用于确定可以在 Log Analytics 工作区中访问哪些数据的因素包括:
- 工作区本身的设置。
- 对将数据发送到工作区的资源的访问权限。
- 访问工作区所用的方法。
本文介绍如何管理对 Log Analytics 工作区中数据的访问。
概述
下表描述了定义可访问的数据的因素。 后面的部分进一步描述了每个因素。
| 因子 | 说明 |
|---|---|
| 访问模式 | 访问工作区所用的方法。 定义可用数据的范围,以及应用的访问控制模式。 |
| 访问控制模式 | 工作区中的设置,用于定义是要在工作区级别还是资源级别应用权限。 |
| Azure 基于角色的访问控制 (RBAC) | 应用于工作区的或向工作区发送数据的资源的个人或用户组的权限。 定义你有权访问的数据。 |
| 精细 RBAC | 可以基于条件来定义表和行级访问的可选权限。 适用于所有访问模式,但只应用于工作区访问控制模式。 |
| 表级别 Azure RBAC | 定义你可以在工作区中访问的特定数据类型的可选权限。 适用于所有访问模式或访问控制模式。 |
访问模式
访问模式是指如何访问 Log Analytics 工作区,并定义在当前会话期间可以访问的数据。 模式是根据你在 Log Analytics 中选择的范围确定的。
有两种访问模式:
工作区上下文:你可以查看工作区中你有权访问的所有日志。 在此模式下,只能查询工作区中你有权访问的表内的所有数据。 使用工作区作为范围来访问日志时(例如,在 Azure 门户上的“Azure Monitor”菜单中选择“日志”时),将使用此访问模式。
资源上下文:访问特定资源、资源组或订阅的工作区时(例如,在 Azure 门户上的资源菜单中选择“日志”时),只能查看所有表中你有权访问的资源的日志。 在此模式下,只能查询与该资源关联的数据。 此模式还支持精细 Azure RBAC。 工作区使用资源上下文日志模型,其中 Azure 资源发出的每条日志记录将自动与此资源关联。
仅当记录与相关资源关联时,才可以在资源上下文查询中使用这些记录。 若要检查这种关联,请运行一个查询并验证 _ResourceId 列是否已填充。
以下资源存在已知限制:
- Azure 外部的计算机:只有 Azure Arc for Servers 支持资源上下文。
- Application Insights:仅在使用基于工作区的 Application Insights 资源时支持资源上下文。
- Azure Service Fabric
比较访问模式
下表汇总了访问模式:
| 问题 | 工作区上下文 | 资源上下文 |
|---|---|---|
| 每种模式适合哪类用户? | 集中管理。 需要配置数据收集的管理员,以及需要访问各种资源的用户。 此外,需要访问 Azure 外部资源的日志的用户目前也需要使用此模式。 |
应用程序团队。 受监视 Azure 资源的管理员。 使他们能够专注于自己的资源而无需筛选。 |
| 用户需要哪些权限才能查看日志? | 对工作区的权限。 请参阅使用工作区权限管理访问权限中的“工作区权限”。 |
对资源的读取访问权限。 请参阅使用 Azure 权限管理访问权限中的“资源权限”。 权限可以从资源组或订阅继承,也可以直接分配给资源。 系统会自动分配对资源日志的权限。 用户不需要访问工作区。 |
| 权限范围是什么? | 工作区。 有权访问工作区的用户可以通过他们有权访问的表查询该工作区中的所有日志。 请参阅设置表级读取访问权限。 |
Azure 资源。 用户可以在任何工作区中查询他们有权访问的资源、资源组或订阅的日志,但无法查询其他资源的日志。 |
| 用户如何访问日志? | 在“Azure Monitor”菜单中选择“日志”。 在“Log Analytics 工作区”中选择“日志”。 当选择了“Log Analytics 工作区”作为资源类型时,从 Azure Monitor“工作簿”中。 |
在 Azure 资源的菜单中选择“日志”。 用户有权访问该资源的数据。 在“Azure Monitor”菜单中选择“日志”。 用户有权访问他们有权访问的所有资源的数据。 如果用户有权访问该工作区,请选择“Log Analytics 工作区”中的“日志”。 当选择了该资源作为资源类型时,从 Azure Monitor“工作簿”中。 |
访问控制模式
访问控制模式是每个工作区中的一项设置,定义如何确定该工作区的权限。
需要工作区权限。 此控制模式不允许精细 Azure RBAC。 要使某个用户能够访问工作区,必须为其授予对该工作区或特定表的权限。
如果用户以工作区上下文模式访问工作区,将可以访问他们有权访问的任何表中的所有数据。 如果用户以资源上下文模式访问工作区,则只能访问他们有权访问的任何表中该资源的数据。
这是在 2019 年 3 月之前创建的所有工作区的默认设置。
使用资源或工作区权限。 此控制模式允许精细 Azure RBAC。 可以通过分配 Azure
read权限,仅向用户授予与他们可查看的资源相关联的数据的访问权限。当用户以工作区上下文模式访问工作区时,将应用工作区权限。 当用户以资源上下文模式访问工作区时,只会验证资源权限,而会忽略工作区权限。 要为用户启用 Azure RBAC,可将其从工作区权限中删除,并允许识别其资源权限。
这是在 2019 年 3 月之后创建的所有工作区的默认设置。
注意
如果用户只对工作区拥有资源权限,则他们只能使用资源上下文模式访问工作区(假设工作区访问模式设置为“使用资源或工作区权限”)。
为工作区配置访问控制模式
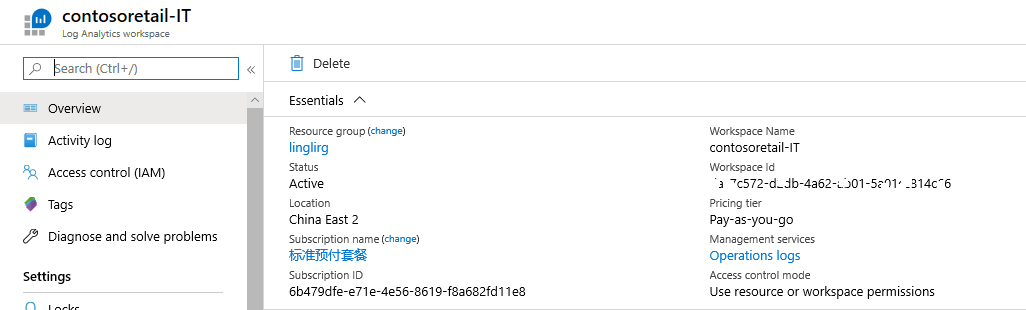
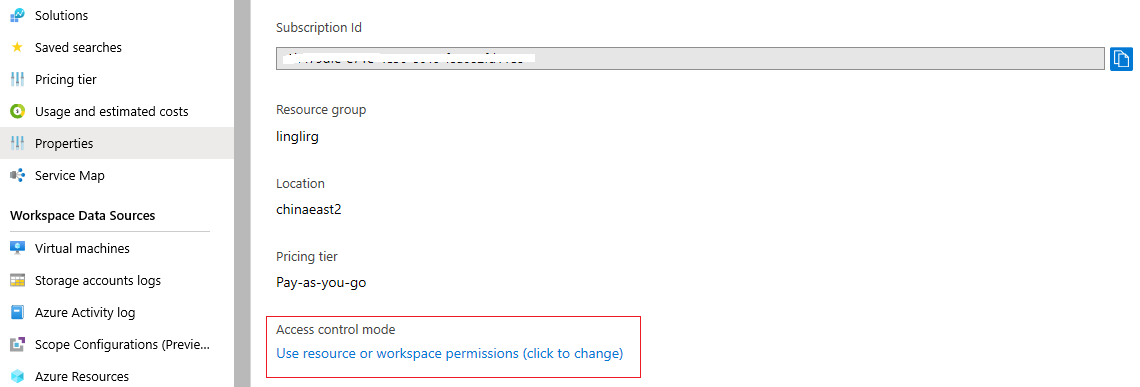
在工作区“概述”页上的“Log Analytics 工作区”菜单中查看当前的工作区访问控制模式。
在工作区的“属性”页中更改此设置。 如果你无权配置工作区,则会禁止更改此设置。
Azure RBAC
对工作区的访问权限是使用 Azure RBAC 管理的。 若要使用 Azure 权限授予对 Log Analytics 工作区的访问权限,请执行分配 Azure 角色来管理对 Azure 订阅资源的访问权限中的步骤。
工作区权限
每个工作区可以关联多个帐户。 每个帐户可以访问多个工作区。 下表列出了不同工作区操作的 Azure 权限:
| 操作 | 所需 Azure 权限 | 说明 |
|---|---|---|
| 更改定价层。 | Microsoft.OperationalInsights/workspaces/*/write |
|
| 在 Azure 门户中创建工作区。 | Microsoft.Resources/deployments/* Microsoft.OperationalInsights/workspaces/* |
|
| 查看工作区基本属性并进入门户中的工作区窗格。 | Microsoft.OperationalInsights/workspaces/read |
|
| 使用任何接口查询日志。 | Microsoft.OperationalInsights/workspaces/query/read |
|
| 使用查询访问所有日志类型。 | Microsoft.OperationalInsights/workspaces/query/*/read |
|
| 访问特定的日志表 - 旧方法 | Microsoft.OperationalInsights/workspaces/query/<table_name>/read |
|
| 读取工作区密钥,以便能够将日志发送到此工作区。 | Microsoft.OperationalInsights/workspaces/sharedKeys/action |
|
| 创建或更新摘要规则 | Microsoft.Operationalinsights/workspaces/summarylogs/write |
|
| 添加和删除监视解决方案。 | Microsoft.Resources/deployments/*Microsoft.OperationalInsights/*Microsoft.OperationsManagement/*Microsoft.Automation/*Microsoft.Resources/deployments/*/write需要在资源组或订阅级别授予这些权限。 |
|
| 查看“备份”和“Site Recovery”解决方案磁贴中的数据。 | 管理员/共同管理员 访问通过经典部署模型部署的资源。 |
|
| 运行搜索作业。 | Microsoft.OperationalInsights/workspaces/tables/writeMicrosoft.OperationalInsights/workspaces/searchJobs/write |
|
| 从长期保留内容中还原数据。 | Microsoft.OperationalInsights/workspaces/tables/writeMicrosoft.OperationalInsights/workspaces/restoreLogs/write |
|
| 创建或编辑汇总规则 | Microsoft.Operationalinsights/workspaces/summarylogs/write |
内置角色
将用户分配到这些角色,以便在不同的范围为其授予访问权限:
- 订阅:访问订阅中的所有工作区
- 资源组:访问资源组中的所有工作区
- 资源:仅访问指定工作区
在资源(工作区)级别创建分配,以确保准确进行访问控制。 使用自定义角色,创建具有所需的特定权限的角色。
注意
若要为某个用户角色添加和删除用户,必须拥有 Microsoft.Authorization/*/Delete 和 Microsoft.Authorization/*/Write 权限。
Log Analytics 数据读者
提供运行查询所需的最低权限,并使用 Log Analytics 数据读取者角色查看元数据。 它是精细 RBAC 的理想角色,它使用角色分配条件进一步控制 对表 和 行 级别的数据的访问。 有关详细信息,请参阅 粒度化的 RBAC。
| 类型 | 权限 | 说明 |
|---|---|---|
| 操作 | Microsoft.OperationalInsights/workspaces/query/read |
对工作区中的数据运行查询 |
| 操作 | Microsoft.OperationalInsights/workspaces/read |
读取现有工作区 |
| DataActions | Microsoft.OperationalInsights/workspaces/tables/data/read |
在与精细 RBAC 一起使用时,读取对工作区或更多细粒度数据实体(例如特定表或行)的数据访问权限 |
Log Analytics 读者
Log Analytics 读取者角色的成员可以查看所有监视数据和监视设置,包括所有 Azure 资源上的 Azure 诊断配置。 允许成员查看有关分配范围内资源的所有数据,包括:
- 查看和搜索所有监视数据。
- 查看监视设置,包括查看 Azure 诊断在所有 Azure 资源上的配置。
Log Analytics 读者角色包括以下 Azure 操作:
| 类型 | 权限 | 说明 |
|---|---|---|
| 操作 | */read |
能够查看所有 Azure 资源和资源配置。 包括查看: - 虚拟机扩展状态。 - Azure 诊断在资源上的配置。 - 所有资源的所有属性和设置。 对于工作区,允许使用完全不受限制的权限来读取工作区设置和查询数据。 在前面的列表中查看更精细的选项。 |
| 操作 | Microsoft.Support/* |
能够创建支持案例。 |
| 非操作 | Microsoft.OperationalInsights/workspaces/sharedKeys/read |
防止读取工作区密钥,该密钥是使用数据集合 API 和安装代理所必需的。 这可以防止用户向工作区添加新资源。 |
Log Analytics 参与者
Log Analytics 参与者角色的成员可以:
- 读取 Log Analytics 读取者角色授予的所有监视数据。
- 编辑 Azure 资源的监视设置,包括:
- 将 VM 扩展添加到 VM。
- 在所有 Azure 资源上配置 Azure 诊断。
- 创建和配置自动化帐户。 必须在资源组或订阅级别授予权限。
- 添加和删除管理解决方案。 必须在资源组或订阅级别授予权限。
- 读取存储帐户密钥。
- 从 Azure 存储配置日志收集。
- 配置数据导出规则。
- 运行搜索作业。
- 从长期保留内容中还原数据。
警告
可以使用该权限向虚拟机添加虚拟机扩展,以获取对虚拟机的完全控制。
Log Analytics 参与者角色包括以下 Azure 操作:
| 权限 | 说明 |
|---|---|
*/read |
能够查看所有 Azure 资源和资源配置。 包括查看: - 虚拟机扩展状态。 - Azure 诊断在资源上的配置。 - 所有资源的所有属性和设置。 对于工作区,允许使用完全不受限制的权限来读取工作区设置和查询数据。 在前面的列表中查看更精细的选项。 |
Microsoft.Automation/automationAccounts/* |
能够创建和配置 Azure 自动化帐户,包括添加和编辑 runbook。 |
Microsoft.ClassicCompute/virtualMachines/extensions/*Microsoft.Compute/virtualMachines/extensions/* |
添加、更新和删除虚拟机扩展,包括旧代理。 |
Microsoft.ClassicStorage/storageAccounts/listKeys/actionMicrosoft.Storage/storageAccounts/listKeys/action |
查看存储帐户密钥。 在将 Log Analytics 配置为从 Azure 存储帐户读取日志时需要。 |
Microsoft.Insights/alertRules/* |
添加、更新和删除警报规则。 |
Microsoft.Insights/diagnosticSettings/* |
添加、更新和删除 Azure 资源上的诊断设置。 |
Microsoft.OperationalInsights/* |
添加、更新和删除 Log Analytics 工作区的配置。 若要编辑工作区高级设置,用户需要 Microsoft.OperationalInsights/workspaces/write。 |
Microsoft.OperationsManagement/* |
添加和删除管理解决方案。 |
Microsoft.Resources/deployments/* |
创建和删除部署。 添加和删除解决方案、工作区和自动化帐户所必需。 |
Microsoft.Resources/subscriptions/resourcegroups/deployments/* |
创建和删除部署。 添加和删除解决方案、工作区和自动化帐户所必需。 |
资源权限
要从资源上下文中的工作区读取数据或将数据发送到工作区,需要对资源拥有以下权限:
| 权限 | 说明 |
|---|---|
Microsoft.Insights/logs/*/read |
可以查看资源的所有日志数据 |
Microsoft.Insights/logs/<tableName>/read例如: Microsoft.Insights/logs/Heartbeat/read |
能够查看此资源的特定表 - 旧方法 |
Microsoft.Insights/diagnosticSettings/write |
可配置诊断设置以允许设置此资源的日志 |
/read 权限通常是通过包含 */read 或 * 权限的角色(例如内置读者和参与者角色)授予的。 包含特定操作的自定义角色或专用内置角色可能没有此权限。
自定义角色示例
除了为 Log Analytics 工作区使用内置角色外,还可以创建自定义角色来分配更精细的权限。 下面是一些常用示例。
示例 1:授予用户从其资源读取日志数据的权限。
- 将工作区访问控制模式配置为使用工作区或资源权限。
- 向用户授予对其资源的
*/read或Microsoft.Insights/logs/*/read权限。 如果已经为用户分配了对工作区的 Log Analytics 读取者角色,则不需要执行额外的操作。
示例 2:授予用户从其资源读取日志数据以及运行搜索作业的权限。
- 将工作区访问控制模式配置为使用工作区或资源权限。
- 向用户授予对其资源的
*/read或Microsoft.Insights/logs/*/read权限。 如果已经为用户分配了对工作区的 Log Analytics 读取者角色,则不需要执行额外的操作。 - 为用户授予对工作区的以下权限:
-
Microsoft.OperationalInsights/workspaces/tables/write:必须具有此权限才能创建搜索结果表 (_SRCH)。 -
Microsoft.OperationalInsights/workspaces/searchJobs/write:必须具有此权限才允许执行搜索作业操作。
-
示例 3:授予用户从其资源读取日志数据以及将其资源配置为向 Log Analytics 工作区发送日志的权限。
- 将工作区访问控制模式配置为使用工作区或资源权限。
- 为用户授予对工作区的以下权限:
Microsoft.OperationalInsights/workspaces/read和Microsoft.OperationalInsights/workspaces/sharedKeys/action。 用户无法使用这些权限执行任何工作区级别的查询。 他们只能枚举工作区,并将其用作诊断设置或代理配置的目标。 - 为用户授予对其资源的以下权限:
Microsoft.Insights/logs/*/read和Microsoft.Insights/diagnosticSettings/write。 如果已经为用户分配了 Log Analytics 参与者角色、读取者角色或者为其授予了对此资源的*/read权限,则不需要执行额外的操作。
示例 4:授予用户从其资源读取日志数据的权限,但不允许将日志发送到 Log Analytics 工作区或读取安全事件。
- 将工作区访问控制模式配置为使用工作区或资源权限。
- 为用户授予对其资源的以下权限:
Microsoft.Insights/logs/*/read。 - 添加以下 NonAction 以阻止用户读取 SecurityEvent 类型:
Microsoft.Insights/logs/SecurityEvent/read。 NonAction 应该与提供读取权限的操作 (Microsoft.Insights/logs/*/read) 包含在同一个自定义角色中。 如果用户从已分配到此资源或已分配到订阅或资源组的另一个角色继承读取操作,他们将能够读取所有日志类型。 如果他们继承*/read(例如,“读取者”或“参与者”角色存在的此操作),此方案也是如此。
示例 5:授予用户从其资源和所有 Microsoft Entra 登录中读取日志数据以及读取 Log Analytics 工作区中的更新管理解决方案日志数据的权限。
- 将工作区访问控制模式配置为使用工作区或资源权限。
- 为用户授予对工作区的以下权限:
-
Microsoft.OperationalInsights/workspaces/read:需要此权限用户才可以枚举工作区并在 Azure 门户中打开工作区窗格 -
Microsoft.OperationalInsights/workspaces/query/read:需要此权限每位用户才可以执行查询 -
Microsoft.OperationalInsights/workspaces/query/SigninLogs/read:能够读取 Microsoft Entra 登录日志 -
Microsoft.OperationalInsights/workspaces/query/Update/read:需要此权限才能读取更新管理解决方案日志 -
Microsoft.OperationalInsights/workspaces/query/UpdateRunProgress/read:需要此权限才能读取更新管理解决方案日志 -
Microsoft.OperationalInsights/workspaces/query/UpdateSummary/read:需要此权限才能读取更新管理日志 -
Microsoft.OperationalInsights/workspaces/query/Heartbeat/read:需要此权限才能使用更新管理解决方案 -
Microsoft.OperationalInsights/workspaces/query/ComputerGroup/read:需要此权限才能使用更新管理解决方案 - 为用户授予对其资源的以下权限:分配给“读取者”角色的
*/read,或Microsoft.Insights/logs/*/read
-
示例 6:限制用户从长期保留内容中还原数据。
- 将工作区访问控制模式配置为使用工作区或资源权限。
- 为用户分配 Log Analytics 参与者角色。
- 添加以下 NonAction 以阻止用户从长期保留内容中还原数据:
Microsoft.OperationalInsights/workspaces/restoreLogs/write
设置精细 RBAC
这是表和行级访问控制的建议方法。 有关详细信息,请参阅 Azure Monitor 中的精细基于角色的访问控制(RBAC)。
设置表级读取访问权限
精细 RBAC 具有表级读取访问的所有功能。 新访问控制配置的最佳做法是实现精细的 RBAC。 若要引用仅执行表级控制的方法,请参阅 “管理表级读取访问权限”。
后续步骤
- 请参阅 Log Analytics 代理概述,以从数据中心或其他云环境中的计算机收集数据。
- 请参阅收集有关 Azure 虚拟机的数据,以配置 Azure VM 的数据收集。