在 Azure SignalR 服务中,可以使用 Microsoft Entra ID 中的托管标识来执行以下操作:
- 获取访问令牌。
- 访问 Azure 密钥保管库中的机密。
该服务仅支持一个托管标识。 可以创建系统分配的标识或用户分配的标识。 系统分配的标识专用于 Azure SignalR 服务实例,并且会在删除实例时被删除。 用户分配的标识独立于 Azure SignalR 服务资源进行管理。
本文介绍了如何为 Azure SignalR 服务创建托管标识,以及如何在无服务器方案中使用它。
先决条件
若要使用托管标识,必须具有以下项:
- Azure 订阅。 如果没有 Azure 订阅,可在开始前创建一个试用帐户。
- Azure SignalR 服务资源。
- 要访问的上游资源,例如 Azure 密钥保管库资源。
- Azure Functions 应用(函数应用)。
将托管标识添加到 Azure SignalR 服务
可以在 Azure 门户或 Azure CLI 中将托管标识添加到 Azure SignalR 服务。 本文介绍如何在 Azure 门户中将托管标识添加到 Azure SignalR 服务。
添加系统分配的标识
要将系统分配的托管标识添加到 Azure SignalR 服务实例,请:
在 Azure 门户中,浏览到 Azure SignalR 服务实例。
选择“标识”。
在“系统分配”选项卡中,将“状态”切换为“启用” 。
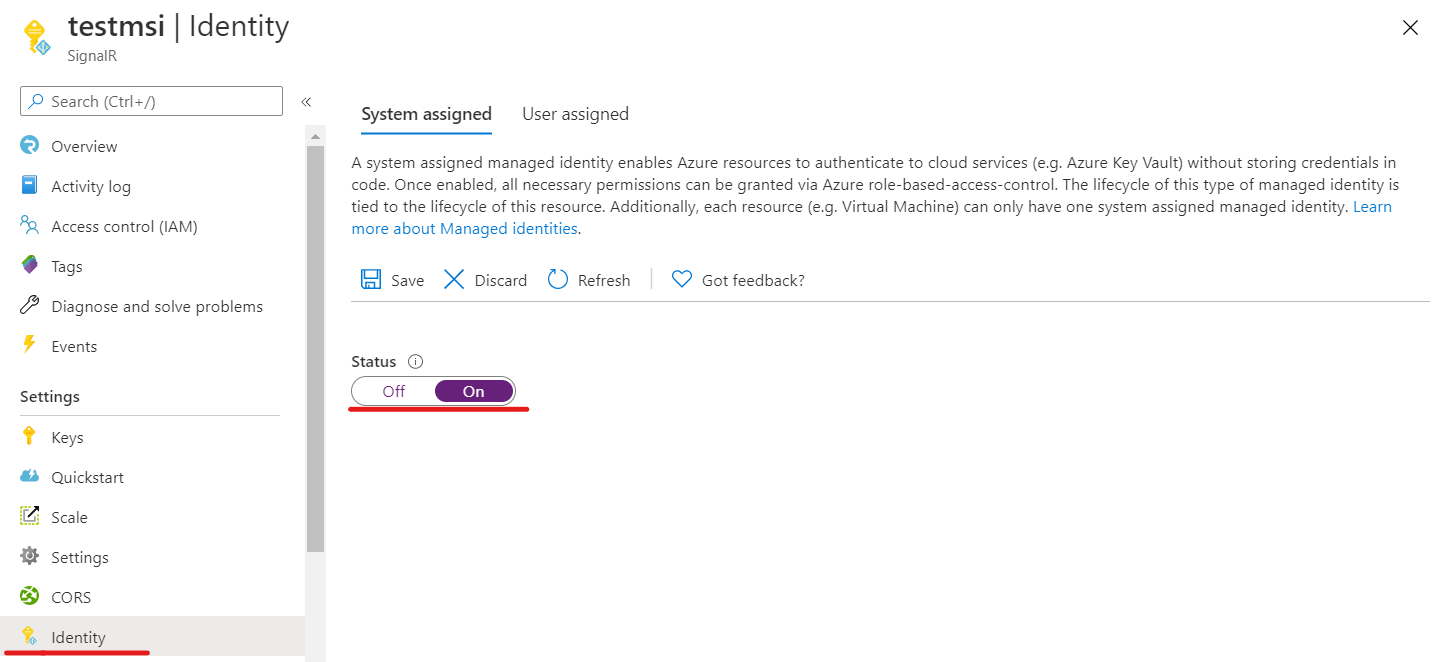
选择“保存”。
选择“是”确认更改。
添加用户分配的标识
要将用户分配的标识添加到 Azure SignalR 服务实例,需要创建标识,然后将其添加到服务。
根据这些说明创建用户分配的托管标识资源。
在 Azure 门户中,浏览到 Azure SignalR 服务实例。
选择“标识”。
在“用户分配”选项卡上,选择“添加”。
在“用户分配的托管标识”下拉菜单中选择标识。
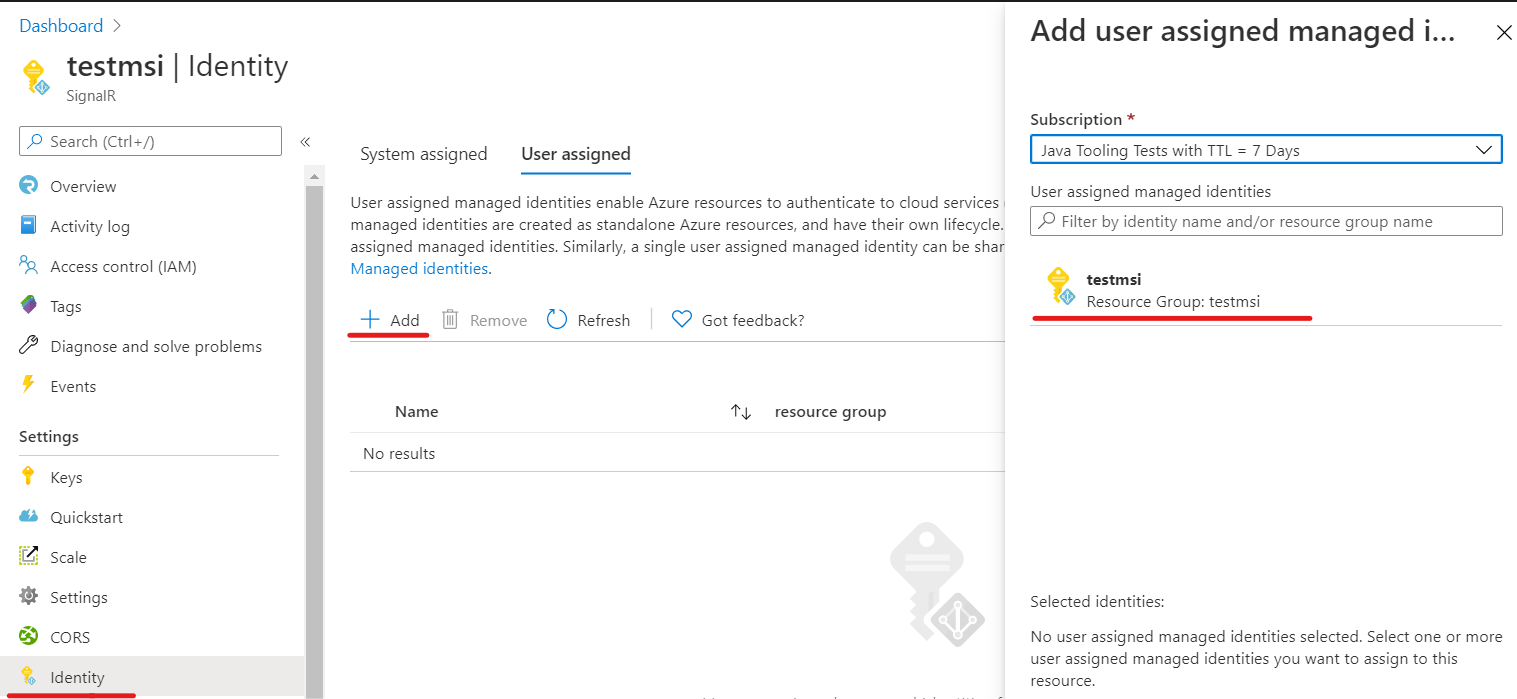
选择 添加 。
在无服务器方案中使用托管标识
Azure SignalR 服务是一项完全托管的服务。 它使用托管标识来获取访问令牌。 在无服务器方案中,该服务将访问令牌添加到上游请求中的 Authorization 标头中。
在上游设置中启用托管标识身份验证
将系统分配的标识 或 用户分配的标识 添加到 Azure SignalR 服务实例后,可以在上游终结点设置中启用托管标识身份验证:
在 Azure 门户中,浏览到 Azure SignalR 服务实例。
在菜单中选择“设置”。
选择“无服务器”服务模式。
在“添加上游 URL 模式”文本框中输入上游终结点 URL 模式。 请参阅《URL 模板设置》。
选择“添加一个上游设置”,然后选择任何星号。
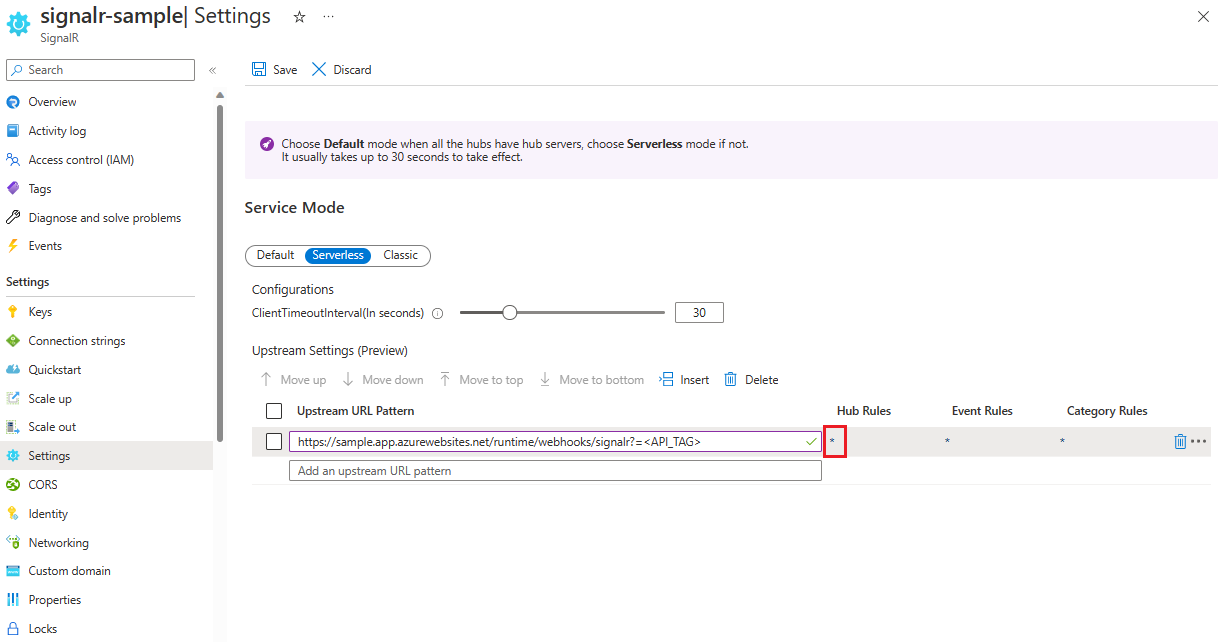
在“上游设置”中,配置上游终结点设置。
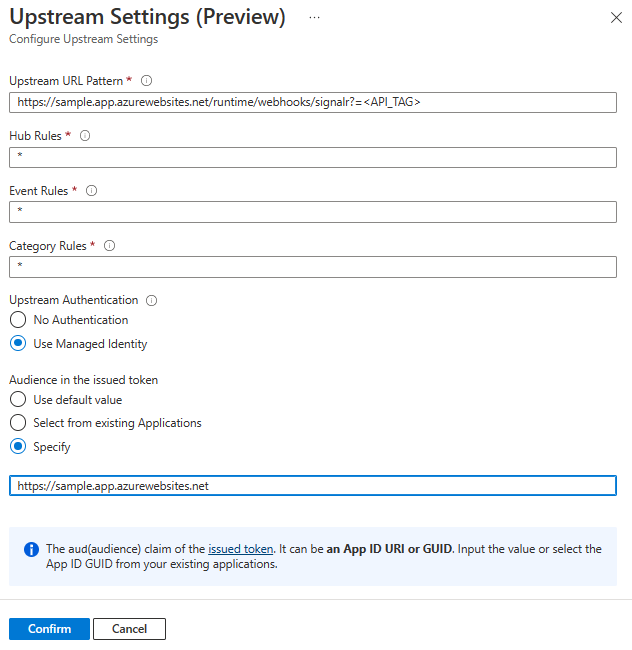
在托管标识身份验证设置中,对于“颁发的令牌中的受众”,可以指定目标资源。 该资源将成为获取的访问令牌中的
aud声明,可在上游终结点中用作验证的一部分。 资源可以采用下列格式之一:- 服务主体的应用程序(客户端)ID。
- 服务主体的应用程序 ID URI。
重要
使用空资源实际上可获取一个以 Microsoft Graph 为目标的令牌。 如今,Microsoft Graph 启用令牌加密,因此应用程序无法对 Microsoft Graph 以外的令牌进行身份验证。 在常见做法中,应始终创建服务主体来表示上游目标。 同时,设置已创建的服务主体的“应用程序 ID”或“应用程序 ID URI”。
函数应用中的身份验证
可以使用 Azure 门户轻松设置函数应用的访问验证,而无需更改代码:
在 Azure 门户中转到函数应用。
从菜单中选择“身份验证”。
选择“添加标识提供者”。
在“基本信息”选项卡上的“标识提供者”下拉列表中,选择“Microsoft”。
在“请求未经身份验证时需执行的操作”中,选择“使用 Microsoft Entra ID 登录”。
默认会选中用于创建新注册的选项。 可以更改注册的名称。 有关启用 Microsoft Entra 提供程序的详细信息,请参阅《配置应用服务或 Azure Functions 应用以使用 Microsoft Entra ID 登录。
转到 SignalR 服务并按照步骤添加系统分配的标识或用户分配的标识。
在 Azure SignalR 服务中,转到“上游设置”,然后选择“使用托管标识”和“从现有应用程序中选择”。 选择之前创建的应用程序。
配置这些设置后,函数应用会拒绝标头中不带访问令牌的请求。
验证访问令牌
如果不使用 WebApp 或 Azure 函数,则还可以验证令牌。
Authorization 标头中的令牌是 Microsoft 标识平台访问令牌。
若要验证访问令牌,你的应用还应当验证受众和签名令牌。 需要根据 OpenID 发现文档中的值对这些令牌进行验证。 有关示例,请参阅《文档的独立于租户的版本》。
Microsoft Entra 中间件具有用于验证访问令牌的内置功能。 可以浏览 Microsoft 标识平台代码示例,以所选语言查找一个。
我们提供了演示如何处理令牌验证的库和代码示例。 还有多个可用于 JSON Web 令牌 (JWT) 验证的开放源代码合作伙伴库。 几乎每种平台和语言都至少有一个适用的选项。 有关 Microsoft Entra 身份验证库和代码示例的详细信息,请参阅 Microsoft 标识平台身份验证库。
使用托管标识实现密钥保管库引用
Azure SignalR 服务可以使用托管标识访问密钥保管库来获取机密。
- 向 Azure SignalR 服务实例添加系统分配的标识或用户分配的标识。
- 在密钥保管库的访问策略中授予对托管标识的机密读取权限。 请参阅《使用 Azure 门户分配密钥保管库访问策略》。
目前,可以使用此功能在上游 URL 模式中引用机密。