本文介绍了如何使用 PowerShell cmdlet 在 Azure 备份恢复服务保管库中备份和还原 Azure VM。
Azure 备份提供独立且隔离的备份来防止 VM 上的数据被意外破坏。 备份存储在提供恢复点内置管理的恢复服务保管库中。 配置和缩放很简单,备份经过优化,可以轻松地根据需要还原。
在备份(或保护)虚拟机之前,必须完成先决条件中的步骤来准备好保护 VM 的环境。
开始之前
恢复服务对象层次结构
下图汇总了对象层次结构。
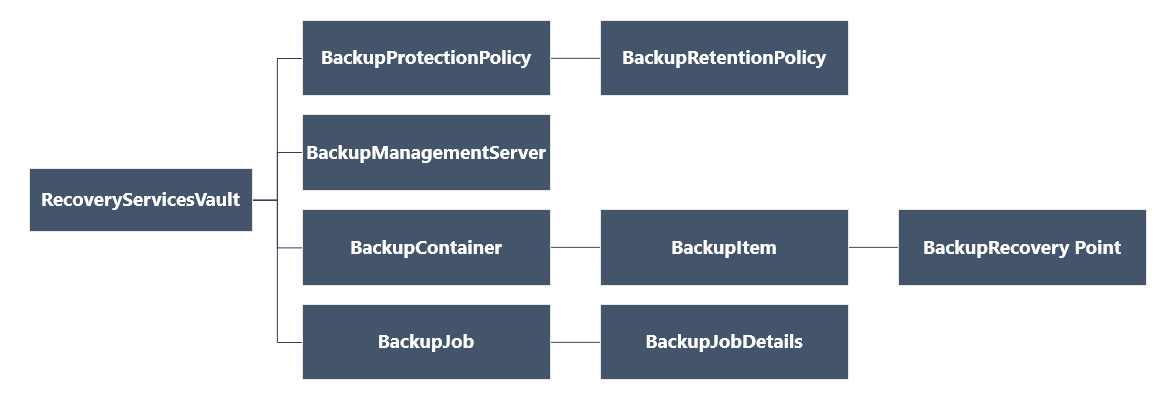
查看 Azure 库中的 Az.RecoveryServicescmdlet 命令参考。
为 Azure VM 备份设置 Azure PowerShell
注意
建议使用 Azure Az PowerShell 模块与 Azure 交互。 若要开始,请参阅安装 Azure PowerShell。 若要了解如何迁移到 Az PowerShell 模块,请参阅 将 Azure PowerShell 从 AzureRM 迁移到 Az。
开始时,请执行以下操作:
键入以下命令查找可用的 Azure 备份 PowerShell cmdlet:
Get-Command *azrecoveryservices*Azure 备份、Azure Site Recovery 和 Azure 恢复服务保管库的别名和 cmdlet 出现。 下图是你将看到的内容的一个示例。 这不是完整的 cmdlet 命令列表。
使用 Connect-AzAccount -Environment AzureChinaCloud 登录到 Azure 帐户。 此 cmdlet 打开一个网页,提示输入帐户凭据:
- 也可使用 -Credential 参数将帐户凭据作为参数包含在 Connect-AzAccount -Environment AzureChinaCloud cmdlet 中。
- 如果你是代表租户的 CSP 合作伙伴,则需使用 tenantID 或租户主域名将客户指定为一名租户。 例如:Connect-AzAccount -Environment AzureChinaCloud -Tenant "fabrikam.com"
由于一个帐户可以有多个订阅,因此请将要使用的订阅与帐户关联在一起:
Select-AzSubscription -SubscriptionName $SubscriptionName首次使用 Azure 备份时,必须使用 Register-AzResourceProvider cmdlet 将 Azure 恢复服务提供程序注册到订阅。
Register-AzResourceProvider -ProviderNamespace "Microsoft.RecoveryServices"可使用以下命令验证提供程序是否已成功注册:
Get-AzResourceProvider -ProviderNamespace "Microsoft.RecoveryServices"在命令输出中,RegistrationState 应当会变为 Registered。 如果没有,则再次运行 Register-AzResourceProvider cmdlet。
为 Azure VM 备份创建恢复服务保管库
以下步骤引导用户创建恢复服务保管库。 恢复服务保管库不同于备份保管库。
恢复服务保管库是一种 Resource Manager 资源,因此需要将它放在资源组中。 可以使用现有的资源组,也可以使用 New-AzResourceGroup cmdlet 创建资源组。 创建资源组时,请指定资源组的名称和位置。
New-AzResourceGroup -Name "test-rg" -Location "China North"使用 New-AzRecoveryServicesVault cmdlet 创建恢复服务保管库。 确保为保管库指定的地点与资源组使用的地点相同。
New-AzRecoveryServicesVault -Name "testvault" -ResourceGroupName "test-rg" -Location "China North"请指定要使用的存储冗余类型。 可使用本地冗余存储 (LRS)、异地冗余存储 (GRS) 或区域冗余存储 (ZRS)。 以下示例显示 -BackupStorageRedundancy 的选项已设置为 GeoRedundant。
$vault1 = Get-AzRecoveryServicesVault -Name "testvault" Set-AzRecoveryServicesBackupProperty -Vault $vault1 -BackupStorageRedundancy GeoRedundant提示
许多 Azure 备份 cmdlet 要求使用恢复服务保管库对象作为输入。 出于此原因,可方便地在变量中存储备份恢复服务保管库对象。
在订阅中查看保管库
若要查看订阅中的所有保管库,请使用 Get-AzRecoveryServicesVault:
Get-AzRecoveryServicesVault
输出类似于以下示例,请注意提供了关联的 ResourceGroupName 和 Location。
Name : Contoso-vault
ID : /subscriptions/1234
Type : Microsoft.RecoveryServices/vaults
Location : ChinaNorth
ResourceGroupName : Contoso-docs-rg
SubscriptionId : 1234-567f-8910-abc
Properties : Microsoft.Azure.Commands.RecoveryServices.ARSVaultProperties
备份 Azure VM
使用恢复服务保管库保护虚拟机。 应用保护前,请先设置保管库上下文(保管库中受保护的数据类型)并验证保护策略。 保护策略是指备份作业运行时以及每个备份快照的保留时长的计划。
设置保管库上下文
在 VM 上启用保护之前,请使用 Set-AzRecoveryServicesVaultContext 来设置保管库上下文。 设置保管库上下文后,它将应用于所有后续 cmdlet。 以下示例为保管库 testvault 设置保管库上下文。
Get-AzRecoveryServicesVault -Name "testvault" -ResourceGroupName "Contoso-docs-rg" | Set-AzRecoveryServicesVaultContext
提取保管库 ID
我们已计划根据 Azure PowerShell 指南弃用保管库上下文设置。 可以改为存储或提取保管库 ID,并将其传递给相关命令。 因此,如果你尚未设置保管库上下文或想要指定为某个保管库运行的命令,请将保管库 ID 作为“-vaultID”传递给所有相关命令,如下所示:
$targetVault = Get-AzRecoveryServicesVault -ResourceGroupName "Contoso-docs-rg" -Name "testvault"
$targetVault.ID
或
$targetVaultID = Get-AzRecoveryServicesVault -ResourceGroupName "Contoso-docs-rg" -Name "testvault" | select -ExpandProperty ID
修改存储复制设置
使用 Set-AzRecoveryServicesBackupProperty 命令,将保管库的存储复制配置设置为 LRS/GRS
Set-AzRecoveryServicesBackupProperty -Vault $targetVault -BackupStorageRedundancy GeoRedundant/LocallyRedundant
注意
只有在没有受保管库保护的备份项的情况下,才能修改存储冗余性。
创建保护策略
在创建恢复服务保管库时,它附带了默认的保护和保留策略。 默认保护策略在每天的指定时间触发备份作业。 默认保留策略将每日恢复点保留 30 天。 可以使用默认策略快速保护 VM,以后再使用不同的详细信息编辑该策略。
若要查看保管库中可用的保护策略,请使用 Get-AzRecoveryServicesBackupProtectionPolicy 。 可以使用此 cmdlet 获取特定策略,或者查看与某个工作负荷类型关联的策略。 以下示例获取适用于工作负荷类型 AzureVM 的策略。
Get-AzRecoveryServicesBackupProtectionPolicy -WorkloadType "AzureVM" -VaultId $targetVault.ID
输出类似于以下示例:
Name WorkloadType BackupManagementType BackupTime DaysOfWeek
---- ------------ -------------------- ---------- ----------
DefaultPolicy AzureVM AzureVM 4/14/2016 5:00:00 PM
注意
PowerShell 中 BackupTime 字段的时区是 UTC。 但是,在 Azure 门户中显示备份时间时,时间根据本地时区调整。
一个备份保护策略至少与一个保留策略相关联。 保留策略定义了在将恢复点删除之前将其保留的时限。
- 使用 Get-AzRecoveryServicesBackupRetentionPolicyObject 查看默认保留策略。
- 类似地,可以使用 Get-AzRecoveryServicesBackupSchedulePolicyObject 获取默认计划策略。
- New-AzRecoveryServicesBackupProtectionPolicy cmdlet 创建用于保存备份策略信息的 PowerShell 对象。
- 计划和保留策略对象用作 New-AzRecoveryServicesBackupProtectionPolicy cmdlet 的输入。
默认情况下,会在“计划策略对象”中定义开始时间。 请使用以下示例将开始时间更改为所需的开始时间。 所需的开始时间也应采用 UTC 格式。 下面的示例假设在进行每日备份时,所需的开始时间为 UTC 时间凌晨 1:00。
$schPol = Get-AzRecoveryServicesBackupSchedulePolicyObject -WorkloadType "AzureVM"
$UtcTime = Get-Date -Date "2019-03-20 01:00:00Z"
$UtcTime = $UtcTime.ToUniversalTime()
$schpol.ScheduleRunTimes[0] = $UtcTime
重要
只需以 30 分钟的倍数提供开始时间。 在上面的示例中,开始时间只能是“01:00:00”或“02:30:00”。 开始时间不能为“01:15:00”
以下示例将计划策略和保留策略存储在变量中。 此示例使用这些变量来定义在创建保护策略 NewPolicy 时要使用的参数。
$retPol = Get-AzRecoveryServicesBackupRetentionPolicyObject -WorkloadType "AzureVM"
New-AzRecoveryServicesBackupProtectionPolicy -Name "NewPolicy" -WorkloadType "AzureVM" -RetentionPolicy $retPol -SchedulePolicy $schPol -VaultId $targetVault.ID
输出类似于以下示例:
Name WorkloadType BackupManagementType BackupTime DaysOfWeek
---- ------------ -------------------- ---------- ----------
NewPolicy AzureVM AzureVM 4/24/2016 1:30:00 AM
启用保护
在定义保护策略后,还必须为相应的项启用该策略。 请使用 Enable-AzRecoveryServicesBackupProtection 来启用保护。 启用保护需要两个对象,项目和策略。 将策略与保管库关联之后,将在策略计划中定义的时间触发备份工作流。
重要
使用 PowerShell 一次为多个 VM 启用备份时,请确保单个策略关联的 VM 不超过 100 个。 这是建议的最佳做法。 目前,如果 VM 超过 100 个,PowerShell 客户端不会显式阻止,但计划在将来添加检查。
以下示例使用策略 NewPolicy 为项 V2VM 启用保护。 根据 VM 是否已加密以及采用了何种加密类型,示例将有所不同。
在非加密资源管理器 VM 上启用保护:
$pol = Get-AzRecoveryServicesBackupProtectionPolicy -Name "NewPolicy" -VaultId $targetVault.ID
Enable-AzRecoveryServicesBackupProtection -Policy $pol -Name "V2VM" -ResourceGroupName "RGName1" -VaultId $targetVault.ID
若要在加密 VM(使用 BEK 和 KEK 加密)上启用保护,必须向 Azure 备份服务授予权限来读取密钥保管库中的密钥和机密。
Set-AzKeyVaultAccessPolicy -VaultName "KeyVaultName" -ResourceGroupName "RGNameOfKeyVault" -PermissionsToKeys backup,get,list -PermissionsToSecrets get,list -ServicePrincipalName 262044b1-e2ce-469f-a196-69ab7ada62d3
$pol = Get-AzRecoveryServicesBackupProtectionPolicy -Name "NewPolicy" -VaultId $targetVault.ID
Enable-AzRecoveryServicesBackupProtection -Policy $pol -Name "V2VM" -ResourceGroupName "RGName1" -VaultId $targetVault.ID
若要在加密 VM(仅使用 BEK 加密的) 上启用保护,必须向 Azure 备份服务授予权限来读取密钥保管库中的机密。
Set-AzKeyVaultAccessPolicy -VaultName "KeyVaultName" -ResourceGroupName "RGNameOfKeyVault" -PermissionsToSecrets backup,get,list -ServicePrincipalName 262044b1-e2ce-469f-a196-69ab7ada62d3
$pol = Get-AzRecoveryServicesBackupProtectionPolicy -Name "NewPolicy" -VaultId $targetVault.ID
Enable-AzRecoveryServicesBackupProtection -Policy $pol -Name "V2VM" -ResourceGroupName "RGName1" -VaultId $targetVault.ID
如果想要有选择地备份少量磁盘,并按这些方案中所述排除其他磁盘,可配置保护并仅备份相关磁盘,如此处所述。
监视 Azure VM 的备份作业
可以在不使用 Azure 门户的情况下监视长时间运行的操作,例如备份作业。 若要获取正在进行的作业的状态,请使用 Get-AzRecoveryservicesBackupJob cmdlet。 此 cmdlet 获取特定保管库的备份作业,该保管库是在保管库上下文环境中所指定的。 以下示例将正在进行的作业的状态获取为数组,并将状态存储在 $joblist 变量中。
$joblist = Get-AzRecoveryservicesBackupJob -Status "InProgress" -VaultId $targetVault.ID
$joblist[0]
输出类似于以下示例:
WorkloadName Operation Status StartTime EndTime JobID
------------ --------- ------ --------- ------- ----------
V2VM Backup InProgress 4/23/2016 5:00:30 PM cf4b3ef5-2fac-4c8e-a215-d2eba4124f27
与其编写额外且不必要的代码来轮询这些作业是否完成,不如使用 Wait-AzRecoveryServicesBackupJob cmdlet。 该 cmdlet 暂停操作的执行,直到作业完成或达到了指定的超时值。
Wait-AzRecoveryServicesBackupJob -Job $joblist[0] -Timeout 43200 -VaultId $targetVault.ID
管理 Azure VM 备份
修改保护策略
若要修改保护策略,请使用 Set-AzRecoveryServicesBackupProtectionPolicy 修改 SchedulePolicy 或 RetentionPolicy 对象。
修改计划时间
创建保护策略时,默认情况下会为其分配开始时间。 下面的示例演示如何修改保护策略的开始时间。
$SchPol = Get-AzRecoveryServicesBackupSchedulePolicyObject -WorkloadType "AzureVM"
$UtcTime = Get-Date -Date "2019-03-20 01:00:00Z" (This is the time that you want to start the backup)
$UtcTime = $UtcTime.ToUniversalTime()
$SchPol.ScheduleRunTimes[0] = $UtcTime
$pol = Get-AzRecoveryServicesBackupProtectionPolicy -Name "NewPolicy" -VaultId $targetVault.ID
Set-AzRecoveryServicesBackupProtectionPolicy -Policy $pol -SchedulePolicy $SchPol -VaultId $targetVault.ID
修改保留期
以下示例将恢复点保留期更改为 365 天。
$retPol = Get-AzRecoveryServicesBackupRetentionPolicyObject -WorkloadType "AzureVM"
$retPol.DailySchedule.DurationCountInDays = 365
$pol = Get-AzRecoveryServicesBackupProtectionPolicy -Name "NewPolicy" -VaultId $targetVault.ID
Set-AzRecoveryServicesBackupProtectionPolicy -Policy $pol -RetentionPolicy $RetPol -VaultId $targetVault.ID
配置即时还原快照保留期
注意
从 Azure PowerShell 版本 1.6.0 开始,可以使用 PowerShell 在策略中更新即时还原快照保留期
$bkpPol = Get-AzRecoveryServicesBackupProtectionPolicy -WorkloadType "AzureVM" -VaultId $targetVault.ID
$bkpPol.SnapshotRetentionInDays=7
Set-AzRecoveryServicesBackupProtectionPolicy -policy $bkpPol -VaultId $targetVault.ID
默认值将为 2。 可以将值的最小值设置为 1,最大值设置为 5。 每周备份策略的保留期设置为 5,不能更改。
在快照保留期间创建 Azure 备份资源组
注意
从 Azure PowerShell 版本 3.7.0 开始,可以创建和编辑为存储即时快照而创建的资源组。
若要详细了解资源组创建规则和其他相关详细信息,请参阅适用于虚拟机的 Azure 备份资源组文档。
$bkpPol = Get-AzureRmRecoveryServicesBackupProtectionPolicy -name "DefaultPolicyForVMs"
$bkpPol.AzureBackupRGName="Contoso_"
$bkpPol.AzureBackupRGNameSuffix="ForVMs"
Set-AzureRmRecoveryServicesBackupProtectionPolicy -policy $bkpPol
排除受保护的 VM 的磁盘
Azure VM 备份提供了一项有选择地排除或包括磁盘的功能,这在这些方案中很有用。 如果虚拟机已经受 Azure VM 备份保护,并且所有磁盘都已备份,则可以修改保护以有选择地包括或排除磁盘,如此处所述。
触发备份
请使用 Backup-AzRecoveryServicesBackupItem 来触发备份作业。 如果它是初始备份,则是一个完整备份。 后续备份将创建增量副本。 以下示例将 VM 备份保留 60 天。
$namedContainer = Get-AzRecoveryServicesBackupContainer -ContainerType "AzureVM" -Status "Registered" -FriendlyName "V2VM" -VaultId $targetVault.ID
$item = Get-AzRecoveryServicesBackupItem -Container $namedContainer -WorkloadType "AzureVM" -VaultId $targetVault.ID
$endDate = (Get-Date).AddDays(60).ToUniversalTime()
$job = Backup-AzRecoveryServicesBackupItem -Item $item -VaultId $targetVault.ID -ExpiryDateTimeUTC $endDate
输出类似于以下示例:
WorkloadName Operation Status StartTime EndTime JobID
------------ --------- ------ --------- ------- ----------
V2VM Backup InProgress 4/23/2016 5:00:30 PM cf4b3ef5-2fac-4c8e-a215-d2eba4124f27
注意
PowerShell 中 StartTime 和 EndTime 字段的时区是 UTC。 但是,在 Azure 门户中显示时间时,时间根据本地时区调整。
更改备份项的策略
可以修改现有策略,也可以将备份项的策略从 Policy1 更改为 Policy2。 若要切换备份项的策略,请提取相关策略并备份项,并使用 Enable-AzRecoveryServices 命令以备份项作为参数。
$TargetPol1 = Get-AzRecoveryServicesBackupProtectionPolicy -Name <PolicyName> -VaultId $targetVault.ID
$anotherBkpItem = Get-AzRecoveryServicesBackupItem -WorkloadType AzureVM -BackupManagementType AzureVM -Name "<BackupItemName>" -VaultId $targetVault.ID
Enable-AzRecoveryServicesBackupProtection -Item $anotherBkpItem -Policy $TargetPol1 -VaultId $targetVault.ID
该命令将一直等到配置备份完成并返回以下输出。
WorkloadName Operation Status StartTime EndTime JobID
------------ --------- ------ --------- ------- -----
TestVM ConfigureBackup Completed 3/18/2019 8:00:21 PM 3/18/2019 8:02:16 PM 654e8aa2-4096-402b-b5a9-e5e71a496c4e
停止保护
保留数据
如果希望停止保护,可以使用 Disable-AzRecoveryServicesBackupProtection PowerShell cmdlet。 此命令将停止计划的备份,但到目前为止备份的数据将永远保留。
$bkpItem = Get-AzRecoveryServicesBackupItem -BackupManagementType AzureVM -WorkloadType AzureVM -Name "<backup item name>" -VaultId $targetVault.ID
Disable-AzRecoveryServicesBackupProtection -Item $bkpItem -VaultId $targetVault.ID
恢复备份
如果停止保护后保留了备份数据,则可以再次恢复保护。 必须为续期的保护指定策略。 该 cmdlet 与更改备份项策略的功能相同。
$TargetPol1 = Get-AzRecoveryServicesBackupProtectionPolicy -Name <PolicyName> -VaultId $targetVault.ID
$anotherBkpItem = Get-AzRecoveryServicesBackupItem -WorkloadType AzureVM -BackupManagementType AzureVM -Name "<BackupItemName>" -VaultId $targetVault.ID
Enable-AzRecoveryServicesBackupProtection -Item $anotherBkpItem -Policy $TargetPol1 -VaultId $targetVault.ID
删除备份数据
若要完全删除保管库中存储的备份数据,请将“-RemoveRecoveryPoints”标志/开关添加到“disable”保护命令。
Disable-AzRecoveryServicesBackupProtection -Item $bkpItem -VaultId $targetVault.ID -RemoveRecoveryPoints
还原 Azure VM
使用 Azure 门户还原 VM 与使用 PowerShell 还原 VM 存在重要区别。 如果使用 PowerShell,从恢复点创建磁盘和配置信息即可完成还原操作。 还原操作不会创建虚拟机。 若要通过磁盘创建虚拟机,请参阅通过存储磁盘创建 VM 部分。 如果不希望还原整个 VM,但希望从 Azure VM 备份还原或恢复几个文件,请参阅文件恢复部分。
提示
还原操作不会创建虚拟机。
下图显示从 RecoveryServicesVault 到 BackupRecoveryPoint 的对象层次结构。
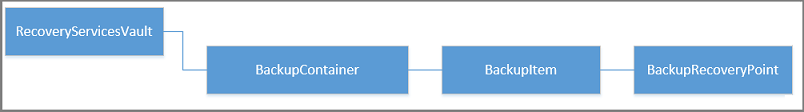
若要还原备份数据,请确定已备份项目以及保留了时间点数据的恢复点。 请使用 Restore-AzRecoveryServicesBackupItem 将数据从保管库还原到帐户。
还原 Azure VM 的基本步骤是:
- 选择 VM。
- 选择恢复点。
- 还原磁盘。
- 从存储的磁盘创建 VM。
现在,还可以使用 PowerShell 将备份内容直接还原到 VM(原始/新),而无需单独执行上述步骤。 有关详细信息,请参阅使用 PowerShell 将数据还原到虚拟机。
选择 VM(还原文件时)
若要获取用于标识正确备份项的 PowerShell 对象,请从保管库中的容器开始,按对象层次结构进行操作。 若要选择代表 VM 的容器,请使用 Get-AzRecoveryServicesBackupContainer cmdlet,然后通过管道将其传递给 Get-AzRecoveryServicesBackupItem cmdlet。
$namedContainer = Get-AzRecoveryServicesBackupContainer -ContainerType "AzureVM" -Status "Registered" -FriendlyName "V2VM" -VaultId $targetVault.ID
$backupitem = Get-AzRecoveryServicesBackupItem -Container $namedContainer -WorkloadType "AzureVM" -VaultId $targetVault.ID
选择恢复点(还原文件时)
使用 Get-AzRecoveryServicesBackupRecoveryPoint cmdlet 列出备份项的所有恢复点。 然后选择要还原的恢复点。 如果您不确定应使用哪个恢复点,建议选择列表中最新的 RecoveryPointType = AppConsistent 类型的恢复点。
在以下脚本中,变量 $rp 是一个数组,其中包含所选备份项在过去七天的恢复点。 该数组按时间进行反向排序,以最新的恢复点作为索引 0。 使用标准 PowerShell 数组索引选取恢复点。 在示例中,$rp[0] 选择最新的恢复点。
$startDate = (Get-Date).AddDays(-7)
$endDate = Get-Date
$rp = Get-AzRecoveryServicesBackupRecoveryPoint -Item $backupitem -StartDate $startdate.ToUniversalTime() -EndDate $enddate.ToUniversalTime() -VaultId $targetVault.ID
$rp[0]
输出类似于以下示例:
RecoveryPointAdditionalInfo :
SourceVMStorageType : NormalStorage
Name : 15260861925810
ItemName : VM;iaasvmcontainer;RGName1;V2VM
RecoveryPointId : /subscriptions/XX/resourceGroups/ RGName1/providers/Microsoft.RecoveryServices/vaults/testvault/backupFabrics/Azure/protectionContainers/IaasVMContainer;iaasvmcontainer;RGName1;V2VM/protectedItems/VM;iaasvmcontainer; RGName1;V2VM/recoveryPoints/15260861925810
RecoveryPointType : AppConsistent
RecoveryPointTime : 4/23/2016 5:02:04 PM
WorkloadType : AzureVM
ContainerName : IaasVMContainer;iaasvmcontainer; RGName1;V2VM
ContainerType : AzureVM
BackupManagementType : AzureVM
还原磁盘
请使用 Restore-AzRecoveryServicesBackupItem cmdlet 将备份项的数据和配置还原到某个恢复点。 确定某个恢复点后,即可使用它作为 -RecoveryPoint 参数的值。 在上面的示例中,$rp[0] 是要使用的恢复点。 在下面的示例代码中, $rp[0] 是还原磁盘时要使用的恢复点。
还原磁盘和配置信息:
$restorejob = Restore-AzRecoveryServicesBackupItem -RecoveryPoint $rp[0] -StorageAccountName "DestAccount" -StorageAccountResourceGroupName "DestRG" -VaultId $targetVault.ID
$restorejob
还原托管磁盘
注意
如果被备份的 VM 具有托管磁盘,并且你想将其还原为托管磁盘,我们在 Azure PowerShell RM 模块 v 6.7.0 中新增了该功能。 向前
提供一个附加参数 TargetResourceGroupName,以便指定托管磁盘将还原到的资源组。
重要
强烈建议使用 TargetResourceGroupName 参数来还原托管磁盘,因为它可以显著提高性能。 如果未指定此参数,则无法从即时还原功能中受益,并且相比之下,还原操作的速度将更慢。 如果目的是将托管磁盘还原为非托管磁盘,则不要提供此参数,而应通过提供 -RestoreAsUnmanagedDisks 参数,使该目的明确。 此 -RestoreAsUnmanagedDisks 参数从 Azure PowerShell 3.7.0 开始提供。 在将来的版本中,必须提供其中任意一个参数,以获得正确的还原体验。
$restorejob = Restore-AzRecoveryServicesBackupItem -RecoveryPoint $rp[0] -StorageAccountName "DestAccount" -StorageAccountResourceGroupName "DestRG" -TargetResourceGroupName "DestRGforManagedDisks" -VaultId $targetVault.ID
VMConfig.JSON 文件将还原到存储帐户,托管磁盘将还原到指定的目标 RG。
输出类似于以下示例:
WorkloadName Operation Status StartTime EndTime JobID
------------ --------- ------ --------- ------- ----------
V2VM Restore InProgress 4/23/2016 5:00:30 PM cf4b3ef5-2fac-4c8e-a215-d2eba4124f27
请使用 Wait-AzRecoveryServicesBackupJob cmdlet 等待还原作业完成。
Wait-AzRecoveryServicesBackupJob -Job $restorejob -Timeout 43200
还原作业完成后,可以使用 Get-AzRecoveryServicesBackupJobDetail cmdlet 获取还原操作的详细信息。 JobDetails 属性提供重建 VM 所需的信息。
$restorejob = Get-AzRecoveryServicesBackupJob -Job $restorejob -VaultId $targetVault.ID
$details = Get-AzRecoveryServicesBackupJobDetail -Job $restorejob -VaultId $targetVault.ID
使用托管标识来还原磁盘
Azure 备份还允许在还原操作期间使用托管标识 (MSI) 来访问必须将磁盘还原到的存储帐户。 目前仅托管磁盘还原支持此选项。
如果希望使用保管库的系统分配的托管身份来还原磁盘,请在 Restore-AzRecoveryServicesBackupItem 命令中添加附加标志 -UseSystemAssignedIdentity。 如果要使用用户分配的托管标识,请传递参数-UserAssignedIdentityId,并将保管库的托管标识的 Azure 资源管理器 ID 作为参数的值。 请参阅此文,了解如何为保管库启用托管标识。
还原选择性磁盘
用户可以有选择地还原少数磁盘,而不是整个备份集。 提供所需的磁盘 LUN 作为参数,以便仅还原这些磁盘,而不是整个磁盘集,如此处所述。
重要
若要有选择地还原磁盘,必须有选择地备份磁盘。 此处提供了详细信息。
还原磁盘以后,转到下一部分来了解如何创建 VM。
将磁盘恢复到备用区域
如果在用于保护 VM 的保管库上启用跨区域还原,则会将备份数据复制到次要区域。 可使用备份数据来执行还原。 执行以下步骤,在次要区域中触发还原:
提取用于保护 VM 的保管库 ID。
选择要还原的正确备份项。
在次要区域中选择适当的恢复点,以执行还原操作。
若要完成此步骤,请运行以下命令:
$rp=Get-AzRecoveryServicesBackupRecoveryPoint -UseSecondaryRegion -Item $backupitem -VaultId $targetVault.ID $rp=$rp[0]执行 Restore-AzRecoveryServicesBackupItem cmdlet,并使用
-RestoreToSecondaryRegion参数以在次要区域触发还原。若要完成此步骤,请运行以下命令:
$restorejob = Restore-AzRecoveryServicesBackupItem -RecoveryPoint $rp[0] -StorageAccountName "DestAccount" -StorageAccountResourceGroupName "DestRG" -TargetResourceGroupName "DestRGforManagedDisks" -VaultId $targetVault.ID -VaultLocation $targetVault.Location -RestoreToSecondaryRegion -RestoreOnlyOSDisk输出将类似于以下示例:
WorkloadName Operation Status StartTime EndTime JobID ------------ --------- ------ --------- ------- ---------- V2VM CrossRegionRestore InProgress 4/23/2016 5:00:30 PM cf4b3ef5-2fac-4c8e-a215-d2eba4124f27使用
-UseSecondaryRegion参数执行 Get-AzRecoveryServicesBackupJob cmdlet,以监视恢复作业。若要完成此步骤,请运行以下命令:
Get-AzRecoveryServicesBackupJob -From (Get-Date).AddDays(-7).ToUniversalTime() -To (Get-Date).ToUniversalTime() -UseSecondaryRegion -VaultId $targetVault.ID输出将类似于以下示例:
WorkloadName Operation Status StartTime EndTime JobID ------------ --------- ------ --------- ------- ----- V2VM CrossRegionRestore InProgress 2/8/2021 4:24:57 PM 2d071b07-8f7c-4368-bc39-98c7fb2983f7
跨区域还原
可以在同一区域的任何可用性区域中还原 Azure 区域固定的 VM。
若要将 VM 还原到另一个区域,请在 Restore-AzRecoveryServicesBackupItem cmdlet 中指定 TargetZoneNumber 参数。
$restorejob = Restore-AzRecoveryServicesBackupItem -RecoveryPoint $rp[0] -StorageAccountName "DestAccount" -StorageAccountResourceGroupName "DestRG" -VaultId $targetVault.ID -TargetZoneNumber 3
输出将类似于以下示例:
WorkloadName Operation Status StartTime EndTime JobID
------------ --------- ------ --------- ------- -----
zonevmeus2 Restore InProgress 1/3/2022 10:27:20 AM b2298...
仅在以下情况下支持跨区域还原:
- 源 VM 已进行区域固定且未加密。
- 恢复点仅存在于存储库层中。 不支持仅快照或快照和保管库层。
- 恢复选项是创建新的 VM 或还原磁盘。 替换磁盘选项替换源数据;因此可用性区域选项不适用。
- 当存储库的存储冗余为 ZRS 时,请在同一区域创建虚拟机或磁盘。 请注意,如果保管库的存储冗余为 GRS,则将不起作用,即使源 VM 进行了区域固定。
- 如果为跨区域还原启用了保管库的存储冗余,并且配对区域支持区域,则在配对区域中创建 VM/磁盘。
更换 Azure VM 中的磁盘
若要更换磁盘和配置信息,请执行以下步骤:
- 步骤 1:还原磁盘
- 步骤 2:使用 PowerShell 分离数据磁盘
- 步骤 3:使用 PowerShell 将数据磁盘附加到 Windows VM
从还原的磁盘创建 VM
还原磁盘以后,通过以下步骤从磁盘创建和配置虚拟机。
注意
- 需要 AzureAz 模块 3.0.0 或更高版本。
- 若要使用已还原的磁盘创建加密 VM,则 Azure 角色必须有权执行 Microsoft.KeyVault/vaults/deploy/action 操作。 如果用户角色不具有此权限,请通过此操作创建自定义角色。 有关详细信息,请参阅 Azure 自定义角色。
- 还原磁盘后,你现在可以获取可以直接用来创建新 VM 的部署模板。 不需要使用不同的 PowerShell cmdlet 来创建加密/未加密的托管/非托管 VM。
使用部署模板创建 VM
生成的作业详细信息提供了可以查询和部署的模板 URI。
$properties = $details.properties
$storageAccountName = $properties["Target Storage Account Name"]
$containerName = $properties["Config Blob Container Name"]
$templateBlobURI = $properties["Create VM Template Blob Uri"]
模板不能直接访问,因为它在客户的存储帐户和给定容器下。 需要完整的 URL(以及临时 SAS 令牌)才能访问此模板。
首先从 templateBlobURI 中提取模板名称。 此格式如下所述。 可以使用 PowerShell 中的拆分操作从该 URL 提取最终模板名称。
https://<storageAccountName.blob.core.chinacloudapi.cn>/<containerName>/<templateName>然后,可以生成完整的 URL,如此处所述。
Set-AzCurrentStorageAccount -Name $storageAccountName -ResourceGroupName <StorageAccount RG name> $templateBlobFullURI = New-AzStorageBlobSASToken -Container $containerName -Blob <templateName> -Permission r -FullUri部署模板来创建新的 VM,如此处所述。
New-AzResourceGroupDeployment -Name ExampleDeployment -ResourceGroupName ExampleResourceGroup -TemplateUri $templateBlobFullURI
使用配置文件创建 VM
以下部分列出了使用 VMConfig 文件创建 VM 所需的步骤。
注意
强烈建议使用上面详述的部署模板来创建 VM。 本部分(要点 1-6)不久将被弃用。
查询已还原磁盘属性以获取作业详细信息。
$properties = $details.properties $storageAccountName = $properties["Target Storage Account Name"] $containerName = $properties["Config Blob Container Name"] $configBlobName = $properties["Config Blob Name"]设置 Azure 存储上下文和还原 JSON 配置文件。
Set-AzCurrentStorageAccount -Name $storageaccountname -ResourceGroupName "testvault" $destination_path = "C:\vmconfig.json" Get-AzStorageBlobContent -Container $containerName -Blob $configBlobName -Destination $destination_path $obj = ((Get-Content -Path $destination_path -Raw -Encoding Unicode)).TrimEnd([char]0x00) | ConvertFrom-Json使用 JSON 配置文件来创建 VM 配置。
$vm = New-AzVMConfig -VMSize $obj.'properties.hardwareProfile'.vmSize -VMName "testrestore"附加 OS 磁盘和数据磁盘。 此步骤提供了各种托管和加密的 VM 配置的示例。 请使用适合你的 VM 配置的示例。
- 非托管且非加密 VM - 对于非托管的非加密 VM,请使用以下示例。
Set-AzVMOSDisk -VM $vm -Name "osdisk" -VhdUri $obj.'properties.StorageProfile'.osDisk.vhd.Uri -CreateOption "Attach" $vm.StorageProfile.OsDisk.OsType = $obj.'properties.StorageProfile'.OsDisk.OsType foreach($dd in $obj.'properties.StorageProfile'.DataDisks) { $vm = Add-AzVMDataDisk -VM $vm -Name "datadisk1" -VhdUri $dd.vhd.Uri -DiskSizeInGB 127 -Lun $dd.Lun -CreateOption "Attach" }- 具有 Microsoft Entra ID 的非托管加密 VM(仅限 BEK)- 对于具有 Microsoft Entra ID 的非托管加密 VM(仅使用 BEK 加密),需要先将密码还原到密钥保管库,然后才能附加磁盘。 有关详细信息,请参阅从 Azure 备份恢复点还原已加密的虚拟机。 以下示例展示了如何为加密的 VM 附加 OS 和数据磁盘。 设置 OS 磁盘时,请确保提及相关的 OS 类型。
$dekUrl = "https://ContosoKeyVault.vault.azure.cn:443/secrets/ContosoSecret007/xx000000xx0849999f3xx30000003163" $dekUrl = "/subscriptions/abcdedf007-4xyz-1a2b-0000-12a2b345675c/resourceGroups/ContosoRG108/providers/Microsoft.KeyVault/vaults/ContosoKeyVault" Set-AzVMOSDisk -VM $vm -Name "osdisk" -VhdUri $obj.'properties.storageProfile'.osDisk.vhd.uri -DiskEncryptionKeyUrl $dekUrl -DiskEncryptionKeyVaultId $keyVaultId -CreateOption "Attach" -Windows/Linux $vm.StorageProfile.OsDisk.OsType = $obj.'properties.storageProfile'.osDisk.osType foreach($dd in $obj.'properties.storageProfile'.dataDisks) { $vm = Add-AzVMDataDisk -VM $vm -Name "datadisk1" -VhdUri $dd.vhd.Uri -DiskSizeInGB 127 -Lun $dd.Lun -CreateOption "Attach" }- 具有 Microsoft Entra ID 的非托管加密 VM(BEK 和 KEK)- 对于具有 Microsoft Entra ID 的非托管加密 VM(使用 BEK 和 KEK 加密),先将密钥和密码还原到密钥保管库,然后再附加磁盘。 有关详细信息,请参阅从 Azure 备份恢复点还原已加密的虚拟机。 以下示例展示了如何为加密的 VM 附加 OS 和数据磁盘。
$dekUrl = "https://ContosoKeyVault.vault.azure.cn:443/secrets/ContosoSecret007/xx000000xx0849999f3xx30000003163" $kekUrl = "https://ContosoKeyVault.vault.azure.cn:443/keys/ContosoKey007/x9xxx00000x0000x9b9949999xx0x006" $keyVaultId = "/subscriptions/abcdedf007-4xyz-1a2b-0000-12a2b345675c/resourceGroups/ContosoRG108/providers/Microsoft.KeyVault/vaults/ContosoKeyVault" Set-AzVMOSDisk -VM $vm -Name "osdisk" -VhdUri $obj.'properties.storageProfile'.osDisk.vhd.uri -DiskEncryptionKeyUrl $dekUrl -DiskEncryptionKeyVaultId $keyVaultId -KeyEncryptionKeyUrl $kekUrl -KeyEncryptionKeyVaultId $keyVaultId -CreateOption "Attach" -Windows $vm.StorageProfile.OsDisk.OsType = $obj.'properties.storageProfile'.osDisk.osType foreach($dd in $obj.'properties.storageProfile'.dataDisks) { $vm = Add-AzVMDataDisk -VM $vm -Name "datadisk1" -VhdUri $dd.vhd.Uri -DiskSizeInGB 127 -Lun $dd.Lun -CreateOption "Attach" }- 不具有 Microsoft Entra ID 的非托管加密 VM(仅限 BEK)- 对于不具有 Microsoft Entra ID 的非托管加密 VM(仅使用 BEK 加密),如果源 keyVault/密码不可用,可使用从 Azure 备份恢复点还原非加密虚拟机中的过程,将密码还原到密钥保管库。 然后执行以下脚本,在已还原的 OS Blob 上设置加密详细信息(对于数据 Blob,不需要执行此步骤)。 可以从已还原的密钥保管库中提取 $dekurl。
仅当源 keyVault/密钥不可用时,才需要执行以下脚本。
$dekUrl = "https://ContosoKeyVault.vault.azure.cn/secrets/ContosoSecret007/xx000000xx0849999f3xx30000003163" $keyVaultId = "/subscriptions/abcdedf007-4xyz-1a2b-0000-12a2b345675c/resourceGroups/ContosoRG108/providers/Microsoft.KeyVault/vaults/ContosoKeyVault" $encSetting = "{""encryptionEnabled"":true,""encryptionSettings"":[{""diskEncryptionKey"":{""sourceVault"":{""id"":""$keyVaultId""},""secretUrl"":""$dekUrl""}}]}" $osBlobName = $obj.'properties.StorageProfile'.osDisk.name + ".vhd" $osBlob = Get-AzStorageBlob -Container $containerName -Blob $osBlobName $osBlob.ICloudBlob.Metadata["DiskEncryptionSettings"] = $encSetting $osBlob.ICloudBlob.SetMetadata()密钥可用且将加密信息设定在 OS Blob 上之后,使用下面提供的脚本附加到磁盘。
如果源 keyVault/密钥已经可用,则不需要执行上述脚本。
Set-AzVMOSDisk -VM $vm -Name "osdisk" -VhdUri $obj.'properties.StorageProfile'.osDisk.vhd.Uri -CreateOption "Attach" $vm.StorageProfile.OsDisk.OsType = $obj.'properties.StorageProfile'.OsDisk.OsType foreach($dd in $obj.'properties.StorageProfile'.DataDisks) { $vm = Add-AzVMDataDisk -VM $vm -Name "datadisk1" -VhdUri $dd.vhd.Uri -DiskSizeInGB 127 -Lun $dd.Lun -CreateOption "Attach" }- 不使用 Microsoft Entra ID 的非托管加密 VM(BEK 和 KEK)- 对于不使用 Microsoft Entra ID 的非托管加密 VM(使用 BEK 和 KEK 加密),如果源 keyVault/密钥/机密不可用,请使用从 Azure 备份恢复点还原未加密的虚拟机中的过程,将密钥和机密还原到 Key Vault。 然后执行以下脚本,在已还原的 OS Blob 上设置加密详细信息(对于数据 Blob,不需要执行此步骤)。 可从已还原的 keyVault 提取 $dekurl 和 $kekurl。
仅当源 Key Vault/密钥/机密不可用时,才需要执行以下脚本。
$dekUrl = "https://ContosoKeyVault.vault.azure.cn/secrets/ContosoSecret007/xx000000xx0849999f3xx30000003163" $kekUrl = "https://ContosoKeyVault.vault.azure.cn/keys/ContosoKey007/x9xxx00000x0000x9b9949999xx0x006" $keyVaultId = "/subscriptions/abcdedf007-4xyz-1a2b-0000-12a2b345675c/resourceGroups/ContosoRG108/providers/Microsoft.KeyVault/vaults/ContosoKeyVault" $encSetting = "{""encryptionEnabled"":true,""encryptionSettings"":[{""diskEncryptionKey"":{""sourceVault"":{""id"":""$keyVaultId""},""secretUrl"":""$dekUrl""},""keyEncryptionKey"":{""sourceVault"":{""id"":""$keyVaultId""},""keyUrl"":""$kekUrl""}}]}" $osBlobName = $obj.'properties.StorageProfile'.osDisk.name + ".vhd" $osBlob = Get-AzStorageBlob -Container $containerName -Blob $osBlobName $osBlob.ICloudBlob.Metadata["DiskEncryptionSettings"] = $encSetting $osBlob.ICloudBlob.SetMetadata()密钥/机密可用并且在 OS Blob 上设置加密详细信息之后,使用下面提供的脚本附加磁盘。
如果源 keyVault/密钥/机密可用,则不需要执行上述脚本。
Set-AzVMOSDisk -VM $vm -Name "osdisk" -VhdUri $obj.'properties.StorageProfile'.osDisk.vhd.Uri -CreateOption "Attach" $vm.StorageProfile.OsDisk.OsType = $obj.'properties.StorageProfile'.OsDisk.OsType foreach($dd in $obj.'properties.StorageProfile'.DataDisks) { $vm = Add-AzVMDataDisk -VM $vm -Name "datadisk1" -VhdUri $dd.vhd.Uri -DiskSizeInGB 127 -Lun $dd.Lun -CreateOption "Attach" }托管的非加密 VM。对于托管的非加密 VM,请附加已还原的托管磁盘。 有关深入信息,请参阅使用 PowerShell 将数据磁盘附加到 Windows VM。
使用 Microsoft Entra ID 托管的加密 VM(仅限 BEK)- 对于使用 Microsoft Entra ID 托管的且仅用 BEK 加密的加密 VM,附加还原的托管磁盘。 有关深入信息,请参阅使用 PowerShell 将数据磁盘附加到 Windows VM。
采用 Microsoft Entra ID 托管和加密的 VM(BEK 和 KEK)- 对于采用 Microsoft Entra ID 加密的托管 VM(使用 BEK 和 KEK),请附加已还原的托管磁盘。 有关深入信息,请参阅使用 PowerShell 将数据磁盘附加到 Windows VM。
不使用 Microsoft Entra ID 的托管并加密的虚拟机(仅限 BEK) - 对于不使用 Microsoft Entra ID 的托管并加密的虚拟机(仅使用 BEK 加密),如果源 密钥保管库/机密不可用,请使用从 Azure 备份恢复点还原未加密的虚拟机中的过程,将机密还原到密钥保管库。 然后执行以下脚本,在已还原的 OS 磁盘上设置加密详细信息(对于数据磁盘,不需要执行此步骤)。 可以从已还原的 KeyVault 中获取 $dekurl。
仅当源 keyVault/secret 不可用时,才需要执行下列脚本。
$dekUrl = "https://ContosoKeyVault.vault.azure.cn/secrets/ContosoSecret007/xx000000xx0849999f3xx30000003163" $keyVaultId = "/subscriptions/abcdedf007-4xyz-1a2b-0000-12a2b345675c/resourceGroups/ContosoRG108/providers/Microsoft.KeyVault/vaults/ContosoKeyVault" $diskupdateconfig = New-AzDiskUpdateConfig -EncryptionSettingsEnabled $true $encryptionSettingsElement = New-Object Microsoft.Azure.Management.Compute.Models.EncryptionSettingsElement $encryptionSettingsElement.DiskEncryptionKey = New-Object Microsoft.Azure.Management.Compute.Models.KeyVaultAndSecretReference $encryptionSettingsElement.DiskEncryptionKey.SourceVault = New-Object Microsoft.Azure.Management.Compute.Models.SourceVault $encryptionSettingsElement.DiskEncryptionKey.SourceVault.Id = $keyVaultId $encryptionSettingsElement.DiskEncryptionKey.SecretUrl = $dekUrl $diskupdateconfig.EncryptionSettingsCollection.EncryptionSettings = New-Object System.Collections.Generic.List[Microsoft.Azure.Management.Compute.Models.EncryptionSettingsElement] $diskupdateconfig.EncryptionSettingsCollection.EncryptionSettings.Add($encryptionSettingsElement) $diskupdateconfig.EncryptionSettingsCollection.EncryptionSettingsVersion = "1.1" Update-AzDisk -ResourceGroupName "testvault" -DiskName $obj.'properties.StorageProfile'.osDisk.name -DiskUpdate $diskupdateconfig机密可用并且在 OS 磁盘上设置加密详细信息之后,若要附加已还原的托管磁盘,请参阅使用 PowerShell 将数据磁盘附加到 Windows VM。
- 不使用 Microsoft Entra ID 的托管加密 VM(BEK 和 KEK) - 对于使用 BEK 和 KEK 加密、不使用 Microsoft Entra ID 的托管加密 VM,如果源密钥保管库、密钥或机密不可用,请使用 从 Azure 备份恢复点还原未加密的虚拟机 中的过程,将密钥和机密还原到密钥保管库。 然后执行以下脚本,在已还原的 OS 磁盘上设置加密详细信息(对于数据磁盘,不需要执行此步骤)。 可从已还原的 keyVault 提取 $dekurl 和 $kekurl。
仅当源 keyVault/密钥/机密不可用时,才需要执行以下脚本。
$dekUrl = "https://ContosoKeyVault.vault.azure.cn/secrets/ContosoSecret007/xx000000xx0849999f3xx30000003163" $kekUrl = "https://ContosoKeyVault.vault.azure.cn/keys/ContosoKey007/x9xxx00000x0000x9b9949999xx0x006" $keyVaultId = "/subscriptions/abcdedf007-4xyz-1a2b-0000-12a2b345675c/resourceGroups/ContosoRG108/providers/Microsoft.KeyVault/vaults/ContosoKeyVault" $diskupdateconfig = New-AzDiskUpdateConfig -EncryptionSettingsEnabled $true $encryptionSettingsElement = New-Object Microsoft.Azure.Management.Compute.Models.EncryptionSettingsElement $encryptionSettingsElement.DiskEncryptionKey = New-Object Microsoft.Azure.Management.Compute.Models.KeyVaultAndSecretReference $encryptionSettingsElement.DiskEncryptionKey.SourceVault = New-Object Microsoft.Azure.Management.Compute.Models.SourceVault $encryptionSettingsElement.DiskEncryptionKey.SourceVault.Id = $keyVaultId $encryptionSettingsElement.DiskEncryptionKey.SecretUrl = $dekUrl $encryptionSettingsElement.KeyEncryptionKey = New-Object Microsoft.Azure.Management.Compute.Models.KeyVaultAndKeyReference $encryptionSettingsElement.KeyEncryptionKey.SourceVault = New-Object Microsoft.Azure.Management.Compute.Models.SourceVault $encryptionSettingsElement.KeyEncryptionKey.SourceVault.Id = $keyVaultId $encryptionSettingsElement.KeyEncryptionKey.KeyUrl = $kekUrl $diskupdateconfig.EncryptionSettingsCollection.EncryptionSettings = New-Object System.Collections.Generic.List[Microsoft.Azure.Management.Compute.Models.EncryptionSettingsElement] $diskupdateconfig.EncryptionSettingsCollection.EncryptionSettings.Add($encryptionSettingsElement) $diskupdateconfig.EncryptionSettingsCollection.EncryptionSettingsVersion = "1.1" Update-AzDisk -ResourceGroupName "testvault" -DiskName $obj.'properties.StorageProfile'.osDisk.name -DiskUpdate $diskupdateconfig密钥/机密可用并且在 OS 磁盘上设置加密详细信息之后,若要附加已还原的托管磁盘,请参阅使用 PowerShell 将数据磁盘附加到 Windows VM。
设置网络设置。
$nicName="p1234" $pip = New-AzPublicIpAddress -Name $nicName -ResourceGroupName "test" -Location "ChinaNorth" -AllocationMethod Dynamic $virtualNetwork = New-AzVirtualNetwork -ResourceGroupName "test" -Location "ChinaNorth" -Name "testvNET" -AddressPrefix 10.0.0.0/16 $virtualNetwork | Set-AzVirtualNetwork $vnet = Get-AzVirtualNetwork -Name "testvNET" -ResourceGroupName "test" $subnetindex=0 $nic = New-AzNetworkInterface -Name $nicName -ResourceGroupName "test" -Location "ChinaNorth" -SubnetId $vnet.Subnets[$subnetindex].Id -PublicIpAddressId $pip.Id $vm=Add-AzVMNetworkInterface -VM $vm -Id $nic.Id创建虚拟机。
New-AzVM -ResourceGroupName "test" -Location "ChinaNorth" -VM $vm推送 ADE 扩展。 如果未推送 ADE 扩展,则数据磁盘将标记为未加密,因此必须执行以下步骤:
对于具有 Microsoft Entra ID 的 VM - 使用以下命令手动对数据磁盘启用加密
仅限 BEK
Set-AzVMDiskEncryptionExtension -ResourceGroupName $RG -VMName $vm.Name -AadClientID $aadClientID -AadClientSecret $aadClientSecret -DiskEncryptionKeyVaultUrl $dekUrl -DiskEncryptionKeyVaultId $keyVaultId -VolumeType DataBEK 和 KEK
Set-AzVMDiskEncryptionExtension -ResourceGroupName $RG -VMName $vm.Name -AadClientID $aadClientID -AadClientSecret $aadClientSecret -DiskEncryptionKeyVaultUrl $dekUrl -DiskEncryptionKeyVaultId $keyVaultId -KeyEncryptionKeyUrl $kekUrl -KeyEncryptionKeyVaultId $keyVaultId -VolumeType Data对于不具有 Microsoft Entra ID 的 VM - 使用以下命令手动对数据磁盘启用加密。
如果在执行该命令期间系统要求提供 AADClientID,则你需要更新 Azure PowerShell。
仅限 BEK
Set-AzVMDiskEncryptionExtension -ResourceGroupName $RG -VMName $vm.Name -DiskEncryptionKeyVaultUrl $dekUrl -DiskEncryptionKeyVaultId $keyVaultId -SkipVmBackup -VolumeType "All"BEK 和 KEK
Set-AzVMDiskEncryptionExtension -ResourceGroupName $RG -VMName $vm.Name -DiskEncryptionKeyVaultUrl $dekUrl -DiskEncryptionKeyVaultId $keyVaultId -KeyEncryptionKeyUrl $kekUrl -KeyEncryptionKeyVaultId $keyVaultId -SkipVmBackup -VolumeType "All"
注意
确保手动删除在加密 VM 还原磁盘过程中创建的 JASON 文件。
从 Azure 虚拟机备份中还原文件
除了可以还原磁盘以外,还可以从 Azure VM 备份还原单个文件。 还原文件功能提供了对恢复点中的所有文件的访问权限。 可以像对普通文件那样通过文件资源管理器管理这些文件。
从 Azure VM 备份还原文件的基本步骤是:
- 选择虚拟机
- 选择恢复点
- 装载恢复点的磁盘
- 复制所需的文件
- 卸载磁盘
选择虚拟机(在还原虚拟机时)
若要获取用于标识正确备份项的 PowerShell 对象,请从保管库中的容器开始,按对象层次结构进行操作。 若要选择代表 VM 的容器,请使用 Get-AzRecoveryServicesBackupContainer cmdlet,然后通过管道将其传递给 Get-AzRecoveryServicesBackupItem cmdlet。
$namedContainer = Get-AzRecoveryServicesBackupContainer -ContainerType "AzureVM" -Status "Registered" -FriendlyName "V2VM" -VaultId $targetVault.ID
$backupitem = Get-AzRecoveryServicesBackupItem -Container $namedContainer -WorkloadType "AzureVM" -VaultId $targetVault.ID
选择恢复点(还原 VM 时)
使用 Get-AzRecoveryServicesBackupRecoveryPoint cmdlet 列出备份项的所有恢复点。 然后选择要还原的恢复点。 如果您不确定应使用哪个恢复点,建议选择列表中最新的 RecoveryPointType = AppConsistent 类型的恢复点。
在以下脚本中,变量 $rp 是一个数组,其中包含所选备份项在过去七天的恢复点。 该数组按时间进行反向排序,以最新的恢复点作为索引 0。 使用标准 PowerShell 数组索引选取恢复点。 在示例中,$rp[0] 选择最新的恢复点。
$startDate = (Get-Date).AddDays(-7)
$endDate = Get-Date
$rp = Get-AzRecoveryServicesBackupRecoveryPoint -Item $backupitem -StartDate $startdate.ToUniversalTime() -EndDate $enddate.ToUniversalTime() -VaultId $targetVault.ID
$rp[0]
输出类似于以下示例:
RecoveryPointAdditionalInfo :
SourceVMStorageType : NormalStorage
Name : 15260861925810
ItemName : VM;iaasvmcontainer;RGName1;V2VM
RecoveryPointId : /subscriptions/XX/resourceGroups/ RGName1/providers/Microsoft.RecoveryServices/vaults/testvault/backupFabrics/Azure/protectionContainers/IaasVMContainer;iaasvmcontainer;RGName1;V2VM/protectedItems/VM;iaasvmcontainer; RGName1;V2VM/recoveryPoints/15260861925810
RecoveryPointType : AppConsistent
RecoveryPointTime : 4/23/2016 5:02:04 PM
WorkloadType : AzureVM
ContainerName : IaasVMContainer;iaasvmcontainer; RGName1;V2VM
ContainerType : AzureVM
BackupManagementType : AzureVM
装载恢复点的磁盘
请使用 Get-AzRecoveryServicesBackupRPMountScript cmdlet 获取用于装载恢复点的所有磁盘的脚本。
注意
这些磁盘作为 iSCSI 附加磁盘装载到运行此脚本的计算机中。 装载是即时发生的,并且不会产生任何费用。
Get-AzRecoveryServicesBackupRPMountScript -RecoveryPoint $rp[0] -VaultId $targetVault.ID
输出类似于以下示例:
OsType Password Filename
------ -------- --------
Windows e3632984e51f496 V2VM_wus2_8287309959960546283_451516692429_cbd6061f7fc543c489f1974d33659fed07a6e0c2e08740.exe
在要在它上面恢复文件的计算机上运行此脚本。 若要执行该脚本,必须输入所提供的密码。 附加磁盘后,使用 Windows 文件资源管理器浏览新的卷和文件。 有关详细信息,请参阅备份文章从 Azure 虚拟机备份恢复文件。
卸载磁盘
复制所需的文件后,请使用 Disable-AzRecoveryServicesBackupRPMountScript 卸载磁盘。 请确保卸载磁盘,以便删除对恢复点的文件的访问权限。
Disable-AzRecoveryServicesBackupRPMountScript -RecoveryPoint $rp[0] -VaultId $targetVault.ID
使用 PowerShell 将数据还原到虚拟机
现在,无需执行多个步骤即可将数据直接还原到原始/备用 VM。
将数据还原到原始 VM
$vault = Get-AzRecoveryServicesVault -ResourceGroupName "resourceGroup" -Name "vaultName"
$BackupItem = Get-AzRecoveryServicesBackupItem -BackupManagementType "AzureVM" -WorkloadType "AzureVM" -Name "V2VM" -VaultId $vault.ID
$StartDate = (Get-Date).AddDays(-7)
$EndDate = Get-Date
$RP = Get-AzRecoveryServicesBackupRecoveryPoint -Item $BackupItem -StartDate $StartDate.ToUniversalTime() -EndDate $EndDate.ToUniversalTime() -VaultId $vault.ID
$OriginalLocationRestoreJob = Restore-AzRecoveryServicesBackupItem -RecoveryPoint $RP[0] -StorageAccountName "DestStorageAccount" -StorageAccountResourceGroupName "DestStorageAccRG" -VaultId $vault.ID -VaultLocation $vault.Location
WorkloadName Operation Status StartTime EndTime
------------ --------- ------ --------- -------
V2VM Restore InProgress 26-Apr-16 1:14:01 PM 01-Jan-01 12:00:00 AM
最后一个命令触发原始位置还原操作,以还原现有 VM 中的数据。
将数据还原到新创建的 VM
$vault = Get-AzRecoveryServicesVault -ResourceGroupName "resourceGroup" -Name "vaultName"
$BackupItem = Get-AzRecoveryServicesBackupItem -BackupManagementType "AzureVM" -WorkloadType "AzureVM" -Name "V2VM" -VaultId $vault.ID
$StartDate = (Get-Date).AddDays(-7)
$EndDate = Get-Date
$RP = Get-AzRecoveryServicesBackupRecoveryPoint -Item $BackupItem -StartDate $StartDate.ToUniversalTime() -EndDate $EndDate.ToUniversalTime() -VaultId $vault.ID
$AlternateLocationRestoreJob = Restore-AzRecoveryServicesBackupItem -RecoveryPoint $RP[0] -TargetResourceGroupName "Target_RG" -StorageAccountName "DestStorageAccount" -StorageAccountResourceGroupName "DestStorageAccRG" -TargetVMName "TargetVirtualMachineName" -TargetVNetName "Target_VNet" -TargetVNetResourceGroup "" -TargetSubnetName "subnetName" -VaultId $vault.ID -VaultLocation $vault.Location
WorkloadName Operation Status StartTime EndTime
------------ --------- ------ --------- -------
V2VM Restore InProgress 26-Apr-16 1:14:01 PM 01-Jan-01 12:00:00 AM
最后一个命令会触发备用位置还原操作,根据参数 TargetVMName、TargetVNetName、TargetVNetResourceGroup、TargetSubnetName 在 Target_RG 资源组中创建新 VM。 这可确保数据在所需的 VM、虚拟网络和子网中还原。
后续步骤
如果你更愿意使用 PowerShell 来处理 Azure 资源,请查看 PowerShell 文章:为 Windows Server 部署和管理备份。 如果管理 DPM 备份,请参阅为 DPM 部署和管理备份。