本文介绍了在使用含设备预配服务的对称密钥时的标识证明过程。 对称密钥证明是一种通过设备预配服务实例对设备进行身份验证的简单方法。 此证明方法表示不熟悉设备预配或不具备严格安全要求的开发人员的“Hello world”体验。 使用 TPM 或 X.509 证书 的设备证明更安全,并且应该用于更严格的安全要求。
对称密钥注册还为具有有限安全功能的旧设备提供了一种通过 Azure IoT 启动到云的方法。
对称密钥创建
默认情况下,当创建新注册且启用“自动生成对称密钥”选项时,设备预配服务会创建长度为 64 个字节的新对称密钥。
还可以通过禁用此选项来为注册提供你自己的对称密钥。 对称密钥必须采用 Base 64 格式,且密钥长度介于 16 个字节与 64 个字节之间。
详细证明过程
使用 IoT 中心支持的相同安全令牌来执行含设备预配服务的对称密钥证明,以标识设备。 这些安全令牌都是共享访问签名 (SAS) 令牌。
SAS 令牌具有使用对称密钥创建的哈希签名 。 设备预配服务会重新创建该签名,以验证在证明期间显示的安全令牌是否可信。
SAS 令牌的格式如下:
SharedAccessSignature sig={signature}&se={expiry}&skn={policyName}&sr={URL-encoded-resourceURI}
下面是每个令牌的组成元素:
| 值 | 说明 |
|---|---|
| {signature} | HMAC-SHA256 签名字符串。 对于单个注册,此签名通过使用对称密钥(主密钥或辅助密钥)执行哈希而生成。 对于注册组,从注册组密钥中派生的密钥用于执行哈希。 哈希在以下格式的消息上执行:URL-encoded-resourceURI + "\n" + expiry。
重要说明:必须先从 base64 解码密钥,然后才能将其用于执行 HMAC-SHA256 计算。 此外,签名结果必须为 URL 编码。 |
| {resourceURI} | 以设备预配服务实例的范围 ID 开头、可通过此令牌访问的注册终结点的 URI。 例如: {Scope ID}/registrations/{Registration ID} |
| {expiry} | 从纪元 1970 年 1 月 1日 00:00:00 UTC 时间至今秒数的 UTF8 字符串。 |
| {URL-encoded-resourceURI} | 小写资源 URI 的小写 URL 编码 |
| {policyName} | 此令牌所引用的共享访问策略名称。 使用对称密钥证明预配时使用的策略名称是“注册” 。 |
有关创建 SAS 令牌的代码示例,请参阅 SAS 令牌结构。
采用对称密钥的单独注册
当设备使用单个注册进行证明时,设备将使用在单个注册条目中定义的对称密钥创建 SAS 令牌的哈希签名。
采用对称密钥的组注册
与单个注册不同,设备在预配时不会直接使用注册组的对称密钥。 通过注册组进行预配的设备改为使用派生的设备密钥来预配。 派生的设备密钥是设备的注册 ID 的哈希,我们使用注册组的对称密钥来计算它。 然后,设备就可以使用其派生的设备密钥对用于向 DPS 注册的 SAS 令牌进行签名。 由于设备在注册时发送其注册 ID,DPS 可以使用注册组对称密钥重新生成设备的派生设备密钥并验证 SAS 令牌上的签名。
首先,为通过注册组进行身份验证的每个设备定义一个唯一的注册 ID。 注册 ID 是一个不区分大小写的字符串(最大长度为 128 个字符),包含字母数字字符和有效的特殊字符:- . _ :。 最后一个字符必须是字母数字或短划线 ('-')。 注册 ID 应是标识设备的唯一 ID。 例如,可用于唯一标识该设备的 MAC 地址或序列号。 在这种情况下,注册 ID 可以由 MAC 地址和序列号组成,类似于以下示例:
sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6
如何使用对称密钥预配旧设备一文中使用了该示例。
为设备定义注册 ID 后,注册组的对称密钥用于计算注册 ID 的 HMAC-SHA256 哈希,以生成派生的设备密钥。 下方选项卡中提供了计算派生设备密钥的一些示例方法。
Azure CLI 的 IoT 扩展提供了用于生成派生设备密钥的 compute-device-key 命令。 此命令可从基于 Windows 或 Linux 的系统、PowerShell 或 Bash shell 中使用。
将 --key 参数值替换为注册组中的主密钥。
将 --registration-id 参数值替换为注册 ID。
az iot dps enrollment-group compute-device-key --key 8isrFI1sGsIlvvFSSFRiMfCNzv21fjbE/+ah/lSh3lF8e2YG1Te7w1KpZhJFFXJrqYKi9yegxkqIChbqOS9Egw== --registration-id sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6
示例结果:
"Jsm0lyGpjaVYVP2g3FnmnmG9dI/9qU24wNoykUmermc="
然后使用生成的设备密钥来生成要用于证明的 SAS 令牌。 注册组中的每个设备都需要使用从唯一派生密钥中生成的安全令牌进行证明。 注册组对称密钥不能直接用于证明。
安装派生的设备密钥
理想情况下,在中心中派生和安装设备密钥。 此方法可保证不会在部署到设备的任何软件中包含组密钥。 将 MAC 地址或序列号分配给设备时,可以派生密钥并将其注入设备,制造商可以根据其选择的存储方式进行存储。
请考虑下图,该图显示了一个设备密钥表,这些设备密钥通过以下方式在中心中生成:通过组注册密钥 (K) 对每个设备注册 ID 进行哈希处理 。
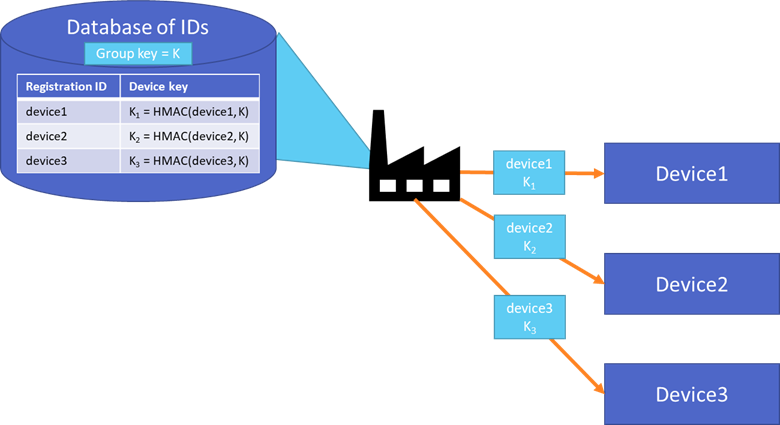
工厂中安装的注册 ID 和派生设备密钥表示每个设备的标识。 设备密钥不会复制到其他位置,且组密钥不会存储在设备上。
如果未在工厂中安装设备密钥,则应使用 硬件安全模块 (HSM)安全地存储设备标识。
后续步骤
了解对称密钥证明后,请参阅以下文章以了解更多信息: