本文介绍了如何设置和使用 Azure HDInsight ID 代理功能。 可以使用此功能获得对 Apache Ambari 的新式 OAuth 身份验证,同时执行多重身份验证,而无需在 Microsoft Entra 域服务中使用旧密码哈希。
概述
在以下情况下,HDInsight ID 代理简化了复杂的身份验证设置:
- 你的组织依赖于联合身份验证对访问云资源的用户进行身份验证。 以前,若要使用 HDInsight 企业安全性套餐群集,必须启用从本地环境到 Microsoft Entra ID 的密码哈希同步。 对于某些组织而言,此要求可能比较困难或不理想。
- 你的组织希望对基于 Web 或 HTTP 的 Apache Ambari 和其他群集资源的访问强制执行多重身份验证。
HDInsight ID 代理提供身份验证基础结构,支持协议从 OAuth(新式)转换到 Kerberos(旧式),而无需将密码哈希同步到 Microsoft Entra 域服务。 此基础结构包括在启用了 HDInsight ID 代理节点的 Windows Server 虚拟机 (VM) 上运行的组件以及群集网关节点。
使用下表根据你的组织需求确定最佳身份验证选项。
| 身份验证选项 | HDInsight 配置 | 需考虑的因素 |
|---|---|---|
| 完全 OAuth | 企业安全性套餐 + HDInsight ID 代理 | 最安全的选项。 (支持多重身份验证。)不需要哈希传递同步。 不支持本地帐户的 ssh/kinit/keytab 访问,这些帐户在 Microsoft Entra 域服务中没有密码哈希。 仅限云的帐户仍然可以使用 ssh/kinit/keytab 访问。 通过 OAuth 实现的对 Ambari 的基于 Web 的访问。 需要更新旧版应用(例如 JDBC/ODBC)以支持 OAuth。 |
| OAuth + 基本身份验证 | 企业安全性套餐 + HDInsight ID 代理 | 通过 OAuth 实现的对 Ambari 的基于 Web 的访问。 旧版应用继续使用基本身份验证。对于基本身份验证访问,必须禁用多重身份验证。 不需要哈希传递同步。 不支持本地帐户的 ssh/kinit/keytab 访问,这些帐户在 Microsoft Entra 域服务中没有密码哈希。 仅限云的帐户仍然可以使用 ssh/kinit 访问。 |
| 完全基本身份验证 | 企业安全性套餐 | 最类似于本地设置。 需要将密码哈希同步到 Microsoft Entra 域服务。 本地帐户可以使用 ssh/kinit 或使用 keytab。 如果后备存储是 Azure Data Lake Storage Gen2,则必须禁用多重身份验证。 |
下图显示了启用 HDInsight ID 代理后针对所有用户(包括联合用户)的基于 OAuth 的新式身份验证流:
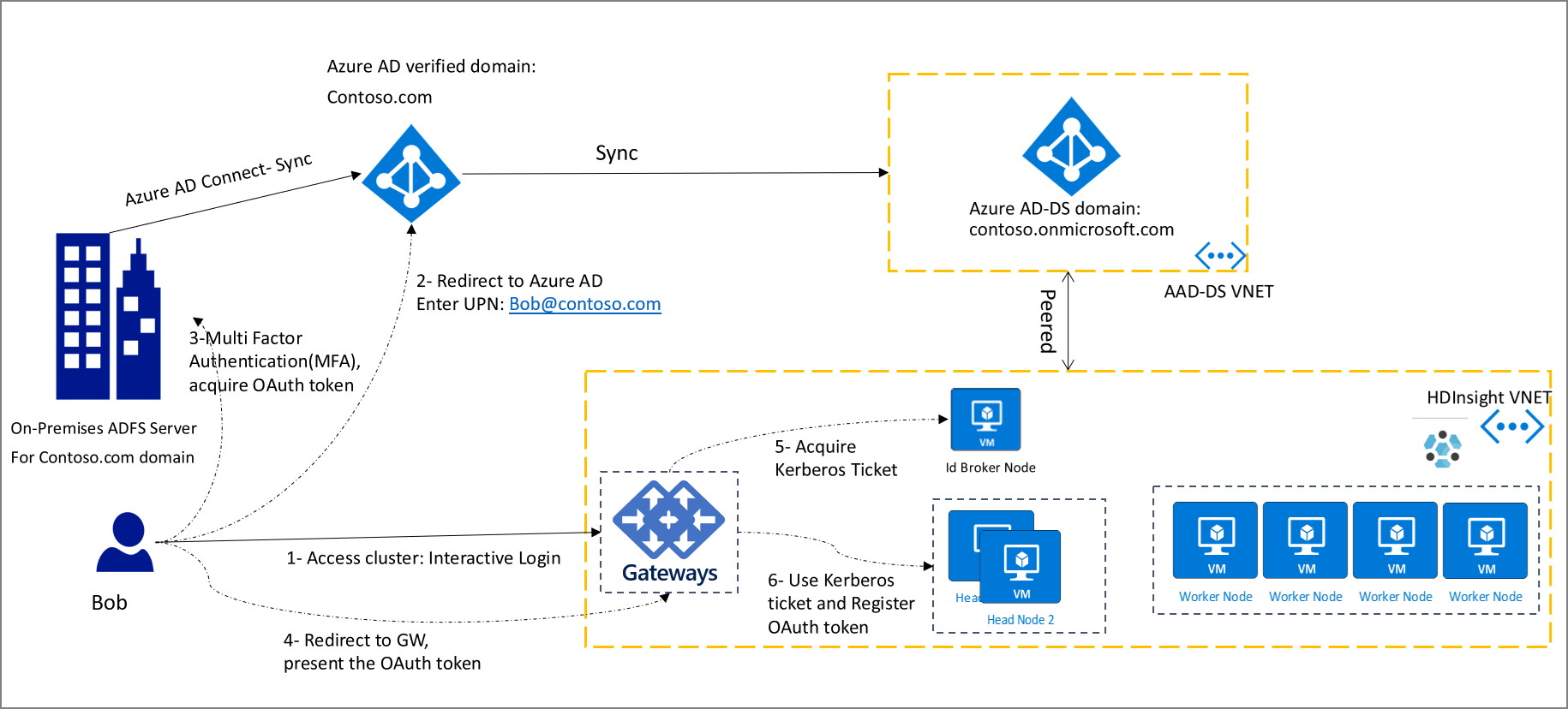
在此图中,客户端(即浏览器或应用)需要首先获取 OAuth 令牌。 然后,将该令牌提供给 HTTP 请求中的网关。 如果已登录到其他 Azure 服务(例如 Azure 门户),可以使用单一登录体验登录到 HDInsight 群集。
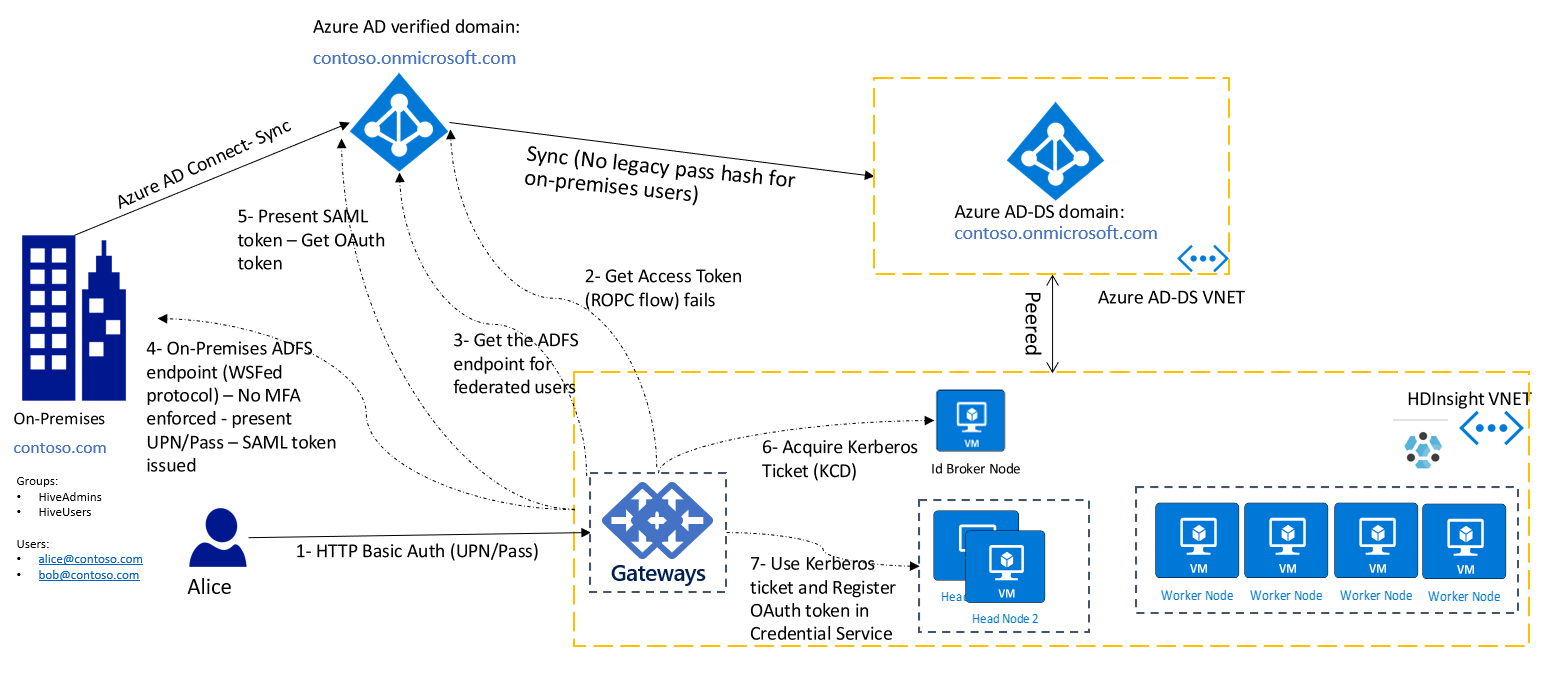
仍有许多旧版应用程序仅支持基本身份验证(即用户名和密码)。 对于这些情况,仍然可以使用 HTTP 基本身份验证连接到群集网关。 在此设置中,必须确保从网关节点到 Active Directory 联合身份验证服务 (AD FS) 终结点的网络连接性,从而确保网关节点的直接视线。
下图显示了联合用户的基本身份验证流。 首先,网关尝试使用 ROPC 流完成身份验证。 如果没有密码哈希同步到 Microsoft Entra ID,则会回退到发现 AD FS 终结点并通过访问 AD FS 终结点完成身份验证。
启用 HDInsight ID 代理
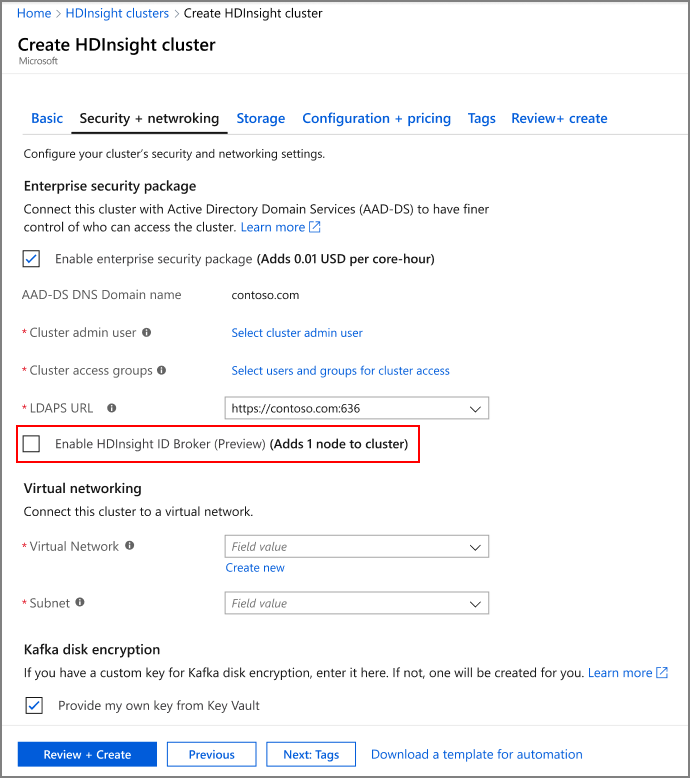
创建启用了 HDInsight ID 代理的企业安全性套餐群集,
- 登录 Azure 门户。
- 按照企业安全性套餐群集的基本创建步骤进行操作。 有关详细信息,请参阅创建使用企业安全性套餐的 HDInsight 群集。
- 选择“启用 HDInsight ID 代理”。
HDInsight ID 代理功能将向群集添加一个额外的 VM。 此 VM 是 HDInsight ID 代理节点,包括用来支持身份验证的服务器组件。 HDInsight ID 代理节点以域加入方式加入到 Microsoft Entra 域服务域。
使用 Azure 资源管理器模板
如果将名为idbrokernode且具有以下特性的新角色添加到模板的计算配置文件中,则会在启用了 HDInsight ID 代理节点的情况下创建群集:
.
.
.
"computeProfile": {
"roles": [
{
"autoscale": null,
"name": "headnode",
....
},
{
"autoscale": null,
"name": "workernode",
....
},
{
"autoscale": null,
"name": "idbrokernode",
"targetInstanceCount": 2,
"hardwareProfile": {
"vmSize": "Standard_A2_V2"
},
"virtualNetworkProfile": {
"id": "string",
"subnet": "string"
},
"scriptActions": [],
"dataDisksGroups": null
}
]
}
.
.
.
要查看 ARM 模板的完整示例,请参阅此处发布的模板。
工具集成
更新 HDInsight 工具以本机支持 OAuth。 使用这些工具对群集进行基于 OAuth 的新式访问。 HDInsight IntelliJ 插件可以用于基于 Java 的应用程序,例如 Scala。 适用于 Visual Studio Code 的 Spark 和 Hive 工具可用于 PySpark 和 Hive 作业。 这些工具同时支持批处理和交互式作业。
在 Microsoft Entra 域服务中没有密码哈希的 SSH 访问
| SSH 选项 | 需考虑的因素 |
|---|---|
| 本地 VM 帐户(例如 sshuser) | 你创建群集时提供了此帐户。 此帐户没有 Kerberos 身份验证。 |
| 仅限云的帐户(例如 alice@contoso.partner.onmschina.cn) | Microsoft Entra 域服务中提供了密码哈希。 Kerberos 身份验证可以通过 SSH Kerberos 进行。 |
| 本地帐户(例如 alice@contoso.com) | 只有在 Microsoft Entra 域服务中提供了密码哈希,才能进行 SSH Kerberos 身份验证。 否则,该用户无法通过 SSH 连接到群集。 |
若要通过 SSH 连接到已加入域的 VM,或者要运行 kinit 命令,必须提供密码。 SSH Kerberos 身份验证要求在 Microsoft Entra 域服务中提供哈希。 如果只想将 SSH 用于管理方案,则可创建一个仅限云的帐户,并使用该帐户通过 SSH 连接到群集。 其他本地用户仍可使用 Ambari、HDInsight 工具或 HTTP 基本身份验证,而不需要在 Microsoft Entra 域服务中有密码哈希。
如果你的组织未将密码哈希同步到 Microsoft Entra 域服务,则最佳做法是在 Microsoft Entra ID 中创建一个仅限云的用户。 然后,在创建群集时将其分配为群集管理员,并将其用于管理目的。 可以使用该用户通过 SSH 获取对 VM 的根访问权限。
若要排查身份验证问题,请参阅此指南。
客户端使用 OAuth 连接到使用 HDInsight ID 代理的 HDInsight 网关
在 HDInsight ID 代理设置中,可以更新连接到网关的自定义应用和客户端,以便首先获取所需的 OAuth 令牌。 有关详细信息,请参阅《如何使用 Azure 服务对 .NET 应用程序进行身份验证》。 授权访问 HDInsight 网关所需的密钥值为:
- OAuth 资源 URI:
https://hib.azurehdinsight.cn - AppId:00001111-aaaa-2222-bbbb-3333cccc4444
- 权限:(名称:Cluster.ReadWrite,id:8f89faa0-ffef-4007-974d-4989b39ad77d)
获取 OAuth 令牌后,在向群集网关(例如 https://<clustername>-int.azurehdinsight.cn)发出的 HTTP 请求的授权标头中使用该令牌。 Apache livy API 的示例 curl 命令可能如下例所示:
curl -k -v -H "Authorization: Bearer Access_TOKEN" -H "Content-Type: application/json" -X POST -d '{ "file":"wasbs://mycontainer@mystorageaccount.blob.core.chinacloudapi.cn/data/SparkSimpleTest.jar", "className":"com.microsoft.spark.test.SimpleFile" }' "https://<clustername>-int.azurehdinsight.cn/livy/batches" -H "X-Requested-By:<username@domain.com>"
要使用 Beeline 和 Livy,还可以按照此处提供的示例代码来设置客户端,以使用 OAuth 并连接到群集。
常见问题解答
Microsoft Entra ID 中的 HDInsight 创建了什么应用?
对于每个群集,会在 Microsoft Entra ID 中注册第三方应用程序,并将群集 URI 作为 identifierUri(如 https://clustername.azurehdinsight.cn)。
为什么在使用支持 HIB 的群集之前,用户会看到要求提供许可的提示?
在 Microsoft Entra ID 中,所有第三方应用程序都需要先获得用户许可才能对用户进行身份验证或访问数据。
同意是否可以以编程方式获得批准?
Microsoft Graph API 允许自动提供许可,请参阅 API 文档了解相关信息。自动提供许可的顺序为:
- 注册应用并向应用授予 Application.ReadWrite.All 权限,以访问 Microsoft Graph
- 创建群集后,基于标识符 URI 查询群集应用
- 注册应用的许可
删除群集后,HDInsight 会删除该应用,无需清除任何许可。