拒绝分配类似于角色分配,可将一组拒绝操作附加到特定范围内的用户、组或服务主体,以便拒绝访问。 即使角色分配授予用户访问权限,拒绝分配也会阻止用户执行特定的 Azure 资源作。
本文介绍如何列出拒绝分配。
重要
不能直接创建自己的拒绝分配。 拒绝分配由 Azure 创建和管理。
如何创建拒绝分配
拒绝分配由 Azure 创建和管理以保护资源。 不能直接创建自己的拒绝分配。 但是,可以在创建部署堆栈时指定拒绝设置,这会创建部署堆栈资源拥有的拒绝分配。 有关详细信息,请参阅 Azure RBAC 限制。
比较角色分配和拒绝分配
拒绝分配遵循与角色分配类似的模式,但也存在一些差异。
| 能力 |
角色分配 |
拒绝分配 |
| 授予访问权限 |
✅ |
|
| 拒绝访问 |
|
✅ |
| 可以直接创建 |
✅ |
|
| 在某个范围应用 |
✅ |
✅ |
| 排除主体 |
|
✅ |
| 阻止子范围进行继承 |
|
✅ |
| 适用于经典订阅管理员分配。 |
|
✅ |
拒绝分配属性
拒绝分配具有以下属性:
| 资产 |
必选 |
类型 |
DESCRIPTION |
DenyAssignmentName |
是的 |
字符串 |
拒绝分配的显示名称。 对于给定作用域,名称必须是唯一的。 |
Description |
否 |
字符串 |
拒绝分配的说明。 |
Permissions.Actions |
至少一个 Actions 或一个 DataActions |
字符串数组[] |
一个字符串数组,用于指定拒绝分配阻止对其进行访问的控制平面操作。 |
Permissions.NotActions |
否 |
字符串数组[] |
一个字符串数组,用于指定要从拒绝分配中排除的控制平面操作。 |
Permissions.DataActions |
至少一个 Actions 或一个 DataActions |
字符串数组[] |
一个字符串数组,用于指定拒绝分配阻止对其进行访问的数据平面操作。 |
Permissions.NotDataActions |
否 |
字符串数组[] |
一个字符串数组,用于指定要从拒绝分配中排除的数据平面操作。 |
Scope |
否 |
字符串 |
用于指定拒绝分配应用到的作用域的字符串。 |
DoNotApplyToChildScopes |
否 |
布尔型 |
指定拒绝分配是否应用到子作用域。 默认值为 false。 |
Principals[i].Id |
是的 |
字符串数组[] |
拒绝分配应用到的 Microsoft Entra 主体对象 ID(用户、组、服务主体或托管主体)的数组。 设置为空 GUID 00000000-0000-0000-0000-000000000000 将表示所有主体。 |
Principals[i].Type |
否 |
字符串数组[] |
Principals[i].Id 所表示的对象类型的数组。设置为 SystemDefined 将表示所有主体。 |
ExcludePrincipals[i].Id |
否 |
字符串数组[] |
拒绝分配不会应用到的 Microsoft Entra 主体对象 ID(用户、组、服务主体或托管主体)的数组。 |
ExcludePrincipals[i].Type |
否 |
字符串数组[] |
ExcludePrincipals[i].Id 所表示的对象类型的数组。 |
IsSystemProtected |
否 |
布尔型 |
指定此拒绝分配是否由 Azure 创建,并且无法编辑或删除。 当前,所有拒绝分配受系统保护。 |
“所有主体”主体
为了支持拒绝分配,引入了名为“所有主体”的系统定义的主体。 此主体表示 Microsoft Entra 目录中的所有用户、组、服务主体和托管标识。 如果主体 ID 是零 GUID 00000000-0000-0000-0000-000000000000 且主体类型是 SystemDefined,则此主体表示所有主体。 在 Azure PowerShell 输出中,“所有主体”的外观如下所示:
Principals : {
DisplayName: All Principals
ObjectType: SystemDefined
ObjectId: 00000000-0000-0000-0000-000000000000
}
可以将“所有主体”与 ExcludePrincipals 组合使用来拒绝除了某些用户之外的所有主体。 “所有主体”具有以下约束:
- 只能用于
Principals,不能用于 ExcludePrincipals。
-
Principals[i].Type 必须设置为 SystemDefined。
列出拒绝分配
按照以下步骤列出拒绝分配。
重要
不能直接创建自己的拒绝分配。 拒绝分配由 Azure 创建和管理。
先决条件
如要获取拒绝分配的相关信息,必须具有:
-
Microsoft.Authorization/denyAssignments/read 权限,大多数 Azure 内置角色都包含该权限。
在 Azure 门户中列出拒绝分配
请执行以下步骤,在订阅或管理组范围列出拒绝分配。
在 Azure 门户中,打开所选范围,例如资源组或订阅。
选择“访问控制(IAM)”。
选择“拒绝分配”选项卡(或选择“查看拒绝分配”磁贴上的“视图”按钮)。
如果此范围内有任何拒绝分配或继承到此范围的角色,则会将其列出。
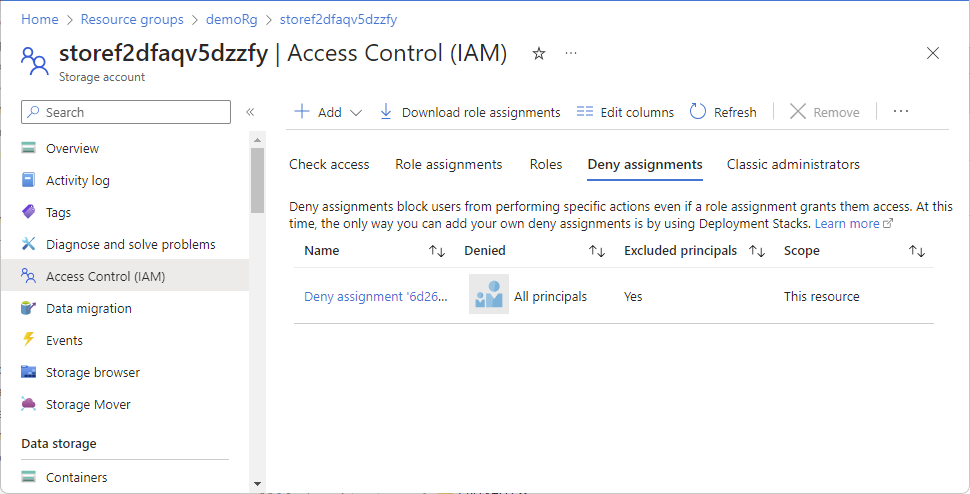
若要显示其他列,请选择“编辑列”。
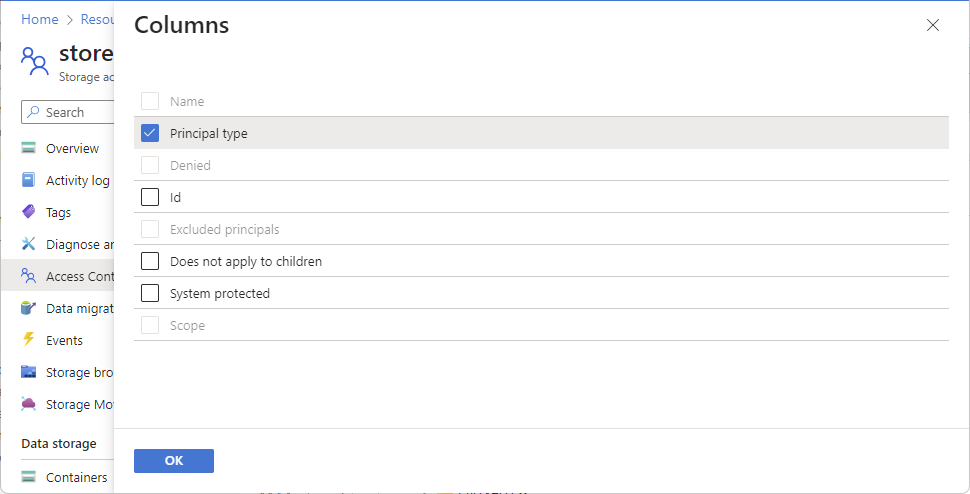
| 列 |
DESCRIPTION |
|
名称 |
拒绝分配的名称。 |
|
主体类型 |
用户、组、系统定义的组或服务主体。 |
|
已拒绝 |
包括在拒绝分配中的安全主体的名称。 |
|
Id |
拒绝分配的唯一标识符。 |
|
排除的主体 |
是否有排除在拒绝分配之外的安全主体。 |
|
不适用于儿童 |
是否已将拒绝分配继承到子范围。 |
|
受系统保护 |
拒绝分配是否由 Azure 托管。 当前始终为“是”。 |
|
范围 |
管理组、订阅、资源组或资源。 |
将一个复选标记添加到任何已启用的项,然后选择“确定”以显示所选列。
列出有关拒绝分配的详细信息
执行以下步骤,以便列出有关拒绝分配的更多详细信息。
按照上一部分的说明打开“拒绝分配”窗格。
选择拒绝分配名称,打开“用户”页。
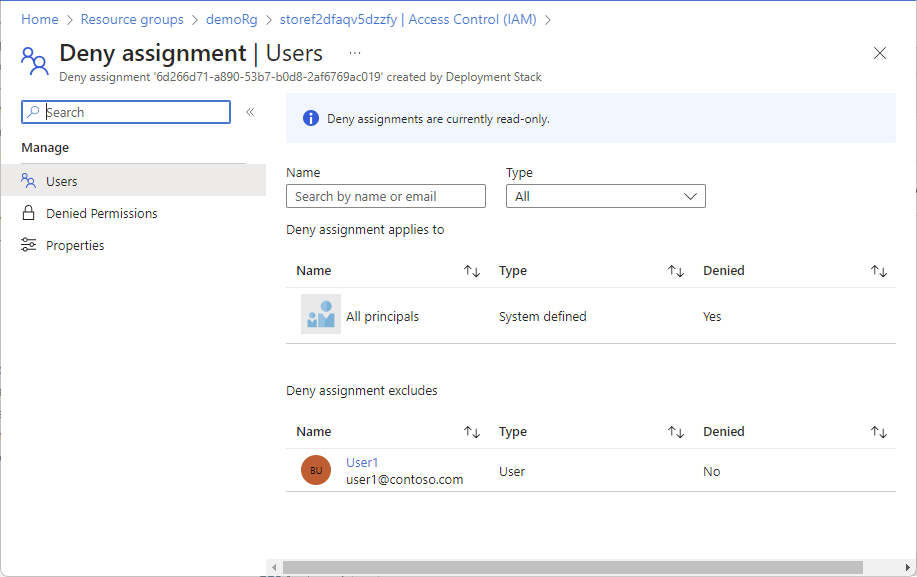
“用户”页包括下述两个部分。
| 拒绝设置 |
DESCRIPTION |
|
拒绝分配适用于 |
拒绝分配应用到的安全主体。 |
|
拒绝分配排除 |
排除在拒绝分配之外的安全主体。 |
系统定义的主体代表 Azure AD 目录中的所有用户、组、服务主体和托管标识。
若要查看已拒绝权限的列表,请选择“已拒绝权限”。
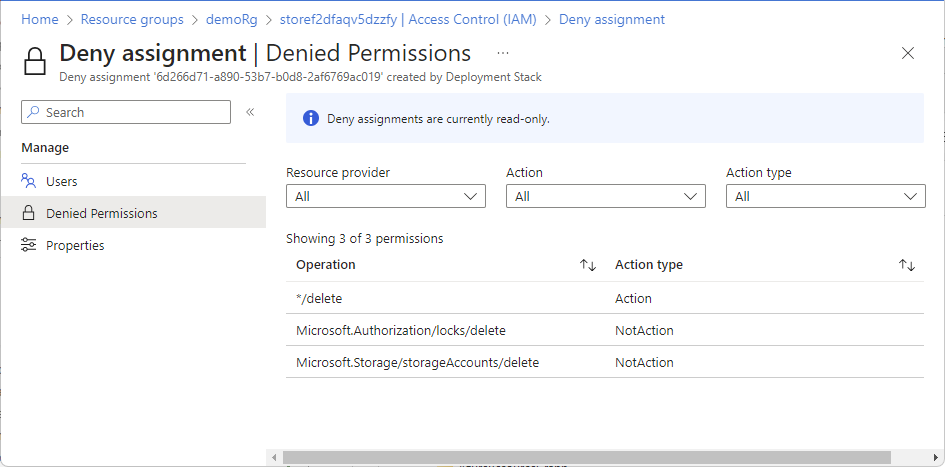
| 操作类型 |
DESCRIPTION |
|
行动 |
拒绝控制平面操作。 |
|
不操作 |
从拒绝控制平面操作中排除的控制平面操作。 |
|
DataActions |
拒绝数据平面操作。 |
|
NotDataActions |
从拒绝数据平面操作中排除的数据平面操作。 |
就上一屏幕截图中显示的示例来说,下面是有效的权限:
若要查看拒绝分配的属性,请选择“属性”。
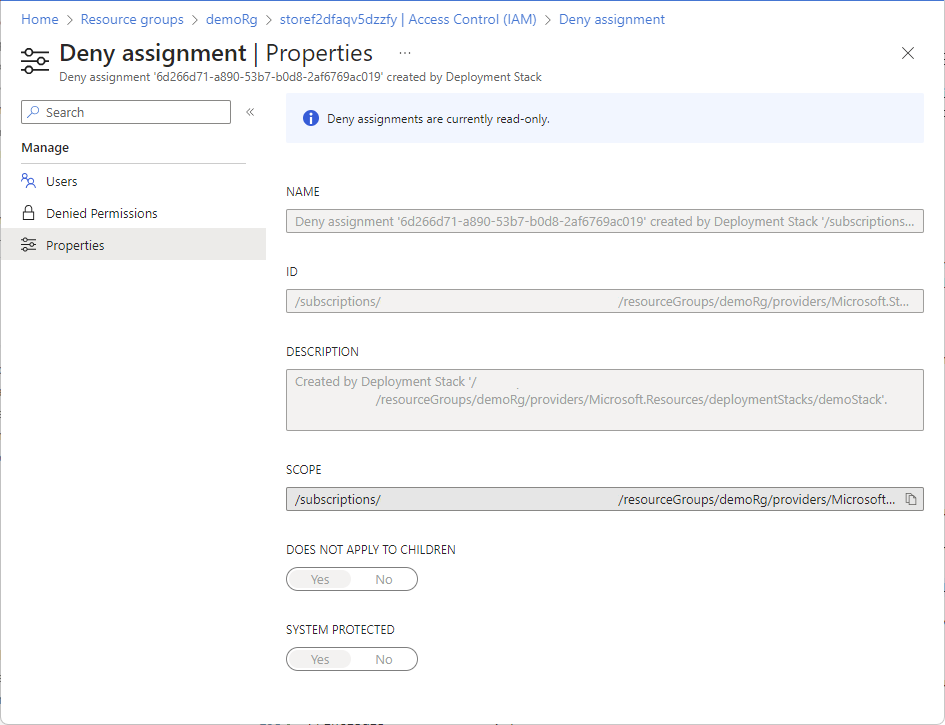
在“属性”页上,可以看到拒绝分配名称、ID、说明和范围。 “不适用于儿童”开关指示是否已将拒绝分配继承到子范围。 “受系统保护”开关指示此拒绝分配是否由 Azure 托管。 当前,所有情况下此项均为“是”。
先决条件
如要获取拒绝分配的相关信息,必须具有:
列出所有拒绝分配
若要列出当前订阅的所有“拒绝分配”信息,请使用 Get-AzDenyAssignment。
Get-AzDenyAssignment
PS C:\> Get-AzDenyAssignment
Id : /subscriptions/11111111-1111-1111-1111-111111111111/resourceGroups/demoRg/providers/Microsoft.Storage/storageAccounts/storef2dfaqv5dzzfy/providers/Microsoft.Authorization/denyAssignments/6d266d71-a890-53b7-b0d8-2af6769ac019
DenyAssignmentName : Deny assignment '6d266d71-a890-53b7-b0d8-2af6769ac019' created by Deployment Stack '/subscriptions/11111111-1111-1111-1111-111111111111/resourceGroups/demoRg/providers/Microsoft.Resources/deploymentStacks/demoStack'.
Description : Created by Deployment Stack '/subscriptions/11111111-1111-1111-1111-111111111111/resourceGroups/demoRg/providers/Microsoft.Resources/deploymentStacks/demoStack'.
Actions : {*/delete}
NotActions : {Microsoft.Authorization/locks/delete, Microsoft.Storage/storageAccounts/delete}
DataActions : {}
NotDataActions : {}
Scope : /subscriptions/11111111-1111-1111-1111-111111111111/resourceGroups/demoRg/providers/Microsoft.Storage/storageAccounts/storef2dfaqv5dzzfy
DoNotApplyToChildScopes : True
Principals : {
DisplayName: All Principals
ObjectType: SystemDefined
ObjectId: 00000000-0000-0000-0000-000000000000
}
ExcludePrincipals : {
DisplayName: User1
ObjectType: User
ObjectId: 675986ff-5b6a-448c-9a22-fd2a65100221
}
IsSystemProtected : True
Id : /subscriptions/11111111-1111-1111-1111-111111111111/resourceGroups/demoRg/providers/Microsoft.Network/virtualNetworks/vnetf2dfaqv5dzzfy/providers/Microsoft.Authorization/denyAssignments/36a162b5-ddcc-529a-9deb-673250f90ba7
DenyAssignmentName : Deny assignment '36a162b5-ddcc-529a-9deb-673250f90ba7' created by Deployment Stack '/subscriptions/11111111-1111-1111-1111-111111111111/resourceGroups/demoRg/providers/Microsoft.Resources/deploymentStacks/demoStack'.
Description : Created by Deployment Stack '/subscriptions/11111111-1111-1111-1111-111111111111/resourceGroups/demoRg/providers/Microsoft.Resources/deploymentStacks/demoStack'.
Actions : {*/delete}
NotActions : {Microsoft.Authorization/locks/delete, Microsoft.Storage/storageAccounts/delete}
DataActions : {}
NotDataActions : {}
Scope : /subscriptions/11111111-1111-1111-1111-111111111111/resourceGroups/demoRg/providers/Microsoft.Network/virtualNetworks/vnetf2dfaqv5dzzfy
DoNotApplyToChildScopes : True
Principals : {
DisplayName: All Principals
ObjectType: SystemDefined
ObjectId: 00000000-0000-0000-0000-000000000000
}
ExcludePrincipals : {
DisplayName: User1
ObjectType: User
ObjectId: 675986ff-5b6a-448c-9a22-fd2a65100221
}
IsSystemProtected : True
列出资源组范围内的拒绝分配
若要列出资源组范围内的所有拒绝分配,请使用 Get-AzDenyAssignment。
Get-AzDenyAssignment -ResourceGroupName <resource_group_name>
列出订阅范围内的拒绝分配
若要列出订阅范围内的所有拒绝分配,请使用 Get-AzDenyAssignment。 若要获取订阅 ID,可以在 Azure 门户中的“订阅”页上找到它,也可以使用 Get-AzSubscription。
Get-AzDenyAssignment -Scope /subscriptions/<subscription_id>
先决条件
如要获取拒绝分配的相关信息,必须具有:
-
Microsoft.Authorization/denyAssignments/read 权限,大多数 Azure 内置角色都包含该权限。
必须使用以下版本:
-
2018-07-01-preview 或更高版本
-
2022-04-01 是第一个稳定版本
列出单个拒绝分配
若要列出单个拒绝分配,请使用拒绝分配 - 获取 REST API。
从下面的请求开始:
GET https://management.chinacloudapi.cn/{scope}/providers/Microsoft.Authorization/denyAssignments/{deny-assignment-id}?api-version=2022-04-01
在 URI 中,将 {scope} 替换为要列出拒绝分配的范围。
| 范围 |
类型 |
subscriptions/{subscriptionId} |
订阅 |
subscriptions/{subscriptionId}/resourceGroups/myresourcegroup1 |
资源组 |
subscriptions/{subscriptionId}/resourceGroups/myresourcegroup1/providers/Microsoft.Web/sites/mysite1 |
资源 |
将 {deny-assignment-id} 替换为要检索的拒绝分配标识符。
列出多个拒绝分配
若要列出多个拒绝分配,请使用拒绝分配 - 列出 REST API。
先处理下述请求之一:
GET https://management.chinacloudapi.cn/{scope}/providers/Microsoft.Authorization/denyAssignments?api-version=2022-04-01
含有可选参数:
GET https://management.chinacloudapi.cn/{scope}/providers/Microsoft.Authorization/denyAssignments?api-version=2022-04-01&$filter={filter}
在 URI 中,将 {scope} 替换为要列出拒绝分配的范围。
| 范围 |
类型 |
subscriptions/{subscriptionId} |
订阅 |
subscriptions/{subscriptionId}/resourceGroups/myresourcegroup1 |
资源组 |
subscriptions/{subscriptionId}/resourceGroups/myresourcegroup1/providers/Microsoft.Web/sites/mysite1 |
资源 |
将 {filter} 替换为筛选拒绝分配列表时要应用的条件。
| 过滤器 |
DESCRIPTION |
| (无筛选器) |
列出指定范围之内、之上和之下的所有拒绝分配。 |
$filter=atScope() |
仅列出指定范围内及其上的拒绝分配。 不包含子范围处的拒绝分配。 |
$filter=assignedTo('{objectId}') |
列出指定用户或服务主体的拒绝分配。
如果用户属于包含拒绝分配的组,则也会列出该拒绝分配。 此筛选器对于组是可传递的,这意味着如果用户是组的成员,并且该组是包含拒绝分配的另一个组的成员,则该拒绝分配也会列出。
此筛选器仅接受用户或服务主体的对象 ID。 不能传递组的对象 ID。 |
$filter=atScope()+and+assignedTo('{objectId}') |
列出指定范围内指定用户或服务主体的拒绝分配。 |
$filter=denyAssignmentName+eq+'{deny-assignment-name}' |
列出具有指定名称的拒绝分配。 |
$filter=principalId+eq+'{objectId}' |
列出指定用户、组或服务主体的拒绝分配。 |
列出根范围 (/) 处的拒绝分配
提升访问权限,如提升访问权限以管理所有 Azure 订阅和管理组所述。
使用以下请求:
GET https://management.chinacloudapi.cn/providers/Microsoft.Authorization/denyAssignments?api-version=2022-04-01&$filter={filter}
将 {filter} 替换为筛选拒绝分配列表时要应用的条件。 需使用筛选器。
| 过滤器 |
DESCRIPTION |
$filter=atScope() |
仅列出根范围处的拒绝分配。 不包含子范围处的拒绝分配。 |
$filter=denyAssignmentName+eq+'{deny-assignment-name}' |
列出具有指定名称的拒绝分配。 |
删除已提升的访问权限。




