Azure 为传统经销商和分销商(CSP)提供超大规模服务,以便能够快速为客户预配新的服务和解决方案,而无需投资开发这些新服务。 为了允许云解决方案提供商(CSP)能够直接管理这些新服务,Azure 提供了允许云解决方案提供商代表客户管理 Azure 资源的计划和 API。 其中一个资源是 ExpressRoute。 ExpressRoute 允许 CSP 将现有客户资源连接到 Azure 服务。 ExpressRoute 是 Azure 中服务的高速专用通信链接。
ExpressRoute 由一对线路组成,以实现高可用性,这些线路连接到单个客户的一个或多个订阅,不能由多个客户共享。 每个线路都应在不同的路由器中终止,以保持高可用性。
注释
每个 ExpressRoute 线路上的带宽和连接数都有限制。 如果单个客户的需求超过这些限制,则需要多个 ExpressRoute 线路才能实现其混合网络。 有关详细信息,请参阅 ExpressRoute 限制。
Azure 提供了越来越多的服务,你可以为客户提供这些服务。 ExpressRoute 通过提供对 Azure 环境的高速低延迟访问,帮助你和客户利用这些服务。
Azure 管理
Azure 通过允许与你自己的服务管理系统进行编程集成,为 CSP 提供 API 来管理 Azure 客户订阅。 可 在此处找到支持的管理功能。
Azure 资源管理
与客户签订的合同决定了订阅的托管方式。 CSP 可以直接管理资源的创建和维护,或者客户可以维护对 Azure 订阅的控制,并根据需要创建 Azure 资源。 如果客户在其 Azure 订阅中管理资源的创建,则他们使用以下两种模型之一:“连通”模型或“直接连接”模型。 以下部分详细介绍了这些模型。
连接模型
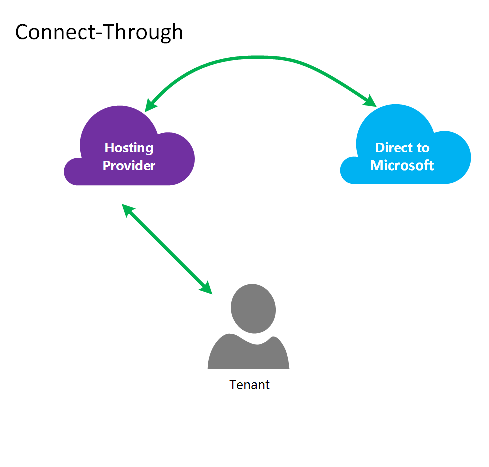
在连接模型中,CSP 会在数据中心和客户的 Azure 订阅之间创建直接连接。 直接连接是使用 ExpressRoute 建立的,将网络连接到 Azure。 然后,客户连接到您的网络。 此方案要求客户通过 CSP 网络访问 Azure 服务。
如果客户没有由你管理的其他 Azure 订阅,他们将使用公共 Internet 或其自己的专用连接连接到非 CSP 订阅下预配的服务。
对于管理 Azure 服务的 CSP,假定 CSP 具有已经建立的客户身份存储,该存储将复制到 Microsoft Entra ID,以便通过代表管理 (AOBO) 管理其 CSP 订阅。 此方案的关键驱动因素包括给定的合作伙伴或服务提供商与客户建立了关系,客户当前正在使用提供商服务,或者合作伙伴希望提供提供商托管的解决方案和 Azure 托管解决方案的组合,以提供灵活性,并解决无法单独由 CSP 满足的客户挑战。 下图演示了此模型。
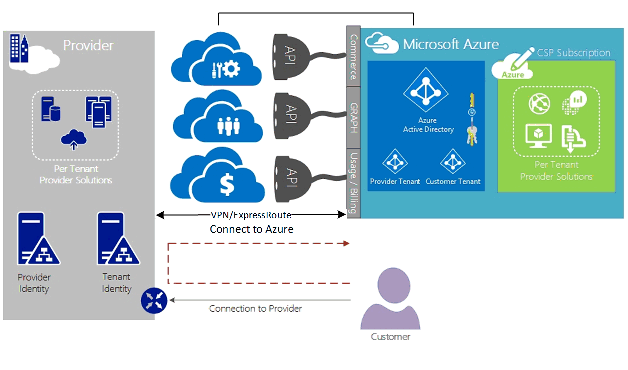
连接到模型
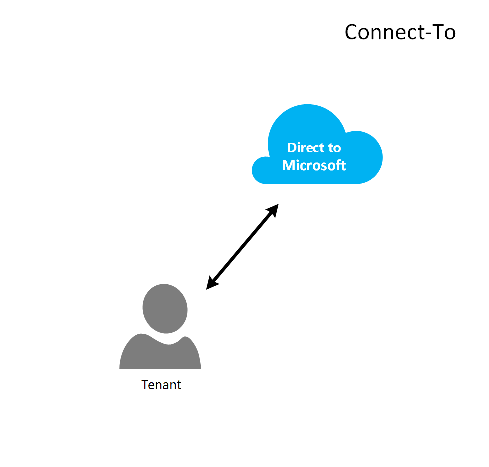
在 Connect-To 模型中,服务提供商使用 ExpressRoute 通过客户的(客户)网络在客户的数据中心与 CSP 预配的 Azure 订阅之间建立直接连接。
注释
对于 ExpressRoute,客户需要创建和维护 ExpressRoute 线路。
此连接方案要求客户直接通过客户网络进行连接,以访问 CSP 管理的 Azure 订阅,该订阅使用完全或部分由客户创建、拥有和管理的直接网络连接。 对于这些客户,假定提供商当前没有建立客户标识存储,并且提供商将协助客户将当前标识存储复制到 Microsoft Entra ID 中,以便通过 AOBO 管理其订阅。 此方案的关键驱动因素包括给定的合作伙伴或服务提供商与客户建立了关系、客户当前正在使用提供商服务,或者合作伙伴希望提供仅基于 Azure 托管的解决方案的服务,而无需现有提供商数据中心或基础结构。
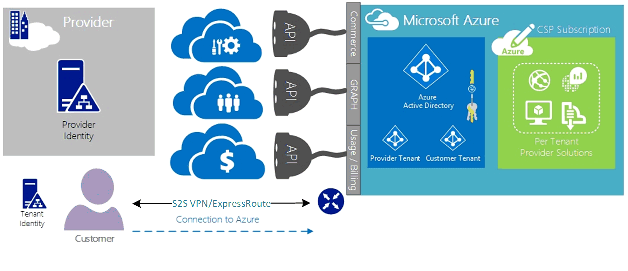
这两个选项之间的选择取决于客户需求和当前提供 Azure 服务的需求。 以下链接中详细介绍了这些模型和关联的基于角色的访问控制、网络和标识设计模式:
- Azure 基于角色的访问控制 (Azure RBAC) - Azure RBAC 基于 Microsoft Entra ID。 有关 Azure RBAC 的详细信息,请参阅 此处。
- 网络 - 介绍 Azure 中网络的各种文章。
- Microsoft Entra ID - Microsoft Entra ID 为 Azure 和第三方 SaaS 应用程序提供标识管理。 有关 Microsoft Entra ID 的详细信息,请参阅什么是 Microsoft Entra ID?。
网络速度
ExpressRoute 支持从 50 Mb/秒到 10 Gb/秒的网络速度。 这样,客户就可以购买其独特环境所需的网络带宽量。
注释
无需中断通信即可根据需要增加网络带宽,但为了降低网络速度,需要拆毁线路,以较低的网络速度重新创建线路。 有关详细信息,请参阅 修改 ExpressRoute 线路
ExpressRoute 支持将多个 VNet 连接到单个 ExpressRoute 线路,以便更好地利用高速连接。 单个 ExpressRoute 线路可以在同一客户拥有的多个 Azure 订阅之间共享。
配置 ExpressRoute
ExpressRoute 可配置为通过单个 ExpressRoute 线路支持两种类型的流量(路由域)。 此流量分为私有对等连接和微软对等连接。 可以选择一种或两种类型的流量,以便通过单个 ExpressRoute 线路发送,或使用多个 ExpressRoute 线路,具体取决于客户所需的 ExpressRoute 线路大小和隔离。 客户的安全策略可能不允许公共流量和专用流量通过同一线路传输。
连接模型
在透传连接配置中,你需负责所有网络基础架构,以连接客户的数据中心资源到在 Azure 上托管的订阅。 每个想要使用 Azure 功能的客户都需要自己的 ExpressRoute 连接,这些连接将由你管理。 您使用客户采购 ExpressRoute 线路时使用的相同方法。 按照 ExpressRoute 工作流 中概述的相同步骤进行线路预配和线路状态。 然后,配置边界网关协议(BGP)路由来控制本地网络和 Azure VNet 之间的流量。
连接到模型
在连接配置中,您的客户已与 Azure 建立现有连接,或者将会启动与互联网服务提供商的连接,将其 ExpressRoute 从自己的数据中心直接链接到 Azure,而不是您的数据中心。 若要开始预配过程,客户遵循上述 Connect-Through 模型中所述的步骤。 建立线路后,客户需要配置本地路由器才能访问网络和 Azure VNet。
可以协助设置连接和配置路由,以允许数据中心中的资源与数据中心中的客户端资源通信,或者与 Azure 中托管的资源通信。
ExpressRoute 路由域
ExpressRoute 为新电路提供两个路由域:专用对等互连和 Microsoft 对等互连。 每个路由域都配置了相同的路由器,并采用主动-主动配置,以实现高可用性。 有关 ExpressRoute 路由域的更多详细信息, 请查看此处。
可以定义自定义路由筛选器,以仅允许想要允许或需要的路由。 有关详细信息或要了解如何进行这些更改,请参阅文章: 使用 PowerShell 创建和修改 ExpressRoute 线路的路由 ,以获取有关路由筛选器的更多详细信息。
注释
对于Microsoft对等连接,连接必须通过客户或CSP拥有的公共IP地址,并且必须遵守所有已定义的规则。 有关详细信息,请参阅 ExpressRoute 先决条件 页。
路线规划
ExpressRoute 通过 Azure 虚拟网络网关连接到 Azure 网络。 网络网关为 Azure 虚拟网络提供路由。
创建 Azure 虚拟网络还会为 VNet 创建一个默认路由表,以便将流量定向到 VNet 的子网或从子网传入/传出流量。 如果默认路由表不足以用于解决方案,则可以创建自定义路由,以将传出流量路由到自定义设备或阻止路由到特定子网或外部网络。
默认路由
默认路由表包括以下路由:
- 子网中的路由
- 虚拟网络中的子网到子网
- 到 Internet
- 使用 VPN 网关的虚拟网络到虚拟网络连接
- 虚拟网络通过 VPN 或 ExpressRoute 网关连接到本地网络
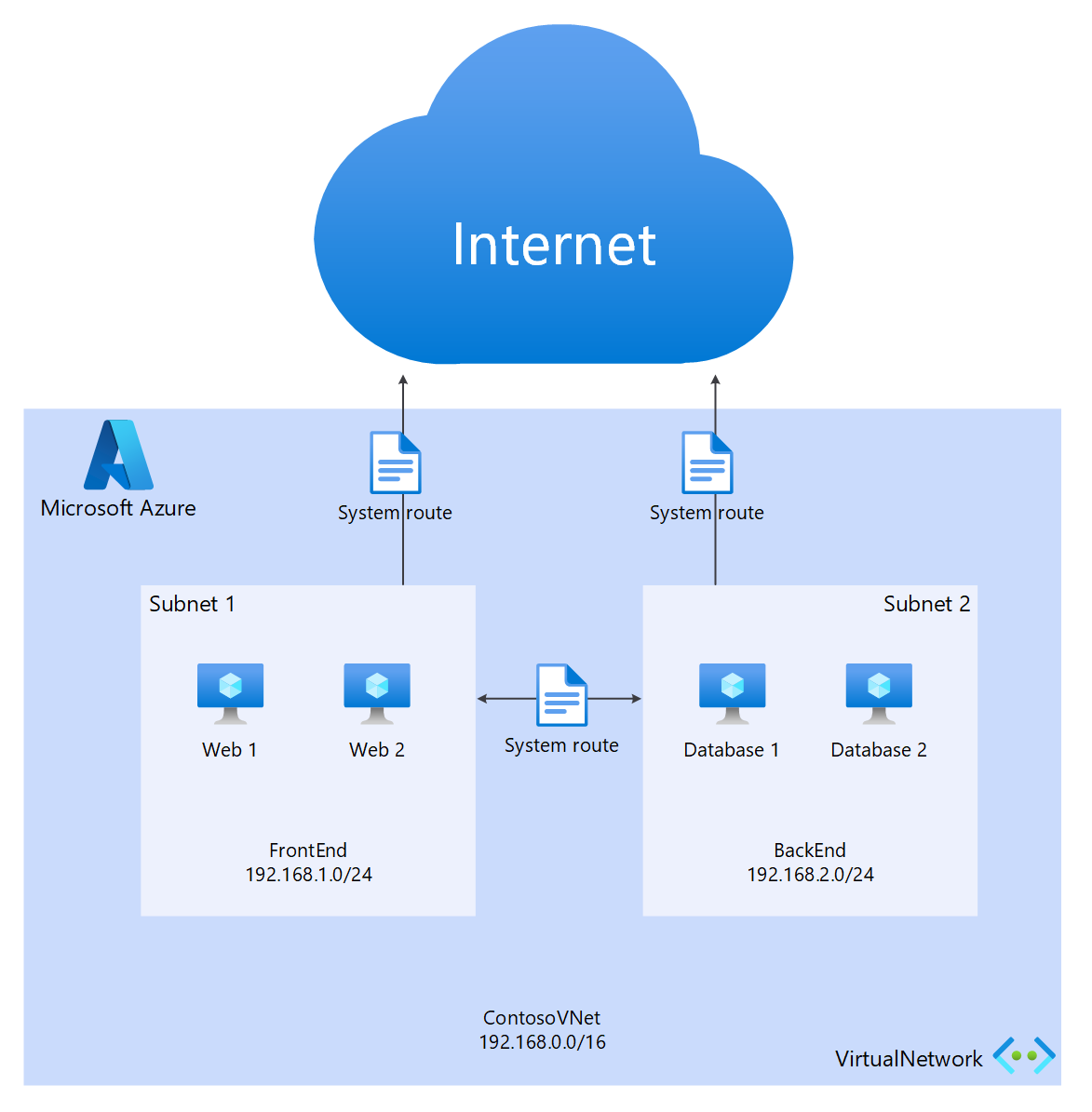
用户定义的路由(UDR)
用户定义的路由允许控制从分配的子网到虚拟网络中的其他子网或其他预定义网关(如 ExpressRoute、internet 或 VPN)的出站流量。 默认系统路由表可以替换为用户定义的路由表,该表将默认路由表替换为自定义路由。 使用用户定义的路由,客户可以创建到设备(例如防火墙或入侵检测设备)的特定路由,或者阻止从托管用户定义路由的子网访问特定子网。 有关用户定义的路由的概述,请参阅此处。
安全性
根据所使用的模型(Connect-To 或 Connect-Through),客户可以在其 VNet 中定义安全策略,或者向 CSP 提供安全策略要求以便于在其 VNet 中进行定义。 可以定义以下安全条件:
客户隔离 - Azure 平台通过将客户 ID 和 VNet 信息存储在安全数据库中来提供客户隔离,该信息用于封装 GRE 隧道中的每个客户的流量。
网络安全组(NSG) 规则用于定义允许传入和传出 Azure 中 VNet 中的子网的流量。 默认情况下,NSG 包含用于阻止从 Internet 到 VNet 流量的阻止规则,以及用于允许 VNet 内部流量的允许规则。 有关网络安全组的详细信息, 请查看此处。
强制隧道 - 此选项用于重定向源自 Azure 的 Internet 绑定流量,以便通过 ExpressRoute 连接重定向到本地数据中心。 有关强制隧道的详细信息, 请查看此处。
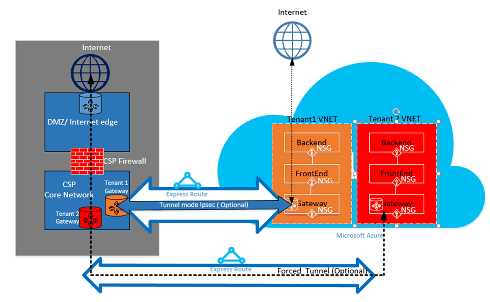
加密 - 即使 ExpressRoute 线路专用于特定客户,也有可能破坏网络提供商,从而允许入侵者检查数据包流量。 为了解决这种潜在风险,客户或 CSP 可以通过定义本地资源与 Azure 资源之间的所有流量的 IPsec 隧道模式策略,加密连接上的流量(详见上图 5:“ExpressRoute 安全性”中的客户 1 可选隧道模式 IPsec)。 第二个选项是在 ExpressRoute 线路的每个终结点使用防火墙设备。 这要求在两端安装另一个第三方防火墙 VM/设备,以通过 ExpressRoute 线路加密流量。
后续步骤
云解决方案提供商服务提供了一种提高客户价值的方法,而无需昂贵的基础结构和功能购买,同时保持你作为主要外包提供商的地位。 可以通过 CSP API 实现与 Azure 的无缝集成,从而在现有管理框架中集成 Azure 的管理。