本文将向你介绍如何使用虚拟 WAN 和 Azure 防火墙规则和筛选器来管理对通过点到站点 IKEv2 或 OpenVPN 连接到 Azure 中资源的连接的安全访问。 如果某些远程用户要限制对 Azure 资源的访问或保护 Azure 中资源的安全,此配置非常有用。
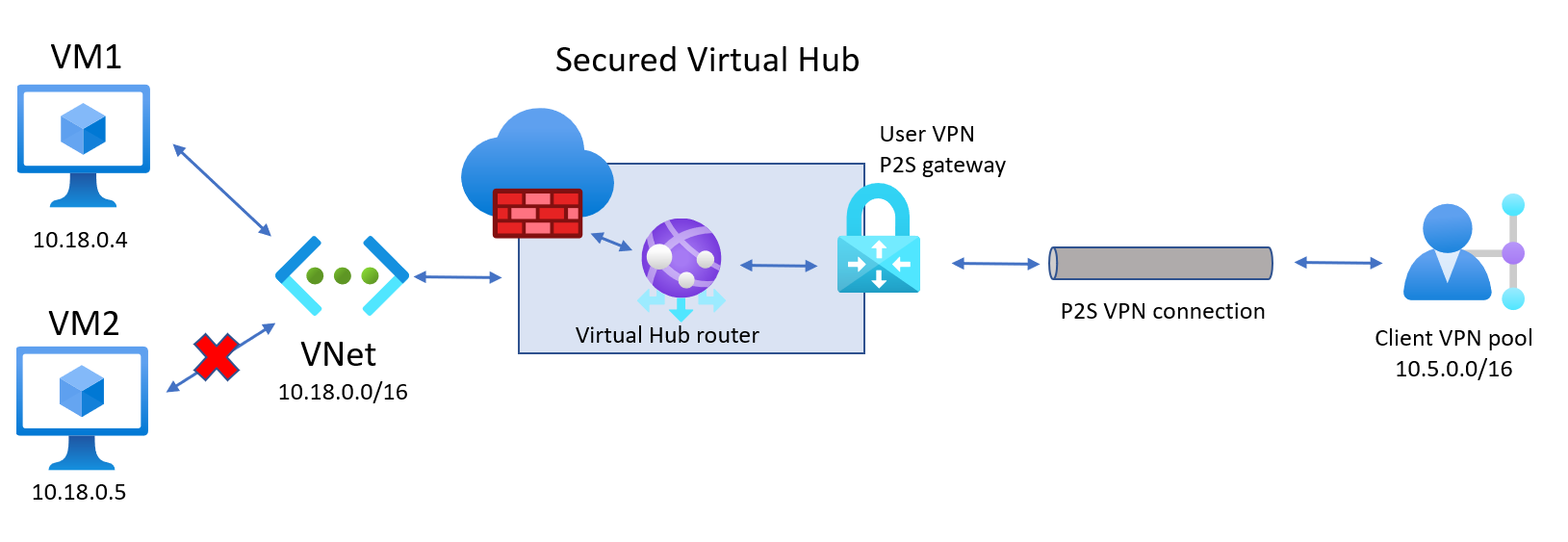
本文中的步骤可帮助你在下图中创建体系结构,以允许用户 VPN 客户端访问连接到虚拟中心的分支 VNet 中的特定资源 (VM1),但不能访问其他资源 (VM2)。 使用此体系结构示例作为基本准则。
先决条件
你有一个 Azure 订阅。 如果没有 Azure 订阅,请创建一个试用版版订阅。
有一个要连接到的虚拟网络。
- 确认本地网络的任何子网都不会与要连接到的虚拟网络重叠。
- 若要在 Azure 门户中创建虚拟网络,请参阅快速入门一文。
虚拟网络不能包含任何现有虚拟网络网关。
- 如果虚拟网络已有网关(VPN 或 ExpressRoute),必须先删除所有网关再继续。
- 此配置要求虚拟网络仅连接到虚拟 WAN 中心网关。
确定要用于虚拟中心专用地址空间的 IP 地址范围。 配置虚拟中心时,将使用此信息。 虚拟中心是虚拟 WAN 创建和使用的虚拟网络。 这是区域中虚拟 WAN 网络的核心。 地址空间范围必须符合某些规则:
- 为中心指定的地址范围不能与连接到的任何现有虚拟网络重叠。
- 地址范围不能与连接到的本地地址范围重叠。
- 如果不熟悉本地网络配置中的 IP 地址范围,请咨询能够提供此类详细信息的人员。
- 你具有要使用的身份验证配置的可用值。 例如,RADIUS 服务器、Microsoft Entra 身份验证或生成和导出证书。
创建虚拟 WAN
在门户中的“搜索资源”栏中,在搜索框中键入“虚拟 WAN”,然后选择 Enter 。
从结果中选择“虚拟 WAN”。 在“虚拟 WAN”页面上,选择“+ 创建”以打开“创建 WAN”页面 。
在“创建 WAN”页的“基本信息”选项卡上,填写以下字段 。 修改示例值以应用于你的环境。
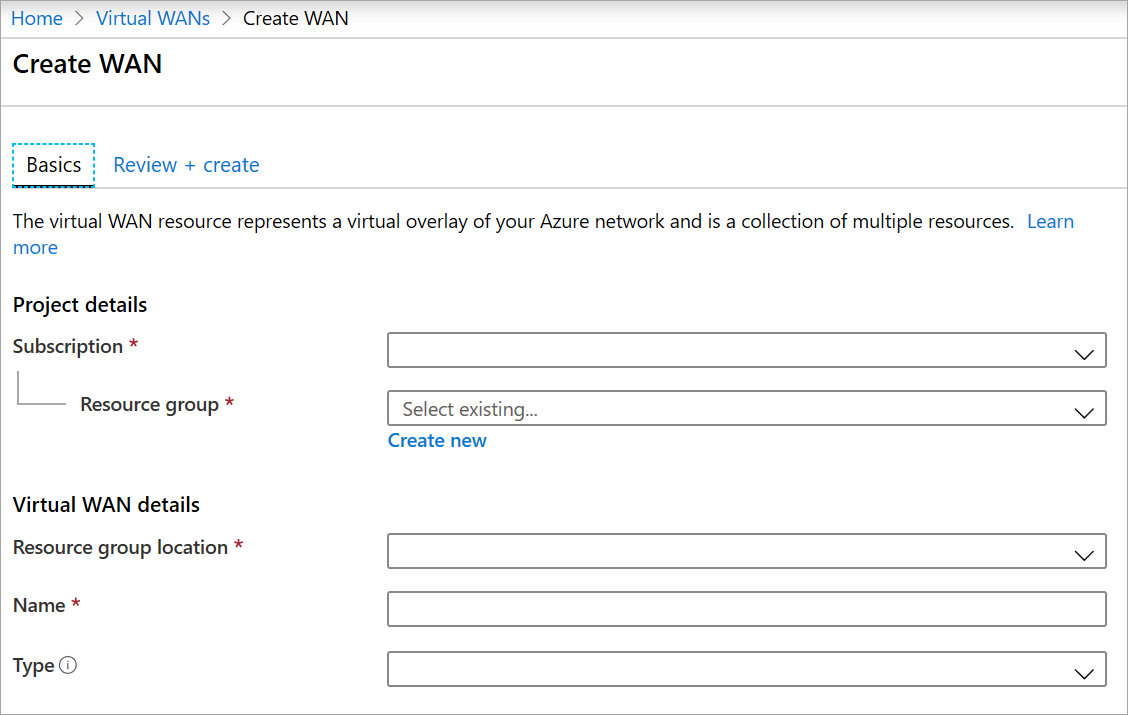
- 订阅:选择要使用的订阅。
- 资源组:新建资源组或使用现有的资源组。
- 资源组位置:从下拉列表中选择资源位置。 WAN 是一个全局资源,不会驻留在某个特定区域。 但是,必须选择一个区域才能管理和查找所创建的 WAN 资源。
- 名称:键入要用于称呼虚拟 WAN 的名称。
- 类型:基本或标准。 选择“标准”。 如果选择“基本”,请了解基本虚拟 WAN 只能包含基本中心。 基本中心只能用于站点到站点连接。
填写完字段后,在页面底部,选择“查看 + 创建”。
验证通过后,单击“创建”以创建虚拟 WAN。
定义 P2S 配置参数
点到站点 (P2S) 配置定义连接远程客户端的参数。 本部分介绍如何定义 P2S 配置参数,然后创建将用于 VPN 客户端 配置文件的配置。 遵循的说明取决于要使用的身份验证方法。
身份验证方法
选择身份验证方法时,有三种选择。 每种方法都有特定的要求。 选择以下某种方法,然后完成步骤。
Microsoft Entra 身份验证:获取以下内容:
- 在 Microsoft Entra 租户中注册的 Azure VPN 企业应用程序的应用程序 ID。
- 颁发者。 示例:
https://sts.chinacloudapi.cn/your-Directory-ID。 - Microsoft Entra 租户。
基于 RADIUS 的身份验证: 获取 RADIUS 服务器 IP、RADIUS 服务器机密和证书信息。
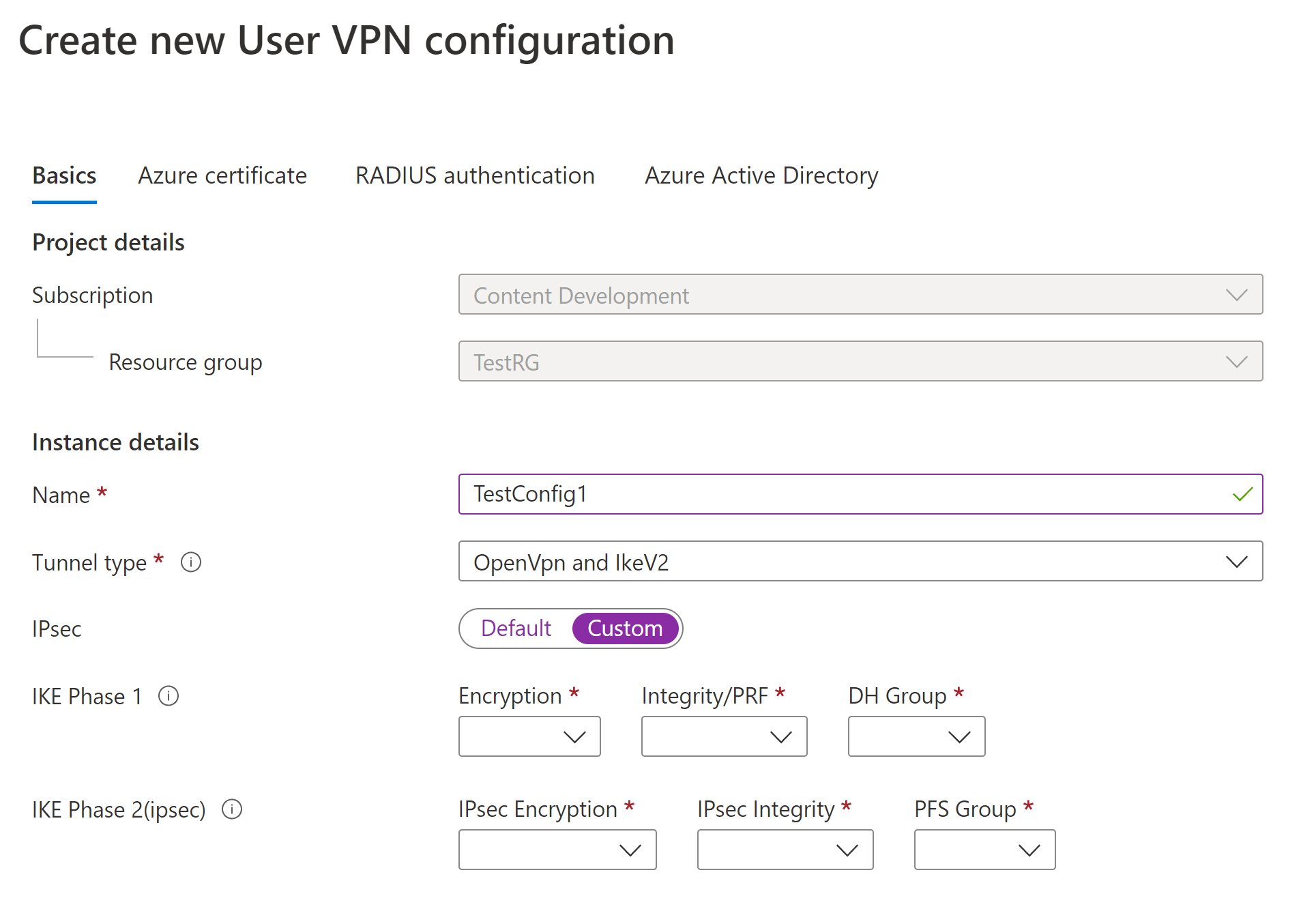
Azure 证书: 此配置需要证书。 你需要生成或获取证书。 每个客户端都需要客户端证书。 此外,需要上传根证书信息(公钥)。 有关所需证书的详细信息,请参阅生成和导出证书。
导航到你已创建的虚拟 WAN。
从左侧菜单中选择“用户 VPN 配置”。
在“用户 VPN 配置”页上,选择“+ 创建用户 VPN 配置” 。
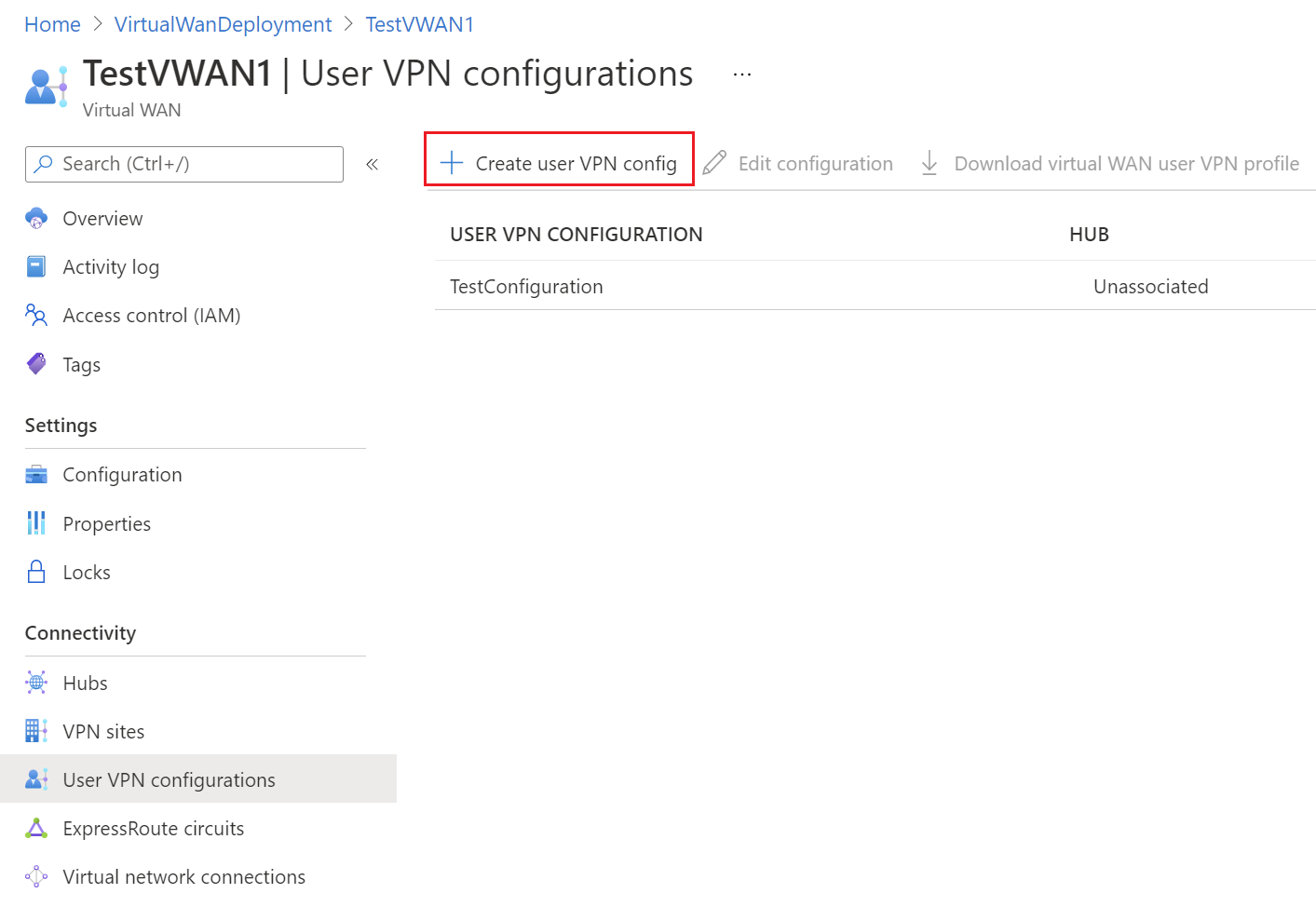
在“创建新用户 VPN 配置”页的“基本信息”选项卡上,在“实例详细信息”下,输入要分配给 VPN 配置的“名称” 。
对于“隧道类型”,请从下拉列表中选择所需的隧道类型。 隧道类型选项包括:“IKEv2 VPN、OpenVPN”以及“OpenVpn 和 IKEv2” 。 每种隧道类型都有特定的必需设置。 选择的隧道类型对应于可用的身份验证选项。
要求和参数:
IKEv2 VPN
要求: 选择“IKEv2”隧道类型时,会显示一条消息,指示你选择一种身份验证方法。 对于 IKEv2,你只能指定一种身份验证方法。 可以选择 Azure 证书或基于 RADIUS 的身份验证。
IPSec 自定义参数: 若要自定义 IKE 阶段 1 和 IKE 阶段 2 的参数,请将 IPsec 开关切换到“自定义”,然后选择参数值。
OpenVPN
- 要求: 选择“OpenVPN”隧道类型时,会显示一条消息,指示你选择一种身份验证机制。 如果选择“OpenVPN”作为隧道类型,则可以指定多种身份验证方法。 可以选择“Azure 证书”、“Azure Active Directory”和“基于 RADIUS 的身份验证”的任何子集。 对于基于 RADIUS 的身份验证,可以提供辅助 RADIUS 服务器 IP 地址和服务器机密。
配置要使用的身份验证方法。 每种身份验证方法都位于单独的选项卡中:“Azure 证书”、“RADIUS 身份验证”和“Azure Active Directory” 。 某些身份验证方法仅适用于特定隧道类型。
在要配置的身份验证方法选项卡上,选择“是”以显示可用的配置设置。
示例 - 证书身份验证
若要配置此设置,“基本信息”页上的隧道类型可以是 IKEv2、OpenVPN 或 OpenVPN 和 IKEv2。
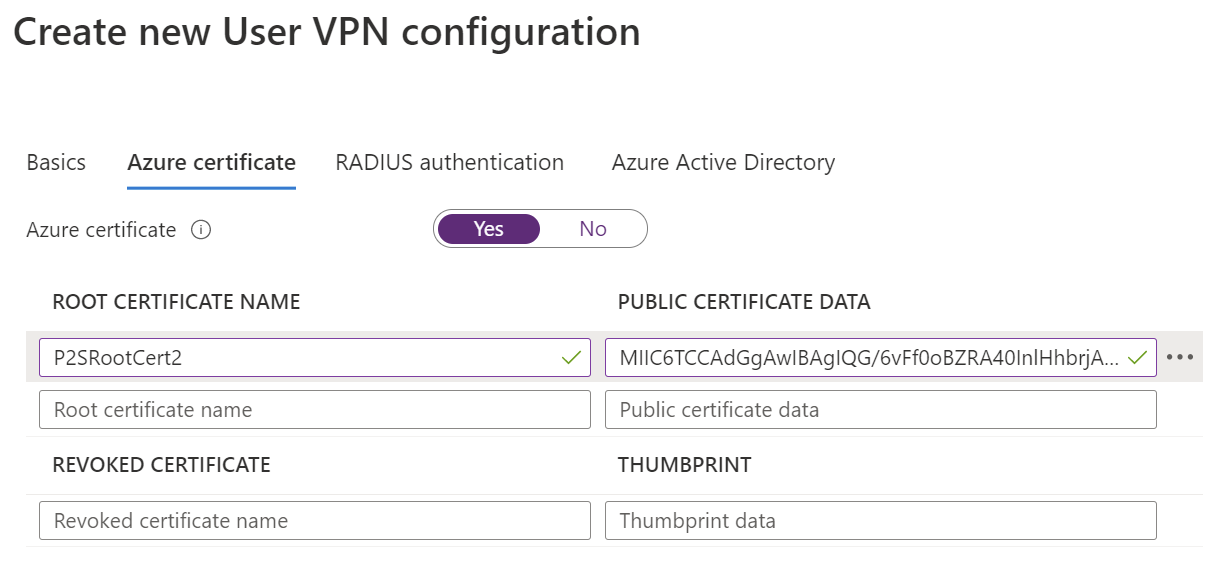
示例 - RADIUS 身份验证
若要配置此设置,“基本信息”页上的隧道类型可以是 Ikev2、OpenVPN 或 OpenVPN 和 IKEv2。
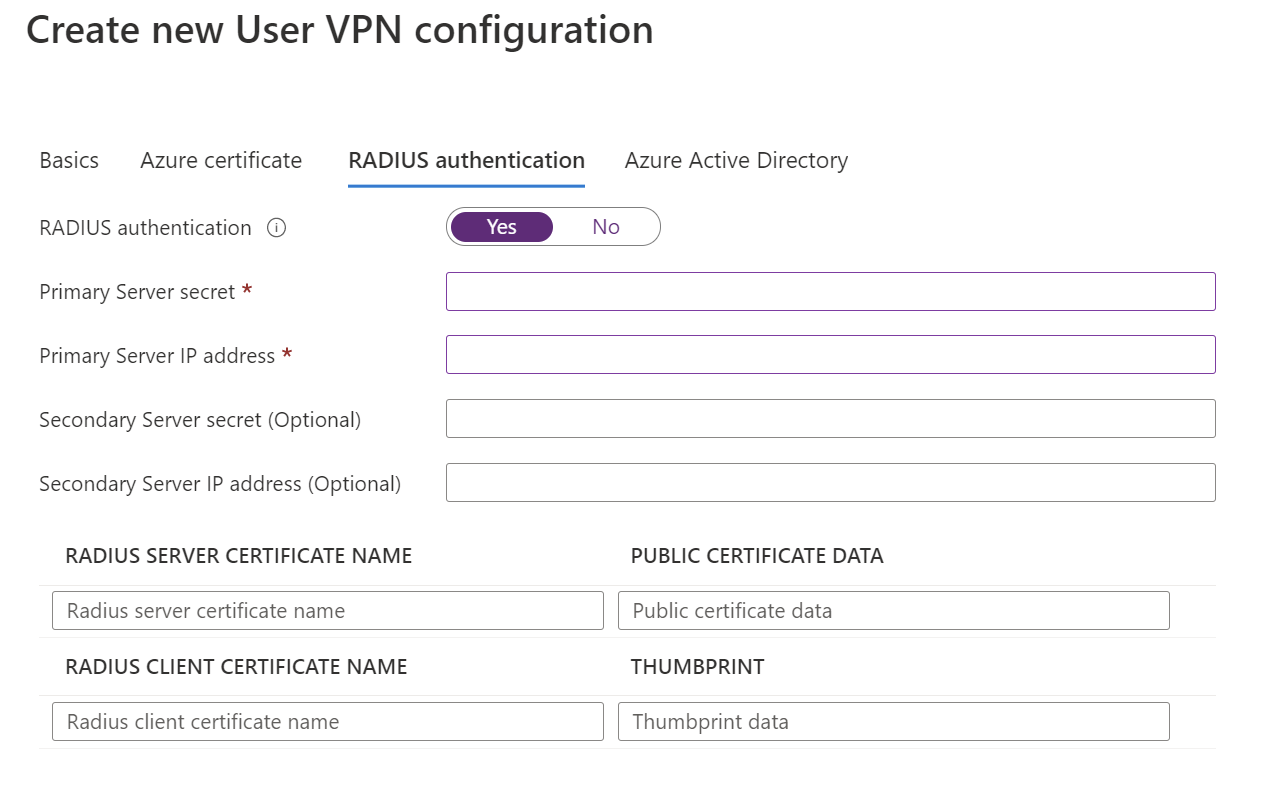
示例 - Azure Active Directory 身份验证
若要配置此设置,“基本信息”页上的隧道类型必须是 OpenVPN。 仅 OpenVPN 支持基于 Azure Active Directory 的身份验证。
配置完设置后,选择页面底部的“查看 + 创建”。
选择“创建”以创建用户 VPN 配置。
创建中心和网关
在本部分中,创建具有点到站点网关的虚拟中心。 配置时,可以使用以下示例值:
- 中心专用 IP 地址空间:10.1.0.0/16
- 客户端地址池: 10.5.0.0/16
- 自定义 DNS 服务器: 最多可以列出 5 个 DNS 服务器
“基本信息”页
转到你创建的虚拟 WAN。 在虚拟 WAN 页左侧窗格上的“连接性”下,选择“中心”。
在“中心”页上,选择“+ 新建中心”以打开“创建虚拟中心”页 。
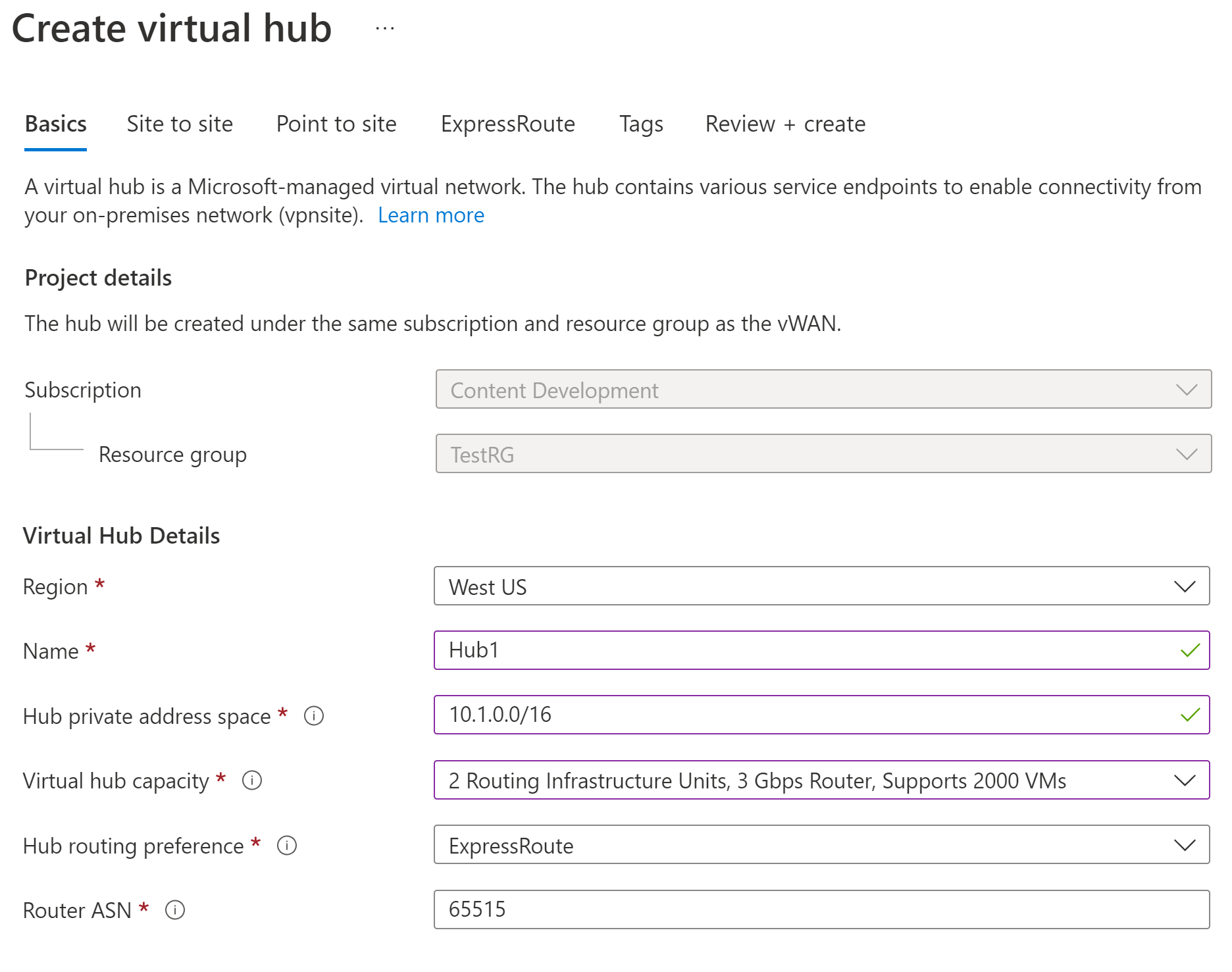
在“创建虚拟中心”页上的“基本”选项卡上,请填写以下字段 :
- 区域:选择要在其中部署虚拟中心的区域。
- 名称:想要用于称呼虚拟中心的名称。
- 中心专用地址空间:用 CIDR 表示法来表示的中心地址范围。 用于创建中心的最小地址空间为 /24。
- 虚拟中心容量:从下拉列表中选择。 有关详细信息,请参阅虚拟中心设置。
“点到站点”页
单击“点到站点”选项卡,打开点到站点的配置页。 若要查看点到站点设置,请单击“是”。
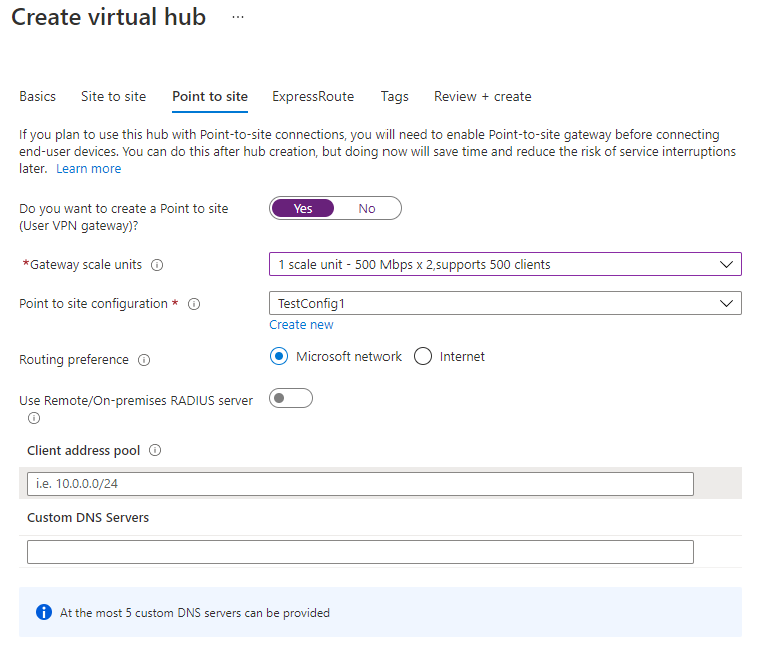
配置下列设置:
网关缩放单元 - 这表示用户 VPN 网关的聚合容量。 如果选择 40 或更多网关缩放单元,请相应地规划客户端地址池。 有关此设置如何影响客户端地址池的信息,请参阅关于客户端地址池。 有关网关缩放单元的信息,请参阅常见问题解答。
点到站点配置 - 选择你在上一步中创建的用户 VPN 配置。
使用远程/本地 RADIUS 服务器 - 将虚拟 WAN 用户 VPN 网关配置为使用基于 RADIUS 的身份验证时,用户 VPN 网关将充当代理,将 RADIUS 访问请求发送到 RADIUS 服务器。 默认情况下,“使用远程/本地 RADIUS 服务器”设置处于禁用状态,这意味着用户 VPN 网关只能将身份验证请求转发到连接到网关中心的虚拟网络中的 RADIUS 服务器。 启用此设置将使用户 VPN 网关能够通过与远程中心连接或本地部署的 RADIUS 服务器进行身份验证。
注意
仅当网关配置为使用基于 RADIUS 的身份验证时,才使用远程/本地 RADIUS 服务器设置和相关代理 IP。 如果网关未配置为使用基于 RADIUS 的身份验证,则将忽略此设置。
如果用户要连接到全局 VPN 配置文件而不是基于中心的配置文件,则必须启用“使用远程/本地 RADIUS 服务器”。 有关详细信息,请参阅全局和中心级配置文件。
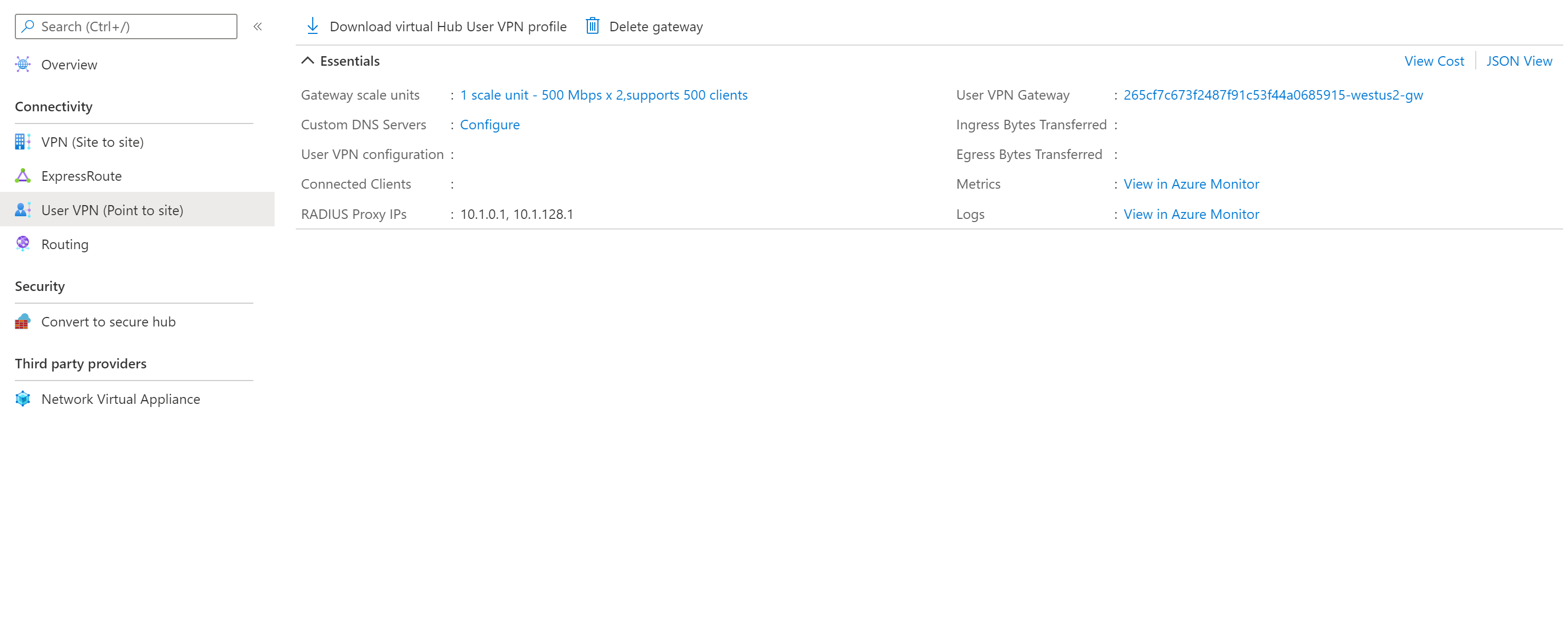
创建用户 VPN 网关后转到网关,并记下 RADIUS 代理 IP 字段。 RADIUS 代理 IP 是用户 VPN 网关发送到 RADIUS 服务器的 RADIUS 数据包的源 IP。 因此,RADIUS 服务器需要配置为接受来自 RADIUS 代理 IP 的身份验证请求。 如果 RADIUS 代理 IP 字段为空或无,请将 RADIUS 服务器配置为接受来自中心地址空间的身份验证请求。
此外,请确保设置将托管 RADIUS 服务器的连接的关联和传播(VNet 或本地)传播到使用点到站点 VPN 网关部署的中心的 defaultRouteTable,并且将点到站点 VPN 配置传播到托管 RADIUS 服务器的连接的路由表。 这是必需的,以确保网关可以与 RADIUS 服务器通信,反之亦然。
客户端地址池 - 自动从中将 IP 地址分配到 VPN 客户端的地址池。 有关详细信息,请参阅关于客户端地址池。
自定义 DNS 服务器 - 客户端将使用的 DNS 服务器的 IP 地址。 最多可以指定 5 个。
选择“查看 + 创建”以验证自己的设置 。
验证通过后,选择“创建”。 创建一个中心可能需要 30 分钟或更长时间才能完成。
生成 VPN 客户端配置文件
在本部分中,生成并下载配置配置文件。 这些文件用于在客户端计算机上配置本机 VPN 客户端。
若要生成 WAN 级全局配置文件 VPN 客户端配置包,请转到“虚拟 WAN”(而不是虚拟中心)。
在左侧窗格中,选择“用户 VPN 配置”。
选择要下载其配置文件的配置。 如果有多个中心分配给同一个配置文件,请展开配置文件以显示中心,然后选择使用配置文件的中心之一。
选择“下载虚拟 WAN 用户 VPN 配置文件”。
在下载页上,选择“EAPTLS”,然后选择“生成并下载配置文件”。 系统将生成包含客户端配置设置的配置文件包(zip 文件),并将其下载到计算机。 包的内容取决于适用于你的配置的身份验证和隧道选项。
配置 VPN 客户端
使用下载的配置文件配置远程访问客户端。 每个操作系统的过程均不同,请按照适用于你的系统的说明进行操作。
IKEv2
在用户 VPN 配置中,如果指定了 IKEv2 VPN 隧道类型,则可以配置本机 VPN 客户端(Windows 和 macOS Catalina 或更高版本)。
以下步骤适用于 Windows。 对于 macOS,请参阅 IKEv2-macOS 步骤。
根据 Windows 计算机的体系结构选择 VPN 客户端配置文件。 对于 64 位处理器体系结构,请选择“VpnClientSetupAmd64”安装程序包。 对于 32 位处理器体系结构,请选择“VpnClientSetupX86”安装程序包。
双击所需的包进行安装。 如果看到弹出 SmartScreen,选择“详细信息”,然后选择“仍要运行” 。
在客户端计算机上,导航到“网络设置”,并选择“VPN” 。 VPN 连接显示所连接到的虚拟网络的名称。
在要通过此用户 VPN 配置连接的每台计算机上安装客户端证书。 使用本机 Azure 证书身份验证类型时,客户端证书是身份验证必需的。 有关生成证书的详细信息,请参阅生成证书。 有关如何安装客户端证书的信息,请参阅安装客户端证书。
OpenVPN
在用户 VPN 配置中,如果指定了 OpenVPN 隧道类型,则可以下载并配置 Azure VPN 客户端,或者在某些情况下,可以使用 OpenVPN 客户端软件。 有关步骤,请使用与配置对应的链接。
- Azure AD 身份验证 - Azure VPN 客户端 - Windows
- Azure AD 身份验证 - Azure VPN 客户端 - macOS
- 配置 OpenVPN 客户端软件 - Windows、macOS、iOS、Linux
连接分支 VNet
在此部分中,将在中心与分支 VNet 之间创建连接。
在 Azure 门户中,转到“虚拟 WAN”,在左侧窗格中,选择“虚拟网络连接”。
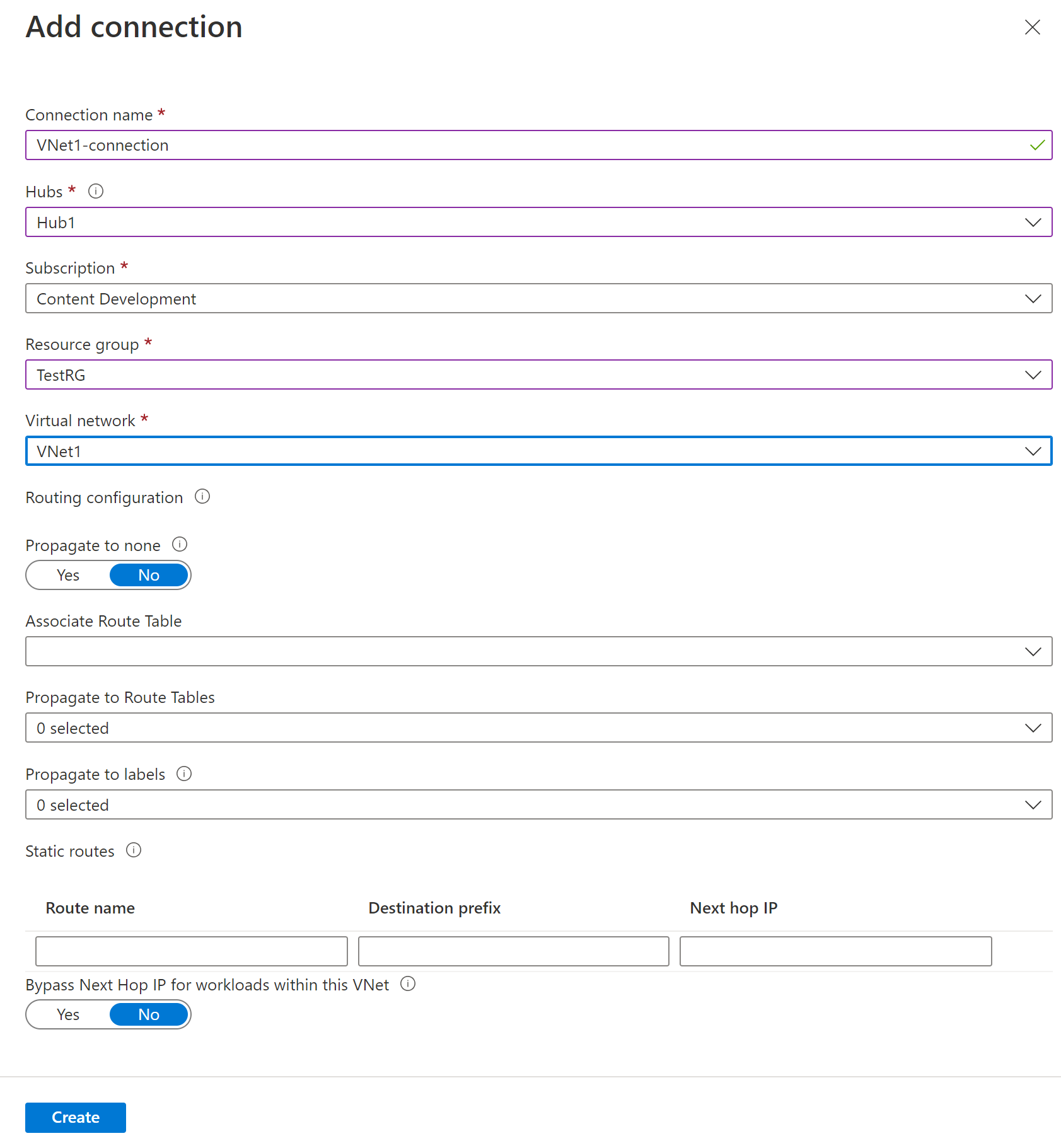
在“虚拟网络连接”页上,选择“+ 添加连接”。
在“添加连接”页上,配置连接设置。 有关路由设置的信息,请参阅关于路由。
- 连接名称:为连接命名。
- 中心:选择要与此连接关联的中心。
- 订阅:验证订阅。
- 资源组:选择包含要连接的虚拟网络的资源组。
- 虚拟网络:选择要连接到此中心的虚拟网络。 选择的虚拟网络不能包含现有的虚拟网络网关。
- 不传播到任何内容:默认设置为“否”。 将开关更改为“是”会使“传播到路由表”和“传播到标签”的配置选项对配置不可用 。
- 关联路由表:从下拉列表中,可以选择要关联的路由表。
- 传播到标签:标签是路由表的逻辑组。 对于此设置,请从下拉列表中选择。
- 静态路由:如有必要,请配置静态路由。 为网络虚拟设备配置静态路由(如果适用)。 对于虚拟网络连接中的静态路由,虚拟 WAN 支持单个下一跃点 IP。 例如,如果你有一个单独的虚拟设备用于入口和出口流量,则最好将虚拟设备置于单独的 VNet 中,并将 VNet 连接到虚拟中心。
- 绕过此 VNet 中的工作负载的下一个跃点 IP:此设置允许将 NVA 和其他工作负载部署到同一个 VNet 中,而无需强制所有流量通过 NVA。 只有在配置新连接时,才能配置此设置。 如果要将此设置用于已创建的连接,请删除该连接,然后添加新连接。
完成要配置的设置后,单击“创建”以创建连接。
创建虚拟机
在本部分,在 VNet 中创建两个 VM:VM1 和 VM2。 在网络示意图中,我们使用 10.18.0.4 和 10.18.0.5。 配置 VM 时,请确保选择所创建的虚拟网络(位于“网络”选项卡上)。 有关创建 VM 的步骤,请参阅 快速入门:创建 VM 的说明创建一个。
保护虚拟中心
标准虚拟中心没有用于保护分支虚拟网络中的资源的内置安全策略。 安全虚拟中心使用 Azure 防火墙或第三方提供程序来管理传入和传出的流量,从而保护 Azure 中的资源。
使用以下文章将中心转换为安全中心:在虚拟 WAN 中心配置 Azure 防火墙。
创建规则以管理和筛选流量
创建指示 Azure 防火墙行为的规则。 通过保护中心,我们确保进入虚拟中心的所有数据包在访问 Azure 资源之前都要经过防火墙处理。
完成这些步骤后,便已创建了一个体系结构,以允许 VPN 用户访问专用 IP 地址为 10.18.0.4 的 VM,但不能访问专用 IP 地址为 10.18.0.5 的 VM
在 Azure 门户中,导航到“防火墙管理器”。
在“安全性”下,选择“Azure 防火墙策略”。
选择“创建 Azure 防火墙策略”。
在“策略详细信息”下,输入名称,然后选择要部署虚拟中心的区域。
选择下一步:DNS 设置。
在完成时选择“下一步:规则”。
在“规则”选项卡上,选择“添加规则集合”。
为集合提供一个名称。 将类型设置为“网络”。 添加优先级值 100。
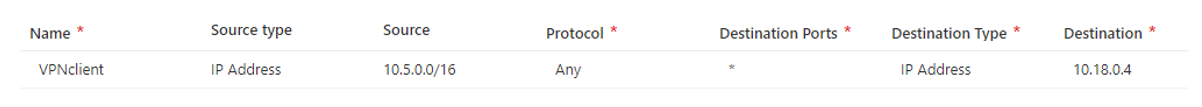
填写规则的名称、源类型、源、协议、目标端口和目标类型,如下例所示。 然后选择“添加”。 此规则允许 VPN 客户端池中的任何 IP 地址访问专用 IP 地址为 10.18.04 的 VM,但不能访问连接到虚拟中心的任何其他资源。 根据所需的体系结构和权限规则创建所需的任何规则。
在完成时选择“下一步:威胁智能” 。
在完成时选择“下一步:中心”。
在“中心”选项卡上,选择“关联虚拟中心”。
选择此前创建的虚拟中心,然后选择“添加”。
选择“查看 + 创建”。
选择“创建”。
此过程可能需要 5 分钟或更长时间才能完成。
通过 Azure 防火墙路由流量
在本部分,需要确保流量通过 Azure 防火墙路由。
- 在门户中,从“防火墙管理器”中选择“安全虚拟中心” 。
- 选择创建的虚拟中心。
- 在“设置”下,选择“安全配置” 。
- 在“专用流量”下,选择“通过 Azure 防火墙发送” 。
- 验证 Azure 防火墙是否保护 VNet 连接和分支连接专用流量。
- 选择“保存”。
注意
如果要使用安全虚拟中心中的 Azure 防火墙检查指向专用终结点的流量,请参阅保护发送到 Azure 虚拟 WAN 中专用终结点的流量。 需要根据 Azure 防火墙管理器的安全配置,在专用流量前缀中为每个专用终结点添加 /32 前缀,以便通过安全虚拟中心中的 Azure 防火墙对其进行检查。 如果未配置这些 /32 前缀,发往专用终结点的流量将绕过 Azure 防火墙。
验证
验证安全中心的设置。
- 通过 VPN 从客户端设备连接到“安全虚拟中心”。
- 从客户端对 IP 地址 10.18.0.4 执行 Ping 操作。 应该会看到响应。
- 从客户端对 IP 地址 10.18.0.5 执行 Ping 操作。 应该看不到响应。
注意事项
- 确保安全虚拟中心上的“有效路由表”具有防火墙的专用流量的下一个跃点。 要访问“有效路由表”,请导航到“虚拟中心”资源。 在“连接性”下,选择“路由”,然后选择“有效路由” 。 在此处,选择“默认”路由表。
- 验证是否在创建规则部分创建了规则。 如果缺少这些步骤,则你创建的规则实际上将不会与中心关联,并且路由表和数据包流将不会使用 Azure 防火墙。
后续步骤
- 有关虚拟 WAN 的详细信息,请参阅虚拟 WAN 常见问题解答。
- 有关 Azure 防火墙的详细信息,请参阅 Azure 防火墙常见问题解答。