Azure 防火墙是一种云原生的智能网络防火墙安全服务,用于为 Azure 云工作负载提供顶层威胁防护。 它是一个服务形式的完全有状态防火墙,具有内置的高可用性和不受限制的云可伸缩性。 Azure 防火墙检查东-西和南-北流量。 若要了解这些流量类型,请参阅东-西和南-北流量。
Azure 防火墙在三个 SKU 中可用:基本、标准和高级。
Azure 防火墙基本版
Azure 防火墙基本版适用于中小型客户 (SMB),用于保护其 Azure 云环境。 它以负担得起的价格提供基本保护。
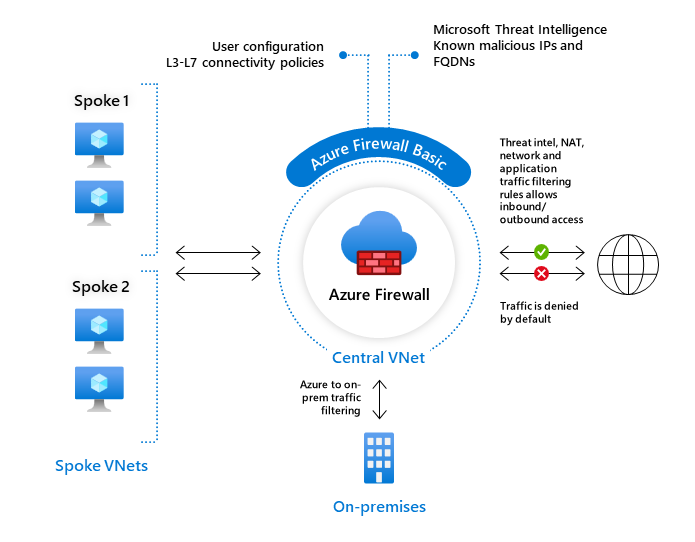
Azure 防火墙基本版的主要限制包括:
- 仅支持威胁 Intel 警报模式。
- 具有两个虚拟机后端实例的固定缩放单元
- 建议用于预估吞吐量为 250 Mbps 的环境
Azure 防火墙标准版
Azure 防火墙标准版直接从 Azure 网络安全提供 L3-L7 筛选和威胁情报源。 它可以发出警报,并阻止来自/发往已知恶意 IP 地址和域的流量,这些地址和域会实时更新以防范新兴威胁。
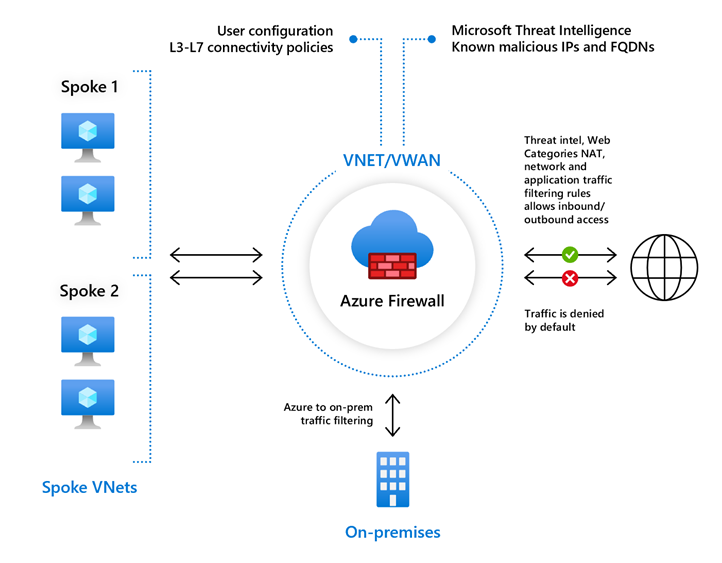
有关详细信息,请参阅 Azure 防火墙标准版功能。
Azure 防火墙高级版
Azure 防火墙高级版提供高级功能,包括基于签名的 IDPS,以便通过查找特定模式来快速检测攻击。 这些模式可能包括网络流量中的字节序列或恶意软件使用的已知恶意指令序列。 超过 50 个类别的 67,000 个签名实时更新,可防范恶意软件、网络钓鱼、硬币挖掘和特洛伊木马攻击等新兴攻击。
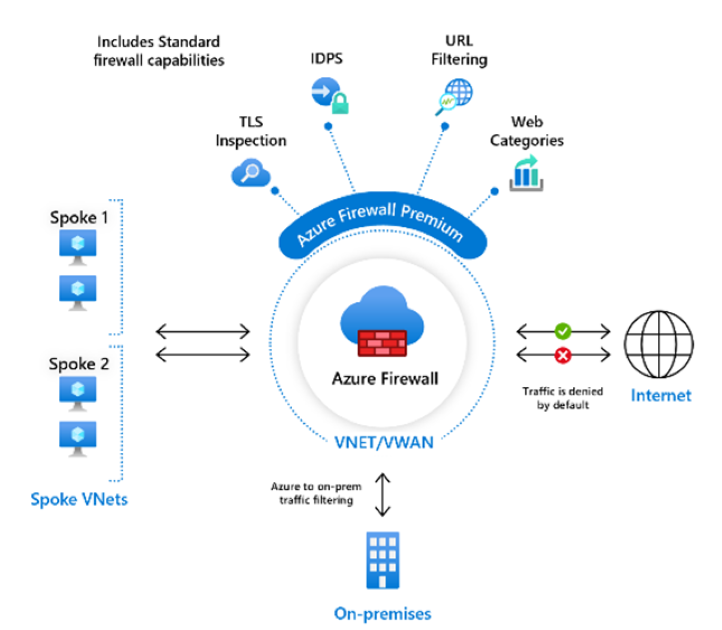
有关详细信息,请参阅 Azure 防火墙高级版功能。
功能比较
若要比较所有 Azure 防火墙 SKU 功能,请参阅根据需求选择合适的 Azure 防火墙 SKU。
Azure 防火墙管理器
Azure 防火墙管理器可以跨多个订阅集中管理 Azure 防火墙。 它使用防火墙策略,将一套通用的网络和应用程序规则和配置应用到租户中的防火墙。
防火墙管理器在虚拟网络和虚拟 WAN(安全虚拟中心)环境中都支持防火墙。 安全虚拟中心使用虚拟 WAN 路由自动化解决方案,来简化将流量路由到防火墙的过程 - 只需几个步骤便可完成。
有关详细信息,请参阅 Azure 防火墙管理器。
定价和 SLA
有关定价详细信息,请参阅 Azure 防火墙定价。
有关 SLA 的信息,请参阅 Azure 防火墙 SLA。
支持的区域
有关受支持区域的列表,请参阅 Azure 可用产品(按区域)。
新增功能
若要了解 Azure 防火墙的新增功能,请参阅 Azure 更新。
已知问题
有关已知问题,请参阅 Azure 防火墙已知问题。