适用于: Azure SQL 数据库
Azure SQL 数据库 Azure SQL 托管实例
Azure SQL 托管实例 Azure Synapse Analytics(仅限专用 SQL 池)
Azure Synapse Analytics(仅限专用 SQL 池)
本文介绍使用 Azure Key Vault 中的 TDE 保护器对服务器进行的密钥轮换。 为服务器轮换逻辑 TDE 保护器意味着切换到用于保护服务器上数据库的新非对称密钥。 密钥轮换是一种联机操作,应该只需数秒即可完成,因为此操作只在解密数据库的数据加密密钥后重新将其加密,而不是对整个数据库进行操作。
本文讨论了在服务器上轮换 TDE 保护器的自动方法和手动方法。
轮换 TDE 保护器时的重要注意事项
- 更改/轮换 TDE 保护器后,数据库的旧备份(包括已备份的日志文件)不会更新为使用最新的 TDE 保护器。 若要从 Azure Key Vault 还原使用 TDE 保护程序加密的备份,请确保密钥材料可用于目标服务器。 因此,我们建议在 Azure Key Vault 中保留 TDE 保护程序的所有旧版本,以便可以还原数据库备份。
- 即使从客户管理的密钥(CMK)切换到服务管理的密钥,也会保留 Azure Key Vault 中以前使用的所有密钥。 这可确保使用存储在 Azure Key Vault 中的 TDE 保护程序还原数据库备份,包括备份日志文件。
- 除了旧备份以外,事务日志文件可能还需要访问较旧的 TDE 保护器。 若要确定是否有任何剩余的日志仍需要旧密钥,请在执行密钥轮换后,使用 (DMV) sys.dm_db_log_info 动态管理视图 (DMV)。 此 DMV 返回有关事务日志的虚拟日志文件 (VLF) 的信息及其 VLF 的加密密钥指纹。
- 旧密钥需要保留在 Azure Key Vault 中,并根据配置在数据库上的备份保留策略所定义的备份保留期可供服务器使用。 这有助于确保仍可使用旧密钥还原服务器上的任何长期保留 (LTR) 备份。
注意
需要在密钥轮换之前先恢复 Azure Synapse Analytics 中已暂停的专用 SQL 池。
本文适用于 Azure SQL 数据库、Azure SQL 托管实例和 Azure Synapse Analytics 专用 SQL 池(以前称为 SQL DW)。 有关 Synapse 工作区内专用 SQL 池的透明数据加密的文档,请参阅 Azure Synapse Analytics 加密。
先决条件
- 本操作指南假设已使用 Azure Key Vault 中的密钥作为 Azure SQL 数据库或 Azure Synapse Analytics 的 TDE 保护器。 请参阅提供 BYOK 支持的透明数据加密。
- 必须安装并运行 Azure PowerShell。
自动密钥轮换
为服务器或数据库配置 TDE 保护程序时,可以从 Azure 门户或使用以下 PowerShell 或 Azure CLI 命令启用 TDE 保护程序的自动轮换。 启用后,服务器或数据库将持续检查密钥保管库,获取用作 TDE 保护程序的任何新版本的密钥。 如果检测到新版密钥,服务器或数据库上的 TDE 保护程序将在24 小时内自动轮换到最新密钥版本。
服务器、数据库或托管实例中的自动轮换可用于 Azure 密钥保管库中的自动密钥轮换,以启用 TDE 密钥的端到端零触摸轮换。
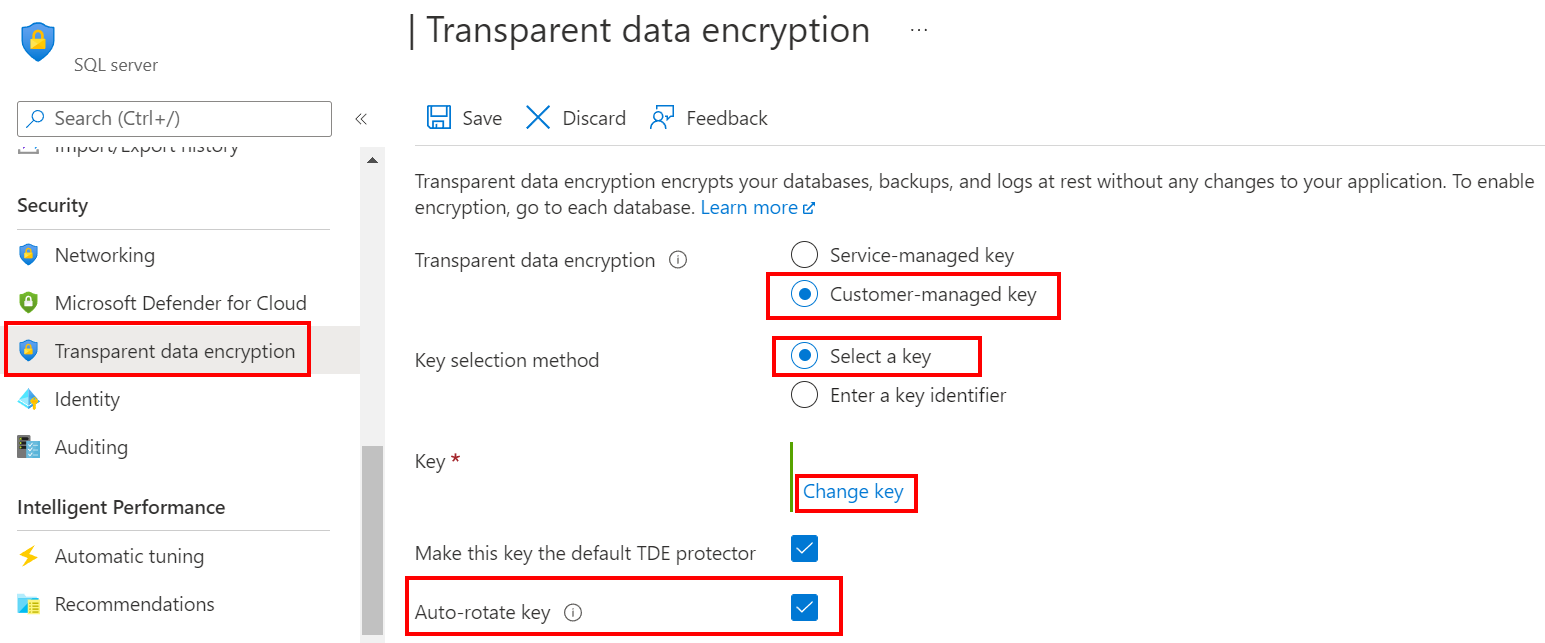
使用 Azure 门户:
- 浏览到现有服务器或托管实例的“透明数据加密”部分。
- 选择“客户管理的密钥”选项,并选择要用作 TDE 保护器的密钥保管库和密钥。
- 选中“自动轮换密钥”复选框。
- 选择“保存”。
有关 Az PowerShell 模块安装说明,请参阅安装 Azure PowerShell。
若要使用 PowerShell 启用 TDE 保护器的自动轮换,请参阅以下脚本。
<keyVaultKeyId>可以从 Azure Key Vault 检索该密钥。
Azure SQL 数据库
使用 Set-AzSqlServerTransparentDataEncryptionProtector 命令。
Set-AzSqlServerTransparentDataEncryptionProtector -Type AzureKeyVault -KeyId <keyVaultKeyId> `
-ServerName <logicalServerName> -ResourceGroup <SQLDatabaseResourceGroupName> `
-AutoRotationEnabled <boolean>
Azure SQL 托管实例
使用 Set-AzSqlInstanceTransparentDataEncryptionProtector 命令。
Set-AzSqlInstanceTransparentDataEncryptionProtector -Type AzureKeyVault -KeyId <keyVaultKeyId> `
-InstanceName <ManagedInstanceName> -ResourceGroup <ManagedInstanceResourceGroupName> `
-AutoRotationEnabled <boolean>
有关安装当前版本的 Azure CLI 的信息,请参阅安装 Azure CLI 一文。
若要使用 Azure CLI 启用 TDE 保护器的自动轮换,请参阅以下脚本。
Azure SQL 数据库
使用 az sql server tde-key set 命令。
az sql server tde-key set --server-key-type AzureKeyVault
--auto-rotation-enabled true
[--kid] <keyVaultKeyId>
[--resource-group] <SQLDatabaseResourceGroupName>
[--server] <logicalServerName>
Azure SQL 托管实例
使用 az sql mi tde-key set 命令。
az sql mi tde-key set --server-key-type AzureKeyVault
--auto-rotation-enabled true
[--kid] <keyVaultKeyId>
[--resource-group] <ManagedInstanceGroupName>
[--managed-instance] <ManagedInstanceName>
数据库级别的自动密钥轮换
也可以在 Azure SQL 数据库的数据库级别启用自动密钥轮换。 如果只想为服务器上的一个数据库或数据库子集启用自动密钥轮换,这非常有用。 有关详细信息,请参阅使用数据库级别客户管理的密钥进行 TDE 标识和密钥管理。
要使用 PowerShell 在数据库级别为 TDE 保护程序启用自动轮换,请参阅以下命令。 使用-EncryptionProtectorAutoRotation参数并设置为$true以启用自动密钥轮换,或者设置为$false以禁用自动密钥轮换。
Set-AzSqlDatabase -ResourceGroupName <resource_group_name> -ServerName <server_name> -DatabaseName <database_name> -EncryptionProtectorAutoRotation:$true
要使用 Azure CLI 在数据库级别为 TDE 保护程序启用自动轮换,请参阅以下命令。 使用--encryption-protector-auto-rotation参数并设置为True以启用自动密钥轮换,或者设置为False以禁用自动密钥轮换。
az sql db update --resource-group <resource_group_name> --server <server_name> --name <database_name> --encryption-protector-auto-rotation True
异地复制配置的自动密钥轮换
在将主服务器设置为将 TDE 与 CMK 配合使用的 Azure SQL 数据库异地复制配置中,还需要将辅助服务器配置为使用 CMK 启用 TDE,并使用与主服务器相同的密钥。
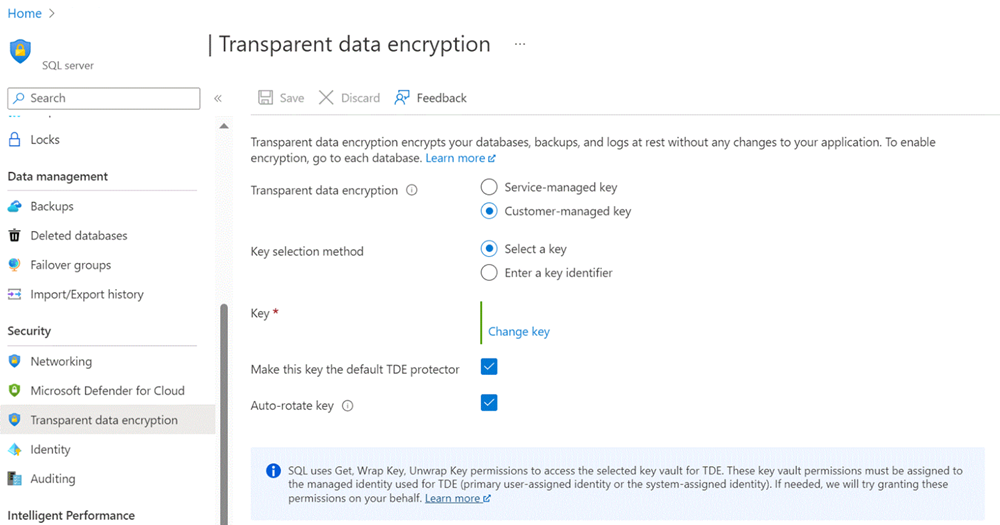
使用 Azure 门户:
浏览到主服务器的“透明数据加密”部分。
选择“客户管理的密钥”选项,并选择要用作 TDE 保护器的密钥保管库和密钥。
选中“自动轮换密钥”复选框。
选择“保存”。
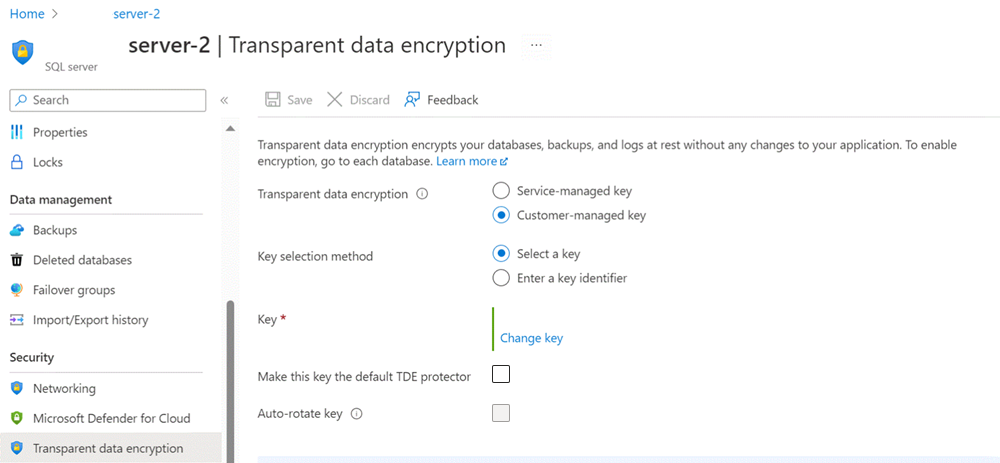
浏览到辅助服务器的“透明数据加密”部分。
选择“客户管理的密钥”选项,并选择要用作 TDE 保护器的密钥保管库和密钥。 使用与主服务器相同的密钥。
取消选中“将此密钥设置为默认的 TDE 保护程序”。
选择“保存”。
当密钥在主服务器上轮换时,它会自动传输到辅助服务器。
注意
如果主服务器上的密钥保管库密钥也用作辅助服务器上的默认 TDE 保护程序,请确保这两个服务器均启用“自动轮换密钥”, 否则可能导致自动轮换工作流发生错误,并且无法进一步手动轮换密钥。
<keyVaultKeyId>可以从 Azure Key Vault 检索该密钥。
使用 Add-AzSqlServerKeyVaultKey 命令将新密钥添加到辅助服务器。
# add the key from Azure Key Vault to the secondary server
Add-AzSqlServerKeyVaultKey -KeyId <keyVaultKeyId> -ServerName <logicalServerName> -ResourceGroup <SQLDatabaseResourceGroupName>
将第一步中的相同密钥添加到主服务器。
# add the key from Azure Key Vault to the primary server
Add-AzSqlServerKeyVaultKey -KeyId <keyVaultKeyId> -ServerName <logicalServerName> -ResourceGroup <SQLDatabaseResourceGroupName>
使用 Set-AzSqlInstanceTransparentDataEncryptionProtector 将密钥设置为主服务器上的主要保护程序,并将自动密钥轮换设置为 true。
Set-AzSqlServerTransparentDataEncryptionProtector -Type AzureKeyVault -KeyId <keyVaultKeyId> `
-ServerName <logicalServerName> -ResourceGroup <SQLDatabaseResourceGroupName> `
-AutoRotationEnabled $true
使用命令 Get-AzKeyVaultKey 和 Set-AzKeyVaultKeyRotationPolicy 在 Azure Key Vault 中轮转 Azure Key Vault 密钥。
Get-AzKeyVaultKey -VaultName <keyVaultName> -Name <keyVaultKeyName> | Set-AzKeyVaultKeyRotationPolicy -KeyRotationLifetimeAction @{Action = "Rotate"; TimeBeforeExpiry = "P18M"}
检查 SQL Server(主要和辅助)是否具有新密钥或密钥版本:
注意
密钥轮换最多可能需要一个小时才能应用于服务器。 请至少等待一小时后再执行此命令。
Get-AzSqlServerKeyVaultKey -KeyId <keyVaultKeyId> -ServerName <logicalServerName> -ResourceGroupName <SQLDatabaseResourceGroupName>
为每个服务器使用不同的密钥
在 Azure 门户中使用 CMK 配置 TDE 时,可以使用不同的密钥保管库密钥配置主服务器和辅助服务器。 在 Azure 门户中,用于保护主服务器的密钥也与保护已复制到辅助服务器的主数据库的密钥相同,这并不明显。 但是,可以使用 PowerShell、Azure CLI 或 REST API 来获取有关在服务器上使用的密钥的详细信息。 这表明自动轮换密钥已从主服务器传输到辅助服务器。
下面是使用 PowerShell 命令检查密钥轮换后从主服务器传输到辅助服务器的密钥的示例。
在主服务器上执行以下命令,以显示某台服务器的密钥详细信息:
Get-AzSqlServerKeyVaultKey -ServerName <logicalServerName> -ResourceGroupName <SQLDatabaseResourceGroupName>
应看到类似于以下内容的结果:
ResourceGroupName : <SQLDatabaseResourceGroupName>
ServerName : <logicalServerName>
ServerKeyName : <keyVaultKeyName>
Type : AzureKeyVault
Uri : https://<keyvaultname>.vault.azure.cn/keys/<keyName>/<GUID>
Thumbprint : <thumbprint>
CreationDate : 12/13/2022 8:56:32 PM
在辅助服务器上执行相同的 Get-AzSqlServerKeyVaultKey 命令:
Get-AzSqlServerKeyVaultKey -ServerName <logicalServerName> -ResourceGroupName <SQLDatabaseResourceGroupName>
如果辅助服务器的默认 TDE 保护程序使用的密钥与主服务器不同,应会显示两个(或多个)密钥。 第一个密钥是默认的 TDE 保护程序,第二个密钥是用于保护复制数据库的主服务器中使用的密钥。
当密钥在主服务器上轮换时,它会自动传输到辅助服务器。 如果在主服务器上再次运行 Get-AzSqlServerKeyVaultKey,应会显示两个密钥。 第一个密钥是原始密钥,第二个密钥是作为密钥轮换的一部分生成的当前密钥。
在辅助服务器上运行 Get-AzSqlServerKeyVaultKey 命令,也应显示与主服务器中相同的密钥。 这将确认主服务器上的轮换密钥会自动传输到辅助服务器,并用于保护数据库副本。
手动密钥轮换
手动密钥轮换使用以下命令来添加新密钥,该密钥可能使用新的密钥名称,甚至在另一密钥保管库中。 使用此方法时支持将同一密钥添加到不同的密钥保管库来支持高可用性和异地灾难恢复方案。 手动密钥轮换也可以使用 Azure 门户完成。
如果使用手动密钥轮换,当密钥保管库中生成新的密钥版本时(在密钥保管库中手动操作或通过自动密钥轮换策略),必须将同一版本手动设置为服务器上的 TDE 保护器。
注意
Key Vault 名称和密钥名称的总长度不能超过 94 个字符。
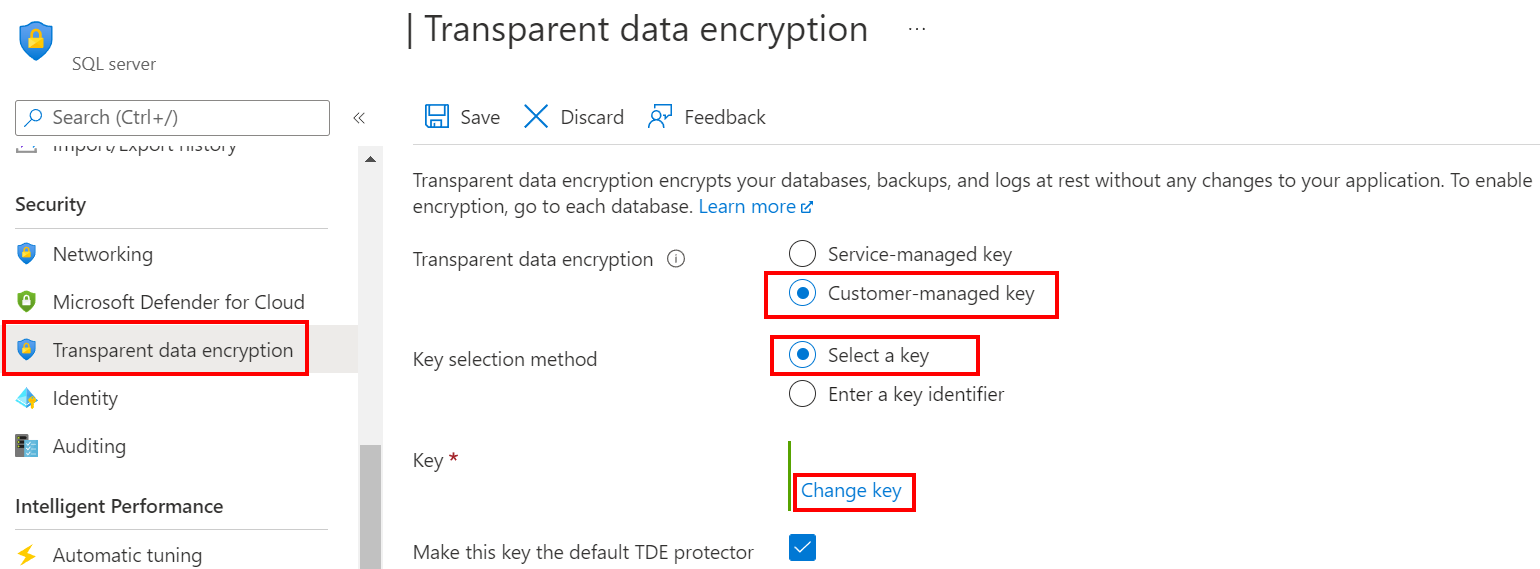
使用 Azure 门户:
- 浏览到现有服务器或托管实例的“透明数据加密”菜单。
- 选择“客户管理的密钥”选项,并选择要用作新的 TDE 保护器的密钥保管库和密钥。
- 选择“保存”。
使用 Add-AzKeyVaultKey 命令将新密钥添加到密钥保管库。
# add a new key to Azure Key Vault
Add-AzKeyVaultKey -VaultName <keyVaultName> -Name <keyVaultKeyName> -Destination <hardwareOrSoftware>
对于 Azure SQL 数据库,请使用以下命令:
# add the new key from Azure Key Vault to the server
Add-AzSqlServerKeyVaultKey -KeyId <keyVaultKeyId> -ServerName <logicalServerName> -ResourceGroup <SQLDatabaseResourceGroupName>
# set the key as the TDE protector for all resources under the server
Set-AzSqlServerTransparentDataEncryptionProtector -Type AzureKeyVault -KeyId <keyVaultKeyId> `
-ServerName <logicalServerName> -ResourceGroup <SQLDatabaseResourceGroupName>
对于 Azure SQL 托管实例,请使用以下命令:
# add the new key from Azure Key Vault to the managed instance
Add-AzSqlInstanceKeyVaultKey -KeyId <keyVaultKeyId> -InstanceName <ManagedInstanceName> -ResourceGroup <ManagedInstanceResourceGroupName>
# set the key as the TDE protector for all resources under the managed instance
Set-AzSqlInstanceTransparentDataEncryptionProtector -Type AzureKeyVault -KeyId <keyVaultKeyId> `
-InstanceName <ManagedInstanceName> -ResourceGroup <ManagedInstanceResourceGroupName>
使用 az keyvault key create 命令将新密钥添加到密钥保管库。
# add a new key to Azure Key Vault
az keyvault key create --name <keyVaultKeyName> --vault-name <keyVaultName> --protection <Software>
对于 Azure SQL 数据库,请使用以下命令:
# add the new key from Azure Key Vault to the server
az sql server key create --kid <keyVaultKeyId> --resource-group <SQLDatabaseResourceGroupName> --server <logicalServerName>
# set the key as the TDE protector for all resources under the server
az sql server tde-key set --server-key-type AzureKeyVault --kid <keyVaultKeyId> --resource-group <SQLDatabaseResourceGroupName> --server <logicalServerName>
对于 Azure SQL 托管实例,请使用以下命令:
# add the new key from Azure Key Vault to the managed instance
az sql mi key create --kid <keyVaultKeyId> --resource-group <Managed InstanceResourceGroupName> --managed-instance <ManagedInstanceName>
# set the key as the TDE protector for all resources under the managed instance
az sql mi tde-key set --server-key-type AzureKeyVault --kid <keyVaultKeyId> --resource-group <ManagedInstanceResourceGroupName> --managed-instance <ManagedInstanceName>
切换 TDE 保护器模式
使用 Azure 门户将 TDE 保护器从“Microsoft 托管”切换到“BYOK”模式:
- 浏览到现有服务器或托管实例的“透明数据加密”菜单。
- 选择“客户管理的密钥”选项。
- 选择要用作 TDE 保护器的密钥保管库和密钥。
- 选择“保存”。
Azure SQL 数据库
要将 TDE 保护器从 Microsoft 托管模式切换到 BYOK 模式,请使用 Set-AzSqlServerTransparentDataEncryptionProtector 命令。
Set-AzSqlServerTransparentDataEncryptionProtector -Type AzureKeyVault `
-KeyId <keyVaultKeyId> -ServerName <logicalServerName> -ResourceGroup <SQLDatabaseResourceGroupName>
要将 TDE 保护器从 BYOK 模式切换到 Microsoft 托管模式,请使用 Set-AzSqlServerTransparentDataEncryptionProtector 命令。
Set-AzSqlServerTransparentDataEncryptionProtector -Type ServiceManaged `
-ServerName <logicalServerName> -ResourceGroup <SQLDatabaseResourceGroupName>
Azure SQL 托管实例
要将 TDE 保护器从 Microsoft 托管模式切换到 BYOK 模式,请使用 Set-AzSqlInstanceTransparentDataEncryptionProtector 命令。
Set-AzSqlServerTransparentDataEncryptionProtector -Type AzureKeyVault `
-KeyId <keyVaultKeyId> <ManagedInstanceName> -ResourceGroup <ManagedInstanceResourceGroupName>
要将 TDE 保护器从 BYOK 模式切换到 Microsoft 托管模式,请使用 Set-AzSqlInstanceTransparentDataEncryptionProtector 命令。
Set-AzSqlServerTransparentDataEncryptionProtector -Type ServiceManaged `
-InstanceName <ManagedInstanceName> -ResourceGroup <ManagedInstanceResourceGroupName>e>
Azure SQL 数据库
以下示例使用 az sql server tde-key set。
将 TDE 保护器从“Microsoft 托管”切换到“BYOK”模式:
az sql server tde-key set --server-key-type AzureKeyVault --kid <keyVaultKeyId> --resource-group <SQLDatabaseResourceGroupName> --server <logicalServerName>
将 TDE 保护器从“BYOK”模式切换到“Microsoft 托管”:
az sql server tde-key set --server-key-type ServiceManaged --resource-group <SQLDatabaseResourceGroupName> --server <logicalServerName>
Azure SQL 托管实例
以下示例使用 az sql mi tde-key set。
将 TDE 保护器从“Microsoft 托管”切换到“BYOK”模式:
az sql mi tde-key set --server-key-type AzureKeyVault --kid <keyVaultKeyId> --resource-group <ManagedInstanceResourceGroupName> --managed-instance <ManagedInstanceName>
将 TDE 保护器从“BYOK”模式切换到“Microsoft 托管”:
az sql mi tde-key set --server-key-type ServiceManaged --resource-group <ManagedInstanceResourceGroupName> --managed-instance <ManagedInstanceName>
相关内容
Azure SQL 数据库
Azure SQL 托管实例
Azure Synapse Analytics(仅限专用 SQL 池)



