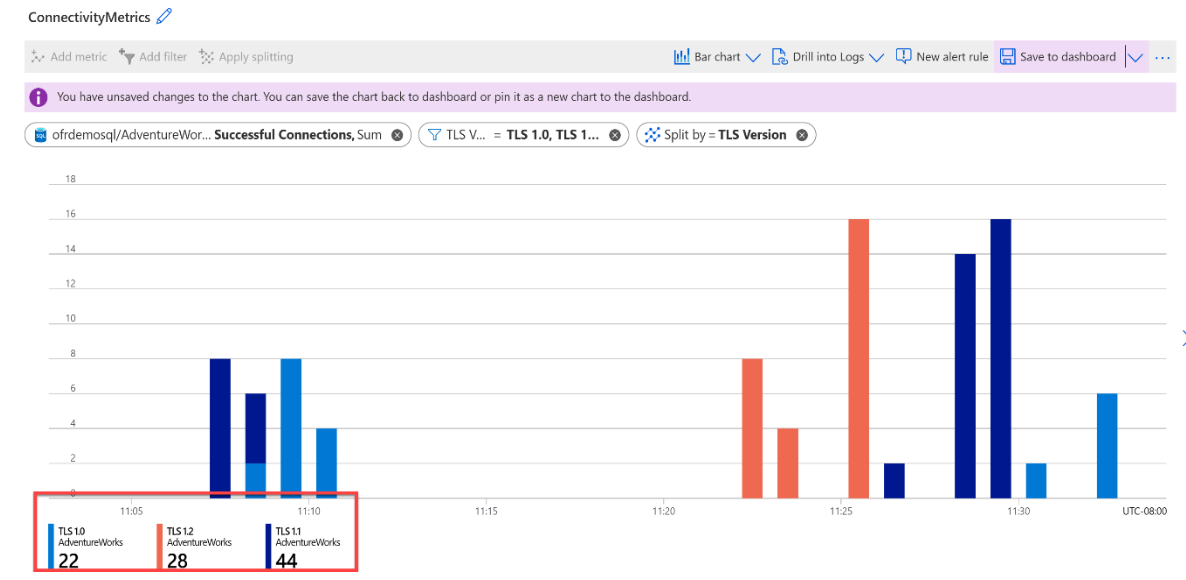
可以使用 Azure 门户和 SQL 审核日志来识别使用 TLS 1.0 和 1.1 进行连接的客户端。
在 Azure 门户中,转到数据库资源的“监视”下的“指标”,然后按“成功连接”以及 TLS 版本 = 1.0 和 1.1 进行筛选:
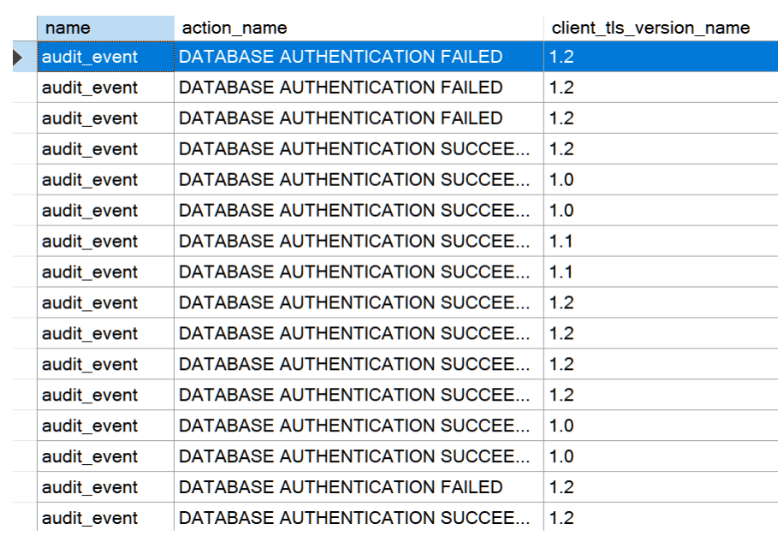
还可以直接在数据库中查询 sys.fn_get_audit_file 以查看审核文件中的 client_tls_version_name,查找名为 audit_event的事件。
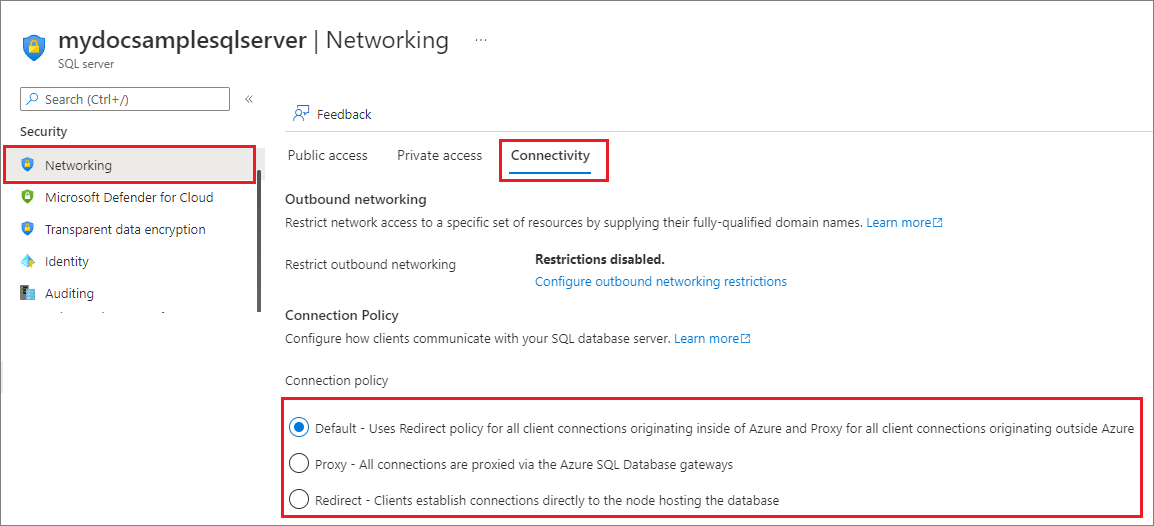
更改连接策略
连接策略确定客户连接的方式。 我们强烈建议使用 Redirect 连接策略而不要使用 Proxy 连接策略,以最大程度地降低延迟和提高吞吐量。
可以使用 Azure 门户、Azure PowerShell 和 Azure CLI 更改连接策略。
可以使用 Azure 门户更改逻辑服务器的连接策略。
- 转到 Azure 门户。 转到“Azure 中的逻辑服务器”。
- 在“安全性”部分下,选择“网络”页。
- 选择“连接”选项卡。选择所需的连接策略,然后选择“保存”。
即将推出的 TLS 1.0 和 1.1 停用更改常见问题解答
Azure 已宣布对旧 TLS 版本(TLS 1.0 和 1.1)的支持将于 2025 年 8 月 31 日结束。 有关详细信息,请参阅 TLS 1.0 和 1.1 弃用。
从 2024 年 11 月开始,将无法再为低于 TLS 1.2 的 Azure SQL 数据库和 Azure SQL 托管实例客户端连接设置最低 TLS 版本。
为什么 TLS 1.0 和 1.1 即将停用?
TLS 版本 1.0 和 1.1 已过时,不再满足现代安全标准。 他们即将停用:
- 减少对已知漏洞的暴露。
- 符合行业最佳做法和合规性要求。
- 确保客户端使用更强大的加密协议,例如 TLS 1.2 或 TLS 1.3。
如果在 2025 年 8 月 31 日之后使用 TLS 1.0 和 1.1,会发生什么情况?
2025 年 8 月 31 日之后,将不再支持 TLS 1.0 和 1.1,并且使用 TLS 1.0 和 1.1 的连接可能会失败。 在截止时间之前过渡到最低 TLS 1.2 或更高版本至关重要。
如何检查 SQL 数据库、SQL 托管实例、Cosmos DB 或 MySQL 实例是否正在使用 TLS 1.0/1.1?
若要识别使用 TLS 1.0 和 1.1 连接到 Azure SQL 数据库的客户端,必须启用 SQL 审核日志 。 启用审核后,可以查看客户端连接。
若要识别使用 TLS 1.0 和 1.1 连接到 Azure SQL 托管实例的客户端,必须启用 审核 。 启用审核后,可以使用 Azure 存储、事件中心或 Azure Monitor 日志的 审核 日志来查看客户端连接。
若要验证 Azure Cosmos DB 的最低 TLS 版本,请使用 Azure CLI 或 Azure PowerShell 获取属性的
minimalTlsVersion当前值 。若要验证为 Azure Database for MySQL 服务器配置的最低 TLS 版本,请使用 MySQL 命令行接口检查服务器参数的值
tls_version,以了解配置了哪些协议。
如果我已配置 TLS 1.2,为什么我的服务已标记?
由于以下原因,服务可能未正确标记:
- 旧客户端间歇性回退到旧版 TLS 版本。
- 未强制实施 TLS 1.2 的客户端库或连接字符串配置错误。
- 检测逻辑中的遥测延迟或误报。
如果我收到错误停用通知,该怎么办?
如果服务器或数据库已配置为最低 TLS 1.2,或未配置最低 TLS(SQL 数据库和映射到minimalTLSVersion的 SQL 托管实例0中的默认设置),并且使用 1.2 进行连接,则无需执行任何作。
如果应用程序或客户端库不支持 TLS 1.2,会发生什么情况?
禁用 TLS 1.0/1.1 后,连接将失败。 必须将客户端库、驱动程序或框架升级到支持 TLS 1.2 的版本。
如果我的服务器未配置最低 TLS 版本,该怎么办?
未配置最低 TLS 版本且使用 TLS 1.0/1.1 进行连接的服务器应升级到最低 TLS 版本 1.2。 对于未配置最低 TLS 版本且使用 1.2 进行连接的服务器,无需执行任何作。 对于未配置最低 TLS 版本和使用加密连接的服务器,无需执行任何作。
如何收到有关我的资源的 TLS 停用的通知?
8 月,电子邮件提醒将继续停用 TLS 1.0 和 1.1。
如果需要有关验证或更新 TLS 设置的帮助,我可以联系谁?
如果需要有关验证或更新 TLS 设置的帮助,请使用 Azure 门户开具支持票证。