This article describes how to add IPv6 support to connect via ExpressRoute to your resources in Azure using the Azure portal, Azure CLI, or Azure PowerShell.
Note
Some aspects of the portal experience are still being implemented. Therefore, when using the Azure portal, follow the exact order of steps provided in this document to successfully add IPv6 support. Specifically, make sure to create your virtual network and subnet, or add IPv6 address space to your existing virtual network and GatewaySubnet, prior to creating a new virtual network gateway in the portal.
Prerequisites
Sign in to the Azure portal
From a web browser, sign in to the Azure portal.
Note
Before you can use Azure CLI in Microsoft Azure operated by 21Vianet, please run az cloud set -n AzureChinaCloud first to change the cloud environment. If you want to switch back to Azure Public Cloud, run az cloud set -n AzureCloud again.
The steps and examples in this article use Azure PowerShell Az modules. To install the Az modules locally on your computer, see Install Azure PowerShell. To learn more about the new Az module, see Introducing the new Azure PowerShell Az module. PowerShell cmdlets are updated frequently. If you are not running the latest version, the values specified in the instructions may fail. To find the installed versions of PowerShell on your system, use the Get-Module -ListAvailable Az cmdlet.
Add IPv6 Private Peering to your ExpressRoute circuit
Create an ExpressRoute circuit or navigate to the existing circuit you want to change.
Select the Azure private peering configuration.
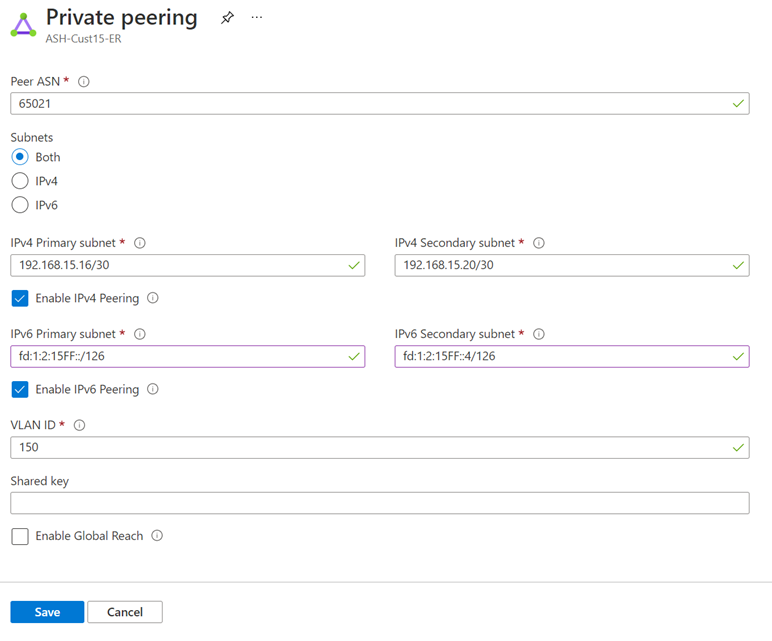
Add an IPv6 Private Peering to your existing IPv4 Private Peering configuration by selecting "Both" for Subnets, or only enable IPv6 Private Peering on your new circuit by selecting "IPv6". Provide a pair of /126 IPv6 subnets that you own for your primary link and secondary links. From each of these subnets, you assign the first usable IP address to your router as Microsoft uses the second usable IP for its router. Save your peering configuration once you defined all parameters.
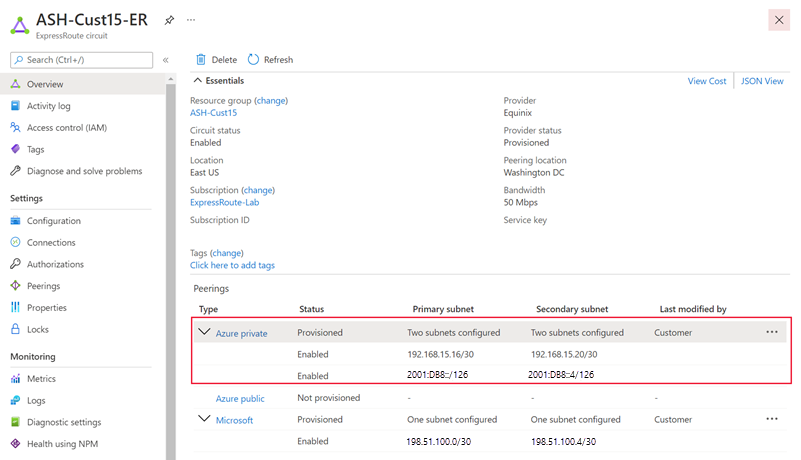
After the configuration is accepted successfully, you should see something similar to the following example.
Create an ExpressRoute circuit or use an existing circuit. View the circuit details by running the following command:
az network express-route show --resource-group "<ExpressRouteResourceGroup>" --name "<MyCircuit>"
View the private peering configuration for the circuit by running the following command:
az network express-route peering show -g "<ExpressRouteResourceGroup>" --circuit-name "<MyCircuit>" --name AzurePrivatePeering
Add an IPv6 Private Peering to your existing IPv4 Private Peering configuration. Provide a pair of /126 IPv6 subnets that you own for your primary link and secondary links. From each of these subnets, you assign the first usable IP address to your router as Azure uses the second usable IP for its router.
az network express-route peering update -g "<ExpressRouteResourceGroup>" --circuit-name "<MyCircuit>" --name AzurePrivatePeering --ip-version ipv6 --primary-peer-subnet "<X:X:X:X/126>" --secondary-peer-subnet "<Y:Y:Y:Y/126>"
Create an ExpressRoute circuit or use an existing circuit. Retrieve the circuit by running the Get-AzExpressRouteCircuit command:
$ckt = Get-AzExpressRouteCircuit -Name "ExpressRouteARMCircuit" -ResourceGroupName "ExpressRouteResourceGroup"
Retrieve the private peering configuration for the circuit by running Get-AzExpressRouteCircuitPeeringConfig:
Get-AzExpressRouteCircuitPeeringConfig -Name "AzurePrivatePeering" -ExpressRouteCircuit $ckt
Add an IPv6 Private Peering to your existing IPv4 Private Peering configuration. Provide a pair of /126 IPv6 subnets that you own for your primary link and secondary links. From each of these subnets, you assign the first usable IP address to your router as Azure uses the second usable IP for its router.
Note
The peer ASN and VlanId should match those in your IPv4 Private Peering configuration.
Set-AzExpressRouteCircuitPeeringConfig -Name "AzurePrivatePeering" -ExpressRouteCircuit $ckt -PeeringType AzurePrivatePeering -PeerASN 100 -PrimaryPeerAddressPrefix "3FFE:FFFF:0:CD30::/126" -SecondaryPeerAddressPrefix "3FFE:FFFF:0:CD30::4/126" -VlanId 200 -PeerAddressType IPv6
Set-AzExpressRouteCircuit -ExpressRouteCircuit $ckt
After the configuration is saved successfully, get the circuit again by running the Get-AzExpressRouteCircuit command. The response should look similar to the following example:
Name : ExpressRouteARMCircuit
ResourceGroupName : ExpressRouteResourceGroup
Location : chinaeast
Id : /subscriptions/***************************/resourceGroups/ExpressRouteResourceGroup/providers/Microsoft.Network/expressRouteCircuits/ExpressRouteARMCircuit
Etag : W/"################################"
ProvisioningState : Succeeded
Sku : {
"Name": "Standard_MeteredData",
"Tier": "Standard",
"Family": "MeteredData"
}
CircuitProvisioningState : Enabled
ServiceProviderProvisioningState : Provisioned
ServiceProviderNotes :
ServiceProviderProperties : {
"ServiceProviderName": "Equinix",
"PeeringLocation": "Washington DC",
"BandwidthInMbps": 50
}
ExpressRoutePort : null
BandwidthInGbps :
Stag : 29
ServiceKey : **************************************
Peerings : [
{
"Name": "AzurePrivatePeering",
"Etag": "W/\"facc8972-995c-4861-a18d-9a82aaa7167e\"",
"Id": "/subscriptions/***************************/resourceGroups/ExpressRouteResourceGroup/providers/Microsoft.Network/expressRouteCircuits/ExpressRouteARMCircuit/peerings/AzurePrivatePeering",
"PeeringType": "AzurePrivatePeering",
"State": "Enabled",
"AzureASN": 12076,
"PeerASN": 100,
"PrimaryPeerAddressPrefix": "192.168.15.16/30",
"SecondaryPeerAddressPrefix": "192.168.15.20/30",
"PrimaryAzurePort": "",
"SecondaryAzurePort": "",
"VlanId": 200,
"ProvisioningState": "Succeeded",
"GatewayManagerEtag": "",
"LastModifiedBy": "Customer",
"Ipv6PeeringConfig": {
"State": "Enabled",
"PrimaryPeerAddressPrefix": "3FFE:FFFF:0:CD30::/126",
"SecondaryPeerAddressPrefix": "3FFE:FFFF:0:CD30::4/126"
},
"Connections": [],
"PeeredConnections": []
},
]
Authorizations : []
AllowClassicOperations : False
GatewayManagerEtag :
Update your connection to an existing virtual network
To use IPv6 Private Peering with your existing Azure resources, follow these steps:
Follow these steps if you have an existing environment of Azure resources that you would like to use your IPv6 Private Peering with.
Navigate to the virtual network that your ExpressRoute circuit is connected to.
Navigate to the Address space tab and add an IPv6 address space to your virtual network. Save your address space.

Navigate to the Subnets tab and select the GatewaySubnet. Check Add IPv6 address space and provide an IPv6 address space for your subnet. The gateway IPv6 subnet should be /64 or larger. Save your configuration once you defined all parameters.

If you have an existing zone-redundant gateway, run the following command in PowerShell to enable IPv6 connectivity (note that it can take up to 1 hour for changes to reflect). Otherwise, create the virtual network gateway using any SKU and a Standard, Static public IP address. If you plan to use FastPath, use UltraPerformance or ErGw3AZ (note that this option is only available for circuits using ExpressRoute Direct).
$gw = Get-AzVirtualNetworkGateway -Name "GatewayName" -ResourceGroupName "ExpressRouteResourceGroup"
Set-AzVirtualNetworkGateway -VirtualNetworkGateway $gw
Add an IPv6 address space to the virtual network that your ExpressRoute circuit is connected to.
az network vnet update -g "<MyResourceGroup>" -n "<MyVNet>" --address-prefixes "X:X:X:X::/64"
Add IPv6 address space to your gateway subnet. The gateway IPv6 subnet should be /64 or larger.
az network vnet subnet update -g "<MyResourceGroup>" -n "<MySubnet>" -vnet-name "<MyVNet>" --address-prefixes "10.0.0.0/26", "X:X:X:X::/64"
If you have an existing zone-redundant gateway, run the following to enable IPv6 connectivity (note that it can take up to 1 hour for changes to reflect). Otherwise, create the virtual network gateway using any SKU. If you plan to use FastPath, use UltraPerformance or ErGw3AZ (note that this feature is only available for circuits using ExpressRoute Direct).
az network vnet-gateway update --name "<GatewayName>" --resource-group "<MyResourceGroup>"
Retrieve the virtual network that your ExpressRoute circuit is connected to.
$vnet = Get-AzVirtualNetwork -Name "VirtualNetwork" -ResourceGroupName "ExpressRouteResourceGroup"
Add an IPv6 address space to your virtual network.
$vnet.AddressSpace.AddressPrefixes.add("ace:daa:daaa:deaa::/64")
Set-AzVirtualNetwork -VirtualNetwork $vnet
Add IPv6 address space to your gateway subnet. The gateway IPv6 subnet should be /64 or larger.
Set-AzVirtualNetworkSubnetConfig -Name GatewaySubnet -VirtualNetwork $vnet -AddressPrefix "10.0.0.0/26", "ace:daa:daaa:deaa::/64"
Set-AzVirtualNetwork -VirtualNetwork $vnet
If you have an existing zone-redundant gateway, run the following to enable IPv6 connectivity (note that it can take up to 1 hour for changes to reflect). Otherwise, create the virtual network gateway using any SKU. If you plan to use FastPath, use UltraPerformance or ErGw3AZ (note that this feature is only available for circuits using ExpressRoute Direct).
$gw = Get-AzVirtualNetworkGateway -Name "GatewayName" -ResourceGroupName "ExpressRouteResourceGroup"
Set-AzVirtualNetworkGateway -VirtualNetworkGateway $gw
Note
If you have an existing gateway that is not zone-redundant (meaning it is Standard, High Performance, or Ultra Performance SKU) and uses a public IP address of Basic SKU, you will need to delete and recreate the gateway using any SKU.
The gateway of type zone-redundant SKU (meaning it is Standard, High Performance, or Ultra Performance) can be deployed only in availability-zone supported regions.
Create a connection to a new virtual network
To connect to a new set of Azure resources via IPv6 Private Peering, follow these steps:
Limitations
While IPv6 support is available for connections to deployments in global Azure regions, it doesn't support the following use cases:
Connections to existing ExpressRoute gateways that aren't zone-redundant. Newly created ExpressRoute gateways of any SKU (both zone-redundant and not) using a Standard, Static IP address can be used for dual-stack ExpressRoute connections
Use of ExpressRoute with Virtual WAN
Use of ExpressRoute with Route Server (Portal only)
Coexistence with VPN Gateway for IPv6 traffic. You can still configure coexistence with VPN Gateway in a dual-stack virtual network, but VPN Gateway only supports IPv4 traffic.
It isn't possible to connect a dual-stack ExpressRoute Virtual Network Gateway to an ExpressRoute Circuit that only has IPv4 enabled on the Private Peering. IPv6 must also be enabled on the ExpressRoute Circuit. You must also configure IPv6 on your on-premises CPE device.
Next steps
To troubleshoot ExpressRoute problems, see the following articles:



