适用范围: Azure CLI ml 扩展 v2(最新版)
Azure CLI ml 扩展 v2(最新版) Python SDK azure-ai-ml v2(最新版)
Python SDK azure-ai-ml v2(最新版)
提示
可以使用 Azure 机器学习托管虚拟网络,而不是执行本文中的步骤。 使用托管虚拟网络,Azure 机器学习可处理工作区和托管计算的网络隔离作业。 还可以为工作区所需的资源(例如 Azure 存储帐户)添加专用终结点。 有关详细信息,请参阅工作区托管网络隔离。
本文中介绍如何在 Azure 虚拟网络中保护 Azure 机器学习工作区及其关联资源。
本文是介绍如何保护 Azure 机器学习工作流系列文章的一部分。 请参阅本系列中的其他文章:
有关创建安全工作区的教程,请参阅教程:创建安全工作区、Bicep 模板或 Terraform 模板。
本文介绍如何在虚拟网络中启用以下工作区资源:
- Azure 机器学习工作区
- Azure 存储帐户
- Azure Key Vault
- Azure 容器注册表
先决条件
阅读网络安全概述一文,了解常见的虚拟网络方案和总体虚拟网络体系结构。
请阅读 Azure 机器学习之企业安全最佳实践一文,了解最佳做法。
用于计算资源的现有虚拟网络和子网。
警告
请勿对 VNet 使用 172.17.0.0/16 IP 地址范围。 此范围是 Docker 网桥网络使用的默认子网范围。 将它用于 VNet 会导致错误。 其他范围可能也会根据要连接到虚拟网络的内容而发生冲突。 例如,如果您计划将本地网络连接到 VNet,且本地网络也使用 172.16.0.0/16 范围。 最终,规划网络基础结构。
若要将资源部署到虚拟网络或子网中,你的用户帐户必须在 Azure 基于角色的访问控制 (Azure RBAC) 中具有以下操作的权限:
- 虚拟网络资源上的“Microsoft.Network/*/read”。 对于 Azure 资源管理器 (ARM) 模板部署,不需要此权限。
- “Microsoft.Network/virtualNetworks/join/action”(在虚拟网络资源上)。
- "Microsoft.Network/virtualNetworks/subnets/join/action"(在子网资源上)。
若要详细了解如何将 Azure RBAC 与网络配合使用,请参阅网络内置角色
Azure 容器注册表
Azure 容器注册表必须是高级版。 若要详细了解如何升级,请参阅更改 SKU。
如果 Azure 容器注册表使用 专用终结点,请将其置于与存储帐户和用于训练或推理的计算目标相同的 虚拟网络 中。 但是,它也可以位于 对等互连 的虚拟网络中。
如果它使用服务终结点,则它必须与存储帐户和计算目标在同一虚拟网络和子网中。
Azure 机器学习工作区必须包含 Azure 机器学习计算群集。
限制
Azure 存储帐户
如果计划使用 Azure 机器学习工作室并且存储帐户也在虚拟网络中,则存在额外的验证要求:
- 如果存储帐户使用服务终结点,则工作区专用终结点和存储服务终结点必须位于虚拟网络的同一子网中。
- 如果存储帐户使用专用终结点,则工作区专用终结点和存储专用终结点必须位于同一虚拟网络中。 在这种情况下,它们可以位于不同的子网中。
Azure 容器实例
使用专用终结点配置 Azure 机器学习工作区时,不支持部署到虚拟网络中的 Azure 容器实例。 相反,请考虑使用具有网络隔离的托管联机终结点。
Azure 容器注册表
使用专用终结点配置 Azure 机器学习工作区或任何资源时,可能需要为 Azure 机器学习环境映像生成设置用户托管计算群集。 默认方案利用 无服务器计算 ,目前适用于对与 Azure 机器学习工作区关联的资源没有网络限制的方案。
重要
用于生成 Docker 映像的计算群集需要访问用于训练和部署模型的包存储库。 你可能需要添加允许访问公用存储库、使用专用 Python 包,或使用已包含该包的自定义 Docker 映像 (SDK v1) 的网络安全规则。
自带虚拟网络(BYO VNet)配置不支持通过工作区连接使用专用 Azure 容器注册表来拉取映像。 若要使用专用 ACR,请将其配置为工作区的默认附加 ACR,并遵循 “启用 Azure 容器注册表”(ACR) 部分中的准则。
Azure Monitor
警告
Azure Monitor 支持使用 Azure 专用链接连接到 VNet。 但是,你必须在 Azure Monitor 中使用开放专用链接模式。 有关更多信息,请参阅专用链接访问模式:专用与开放。
必需的公共互联网访问
Azure 机器学习需要对公共 Internet 进行入站和出站访问。 下表概述了需要的访问权限及其用途。 对于以 .region 结尾的服务标记,请将 region 替换为包含你的工作区的 Azure 区域。 例如,Storage.chinanorth:
提示
“必需”选项卡列出了必需的入站和出站配置。 “特定情况”选项卡列出了可能要启用的特定配置所需的可选入站和出站配置。
| 方向 | 协议和 港口 |
服务标记 | 目的 |
|---|---|---|---|
| 出站 | TCP:80、443 | AzureActiveDirectory |
使用 Microsoft Entra ID 进行身份验证。 |
| 出站 | TCP:443、18881 UDP:5831 |
AzureMachineLearning |
使用 Azure 机器学习服务。 笔记本中的 Python Intellisense 使用端口 18881。 创建、更新和删除 Azure 机器学习计算实例时使用端口 5831。 |
| 出站 | 任意:443 | BatchNodeManagement.region |
与 Azure 机器学习计算实例/群集的 Azure Batch 后端系统进行通信。 |
| 出站 | TCP:443 | AzureResourceManager |
使用 Azure 机器学习、Azure CLI 和 Azure 机器学习 SDK 创建 Azure 资源。 |
| 出站 | TCP:443 | Storage.region |
访问存储在 Azure 存储帐户中、用于计算群集和计算实例的数据。 有关防止数据通过此出站外泄的信息,请参阅数据外泄保护。 |
| 出站 | TCP:443 |
AzureFrontDoor.FrontEnd
* 在由世纪互联运营的 Azure 中不需要。 |
Azure 机器学习工作室的全球入口点。 为 AutoML 存储图像和环境。 有关防止数据通过此出站外泄的信息,请参阅数据外泄保护。 |
| 出站 | TCP:443 |
MicrosoftContainerRegistry.region
注意:此标记依赖于 AzureFrontDoor.FirstParty 标记 |
访问由 Microsoft 提供的 Docker 镜像。 为 Azure Kubernetes 服务设置 Azure 机器学习路由器。 |
提示
如果需要 IP 地址而不是服务标记,请使用下列选项之一:
- 从 Azure IP 范围和服务标记下载列表。
- 使用 Azure CLI az network list-service-tags 命令。
- 使用 Azure PowerShell Get-AzNetworkServiceTag 命令。
IP 地址可能会定期改变。
可能还需要允许出站流量发往 Visual Studio Code 和非 Microsoft 站点,以便安装机器学习项目所需的包。 下表列出了用于机器学习的常用存储库:
| 主机名 | 目的 |
|---|---|
anaconda.com*.anaconda.com |
用于安装默认包。 |
*.anaconda.org |
用于获取存储库数据。 |
pypi.org |
用于列出默认索引的依赖项(如果有),索引不会被用户设置覆盖。 如果索引被覆盖,则还必须允许 *.pythonhosted.org。 |
cloud.r-project.org |
在安装用于 R 开发的 CRAN 包时使用。 |
*.pytorch.org |
被一些基于 PyTorch 的示例使用。 |
*.tensorflow.org |
一些基于 TensorFlow 的示例使用了它。 |
code.visualstudio.com |
必需下载和安装 Visual Studio Code 桌面版。 Visual Studio Code Web 不需要。 |
update.code.visualstudio.com*.vo.msecnd.net |
用于检索通过安装脚本安装在计算实例上的 Visual Studio Code 服务器组件。 |
marketplace.visualstudio.comvscode.blob.core.chinacloudapi.cn*.gallerycdn.vsassets.io |
安装和下载 Visual Studio Code 的扩展是必须的。 这些主机启用了通过适用于 Visual Studio Code 的 Azure ML 扩展提供的计算实例的远程连接。 有关详细信息,请参阅在 Visual Studio Code 中连接到 Azure 机器学习计算实例。 |
raw.githubusercontent.com/microsoft/vscode-tools-for-ai/master/azureml_remote_websocket_server/* |
用于检索安装在计算实例上的 WebSocket 服务器组件。 websocket 服务器用于将来自 Visual Studio Code 客户端(桌面应用程序)的请求传输到计算实例上运行的 Visual Studio Code 服务器。 |
注意事项
使用 Azure 机器学习 VS Code 扩展时,远程计算实例需要访问公共存储库才能安装该扩展所需的包。 如果计算实例需要代理来访问这些公共存储库或 Internet,则需要在计算实例的 HTTP_PROXY 文件中设置和导出 HTTPS_PROXY 和 ~/.bashrc 环境变量。 可以使用自定义脚本在预配时自动执行此过程。
将 Azure Kubernetes Service (AKS) 与 Azure 机器学习一起使用时,请允许将以下流量发送到 AKS VNet:
- AKS 的一般入站/出站要求,如限制 Azure Kubernetes 服务中的出口流量一文中所述。
- 发往 mcr.microsoft.com 的出站流量。
- 将模型部署到 AKS 群集时,请遵循将 ML 模型部署到 Azure Kubernetes 服务一文中的指导。
有关使用防火墙解决方案的信息,请参阅配置所需的输入和输出通信。
通过专用终结点保护工作区
Azure 专用链接允许使用专用终结点连接到工作区。 专用终结点是虚拟网络中的一组专用 IP 地址。 然后,你可以限制工作区访问权限,只允许通过专用 IP 地址访问你的工作区。 专用终结点有助于降低数据泄露风险。
有关为工作区配置专用终结点的信息,请参阅如何配置专用终结点。
警告
使用专用终结点保护工作区并不能确保端到端安全性。 必须按照本文其余部分的步骤和 VNet 系列中的步骤进行操作,以确保解决方案中各个组件的安全。 例如,如果对工作区使用专用终结点,但 Azure 存储帐户不在 VNet 后面,则工作区和存储之间的流量不会使用 VNet 来保护。
保护 Azure 存储帐户
Azure 机器学习支持将存储帐户配置为使用专用终结点或服务终结点。
在 Azure 门户中,选择 Azure 存储帐户。
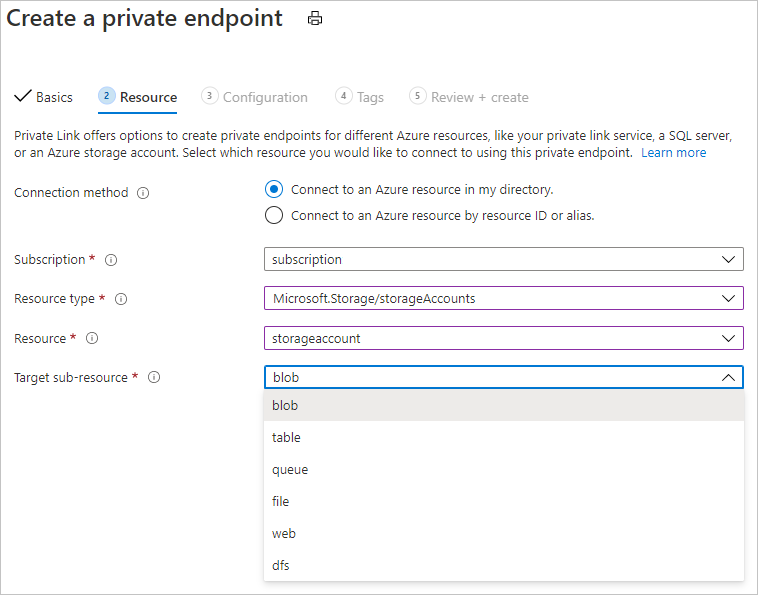
使用 Azure 存储的专用终结点中的信息,为以下存储资源添加专用终结点:
- Blob
- 文件
- 队列 - 仅当你计划在 Azure 机器学习管道中使用 Batch 终结点或 ParallelRunStep 时才需要。
- 表 - 仅当你计划在 Azure 机器学习管道中使用 Batch 终结点或 ParallelRunStep 时才需要。
提示
配置不是默认存储的存储帐户时,请选择与要添加的存储帐户对应的 目标子资源 类型。
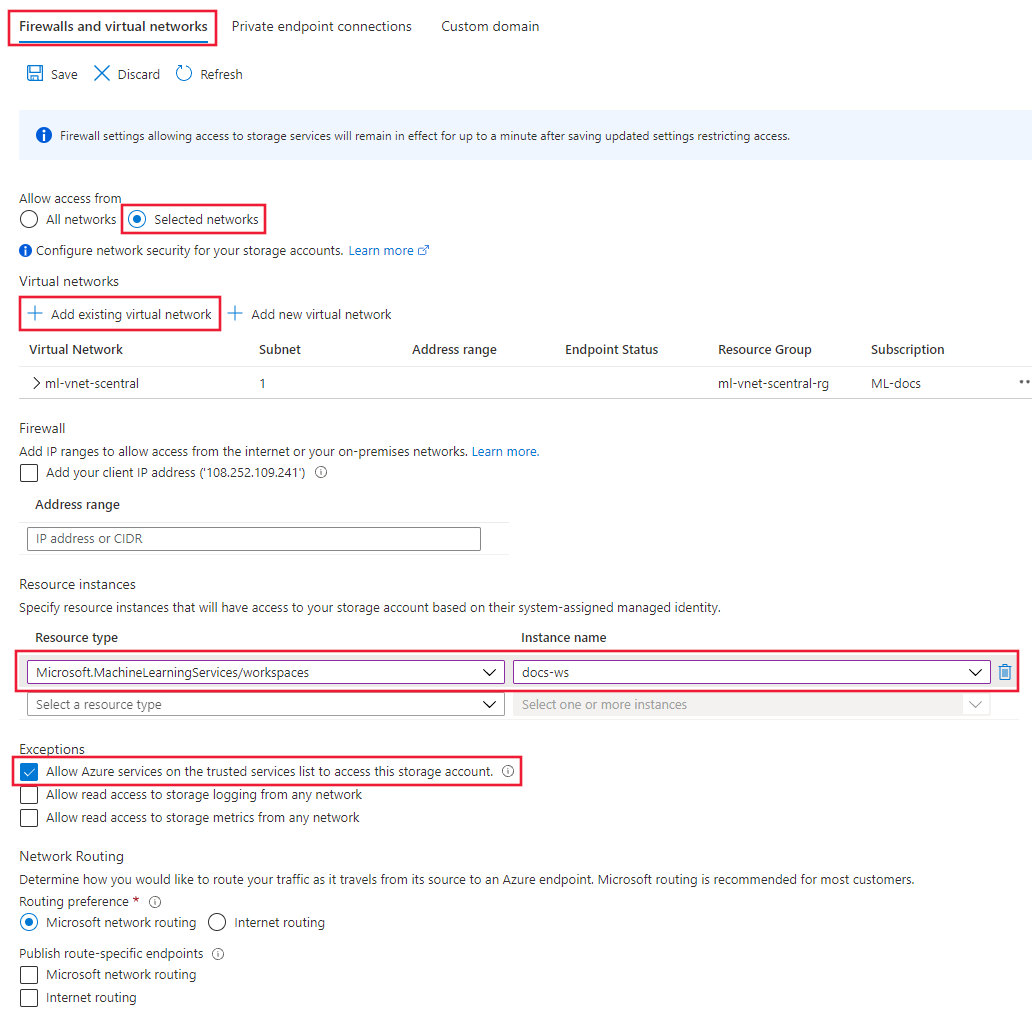
为存储资源创建专用终结点后,请在“存储帐户”的“网络”下选择“防火墙和虚拟网络”选项卡。
选择“所选网络”,然后在“资源实例”下选择
Microsoft.MachineLearningServices/Workspace作为资源类型。 使用“实例名称”选择工作区。 有关更多信息,请参阅基于系统分配的托管标识的受信任访问。提示
或者,可以选择“允许受信任服务列表中的 Azure 服务访问此存储帐户”,以便更广泛地允许来自受信任服务的访问。 有关详细信息,请参阅配置 Azure 存储防火墙和虚拟网络。
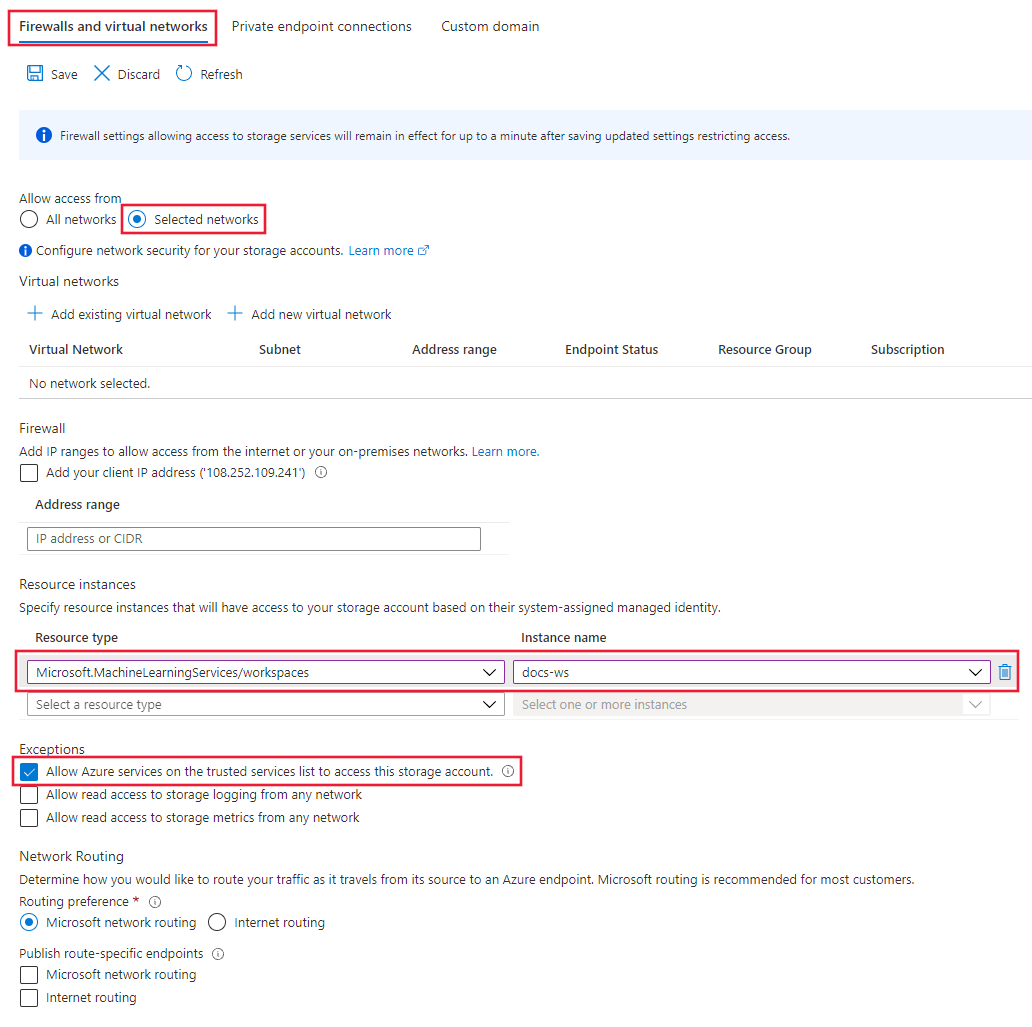
选择“保存”以保存配置。
提示
在使用专用终结点时,还可禁用匿名访问。 有关详细信息,请参阅禁止匿名访问。
保护 Azure Key Vault
Azure 机器学习使用关联的 Key Vault 实例存储以下凭据:
- 关联的存储帐户连接字符串
- Azure 容器注册表实例的密码
- 数据存储的连接字符串
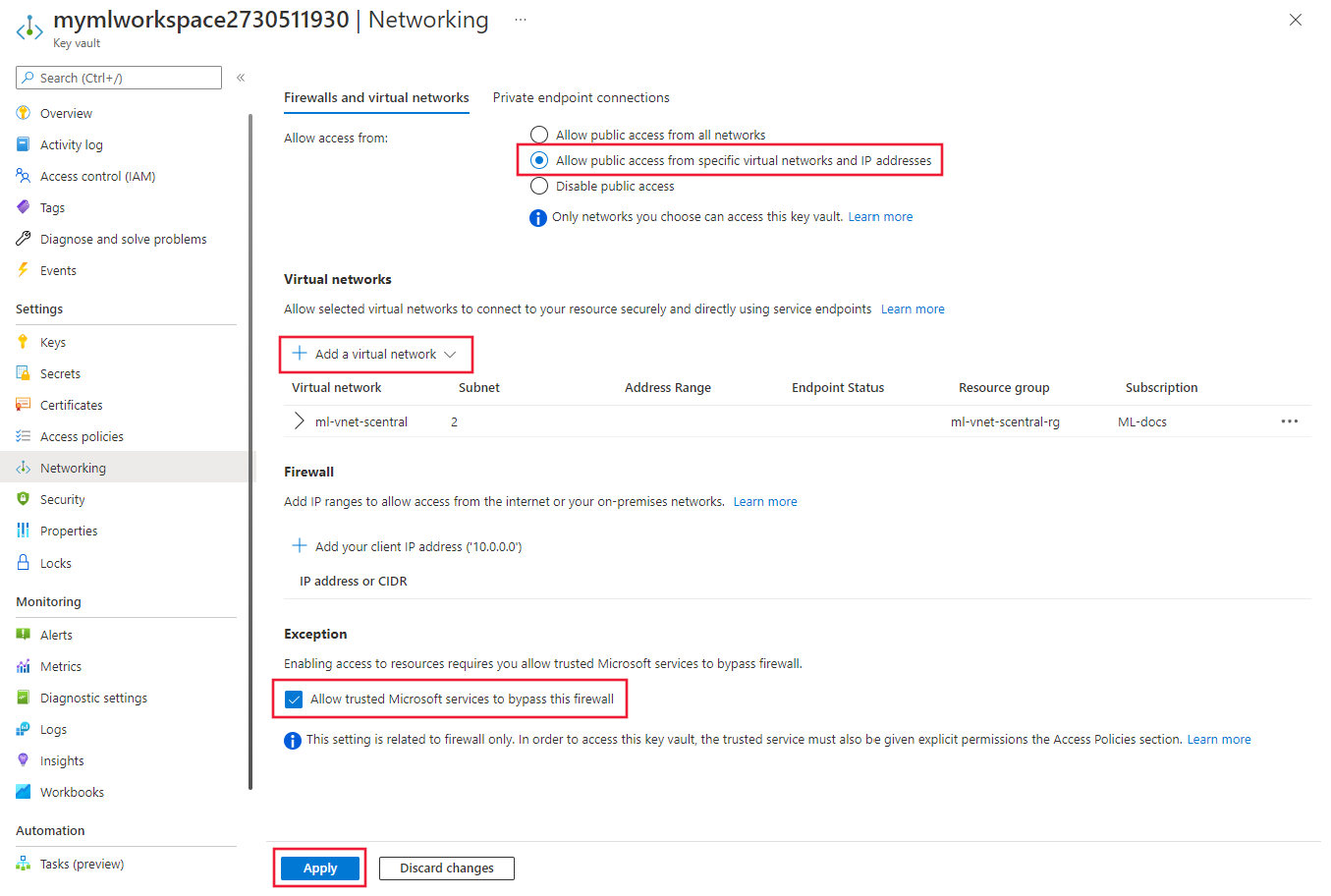
可以将 Azure 密钥保管库配置为使用专用终结点或服务终结点。 若要在虚拟网络的后面将 Azure 机器学习试验功能与 Azure Key Vault 配合使用,请执行以下步骤:
提示
密钥保管库应与工作区位于同一虚拟网络中,但它可以位于 对等互连 的虚拟网络中。
有关将专用终结点与 Azure Key Vault 结合使用的信息,请参阅将密钥保管库与 Azure 专用链接集成。
启用 Azure 容器注册表 (ACR)
提示
如果在创建工作区时未使用现有的 Azure 容器注册表,则可能不存在。 默认情况下,工作区在需要 ACR 实例之前不会创建 ACR 实例。 若要强制创建一个模型,请在使用本部分中的步骤之前使用工作区训练或部署模型。
可以将 Azure 容器注册表配置为使用专用终结点。 使用以下步骤配置工作区以便在虚拟网络中使用 ACR:
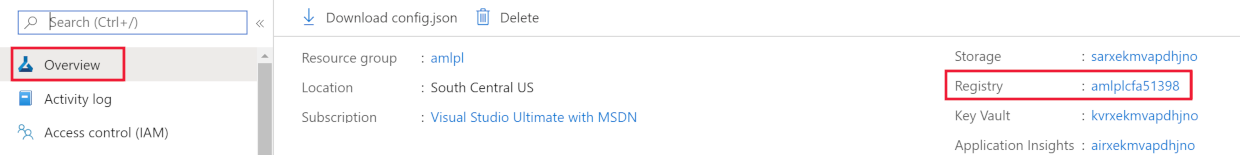
使用以下方法之一查找工作区的 Azure 容器注册表的名称:
如果 为 Azure CLI 安装了机器学习扩展 v2,请使用
az ml workspace show该命令显示工作区信息。 v1 扩展不返回此信息。az ml workspace show -n yourworkspacename -g resourcegroupname --query 'container_registry'此命令会返回类似于
"/subscriptions/{GUID}/resourceGroups/{resourcegroupname}/providers/Microsoft.ContainerRegistry/registries/{ACRname}"的值。 此字符串的最后一部分是工作区的 Azure 容器注册表的名称。使用 专用连接到 Azure 容器注册表中的步骤限制对虚拟网络的访问。 添加虚拟网络时,为 Azure 机器学习资源选择虚拟网络和子网。
将工作区的 ACR 配置为允许受信任的服务进行访问。
默认情况下,Azure 机器学习会尝试使用 无服务器计算 来生成映像。 仅当依赖于工作区的资源(例如存储帐户或容器注册表)不受任何网络限制(专用终结点)时,此方法才有效。 如果限制对依赖于工作区的资源的网络访问,请改用映像生成计算。
要设置映像生成计算,请在依赖于工作区的资源所在的 VNet 中创建 Azure 机器学习 CPU SKU 计算群集。 可以将此群集设置为默认的映像生成计算。 它从该点之后开始生成工作区中的每个镜像。 使用以下方法之一配置工作区,以使用计算群集生成 Docker 映像。
重要
将计算群集用于映像生成时,以下限制适用:
- 仅支持 CPU SKU。
- 如果使用配置为无公共 IP 地址的计算群集,则必须为群集提供某种方法来访问公共 Internet。 访问存储在 Microsoft 容器注册表上的映像、Pypi、Conda 上安装的包以及类似的存储库时,需要 Internet 访问。 需要将用户定义的路由(UDR)配置为访问公共 IP 以访问 Internet。 例如,可以使用防火墙的公共 IP,也可以将虚拟网络 NAT 与公共 IP 配合使用。 有关详细信息,请参阅如何安全地在 VNet 中训练。
使用
az ml workspace update命令设置构建计算。 对于机器学习的 v1 和 v2 Azure CLI 扩展,此命令的功能相同。 在以下命令中,将myworkspace替换为工作区名称,将myresourcegroup替换为包含工作区的资源组,将mycomputecluster替换为计算群集名称:az ml workspace update --name myworkspace --resource-group myresourcegroup --image-build-compute mycomputecluster可以通过运行相同的命令并将计算引用为空空间来切换回无服务器计算:
--image-build-compute ''
提示
当 ACR 位于虚拟网络后面时,还可以 禁用对该虚拟网络的公共访问 。
保护 Azure Monitor 和 Application Insights
若要为 Azure Monitor 和工作区的 Application Insights 实例启用网络隔离,请执行以下步骤:
在 Azure 门户中打开 Application Insights 资源。 “ 概述 ”选项卡可能具有工作区属性。 如果它没有该属性,请执行步骤 2。 如果是这样,则可以直接转到步骤 3。
提示
默认情况下,新工作区会创建基于工作区的 Application Insights 资源。 如果最近创建了工作区,则无需执行步骤 2。
升级工作区的 Application Insights 实例。 有关如何升级的步骤,请参阅迁移到基于工作区的 Application Insights 资源。
创建 Azure Monitor 专用链接范围,并将步骤 1 中的 Application Insights 实例添加到该范围。 有关详细信息,请参阅配置 Azure Monitor 专用链接。
安全连接到工作区
若要连接到 VNet 后面保护的工作区,请使用以下方法之一:
Azure VPN 网关 - 通过专用连接将本地网络连接到 VNet。 通过公共 Internet 建立连接。 可以使用两种类型的 VPN 网关:
ExpressRoute - 通过专用连接将本地网络连接到云。 通过连接提供商建立连接。
Azure Bastion - 在此方案中,你将在 VNet 内部创建 Azure 虚拟机(有时称作 Jump Box)。 然后使用 Azure Bastion 连接到 VM。 Bastion 允许在本地 Web 浏览器中使用 RDP 或 SSH 会话连接到 VM。 然后使用 Jump Box 作为开发环境。 由于它位于 VNet 中,因此可以直接访问工作区。 有关使用 Jump Box 的示例,请参阅教程:创建安全工作区。
重要
使用“VPN 网关”或“ExpressRoute”时,需要规划本地资源与 VNet 中资源之间名称解析的工作方式 。 有关详细信息,请参阅使用自定义 DNS 服务器。
如果在连接到工作区时遇到问题,请参阅排查安全工作区连接问题。
工作区诊断
在 Azure 机器学习工作室或 Python SDK 中,可以在工作区上运行诊断。 运行诊断后,将返回检测到的任何问题的列表。 此列表包含指向可能的解决方案的链接。 有关详细信息,请参阅如何使用工作区诊断。
对工作区的公共访问
重要
尽管 Azure 机器学习支持此配置,但Microsoft不建议这样做。 在生产环境中使用该配置之前,请与安全团队验证此配置。
在某些情况下,可能需要允许从公用网络访问工作区(无需使用安全连接到工作区部分详述的方法通过虚拟网络进行连接)。 使用 TLS 保护通过公共 Internet 的访问。
若要实现通过公共网络访问工作区,请采用以下步骤:
- 在配置工作区的专用终结点后,启用对工作区的公共访问。
- 配置 Azure 存储防火墙,以允许与通过公共 Internet 连接的客户端的 IP 地址通信。 如果客户端没有静态 IP,则可能需要更改允许的 IP 地址。 例如,如果一位数据科学家在家办公,并且无法与 VNet 建立 VPN 连接。
后续步骤
本文是介绍如何保护 Azure 机器学习工作流系列文章的一部分。 请参阅本系列中的其他文章: