本教程演示了如何使用注册组将多个模拟对称密钥设备安全地预配到一个 IoT 中心。
Azure IoT 中心设备预配服务支持两种类型的预配设备注册:
- 注册组:用于注册多个相关设备。 本教程演示如何使用注册组进行预配。
- 单个注册:用于注册单个设备。
Azure IoT 中心设备预配服务支持用于预配设备的三种身份验证形式:
- X.509 证书
- 可信平台模块 (TPM)
- 对称密钥 - 本教程演示对称密钥证明
有些设备可能没有证书、TPM 或任何其他可用于安全地标识设备的安全功能。 对于此类设备,Azure IoT 中心设备预配服务 (DPS) 包括对称密钥证明。 对称密钥证明可以用于根据 MAC 地址或序列号等唯一信息来标识设备。
在本教程中,你将完成以下目标:
- 为每个设备定义唯一的注册 ID。
- 创建使用对称密钥证明的注册组。
- 使用每个设备的唯一注册 ID 和共享注册组密钥为它们生成设备密钥。
- 使用 Azure IoT 设备 SDK 中的设备密钥和示例代码预配设备。
本教程面向基于 Windows 的工作站。 但是,你也可以在 Linux 上执行过程。 有关 Linux 示例,请参阅教程:预配地理延迟。
注意
如果之前已完成 快速入门:预配模拟对称密钥设备 ,但仍设置了 Azure 资源和开发环境,则可以继续在本教程 中创建对称密钥注册组 。
先决条件
如果没有 Azure 订阅,请在开始前创建一个试用版订阅。
完成通过 Azure 门户设置 IoT 中心设备预配服务中的步骤。
如果使用 Windows 开发环境,请安装启用了“使用 C++ 的桌面开发”工作负载的 Visual Studio 2022。 Visual Studio 2019、Visual Studio 2017 和 Visual Studio 2015 也受支持。 对于 Linux 或 macOS,请参阅 SDK 文档的准备开发环境中的相应部分。
安装最新的 CMake 生成系统。 请确保选中将 CMake 可执行文件添加到路径的选项。
重要
在开始 安装之前,请确认在计算机上安装 Visual Studio 必备组件(Visual Studio 和“使用 C++ 的桌面开发”工作负载)。 满足先决条件并验证下载内容后,安装 CMake 生成系统。 此外,旧版本的 CMake 生成系统无法生成本文中使用的解决方案文件。 请确保使用最新版本的 CMake。
在基于 Windows 的计算机上安装 .NET SDK 6.0 或更高版本。 可使用以下命令来检查你的版本。
dotnet --info
- 安装 Node.js v4.0+。
- 在基于 Windows 的计算机上安装 Python 3.7 或更高版本。 可以通过运行
python --version来检查 Python 版本。
在计算机上安装 Java SE 开发工具包 8 或更高版本。
下载并安装 Maven。
-
安装最新版本的 Git。 确保将 Git 添加到可供命令窗口访问的环境变量。 请参阅软件自由保护组织提供的 Git 客户端工具,了解要安装的最新版
git工具,其中包括 Git Bash,这是一个命令行应用,可以用来与本地 Git 存储库交互。
准备开发环境
在本部分中,你将准备一个开发环境来构建适用于 C 的 Azure IoT 设备 SDK。该示例代码在设备的启动序列期间预配设备。
在 Web 浏览器中,转到 Azure IoT C SDK 发布页。
复制最新版 Azure IoT C SDK 的标记名称,例如:
lts_03_2024。打开 Windows 命令提示符,运行以下命令以克隆最新版本的适用于 C 的 Azure IoT 设备 SDK GitHub 存储库。 请将
<release-tag>替换为在上一步骤中复制的标记。git clone -b <release-tag> https://github.com/Azure/azure-iot-sdk-c.git cd azure-iot-sdk-c git submodule update --init此操作可能需要几分钟才能完成。
操作完成后,从
azure-iot-sdk-c目录中运行以下命令:mkdir cmake cd cmake代码示例使用对称密钥来提供证明。 运行以下命令,生成特定于你的开发客户端平台(包括设备预配客户端)的 SDK 版本:
cmake -Dhsm_type_symm_key:BOOL=ON -Duse_prov_client:BOOL=ON ..提示
如果
cmake找不到C++编译器,则在运行上一个命令时可能会遇到生成错误。 如果出现这种情况,请尝试在 Visual Studio 命令提示符窗口中运行该命令。生成成功完成后,最后的几个输出行类似于以下输出:
$ cmake -Dhsm_type_symm_key:BOOL=ON -Duse_prov_client:BOOL=ON .. -- Building for: Visual Studio 16 2019 -- Selecting Windows SDK version 10.0.19041.0 to target Windows 10.0.22621. -- The C compiler identification is MSVC 19.29.30146.0 -- The CXX compiler identification is MSVC 19.29.30146.0 ... -- Configuring done -- Generating done -- Build files have been written to: C:/azure-iot-sdk-c/cmake
打开命令提示符或 Git Bash 终端。
使用以下命令克隆适用于 C# 的 Azure IoT SDK GitHub 存储库:
git clone https://github.com/Azure/azure-iot-sdk-csharp.git
打开命令提示符或 Git Bash 终端。
使用以下命令克隆适用于 Node.js 的 Azure IoT SDK GitHub 存储库:
git clone https://github.com/Azure/azure-iot-sdk-node.git --recursive
打开命令提示符或 Git Bash 终端。
使用以下命令克隆适用于 Python 的 Azure IoT 设备 SDK GitHub 存储库:
git clone -b v2 https://github.com/Azure/azure-iot-sdk-python.git --recursive注意
本教程中使用的示例位于 azure-iot-sdk-python 存储库的 v2 分支中。 Python SDK 的 V3 可用于 beta 版。 有关更新 V2 代码示例以使用 Python SDK V3 版本的信息,请参阅 适用于 Python 的 Azure IoT 设备 SDK 迁移指南。
打开命令提示符或 Git Bash 终端。
使用以下命令克隆适用于 Java 的 Azure IoT SDK GitHub 存储库:
git clone https://github.com/Azure/azure-iot-sdk-java.git --recursive转到
azure-iot-sdk-java根目录,并生成项目以下载全部所需的包。 此步骤可能需要几分钟才能完成。cd azure-iot-sdk-java mvn install -DskipTests=true
创建对称密钥注册组
登录到 Azure 门户,并导航到设备预配服务实例。
从导航菜单的“设置”部分选择“管理注册”。
选择“添加注册组”。
在“添加注册组”页的“注册 + 预配”选项卡上,提供以下信息以配置注册组详细信息:
字段 说明 证明 选择“对称密钥”作为证明类型。 对称密钥设置 如果要使用随机生成的密钥,请选中“自动生成对称密钥”复选框。 如果要提供自己的密钥,请取消选中此框。 组名 提供设备组的名称。 注册组名称是一个不区分大小写的字符串(最大长度为 128 个字符),包含字母数字字符和以下特殊字符: '-'、'.'、'_'、':'。 最后一个字符必须是字母数字或短划线 ('-')。预配状态 如果希望此注册组用于预配设备,请选中“启用此注册”复选框。 如果希望禁用该组,请取消选中此框。 稍后可以更改此设置。 重新预配策略 选择一个重新预配策略,反映希望 DPS 如何处理请求重新预配的设备。 有关详细信息,请参阅重新预配策略 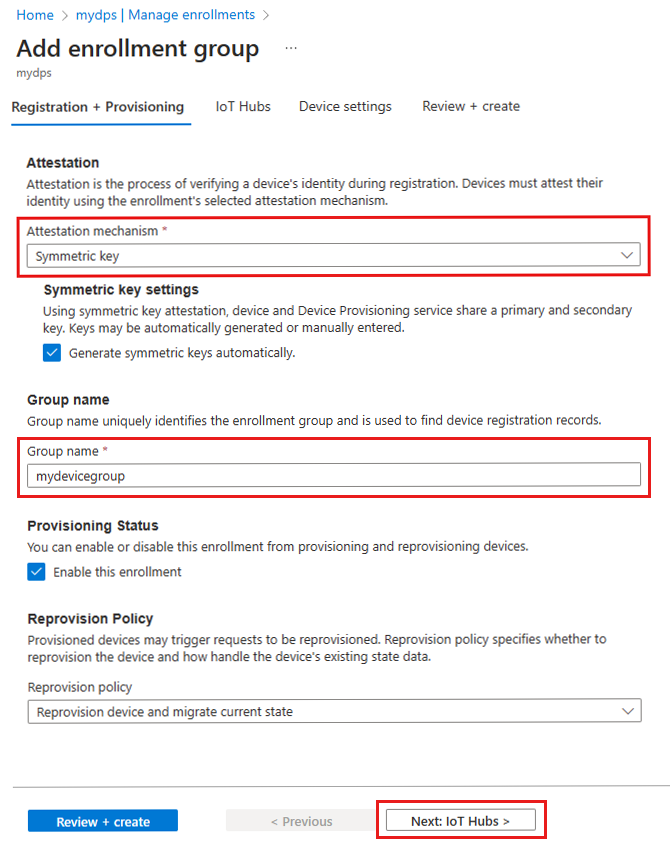
选择“下一步:IoT 中心”。
在“添加注册组”页的“IoT 中心”选项卡上,提供以下信息以确定注册组可以预配设备的目标 IoT 中心:
字段 说明 目标 IoT 中心 选择一个或多个链接的 IoT 中心,或向 IoT 中心添加新链接。 若要详细了解如何将 IoT 中心链接到 DPS 实例,请参阅如何链接和管理 IoT 中心。 分配策略 如果选择了多个已链接的 IoT 中心,请选择要将设备分配到不同中心的方式。 如需详细了解分配策略,请参阅如何使用分配策略。
如果仅选择了一个已链接的 IoT 中心,建议使用均匀加权分发策略。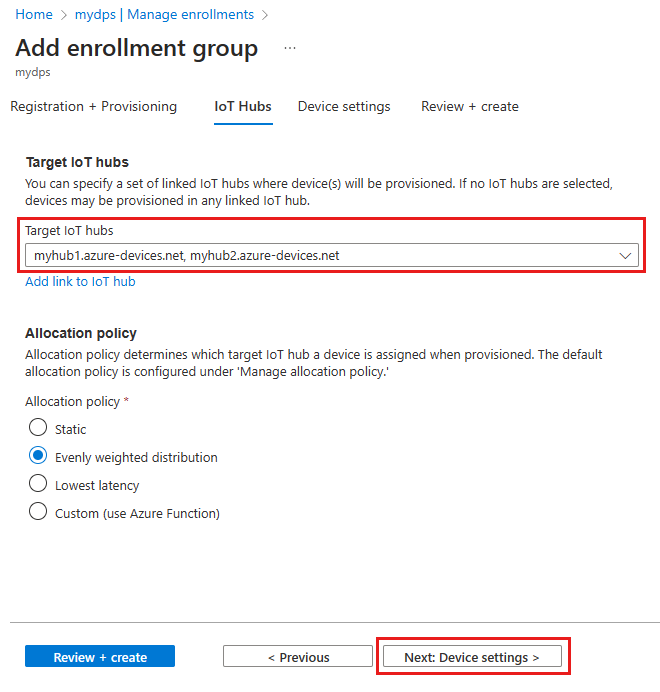
选择“下一步:设备设置”
在“添加注册组”页的“设备设置”选项卡上,提供以下信息来定义如何配置新预配的设备:
字段 说明 IoT Edge 请勾选“在预配设备上启用 IoT Edge”选项,如果此组中预配的所有设备都运行 Azure IoT Edge。 如果此组仅适用于未启用 IoT Edge 的设备,请取消选中此框。 组中的所有设备都已启用 IoT Edge,也可以不启用。 设备标记 使用此文本框可提供要应用于预配设备的设备孪生的任何标记。 所需属性 使用此文本框可提供要应用于预配设备的设备孪生的任何所需属性。 有关详细信息,请参阅了解并在 IoT 中心内使用设备孪生。
在完成时选择“下一步:查看 + 创建”。
在“审阅 + 创建”选项卡上,验证你的全部值,然后选择“创建”。
创建注册组时,DPS 会生成“主密钥”和“辅助密钥”,并将其添加到注册项。 对称密钥注册组显示在“注册组”选项卡的“组名”栏下。
打开注册并复制“主密钥”的值。 此密钥是你的组密钥。
选择设备的唯一注册 ID
必须定义唯一注册 ID 来标识每个设备。 可以使用 MAC 地址、序列号或设备中的任何唯一信息。
在此示例中,我们使用 MAC 地址和序列号的组合,构成以下注册 ID 字符串。
sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6
为每个设备创建唯一的注册 ID。 注册 ID 是一个不区分大小写的字符串(最大长度为 128 个字符),包含字母数字字符和以下特殊字符:- . _ :。 最后一个字符必须是字母数字或短划线 (-)。
派生一个设备密钥
要生成设备密钥,请使用注册组主密钥计算每个设备的注册 ID 的 HMAC-SHA256。 然后,为每个设备将结果转换 Base64 格式。
警告
每个设备的设备代码应该只包含该设备的派生设备密钥。 不要在设备代码中包含组主密钥。 泄露的组密钥可能会危及所有使用该密钥进行身份验证的设备的安全。
Azure CLI 的 IoT 扩展提供了用于生成派生设备密钥的 az iot dps enrollment-group compute-device-key 命令。 该命令可以在基于 Windows 的系统和 Linux 系统上使用。
将 --key 参数值替换为注册组中的主密钥。
将 --registration-id 参数值替换为注册 ID。
az iot dps enrollment-group compute-device-key --key <group_primary_key> --registration-id <device_registration_id>
示例结果:
"Jsm0lyGpjaVYVP2g3FnmnmG9dI/9qU24wNoykUmermc="
每个设备将使用其派生的设备密钥和唯一注册 ID,于预配期间在注册组中执行对称密钥证明。
准备和运行设备预配代码
在本部分,你将更新向设备预配服务实例发送设备启动序列的设备示例代码。 此启动序列使得设备可被识别、完成身份验证并分配到与设备预配服务实例链接的 IoT 中心。
示例预配代码按顺序完成以下任务:
使用以下三个参数通过设备预配资源对你的设备进行身份验证:
- 设备预配服务的 ID 范围
- 设备的注册 ID。
- 设备的派生设备密钥。
将设备分配到已与设备预配服务实例链接的 IoT 中心。
若要使用设备信息更新并运行预配示例,请执行以下操作:
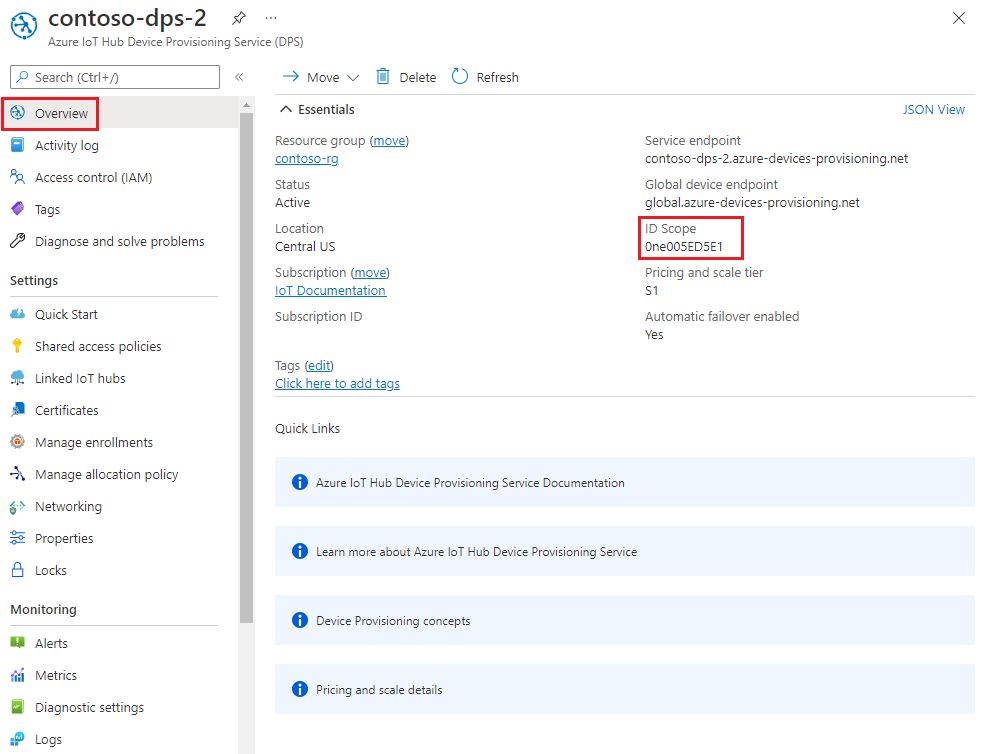
在设备预配服务的主菜单中,选择“概述”。
复制“ID 范围”值。
在 Visual Studio 中,打开通过运行 CMake 生成的 azure_iot_sdks.sln 解决方案文件。 解决方案文件应位于以下位置:
\azure-iot-sdk-c\cmake\azure_iot_sdks.sln提示
如果在 cmake 目录中未生成该文件,请确保使用了最新版本的 CMake 生成系统。
在 Visual Studio 的“解决方案资源管理器”窗口中,转到“Provision_Samples”文件夹。 展开名为“prov_dev_client_sample”的示例项目。 展开“源文件”,打开“prov_dev_client_sample.c”。
找到
id_scope常量,将值替换为你从 Azure 门户复制的“ID 范围”值。static const char* id_scope = "0ne00002193";在同一文件中找到
main()函数的定义。 确保将变量hsm_type设置为SECURE_DEVICE_TYPE_SYMMETRIC_KEY,如以下示例所示:SECURE_DEVICE_TYPE hsm_type; //hsm_type = SECURE_DEVICE_TYPE_TPM; //hsm_type = SECURE_DEVICE_TYPE_X509; hsm_type = SECURE_DEVICE_TYPE_SYMMETRIC_KEY;在“prov_dev_client_sample.c”中,找到已注释掉的对
prov_dev_set_symmetric_key_info()的调用。// Set the symmetric key if using they auth type //prov_dev_set_symmetric_key_info("<symm_registration_id>", "<symmetric_Key>");取消注释该函数调用,并将占位符值(包括尖括号)替换为在选择设备的唯一注册 ID 中选择的注册 ID 以及在派生设备密钥中生成的派生设备密钥。
// Set the symmetric key if using they auth type prov_dev_set_symmetric_key_info("sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6", "Jsm0lyGpjaVYVP2g3FnmnmG9dI/9qU24wNoykUmermc=");注意
此步骤将派生的设备密钥包含在每个设备的映像中,这不是推荐的安全最佳实践。 这是通常需要在安全性与易用性之间进行权衡的原因之一。 你必须根据自己的要求全面检查设备的安全性。
保存文件。
右键单击“prov_dev_client_sample”项目,然后选择“设为启动项目”。
在 Visual Studio 菜单中,选择“调试”“开始执行(不调试)”以运行该解决方案。 在重新生成项目提示中,选择“是”,以便在运行项目之前重新生成项目。
以下输出是设备成功连接到要分配到 IoT 中心的预配服务实例的示例:
Provisioning API Version: 1.9.1 Registering Device Provisioning Status: PROV_DEVICE_REG_STATUS_CONNECTED Provisioning Status: PROV_DEVICE_REG_STATUS_ASSIGNING Registration Information received from service: contoso-hub-2.azure-devices.cn, deviceId: sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6 Press enter key to exit:
示例预配代码完成以下任务:
使用以下三个参数通过设备预配资源对你的设备进行身份验证:
- 设备预配服务的 ID 范围
- 设备的注册 ID。
- 设备的派生设备密钥。
将设备分配到已与设备预配服务实例链接的 IoT 中心。
将测试消息发送到 IoT 中心。
若要使用设备信息更新并运行预配示例,请执行以下操作:
在设备预配服务的主菜单中,选择“概述”。
复制“ID 范围”值。

打开命令提示符,转到克隆的 SDK 存储库中的“SymmetricKeySample”:
cd .\azure-iot-sdk-csharp\provisioning\device\samples\how to guides\SymmetricKeySample在 SymmetricKeySample 文件夹中,在文本编辑器中打开 Parameters.cs 。 此文件显示该示例引用的参数。 运行示例时,本文中仅使用前三个必需的参数。 查看此文件中的代码。 无需任何更改。
参数 必需 说明 --i或--IdScope正确 DPS 实例的 ID 范围 --r或--RegistrationId正确 设备的注册 ID。 注册 ID 是一个不区分大小写的字符串(最大长度为 128 个字符),包含字母数字字符和以下特殊字符: '-'、'.'、'_'、':'。 最后一个字符必须是字母数字或短划线 ('-')。--p或--PrimaryKey正确 单个注册的主密钥或组注册的派生设备密钥。 --g或--GlobalDeviceEndpoint错误 设备要连接到的全局终结点。 默认为 global.azure-devices-provisioning.net--t或--TransportType错误 用于与设备预配实例通信的传输。 默认为 Mqtt。 可能的值包括Mqtt、Mqtt_WebSocket_Only、Mqtt_Tcp_Only、Amqp、Amqp_WebSocket_Only、Amqp_Tcp_only和Http1。在 SymmetricKeySample 文件夹中,在文本编辑器中打开 ProvisioningDeviceClientSample.cs 。 此文件显示 SecurityProviderSymmetricKey 类如何与 ProvisioningDeviceClient 类配合使用来预配模拟的对称密钥设备。 查看此文件中的代码。 无需任何更改。
使用以下命令生成并运行示例代码:
- 将
<id-scope>替换为你从 Azure 门户复制的“ID 范围”。 - 将
<registration-id>替换为在选择设备的唯一注册 ID 中选择的注册 ID。 - 将
<primarykey>替换为生成的派生设备密钥。
dotnet run --i <id-scope> --r <registration-id> --p <primarykey>- 将
应会看到类似于以下输出的内容。 “TestMessage”字符串已作为测试消息发送到中心。
D:\azure-iot-sdk-csharp\provisioning\device\samples\how to guides\SymmetricKeySample>dotnet run --i 0ne00000A0A --r sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6 --p sbDDeEzRuEuGKag+kQKV+T1QGakRtHpsERLP0yPjwR93TrpEgEh/Y07CXstfha6dhIPWvdD1nRxK5T0KGKA+nQ== Initializing the device provisioning client... Initialized for registration Id sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6. Registering with the device provisioning service... Registration status: Assigned. Device sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6 registered to contoso-hub-2.azure-devices.cn. Creating symmetric key authentication for IoT Hub... Testing the provisioned device with IoT Hub... Sending a telemetry message... Finished.
示例预配代码按顺序完成以下任务:
使用以下四个参数通过设备预配资源对你的设备进行身份验证:
PROVISIONING_HOSTPROVISIONING_IDSCOPEPROVISIONING_REGISTRATION_IDPROVISIONING_SYMMETRIC_KEY
将设备分配到已与设备预配服务实例链接的 IoT 中心。
将测试遥测消息发送到 IoT 中心。
若要使用设备信息更新并运行预配示例,请执行以下操作:
在设备预配服务的主菜单中,选择“概述”。
复制“ID 范围”值。

打开命令提示符以执行 Node.js 命令,然后转到以下目录:
cd azure-iot-sdk-node\provisioning\device\samples在“provisioning/device/samples”文件夹中打开“register_symkey.js”并查看代码 。
示例默认使用 MQTT 作为传输协议。 如果要使用不同的协议,请注释掉以下行并取消注释相应协议的行。
var ProvisioningTransport = require('azure-iot-provisioning-device-mqtt').Mqtt;另请注意,示例代码设置了一个自定义有效负载:
provisioningClient.setProvisioningPayload({a: 'b'});可以注释掉此代码,因为本教程不需要这样做。 使用自定义分配 Webhook 将设备分配到 IoT 中心时,可以使用自定义有效负载。 有关详细信息,请参阅教程:使用自定义分配策略。
使用
provisioningClient.register()方法尝试注册设备。在命令提示符中,运行以下命令以设置示例使用的环境变量:
- 第一个命令将
PROVISIONING_HOST环境变量设置为“全局设备终结点”。 对于所有 DPS 实例,此终结点相同。 - 将
<id-scope>替换为你从 Azure 门户复制的“ID 范围”。 - 将
<registration-id>替换为在选择设备的唯一注册 ID 中选择的注册 ID。 - 将
<derived-device-key>替换为在派生设备密钥中生成的派生设备密钥。
set PROVISIONING_HOST=global.azure-devices-provisioning.netset PROVISIONING_IDSCOPE=<id-scope>set PROVISIONING_REGISTRATION_ID=<registration-id>set PROVISIONING_SYMMETRIC_KEY=<derived-device-key>- 第一个命令将
使用以下命令生成并运行示例代码:
npm installnode register_symkey.js现在应会看到类似于以下输出的内容。 “Hello World”字符串已作为测试消息发送到此中心。
registration succeeded assigned hub=contoso-hub-2.azure-devices.cn deviceId=sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6 payload=undefined Client connected send status: MessageEnqueued
示例预配代码按顺序完成以下任务:
使用以下四个参数通过设备预配资源对你的设备进行身份验证:
PROVISIONING_HOSTPROVISIONING_IDSCOPEPROVISIONING_REGISTRATION_IDPROVISIONING_SYMMETRIC_KEY
将设备分配到已与设备预配服务实例链接的 IoT 中心。
将测试消息发送到 IoT 中心。
若要使用设备信息更新并运行预配示例,请执行以下操作:
在设备预配服务的主菜单中,选择“概述”。
复制“ID 范围”值。

打开命令提示符,然后转到 provision_symmetric_key.py 示例文件所在的目录。
cd azure-iot-sdk-python\samples\async-hub-scenarios在命令提示符中,运行以下命令以设置示例使用的环境变量:
- 第一个命令将
PROVISIONING_HOST环境变量设置为“全局设备终结点”。 对于所有 DPS 实例,此终结点相同。 - 将
<id-scope>替换为你从 Azure 门户复制的“ID 范围”。 - 将
<registration-id>替换为在选择设备的唯一注册 ID 中选择的注册 ID。 - 将
<derived-device-key>替换为在派生设备密钥中生成的派生设备密钥。
set PROVISIONING_HOST=global.azure-devices-provisioning.netset PROVISIONING_IDSCOPE=<id-scope>set PROVISIONING_REGISTRATION_ID=<registration-id>set PROVISIONING_SYMMETRIC_KEY=<derived-device-key>- 第一个命令将
通过运行以下命令来安装 azure-iot-device 库。
pip install azure-iot-device运行 provision_symmetric_key.py 中的 Python 示例代码。
python provision_symmetric_key.py现在应会看到类似于以下输出的内容。 一些示例风速遥测消息也已作为测试发送到中心。
D:\azure-iot-sdk-python\samples\async-hub-scenarios>python provision_symmetric_key.py The complete registration result is sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6 contoso-hub-2.azure-devices.cn initialAssignment null Will send telemetry from the provisioned device sending message #1 sending message #2 sending message #3 sending message #4 sending message #5 sending message #6 sending message #7 sending message #8 sending message #9 sending message #10 done sending message #1 done sending message #2 done sending message #3 done sending message #4 done sending message #5 done sending message #6 done sending message #7 done sending message #8 done sending message #9 done sending message #10
示例预配代码按顺序完成以下任务:
使用以下四个参数通过设备预配资源对你的设备进行身份验证:
GLOBAL_ENDPOINTSCOPE_IDREGISTRATION_IDSYMMETRIC_KEY
将设备分配到已与设备预配服务实例链接的 IoT 中心。
将测试消息发送到 IoT 中心。
若要使用设备信息更新并运行预配示例,请执行以下操作:
在设备预配服务的主菜单中,选择“概述”。
复制“ID 范围”值。

打开 Java 设备示例代码进行编辑。 设备示例代码的完整路径为:
azure-iot-sdk-java/provisioning/provisioning-samples/provisioning-symmetrickey-individual-sample/src/main/java/samples/com/microsoft/azure/sdk/iot/ProvisioningSymmetricKeyIndividualEnrollmentSample.java为 DPS 和设备注册设置以下变量的值:
- 将
[Your scope ID here]替换为你从 Azure 门户复制的“ID 范围”。 - 将
[Your Provisioning Service Global Endpoint here]替换为全局设备终结点 global.azure-devices-provisioning.net。 对于所有 DPS 实例,此终结点相同。 - 将
[Enter your Symmetric Key here]替换为在派生设备密钥中生成的派生设备密钥。 - 将
[Enter your Registration ID here]替换为在选择设备的唯一注册 ID 中选择的注册 ID。
private static final String SCOPE_ID = "[Your scope ID here]"; private static final String GLOBAL_ENDPOINT = "[Your Provisioning Service Global Endpoint here]"; private static final String SYMMETRIC_KEY = "[Enter your Symmetric Key here]"; private static final String REGISTRATION_ID = "[Enter your Registration ID here]";注意
此步骤将派生的设备密钥包含在每个设备的映像中,这不是推荐的安全最佳实践。 这是通常需要在安全性与易用性之间进行权衡的原因之一。 你必须根据自己的要求全面检查设备的安全性。
- 将
打开命令提示符进行生成。 转到 Java SDK 存储库的预配示例项目文件夹。
cd azure-iot-sdk-java\provisioning\provisioning-device-client-samples\provisioning-symmetrickey-individual-sample生成示例。
mvn clean install转到
target文件夹,并执行已创建的.jar文件。 在java命令中,将{version}占位符替换为计算机上.jar文件名中的版本。cd target java -jar ./provisioning-symmetrickey-individual-sample-{version}-with-deps.jar现在应会看到类似于以下输出的内容。
Starting... Beginning setup. WARNING: sun.reflect.Reflection.getCallerClass is not supported. This will impact performance. 2022-10-07 18:14:48,388 DEBUG (main) [com.microsoft.azure.sdk.iot.provisioning.device.ProvisioningDeviceClient] - Initialized a ProvisioningDeviceClient instance using SDK version 2.0.2 2022-10-07 18:14:48,390 DEBUG (main) [com.microsoft.azure.sdk.iot.provisioning.device.ProvisioningDeviceClient] - Starting provisioning thread... Waiting for Provisioning Service to register 2022-10-07 18:14:48,392 INFO (global.azure-devices-provisioning.net-002edcf5-CxnPendingConnectionId-azure-iot-sdk-ProvisioningTask) [com.microsoft.azure.sdk.iot.provisioning.device.internal.task.ProvisioningTask] - Opening the connection to device provisioning service... 2022-10-07 18:14:48,518 INFO (global.azure-devices-provisioning.net-002edcf5-Cxn002edcf5-azure-iot-sdk-ProvisioningTask) [com.microsoft.azure.sdk.iot.provisioning.device.internal.task.ProvisioningTask] - Connection to device provisioning service opened successfully, sending initial device registration message 2022-10-07 18:14:48,521 INFO (global.azure-devices-provisioning.net-002edcf5-Cxn002edcf5-azure-iot-sdk-RegisterTask) [com.microsoft.azure.sdk.iot.provisioning.device.internal.task.RegisterTask] - Authenticating with device provisioning service using symmetric key 2022-10-07 18:14:49,252 INFO (global.azure-devices-provisioning.net-002edcf5-Cxn002edcf5-azure-iot-sdk-ProvisioningTask) [com.microsoft.azure.sdk.iot.provisioning.device.internal.task.ProvisioningTask] - Waiting for device provisioning service to provision this device... 2022-10-07 18:14:49,253 INFO (global.azure-devices-provisioning.net-002edcf5-Cxn002edcf5-azure-iot-sdk-ProvisioningTask) [com.microsoft.azure.sdk.iot.provisioning.device.internal.task.ProvisioningTask] - Current provisioning status: ASSIGNING 2022-10-07 18:14:52,459 INFO (global.azure-devices-provisioning.net-002edcf5-Cxn002edcf5-azure-iot-sdk-ProvisioningTask) [com.microsoft.azure.sdk.iot.provisioning.device.internal.task.ProvisioningTask] - Device provisioning service assigned the device successfully IotHUb Uri : contoso-hub-2.azure-devices.cn Device ID : sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6 2022-10-07 18:14:58,424 INFO (main) [com.microsoft.azure.sdk.iot.device.transport.ExponentialBackoffWithJitter] - NOTE: A new instance of ExponentialBackoffWithJitter has been created with the following properties. Retry Count: 2147483647, Min Backoff Interval: 100, Max Backoff Interval: 10000, Max Time Between Retries: 100, Fast Retry Enabled: true 2022-10-07 18:14:58,436 INFO (main) [com.microsoft.azure.sdk.iot.device.transport.ExponentialBackoffWithJitter] - NOTE: A new instance of ExponentialBackoffWithJitter has been created with the following properties. Retry Count: 2147483647, Min Backoff Interval: 100, Max Backoff Interval: 10000, Max Time Between Retries: 100, Fast Retry Enabled: true 2022-10-07 18:14:58,440 DEBUG (main) [com.microsoft.azure.sdk.iot.device.DeviceClient] - Initialized a DeviceClient instance using SDK version 2.1.1 2022-10-07 18:14:58,450 DEBUG (main) [com.microsoft.azure.sdk.iot.device.transport.mqtt.MqttIotHubConnection] - Opening MQTT connection... 2022-10-07 18:14:58,471 DEBUG (main) [com.microsoft.azure.sdk.iot.device.transport.mqtt.Mqtt] - Sending MQTT CONNECT packet... 2022-10-07 18:14:59,314 DEBUG (main) [com.microsoft.azure.sdk.iot.device.transport.mqtt.Mqtt] - Sent MQTT CONNECT packet was acknowledged 2022-10-07 18:14:59,315 DEBUG (main) [com.microsoft.azure.sdk.iot.device.transport.mqtt.Mqtt] - Sending MQTT SUBSCRIBE packet for topic devices/sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6/messages/devicebound/# 2022-10-07 18:14:59,378 DEBUG (main) [com.microsoft.azure.sdk.iot.device.transport.mqtt.Mqtt] - Sent MQTT SUBSCRIBE packet for topic devices/sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6/messages/devicebound/# was acknowledged 2022-10-07 18:14:59,379 DEBUG (main) [com.microsoft.azure.sdk.iot.device.transport.mqtt.MqttIotHubConnection] - MQTT connection opened successfully 2022-10-07 18:14:59,381 DEBUG (main) [com.microsoft.azure.sdk.iot.device.transport.IotHubTransport] - The connection to the IoT Hub has been established 2022-10-07 18:14:59,383 DEBUG (main) [com.microsoft.azure.sdk.iot.device.transport.IotHubTransport] - Updating transport status to new status CONNECTED with reason CONNECTION_OK 2022-10-07 18:14:59,389 DEBUG (main) [com.microsoft.azure.sdk.iot.device.DeviceIO] - Starting worker threads 2022-10-07 18:14:59,392 DEBUG (main) [com.microsoft.azure.sdk.iot.device.transport.IotHubTransport] - Invoking connection status callbacks with new status details 2022-10-07 18:14:59,395 DEBUG (main) [com.microsoft.azure.sdk.iot.device.transport.IotHubTransport] - Client connection opened successfully 2022-10-07 18:14:59,404 INFO (main) [com.microsoft.azure.sdk.iot.device.DeviceClient] - Device client opened successfully Sending message from device to IoT Hub... 2022-10-07 18:14:59,408 DEBUG (main) [com.microsoft.azure.sdk.iot.device.transport.IotHubTransport] - Message was queued to be sent later ( Message details: Correlation Id [aaaa0000-bb11-2222-33cc-444444dddddd] Message Id [aaaa0000-bb11-2222-33cc-444444dddddd] ) Press any key to exit... 2022-10-07 18:14:59,409 DEBUG (contoso-hub-2.azure-devices.cn-sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6-c32c76d0-Cxn0e70bbf7-8476-441d-8626-c17250585ee6-azure-iot-sdk-IotHubSendTask) [com.microsoft.azure.sdk.iot.device.transport.IotHubTransport] - Sending message ( Message details: Correlation Id [aaaa0000-bb11-2222-33cc-444444dddddd] Message Id [aaaa0000-bb11-2222-33cc-444444dddddd] ) 2022-10-07 18:14:59,777 DEBUG (MQTT Call: sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6) [com.microsoft.azure.sdk.iot.device.transport.IotHubTransport] - IotHub message was acknowledged. Checking if there is record of sending this message ( Message details: Correlation Id [aaaa0000-bb11-2222-33cc-444444dddddd] Message Id [aaaa0000-bb11-2222-33cc-444444dddddd] ) 2022-10-07 18:14:59,779 DEBUG (contoso-hub-2.azure-devices.cn-sn-007-888-abc-mac-a1-b2-c3-d4-e5-f6-c32c76d0-Cxn0e70bbf7-8476-441d-8626-c17250585ee6-azure-iot-sdk-IotHubSendTask) [com.microsoft.azure.sdk.iot.device.transport.IotHubTransport] - Invoking the callback function for sent message, IoT Hub responded to message ( Message details: Correlation Id [aaaa0000-bb11-2222-33cc-444444dddddd] Message Id [aaaa0000-bb11-2222-33cc-444444dddddd] ) with status OK Message received! Response status: OK
确认设备预配注册
本教程使用“静态配置”分配策略将通过注册组注册的设备分配到同一 IoT 中心。 但是,对于可将设备预配到多个 IoT 中心之一的分配,可以检查注册组的注册记录,以查看设备预配到的 IoT 中心:
在 Azure 门户中转到 DPS 实例。
在“设置”菜单中,选择“管理注册” 。
选择“注册组”。
选择为本教程创建的注册组。
在“注册组详细信息”页上,选择“注册状态”。
查找设备“设备 ID”列的设备 ID,并记下“已分配的 IoT 中心”列中的 IoT 中心。
可以选择该设备记录以查看更多详细信息,例如分配给设备的初始孪生。
若要验证 IoT 中心上的设备,请执行以下操作:
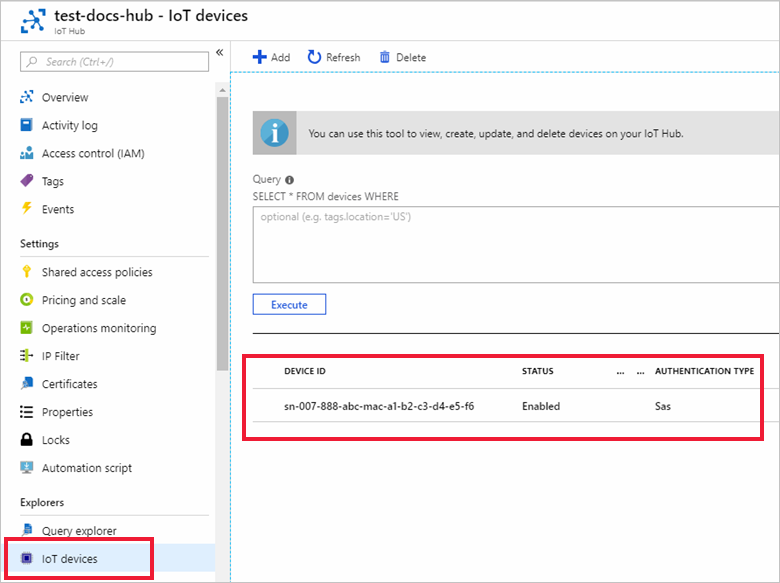
在 Azure 门户中,转到设备分配到的 IoT 中心。
在“设备管理”菜单中选择“设备”。
如果设备预配成功,设备 ID 应显示在列表中,其状态设为“已启用”。 如果未看到你的设备,请选择“刷新”。
注意
如果从注册组中的默认值更改了“初始设备孪生状态”,则它会从中心拉取所需的孪生状态,并执行相应的操作。 有关详细信息,请参阅了解并在 IoT 中心内使用设备孪生。
预配更多设备
若要通过注册组预配更多设备,请按照上述部分中的步骤操作:
清理资源
如果打算继续使用和探索设备客户端示例,请不要清理在本教程中创建的资源。 如果不打算继续学习,请通过以下步骤删除本教程中创建的所有资源。
删除注册组
删除注册组不会删除与之关联的注册记录。 这些孤立记录会计入 DPS 实例的注册配额。 因此,最好先删除与注册组关联的所有注册记录,然后再删除注册组本身。
在 Azure 门户中转到 DPS 实例。
在“设置”菜单中,选择“管理注册” 。
选择“注册组”选项卡。
选择用于本教程的注册组的名称,以打开其详细信息页。
在“注册详细信息”页上,选择“注册状态”。 然后选中“设备 ID”列标题旁边的复选框,以选择注册组的所有注册记录。 选择页面顶部的“删除”以删除注册记录。
返回“管理注册”页。
选中在本教程中使用的注册组组名旁边的复选框。
在页面顶部,选择“删除”。
从 IoT 中心删除设备注册
在 Azure 门户中,转到设备分配到的 IoT 中心。
从导航菜单的“设备管理”部分中选择“设备”。
选中在本教程中注册的设备的设备 ID 旁边的复选框。
在页面顶部,选择“删除”。
后续步骤
在本教程中,你已使用注册组将多个设备预配到 单个 IoT 中心。 接下来了解如何跨多个中心预配 IoT 设备。