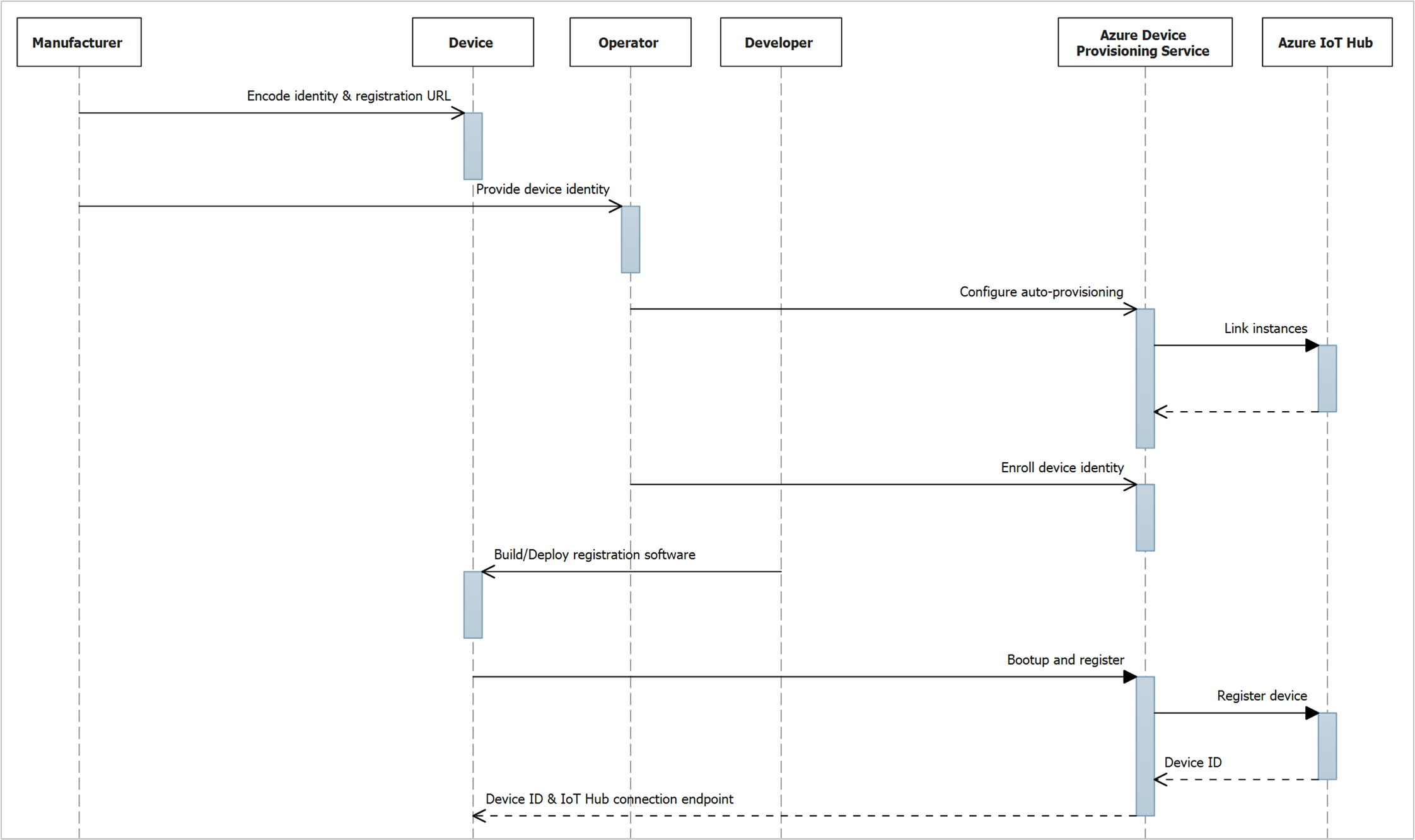
由于制造时间、交货、报关等生产因素,开发 IoT 解决方案的阶段可能会跨数周或数月。此外,如果涉及到多种实体,这些阶段可能需要经历多个角色的活动。 本文更深入地了解与每个阶段相关的各种角色和操作,然后在序列图中展示流程。
预配还对设备制造商施加启用证明机制方面的要求。 制造操作也可能独立于自动预配阶段的时机进行,尤其是在自动预配已建立后购买新设备的情况下。
左侧目录中提供了一系列快速入门指南,以帮助通过实践说明自动预配。 为了促进/简化学习过程,我们将使用软件来模拟用于登记和注册的物理设备。 某些快速入门要求你为多个角色执行操作(包括不存在的角色),由于快速入门的模拟特性。
| 角色 | 操作 | 说明 |
|---|---|---|
| 制造商 | 为标识和注册 URL 编码 | 根据所用的认证机制,制造商需负责为设备标识信息和设备预配服务注册 URL 编码。 快速入门:由于设备是模拟的,因此没有制造商角色。 有关如何获取这些信息以便在编写示例注册应用程序代码时使用的详细信息,请参阅“开发人员角色”。 |
| 提供设备标识 | 作为设备标识信息的发起者,制造商需负责通信向操作员(或指定的代理)传递这些信息,或者通过 API 将其直接登记到设备预配服务。 快速入门:由于设备是模拟的,因此没有制造商角色。 有关如何获取在设备预配服务实例中登记模拟设备时所用的设备标识的详细信息,请参阅“操作员角色”。 |
|
| 运算符 | 配置自动预配 | 此作对应于自动预配的第一个阶段。 快速入门:你需要履行操作员角色,在 Azure 订阅中配置设备预配服务和 IoT 中心实例。 |
| 登记设备标识 | 此作对应于自动预配的第二个阶段。 快速入门:你需要履行操作员角色,在设备预配服务实例中登记模拟设备。 快速入门(TPM 或 X.509)中模拟的证明方法确定设备标识。 有关认证详细信息,请参阅“开发人员角色”。 |
|
| 设备预配服务 IoT 中心 |
<所有操作> | 对于使用物理设备的生产实现和使用模拟设备的快速入门,需要通过 Azure 订阅中配置的 IoT 服务履行这些角色。 角色/操作的功能完全相同,因为 IoT 服务预配物理设备和模拟设备的方式没有差别。 |
| 开发人员 | 生成/部署注册软件 | 此操作对应于自动预配的第三个阶段。 开发人员负责使用相应的 SDK 生成注册软件并将其部署到设备。 快速入门:生成的示例注册应用程序模拟适用于所选平台/语言的、在工作站中运行的真实设备(而不是将其部署到物理设备)。 注册应用程序执行的操作与部署到物理设备的应用程序相同。 需要指定认证方法(TPM 或 X.509 证书),以及设备预配服务实例的注册 URL 和“ID 范围”。 设备标识由 SDK 认证逻辑在运行时根据指定的方法确定:
|
| 设备 | 启动和注册 | 此作对应于自动预配的第三阶段,由开发人员生成的设备注册软件完成。 有关详细信息,请参阅“开发人员角色”。 首次启动时:
|
注意
(可选)制造商还可以使用设备预配服务 API(而不是通过操作员)执行“登记设备标识”操作。
角色和 Azure 帐户
每个角色映射到 Azure 帐户的方式取决于方案,而涉及的方案可能有很多。 以下常见模式应有助于大致了解角色如何映射到 Azure 帐户。
芯片制造商提供安全服务
在此方案中,制造商为一级客户管理安全。 对于这些级别一级客户来说,此方案可能更可取,因为他们不必管理详细的安全性。
制造商将安全性引入硬件安全模块 (HSM)。 此安全性可能包括制造商从可能的客户处获取密钥、证书等,这些客户已经设置 DPS 实例和注册组。 制造商也可以为其客户生成此安全信息。
在此方案中,可能涉及两个 Azure 帐户:
帐户 #1:可能在操作员和开发人员角色之间存在某种程度的共享。 此方可能会从制造商那里购买 HSM 芯片。 这些芯片指向与帐户 1 关联的 DPS 实例。 使用 DPS 注册,该方可以将设备租赁给多个二级客户,只需在 DPS 中重新配置设备注册设置即可。 此方可能还会为最终用户后端系统分配 IoT 中心,以便与之交互,以便访问设备遥测等。在此后一种情况下,可能不需要第二个帐户。
帐户 #2:最终用户,二级客户可能有自己的 IoT 中心。 与帐户 1 相关联的一方可以直接将租赁的设备指向此帐户中的正确中心。 此配置要求跨 Azure 帐户链接 DPS 和 IoT 中心,该操作可以通过 Azure 资源管理器模板来完成。
一体化 OEM
制造商可能是“一体化 OEM”,只需一个制造商帐户。 制造商负责端到端的安全性和预配。
制造商可以为购买设备的客户提供基于云的应用程序。 此应用程序将与制造商分配的 IoT 中心进行交互。
售货机或自动咖啡机是此方案的示例。
后续步骤
在完成相应的自动预配快速入门时,你可能会发现,将本文作为参考点添加书签会很有帮助。
首先完成最适合管理工具首选项的“设置自动预配”快速入门,引导你完成“服务配置”阶段:
然后继续学习最适合你的设备证明机制和设备预配服务 SDK/语言偏好的“预配设备”快速入门。 此快速入门逐步讲解“设备登记”与“设备注册和配置”阶段:
| 设备证明机制 | 快速入门 |
|---|---|
| 对称密钥 | 预配模拟对称密钥设备 |
| X.509 证书 | 预配模拟的 X.509 设备 |
| 模拟的受信任平台模块 (TPM) | 预配模拟的 TPM 设备 |