Azure 存储对静态存储帐户中的所有数据进行加密。 默认情况下,数据使用 Microsoft 管理的密钥进行加密。 若要更进一步控制加密密钥,你可以管理自己的密钥。 客户管理的密钥必须存储在 Azure Key Vault 中。
本文介绍当存储帐户和密钥保管库位于同一租户时,如何使用客户管理的密钥为现有存储帐户配置加密。 客户管理的密钥将存储在密钥保管库中。
若要了解如何为新存储帐户配置客户管理的密钥,请参阅在 Azure 密钥保管库中为新存储帐户配置客户管理的密钥。
你可以使用新的或现有的密钥保管库来存储客户管理的密钥。 存储帐户和密钥保管库可能在同一租户的不同区域或订阅中。 若要了解有关 Azure Key Vault 的详细信息,请参阅 Azure Key Vault 概述和什么是 Azure Key Vault?。
使用带有 Azure 存储加密的客户管理的密钥需要为密钥保管库启用软删除和清除保护。 创建新密钥保管库时,默认会启用软删除,并且无法禁用。 你可以在创建密钥保管库时或创建后启用清除保护。
Azure Key Vault 支持通过 Azure RBAC 权限模型使用 Azure RBAC 进行授权。 Azure 建议对密钥保管库访问策略使用 Azure RBAC 权限模型。 有关详细信息,请参阅使用 Azure RBAC 授予应用程序访问 Azure 密钥保管库的权限。
若要了解如何使用 Azure 门户创建密钥保管库,请参阅快速入门:使用 Azure 门户创建密钥保管库。 创建密钥保管库时,选择“启用清除保护”,如下图所示。
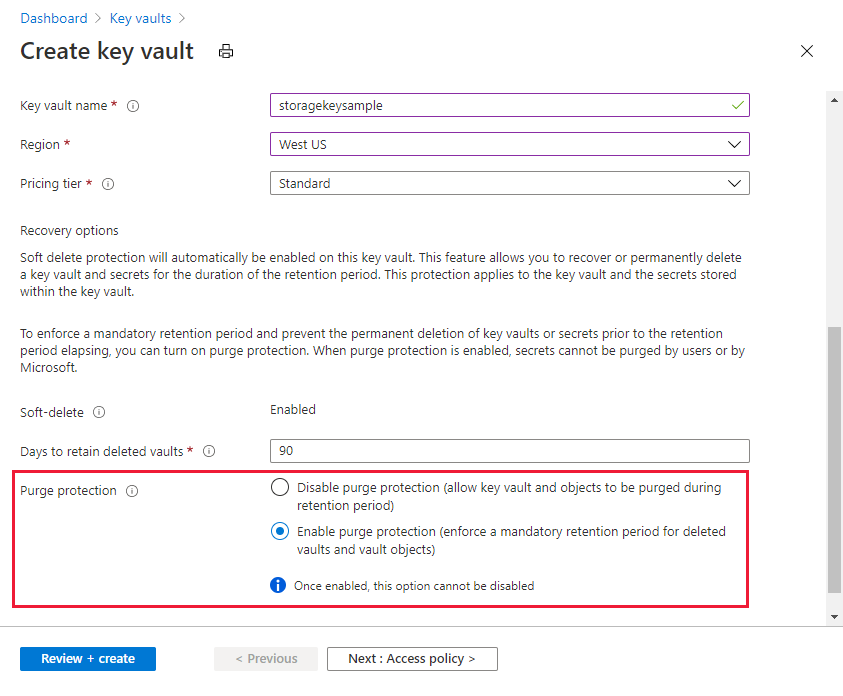
若要在现有密钥保管库上启用清除保护,请执行以下步骤:
- 在 Azure 门户中导航到密钥保管库。
- 在“设置”下面,选择“属性”。
- 在“清除保护”部分,选择“启用清除保护” 。
若要使用 PowerShell 创建新密钥保管库,请安装 Az.KeyVault PowerShell 模块的版本 2.0.0 或更高版本。 然后调用 New-AzKeyVault 来创建新密钥保管库。 在 Az.KeyVault 模块的版本 2.0.0 和更高版本中,当创建新密钥保管库时,默认会启用软删除。
以下示例创建一个启用了软删除和清除保护的新密钥保管库。 密钥保管库的权限模型设置为使用 Azure RBAC。 请记得将括号中的占位符值替换为你自己的值。
$rgName = "<resource_group>"
$location = "<location>"
$kvName = "<key-vault>"
$keyVault = New-AzKeyVault -Name $kvName `
-ResourceGroupName $rgName `
-Location $location `
-EnablePurgeProtection `
-EnableRbacAuthorization
若要了解如何使用 PowerShell 对现有密钥保管库启用清除保护,请参阅 Azure Key Vault 恢复概述。
创建密钥保管库后,你需要将“密钥保管库加密管理人员”角色分配给自己。 使用此角色可以在密钥保管库中创建密钥。 以下示例将此角色分配给用户,范围限定为密钥保管库:
New-AzRoleAssignment -SignInName "<user-email>" `
-RoleDefinitionName "Key Vault Crypto Officer" `
-Scope $keyVault.ResourceId
若要详细了解如何使用 PowerShell 来分配 RBAC 角色,请参阅使用 Azure PowerShell 分配 Azure 角色。
若要使用 Azure CLI 创建新的 Key Vault,请调用 az keyvault create。 以下示例创建一个启用了软删除和清除保护的新密钥保管库。 密钥保管库的权限模型设置为使用 Azure RBAC。 请记得将括号中的占位符值替换为你自己的值。
rgName="<resource_group>"
location="<location>"
kvName="<key-vault>"
az keyvault create \
--name $kvName \
--resource-group $rgName \
--location $location \
--enable-purge-protection \
--enable-rbac-authorization
若要了解如何使用 Azure CLI 对现有密钥保管库启用清除保护,请参阅 Azure Key Vault 恢复概述。
创建密钥保管库后,你需要将“密钥保管库加密管理人员”角色分配给自己。 使用此角色可以在密钥保管库中创建密钥。 以下示例将此角色分配给用户,范围限定为密钥保管库:
kvResourceId=$(az keyvault show --resource-group $rgName \
--name $kvName \
--query id \
--output tsv)
az role assignment create --assignee "<user-email>" \
--role "Key Vault Crypto Officer" \
--scope $kvResourceId
若要详细了解如何使用 Azure CLI 分配 RBAC 角色,请参阅使用 Azure CLI 分配 Azure 角色。
添加密钥
接下来,在密钥保管库中添加密钥。 在添加密钥之前,请确保已将“密钥保管库加密管理人员”角色分配给自己。
Azure 存储加密支持 2048、3072 和 4096 大小的 RSA 密钥。 有关支持的密钥类型详细信息,请参阅关于密钥。
若要使用 PowerShell 添加密钥,请调用 Add-AzKeyVaultKey。 请记得将括号中的占位符值替换为自己的值,并使用前面示例中定义的变量。
$keyName = "<key-name>"
$key = Add-AzKeyVaultKey -VaultName $keyVault.VaultName `
-Name $keyName `
-Destination 'Software'
若要使用 Azure CLI 添加密钥,请调用 az keyvault key create。 请记得将括号中的占位符值替换为你自己的值。
keyName="<key-name>"
az keyvault key create \
--name $keyName \
--vault-name $kvName
选择托管标识授予对密钥保管库的访问权限
为现有存储帐户启用客户管理的密钥时,必须指定一个托管标识,用于授权访问密钥所在的密钥保管库。 托管标识必须有权访问密钥保管库中的密钥。
授权访问密钥保管库的托管标识可能是用户分配的托管标识或系统分配的托管标识。 若要详细了解系统分配的托管标识和用户分配的托管标识,请参阅托管标识类型。
使用用户分配的托管标识授予访问权限
为新存储帐户启用客户管理的密钥时,必须指定用户分配的托管标识。 现有存储帐户支持使用用户分配的托管标识或系统分配的托管标识来配置客户管理的密钥。
使用用户分配的托管标识配置客户管理的密钥时,用户分配的托管标识用来授予对包含密钥的密钥保管库的访问权限。 在配置客户管理的密钥之前,必须创建用户分配的标识。
用户分配的托管标识是独立的 Azure 资源。 若要详细了解用户分配的托管标识,请参阅托管标识类型。 若要了解如何创建和管理用户分配的托管标识,请参阅管理用户分配的托管标识。
用户分配的托管标识必须具有访问密钥保管库中的此密钥的权限。 将“密钥保管库加密服务加密用户”角色分配给用户分配的托管标识(范围是密钥保管库),以授予这些权限。
必须先将“密钥保管库加密服务加密用户”角色分配给用户分配的托管标识(范围是密钥保管库),然后才能使用用户分配的托管标识配置客户管理的密钥。 此角色授予用户分配的托管标识访问密钥保管库中的密钥的权限。 若要详细了解如何使用 Azure 门户分配 Azure RBAC 角色,请参阅使用 Azure 门户分配 Azure 角色。
使用 Azure 门户配置客户管理的密钥时,可以通过门户用户界面选择现有的用户分配的标识。
以下示例显示了如何检索用户分配的托管标识并向其分配所需的 RBAC 角色(范围是密钥保管库)。 请记得将括号中的占位符值替换为自己的值,并使用前面示例中定义的变量:
$userIdentity = Get-AzUserAssignedIdentity -Name <user-assigned-identity> `
-ResourceGroupName $rgName
$principalId = $userIdentity.PrincipalId
New-AzRoleAssignment -ObjectId $principalId `
-RoleDefinitionName "Key Vault Crypto Service Encryption User" `
-Scope $keyVault.ResourceId
以下示例显示了如何检索用户分配的托管标识并向其分配所需的 RBAC 角色(范围是密钥保管库)。 请记得将括号中的占位符值替换为自己的值,并使用前面示例中定义的变量:
identityResourceId=$(az identity show --name <user-assigned-identity> \
--resource-group $rgName \
--query id \
--output tsv)
principalId=$(az identity show --name <user-assigned-identity> \
--resource-group $rgName \
--query principalId \
--output tsv)
az role assignment create --assignee-object-id $principalId \
--role "Key Vault Crypto Service Encryption User" \
--scope $kvResourceId \
--assignee-principal-type ServicePrincipal
使用系统分配的托管标识授予访问权限
系统分配的托管标识与 Azure 服务的实例(在本例中为 Azure 存储帐户)相关联。 必须先将系统分配的托管标识显式分配给存储帐户,才能使用系统分配的托管标识来授权访问客户管理的密钥所在的密钥保管库。
只有现有存储帐户可以使用系统分配的标识来授权访问密钥保管库。 如果在创建帐户时配置客户管理的密钥,则新存储帐户必须使用用户分配的标识。
系统分配的托管标识必须拥有访问密钥保管库中的密钥的权限。 将“密钥保管库加密服务加密用户”角色分配给范围是密钥保管库的系统分配的托管标识,以授予这些权限。
必须先将“密钥保管库加密服务加密用户”角色分配给系统分配的托管标识(范围是密钥保管库),然后才能使用系统分配的托管标识配置客户管理的密钥。 此角色授予系统分配的托管标识访问密钥保管库中的密钥的权限。 若要详细了解如何使用 Azure 门户分配 Azure RBAC 角色,请参阅使用 Azure 门户分配 Azure 角色。
使用系统分配的托管标识在 Azure 门户中配置客户管理的密钥时,系统会在后台将系统分配的托管标识分配给存储帐户。
若要将系统分配的托管标识分配给存储帐户,请先调用 Set-AzStorageAccount:
$accountName = "<storage-account>"
$storageAccount = Set-AzStorageAccount -ResourceGroupName $rgName `
-Name $accountName `
-AssignIdentity
接下来,为系统分配的托管标识分配所需的 RBAC 角色(范围是密钥保管库)。 请记得将括号中的占位符值替换为自己的值,并使用前面示例中定义的变量:
$principalId = $storageAccount.Identity.PrincipalId
New-AzRoleAssignment -ObjectId $storageAccount.Identity.PrincipalId `
-RoleDefinitionName "Key Vault Crypto Service Encryption User" `
-Scope $keyVault.ResourceId
若要使用系统分配的托管标识来验证对密钥保管库的访问,请先通过调用 az storage account update 将系统分配的托管标识分配给存储帐户:
accountName="<storage-account>"
az storage account update \
--name $accountName \
--resource-group $rgName \
--assign-identity
接下来,为系统分配的托管标识分配所需的 RBAC 角色(范围是密钥保管库)。 请记得将括号中的占位符值替换为自己的值,并使用前面示例中定义的变量:
principalId=$(az storage account show --name $accountName \
--resource-group $rgName \
--query identity.principalId \
--output tsv)
az role assignment create --assignee-object-id $principalId \
--role "Key Vault Crypto Service Encryption User" \
--scope $kvResourceId
使用客户管理的密钥为现有存储帐户配置加密时,只要关联的密钥保管库中有新版本可用,就可以选择自动更新用于 Azure 存储加密的密钥版本。 也可显式指定在手动更新密钥版本之前用于加密的密钥版本。
更改密钥版本时,无论是自动还是手动更改,根加密密钥的保护都会更改,但 Azure 存储帐户中的数据始终保持加密状态。 无需执行更多操作即可确保数据受到保护。 轮换密钥版本不会影响性能。 轮换密钥版本不会造成关联性故障时间。
为现有存储帐户配置客户管理的密钥时,可以使用系统分配的或用户分配的托管标识来授权访问密钥保管库。
Azure 存储可以自动更新客户管理的密钥(用于加密),以使用密钥库中的最新密钥版本。 Azure 存储每天都会在密钥保管库中检查是否有密钥的新版本。 新版本可用时,Azure 存储会自动开始使用最新版本的密钥进行加密。
重要
Azure 存储每天只会在密钥保管库中检查一次是否存在密钥的新版本。 轮换密钥时,请务必等待 24 小时,然后再禁用旧版本。
若要在 Azure 门户中通过自动更新密钥版本为现有帐户配置客户管理的密钥,请执行以下步骤:
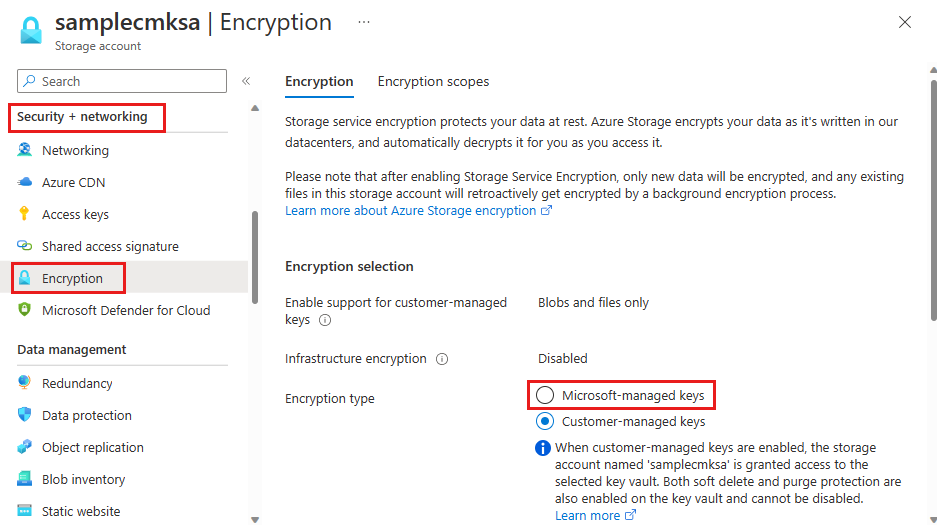
导航到存储帐户。
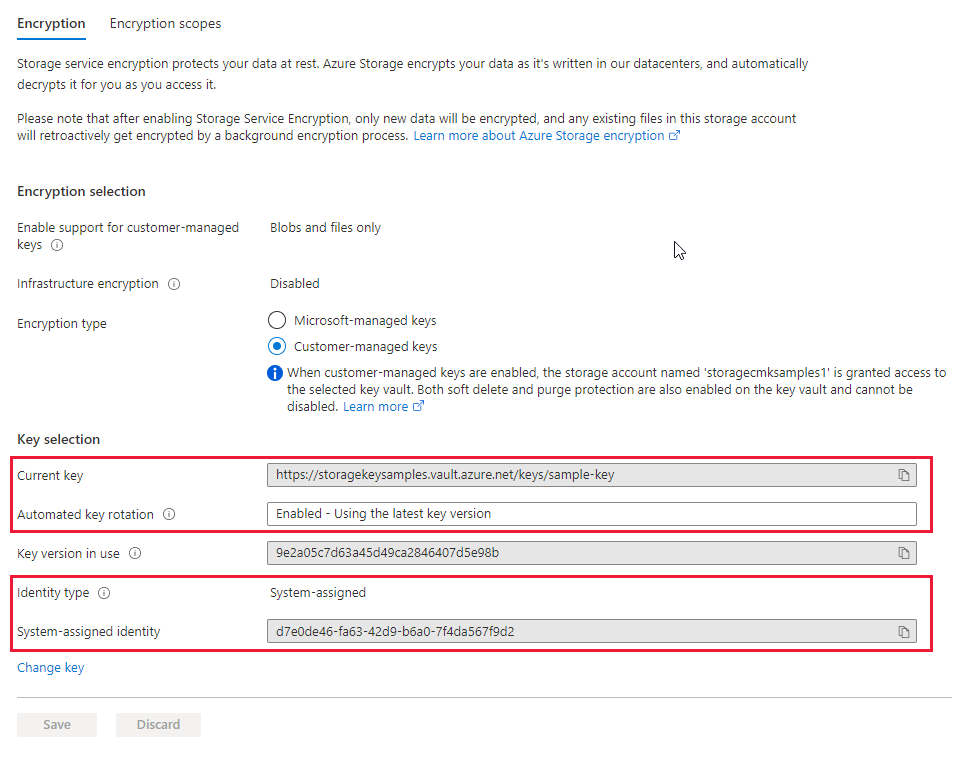
在“安全 + 网络”下,选择“加密”。 默认情况下,密钥管理设置为“Microsoft 管理的密钥”,如下图所示:
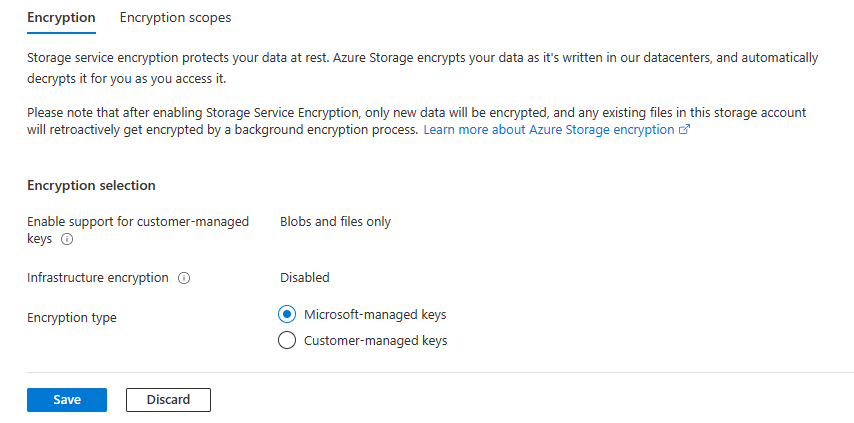
选择“客户管理的密钥”选项。 如果帐户之前已针对“客户管理的密钥”配置了手动更新密钥版本的功能,请选择页面底部附近的“更改密钥”。
选择“从 Key Vault 中选择”选项。
选择“选择密钥保管库和密钥”。
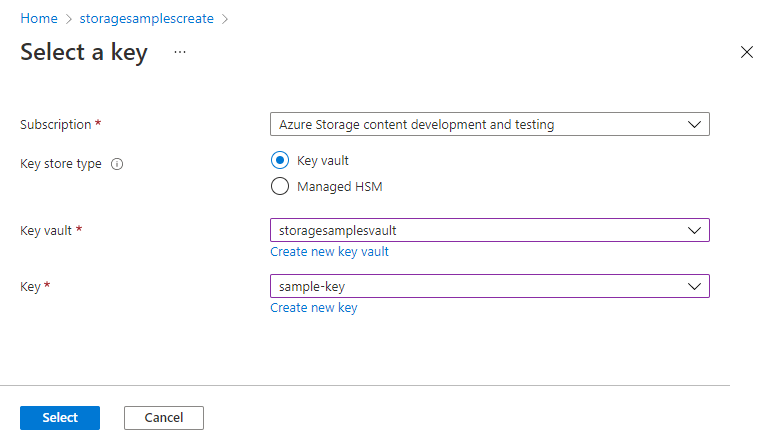
选择包含要使用的密钥的密钥保管库。 你还可以创建新的密钥保管库。
从密钥保管库中选择密钥。 还可以创建新密钥。
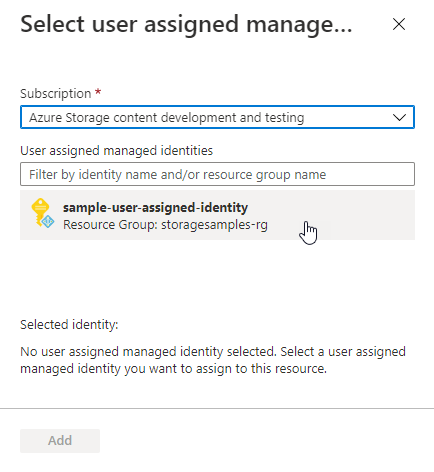
选择用于验证对密钥保管库的访问的标识的类型。 选项包括系统分配(默认)或用户分配 。 若要详细了解每种类型的托管标识,请参阅托管标识类型。
- 如果选择“系统分配”,则将在后台创建存储帐户的系统分配的托管标识(如果尚不存在)。
- 如果选择“用户分配”,则必须选择有权访问密钥保管库的现有用户分配标识。 若要了解如何创建用户分配的标识,请参阅管理用户分配的托管标识。
保存所做更改。
指定密钥后,Azure 门户会指示启用密钥版本的自动更新,并显示当前用于加密的密钥版本。 门户还显示用于授权访问密钥保管库的托管标识的类型和托管标识的主体 ID。
若要使用 PowerShell 通过自动更新密钥版本为现有帐户配置客户管理的密钥,请安装 Az.Storage 模块 2.0.0 或更高版本。
接下来,调用 Set-AzStorageAccount 以更新存储帐户的加密设置。 包括 KeyvaultEncryption 参数,以便为存储帐户启用客户管理的密钥,并将 KeyVersion 设置为空字符串以启用自动更新密钥版本的功能。 如果之前已为具有特定密钥版本的客户管理的密钥配置存储帐户,则将密钥版本设置为空字符串后,会启用在将来自动更新密钥版本的功能。
$accountName = "<storage-account>"
# Use this form of the command with a user-assigned managed identity.
Set-AzStorageAccount -ResourceGroupName $rgName `
-AccountName $accountName `
-IdentityType SystemAssignedUserAssigned `
-UserAssignedIdentityId $userIdentity.Id `
-KeyvaultEncryption `
-KeyVaultUri $keyVault.VaultUri `
-KeyName $key.Name `
-KeyVersion "" `
-KeyVaultUserAssignedIdentityId $userIdentity.Id
# Use this form of the command with a system-assigned managed identity.
Set-AzStorageAccount -ResourceGroupName $rgName `
-AccountName $accountName `
-KeyvaultEncryption `
-KeyName $key.Name `
-KeyVersion "" `
-KeyVaultUri $keyVault.VaultUri
若要使用 Azure CLI 通过自动更新密钥版本为现有帐户配置客户管理的密钥,请安装 Azure CLI 2.4.0 或更高版本。 有关详细信息,请参阅安装 Azure CLI。
接下来,调用 az storage account update 以更新存储帐户的加密设置。 包括 --encryption-key-source 参数并将它设置为 Microsoft.Keyvault 以便为帐户启用客户管理的密钥,同时将 encryption-key-version 设置为空字符串以启用自动更新密钥版本的功能。 如果之前已为具有特定密钥版本的客户管理的密钥配置存储帐户,则将密钥版本设置为空字符串后,会启用在将来自动更新密钥版本的功能。
accountName="<storage-account>"
keyVaultUri=$(az keyvault show \
--name $kvName \
--resource-group $rgName \
--query properties.vaultUri \
--output tsv)
# Use this form of the command with a user-assigned managed identity.
az storage account update \
--name $accountName \
--resource-group $rgName \
--identity-type SystemAssigned,UserAssigned \
--user-identity-id $identityResourceId \
--encryption-key-name $keyName \
--encryption-key-version "" \
--encryption-key-source Microsoft.Keyvault \
--encryption-key-vault $keyVaultUri \
--key-vault-user-identity-id $identityResourceId
# Use this form of the command with a system-assigned managed identity.
az storage account update \
--name $accountName \
--resource-group $rgName \
--encryption-key-name $keyName \
--encryption-key-version "" \
--encryption-key-source Microsoft.Keyvault \
--encryption-key-vault $keyVaultUri
如果希望手动更新密钥版本,请在使用客户管理的密钥配置加密时显式指定该版本。 在这种情况下,在密钥保管库中创建新版本时,Azure 存储不会自动更新密钥版本。 若要使用新的密钥版本,必须手动更新用于 Azure 存储加密的版本。
若要在 Azure 门户中配置客户管理的密钥并手动更新密钥版本,请指定密钥 URI,包括版本。 若要将某个密钥指定为 URI,请执行下列步骤:
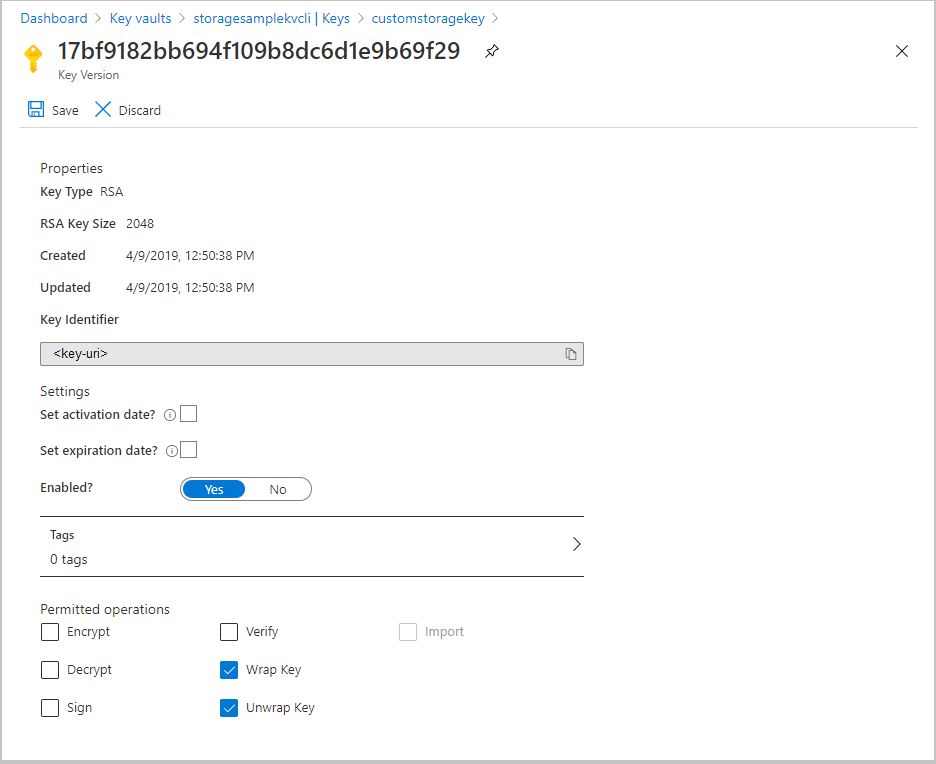
若要在 Azure 门户中查找密钥 URI,请导航到 Key Vault,然后选择“密钥”设置。 选择所需的密钥,然后选择该密钥以查看其版本。 选择一个密钥版本,查看该版本的设置。
复制“密钥标识符”字段的值(提供 URI)。
在存储帐户的“加密密钥”设置中,选择“输入密钥 URI”选项。
将复制的 URI 粘贴到“密钥 URI”字段中。 从 URI 中省略密钥版本,以启用自动更新密钥版本。
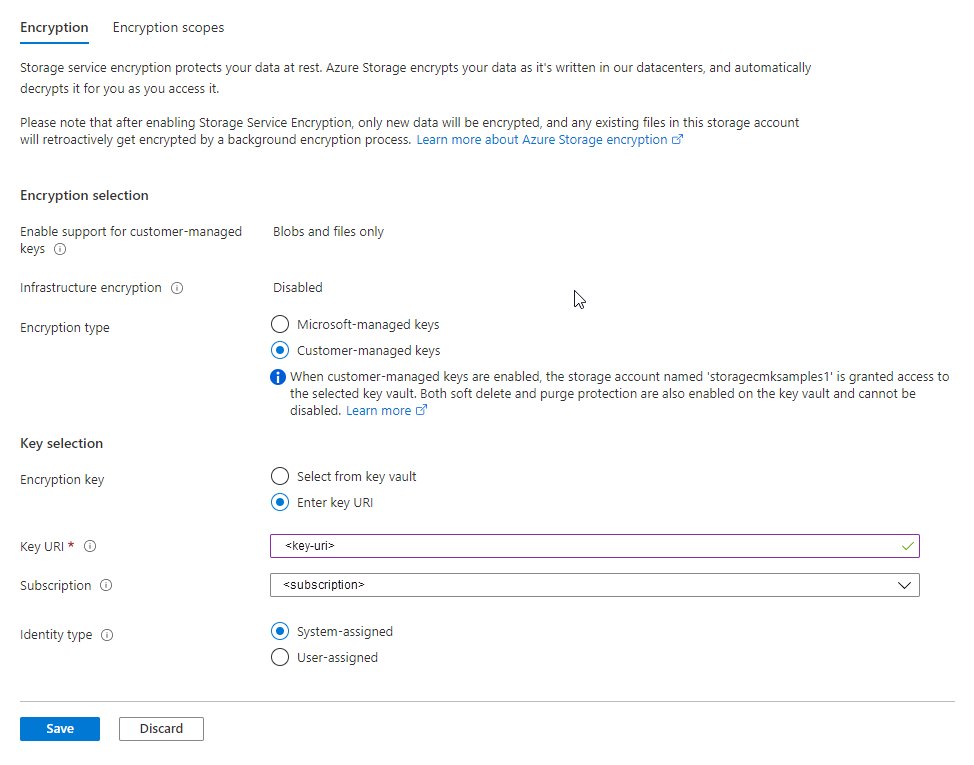
指定包含密钥保管库的订阅。
指定系统分配或用户分配的托管标识。
保存所做更改。
若要配置客户管理的密钥并手动更新密钥版本,请在为存储帐户配置加密时显式提供密钥版本。 调用 AzStorageAccount 以更新存储帐户的加密设置(如以下示例所示),并包含 -KeyvaultEncryption 选项,以便为存储帐户启用客户管理的密钥。
请记得将括号中的占位符值替换为自己的值,并使用前面示例中定义的变量。
$accountName = "<storage-account>"
# Use this form of the command with a user-assigned managed identity.
Set-AzStorageAccount -ResourceGroupName $rgName `
-AccountName $accountName `
-IdentityType SystemAssignedUserAssigned `
-UserAssignedIdentityId $userIdentity.Id `
-KeyvaultEncryption `
-KeyVaultUri $keyVault.VaultUri `
-KeyName $key.Name `
-KeyVersion $key.Version `
-KeyVaultUserAssignedIdentityId $userIdentity.Id
# Use this form of the command with a system-assigned managed identity.
Set-AzStorageAccount -ResourceGroupName $rgName `
-AccountName $accountName `
-KeyvaultEncryption `
-KeyVaultUri $keyVault.VaultUri `
-KeyName $key.Name `
-KeyVersion $key.Version
手动更新密钥版本时,需要更新存储帐户的加密设置以使用新版本。 首先调用 Get-AzKeyVaultKey 以获取最新密钥版本。 然后调用 Set-AzStorageAccount 来更新存储帐户的加密设置,以使用该密钥的新版本,如前面示例所示。
若要配置客户管理的密钥并手动更新密钥版本,请在为存储帐户配置加密时显式提供密钥版本。 请调用 az storage account update,以便更新存储帐户的加密设置,如以下示例所示。 包括 --encryption-key-source 参数并将其设置为 Microsoft.Keyvault 即可为帐户启用客户管理的密钥。
请记得将括号中的占位符值替换为你自己的值。
accountName="<storage-account>"
keyVaultUri=$(az keyvault show \
--name $kvName \
--resource-group $rgName \
--query properties.vaultUri \
--output tsv)
keyVersion=$(az keyvault key list-versions \
--name $keyName \
--vault-name $kvName \
--query [-1].kid \
--output tsv | cut -d '/' -f 6)
# Use this form of the command with a user-assigned managed identity
az storage account update \
--name $accountName \
--resource-group $rgName \
--identity-type SystemAssigned,UserAssigned \
--user-identity-id $identityResourceId \
--encryption-key-name $keyName \
--encryption-key-version $keyVersion \
--encryption-key-source Microsoft.Keyvault \
--encryption-key-vault $keyVaultUri \
--key-vault-user-identity-id $identityResourceId
# Use this form of the command with a system-assigned managed identity
az storage account update \
--name $accountName \
--resource-group $rgName \
--encryption-key-name $keyName \
--encryption-key-version $keyVersion \
--encryption-key-source Microsoft.Keyvault \
--encryption-key-vault $keyVaultUri
手动更新密钥版本时,需要更新存储帐户的加密设置以使用新版本。 首先,通过调用 az keyvault show 查询 Key Vault URI,并通过调用 az keyvault key list-versions 查询密钥版本。 然后调用 az storage account update 来更新存储帐户的加密设置,以使用新的密钥版本,如上一示例所示。
更改密钥
你可以在任何时候更改用于 Azure 存储加密的密钥。
注意
更改密钥或密钥版本时,根加密密钥的保护会更改,但是 Azure 存储帐户中的数据将始终保持加密状态。 无需执行其他操作即可确保数据受到保护。 更改密钥或轮换密钥版本不会影响性能。 更改密钥或轮换密钥版本不会造成关联性故障时间。
若要使用 Azure 门户更改密钥,请执行以下步骤:
- 导航到你的存储帐户,并显示“加密”设置。
- 选择密钥保管库并选择一个新密钥。
- 保存所做更改。
如果新密钥位于其他密钥保管库中,则必须向托管标识授予对新保管库中密钥的访问权限。 如果选择手动更新密钥版本,则还需要更新密钥保管库 URI。
撤销对使用客户管理的密钥的存储帐户的访问权限
若要暂时撤销对使用客户管理的密钥的存储帐户的访问权限,请禁用密钥保管库中当前使用的密钥。 禁用和重新启用密钥不会对性能造成影响或导致停机。
在禁用密钥之后,客户端将无法调用在 Blob 或其元数据中进行读取或写入的操作。 有关哪些操作将会失败的信息,请参阅撤销对使用客户管理的密钥的存储帐户的访问权限。
注意
禁用密钥保管库中的密钥时,Azure 存储帐户中的数据将保持加密状态,但在重新启用密钥之前,这些数据将无法访问。
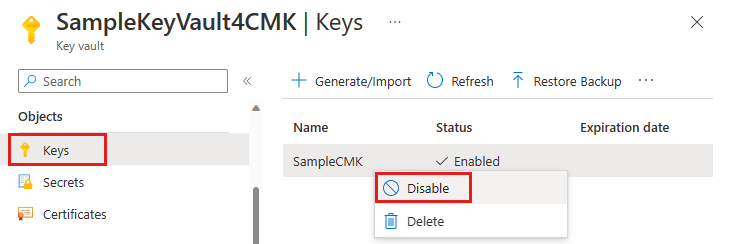
若要使用 Azure 门户禁用客户管理的密钥,请执行以下步骤:
导航到包含该密钥的密钥保管库。
选择“对象”下的“密钥”。
右键单击密钥并选择“禁用”。
若要使用 PowerShell 撤销客户管理的密钥,请调用 Update-AzKeyVaultKey 命令,如以下示例所示。 请记得将括号中的占位符值替换为自己的值以定义变量,或使用前面示例中定义的变量。
$kvName = "<key-vault-name>"
$keyName = "<key-name>"
$enabled = $false
# $false to disable the key / $true to enable it
# Check the current state of the key (before and after enabling/disabling it)
Get-AzKeyVaultKey -Name $keyName -VaultName $kvName
# Disable (or enable) the key
Update-AzKeyVaultKey -VaultName $kvName -Name $keyName -Enable $enabled
若要使用 Azure CLI 撤销客户管理的密钥,请调用 az keyvault key set-attributes 命令,如以下示例所示。 请记得将括号中的占位符值替换为自己的值以定义变量,或使用前面示例中定义的变量。
kvName="<key-vault-name>"
keyName="<key-name>"
enabled="false"
# "false" to disable the key / "true" to enable it:
# Check the current state of the key (before and after enabling/disabling it)
az keyvault key show \
--vault-name $kvName \
--name $keyName
# Disable (or enable) the key
az keyvault key set-attributes \
--vault-name $kvName \
--name $keyName \
--enabled $enabled
切换回 Microsoft 托管密钥
可以使用 Azure 门户、PowerShell 或 Azure CLI 随时从客户管理的密钥切换回 Microsoft 管理的密钥。
若要在 Azure 门户中从客户管理的密钥切换回 Microsoft 管理的密钥,请执行以下步骤:
导航到存储帐户。
在“安全 + 网络”下,选择“加密”。
将“加密类型”更改为“Microsoft 管理的密钥”。
若要使用 PowerShell 从客户管理的密钥切换回 Microsoft 管理的密钥,请使用 选项调用 -StorageEncryption,如以下示例所示。 请记得将括号中的占位符值替换为自己的值,并使用前面示例中定义的变量。
Set-AzStorageAccount -ResourceGroupName $storageAccount.ResourceGroupName `
-AccountName $storageAccount.StorageAccountName `
-StorageEncryption
若要使用 Azure CLI 从客户管理的密钥切换回 Microsoft 管理的密钥,请调用 az storage account update 并将 --encryption-key-source parameter 设置为 Microsoft.Storage,如以下示例所示。 请记得将括号中的占位符值替换为自己的值,并使用前面示例中定义的变量。
az storage account update \
--name <storage-account> \
--resource-group <resource_group> \
--encryption-key-source Microsoft.Storage
后续步骤








