本文介绍了如何通过 ExpressRoute 专用对等互连在传输模式下创建 IPsec 隧道。 隧道需要在运行 Windows 和本地 Windows 主机的 Azure VM 之间进行创建。 本文中针对此配置的步骤使用组策略对象。 尽管无需使用组织单位 (OU) 和组策略对象 (GPO) 就可创建此配置。 OU 和 GPO 的组合有助于简化对安全策略的控制,并允许快速纵向扩展。 本文中的步骤假定你已具有 Active Directory 配置并且可以熟练使用 OU 和 GPO。
关于此配置
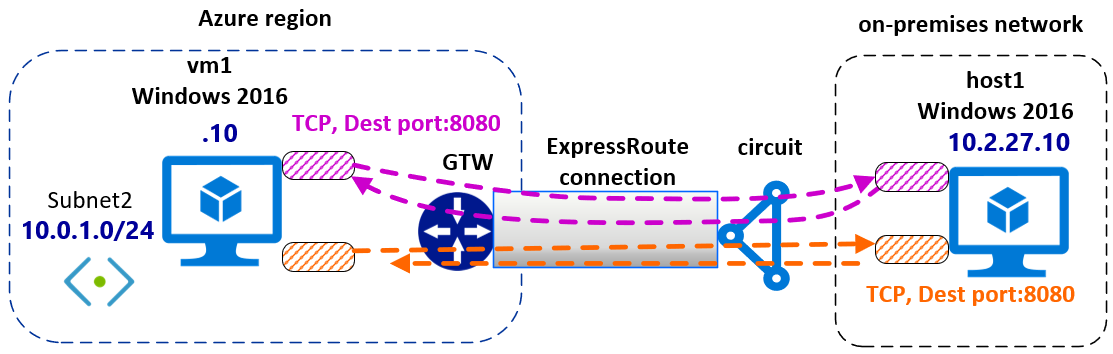
以下步骤中的配置使用具有 ExpressRoute 专用对等互连的单个 Azure 虚拟网络 (VNet)。 但是,此配置可以跨越其他 Azure VNet 和本地网络。 本文有助于定义 IPsec 加密策略,该策略可以应用于一组 Azure VM 或本地主机。 这些 Azure VM 或本地主机是同一 OU 的一部分。 仅针对目标端口为 8080 的 HTTP 流量,在 Auzre VM(vm1 和 vm2)和本地 host1 之间配置加密。 可以根据要求创建不同类型的 IPsec 策略。
使用 OU
与 OU 关联的安全策略将通过 GPO 推送到计算机。 与向单个主机应用策略相比,使用 OU 的几个优点是:
- 将策略与 OU 关联可保证属于相同 OU 的计算机获取相同的策略。
- 更改与 OU 关联的安全策略会将更改应用到 OU 中的所有主机。
图表
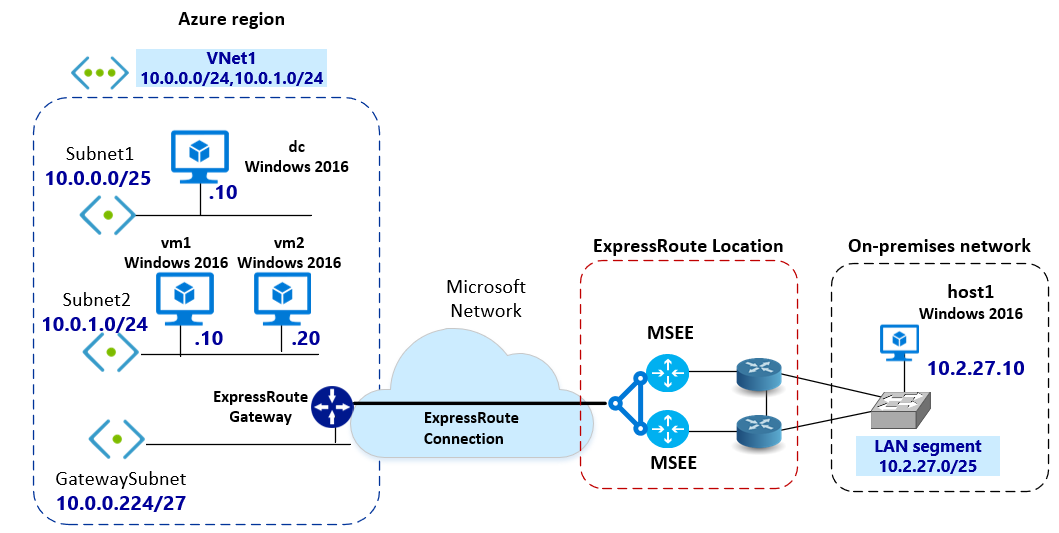
下图显示了互连和分配的 IP 地址空间。 Azure VM 和本地主机运行的是 Windows 2016。 Azure VM 和本地 host1 是同一个域的一部分。 Azure VM 和本地主机可以使用 DNS 正确地解析名称。
此图显示了 ExpressRoute 专用对等互连中正在传输的 IPsec 隧道。
使用 IPsec 策略
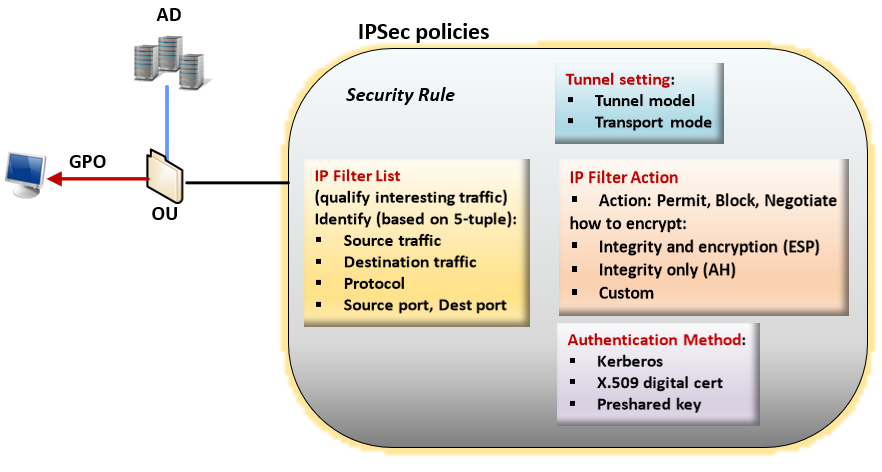
在 Windows 中,加密是与 IPsec 策略相关联的。 IPsec 策略确定哪些 IP 流量是受保护的,以及应用于 IP 数据包的安全机制。 IPSec 策略由以下各项组成:筛选器列表、筛选器操作和安全规则。
在配置 IPsec 策略时,请务必了解以下 IPsec 策略术语:
IPsec 策略:规则的集合。 在任意特定时间只能有一个策略处于活跃状态(“已分配”)。 每个策略可以有一个或多个规则,所有规则可同时启用。 一台计算机在给定的时间只能分配有一个活跃的 IPsec 策略。 但是,在 IPsec 策略内,可以定义在不同情况下可能采取的多个操作。 每个 IPsec 规则集与一个筛选器列表相关联,该列表影响规则所应用到的网络流量类型。
筛选器列表:筛选器列表是一个或多个筛选器的捆绑包。 一个列表可包含多个筛选器。 筛选器基于以下条件定义是否阻止、允许或保护通信:IP 地址范围、协议,甚至是特定端口。 每个筛选器匹配一组特定的条件;例如,从特定子网发送到特定计算机上特定目标端口的数据包。 当网络条件匹配这些筛选器中的一个或多个时,筛选器列表便被激活。 每个筛选器在特定筛选器列表内进行定义。 筛选器不能在筛选器列表之间共享。 但是,给定的筛选器列表可并入多个 IPsec 策略中。
筛选器操作:安全方法定义在 IKE 协议期间计算机提供的一组安全算法、协议和密钥。 筛选器操作是按优先顺序排列的安全方法列表。 在计算机协商 IPsec 会话时,它根据筛选器操作列表中存储的安全设置接受或发送方案。
安全规则:规则控制 IPsec 策略如何及何时保护通信。 它使用筛选器列表和筛选器操作来创建 IPsec 规则以建立 IPsec 连接。 每个策略可以有一个或多个规则,所有规则可同时启用。 每个规则包含一个 IP 筛选器列表和一个在出现与该筛选器列表的匹配时发生的安全操作集合:
- IP 筛选器操作
- 身份验证方法
- IP 隧道设置
- 连接类型
开始之前
确保符合以下先决条件:
必须拥有可用来实现组策略设置的正常运行的 Active Directory 配置。 有关 GPO 的详细信息,请参阅组策略对象。
必须有一个活动的 ExpressRoute 线路。
- 有关创建 ExpressRoute 线路的详细信息,请参阅创建 ExpressRoute 线路。
- 确认线路由连接提供程序启用。
- 确认已为线路配置 Azure 专用对等互连。 有关路由说明,请参阅配置路由一文。
- 确认已创建并完全预配一个 VNet 和一个虚拟网络网关。 按照说明创建 ExpressRoute 的虚拟网络网关。 ExpressRoute 虚拟网络网关使用的 GatewayType 是 ExpressRoute 而非 VPN。
ExpressRoute 虚拟网络网关必须连接到 ExpressRoute 线路。 有关详细信息,请参阅将 VNet 连接到 ExpressRoute 线路。
确认 Azure Windows VM 部署到 VNet。
确认在本地主机和 Azure VM 之间存在连接。
确认 Azure Windows VM 和本地主机能够使用 DNS 正确解析名称。
工作流
- 创建 GPO 并将其关联到 OU。
- 定义 IPsec 筛选器操作。
- 定义 IPsec 筛选器列表。
- 创建具有安全规则的 IPsec 策略。
- 将 IPsec GPO 分配到 OU。
示例值
域名:ipsectest.com
OU:IPSecOU
本地 Windows 计算机:host1
Azure Windows VM:vm1、vm2
1.创建 GPO
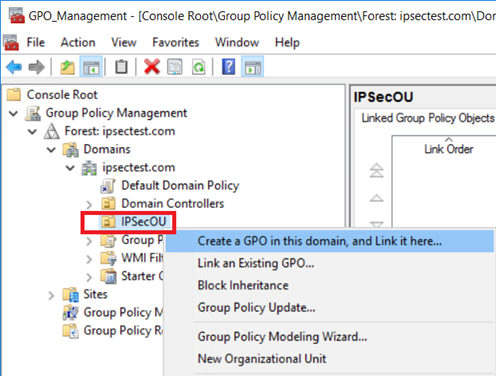
通过打开“组策略管理”管理单元来创建链接到 OU 的新 GPO。 然后找到该 GPO 链接到的 OU。 在示例中,OU 名为“IPSecOU”。
在“组策略管理”管理单元中,选择 OU 并右键单击。 在下拉菜单中,选择“在此域中创建 GPO 并将其链接到此处...”。
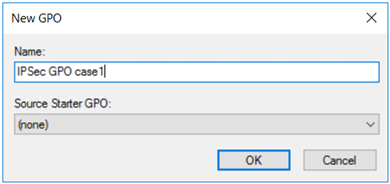
为 GPO 取一个直观的名称,以便可在之后轻松找到它。 选择“确定”以创建并链接 GPO。
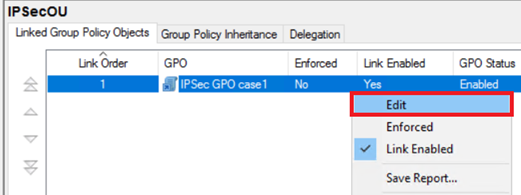
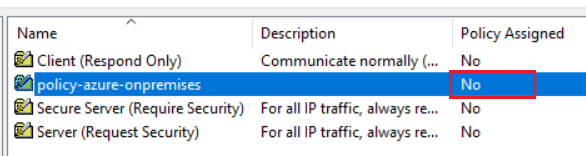
2.启用 GPO 链接
若要将 GPO 应用到 OU,不仅该 GPO 必须链接到 OU,还必须启用启用该链接。
3.定义 IP 筛选器操作
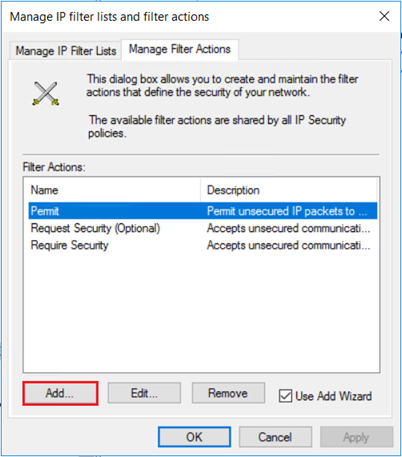
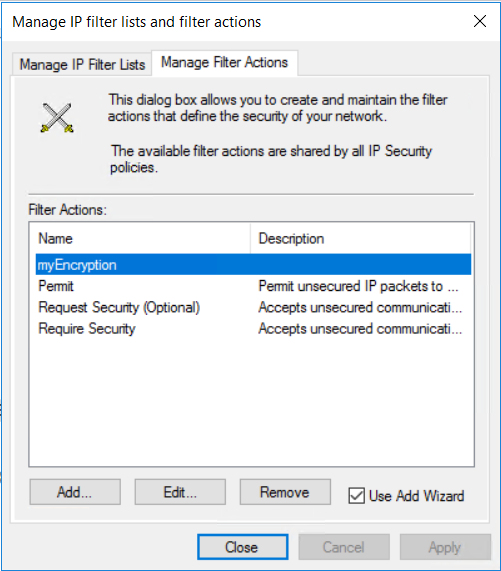
从下拉菜单中,右键单击“Active Directory 上的 IP 安全策略”,然后选择“管理 IP 筛选器列表和筛选器操作...” 。
在“管理筛选器操作”选项卡上,选择“添加” 。
在“IP 安全筛选器操作向导”上,选择“下一步” 。
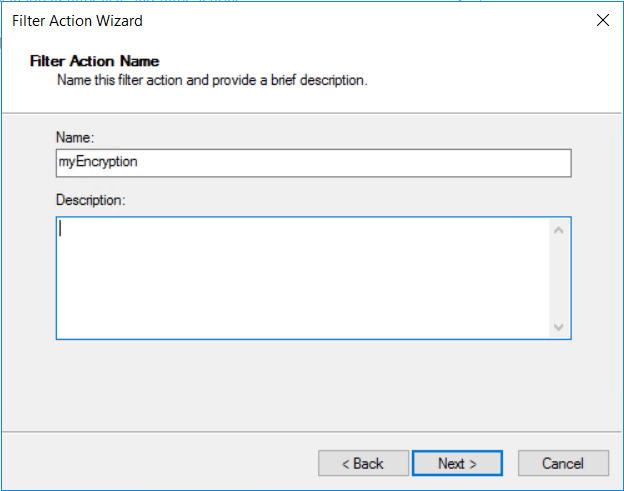
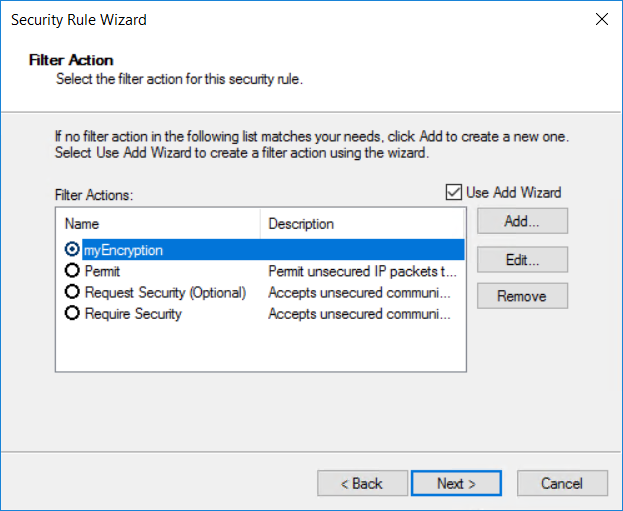
为筛选器操作取一个直观的名称,以便可在之后找到它。 在本示例中,筛选器操作名为“myEncryption”。 还可以添加说明。 然后,选择“下一步” 。
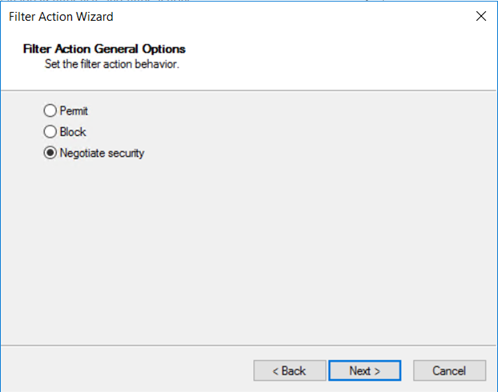
“协商安全性”允许定义在 IPsec 无法与另一台计算机成功建立时的行为。 选择“协商安全性”,然后单击“下一步” 。
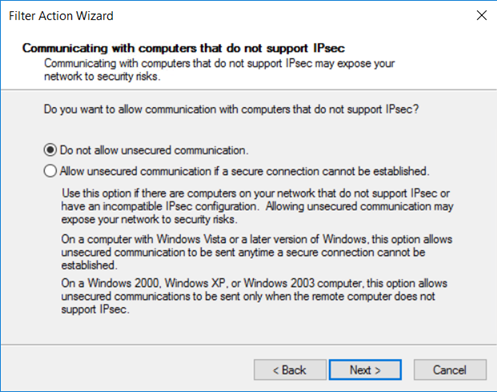
在“与不支持 IPsec 的计算机通信”页上,选择“不允许不安全的通信”,然后选择“下一步” 。
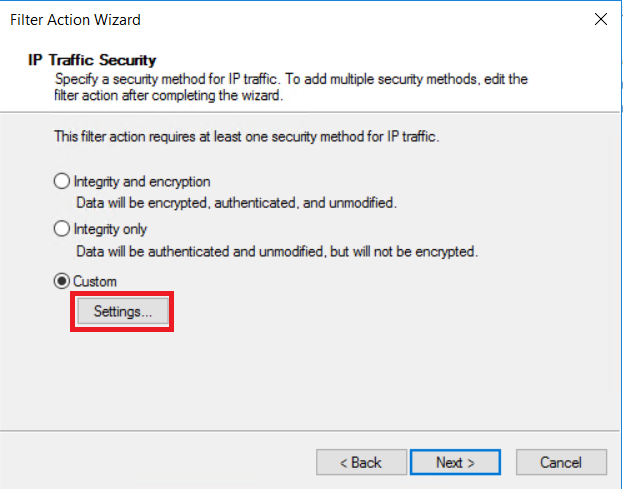
在“IP 流量和安全性”页上,选择“自定义”,然后单击“设置...” 。
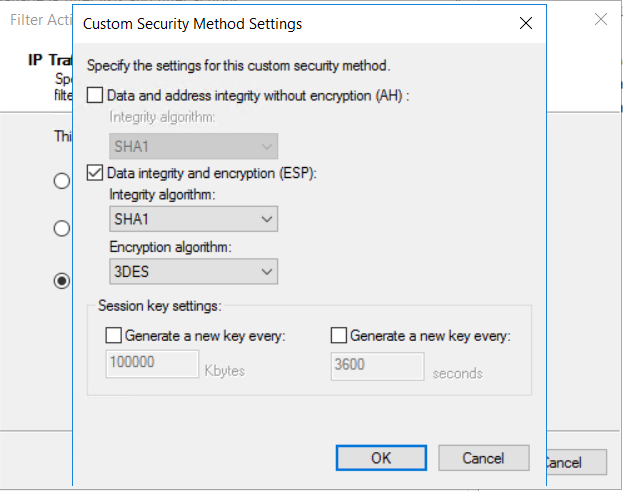
在“自定义安全方法设置”页上,选择“数据完整性和加密 (ESP): SHA1、3DES”。 选择“确定”。
在“管理筛选器操作”页上,可以看到“myEncryption”筛选器已成功添加。 选择关闭。
4.定义 IP 筛选器列表
创建指定目标端口为 8080 的已加密 HTTP 流量的筛选器列表。
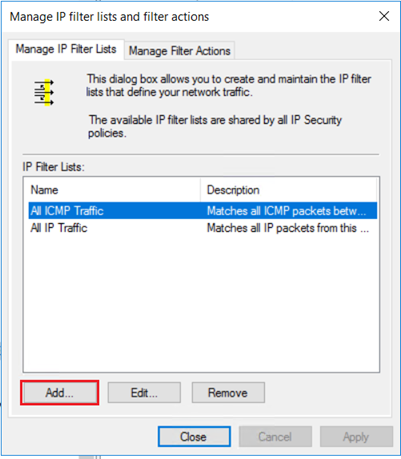
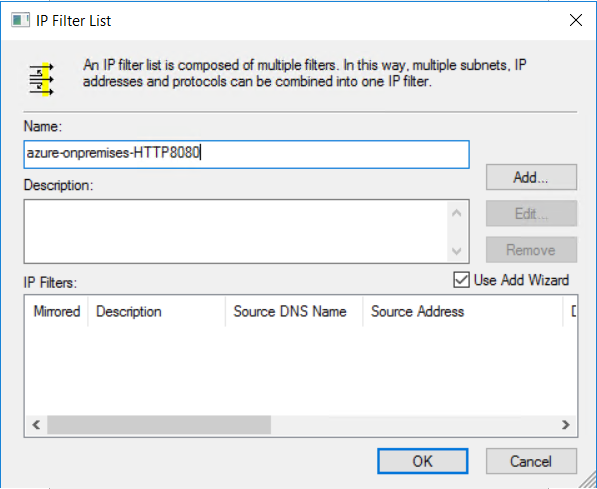
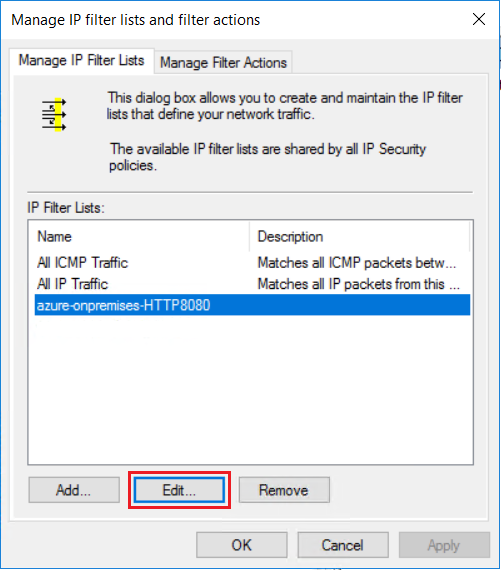
若要限定必须加密哪些类型的流量,请使用 IP 筛选器列表。 在“管理 IP 筛选器列表”选项卡上,单击“添加”以添加新的 IP 筛选器列表 。
在“名称”字段中,键入 IP 筛选器列表的名称。 例如,“azure-onpremises-HTTP8080”。 然后选择“添加”。
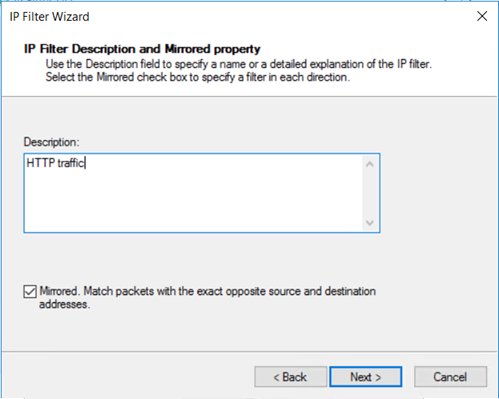
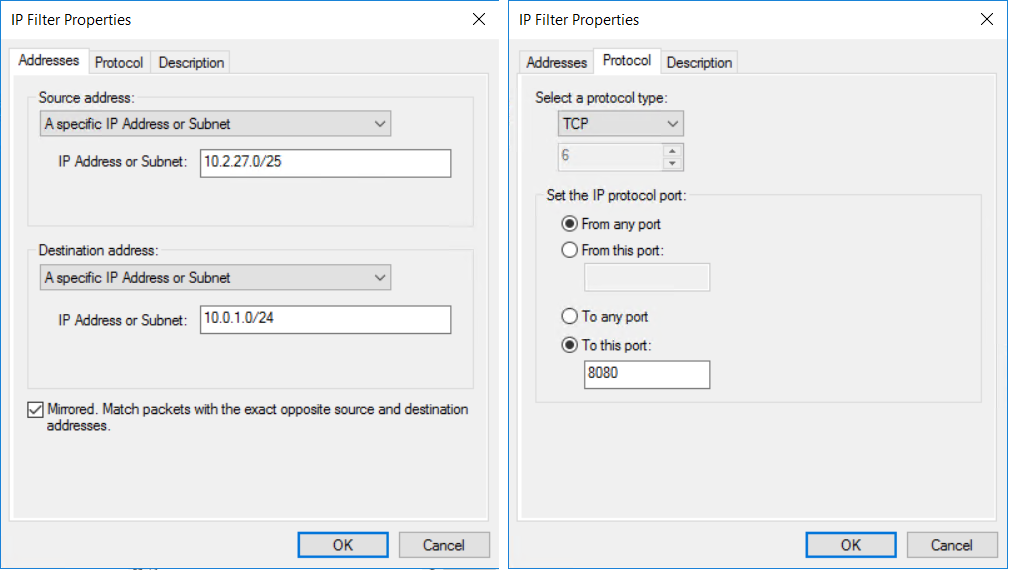
在“IP 筛选器描述和镜像属性”页上,选择“镜像”。 镜像设置匹配两个方向的数据包,这使得可以进行双向通信。 然后,选择“下一步”。
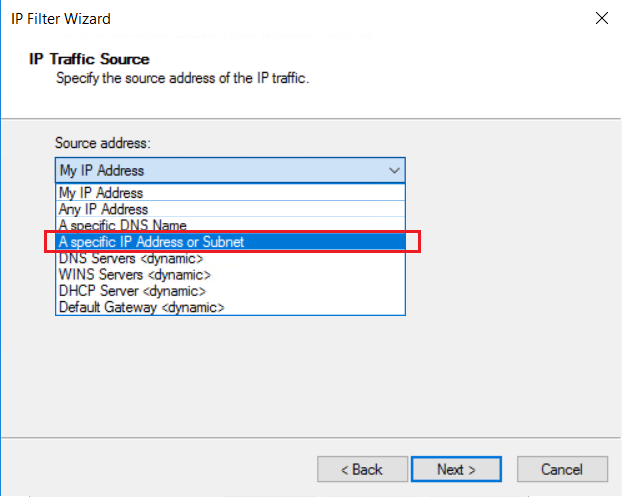
在“IP 流量源”页上,从“源地址:”下拉菜单中,选择“特定的 IP 地址或子网”。
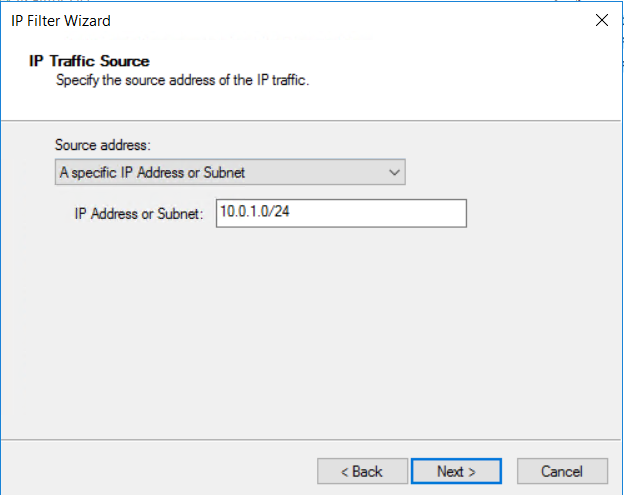
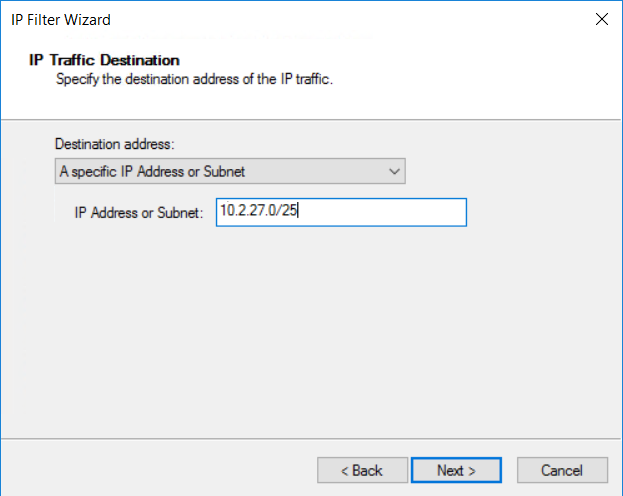
指定 IP 流量的“IP 地址或子网:”,然后单击“下一步” 。
指定“目标地址:”IP 地址或子网。 然后选择下一步。
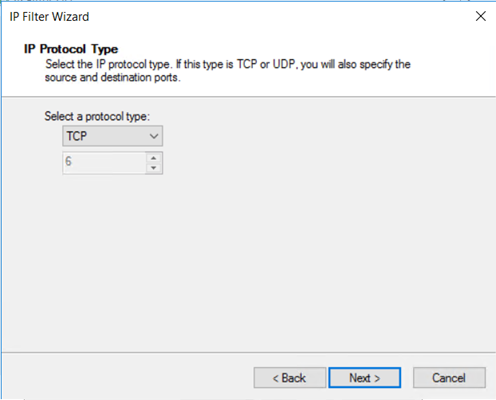
在“IP 协议类型”页上,选择“TCP”。 然后选择下一步。
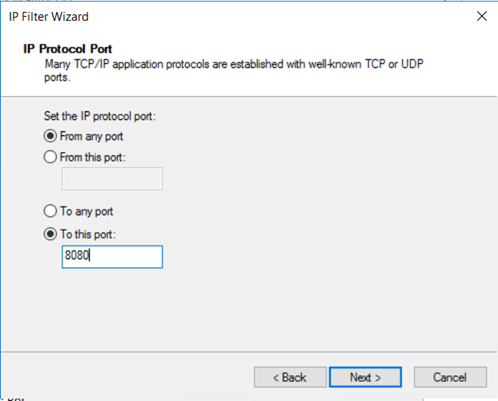
在“IP 协议端口”页上,选择“从任意端口”和“至此端口:”。 在文本框中键入“8080”。 这些设置指定仅目标端口 8080 上的 HTTP 流量会被加密。 然后,选择“下一步” 。
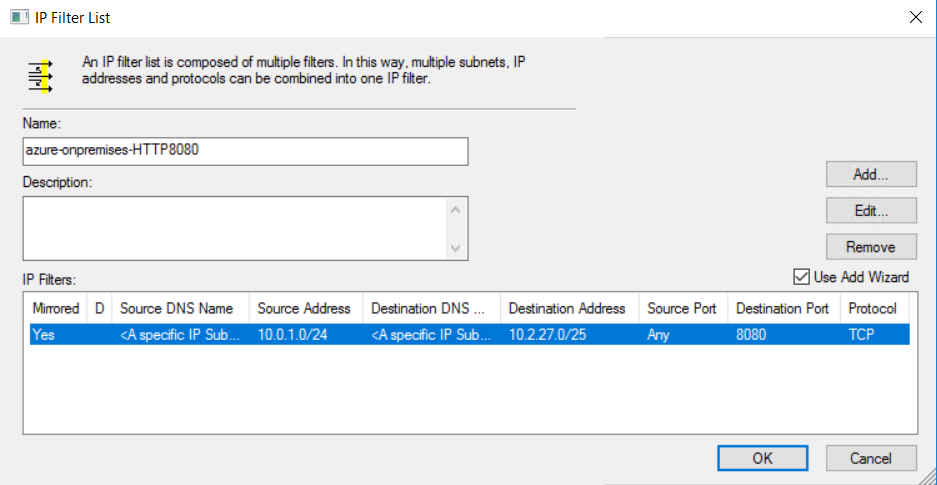
查看 IP 筛选器列表。 IP 筛选器列表“azure-onpremises-HTTP8080”的配置为所有匹配以下条件的流量触发加密:
- 10.0.1.0/24 (Azure Subnet2) 中的任意源地址
- 10.2.27.0/25(本地子网)中的任意目标地址
- TCP 协议
- 目标端口 8080
5.编辑 IP 筛选器列表
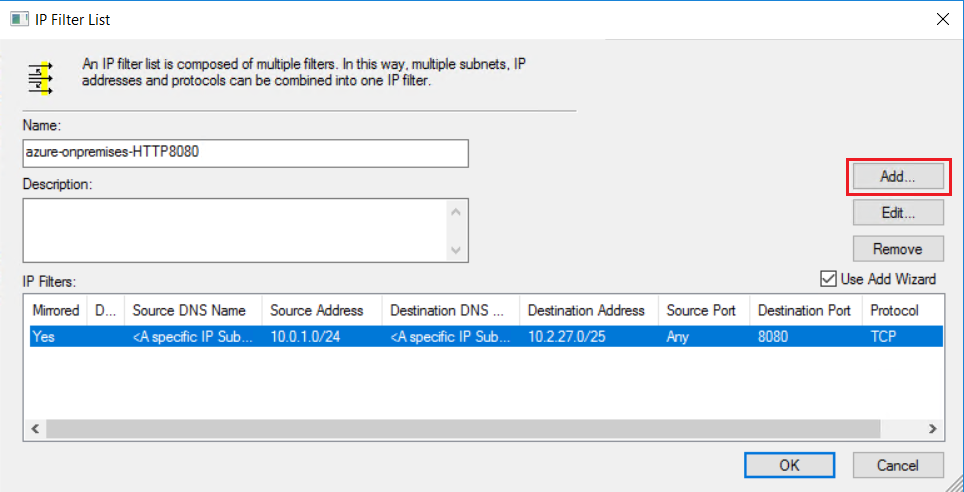
若要加密从本地主机到 Azure VM 的同一类型的流量,需要第二个 IP 筛选器。 按照与设置第一个 IP 筛选器相同的步骤操作,并创建新的 IP 筛选器。 唯一的区别是源子网和目标子网。
若要将新的 IP 筛选器添加到 IP 筛选器列表中,请选择“编辑”。
在“IP 筛选器列表”页上,选择“添加” 。
使用以下示例中的设置创建第二个 IP 筛选器:
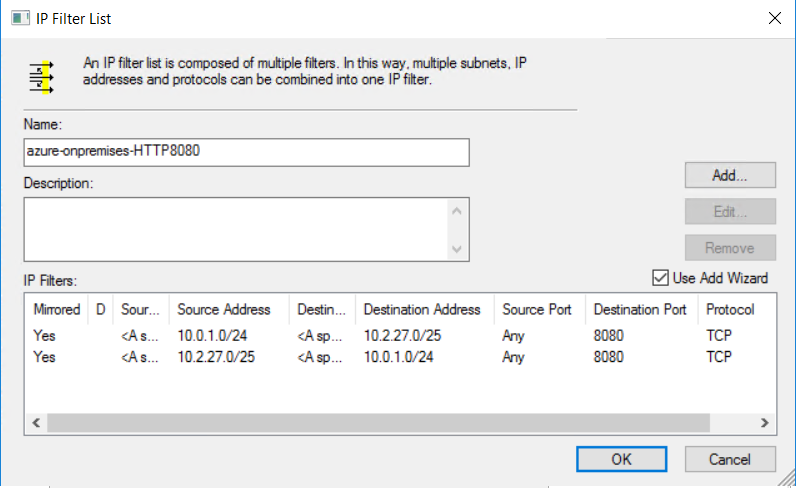
创建第二个 IP 筛选器后,IP 筛选器列表将如下所示:
如果本地位置和 Azure 子网之间需要加密以保护应用程序。 可以添加新的 IP 筛选器列表,而不是修改现有的 IP 筛选器列表。 将两个或多个 IP 筛选器列表关联到同一 IPsec 策略能够提供更大的灵活性。 可以修改或删除 IP 筛选器列表,而不会影响其他 IP 筛选器列表。
6.创建 IPsec 安全策略
创建具有安全规则的 IPsec 策略
选择与 OU 相关联的“Active Directory 上的 IPSecurity 策略”。 右键单击,然后选择“创建 IP 安全策略”。
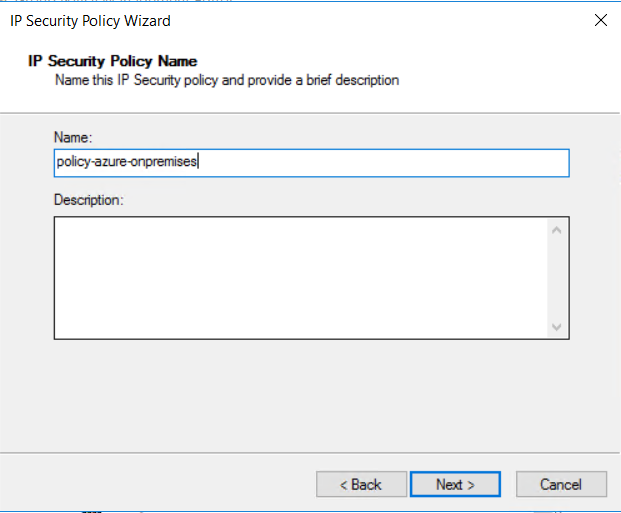
命名安全策略。 例如,“policy-azure-onpremises”。 然后选择下一步。
选择“下一步”,无需选中复选框。
确认已选中“编辑属性”复选框,然后选择“完成” 。
7.编辑 IPsec 安全策略
将 IPsec 策略添加到之前配置的 IP 筛选器列表和筛选器操作。
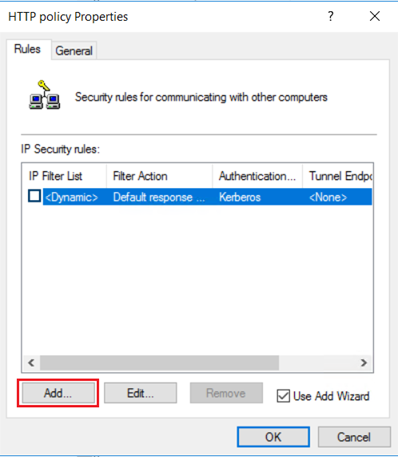
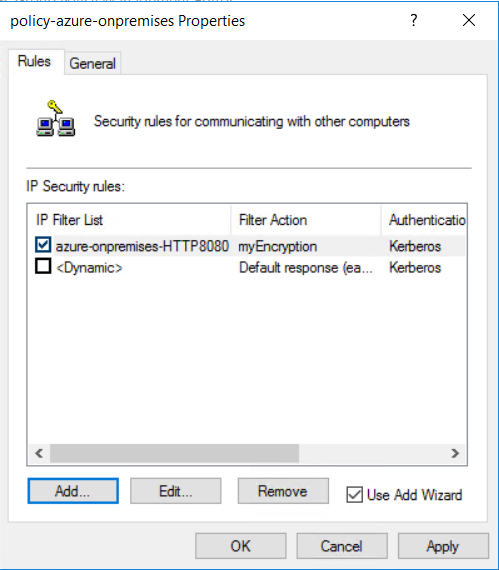
在 HTTP 策略属性“规则”选项卡上,选择“添加” 。
在“欢迎”页上,选择“下一步”。
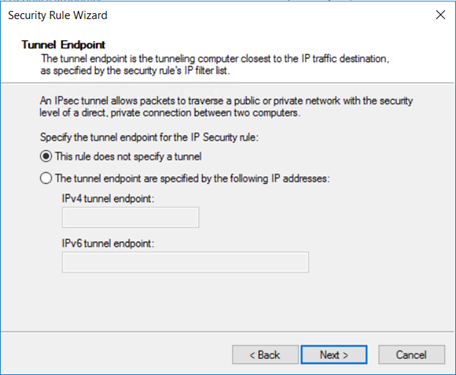
规则提供选项来定义 IPsec 模式:隧道模式或传输模式。
在隧道模式下,原始数据包使用一组 IP 标头来封装。 隧道模式通过加密原始数据包的 IP 标头来保护内部路由信息。 隧道模式在站点到站点 VPN 场景中的网关之间广泛实现。 隧道模式在大多数情况下用于主机之间的端到端加密。
传输模式仅加密有效负载和 ESP 尾部;不会加密原始数据包的 IP 标头。 在传输模式下,数据包的 IP 源和 IP 目标不变。
选择“此规则不指定隧道”,然后选择“下一步” 。
“网络类型”定义哪些网络连接与安全策略关联。 选择“所有网络连接”,然后选择“下一步” 。
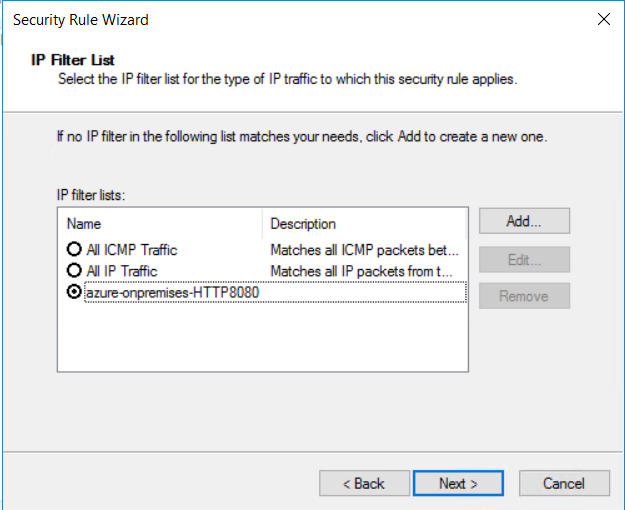
选择之前创建的 IP 筛选器列表“azure-onpremises-HTTP8080”,然后选择“下一步”。
选择之前创建的现有筛选器操作“myEncryption”。
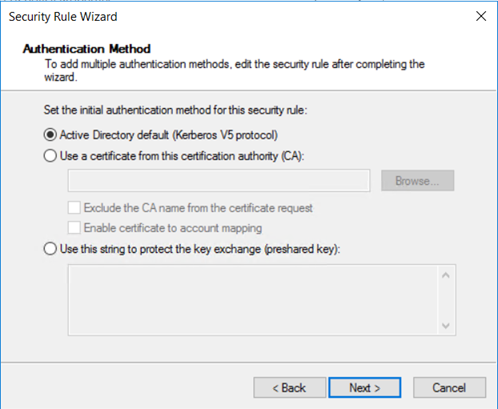
Windows 支持四种不同类型的身份验证:Kerberos、证书、NTLMv2 和预共享密钥。 由于我们使用的是已加入域的主机,因此选择“Active Directory 默认(Kerberos V5 协议)”,然后选择“下一步” 。
新的策略会创建安全规则:“azure-onpremises-HTTP8080”。 选择“确定”。
IPsec 策略要求目标端口 8080 上的所有 HTTP 连接使用 IPsec 传输模式。 由于 HTTP 是明文协议,因此启用安全策略可确保数据通过 ExpressRoute 专用对等互连传输时处于加密状态。 与高级安全 Windows 防火墙相比,配置 Active Directory 的 IPsec 策略更复杂。 但可以对 IPsec 连接进行更多自定义。
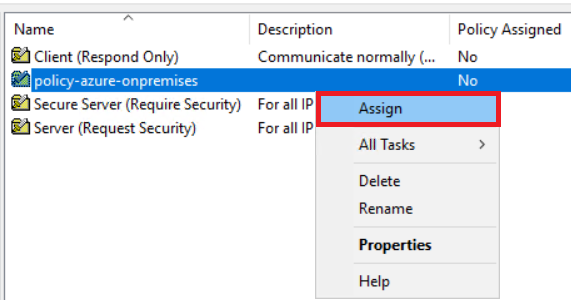
8.将 IPsec GPO 分配到 OU
检查流量加密
若要查看应用于 OU 的加密 GPO,请在所有 Azure VM 上和 host1 中安装 IIS。 每个 IIS 均自定义为答复端口 8080 上的 HTTP 请求。 若要验证加密,可以在 OU 中的所有计算机中安装网络探查器(如 Wireshark)。 PowerShell 脚本充当 HTTP 客户端以在端口 8080 上生成 HTTP 请求:
$url = "http://10.0.1.20:8080"
while ($true) {
try {
[net.httpWebRequest]
$req = [net.webRequest]::create($url)
$req.method = "GET"
$req.ContentType = "application/x-www-form-urlencoded"
$req.TimeOut = 60000
$start = get-date
[net.httpWebResponse] $res = $req.getResponse()
$timetaken = ((get-date) - $start).TotalMilliseconds
Write-Output $res.Content
Write-Output ("{0} {1} {2}" -f (get-date), $res.StatusCode.value__, $timetaken)
$req = $null
$res.Close()
$res = $null
} catch [Exception] {
Write-Output ("{0} {1}" -f (get-date), $_.ToString())
}
$req = $null
# uncomment the line below and change the wait time to add a pause between requests
#Start-Sleep -Seconds 1
}
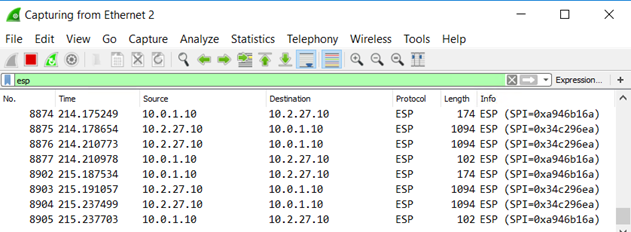
以下网络捕获显示本地 host1 的结果,并显示仅匹配已加密流量的筛选器 ESP:
如果运行本地 PowerShell 脚本(HTTP 客户端),Azure VM 中的网络捕获将显示类似的跟踪。
后续步骤
有关 ExpressRoute 的详细信息,请参阅 ExpressRoute 常见问题。