应用程序网关 v2 SKU 引入了允许与后端服务器建立 TLS 连接的受信任根证书。 此功能删除了 v1 SKU 中所需的身份验证证书(单个叶证书)的使用。 根证书是来自后端证书服务器的 Base-64 编码的 X.509(.CER) 格式根证书。 它标识颁发服务器证书的根证书颁发机构 (CA),服务器证书随后将用于 TLS/SSL 通信。
如果已知 CA(例如 GoDaddy 或 DigiCert)对网站证书进行签名,则应用程序网关默认信任网站的证书。 在这种情况下,不需要显式上传根证书。 有关详细信息,请参阅应用程序网关的 TLS 终止和端到端 TLS 概述。 但是,如果有开发/测试环境,但不想要购买由已验证的 CA 签名的证书,可以创建自己的自定义根 CA 和用该根 CA 签名的分支证书。
注释
默认情况下,自生成证书不受信任,难以维护。 此外,它们还可以使用过时的哈希和密码套件,这些套件并不强。 为了提高安全性,请购买由知名证书颁发机构签名的证书。
使用以下选项为后端 TLS 连接生成专用证书。
使用 专用证书生成器工具。 通过使用提供的域名(公用名),此工具执行与本文中所述的步骤相同的步骤来生成根证书和服务器证书。 使用生成的证书文件,可以立即将根证书 (.CER) 文件上传到网关的后端设置,并将相应的证书链 (.PFX) 上传到后端服务器。 下载的 ZIP 文件中还提供了 PFX 文件的密码。
使用 OpenSSL 命令根据需要自定义和生成证书。 如果要完全自行执行此过程,请继续按照本文中的说明进行作。
在这篇文章中,你将学会如何:
- 创建自己的自定义证书颁发机构
- 创建由自定义 CA 签名的自签名证书
- 将自签名的根证书上传到应用程序网关,以便对后端服务器进行身份验证
先决条件
在运行 Windows 或 Linux 的计算机上安装 OpenSSL
虽然其他工具可能可用于证书管理,但本教程使用 OpenSSL。 你可能会发现,许多 Linux 分发版(如 Ubuntu)中已捆绑 OpenSSL。
一个 Web 服务器
例如,用于测试证书的 Apache、IIS 或 NGINX。
一个应用程序网关 v2 SKU
如果没有现有的应用程序网关,请参阅快速入门:使用 Azure 应用程序网关直接 Web 流量 - Azure 门户。
创建根 CA 证书
使用 OpenSSL 创建根 CA 证书。
创建根密钥
登录到安装了 OpenSSL 的计算机并运行以下命令。 此命令创建加密密钥。
openssl ecparam -out contoso.key -name prime256v1 -genkey
创建根证书并对其进行自签名
使用以下命令生成证书签名请求 (CSR)。
openssl req -new -sha256 -key contoso.key -out contoso.csr出现提示时,键入根密钥的密码,以及自定义 CA 的组织信息,例如国家/地区、州、组织、OU 和完全限定的域名(此域是颁发者)。
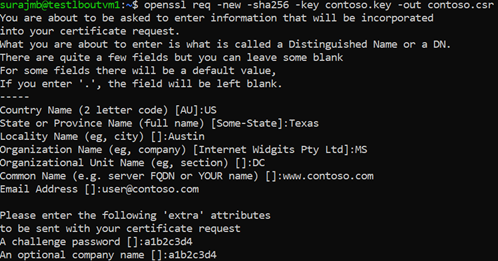
使用以下命令生成根证书。
openssl x509 -req -sha256 -days 365 -in contoso.csr -signkey contoso.key -out contoso.crt上述命令将创建根证书。 使用此证书对服务器证书进行签名。
创建服务器证书
接下来,使用 OpenSSL 创建服务器证书。
创建证书的密钥
使用以下命令生成服务器证书的密钥。
openssl ecparam -out fabrikam.key -name prime256v1 -genkey
创建 CSR(证书签名请求)
CSR 是请求证书时提供给 CA 的公钥。 CA 将针对此特定请求颁发证书。
注释
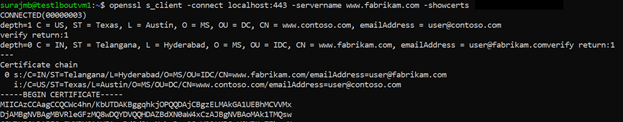
服务器证书的 CN(公用名)必须与颁发者的域不同。 例如,在本例中,颁发者的 CN 是 www.contoso.com,服务器证书的 CN 是 www.fabrikam.com
使用以下命令生成 CSR:
openssl req -new -sha256 -key fabrikam.key -out fabrikam.csr出现提示时,请键入根密钥的密码,以及自定义 CA 的组织信息:国家/地区、省/市/自治区、组织、组织单位和完全限定的域名。 此域名是网站的域名,它应与签发者不同。
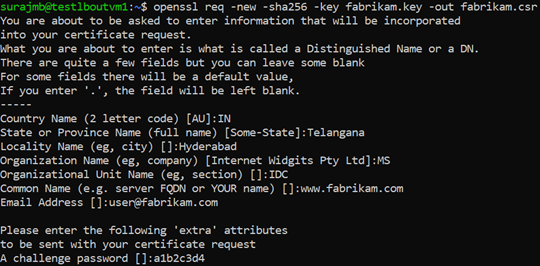
使用 CSR 和密钥生成证书,并使用 CA 的根密钥为该证书签名
使用以下命令以创建证书:
openssl x509 -req -in fabrikam.csr -CA contoso.crt -CAkey contoso.key -CAcreateserial -out fabrikam.crt -days 365 -sha256
验证新建的证书
使用以下命令列显 CRT 文件的输出,并验证其内容:
openssl x509 -in fabrikam.crt -text -noout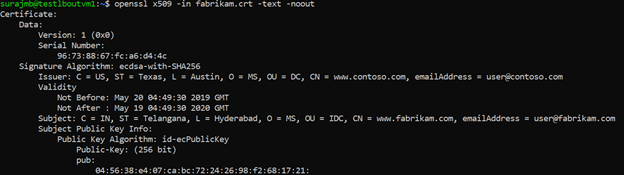
验证目录中的文件,确保其中具有以下文件:
- contoso.crt
- contoso.key
- fabrikam.crt
- fabrikam.key
在 Web 服务器的 TLS 设置中配置证书
在 Web 服务器中,使用 fabrikam.crt 和fabrikam.key文件配置 TLS。 如果 Web 服务器无法获取两个文件,则可以使用 OpenSSL 命令将它们合并为单个 .pem 或 .pfx 文件。
IIS
有关如何导入证书并将其上传为 IIS 上的服务器证书的说明,请参阅如何:在 Windows Server 2003 的 Web 服务器上安装导入的证书。
有关 TLS 绑定说明,请参阅如何在 IIS 7 上设置 SSL。
Apache
以下配置是在 Apache 中为 SSL 配置的虚拟主机示例:
<VirtualHost www.fabrikam:443>
DocumentRoot /var/www/fabrikam
ServerName www.fabrikam.com
SSLEngine on
SSLCertificateFile /home/user/fabrikam.crt
SSLCertificateKeyFile /home/user/fabrikam.key
</VirtualHost>
NGINX
以下配置是 NGINX 服务器块与 TLS 配置的示例:
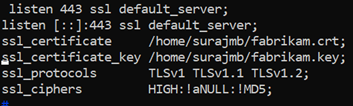
使用自签名证书访问服务器
将根证书添加到计算机的受信任根存储中。 访问网站时,请确保浏览器中显示整个证书链。
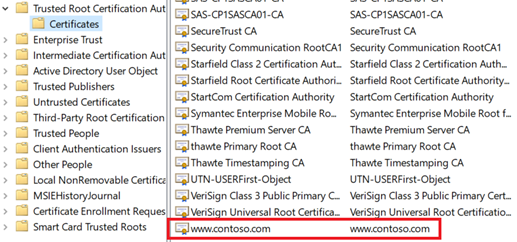
注释
DNS 应配置为将 Web 服务器名称(在本例中)
www.fabrikam.com指向 Web 服务器的 IP 地址。 否则,可以编辑主文件来解析名称。浏览到你的网站,然后单击浏览器地址框中的锁定图标来验证站点和证书信息。
使用 OpenSSL 验证配置
或者,可以使用 OpenSSL 来验证证书。
openssl s_client -connect localhost:443 -servername www.fabrikam.com -showcerts
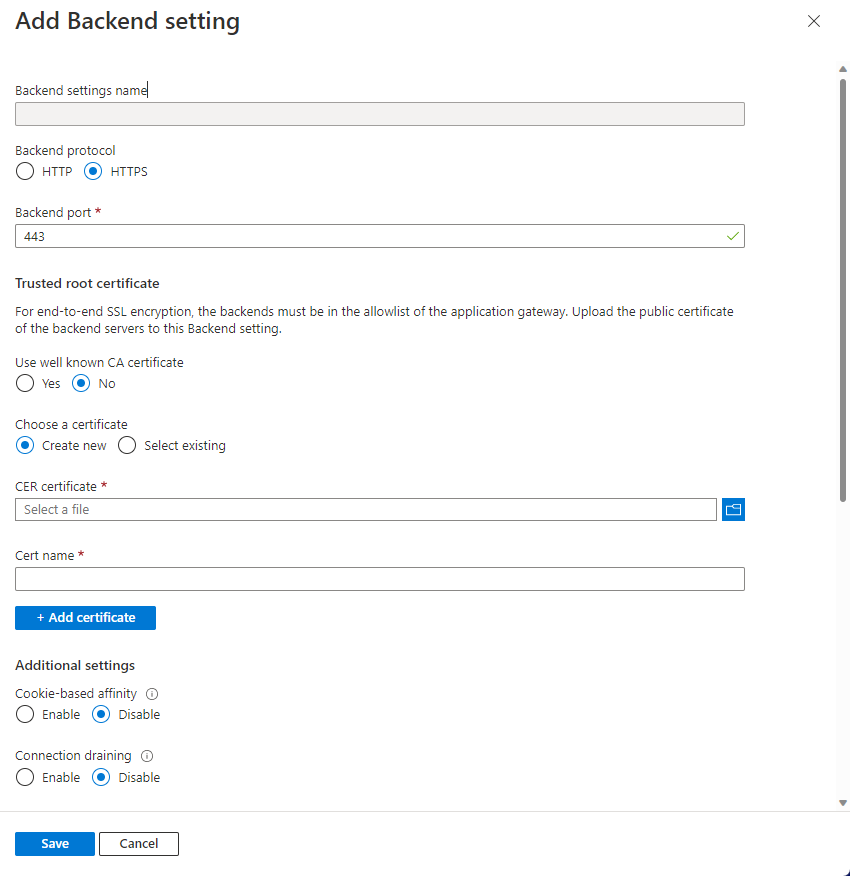
将根证书上传到应用程序网关的 HTTP 设置
若要在应用程序网关中上传证书,必须将 .crt 证书导出为 Base-64 编码的 .cer 格式。 由于 .crt 已包含 Base-64 编码格式的公钥,因此,只需将文件扩展名从 .crt 重命名为 .cer 即可。
Azure 门户
若要从门户上传受信任的根证书,请选择“后端设置”,然后选择“后端协议”中的“HTTPS”。
Azure PowerShell
或者,使用 Azure CLI 或 Azure PowerShell 上传根证书。 以下代码是一个 Azure PowerShell 示例。
注释
以下示例将受信任的根证书添加到应用程序网关,创建新的 HTTP 设置,并添加新规则(假设后端池和侦听器已存在)。
## Add the trusted root certificate to the Application Gateway
$gw=Get-AzApplicationGateway -Name appgwv2 -ResourceGroupName rgOne
Add-AzApplicationGatewayTrustedRootCertificate `
-ApplicationGateway $gw `
-Name CustomCARoot `
-CertificateFile "C:\Users\surmb\Downloads\contoso.cer"
$trustedroot = Get-AzApplicationGatewayTrustedRootCertificate `
-Name CustomCARoot `
-ApplicationGateway $gw
## Get the listener, backend pool and probe
$listener = Get-AzApplicationGatewayHttpListener `
-Name basichttps `
-ApplicationGateway $gw
$bepool = Get-AzApplicationGatewayBackendAddressPool `
-Name testbackendpool `
-ApplicationGateway $gw
Add-AzApplicationGatewayProbeConfig `
-ApplicationGateway $gw `
-Name testprobe `
-Protocol Https `
-HostName "www.fabrikam.com" `
-Path "/" `
-Interval 15 `
-Timeout 20 `
-UnhealthyThreshold 3
$probe = Get-AzApplicationGatewayProbeConfig `
-Name testprobe `
-ApplicationGateway $gw
## Add the configuration to the HTTP Setting and don't forget to set the "hostname" field
## to the domain name of the server certificate as this will be set as the SNI header and
## will be used to verify the backend server's certificate. Note that TLS handshake will
## fail otherwise and might lead to backend servers being deemed as Unhealthy by the probes
Add-AzApplicationGatewayBackendHttpSettings `
-ApplicationGateway $gw `
-Name testbackend `
-Port 443 `
-Protocol Https `
-Probe $probe `
-TrustedRootCertificate $trustedroot `
-CookieBasedAffinity Disabled `
-RequestTimeout 20 `
-HostName www.fabrikam.com
## Get the configuration and update the Application Gateway
$backendhttp = Get-AzApplicationGatewayBackendHttpSettings `
-Name testbackend `
-ApplicationGateway $gw
Add-AzApplicationGatewayRequestRoutingRule `
-ApplicationGateway $gw `
-Name testrule `
-RuleType Basic `
-BackendHttpSettings $backendhttp `
-HttpListener $listener `
-BackendAddressPool $bepool
Set-AzApplicationGateway -ApplicationGateway $gw
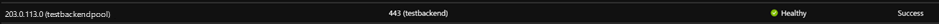
验证应用程序网关后端运行状况
- 选择应用程序网关的 “后端运行状况 ”视图,检查探测是否正常。
- 应会看到,HTTPS 探测的状态为“正常”。
后续步骤
若要了解有关应用程序网关上的 SSL\TLS 的详细信息,请参阅应用程序网关的 TLS 终止和端到端 TLS 概述。