适用于:开发人员 | 高级
可在处于内部模式的虚拟网络中配置 Azure API 管理,以便只能从该虚拟网络内部访问该服务。 Azure 应用程序网关是一种平台即服务 (PaaS),充当第 7 层负载均衡器。 该网关充当反向代理服务,并提供 Azure Web 应用程序防火墙 (WAF) 及其他产品/服务。
通过将内部虚拟网络中预配的 API 管理与应用程序网关前端相结合,可以:
- 使用同时供内部使用者和外部使用者使用的相同 API 管理资源。
- 使用单个 API 管理资源,并向外部使用者提供在 API 管理中定义的一部分 API。
- 提供配套的方式让客户启用和禁用通过公共 Internet 对 API 管理的访问。
有关体系结构指南,请参阅:
注意
本文已更新为使用应用程序网关 WAF_v2 SKU。
先决条件
注意
建议使用 Azure Az PowerShell 模块与 Azure 交互。 请参阅安装 Azure PowerShell 以开始使用。 若要了解如何迁移到 Az PowerShell 模块,请参阅 将 Azure PowerShell 从 AzureRM 迁移到 Az。
要执行本文中所述的步骤,必须具有:
有效的 Azure 订阅
如果没有 Azure 订阅,可在开始前创建一个试用帐户。
证书
- 用于 API 管理自定义主机名的个人信息交换 (PFX) 文件:网关、开发人员门户和管理终结点。
- 适用于 PFX 根证书的证书 (CER) 文件。
最新版本的 Azure PowerShell
场景
本文介绍如何对内部和外部使用者使用单个 API 管理实例,并使其充当本地和云 API 的单一前端。 创建 API 管理实例并将其部署到 Azure 虚拟网络中。 了解如何在应用程序网关中使用公共和专用侦听器。 你了解如何使用应用程序网关中提供的路由功能,仅公开一部分 API 供外部使用。 在示例中,这些 API 以绿色突出显示。
在第一个设置示例中,只能从虚拟网络内部管理所有 API。 内部使用者可以访问所有内部和外部 API。 流量永远不会外发到 Internet。 可以通过 Azure ExpressRoute 线路提供高性能连接。 在示例中,内部使用者以橙色突出显示。
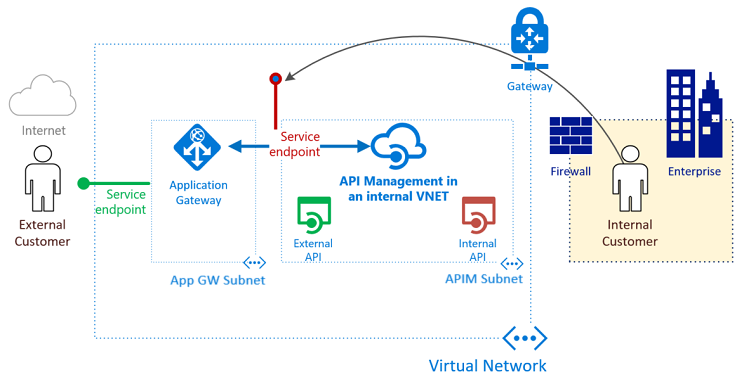
集成 API 管理和应用程序网关需要什么?
- 后端服务器池:此服务器池是 API 管理的内部虚拟 IP 地址。
- 后端服务器池设置:每个池具有端口、协议和基于 Cookie 的相关性等设置。 这些设置将应用到池中的所有服务器。
- 前端端口:此公共端口在应用程序网关上已打开。 进入此端口的流量将重定向到后端服务器之一。
- 侦听器:侦听器具有前端端口、协议(HTTP 或 HTTPS,这些值区分大小写)和传输层安全性 (TLS) 证书名称(如果配置 TLS 卸载)。
- 规则:规则将侦听器绑定到后端服务器池。
- 自定义运行状况探测:默认情况下,应用程序网关使用基于 IP 地址的探测来判断 中的哪些服务器处于活动状态。 API 管理只响应包含正确主机标头的请求,因此默认的探测会失败。 需要定义一个自定义运行状况探测,帮助应用程序网关确定服务是否处于活动状态,以及是否应该转发请求。
- 自定义域证书:要从 Internet 访问 API 管理,请创建域名系统 (DNS) 记录以将其主机名映射到应用程序网关前端 IP 地址。 这种映射可确保发送到 API 管理的主机头和证书有效。 在此示例中,我们将使用三个证书。 这些证书分别用于 API 管理的网关(后端)、开发人员门户和管理终结点。
通过应用程序网关向外部公开开发人员门户和管理终结点
在本文中,我们还会通过应用程序网关向外部用户公开开发人员门户和管理终结点。 需要执行额外的步骤来为每个终结点创建侦听器、探测、设置和规则。 相应步骤中提供了所有详细信息。 如果需要公开自承载网关的 v2 配置终结点,请遵循类似的步骤(未显示)。
如果使用 Microsoft Entra ID 或第三方身份验证,请在应用程序网关中启用基于 Cookie 的会话亲和性功能。
警告
为了防止应用程序网关 WAF 中断开发人员门户中 OpenAPI 规范的下载,请禁用防火墙规则 942200 - "Detects MySQL comment-/space-obfuscated injections and backtick termination"。
可能会中断门户功能的应用程序网关 WAF 规则包括:
- 适用于管理模式的
920300、920330、931130、942100、942110、942180、942200、942260、942340、942370 - 适用于已发布门户的
942200、942260、942370、942430、942440
设置变量
在本指南中,需要定义几个变量。
# These variables must be changed.
$subscriptionId = "aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e" # GUID of your Azure subscription
$domain = "contoso.net" # The custom domain for your certificate
$apimServiceName = "apim-contoso" # API Management service instance name, must be globally unique
$apimDomainNameLabel = $apimServiceName # Domain name label for API Management's public IP address, must be globally unique
$apimAdminEmail = "admin@contoso.net" # Administrator's email address - use your email address
$gatewayHostname = "api.$domain" # API gateway host
$portalHostname = "portal.$domain" # API developer portal host
$managementHostname = "management.$domain" # API management endpoint host
$baseCertPath = "C:\Users\Contoso\" # The base path where all certificates are stored
$trustedRootCertCerPath = "${baseCertPath}trustedroot.cer" # Full path to contoso.net trusted root .cer file
$gatewayCertPfxPath = "${baseCertPath}gateway.pfx" # Full path to api.contoso.net .pfx file
$portalCertPfxPath = "${baseCertPath}portal.pfx" # Full path to portal.contoso.net .pfx file
$managementCertPfxPath = "${baseCertPath}management.pfx" # Full path to management.contoso.net .pfx file
$gatewayCertPfxPassword = "certificatePassword123" # Password for api.contoso.net pfx certificate
$portalCertPfxPassword = "certificatePassword123" # Password for portal.contoso.net pfx certificate
$managementCertPfxPassword = "certificatePassword123" # Password for management.contoso.net pfx certificate
# These variables may be changed.
$resGroupName = "rg-apim-agw" # Resource group name that will hold all assets
$location = "China North 3" # Azure region that will hold all assets
$apimOrganization = "Contoso" # Organization name
$appgwName = "agw-contoso" # The name of the Application Gateway
创建 Resource Manager 的资源组
若要为 Azure 资源管理器创建资源组,请执行以下操作:
登录 Azure。
Connect-AzAccount -Environment AzureChinaCloud使用凭据进行身份验证。
选择所需的订阅。
Get-AzSubscription -Subscriptionid $subscriptionId | Select-AzSubscription创建资源组。 如果使用现有资源组,可跳过此步骤。
New-AzResourceGroup -Name $resGroupName -Location $location
资源管理器要求所有资源组指定一个位置。 此位置将用作该资源组中的资源的默认值。 请确保用于创建应用程序网关的所有命令都使用相同的资源组。
为应用程序网关创建虚拟网络和子网
以下示例演示如何使用 Resource Manager 创建虚拟网络。 本示例中的虚拟网络由应用程序网关和 API 管理的单独子网组成。
设置应用程序网关 IP 地址。
注意
由于会有公共和专用侦听器,因此我们需要公共和专用 IP 地址。 必须创建静态公共 IP 地址,而必须从与应用程序网关关联的子网中选择专用 IP 地址。 已任意选择专用 IP 地址。
$appGatewayExternalIP = New-AzPublicIpAddress -ResourceGroupName $resGroupName -name "pip-ag" -location $location -AllocationMethod Static -Sku Standard -Force $appGatewayInternalIP = "10.0.0.100" [String[]]$appGwNsgDestIPs = $appGatewayInternalIP, $appGatewayExternalIP.IpAddress创建适用于应用程序网关子网的网络安全组 (NSG) 和 NSG 规则。
$appGwRule1 = New-AzNetworkSecurityRuleConfig -Name appgw-in -Description "AppGw inbound" ` -Access Allow -Protocol * -Direction Inbound -Priority 100 -SourceAddressPrefix ` GatewayManager -SourcePortRange * -DestinationAddressPrefix * -DestinationPortRange 65200-65535 $appGwRule2 = New-AzNetworkSecurityRuleConfig -Name appgw-in-internet -Description "AppGw inbound Internet" ` -Access Allow -Protocol "TCP" -Direction Inbound -Priority 110 -SourceAddressPrefix ` Internet -SourcePortRange * -DestinationAddressPrefix $appGwNsgDestIPs -DestinationPortRange 443 $appGwNsg = New-AzNetworkSecurityGroup -ResourceGroupName $resGroupName -Location $location -Name ` "nsg-agw" -SecurityRules $appGwRule1, $appGwRule2创建适用于 API 管理子网的网络安全组 (NSG) 和 NSG 规则。 API 管理需要多个特定的 NSG 规则。
$apimRule1 = New-AzNetworkSecurityRuleConfig -Name APIM-Management -Description "APIM inbound" ` -Access Allow -Protocol Tcp -Direction Inbound -Priority 100 -SourceAddressPrefix ApiManagement ` -SourcePortRange * -DestinationAddressPrefix VirtualNetwork -DestinationPortRange 3443 $apimRule2 = New-AzNetworkSecurityRuleConfig -Name AllowAppGatewayToAPIM -Description "Allows inbound App Gateway traffic to APIM" ` -Access Allow -Protocol Tcp -Direction Inbound -Priority 110 -SourceAddressPrefix "10.0.0.0/24" ` -SourcePortRange * -DestinationAddressPrefix "10.0.1.0/24" -DestinationPortRange 443 $apimRule3 = New-AzNetworkSecurityRuleConfig -Name AllowAzureLoadBalancer -Description "Allows inbound Azure Infrastructure Load Balancer traffic to APIM" ` -Access Allow -Protocol Tcp -Direction Inbound -Priority 120 -SourceAddressPrefix AzureLoadBalancer ` -SourcePortRange * -DestinationAddressPrefix "10.0.1.0/24" -DestinationPortRange 6390 $apimRule4 = New-AzNetworkSecurityRuleConfig -Name AllowKeyVault -Description "Allows outbound traffic to Azure Key Vault" ` -Access Allow -Protocol Tcp -Direction Outbound -Priority 100 -SourceAddressPrefix "10.0.1.0/24" ` -SourcePortRange * -DestinationAddressPrefix AzureKeyVault -DestinationPortRange 443 $apimNsg = New-AzNetworkSecurityGroup -ResourceGroupName $resGroupName -Location $location -Name ` "nsg-apim" -SecurityRules $apimRule1, $apimRule2, $apimRule3, $apimRule4将地址范围 10.0.0.0/24 分配到创建虚拟网络时用于应用程序网关的子网变量。
$appGatewaySubnet = New-AzVirtualNetworkSubnetConfig -Name "appGatewaySubnet" -NetworkSecurityGroup $appGwNsg -AddressPrefix "10.0.0.0/24"将地址范围 10.0.1.0/24 分配到创建虚拟网络时用于 API 管理的子网变量。
$apimSubnet = New-AzVirtualNetworkSubnetConfig -Name "apimSubnet" -NetworkSecurityGroup $apimNsg -AddressPrefix "10.0.1.0/24"创建名为“vnet-contoso”的虚拟网络。 使用前缀 10.0.0.0/16 以及子网 10.0.0.0/24 和 10.0.1.0/24。
$vnet = New-AzVirtualNetwork -Name "vnet-contoso" -ResourceGroupName $resGroupName ` -Location $location -AddressPrefix "10.0.0.0/16" -Subnet $appGatewaySubnet,$apimSubnet分配子网变量,以便在后续步骤中使用。
$appGatewaySubnetData = $vnet.Subnets[0] $apimSubnetData = $vnet.Subnets[1]
在虚拟网络中创建 API 管理实例
以下示例演示如何在配置为仅供内部访问的虚拟网络中创建 API 管理实例。
API 管理需要具有唯一的公共
DomainNameLabelIP。$apimPublicIpAddressId = New-AzPublicIpAddress -ResourceGroupName $resGroupName -name "pip-apim" -location $location ` -AllocationMethod Static -Sku Standard -Force -DomainNameLabel $apimDomainNameLabel使用创建的子网
$apimSubnetData来创建 API 管理虚拟网络对象。$apimVirtualNetwork = New-AzApiManagementVirtualNetwork -SubnetResourceId $apimSubnetData.Id在虚拟网络中创建 API 管理实例。 此示例在“开发人员服务”层中创建服务。 替换为你的 API 管理实例的唯一名称。
$apimService = New-AzApiManagement -ResourceGroupName $resGroupName -Location $location -Name $apimServiceName -Organization $apimOrganization ` -AdminEmail $apimAdminEmail -VirtualNetwork $apimVirtualNetwork -VpnType "Internal" -Sku "Developer" -PublicIpAddressId $apimPublicIpAddressId.Id
在此层中创建和激活 API 管理实例可能需要 30 到 40 分钟。 上述命令成功后,请参阅访问内部虚拟网络 API 管理服务所需的 DNS 配置来确认可访问该服务。
在 API 管理中设置自定义域名
若要在 API 管理中设置自定义域名,请执行以下操作:
使用带有域私钥的证书和受信任的根证书的详细信息初始化以下变量。 本示例使用
api.contoso.net、portal.contoso.net和management.contoso.net。$certGatewayPwd = ConvertTo-SecureString -String $gatewayCertPfxPassword -AsPlainText -Force $certPortalPwd = ConvertTo-SecureString -String $portalCertPfxPassword -AsPlainText -Force $certManagementPwd = ConvertTo-SecureString -String $managementCertPfxPassword -AsPlainText -Force为 API 管理终结点创建和设置
Hostname配置对象。$gatewayHostnameConfig = New-AzApiManagementCustomHostnameConfiguration -Hostname $gatewayHostname ` -HostnameType Proxy -PfxPath $gatewayCertPfxPath -PfxPassword $certGatewayPwd $portalHostnameConfig = New-AzApiManagementCustomHostnameConfiguration -Hostname $portalHostname ` -HostnameType DeveloperPortal -PfxPath $portalCertPfxPath -PfxPassword $certPortalPwd $managementHostnameConfig = New-AzApiManagementCustomHostnameConfiguration -Hostname $managementHostname ` -HostnameType Management -PfxPath $managementCertPfxPath -PfxPassword $certManagementPwd $apimService.ProxyCustomHostnameConfiguration = $gatewayHostnameConfig $apimService.PortalCustomHostnameConfiguration = $portalHostnameConfig $apimService.ManagementCustomHostnameConfiguration = $managementHostnameConfig Set-AzApiManagement -InputObject $apimService
为虚拟网络中的 DNS 解析配置专用区域
若要为虚拟网络中的 DNS 解析配置专用 DNS 区域,请执行以下操作:
创建专用 DNS 区域并链接虚拟网络。
$myZone = New-AzPrivateDnsZone -Name $domain -ResourceGroupName $resGroupName $link = New-AzPrivateDnsVirtualNetworkLink -ZoneName $domain ` -ResourceGroupName $resGroupName -Name "mylink" ` -VirtualNetworkId $vnet.id为映射到 API 管理专用 IP 地址的自定义域主机名创建 A 记录。
$apimIP = $apimService.PrivateIPAddresses[0] New-AzPrivateDnsRecordSet -Name api -RecordType A -ZoneName $domain ` -ResourceGroupName $resGroupName -Ttl 3600 ` -PrivateDnsRecords (New-AzPrivateDnsRecordConfig -IPv4Address $apimIP) New-AzPrivateDnsRecordSet -Name portal -RecordType A -ZoneName $domain ` -ResourceGroupName $resGroupName -Ttl 3600 ` -PrivateDnsRecords (New-AzPrivateDnsRecordConfig -IPv4Address $apimIP) New-AzPrivateDnsRecordSet -Name management -RecordType A -ZoneName $domain ` -ResourceGroupName $resGroupName -Ttl 3600 ` -PrivateDnsRecords (New-AzPrivateDnsRecordConfig -IPv4Address $apimIP)
创建应用程序网关配置
必须先设置所有配置项,然后才能创建应用程序网关。 以下步骤将创建应用程序网关资源所需的配置项。
创建名为 gatewayIP01 的应用程序网关 IP 配置。 当应用程序网关启动时,它从配置的子网获取 IP 地址,再将网络流量路由到后端 IP 池中的 IP 地址。 请记住,每个实例需要一个 IP 地址。
$gipconfig = New-AzApplicationGatewayIPConfiguration -Name "gatewayIP01" -Subnet $appGatewaySubnetData为公共和专用 IP 终结点配置相同的前端端口。 此端口是用户连接到的端口。 通过为两者使用同一端口,我们确保可以向同一端口发出内部和外部请求。
$fp01 = New-AzApplicationGatewayFrontendPort -Name "port01" -Port 443配置两个前端 IP 地址 - 一个公共和一个专用。 专用 IP 地址取自应用程序网关子网,这是第一个在索引 0 中创建的地址。
$fipconfig01 = New-AzApplicationGatewayFrontendIPConfig ` -Name "gateway-public-ip" -PublicIPAddress $appGatewayExternalIP $fipconfig02 = New-AzApplicationGatewayFrontendIPConfig ` -Name "gateway-private-ip" -PrivateIPAddress $appGatewayInternalIP ` -Subnet $vnet.Subnets[0]配置应用程序网关的证书。 这些证书用于解密和重新加密传递的流量。
注意
应用程序网关支持定义自定义 TLS 选项、禁用某些 TLS 协议版本,以及指定密码套件和首选项顺序。 若要详细了解可配置的 TLS 选项,请参阅 TLS 策略概述。
$certGateway = New-AzApplicationGatewaySslCertificate -Name "gatewaycert" ` -CertificateFile $gatewayCertPfxPath -Password $certGatewayPwd $certPortal = New-AzApplicationGatewaySslCertificate -Name "portalcert" ` -CertificateFile $portalCertPfxPath -Password $certPortalPwd $certManagement = New-AzApplicationGatewaySslCertificate -Name "managementcert" ` -CertificateFile $managementCertPfxPath -Password $certManagementPwd为应用程序网关创建 HTTP 侦听器。 为其分配前端 IP 配置、端口和 TLS/SSL 证书。
# Public/external listeners $gatewayListener = New-AzApplicationGatewayHttpListener -Name "gatewaylistener" ` -Protocol "Https" -FrontendIPConfiguration $fipconfig01 -FrontendPort $fp01 ` -SslCertificate $certGateway -HostName $gatewayHostname -RequireServerNameIndication true $portalListener = New-AzApplicationGatewayHttpListener -Name "portallistener" ` -Protocol "Https" -FrontendIPConfiguration $fipconfig01 -FrontendPort $fp01 ` -SslCertificate $certPortal -HostName $portalHostname -RequireServerNameIndication true $managementListener = New-AzApplicationGatewayHttpListener -Name "managementlistener" ` -Protocol "Https" -FrontendIPConfiguration $fipconfig01 -FrontendPort $fp01 ` -SslCertificate $certManagement -HostName $managementHostname -RequireServerNameIndication true # Private/internal listeners $gatewayListenerPrivate = New-AzApplicationGatewayHttpListener -Name "gatewaylistener-private" ` -Protocol "Https" -FrontendIPConfiguration $fipconfig02 -FrontendPort $fp01 ` -SslCertificate $certGateway -HostName $gatewayHostname -RequireServerNameIndication true $portalListenerPrivate = New-AzApplicationGatewayHttpListener -Name "portallistener-private" ` -Protocol "Https" -FrontendIPConfiguration $fipconfig02 -FrontendPort $fp01 ` -SslCertificate $certPortal -HostName $portalHostname -RequireServerNameIndication true $managementListenerPrivate = New-AzApplicationGatewayHttpListener -Name "managementlistener-private" ` -Protocol "Https" -FrontendIPConfiguration $fipconfig02 -FrontendPort $fp01 ` -SslCertificate $certManagement -HostName $managementHostname -RequireServerNameIndication true为 API 管理的
ContosoApi网关域终结点创建自定义探测。 路径/status-0123456789abcdef是所有 API 管理实例中托管的默认运行状况终结点。 将api.contoso.net设置为自定义探测主机名,以便使用 TLS/SSL 证书保护它。注意
主机名
contosoapi.azure-api.cn是在公共 Azure 中创建名为contosoapi的服务时配置的默认代理主机名。$apimGatewayProbe = New-AzApplicationGatewayProbeConfig -Name "apimgatewayprobe" ` -Protocol "Https" -HostName $gatewayHostname -Path "/status-0123456789abcdef" ` -Interval 30 -Timeout 120 -UnhealthyThreshold 8 $apimPortalProbe = New-AzApplicationGatewayProbeConfig -Name "apimportalprobe" ` -Protocol "Https" -HostName $portalHostname -Path "/signin" ` -Interval 60 -Timeout 300 -UnhealthyThreshold 8 $apimManagementProbe = New-AzApplicationGatewayProbeConfig -Name "apimmanagementprobe" ` -Protocol "Https" -HostName $managementHostname -Path "/ServiceStatus" ` -Interval 60 -Timeout 300 -UnhealthyThreshold 8配置后端证书的受信任根证书。 此证书验证后端证书的真实性。
$trustedRootCert = New-AzApplicationGatewayTrustedRootCertificate ` -Name "allowlistcert1" -CertificateFile $trustedRootCertCerPath为应用程序网关配置 HTTP 后端设置,包括后端请求的超时限制,超过该限制后,将取消这些设置。 此值不同于探测超时。
$apimPoolGatewaySetting = New-AzApplicationGatewayBackendHttpSettings -Name "apimPoolGatewaySetting" ` -Port 443 -Protocol "Https" -CookieBasedAffinity "Disabled" -Probe $apimGatewayProbe ` -TrustedRootCertificate $trustedRootCert -PickHostNameFromBackendAddress -RequestTimeout 180 $apimPoolPortalSetting = New-AzApplicationGatewayBackendHttpSettings -Name "apimPoolPortalSetting" ` -Port 443 -Protocol "Https" -CookieBasedAffinity "Disabled" -Probe $apimPortalProbe ` -TrustedRootCertificate $trustedRootCert -PickHostNameFromBackendAddress -RequestTimeout 180 $apimPoolManagementSetting = New-AzApplicationGatewayBackendHttpSettings -Name "apimPoolManagementSetting" ` -Port 443 -Protocol "Https" -CookieBasedAffinity "Disabled" -Probe $apimManagementProbe ` -TrustedRootCertificate $trustedRootCert -PickHostNameFromBackendAddress -RequestTimeout 180使用每个 API 管理终结点各自的域名为其配置后端 IP 地址池。
$apimGatewayBackendPool = New-AzApplicationGatewayBackendAddressPool -Name "gatewaybackend" ` -BackendFqdns $gatewayHostname $apimPortalBackendPool = New-AzApplicationGatewayBackendAddressPool -Name "portalbackend" ` -BackendFqdns $portalHostname $apimManagementBackendPool = New-AzApplicationGatewayBackendAddressPool -Name "managementbackend" ` -BackendFqdns $managementHostname为应用程序网关创建传递规则以使用基本路由。
# Public/external gateway rules $gatewayRule = New-AzApplicationGatewayRequestRoutingRule -Name "gatewayrule" ` -RuleType Basic -HttpListener $gatewayListener -BackendAddressPool $apimGatewayBackendPool ` -BackendHttpSettings $apimPoolGatewaySetting -Priority 10 $portalRule = New-AzApplicationGatewayRequestRoutingRule -Name "portalrule" ` -RuleType Basic -HttpListener $portalListener -BackendAddressPool $apimPortalBackendPool ` -BackendHttpSettings $apimPoolPortalSetting -Priority 20 $managementRule = New-AzApplicationGatewayRequestRoutingRule -Name "managementrule" ` -RuleType Basic -HttpListener $managementListener -BackendAddressPool $apimManagementBackendPool ` -BackendHttpSettings $apimPoolManagementSetting -Priority 30 # Private/internal gateway rules $gatewayRulePrivate = New-AzApplicationGatewayRequestRoutingRule -Name "gatewayrule-private" ` -RuleType Basic -HttpListener $gatewayListenerPrivate -BackendAddressPool $apimGatewayBackendPool ` -BackendHttpSettings $apimPoolGatewaySetting -Priority 11 $portalRulePrivate = New-AzApplicationGatewayRequestRoutingRule -Name "portalrule-private" ` -RuleType Basic -HttpListener $portalListenerPrivate -BackendAddressPool $apimPortalBackendPool ` -BackendHttpSettings $apimPoolPortalSetting -Priority 21 $managementRulePrivate = New-AzApplicationGatewayRequestRoutingRule -Name "managementrule-private" ` -RuleType Basic -HttpListener $managementListenerPrivate -BackendAddressPool $apimManagementBackendPool ` -BackendHttpSettings $apimPoolManagementSetting -Priority 31提示
更改
-RuleType和路由,以限制对开发人员门户某些页面的访问。配置实例数目和应用程序网关的大小。 本示例使用 WAF_v2 SKU 以提高 API 管理资源的安全性。
对生产工作负载至少使用两个实例(容量)。 对于非生产方案或常规试验,建议只使用一个实例。 有关详细信息,请参阅 Azure 应用程序网关定价。
$sku = New-AzApplicationGatewaySku -Name "WAF_v2" -Tier "WAF_v2" -Capacity 2配置 WAF 模式。
提示
在设置过程中的一小段时间内,为测试防火墙规则,最好配置“检测”模式,该模式可监视和记录威胁警报,但不会阻止流量。 然后,可先对防火墙规则进行更新,再转换到“防护”模式,该模式可阻止规则检测到的入侵和攻击。
$config = New-AzApplicationGatewayWebApplicationFirewallConfiguration -Enabled $true -FirewallMode "Prevention"由于 TLS 1.0 目前是默认协议,因此请将应用程序网关设置为使用最新的 TLS 1.2 策略之一。
$policy = New-AzApplicationGatewaySslPolicy -PolicyType Predefined -PolicyName AppGwSslPolicy20220101
创建应用程序网关
创建包含前述步骤中所有配置对象的应用程序网关。 创建实例可能需要 15 分钟。
$appgw = New-AzApplicationGateway ` -Name $appgwName ` -ResourceGroupName $resGroupName ` -Location $location ` -Sku $sku ` -SslPolicy $policy ` -SslCertificates $certGateway, $certPortal, $certManagement ` -TrustedRootCertificate $trustedRootCert ` -BackendAddressPools $apimGatewayBackendPool, $apimPortalBackendPool, $apimManagementBackendPool ` -BackendHttpSettingsCollection $apimPoolGatewaySetting, $apimPoolPortalSetting, $apimPoolManagementSetting ` -GatewayIpConfigurations $gipconfig ` -FrontendIpConfigurations $fipconfig01, $fipconfig02 ` -FrontendPorts $fp01 ` -HttpListeners $gatewayListener, $portalListener, $managementListener, $gatewayListenerPrivate, $portalListenerPrivate, $managementListenerPrivate ` -RequestRoutingRules $gatewayRule, $portalRule, $managementRule, $gatewayRulePrivate, $portalRulePrivate, $managementRulePrivate ` -Probes $apimGatewayProbe, $apimPortalProbe, $apimManagementProbe ` -WebApplicationFirewallConfig $config确认 API 管理后端的运行状况。
Get-AzApplicationGatewayBackendHealth -Name $appgwName -ResourceGroupName $resGroupName
确保每个后端池的运行状况为“正常”。 如果需要对运行不正常的后端或运行状况未知的后端进行故障排除,请参阅排查应用程序网关中的后端运行状况问题。
创建 DNS 记录以从 Internet 访问 API 管理终结点
创建应用程序网关后,配置从 Internet 到 API 管理的通信。 创建 DNS A 记录,用于将你配置的每个 API 管理终结点主机名映射到应用程序网关的静态公共 IP 地址。 在本文中,示例主机名为 api.contoso.net、portal.contoso.net 和 management.contoso.net。
连接验证
出于快速测试目的,请考虑使用将应用程序网关的公共 IP 地址映射到 API 管理终结点主机名的条目以临时修改计算机的主机文件:
- 修改主机文件。 例如,如果应用程序网关的公共 IP 为
172.203.129.101,则条目可能为172.203.129.101 api.contoso.net。 - 针对 API 管理的状态终结点(前面用于运行状况探测的相同路径)执行 curl 命令:
curl -v https://api.contoso.net/status-0123456789abcdef这应返回200 Service Operational状态,这表示通过应用程序网关成功与 API 管理通信。
DNS 注意事项
应用程序网关现在具有专用和公共路径。 使用相同的域和端口可创建拆分式 DNS 情况,在这种情况下,应将外部 DNS 解析程序设置为将api.contoso.net解析为应用程序网关的外部 IP 地址,而内部 DNS 解析程序应将同一域解析为应用程序网关的内部 IP 地址。 此设置的优势在于,应用程序无需更改应用程序和 API 的内部或外部目标域或端口。 目标责任适当地推给了 DNS 解析程序。
总结
在虚拟网络中配置的 API 管理为配置的所有 API 提供单个网关接口,而不考虑这些 API 是托管在本地还是云中。 将应用程序网关与 API 管理集成可以灵活地、有选择性地启用可在 Internet 上访问的特定 API。 集成还会向 API 管理实例提供 WAF 作为前端。
相关内容
使用Azure 资源管理器模板进行设置
详细了解应用程序网关:
详细了解 API 管理和虚拟网络: