使用 Azure 专用链接服务,可以通过虚拟网络中的专用终结点访问 Azure 服务(例如 Azure 服务总线、Azure 存储和 Azure Cosmos DB)以及 Azure 托管的客户服务/合作伙伴服务。
专用终结点是一个网络接口,可以通过专用且安全的方式将你连接到 Azure 专用链接支持的服务。 专用终结点使用虚拟网络中的专用 IP 地址将服务有效地接入虚拟网络中。 发往服务的所有流量都可以通过专用终结点路由,因此不需要网关、NAT 设备、ExpressRoute 或 VPN 连接或公共 IP 地址。 虚拟网络与服务之间的流量将通过 Microsoft 主干网络,因此不会从公共 Internet 泄露。 可以连接到 Azure 资源的实例,从而获得最高级别的访问控制粒度。
有关详细信息,请参阅什么是 Azure 专用链接?
要点
通过 Azure 服务总线高级层支持此功能。 有关高级层的详细信息,请参阅服务总线高级和标准消息传送层。
实施专用终结点可以阻止其他 Azure 服务与服务总线进行交互。 例外情况是,可以允许从某些受信任的服务访问服务总线资源,即使启用了专用终结点也是如此。 有关受信任服务的列表,请参阅受信任服务。
以下 Azure 服务必须在虚拟网络中
- Azure App 服务
- Azure Functions
为命名空间指定至少一个 IP 规则或虚拟网络规则,以便仅允许来自虚拟网络的指定 IP 地址或子网的流量。 如果没有 IP 和虚拟网络规则,则可以通过公共 Internet(使用访问密钥)访问命名空间。
使用 Azure 门户添加专用终结点
Prerequisites
若要将服务总线命名空间与 Azure 专用链接集成,需要以下实体或权限:
- 服务总线命名空间。
- 一个 Azure 虚拟网络。
- 虚拟网络中的子网。 可以使用默认子网。
- 对服务总线命名空间和虚拟网络拥有所有者或参与者权限。
专用终结点和虚拟网络必须位于同一区域。 使用门户选择专用终结点的区域时,只会自动筛选该区域中的虚拟网络。 服务总线命名空间可以位于不同的区域中。 并且,专用终结点使用虚拟网络中的专用 IP 地址。
创建命名空间时配置专用访问
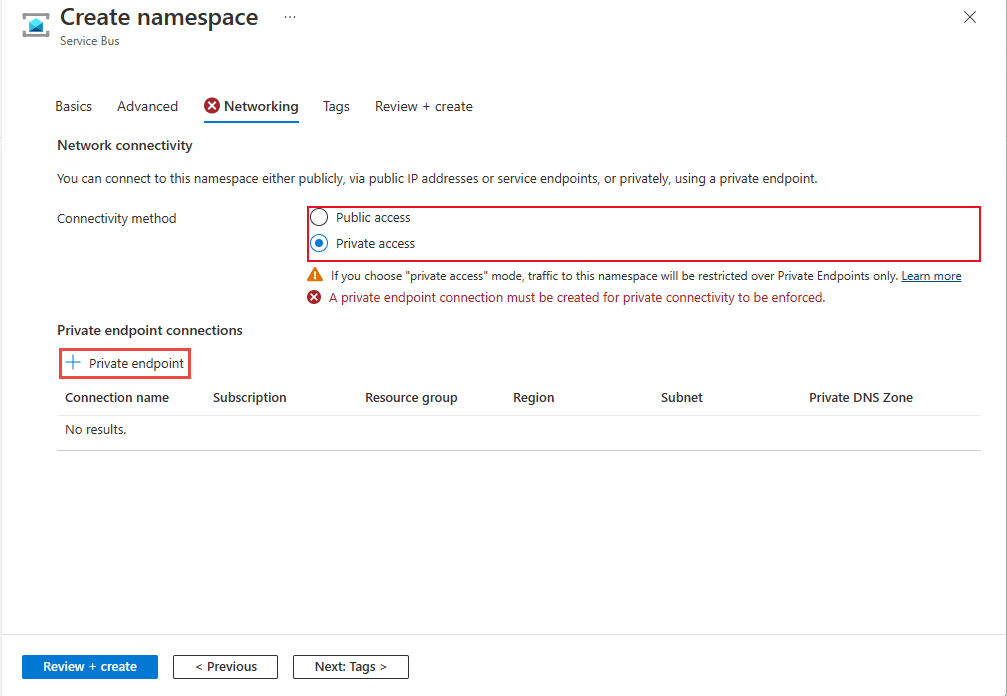
创建命名空间时,可以仅允许对该命名空间进行公共访问(从所有网络进行访问),也可以仅允许对命名空间进行专用访问(仅通过专用终结点进行访问)。
如果在命名空间创建向导的“网络”页上选择“专用访问”选项,则可以通过选择“+ 专用终结点”按钮在页面上添加专用终结点。 有关如何添加专用终结点的详细步骤,请参阅下一部分。
为现有命名空间配置专用访问
如果已有现有命名空间,可按以下步骤创建专用终结点:
登录 Azure 门户。
在搜索栏中键入“服务总线”。
从列表中选择要将专用终结点添加到的“命名空间”。
在左侧菜单上,选择“设置”下的“网络”选项 。
Note
只会为“高级”命名空间显示“网络”选项卡 。
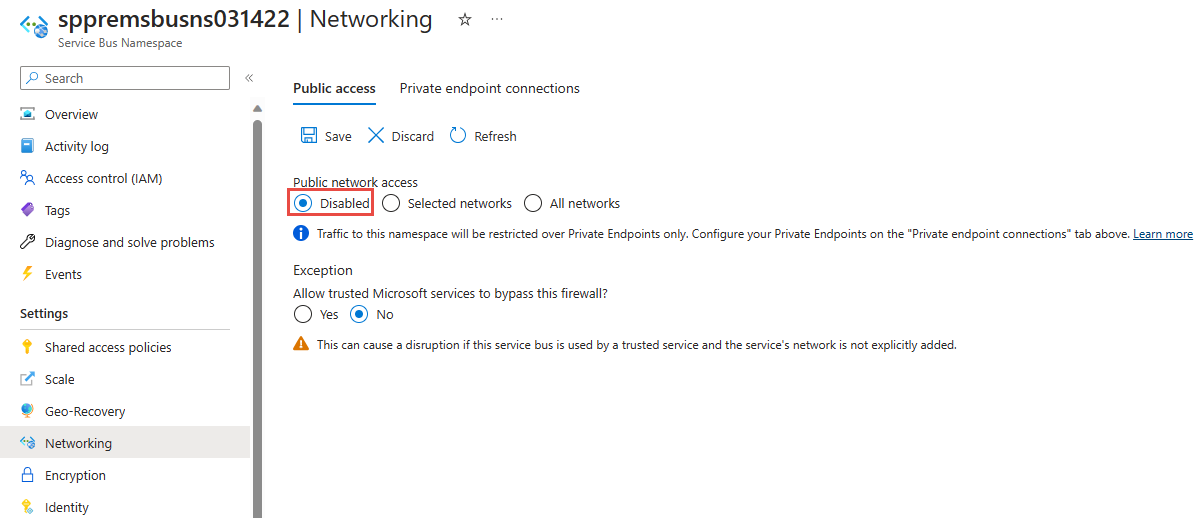
在“网络”页上,对于“公用网络访问”,如果希望仅通过专用终结点访问命名空间,请选择“已禁用”。
如果要允许受信任的 Azure 服务绕过此防火墙,则对“允许受信任的 Azure 服务绕过此防火墙”选择“是”。
在工具栏上选择“保存”。
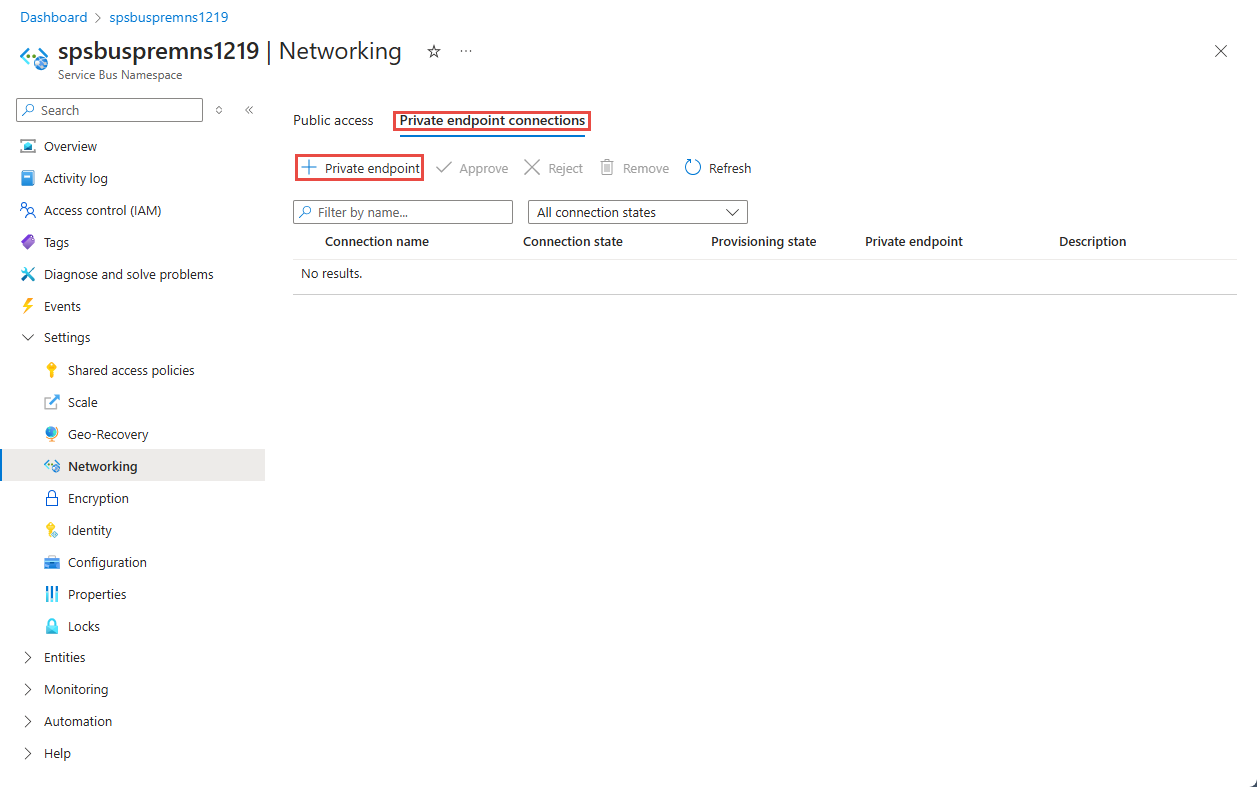
若要允许通过专用终结点访问命名空间,请选择页面顶部的“专用终结点连接”选项卡
在页面顶部选择“+ 专用终结点”按钮。
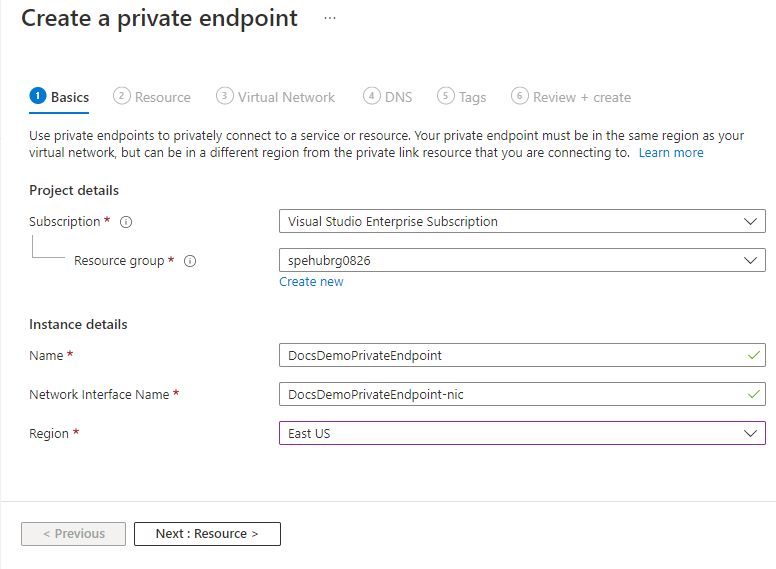
在“基本信息”页上执行以下步骤:
选择要在其中创建专用终结点的 Azure 订阅。
选择专用终结点资源的资源组。
输入专用终结点的名称。
为网络接口输入一个名称。
专用终结点选择“区域”。 专用终结点必须与虚拟网络位于同一区域,但可以与你要连接的专用链接资源位于不同的区域。
选择页面底部的“下一步: 资源 >”。
在“资源”页上,查看设置,然后选择该页底部的“下一步: 虚拟网络”。
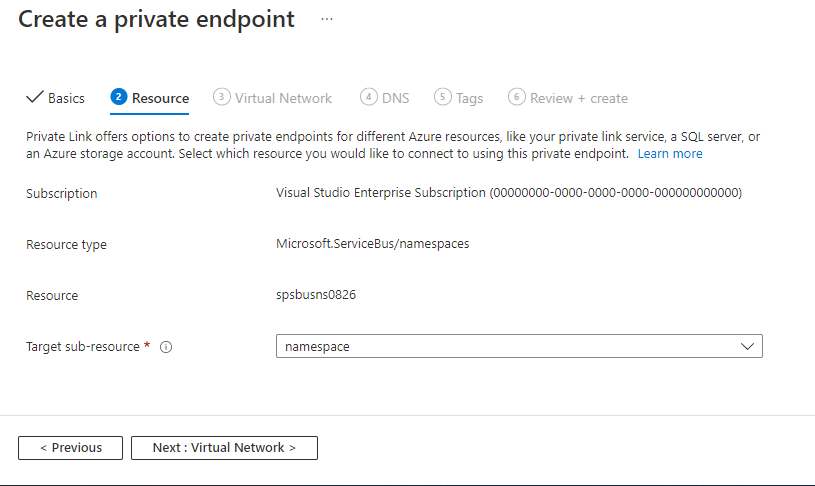
在“虚拟网络”页上,选择要在其中部署专用终结点的虚拟网络中的子网。
选择一个虚拟网络。 下拉列表中仅列出了当前所选订阅和位置中的虚拟网络。
在所选的虚拟网络中选择一个“子网”。
对于专用 IP 配置,默认情况下会选中“动态分配 IP 地址”选项。 如果要分配静态 IP 地址,请选择“静态分配 IP 地址”*。
对于专用 DNS 集成,请选择是否要将专用终结点与专用 DNS 区域集成。
选择页面底部的“下一步: DNS >”按钮。
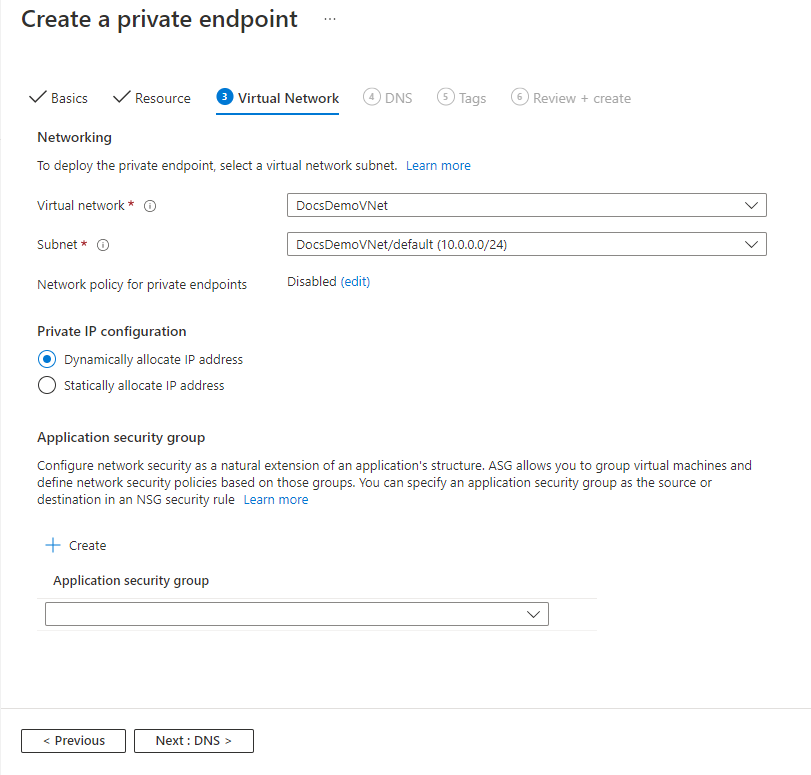
在“DNS”页上,选择是否要将专用终结点与专用 DNS 区域集成,然后选择“下一步: 标记”。
在“标记”页上,创建要与专用终结点资源关联的任何标记(名称和值)。 然后选择页面底部的“查看 + 创建”按钮。
在“查看 + 创建”页上查看所有设置,然后选择“创建”以创建专用终结点 。
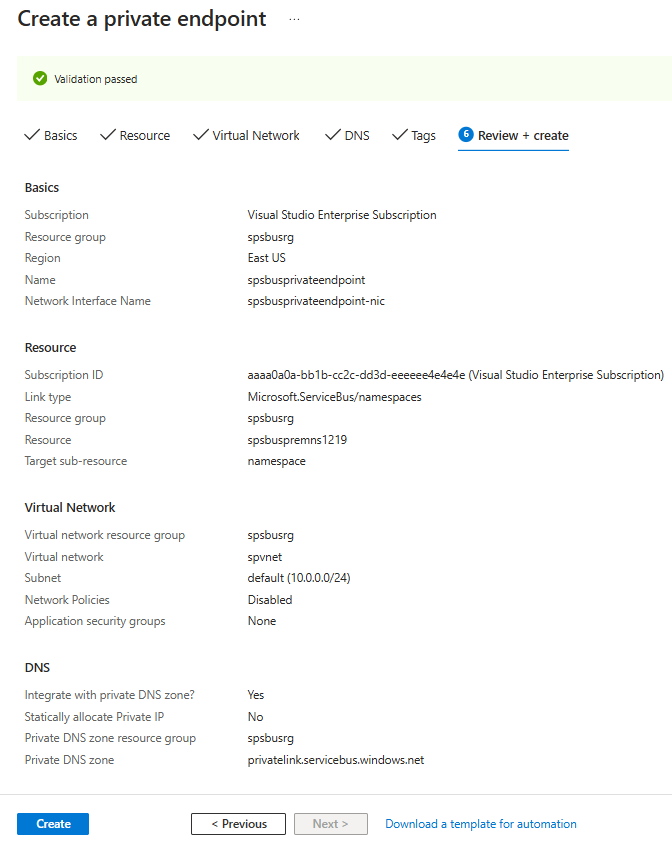
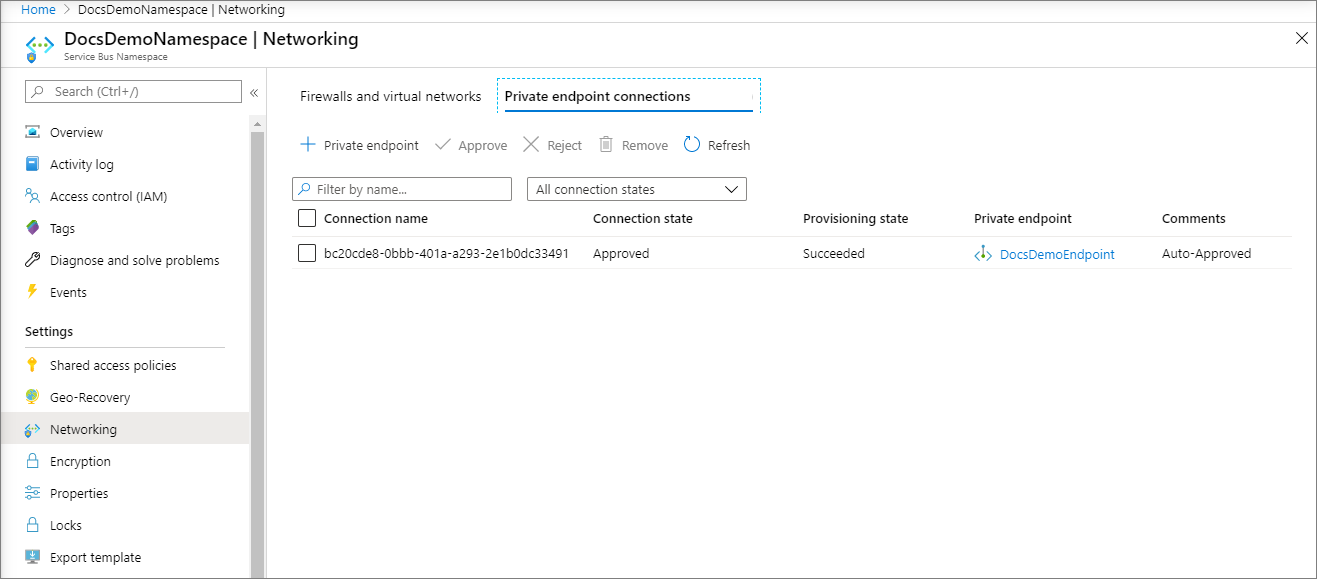
确认已创建专用终结点。 如果你是资源的所有者,在服务总线命名空间的“网络”页面上,终结点连接应自动批准。 如果它处于“挂起”状态,请参阅使用 Azure 门户管理专用终结点部分。
受信任的 Microsoft 服务
启用“允许受信任的 Microsoft 服务绕过此防火墙”设置时,将授权以下服务访问你的服务总线资源。
Important
启用受信任的 Microsoft 服务时,请始终分配托管标识。 此标识可促进服务总线命名空间与受信任的 Azure 服务之间的安全通信。
受信任的服务 支持的使用方案 Azure 事件网格 允许 Azure 事件网格将事件发送到服务总线命名空间中的队列或主题。 还需要执行以下步骤: - 为主题或域启用系统分配的标识
- 为服务总线命名空间中的“Azure 服务总线数据发送方”角色添加标识
- 然后,将使用服务总线队列或主题的事件订阅配置为终结点,以使用系统分配的标识。
有关详细信息,请参阅使用托管标识进行事件传递
Azure 流分析 允许 Azure 流分析作业将数据输出到服务总线队列到主题。 重要说明:流分析作业应配置为使用“托管标识”来访问服务总线命名空间。 为服务总线命名空间中的“Azure 服务总线数据发送方”角色添加标识。
Azure IoT 中心 允许 IoT 中心将消息发送到服务总线命名空间中的队列或主题。 还需要执行以下步骤: - 为 IoT 中心启用系统分配的或用户分配的托管标识。
- 为服务总线命名空间中的“Azure 服务总线数据发送方”角色添加标识。
- 将使用服务总线实体的 IoT 中心配置为终结点,以使用基于标识的身份验证。
Azure API 管理 API 管理服务允许你向服务总线命名空间中的服务总线队列/主题发送消息。
- 使用 send-request 策略调用 API 时,可以通过向服务总线队列/主题发送消息来触发自定义工作流。
- 还可以将服务总线队列/主题视为 API 中的后端。 有关示例策略,请参阅使用托管标识进行身份验证以访问服务总线队列或主题。 还需要执行以下步骤:
- 在 API 管理实例上启用系统分配的标识。 有关说明,请参阅在 Azure API 管理中使用托管标识。
- 为服务总线命名空间中的“Azure 服务总线数据发送方”角色添加标识
Azure Monitor(诊断设置和操作组) 允许 Azure Monitor 将诊断信息和警报通知发送到服务总线命名空间中的服务总线。 Azure Monitor 可以从 Azure 服务总线命名空间读取和向其写入数据。 Azure Synapse 允许 Azure Synapse 使用 Synapse 工作区托管标识连接到服务总线。 将 Azure 服务总线数据发送方、接收方或所有者角色添加到 Azure 服务总线命名空间的标识中。 可在下面找到适用于 Azure 服务总线的其他受信任服务:
- Azure 数据资源管理器
- Azure Health Data Services
- Azure Arc
- Azure Kubernetes
- Azure 机器学习
- Microsoft Purview
- Microsoft Defender for Cloud
- Azure 提供程序中心
若要允许受信任的服务访问你的命名空间,请切换到“网络”页面上的“公共访问”选项卡,然后针对“是否允许受信任的 Azure 服务跳过此防火墙?”选择“是”。
使用 PowerShell 添加专用终结点
以下示例演示如何使用 Azure PowerShell 创建与服务总线命名空间的专用终结点连接。
专用终结点和虚拟网络必须位于同一区域。 服务总线命名空间可以位于不同的区域中。 并且,专用终结点使用虚拟网络中的专用 IP 地址。
$rgName = "<RESOURCE GROUP NAME>"
$vnetlocation = "<VNET LOCATION>"
$vnetName = "<VIRTUAL NETWORK NAME>"
$subnetName = "<SUBNET NAME>"
$namespaceLocation = "<NAMESPACE LOCATION>"
$namespaceName = "<NAMESPACE NAME>"
$peConnectionName = "<PRIVATE ENDPOINT CONNECTION NAME>"
# create resource group
New-AzResourceGroup -Name $rgName -Location $vnetLocation
# create virtual network
$virtualNetwork = New-AzVirtualNetwork `
-ResourceGroupName $rgName `
-Location $vnetlocation `
-Name $vnetName `
-AddressPrefix 10.0.0.0/16
# create subnet with endpoint network policy disabled
$subnetConfig = Add-AzVirtualNetworkSubnetConfig `
-Name $subnetName `
-AddressPrefix 10.0.0.0/24 `
-PrivateEndpointNetworkPoliciesFlag "Disabled" `
-VirtualNetwork $virtualNetwork
# update virtual network
$virtualNetwork | Set-AzVirtualNetwork
# create premium service bus namespace
$namespaceResource = New-AzResource -Location $namespaceLocation -ResourceName $namespaceName -ResourceGroupName $rgName -Sku @{name = "Premium"; capacity = 1} -Properties @{} -ResourceType "Microsoft.ServiceBus/namespaces" -
# create a private link service connection
$privateEndpointConnection = New-AzPrivateLinkServiceConnection `
-Name $peConnectionName `
-PrivateLinkServiceId $namespaceResource.ResourceId `
-GroupId "namespace"
# get subnet object that you will use in the next step
$virtualNetwork = Get-AzVirtualNetwork -ResourceGroupName $rgName -Name $vnetName
$subnet = $virtualNetwork | Select -ExpandProperty subnets `
| Where-Object {$_.Name -eq $subnetName}
# now, create private endpoint
$privateEndpoint = New-AzPrivateEndpoint -ResourceGroupName $rgName `
-Name $vnetName `
-Location $vnetlocation `
-Subnet $subnet `
-PrivateLinkServiceConnection $privateEndpointConnection
(Get-AzResource -ResourceId $namespaceResource.ResourceId -ExpandProperties).Properties
使用 Azure 门户管理专用终结点
创建专用终结点时,必须批准连接。 如果要为其创建专用终结点的资源位于你的目录中,在拥有足够权限的前提下,你可以批准连接请求。 如果要连接到另一个目录中的 Azure 资源,必须等待该资源的所有者批准你的连接请求。
有四种预配状态:
| 服务操作 | 服务使用者专用终结点状态 | Description |
|---|---|---|
| None | Pending | 连接是手动创建的,正等待专用链接资源所有者批准。 |
| Approve | Approved | 连接已自动或手动批准,随时可供使用。 |
| Reject | Rejected | 连接已被专用链接资源所有者拒绝。 |
| Remove | Disconnected | 连接被专用链接资源所有者删除。 专用终结点已变为参考性终结点,应将其删除以清理资源。 |
批准、拒绝或删除专用终结点连接
- 登录到 Azure 门户。
- 在搜索栏中键入“服务总线”。
- 选择要管理的“命名空间”。
- 选择“网络”选项卡。
- 根据要执行的操作(批准、拒绝或删除),查看下面的相应部分。
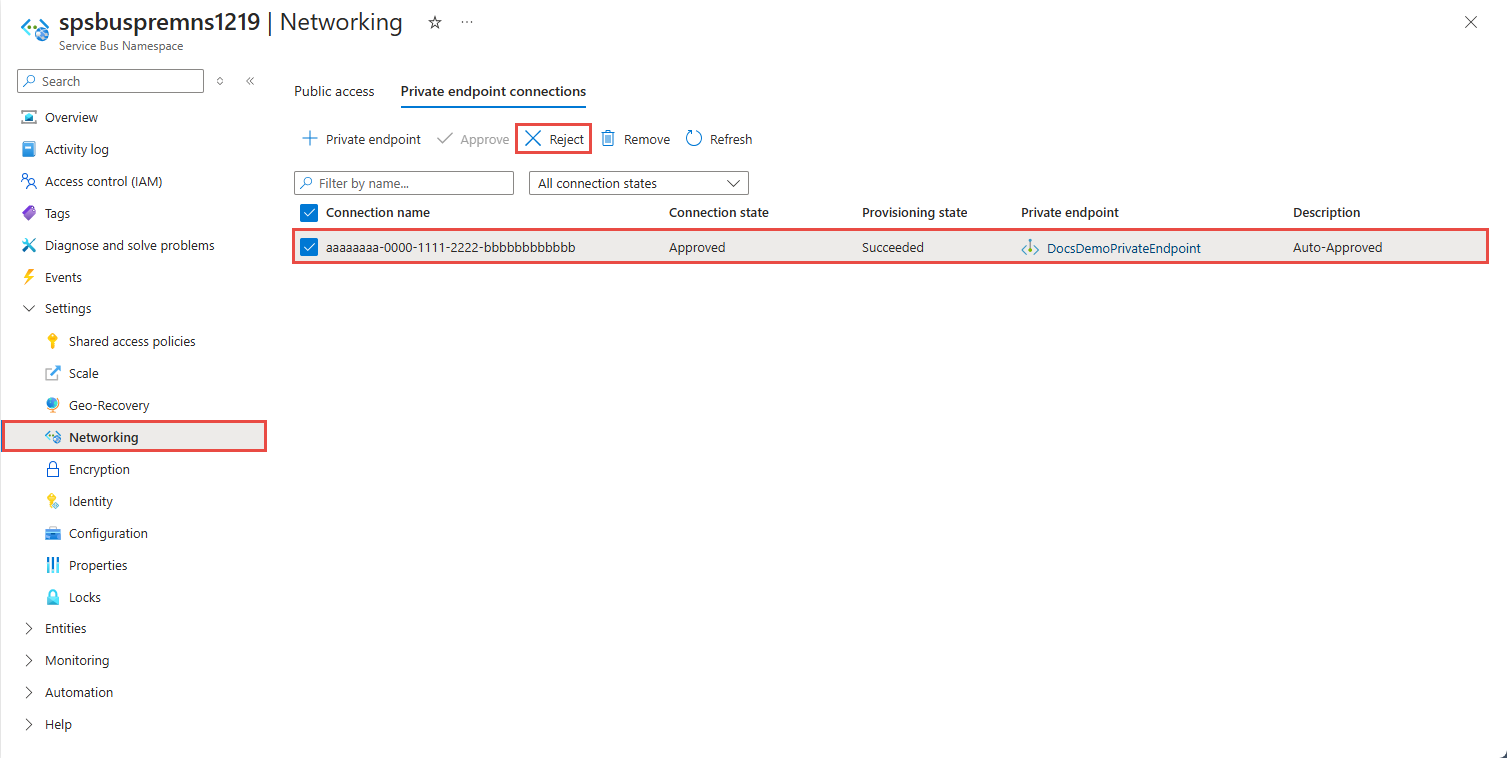
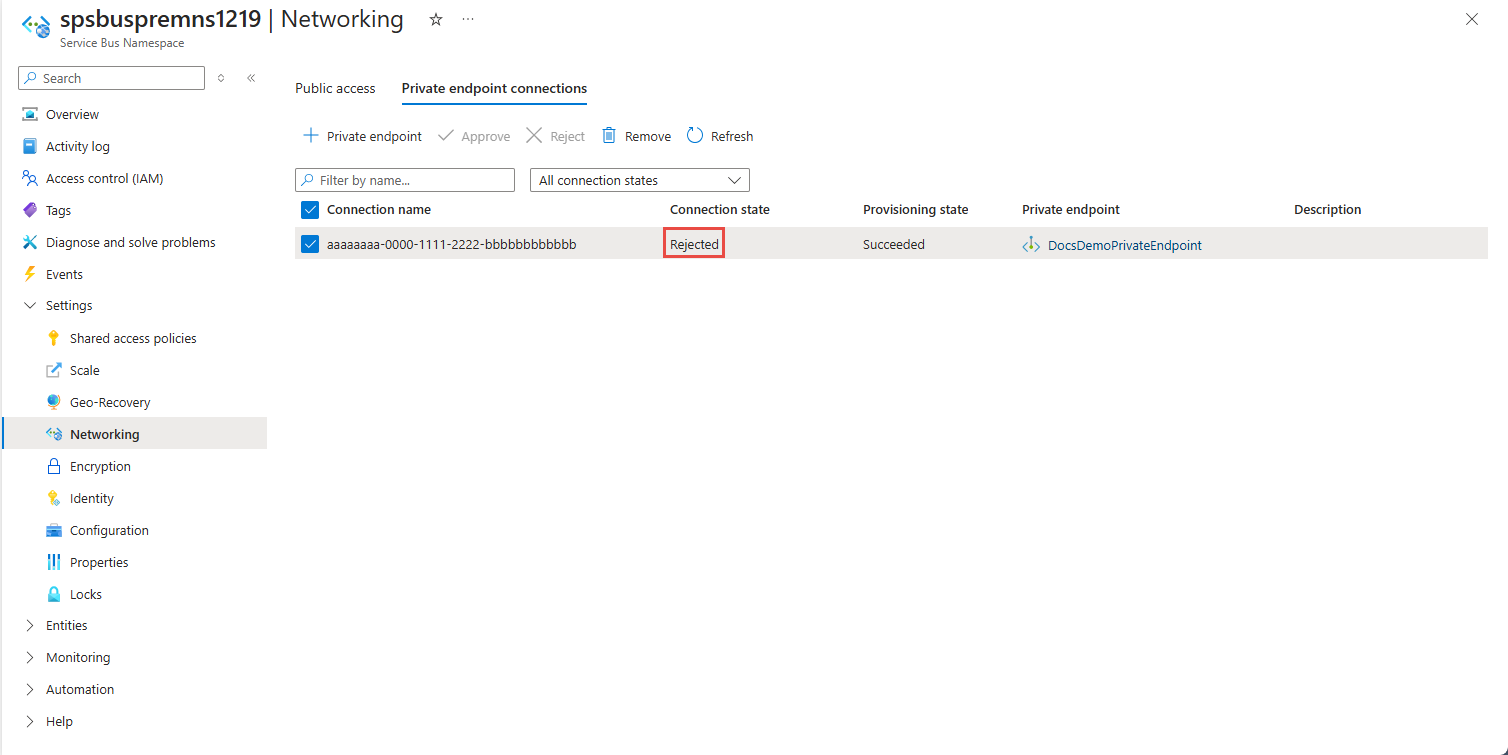
拒绝专用终结点连接
如果要拒绝任何专用终结点连接(不管是挂起的请求还是此前已批准的现有连接),请选择该终结点连接并选择“拒绝”按钮。
在“拒绝连接”页上输入可选注释,然后选择“是” 。 如果选择“否”,则不会执行任何操作。
应会看到,列表中连接的状态已更改为“已拒绝”。
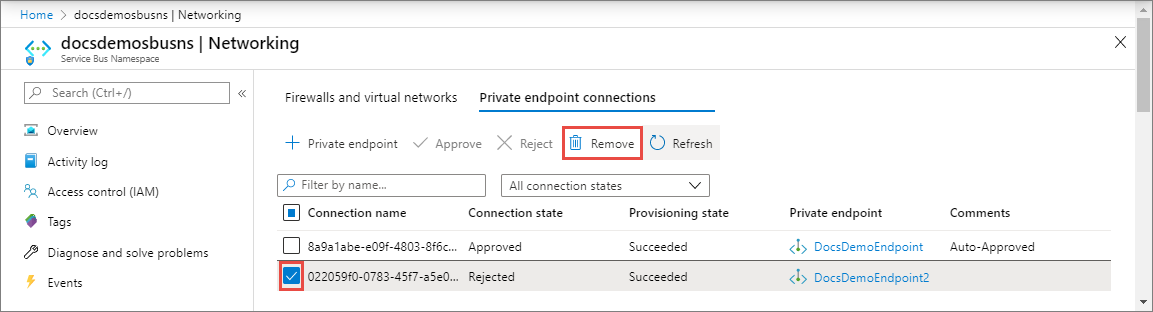
删除专用终结点连接
若要删除某个专用终结点连接,请在列表中选择它,然后在工具栏上选择“删除”。
在“删除连接”页上,选择“是”以确认删除该专用终结点。 如果选择“否”,则不会执行任何操作。
应会看到,状态已更改为“已断开连接”。 然后,该终结点就会从列表中消失。
批准专用终结点连接
- 如果有任何挂起的连接,则会列出预配状态为“挂起”的连接。
- 选择要批准的专用终结点
- 选择工具栏上的“批准”按钮。
- 在“批准连接”页上输入可选注释,然后选择“是” 。 如果选择“否”,则不会执行任何操作。
- 应会看到,列表中连接的状态已更改为“已批准”。
验证专用链接连接是否有效
应该验证专用终结点的虚拟网络中的资源是否可以通过专用 IP 地址连接到服务总线命名空间,以及它们是否具有正确的专用 DNS 区域集成。
首先,遵循在 Azure 门户中创建 Windows 虚拟机中的步骤创建一个虚拟机。
在“网络”选项卡中:
- 指定虚拟网络和子网 。 必须选择已将专用终结点部署到的虚拟网络。
- 指定一个公共 IP 资源。
- 对于“NIC 网络安全组”,请选择“无” 。
- 对于“负载均衡”,请选择“否”。
连接到 VM,打开命令行并运行以下命令:
nslookup <service-bus-namespace-name>.servicebus.chinacloudapi.cn
应会看到如下所示的结果。
Non-authoritative answer:
Name: <service-bus-namespace-name>.privatelink.servicebus.chinacloudapi.cn
Address: 10.0.0.4 (private IP address associated with the private endpoint)
Aliases: <service-bus-namespace-name>.servicebus.chinacloudapi.cn
限制和设计注意事项
- 有关定价信息,请参阅 Azure 专用链接定价。
- 此功能可在所有 Azure 公共区域中使用。
- 每个服务总线命名空间的最大专用终结点数目:120。
- 流量在应用程序层被阻止,而不是在 TCP 层被阻止。 因此,即使公共访问已禁用,也会看到针对公共终结点的 TCP 连接或
nslookup操作成功。
有关详细信息,请参阅 Azure 专用链接服务:限制
后续步骤
- 详细了解 Azure 专用链接
- 详细了解 Azure 服务总线