Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
APPLIES TO: All API Management tiers
API Management allows you to secure access to the backend service of an API by using client certificates and mutual TLS authentication. This article shows how to manage certificates in API Management by using the Azure portal. It also explains how to configure an API to use a certificate to access a backend service.
You can also manage API Management certificates by using the API Management REST API.
Certificate options
API Management provides two options for managing certificates that are used to secure access to backend services:
- Reference a certificate that's managed in Azure Key Vault.
- Add a certificate file directly in API Management.
We recommend that you use key vault certificates because doing so improves API Management security:
- Certificates stored in key vaults can be reused across services.
- Granular access policies can be applied to certificates stored in key vaults.
- Certificates updated in the key vault are automatically rotated in API Management. After an update in the key vault, a certificate in API Management is updated within four hours. You can also manually refresh the certificate by using the Azure portal or via the management REST API.
Prerequisites
Note
We recommend that you use the Azure Az PowerShell module to interact with Azure. See Install Azure PowerShell to get started. To learn how to migrate to the Az PowerShell module, see Migrate Azure PowerShell from AzureRM to Az.
If you haven't created an API Management instance yet, see Create an API Management service instance.
Configure your backend service client certificate authentication. For information about configuring certificate authentication in Azure App Service, see Configure TLS mutual authentication in App Service.
Ensure that you have access to the certificate and the password for management in an Azure key vault, or a certificate to upload to the API Management service. The certificate must be in PFX format. Self-signed certificates are allowed.
If you use a self-signed certificate or other custom CA certificate and your API Management instance is in one of the classic tiers, install the corresponding root and intermediate CA certificates in API Management to enable validation of the backend service certificate. For more information, see How to add a custom CA certificate in Azure API Management
If you don't install the CA certificates, API Management can't validate the backend service certificate, and requests to the backend service fail unless you disable certificate chain validation. See Disable certificate chain validation for self-signed certificates later in this article.
Note
CA certificates for certificate validation aren't supported in the Consumption tier.
Prerequisites for key vault integration
If you don't already have a key vault, create one. For information about creating a key vault, see Quickstart: Create a key vault using the Azure portal.
Enable a system-assigned or user-assigned managed identity in API Management.
Configure access to key vault
- In the portal, go to your key vault.
- In the left menu, select Settings > Access configuration. Note the Permission model that's configured.
- Depending on the permission model, configure either a key vault access policy or Azure RBAC access for an API Management managed identity.
To add a key vault access policy:
- In the left menu, select Access policies.
- On the Access policies page, select + Create.
- On the Permissions tab, under Secret permissions, select Get and List, and then select Next.
- On the Principal tab, search for the resource name of your managed identity, then select Next. If you're using a system-assigned identity, the principal is the name of your API Management instance.
- Select Next again. On the Review + create tab, select Create.
To create a certificate in the key vault or import a certificate to the key vault, see Quickstart: Set and retrieve a certificate from Azure Key Vault using the Azure portal.
Requirements for Key Vault firewall
If Key Vault firewall is enabled on your key vault, you must meet these requirements:
You must use the API Management instance's system-assigned managed identity to access the key vault.
In Key Vault firewall, enable the Allow Trusted Microsoft Services to bypass this firewall option. API Management supports trusted service connectivity to access the key vault for control-plane options.
Ensure that your local client IP address is allowed to access the key vault temporarily while you select a certificate or secret to add to Azure API Management. For more information, see Configure Azure Key Vault networking settings.
After completing the configuration, you can block your client address in the key vault firewall.
Important
Starting March 2026, trusted service connectivity to Azure services from the API Management gateway by enabling the Allow Trusted Microsoft Services to bypass this firewall firewall setting will no longer be supported. To continue accessing these services from the API Management gateway after this change, ensure that you choose a different supported network access option. For control-plane operations, you can continue to use trusted service connectivity. Learn more.
Virtual network requirements
If the API Management instance is deployed in a virtual network, also configure the following network settings:
- Enable a service endpoint to Key Vault on the API Management subnet.
- Configure a network security group (NSG) rule to allow outbound traffic to the AzureKeyVault and AzureActiveDirectory service tags.
For details, see Network configuration when setting up API Management in a virtual network.
Add a key vault certificate
See Prerequisites for key vault integration.
Important
To add a key vault certificate to your API Management instance, you must have permissions to list secrets from the key vault.
Caution
When using a key vault certificate in API Management, be careful not to delete the certificate, key vault, or managed identity that's used to access the key vault.
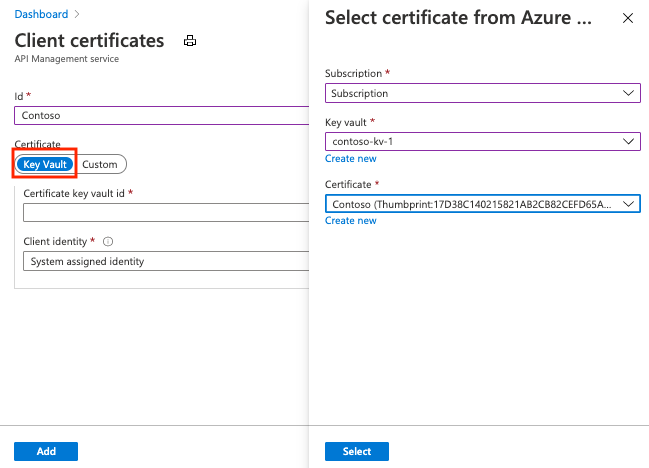
To add a key vault certificate to API Management:
In the Azure portal, go to your API Management instance.
Under Security, select Certificates.
Select Certificates > + Add.
In Id, enter a name.
In Certificate, select Key vault.
Enter the identifier of a key vault certificate, or choose Select to select a certificate from a key vault.
Important
If you enter a key vault certificate identifier yourself, be sure that it doesn't have version information. Otherwise, the certificate won't rotate automatically in API Management after an update in the key vault.
In Client identity, select a system-assigned identity or an existing user-assigned managed identity. For more information, see Use managed identities in Azure API Management.
Note
The identity needs to have permissions to get and list certificates from the key vault. If you haven't already configured access to the key vault, API Management prompts you so that it can automatically configure the identity with the necessary permissions.
Select Add.
Select Save.
Upload a certificate
To upload a client certificate to API Management:
In the Azure portal, go to your API Management instance.
Under Security, select Certificates.
Select Certificates > + Add.
In Id, enter a name.
In Certificate, select Custom.
Browse to select the certificate .pfx file, and enter its password.
Select Add.
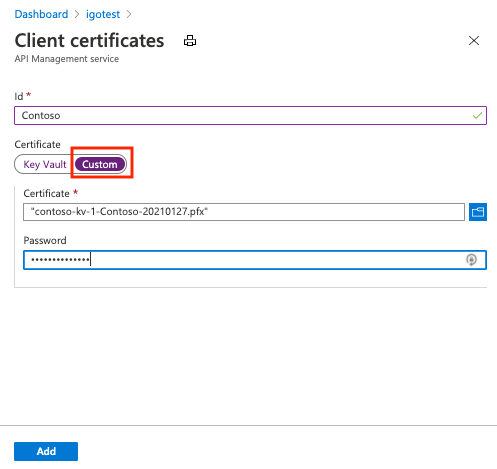
Select Save.
After the certificate is uploaded, it shows in the Certificates window. If you have many certificates, note the thumbprint of the certificate that you just uploaded. You'll need it to configure an API to use the client certificate for gateway authentication.
Configure an API to use client certificate for gateway authentication
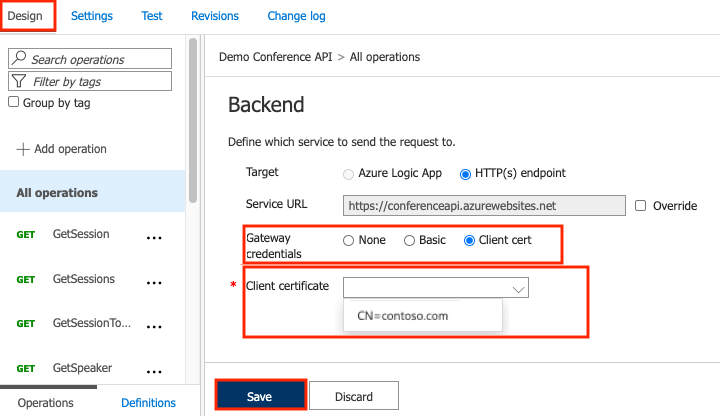
In the Azure portal, go to your API Management instance.
Under APIs, select APIs.
Select an API from the list.
On the Design tab, select the pencil icon in the Backend section.
In Gateway credentials, select Client cert and then select your certificate in the Client certificate list.
Select Save.
Caution
This change is effective immediately. Calls to operations of the API will use the certificate to authenticate on the backend server.
Tip
When a certificate is specified for gateway authentication for the backend service of an API, it becomes part of the policy for that API and can be viewed in the policy editor.
Disable certificate chain validation for self-signed certificates
If you're using self-signed certificates, you need to disable certificate chain validation to enable API Management to communicate with the backend system. Otherwise you'll get a 500 error code. To disable this validation, you can use the New-AzApiManagementBackend (for a new backend) or Set-AzApiManagementBackend (for an existing backend) PowerShell cmdlets and set the -SkipCertificateChainValidation parameter to True:
$context = New-AzApiManagementContext -ResourceGroupName 'ContosoResourceGroup' -ServiceName 'ContosoAPIMService'
New-AzApiManagementBackend -Context $context -Url 'https://contoso.com/myapi' -Protocol http -SkipCertificateChainValidation $true
You can also disable certificate chain validation by using the Backend REST API.
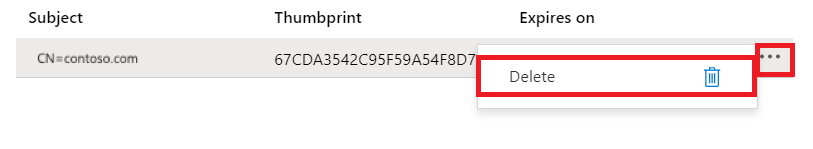
Delete a client certificate
To delete a certificate, select Delete on the ellipsis (...) menu:
Important
If the certificate is referenced by any policies, a warning screen appears. To delete the certificate, you must first remove it from any policies that are configured to use it.