默认情况下,只要请求包含有效的身份验证和授权,就可以从互联网访问服务总线命名空间。 有了 IP 防火墙,入站流量可以限制在一组 IPv4 地址或 IPv4 地址范围内(采用 CIDR(无类别域际路由)表示法)。
在仅应从某些知名站点访问 Azure 服务总线的情况下,此功能很有用。 可以通过防火墙规则来配置规则,以便接受来自特定 IPv4 地址的流量。 例如,如果将服务总线与 Azure Express Route 配合使用,则可创建防火墙规则,以便仅允许来自本地基础结构 IP 地址或企业 NAT 网关地址的流量。
IP 防火墙规则
IP 防火墙规则应用于服务总线命名空间级别。 因此,这些规则适用于通过任何受支持协议(AMQP (5671) 和 HTTPS (443))从客户端发出的所有连接。 如果某 IP 地址与服务总线命名空间上的允许 IP 规则不匹配,则将拒绝来自该地址的任何连接尝试并将其标记为“未经授权”。 响应不会提及 IP 规则。 IP 筛选器规则将按顺序应用,与 IP 地址匹配的第一个规则决定了将执行接受操作还是执行拒绝操作。
Note
服务总线 SKU 之间的网络选项不同。 标准 SKU 支持 IP 筛选,但不包括“受信任的服务”选项。 有关高级 SKU 网络功能,请参阅专用高级 SKU 网络文档。
要点
虚拟网络仅在服务总线的“高级”层中受支持。 如果不能选择升级到“高级”层级,可以通过 Azure 门户、Azure 资源管理器模板、Azure CLI、PowerShell 或 REST API 使用 IP 防火墙规则。 我们建议保护共享访问签名 (SAS) 令牌的安全,只与授权用户共享它。 有关 SAS 身份验证的信息,请参阅身份验证和授权。
为命名空间指定至少一个 IP 防火墙规则或虚拟网络规则,以便仅允许来自虚拟网络的指定 IP 地址或子网的流量。 如果没有 IP 和虚拟网络规则,则可以通过公共 Internet(使用访问密钥)访问命名空间。
实施防火墙规则可以组织其他 Azure 服务与服务总线进行交互。 例外情况是,可以允许从某些受信任的服务访问服务总线资源,即使在启用了 IP 筛选功能时也是如此。 有关受信任服务的列表,请参阅受信任服务。
以下 Azure 服务必须在虚拟网络中
- Azure App 服务
- Azure Functions
使用 Azure 门户
创建命名空间时,可以仅允许对该命名空间进行公共访问(从所有网络进行访问),也可以仅允许对命名空间进行专用访问(仅通过专用终结点进行访问)。 创建命名空间后,可以允许从特定 IP 地址或特定虚拟网络进行的访问(使用网络服务终结点)。
创建命名空间时配置公共访问
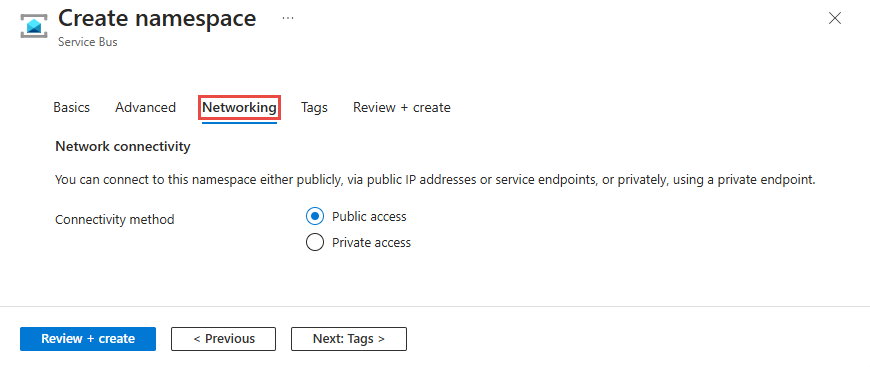
若要启用公共访问,请在命名空间创建向导的“网络”页上选择“公共访问”。
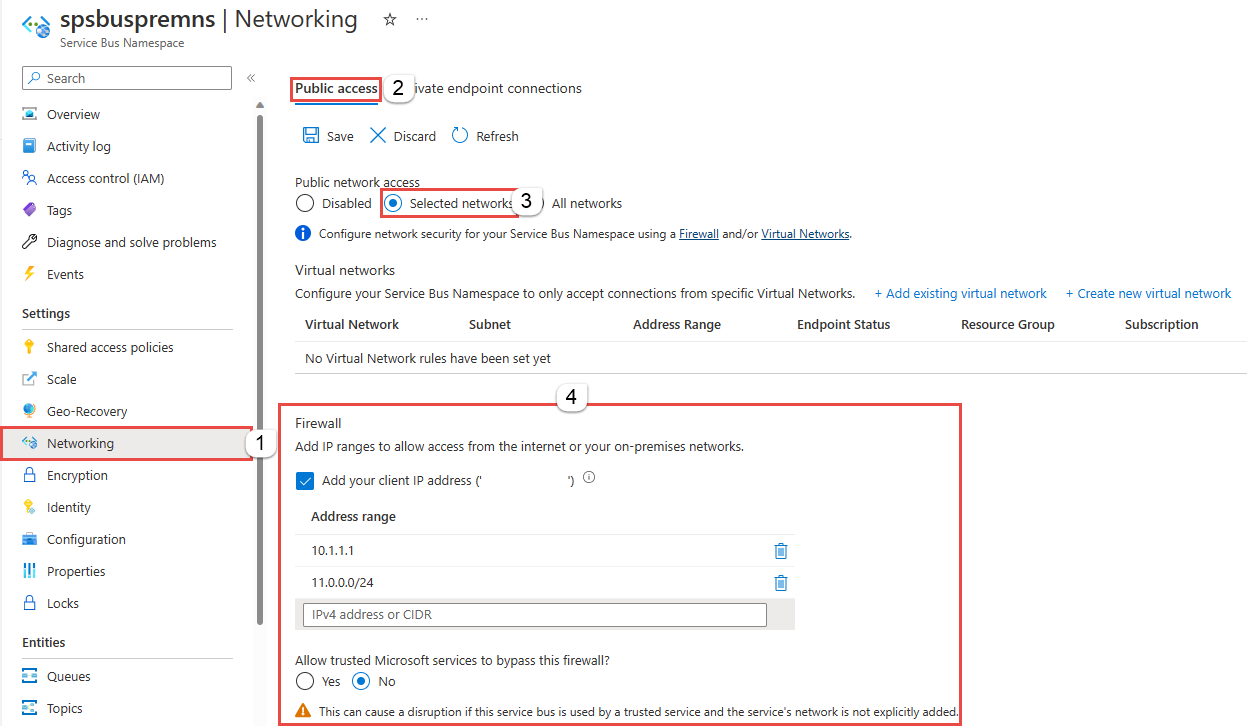
创建命名空间后,在“服务总线命名空间”页的左侧菜单中选择“网络”。 你会看到“所有网络”选项处于选中状态。 可以选择“所选网络”选项,允许来自特定 IP 地址或特定虚拟网络的访问。 下一部分详细介绍如何配置 IP 防火墙,以指定允许从其进行访问的 IP 地址。
为现有命名空间配置 IP 防火墙
本部分介绍了如何使用 Azure 门户为服务总线命名空间创建 IP 防火墙规则。
在 Azure 门户中,导航到“服务总线命名空间”。
在左侧菜单上,选择“设置”下的“网络”选项 。
Note
只会为“高级”命名空间显示“网络”选项卡 。
在“网络”页上,对于“公共网络访问”,可以设置以下三个选项之一。 选择“选定网络”选项将只允许从指定 IP 地址进行访问。
Disabled. 此选项禁用对命名空间的任何公共访问。 只能通过专用终结点访问命名空间。
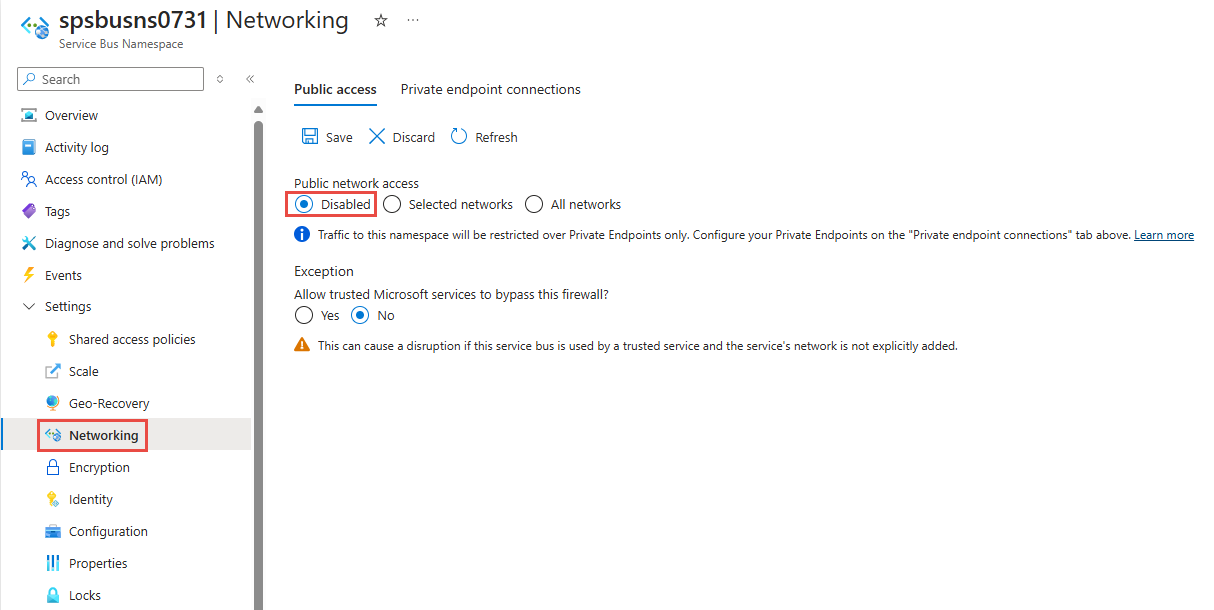
选择是否想要允许受信任的 Azure 服务绕过此防火墙。 有关 Azure 服务总线的受信任 Azure 服务列表,请参阅受信任的 Azure 服务部分。
所选网络。 此选项允许使用选定网络的访问密钥对命名空间进行公共访问。
Important
如果选择“选定网络”,请添加至少一个 IP 防火墙规则或有权访问命名空间的虚拟网络。 如果希望仅通过专用终结点限制流向此命名空间的所有流量,请选择“禁用”。
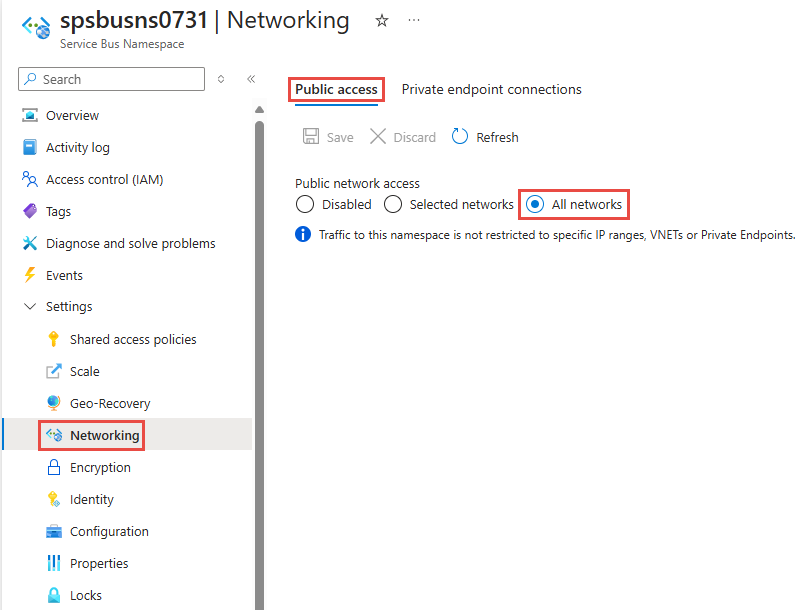
所有网络(默认)。 此选项允许使用访问密钥从所有网络进行公共访问。 如果选择“所有网络”选项,则服务总线会接受来自任何 IP 地址的连接(使用访问密钥)。 此设置等效于一个接受 0.0.0.0/0 IP 地址范围的规则。
若要仅允许从指定的 IP 地址进行访问,请选择“选定网络”选项(如果尚未选择)。 在“防火墙”部分中执行以下步骤:
选择“添加客户端 IP 地址”选项,使当前客户端 IP 可以访问命名空间。
对于“地址范围”,请输入某个特定的 IPv4 地址或以 CIDR 表示法表示的 IPv4 地址范围。
指定是否要“允许受信任的 Microsoft 服务绕过此防火墙”。 有关 Azure 服务总线的受信任 Azure 服务列表,请参阅受信任的 Azure 服务部分。
Warning
如果你在此页上选择了“所选网络”选项并且未添加至少一个 IP 防火墙规则或虚拟网络,则可以通过公共 Internet(使用访问密钥)访问该命名空间。
在工具栏上选择“保存”,保存这些设置。 请等待几分钟,直到门户通知中显示确认消息。
Note
若要限制对特定虚拟网络的访问,请参阅允许从特定网络访问。
受信任的 Microsoft 服务
启用“允许受信任的 Microsoft 服务绕过此防火墙”设置时,将授权以下服务访问你的服务总线资源。
Important
启用受信任的 Microsoft 服务时,请始终分配托管标识。 此标识可促进服务总线命名空间与受信任的 Azure 服务之间的安全通信。
| 受信任的服务 | 支持的使用方案 |
|---|---|
| Azure 事件网格 | 允许 Azure 事件网格将事件发送到服务总线命名空间中的队列或主题。 还需要执行以下步骤:
有关详细信息,请参阅使用托管标识进行事件传递 |
| Azure 流分析 | 允许 Azure 流分析作业将数据输出到服务总线队列到主题。 重要说明:流分析作业应配置为使用“托管标识”来访问服务总线命名空间。 为服务总线命名空间中的“Azure 服务总线数据发送方”角色添加标识。 |
| Azure IoT 中心 | 允许 IoT 中心将消息发送到服务总线命名空间中的队列或主题。 还需要执行以下步骤:
|
| Azure API 管理 | API 管理服务允许你向服务总线命名空间中的服务总线队列/主题发送消息。
|
| Azure Monitor(诊断设置和操作组) | 允许 Azure Monitor 将诊断信息和警报通知发送到服务总线命名空间中的服务总线。 Azure Monitor 可以从 Azure 服务总线命名空间读取和向其写入数据。 |
| Azure Synapse | 允许 Azure Synapse 使用 Synapse 工作区托管标识连接到服务总线。 将 Azure 服务总线数据发送方、接收方或所有者角色添加到 Azure 服务总线命名空间的标识中。 |
可在下面找到适用于 Azure 服务总线的其他受信任服务:
- Azure 数据资源管理器
- Azure Health Data Services
- Azure Arc
- Azure Kubernetes
- Azure 机器学习
- Microsoft Purview
- Microsoft Defender for Cloud
- Azure 提供程序中心
使用 Resource Manager 模板
本部分提供了一个用于将虚拟网络和防火墙规则添加到现有服务总线命名空间的 Azure 资源管理器模板示例。
ipMask 是单个 IPv4 地址或者是以 CIDR 表示法表示的一个 IP 地址块。 例如,在 CIDR 表示法中,70.37.104.0/24 表示从 70.37.104.0 到 70.37.104.255 的 256 个 IPv4 地址,其中 24 表示范围的有效前缀位数。
Note
defaultAction 的默认值为 Allow。 添加虚拟网络或防火墙规则时,请确保将 defaultAction 的值设置为 Deny。
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"namespace_name": {
"defaultValue": "mypremiumnamespace",
"type": "String"
}
},
"variables": {},
"resources": [
{
"type": "Microsoft.ServiceBus/namespaces",
"apiVersion": "2022-10-01-preview",
"name": "[parameters('namespace_name')]",
"location": "China East",
"sku": {
"name": "Premium",
"tier": "Premium",
"capacity": 1
},
"properties": {
"premiumMessagingPartitions": 1,
"minimumTlsVersion": "1.2",
"publicNetworkAccess": "Enabled",
"disableLocalAuth": false,
"zoneRedundant": true
}
},
{
"type": "Microsoft.ServiceBus/namespaces/networkRuleSets",
"apiVersion": "2022-10-01-preview",
"name": "[concat(parameters('namespace_name'), '/default')]",
"location": "China East",
"dependsOn": [
"[resourceId('Microsoft.ServiceBus/namespaces', parameters('namespace_name'))]"
],
"properties": {
"publicNetworkAccess": "Enabled",
"defaultAction": "Deny",
"virtualNetworkRules": [],
"ipRules": [
{
"ipMask": "10.1.1.1",
"action": "Allow"
},
{
"ipMask": "11.0.0.0/24",
"action": "Allow"
}
]
}
}
]
}
若要部署模板,请按照 Azure 资源管理器的说明进行操作。
Important
如果没有 IP 和虚拟网络规则,则所有流量都将流向命名空间,即使你将 defaultAction 设置为 deny。 可以通过公共 Internet(使用访问密钥)访问命名空间。 为命名空间指定至少一个 IP 规则或虚拟网络规则,以便仅允许来自虚拟网络的指定 IP 地址或子网的流量。
使用 Azure CLI
使用 az servicebus namespace network-rule-set 添加、列出、更新和移除命令来管理服务总线命名空间的 IP 防火墙规则。
使用 Azure PowerShell
使用以下 Azure PowerShell 命令来添加、列出、移除、更新和删除 IP 防火墙规则。
-
New-AzServiceBusIPRuleConfig和Set-AzServiceBusNetworkRuleSet一起用于添加 IP 防火墙规则。
默认操作和公用网络访问
REST API
API 为 2021-01-01-preview 版本及更早版本时,defaultAction 属性的默认值为 Deny。 但是,除非已设置 IP 筛选器或虚拟网络规则,否则不会强制实施拒绝规则。 即,如果没有任何 IP 筛选器或虚拟网络规则,服务总线会将该属性值视为 Allow。
从 2021-06-01-preview 及之后的 API 版本开始, 属性的默认值为 defaultAction,以准确反映服务端强制要求。 如果将默认操作设置为 Deny,则系统会强制执行 IP 筛选器和虚拟网络规则。 如果将默认操作设置为 Allow,则系统不会强制执行 IP 筛选器和虚拟网络规则。 关闭这些规则并重新打开后,服务会记住这些规则。
2021-06-01-preview 及之后的 API 版本还引入了一个名为 的新属性。 如果将其设置为 Disabled,则操作仅限于专用链接。 如果将其设置为 Enabled,则可通过公共 Internet 执行操作。
有关这些属性的详细信息,创建或更新专用终结点连接。
Note
以上设置都不会绕过通过 SAS 或 Microsoft Entra 身份验证对声明进行的验证。 身份验证检查始终在服务验证由 defaultAction、publicNetworkAccess、privateEndpointConnections 设置配置的网络检查后运行。
Azure 门户
Azure 门户始终使用最新的 API 版本来获取和设置属性。 如果你之前已使用 2021-01-01-preview 及更早版本配置了命名空间,已将 defaultAction 设置为 Deny,并且指定了零个 IP 筛选器和虚拟网络规则,则门户之前应已在命名空间的“网络”页上勾选“所选网络”。 现在,Azure 门户将检查“所有网络”选项。
相关内容
若要限制服务总线到 Azure 虚拟网络的访问,请参阅以下链接: